F-Secure to Acquire Lookout Mobile Security
F secure to acquire lookout mobile security – F-Secure to acquire Lookout Mobile Security: This major move in the cybersecurity world has sent ripples through the industry. The acquisition promises a significant boost to F-Secure’s mobile security portfolio, combining their existing strengths with Lookout’s cutting-edge threat detection capabilities. This potential merger is a fascinating case study in strategic acquisitions, raising questions about market dominance, technological integration, and the future of mobile security itself.
Let’s dive into the details and explore the implications.
The deal, if finalized, would see F-Secure, a well-established name in cybersecurity, absorb Lookout, a leader in mobile endpoint security. This combination of expertise and technology could create a formidable player, potentially reshaping the competitive landscape. We’ll examine the synergies, potential challenges, and the long-term vision for the combined entity. The financial implications, regulatory hurdles, and market reactions will also be key areas of discussion.
F-Secure’s Current Market Position
F-Secure, a veteran in the cybersecurity industry, holds a respectable, though not dominant, position in the mobile security market. While they’ve established a strong reputation for their comprehensive endpoint protection solutions for businesses and consumers, their mobile security offerings haven’t quite achieved the same market penetration as some of their larger competitors. Understanding their current standing is crucial to assessing the strategic implications of the proposed Lookout acquisition.F-Secure’s existing mobile security products typically include features like antivirus protection, anti-phishing, VPN services, and app control.
These features are generally well-regarded for their effectiveness, but their market share remains relatively modest compared to giants like McAfee, Norton, or even smaller, more specialized players. Precise market share figures are difficult to obtain publicly and fluctuate constantly, but industry analyses consistently place F-Secure in the second or third tier of mobile security providers.
F-Secure’s Strengths and Weaknesses in Mobile Security
F-Secure’s strengths lie in its established brand reputation for security expertise, its strong enterprise solutions, and its generally positive user reviews for its mobile offerings. Their focus on privacy and user-friendly interfaces also contributes to their appeal. However, weaknesses include a smaller market share compared to major competitors, potentially limiting their reach and economies of scale. Additionally, a perceived lack of cutting-edge features in certain areas, such as advanced threat detection and AI-powered security, could be considered a drawback.
This may hinder their ability to attract users seeking the most advanced protection options.
F-Secure’s Strategic Goals and Alignment with the Lookout Acquisition
F-Secure’s strategic goals likely center on expanding their market share in the mobile security sector, particularly in the increasingly lucrative enterprise mobile security market. The acquisition of Lookout, a company known for its strong enterprise mobile threat defense (MTD) capabilities, directly addresses this goal. Lookout’s expertise in cloud-based security, advanced threat detection, and endpoint management would significantly bolster F-Secure’s offerings and allow them to compete more effectively against larger players.
The combined entity would gain access to a wider range of customers and technologies, strengthening F-Secure’s position in the mobile security landscape and enhancing its overall value proposition. For example, integrating Lookout’s capabilities into F-Secure’s existing enterprise security platform would create a more comprehensive and competitive solution, appealing to businesses seeking a single, unified security platform.
Lookout’s Mobile Security Capabilities
Lookout is a prominent player in the mobile security space, boasting a robust suite of features designed to protect both individual users and enterprise clients. Their technology goes beyond basic antivirus, incorporating advanced threat detection and response mechanisms to address the ever-evolving landscape of mobile malware and vulnerabilities. This analysis will delve into the specifics of Lookout’s capabilities, comparing them to F-Secure’s offerings and evaluating their overall strengths and weaknesses.Lookout’s core functionality centers around proactive threat detection and prevention.
This includes traditional antivirus scanning, but also extends to sophisticated techniques like machine learning to identify zero-day threats – malware that hasn’t been seen before. They leverage behavioral analysis to detect malicious apps even before they can fully execute harmful code. Further enhancing security, Lookout offers features like VPN for encrypted browsing and secure Wi-Fi connection management.
For enterprise customers, Lookout provides robust Mobile Device Management (MDM) capabilities, enabling centralized control and security policies for company-owned and BYOD (Bring Your Own Device) devices.
Lookout’s Key Features and Technologies
Lookout’s technology stack is built on a multi-layered approach to mobile threat detection. This involves a combination of cloud-based threat intelligence, on-device analysis, and machine learning algorithms. The cloud infrastructure constantly updates its threat database, allowing for rapid identification of new malware strains. Simultaneously, on-device analysis ensures that threats are identified even without a network connection. The machine learning component plays a crucial role in detecting subtle behavioral patterns that may indicate malicious activity, even in the absence of known malware signatures.
