Fake Antivirus Websites Now Delivering Malware
Fake antivirus websites now delivering malware are a growing threat. These cleverly disguised sites lure unsuspecting users into downloading malicious software, often under the guise of legitimate security protection. It’s a sneaky tactic, preying on our fear of viruses and our trust in established brands. But understanding the methods used and the types of malware deployed can help us stay safe online.
This post will dive deep into the world of these malicious sites, exploring their deceptive tactics, the malware they spread, and most importantly, how to protect yourself.
From sophisticated phishing emails to cleverly designed websites mimicking well-known antivirus brands, the attackers employ a range of techniques to trick users. We’ll examine these techniques, looking at how they exploit human psychology and leverage technical vulnerabilities. We’ll also explore the different types of malware delivered, their impact on your system, and the steps you can take to avoid becoming a victim.
Types of Malware Delivered

Fake antivirus websites are a common vector for delivering a range of malicious software, often disguised to appear legitimate. These deceptive sites trick users into downloading and installing harmful programs that can severely compromise their systems. Understanding the types of malware involved and their methods of infiltration is crucial for effective protection.
The consequences of interacting with these fraudulent sites can range from minor system slowdowns to complete data loss and financial theft. It’s vital to be vigilant and cautious when downloading any software, especially antivirus programs, from sources you don’t fully trust.
Malware Types and Their Impacts
The following table Artikels common malware types delivered through fake antivirus websites, detailing their functionalities and impact.
| Malware Type | Functionality | Impact | Example |
|---|---|---|---|
| Ransomware | Encrypts user files, demanding a ransom for decryption. | Data loss, financial loss, disruption of business operations. | CryptoLocker, WannaCry |
| Spyware | Secretly monitors user activity, collecting sensitive information like passwords, credit card details, and keystrokes. | Identity theft, financial fraud, privacy violation. | Gator, Zlob |
| Trojans | Disguised as legitimate software, granting attackers access to the system. They can perform various malicious actions depending on their design. | Data theft, system damage, installation of other malware. | Emotet, Trickbot |
| Adware | Displays unwanted advertisements, often intrusive and disruptive. Can also track user browsing habits. | Annoying pop-ups, slower system performance, privacy concerns. | Bundled with freeware or shareware. |
| Rootkits | Hides malicious processes and files from the operating system, making detection difficult. | Persistent infection, difficult removal, system instability. | Many rootkits are custom-built and not publicly named. |
Disguising Malware as Legitimate Antivirus Software
Sophisticated techniques are employed to make malware appear as genuine antivirus software. These techniques aim to deceive users into believing they are downloading a legitimate security product. Common methods include:
Mimicking legitimate software interfaces: Fake antivirus programs often copy the look and feel of well-known antivirus brands, using similar logos, icons, and program names. This visual similarity can fool unsuspecting users. They may even include fake scan results showing numerous “infections” that require immediate action.
Using convincing website designs: Fake antivirus websites often use professional-looking designs, complete with testimonials, security seals, and contact information, to create an illusion of legitimacy. These sites may even register legitimate-sounding domain names that are similar to well-known antivirus companies.
Exploiting social engineering: Attackers may use social engineering techniques to convince users to download and install the malware. This might involve using pop-up warnings that claim the user’s system is infected, or through phishing emails that appear to be from a legitimate antivirus company.
Techniques to Bypass Security Measures
Malicious actors utilize several advanced techniques to bypass security software and install malware on unsuspecting users’ systems. These include:
Exploiting software vulnerabilities: Attackers often exploit known vulnerabilities in operating systems or applications to install malware without the user’s knowledge or consent. These vulnerabilities are often patched by software vendors, highlighting the importance of keeping software up-to-date.
Using social engineering and deceptive tactics: As previously mentioned, social engineering techniques are employed to trick users into disabling security software or granting permissions to install malicious programs. This often involves creating a sense of urgency or fear to pressure users into making hasty decisions.
Employing obfuscation and polymorphism: Malware authors use obfuscation techniques to make the malware code difficult to analyze and detect by antivirus software. Polymorphic malware changes its code frequently, making it harder to identify and remove.
