FBI Puts Whole of Us on a Cyber Security Alert
FBI Puts Whole of Us on a Cyber Security Alert – Whoa, that’s a headline that grabs you, right? It feels like something out of a movie, but this is real life. The FBI’s recent cybersecurity alert isn’t just another warning; it’s a wake-up call highlighting a serious and widespread threat impacting individuals and businesses alike. We’re talking about vulnerabilities that could expose sensitive data, disrupt essential services, and even compromise national security.
This post dives deep into what the alert means for you and what steps you can take to protect yourself.
The alert details a sophisticated and evolving threat landscape, targeting critical infrastructure and various sectors. From the specifics of the vulnerabilities to the recommended mitigation strategies, we’ll break down everything you need to know to stay safe in this increasingly digital world. We’ll explore the roles of government and the private sector in collaboration, examining the potential long-term impacts and what changes we might see in the future.
The FBI Alert

The recent FBI cybersecurity alert, while not publicly detailing specific vulnerabilities exploited or named actors involved, underscores a significant and evolving threat landscape. This alert highlights the urgent need for heightened cybersecurity vigilance across all sectors, emphasizing the potential for widespread and devastating consequences from successful cyberattacks. The lack of specific details in the public announcement reflects the sensitive nature of ongoing investigations and the need to avoid providing potential adversaries with actionable intelligence.The alert serves as a general warning, urging individuals and organizations to review and strengthen their cybersecurity postures.
The threats encompassed within the alert are multifaceted, ranging from ransomware attacks targeting critical infrastructure to sophisticated phishing campaigns aimed at stealing sensitive data. The FBI’s action reflects a growing concern about the frequency and sophistication of cyberattacks, and the potential for cascading failures across interconnected systems.
The Circumstances Surrounding the FBI’s Cybersecurity Alert
The alert followed a period of heightened cyber activity, including several high-profile ransomware attacks against critical infrastructure sectors. While the FBI didn’t directly link the alert to a single specific event, the timing suggests a concern about the escalating frequency and severity of these attacks, and the potential for coordinated or interconnected campaigns. The alert’s broad scope indicates a proactive approach to mitigate potential damage before further incidents occur.
This proactive approach contrasts with previous instances where alerts followed significant compromises.
Specific Threats Mentioned in the Alert
Although the FBI’s public statement was intentionally vague, the alert implicitly referenced a range of common cyber threats. These threats include, but are not limited to, ransomware attacks, phishing and spear-phishing campaigns, exploitation of known vulnerabilities in software and hardware, and the use of malicious code to gain unauthorized access to systems. The alert emphasized the importance of robust multi-factor authentication, regular software updates, and employee security awareness training as key preventative measures.
The implicit nature of the threat description highlights the diverse and evolving nature of modern cyberattacks.
Timeline of Events Leading Up to the Alert
Pinpointing a precise timeline for events leading up to the alert is difficult due to the classified nature of intelligence gathering. However, the preceding months witnessed a noticeable increase in publicized ransomware attacks and data breaches. Reports of successful attacks against various sectors – including healthcare, energy, and finance – likely contributed to the FBI’s decision to issue a broad-based alert.
This suggests that the alert wasn’t triggered by a single incident, but rather a cumulative assessment of the threat landscape. The lack of specific details reinforces the ongoing nature of investigations.
Examples of Previous Similar Alerts and Their Impact
The FBI regularly issues cybersecurity alerts, often in response to specific threats or vulnerabilities. Previous alerts, while varying in scope and detail, have generally resulted in increased awareness among organizations and individuals. For example, alerts related to specific ransomware strains like WannaCry and NotPetya led to improved patching practices and security protocols. The impact of these alerts is often difficult to quantify directly, but they undoubtedly contribute to a more informed and prepared cybersecurity landscape.
The long-term impact is seen in the evolving security practices of many organizations.
Targeted Sectors and Vulnerabilities: Fbi Puts Whole Of Us On A Cyber Security Alert
The recent FBI cybersecurity alert highlights a concerning trend: sophisticated cyberattacks targeting specific sectors with devastating potential. Understanding which sectors are most vulnerable and the precise vulnerabilities exploited is crucial for effective mitigation strategies. This analysis will examine several key sectors and their unique vulnerabilities, emphasizing the potential consequences of successful breaches.The current threat landscape shows a clear pattern of targeting sectors with valuable data and interconnected systems.
Critical infrastructure, healthcare, and finance are consistently identified as high-risk targets, but the vulnerabilities exploited vary depending on the sector’s technological landscape and security posture.