F-Secure acquiring Lookout’s mobile security expertise is a big deal, strengthening their overall security portfolio. This move highlights the growing importance of robust mobile security, especially considering the complexities of modern app development. Thinking about that, I was recently reading a great article on domino app dev the low code and pro code future , which got me thinking about how crucial secure development practices are for these apps.
Ultimately, F-Secure’s acquisition underscores the need for comprehensive security solutions across all platforms.
This proactive approach helps Lookout stay ahead of the curve in the constantly shifting mobile threat landscape. For example, Lookout’s machine learning algorithms can identify and flag apps exhibiting suspicious network behavior, such as excessive data transmission to unknown servers.
Comparison of Customer Base and Market Penetration
While precise figures on customer base and market share are often proprietary, it’s clear that both Lookout and F-Secure cater to different market segments. Lookout has a strong presence in the enterprise market, particularly with larger corporations needing robust MDM solutions and secure access to corporate data. F-Secure, on the other hand, has a broader consumer base and a strong presence in the home user market with its consumer-focused security products.
While both companies have overlapping customer segments, Lookout’s focus on enterprise solutions differentiates it from F-Secure’s broader consumer and SMB focus. For example, a large financial institution might choose Lookout for its robust MDM capabilities and compliance features, while a small business might opt for F-Secure’s more comprehensive and potentially less expensive suite of products.
Lookout’s Strengths and Weaknesses
Lookout’s strengths lie in its advanced threat detection technology, particularly its proactive approach using machine learning and behavioral analysis. Its strong focus on enterprise solutions and robust MDM capabilities provides a competitive edge in the enterprise security market. However, a potential weakness could be its relative smaller market share compared to more established players like F-Secure in certain consumer segments.
While Lookout’s technology is sophisticated, its brand recognition among average consumers might be lower than some competitors, which could limit its reach in the consumer market. Another area for potential improvement could be enhancing the user experience to be more intuitive and user-friendly for less technically inclined individuals, especially in its consumer offerings.
Synergies and Potential Benefits of the Acquisition
The acquisition of Lookout by F-Secure presents a compelling opportunity to create a significantly stronger player in the cybersecurity market. By combining F-Secure’s established enterprise security solutions with Lookout’s expertise in mobile threat detection and response, the merged entity can offer a truly comprehensive and unified security platform. This synergy extends beyond simple technological integration; it also encompasses a broadened customer base and enhanced operational efficiencies.The combined strengths of F-Secure and Lookout create a powerful synergy, offering a more robust and comprehensive security solution than either company could provide individually.
F-Secure’s strengths in endpoint protection and enterprise security management complement Lookout’s leading mobile threat detection capabilities. This combination allows for a seamless, integrated security posture across all devices and platforms, significantly reducing the attack surface for businesses.
Enhanced Mobile Security Solution
The combined entity will be able to offer a significantly more comprehensive mobile security solution. F-Secure’s existing endpoint protection solutions can be integrated with Lookout’s mobile threat detection and response capabilities, providing a unified security platform that protects both corporate and personal devices. This unified approach will simplify security management for businesses, reducing complexity and improving overall security posture.
For example, a company using F-Secure’s endpoint protection could seamlessly integrate Lookout’s mobile threat intelligence, enabling proactive threat identification and response across all devices used by employees. This integrated approach offers superior protection compared to using disparate solutions from different vendors.
Cost Savings and Operational Efficiencies
The merger of F-Secure and Lookout is expected to generate significant cost savings and operational efficiencies. By consolidating operations, the combined entity can reduce redundancies in infrastructure, personnel, and processes. This streamlining can lead to significant cost reductions in areas such as IT infrastructure, software licensing, and customer support. Furthermore, the combined customer base allows for economies of scale in marketing and sales, leading to improved profitability.
For example, a single sales team could address both enterprise and mobile security needs, eliminating the need for separate sales forces. The consolidated research and development efforts could also lead to faster innovation and more efficient product development.