Leveraging legitimate software distribution channels: In some cases, malware is distributed through seemingly legitimate software distribution channels, such as app stores or software download websites. This is often done by compromising the legitimate channels or by disguising the malware as a harmless program.
Website Design and Deception Tactics
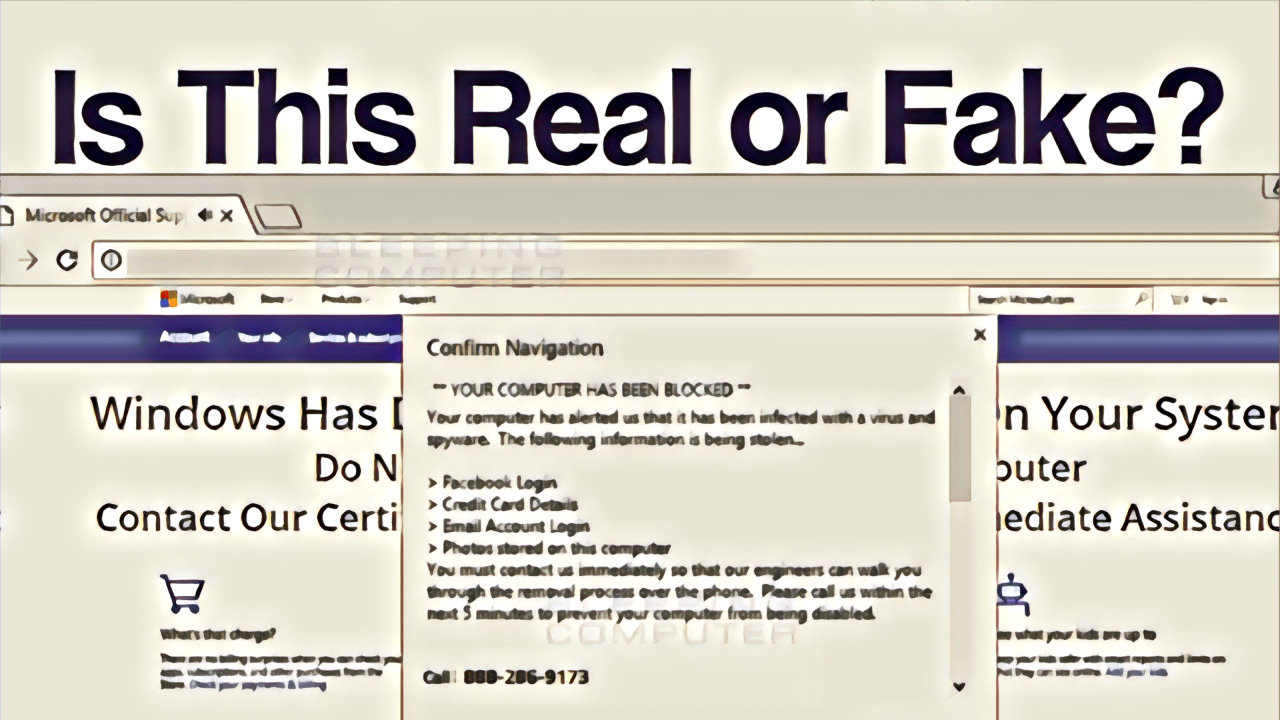
Fake antivirus websites employ sophisticated design elements and psychological manipulation to trick users into downloading malware. These sites often appear incredibly convincing, leveraging familiar design patterns and exploiting common anxieties surrounding computer security. Understanding these tactics is crucial to protecting yourself online.The deceptive nature of these websites stems from their ability to mimic legitimate antivirus software interfaces and leverage psychological pressure to prompt immediate action from unsuspecting users.
This creates a sense of urgency and fear, leading users to bypass their usual caution.
Design Elements Mimicking Legitimate Antivirus Software
Fake antivirus websites are meticulously crafted to appear authentic. They borrow heavily from the design language of established antivirus companies, creating a false sense of security. This deliberate imitation makes it difficult for the average user to distinguish between a legitimate and a fraudulent website.
- Use of Official Logos and Branding: These sites often incorporate near-perfect replicas of legitimate antivirus company logos, color schemes, and fonts. This visual similarity is a key element in their deception.
- Professional-Looking Interface: Fake websites frequently feature clean, well-organized layouts that resemble the user interfaces of genuine antivirus programs. They may even include realistic-looking scan results and system reports.
- Use of Technical Jargon: The sites employ technical terminology and complex-looking graphs to create an impression of authority and expertise, further reinforcing the illusion of legitimacy.
- Fake Security Certificates: Some fake websites may display fake security certificates or trust seals to build confidence and reassure users that the site is safe.
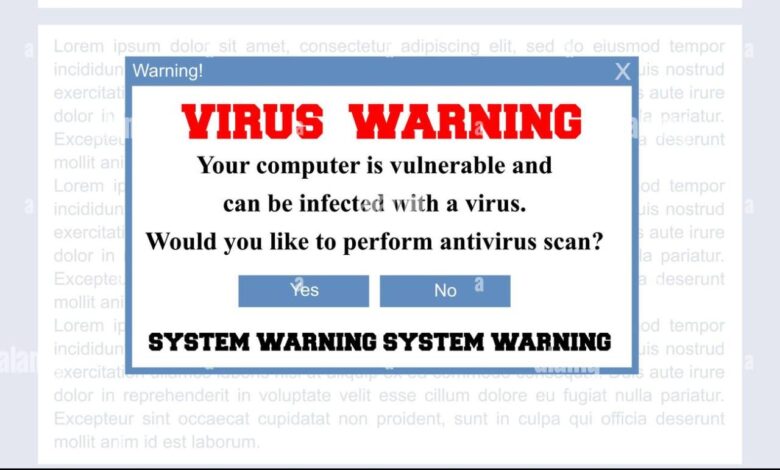
- Realistic Error Messages: Many fake antivirus sites present fake system errors or warnings, designed to scare users into believing their computer is infected and needs immediate attention.
Psychological Manipulation Techniques
Beyond visual mimicry, these websites use psychological manipulation to pressure users into downloading and installing malware. The goal is to create a sense of urgency and fear, overriding rational decision-making.
- Fear-mongering: Fake antivirus sites often display alarming messages, exaggerating the severity of supposed infections and implying significant data loss or system damage if action isn’t taken immediately.
- Sense of Urgency: Countdown timers or flashing warnings are frequently used to create a sense of urgency, pushing users to act quickly without thinking critically.
- Limited-Time Offers: Fake antivirus sites often offer “limited-time discounts” or “special promotions” to incentivize immediate downloads, exploiting the fear of missing out.
- Social Proof: Some sites might include fake testimonials or reviews to create a false sense of credibility and encourage downloads.
- Authority and Expertise: The use of technical jargon and official-looking designs aims to establish a sense of authority, convincing users that the website is trustworthy and the software is necessary.
Mimicking Reputable Antivirus Companies
The most effective fake antivirus websites cleverly mimic the appearance of established antivirus brands. This deception is highly effective because users are already familiar with the genuine brands and trust their reputation. The imitation is often so convincing that even tech-savvy individuals can be fooled. For example, a fake website might use a slightly altered version of a well-known company’s logo, or employ a similar color scheme and font, creating a strong visual resemblance.
The overall design, layout, and even the wording used in error messages or warnings are designed to subtly replicate the genuine product, creating a seamless imitation. This sophisticated approach increases the chances of users falling victim to the scam.
Distribution Methods and Targeting
Fake antivirus websites rely on a multi-pronged approach to reach their victims, employing various distribution methods and targeting specific demographics known to be more vulnerable to their deceptive tactics. Understanding these methods is crucial to protecting yourself and others from these malicious schemes.The spread of these fraudulent websites hinges on exploiting vulnerabilities in human behavior and leveraging readily available online platforms.
This isn’t about sophisticated hacking; it’s about cleverly manipulating users into clicking malicious links.
Malvertising and Compromised Websites
Malvertising, the insertion of malicious advertisements on legitimate websites, is a significant vector for distributing fake antivirus links. These ads often mimic legitimate software advertisements, promising performance boosts or security enhancements. A single click can redirect the user to a convincing fake antivirus site. Furthermore, hackers frequently compromise legitimate websites, injecting malicious code that redirects visitors to their fake antivirus landing pages.