Feature Comparison: Before and After Merger
This table illustrates the key features of F-Secure and Lookout before the hypothetical merger and the potential combined offering.
| Feature | F-Secure (Before) | Lookout (Before) | Combined Entity (After) |
|---|---|---|---|
| Endpoint Protection | Strong endpoint protection for desktops and laptops | Limited endpoint protection | Enhanced endpoint protection across all devices (desktops, laptops, mobiles) |
| Mobile Threat Detection | Basic mobile security features | Advanced mobile threat detection and response | Comprehensive mobile threat detection and response integrated with endpoint protection |
| Data Loss Prevention (DLP) | Robust DLP capabilities | Basic DLP capabilities | Advanced DLP capabilities across all devices |
| Security Management Console | Centralized management console for endpoint protection | Separate management console for mobile security | Unified management console for all devices and security features |
| Customer Base | Strong enterprise customer base | Significant mobile security customer base | Expanded customer base covering both enterprise and mobile segments |
Financial Implications and Valuation
The acquisition of Lookout by F-Secure presents a complex financial picture, requiring careful analysis of potential costs, returns, and financing strategies. Estimating the acquisition price and its subsequent impact on F-Secure’s financial statements necessitates considering Lookout’s current valuation, which is likely influenced by factors such as its revenue, growth trajectory, market share, and intellectual property portfolio. The potential ROI for F-Secure hinges on successful integration, market expansion, and the realization of synergies.
Several financing options exist, each with its own implications for F-Secure’s capital structure and future financial flexibility.
Potential Acquisition Cost and Impact on F-Secure’s Financial Statements
Estimating the acquisition cost for Lookout is challenging without access to private financial information. However, we can consider comparable acquisitions in the cybersecurity sector to provide a reasonable range. For example, if we assume Lookout’s valuation is comparable to other mid-sized cybersecurity firms acquired in recent years – perhaps in the range of $500 million to $1 billion – this would represent a significant investment for F-Secure.
The impact on F-Secure’s financial statements would include a substantial increase in goodwill (an intangible asset reflecting the premium paid over Lookout’s net asset value) and potentially increased debt levels depending on the financing method. This would, in turn, affect key financial ratios such as debt-to-equity and leverage, impacting credit ratings and potentially investor sentiment. Post-acquisition, F-Secure’s revenue would increase, but profitability would depend on successful integration and cost synergies.
A detailed financial model, incorporating projected revenue growth, cost reductions, and amortization of goodwill, would be necessary to accurately assess the long-term impact.
Potential Return on Investment (ROI)
The potential ROI for F-Secure hinges on several key factors. Successful integration of Lookout’s technology and customer base is crucial. Realizing synergies, such as reduced operational costs and cross-selling opportunities, is also essential. Expansion into new markets, leveraging Lookout’s established presence, is another critical driver of ROI. The expected increase in market share and the potential for higher pricing power resulting from a more comprehensive product portfolio would also positively influence the ROI.
To illustrate, let’s assume a scenario where the acquisition generates an additional $100 million in revenue within three years, with cost synergies yielding $20 million in savings annually. This would significantly improve F-Secure’s bottom line, justifying the acquisition cost. However, a detailed financial projection model incorporating various scenarios and risk assessments would be necessary for a robust ROI analysis.
Such a model should account for potential risks such as integration challenges, competition, and market volatility.
Potential Financing Options
F-Secure could pursue several financing options to fund the Lookout acquisition. These include: debt financing (through bank loans or bond issuance), equity financing (through issuing new shares), or a combination of both. Debt financing offers the advantage of maintaining control, but increases financial risk and interest expenses. Equity financing dilutes existing shareholders but avoids increasing debt burden.
The optimal financing strategy would depend on F-Secure’s existing financial position, risk tolerance, and market conditions. For instance, if F-Secure has a strong balance sheet and access to favorable debt financing terms, a debt-heavy approach might be considered. Conversely, if the company seeks to minimize financial risk, a more equity-focused approach might be preferred. A blend of debt and equity financing is also possible, allowing F-Secure to balance risk and control.
The chosen financing strategy will significantly influence F-Secure’s post-acquisition capital structure and its long-term financial health.
Competitive Landscape and Market Reactions: F Secure To Acquire Lookout Mobile Security
The F-Secure acquisition of Lookout significantly alters the mobile security landscape, impacting both direct and indirect competitors. Understanding the existing competitive environment and anticipating market reactions is crucial for assessing the deal’s long-term success. The merger brings together two companies with distinct strengths, potentially creating a formidable competitor and prompting responses from established players.The acquisition’s impact hinges on how effectively F-Secure integrates Lookout’s technology and expands its market reach.
Successful integration could lead to increased market share and a stronger competitive position, while integration challenges could expose vulnerabilities and invite opportunistic attacks from rivals.