This is particularly effective as users trust the seemingly legitimate source. Imagine clicking a seemingly harmless ad on a news site, only to be redirected to a site warning you of a critical virus infection.
Phishing Emails, Fake antivirus websites now delivering malware
Phishing emails remain a highly effective method of distributing malicious links. These emails often appear to be from legitimate organizations, such as banks or software companies, warning recipients of a supposed security threat. The email may include a link to a fake antivirus website, urging the user to download the “solution” to fix the fabricated problem. The urgency and apparent legitimacy of the email often pressure recipients into clicking the link without proper verification.
A common tactic is to use subject lines like “Urgent Security Alert” or “Virus Detected on Your Account.”
Social Engineering Tactics
Attackers skillfully employ social engineering techniques to manipulate users into visiting their malicious websites. These techniques exploit human psychology and trust. For example, they might create fake tech support websites or social media profiles posing as reputable companies. They might create fake posts or comments on forums and social media platforms, warning of a new virus and providing a link to a “solution.” These posts often contain alarming information and encourage immediate action, further pressuring users to click.
Seriously, those fake antivirus websites are a menace; they’re popping up everywhere, silently installing malware. It makes you appreciate the secure development practices discussed in this article on domino app dev the low code and pro code future , where building robust, safe applications is key. The contrast is stark – one creates malicious code, the other focuses on building secure software.
It’s a reminder that secure coding is crucial in combating these kinds of online threats.
Target Demographics
Understanding who is most susceptible to these attacks is key to effective prevention. While anyone can be a victim, certain demographics are particularly vulnerable:
- Older Adults: Often less tech-savvy and more trusting of authority figures, they are more likely to fall for phishing scams and deceptive advertising.
- Individuals with Limited Technical Knowledge: Those unfamiliar with computer security concepts may struggle to identify malicious websites and are more likely to believe claims of critical infections.
- Users in Developing Countries: Lack of awareness about online security threats, combined with less robust cybersecurity infrastructure, makes them a prime target.
- Individuals with Low Digital Literacy: This encompasses a range of skills, from recognizing phishing emails to understanding the importance of software updates. Those with lower digital literacy are often more vulnerable.
Leveraging Social Engineering Principles
Attackers exploit several social engineering principles to trick users:* Urgency and Scarcity: Creating a sense of immediate danger or limited-time offers pressures users to act without thinking. Messages like “Your computer is infected! Act now!” are designed to bypass critical thinking.
Authority and Trust
Fake websites often mimic the look and feel of legitimate security software or organizations to build trust. They may use logos, official-looking language, and even fake testimonials.
Fear, Uncertainty, and Doubt (FUD)
These tactics create anxiety and panic, leading users to make rash decisions without careful consideration. The message is designed to make the user feel vulnerable and in need of an immediate solution.
Reciprocity
Some scams might offer a seemingly helpful service or free scan before attempting to install malware. This creates a sense of obligation, making users more likely to trust the subsequent requests.
Technical Analysis of Malware Delivery
Fake antivirus websites employ a range of sophisticated techniques to deliver malware to unsuspecting users. Understanding the technical steps involved is crucial for both prevention and remediation. The process typically involves exploiting vulnerabilities in the victim’s system or tricking them into executing malicious code.The delivery of malware from a fake antivirus website often begins with a deceptive user interface mimicking legitimate antivirus software.
This interface prompts the user to download and install a seemingly necessary update or security scan. However, this “update” or “scan” is actually a cleverly disguised malware installer. The specific methods used can vary, but they generally follow a predictable pattern of exploitation, installation, and persistence.
Exploit and Vulnerability Utilization
The success of malware delivery hinges on exploiting vulnerabilities in the victim’s system or web browser. Common vulnerabilities include outdated software, unpatched operating systems, and flaws in browser plugins or extensions. Attackers often leverage known vulnerabilities to gain initial access. For instance, an older version of Adobe Flash Player might contain an exploit that allows the malicious code to run directly from the website without user interaction beyond visiting the site.