Main Competitors in the Mobile Security Market
Prior to the acquisition, both F-Secure and Lookout faced competition from a range of established players in the mobile security market. Key competitors included large technology companies with integrated security suites (like Microsoft, Google, and Apple), specialized cybersecurity firms offering comprehensive mobile security solutions (like McAfee and Norton), and smaller, niche players focusing on specific security aspects. Lookout, with its strong presence in the enterprise mobile security space, also competed with providers like VMware Workspace ONE and MobileIron.
F-Secure, meanwhile, held a strong position in the consumer and enterprise markets, competing with the aforementioned players and others offering endpoint protection.
Potential Impact on the Competitive Landscape
The combined entity of F-Secure and Lookout creates a stronger competitor with a broader portfolio of products and services, enhanced capabilities in mobile threat detection and response, and an expanded customer base. This could lead to increased competition for existing players, forcing them to adapt their strategies and offerings to remain competitive. Smaller players might find it harder to compete on features, pricing, or market reach, potentially leading to consolidation or niche specialization within the market.
Larger players might respond by accelerating their own product development or through strategic acquisitions of their own. The acquisition could also trigger a wave of innovation as competitors strive to maintain their market share and offer superior solutions.
Predicted Market Reactions
The market’s reaction to the F-Secure-Lookout acquisition will likely be multifaceted. Initial reactions could range from cautious optimism to outright concern, depending on the perspective of different stakeholders. Investors will likely analyze the financial implications, assessing the potential for increased profitability and market share. Customers might be curious about the integration process and the impact on product offerings and support.
Competitors will assess the strategic implications and consider their own responses, potentially leading to a reshuffling of the market landscape. Regulatory bodies might scrutinize the acquisition to ensure it doesn’t lead to anti-competitive practices.
Potential Competitor Reactions
The following are potential reactions from competitors in the mobile security market:
- Increased investment in R&D: Competitors might accelerate their own research and development efforts to enhance their products and stay ahead of the combined F-Secure-Lookout entity.
- Strategic acquisitions: Competitors might pursue their own acquisitions to bolster their capabilities and market share, mirroring F-Secure’s move.
- Price adjustments: Competitors might adjust their pricing strategies to remain competitive, either lowering prices to attract customers or increasing them to reflect enhanced features.
- Enhanced marketing and sales efforts: Competitors could intensify their marketing and sales campaigns to maintain brand visibility and attract customers.
- Focus on differentiation: Competitors might focus on differentiating their offerings by emphasizing specific features or targeting niche markets that F-Secure-Lookout might not fully address.
- Increased focus on partnerships and collaborations: Competitors may look to strengthen alliances and collaborations to leverage complementary technologies and expand their reach.
Regulatory and Legal Considerations
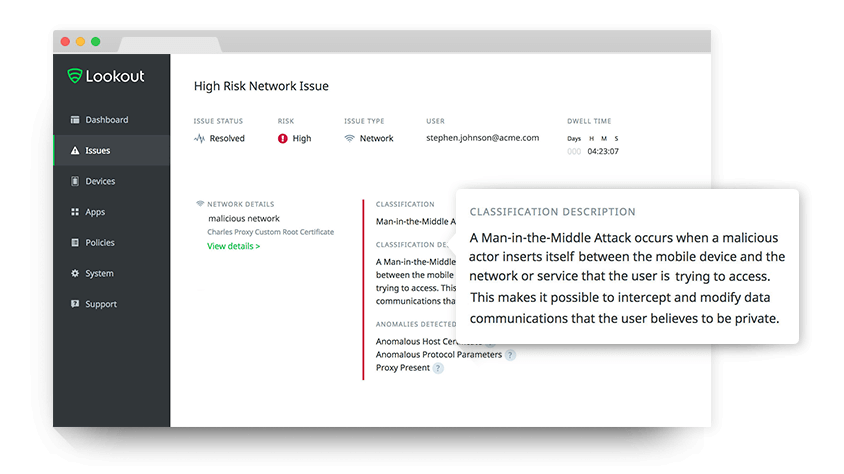
The acquisition of Lookout by F-Secure, while strategically sound, presents a number of regulatory and legal hurdles that need careful consideration. The process will involve navigating complex antitrust laws, data privacy regulations, and international legal frameworks, potentially impacting the timeline and final outcome of the deal. Failure to adequately address these issues could lead to significant delays, increased costs, or even the termination of the acquisition.The primary concern centers around antitrust regulations.