Another example is the use of zero-day exploits, which target vulnerabilities that are unknown to software vendors. These are particularly dangerous as there are no readily available patches. Once a vulnerability is exploited, the attacker gains a foothold on the system, enabling further malicious actions.
Code Execution Process
Once a vulnerability is exploited, the malware typically begins its execution. This often involves downloading additional components from a remote server, potentially bypassing security measures like sandboxing or antivirus software. The downloaded components might include the main malware payload and additional modules for persistence, data exfiltration, or other malicious activities. The execution process may involve techniques such as process injection, where the malicious code is injected into a legitimate running process to avoid detection, or the creation of a new process entirely.
For example, the malware might inject itself into explorer.exe, a core Windows process, making it harder to detect and remove.
Malware Persistence Mechanisms
To ensure continued operation and access to the compromised system, malware often employs persistence mechanisms. This ensures that the malware automatically restarts even after a reboot. Common techniques include adding registry entries to automatically start the malware on system boot, creating scheduled tasks, or modifying system files to include the malware’s code. For instance, the malware could create a registry key under `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run`, which automatically executes the malware every time the user logs in.
Another technique is to modify the boot sector, ensuring that the malware loads before the operating system even starts. The complexity and sophistication of these persistence mechanisms vary depending on the malware’s capabilities and the attacker’s goals.
Prevention and Mitigation Strategies
Protecting yourself from fake antivirus websites requires a multi-layered approach encompassing proactive measures and knowing how to react to suspicious encounters. Ignoring security best practices leaves your system vulnerable to malware, potentially leading to data loss, financial theft, and identity compromise. This section details practical steps to minimize your risk.
Preventative Measures Against Fake Antivirus Websites
Taking proactive steps is crucial in avoiding these malicious websites. Regularly updating your software, being cautious about website legitimacy, and practicing safe browsing habits are key components of a robust security strategy. The following table summarizes essential preventative actions.
| Action | Description | Benefit | Example |
|---|---|---|---|
| Keep Software Updated | Regularly update your operating system, antivirus software, and web browser. | Patches security vulnerabilities that malicious actors could exploit. | Enable automatic updates for Windows, macOS, and your antivirus program. Regularly check for browser updates. |
| Verify Website Legitimacy | Check the website’s URL for suspicious elements (misspellings, unusual characters), look for a valid SSL certificate (https), and research the company’s reputation. | Reduces the likelihood of visiting a fraudulent website. | Before downloading software, verify the company’s website through independent searches. Look for a padlock icon in the URL bar indicating an SSL certificate. |
| Practice Safe Browsing Habits | Avoid clicking on suspicious links in emails or on untrusted websites. Be wary of pop-up ads claiming antivirus issues. | Minimizes exposure to phishing attempts and malicious downloads. | Hover your mouse over links to see the actual URL before clicking. Ignore pop-ups that aggressively push antivirus scans. |
| Use a Reputable Antivirus Program | Install and maintain a reputable antivirus program from a trusted vendor. | Provides real-time protection against malware and other threats. | Consider using well-known antivirus software such as Norton, McAfee, or Bitdefender. |
| Enable Firewall Protection | Ensure your firewall is enabled to block unauthorized network access. | Prevents malicious software from connecting to external servers. | Check your operating system’s settings to verify that the firewall is active and configured correctly. |
Identifying and Reporting Suspicious Websites
Encountering a potentially malicious website requires immediate action. Careful observation and prompt reporting are essential in protecting yourself and others from similar threats.Identifying a suspicious website involves examining several key aspects. Look for poor grammar and spelling on the site, a lack of contact information, unusual or overly aggressive warnings about virus infections, and requests for personal information, such as credit card details or login credentials.
If you suspect a website is fraudulent, avoid interacting with it further. Report the site to the appropriate authorities, including the website hosting provider and relevant anti-phishing organizations. Many web browsers have built-in reporting mechanisms.
Securing Computer Systems Against Malware Infections
A layered security approach is essential to protect your computer from malware. This includes using a robust antivirus solution, regularly updating your software, employing strong passwords, and practicing safe browsing habits. Additionally, creating regular backups of your important data is crucial for data recovery in the event of an infection. Consider enabling two-factor authentication where available to add an extra layer of security to your online accounts.
Regularly scanning your system for malware using your antivirus software is another effective preventive measure. Educating yourself about the latest online threats and security best practices will enhance your ability to identify and avoid potential risks.
Case Studies of Notable Attacks
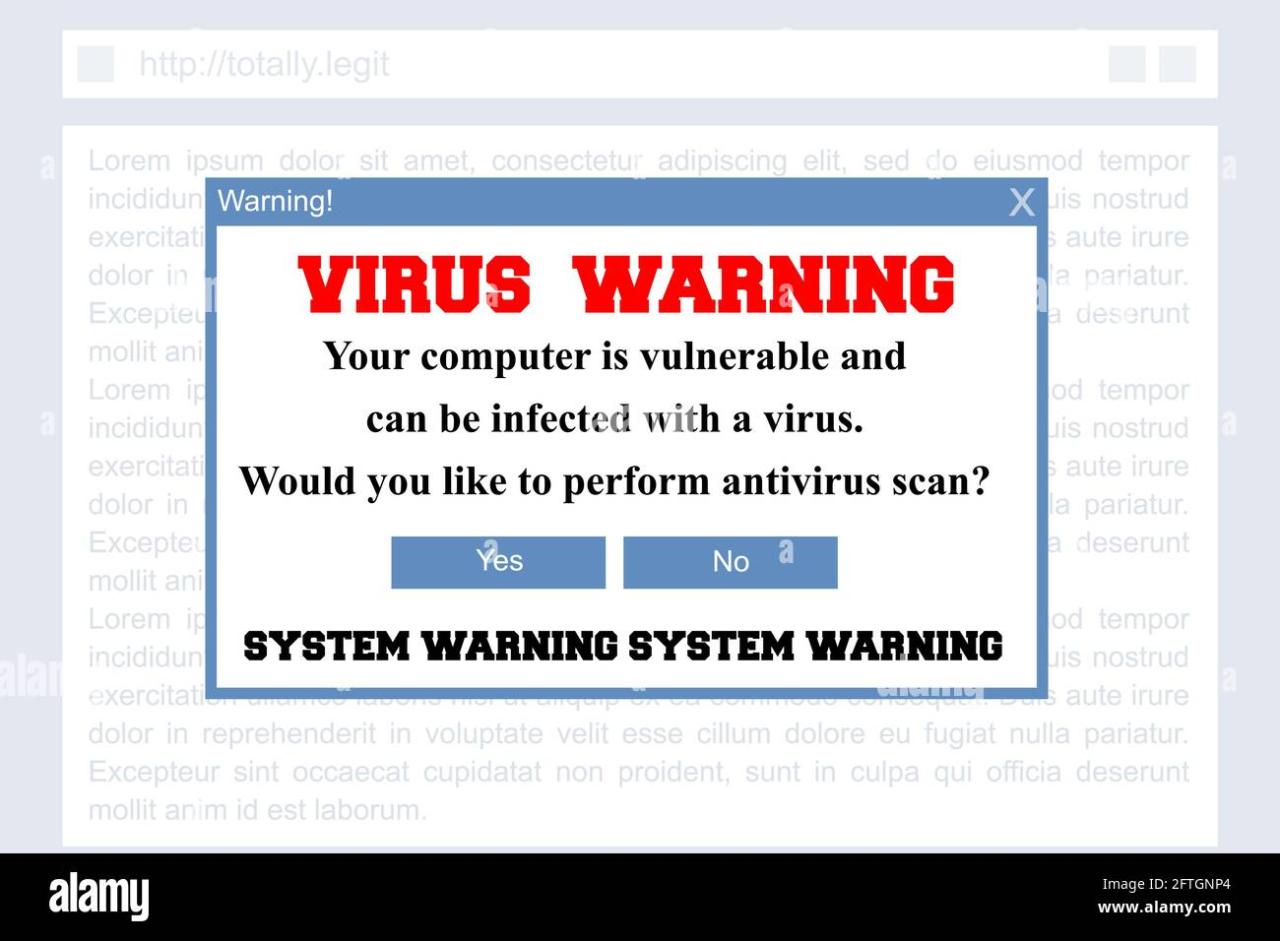
Fake antivirus websites, masquerading as legitimate security solutions, have been a persistent threat for years, resulting in significant financial and data losses for countless individuals and organizations. These attacks leverage sophisticated social engineering and technical subterfuge to trick users into installing malware, often with devastating consequences. Examining specific instances helps illustrate the evolving tactics and the scale of the problem.