Authorities in various jurisdictions will scrutinize the merger to determine whether it creates or enhances market power, leading to reduced competition and potentially harming consumers. This analysis will consider the combined market share of F-Secure and Lookout in the mobile security sector, their respective product offerings, and the presence of other significant competitors. The review process will involve submitting detailed information about the acquisition to relevant regulatory bodies, responding to inquiries, and potentially engaging in negotiations to address any concerns raised.
Antitrust Review Processes
The legal processes involved are multifaceted and vary depending on the jurisdictions involved. Generally, the acquisition will need to be reviewed by competition authorities in key markets where both companies operate. This often involves submitting a detailed notification to the relevant authorities, providing information on the companies’ market positions, product offerings, and the potential impact of the merger on competition.
These authorities will then conduct their own investigations, potentially requesting additional information and engaging in discussions with the companies. In some cases, they might require concessions, such as the divestiture of certain assets, to address antitrust concerns before approving the acquisition. For example, the European Commission’s review process typically involves a detailed investigation and can take several months, sometimes even longer.
Similar processes are followed in the United States by the Department of Justice and the Federal Trade Commission.
Data Privacy and Security Compliance, F secure to acquire lookout mobile security
The acquisition will also need to address data privacy and security regulations, such as GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the United States. Both F-Secure and Lookout handle sensitive user data, and the merger will necessitate a thorough assessment of their data handling practices to ensure compliance with these regulations. This involves evaluating data transfer mechanisms, security protocols, and user consent procedures to guarantee the continued protection of user data post-acquisition.
Failure to address these concerns could lead to significant fines and reputational damage. For example, non-compliance with GDPR can result in hefty fines of up to €20 million or 4% of annual global turnover, whichever is higher.
Addressing Potential Legal Challenges
F-Secure can mitigate potential legal challenges through proactive measures. This includes conducting thorough due diligence before the acquisition, engaging experienced legal counsel specializing in antitrust and data privacy, and proactively engaging with regulatory authorities to address any concerns early on. Furthermore, F-Secure might need to develop and implement comprehensive integration plans that address data privacy and security concerns, demonstrating to regulators a commitment to maintaining high standards of data protection post-merger.
F-Secure’s acquisition of Lookout mobile security is a big deal, strengthening their mobile threat defense capabilities. This move highlights the growing importance of comprehensive security across all devices, especially as we see the rise of cloud-based threats. Understanding the complexities of cloud security is crucial, which is why I recommend checking out this insightful article on bitglass and the rise of cloud security posture management for a better grasp of the landscape.
Ultimately, F-Secure’s acquisition underscores the need for robust, integrated security solutions in today’s interconnected world.
Open communication and collaboration with regulatory bodies are crucial throughout the process to ensure a smooth transition and avoid costly delays or legal disputes. A well-structured and transparent approach can significantly increase the chances of a successful acquisition.
Integration Challenges and Strategies
Integrating Lookout’s technology and operations into F-Secure will present a complex undertaking, requiring careful planning and execution to minimize disruption and maximize the benefits of the acquisition. Success hinges on a well-defined strategy addressing technological compatibility, customer migration, and risk mitigation.The integration process will inevitably face several hurdles. These include differing technological architectures, potentially incompatible data formats, and the need to reconcile distinct security approaches.
Cultural differences between the two organizations, including varying management styles and corporate cultures, also pose a significant challenge. Furthermore, ensuring a seamless transition for Lookout’s existing customer base without impacting their service experience will be critical.
Technological Integration Challenges and Solutions
Successfully merging Lookout’s mobile security technology with F-Secure’s existing suite requires a phased approach. Initial efforts should focus on identifying areas of overlap and potential conflicts between the two systems. A detailed technical assessment, involving experts from both companies, is essential to map out the integration process. This assessment should include data migration planning, API integration, and the development of a comprehensive compatibility matrix.
For instance, Lookout’s endpoint detection and response (EDR) capabilities might need to be carefully integrated with F-Secure’s existing endpoint protection platform, potentially requiring adjustments to both systems to ensure interoperability. A parallel run of both systems for a period of time, allowing for a gradual transition, can mitigate the risk of significant disruption. This phased rollout allows for continuous monitoring and adjustments based on real-time feedback.