Analyzing several high-profile attacks reveals common threads, such as the exploitation of fear and urgency, the use of deceptive website designs mimicking reputable antivirus brands, and the deployment of diverse malware payloads ranging from ransomware to information stealers. While the specific malware and delivery methods may differ, the core principle remains consistent: exploiting user trust to gain unauthorized access and control.
The “Security Tool” Campaign
This campaign, active from 2018-2020, employed a network of websites mimicking popular antivirus software. Users, often lured through search engine results or malicious advertisements, were presented with fake scan results highlighting fictitious threats. The “solution” offered was the download of a rogue antivirus program, which in reality installed a potent information stealer, capturing banking credentials, personal data, and other sensitive information.
The malware used advanced techniques to evade detection, including process injection and encryption. The impact on victims included identity theft, financial losses, and significant emotional distress. The scale of the attack involved thousands of infected systems across multiple countries.
The “Fake Antivirus” Ransomware Attack
In this instance, the fake antivirus website displayed a warning message claiming the user’s system was infected with multiple viruses. The “removal” tool downloaded was actually ransomware that encrypted the user’s files, demanding a ransom payment for decryption. The ransomware was particularly insidious due to its use of strong encryption and its ability to spread through network shares, impacting multiple computers within an organization.
This attack targeted small and medium-sized businesses, causing significant disruption to operations and substantial financial losses due to downtime, data recovery costs, and ransom payments. The attack’s scale was limited, yet its impact on the affected organizations was severe.
Comparison of Attacks
Both the “Security Tool” campaign and the “Fake Antivirus” ransomware attack share similarities in their use of deceptive websites and social engineering to trick users. However, they differ significantly in their ultimate goals. The “Security Tool” campaign aimed to steal data, while the “Fake Antivirus” attack focused on extortion through ransomware. This highlights the diverse motivations behind fake antivirus attacks and the versatility of the techniques employed.
Both campaigns, however, demonstrate the effectiveness of exploiting user fear and lack of security awareness.
Impact on Users and Organizations
The cumulative impact of fake antivirus attacks is substantial. For individual users, the consequences can include financial losses, identity theft, data breaches, and significant emotional distress. Organizations face disruptions to operations, data loss, legal liabilities, and reputational damage. The costs associated with recovery, including remediation, data restoration, and legal fees, can be considerable. The scale of these attacks, while difficult to quantify precisely due to underreporting, is significant, affecting millions of users worldwide each year.
The financial losses caused by these attacks are estimated to be in the hundreds of millions of dollars annually.
Final Summary
In the ever-evolving landscape of online threats, fake antivirus websites represent a significant danger. Their deceptive nature and the potential for serious damage underscore the need for vigilance and proactive security measures. By understanding the tactics employed by these malicious actors and implementing the preventative measures Artikeld above, we can significantly reduce our risk of infection. Remember, a little caution and knowledge can go a long way in keeping your digital life safe and secure.
Stay informed, stay vigilant, and stay safe!
FAQ Guide: Fake Antivirus Websites Now Delivering Malware
What are the common signs of a fake antivirus website?
Look for poor grammar, suspicious URLs, aggressive pop-ups demanding immediate action, and requests for personal information.
Can my antivirus software protect me from fake antivirus websites?
A reputable antivirus program can help, but it’s not foolproof. Be cautious and don’t blindly click links or download software from unknown sources.
What should I do if I think I’ve visited a fake antivirus website?
Immediately run a full system scan with your antivirus software. Change your passwords, and consider contacting a cybersecurity professional for further assistance.
How can I report a fake antivirus website?
Report it to the website hosting provider and to relevant authorities like the Internet Crime Complaint Center (IC3).