Customer Base and Support System Integration
Integrating Lookout’s customer base and support systems into F-Secure’s infrastructure requires a multi-pronged strategy. This includes migrating customer data, consolidating support channels, and retraining support staff. A clear communication plan, outlining the timeline and benefits of the integration for customers, is crucial to minimize disruption and maintain customer loyalty. For example, F-Secure could leverage its existing customer relationship management (CRM) system to incorporate Lookout’s customer data, ensuring a unified view of each customer’s security profile.
The support teams of both companies will need comprehensive training on each other’s products and services to ensure consistent and effective support. A dedicated integration team, responsible for managing the migration process and addressing customer inquiries, will be essential to a smooth transition. This team should proactively communicate with customers throughout the process, providing regular updates and addressing any concerns.
Risk Mitigation Strategies
Several risks accompany the integration process. These include potential data breaches during migration, service disruptions, and customer dissatisfaction. Implementing robust security measures throughout the integration process, including thorough data validation and encryption, is paramount. A comprehensive disaster recovery plan, outlining procedures for handling unexpected events, is also crucial. Regular testing and monitoring of the integrated systems will help identify and address potential issues before they escalate.
Furthermore, establishing clear lines of communication between the integration teams and senior management will ensure that any challenges are addressed promptly and effectively. The success of the integration hinges on proactive risk management and a commitment to minimizing potential disruptions. For example, a pilot program involving a small subset of Lookout’s customer base can help identify and resolve potential issues before a full-scale rollout.
This staged approach reduces the overall risk and allows for continuous improvement throughout the integration process.
Long-Term Strategic Vision
The acquisition of Lookout by F-Secure marks a pivotal moment, creating a cybersecurity powerhouse uniquely positioned to dominate the evolving landscape of mobile and cloud security. This merger transcends a simple acquisition; it represents a strategic leap towards a future where comprehensive, proactive security solutions are seamlessly integrated into the fabric of modern digital life. The combined entity will leverage the strengths of both companies to establish an unparalleled market position and drive innovation for years to come.The acquisition directly contributes to F-Secure’s overall business objectives by expanding its product portfolio into the high-growth mobile security market, diversifying revenue streams, and enhancing its technological capabilities.
Lookout’s expertise in cloud security and mobile threat detection complements F-Secure’s existing strengths in endpoint protection and consumer security, creating a synergistic effect that strengthens the company’s overall value proposition. This strategic move positions F-Secure to capitalize on emerging trends and maintain a competitive edge in the rapidly changing cybersecurity industry.
Market Leadership and Innovation
Maintaining market leadership and driving innovation will be achieved through a multi-pronged strategy focusing on enhanced product development, strategic partnerships, and aggressive market penetration. The combined R&D teams will accelerate the development of innovative security solutions leveraging Lookout’s cloud-based threat intelligence and F-Secure’s expertise in endpoint security. This will result in a more comprehensive and proactive security offering, catering to the diverse needs of both consumer and enterprise clients.
Furthermore, strategic partnerships with leading technology providers will expand the reach and accessibility of the combined entity’s security solutions, increasing market penetration and brand visibility. For example, integrating F-Secure’s solutions with Lookout’s existing partnerships in the enterprise mobility management (EMM) space could unlock significant new market opportunities. A successful example of a similar synergistic merger is the combination of Salesforce and Slack, which integrated complementary products and expanded their market reach significantly.
The combined F-Secure and Lookout entity aims to replicate and surpass this success in the cybersecurity domain.
Last Point
The potential acquisition of Lookout by F-Secure represents a significant shift in the mobile security landscape. While challenges in integration and regulatory approval exist, the potential benefits – a more comprehensive security solution, enhanced market share, and increased innovation – are substantial. The success of this merger will hinge on the ability of F-Secure to effectively integrate Lookout’s technology and customer base while navigating the complexities of the competitive market and regulatory environment.
The coming months will be crucial in determining the ultimate impact of this ambitious undertaking.
Common Queries
What are the main concerns regarding the integration of F-Secure and Lookout’s technologies?
Integrating different security platforms, customer support systems, and potentially conflicting technologies could be complex and time-consuming. Data migration and ensuring seamless functionality for existing customers will be major challenges.
How might this acquisition impact pricing for consumers?
The impact on pricing is uncertain. The combined entity might offer bundled packages at competitive prices or consolidate offerings, potentially resulting in price changes for existing products.
What are the potential antitrust concerns?
Regulators might scrutinize the acquisition to ensure it doesn’t create a monopoly or significantly reduce competition in the mobile security market. The investigation could lead to conditions being imposed on the merger’s completion.