Critical Infrastructure Vulnerabilities
The critical infrastructure sector, encompassing energy grids, water treatment facilities, and transportation networks, faces significant threats. Attackers often exploit vulnerabilities in Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems, which are often outdated and lack robust security measures. A successful attack could lead to widespread power outages, disruptions to water supply, or even damage to physical infrastructure, resulting in significant economic losses and potential loss of life.
For example, a hypothetical attack targeting a power grid’s control system could cause a cascading failure affecting millions. The vulnerabilities stem from a lack of patching, inadequate access controls, and insufficient monitoring of system activity. The consequences are severe, impacting essential services and public safety.
The FBI’s cybersecurity alert has everyone on edge, and rightfully so! We need robust, secure systems now more than ever, which is why I’ve been diving into the world of app development, specifically exploring the possibilities outlined in this great article on domino app dev, the low-code and pro-code future. Learning about efficient development methods feels crucial in this climate, as building secure applications is paramount in the face of increasing cyber threats.
It’s clear we all need to be more proactive about cybersecurity.
Healthcare Sector Vulnerabilities
The healthcare sector is particularly vulnerable due to the sensitive nature of patient data (protected by HIPAA) and the reliance on interconnected medical devices and electronic health records (EHRs). Attackers often exploit vulnerabilities in EHR systems, aiming to steal patient data for financial gain or to disrupt healthcare operations through ransomware attacks. A successful ransomware attack could cripple a hospital’s ability to provide care, potentially leading to patient harm or death.
The vulnerabilities include weak passwords, unpatched software, and insufficient employee training on cybersecurity best practices. The consequences extend beyond financial losses to include reputational damage and legal liabilities. The comparison with other sectors reveals a greater reliance on legacy systems and a higher risk of human error in the healthcare sector.
Financial Sector Vulnerabilities
The financial sector, with its vast stores of financial data and online transaction systems, is a prime target for cybercriminals. Attackers exploit vulnerabilities in online banking systems, payment processors, and internal networks to steal money or sensitive financial information. Phishing scams, malware infections, and SQL injection attacks are commonly used techniques. A successful attack could result in significant financial losses for both institutions and individuals, as well as reputational damage and loss of customer trust.
The vulnerabilities are similar to those in other sectors, such as weak passwords and outdated software, but the potential consequences are amplified by the high value of the targeted assets. Unlike critical infrastructure, the financial sector has generally invested more heavily in cybersecurity, but the sophistication of attacks continues to evolve.
Recommended Mitigation Strategies
The FBI’s cybersecurity alert underscores the urgent need for proactive measures to protect individuals and businesses from potential cyber threats. Implementing robust security practices is no longer optional; it’s a necessity. The following strategies offer a layered approach to mitigating risks and enhancing overall security posture.
Taking personal responsibility for online security is crucial. Even small steps can significantly reduce your vulnerability. The following list provides actionable steps you can take to improve your personal cyber hygiene.
Personal Security Measures
- Strong Passwords: Use unique, complex passwords for each online account. Consider using a password manager to generate and securely store these passwords.
- Multi-Factor Authentication (MFA): Enable MFA wherever possible. This adds an extra layer of security, requiring more than just a password to access your accounts.
- Software Updates: Regularly update your operating system, applications, and antivirus software. These updates often include critical security patches.
- Phishing Awareness: Be wary of suspicious emails, links, and attachments. Never click on links or open attachments from unknown senders.
- Secure Wi-Fi: Use strong passwords for your home Wi-Fi network and avoid using public Wi-Fi for sensitive transactions.
- Regular Backups: Regularly back up your important data to an external hard drive or cloud storage service. This protects you from data loss in case of a cyberattack or hardware failure.
- Use Caution with Social Media: Be mindful of the information you share on social media, as it can be used to target you in phishing attacks.
For businesses, a more comprehensive approach is required, encompassing both software and security practices. The following table Artikels recommended tools and strategies.
The FBI’s cybersecurity alert is a serious wake-up call; we’re all vulnerable. This heightened risk is highlighted by recent reports of facebook asking bank account info and card transactions of users , a blatant example of the kind of phishing scams the FBI is warning us about. Stay vigilant and protect your data; it’s more important than ever.
Business Security Measures
| Software/Practice | Description | Benefits | Cost/Effort |
|---|---|---|---|
| Firewall | A network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. | Prevents unauthorized access to internal networks and systems. | Moderate (initial purchase and ongoing maintenance) |
| Intrusion Detection/Prevention System (IDS/IPS) | Monitors network traffic for malicious activity and either alerts administrators (IDS) or automatically blocks threats (IPS). | Detects and prevents network intrusions and attacks. | High (purchase, installation, and ongoing management) |
| Endpoint Detection and Response (EDR) | Provides real-time monitoring and threat detection on individual devices (computers, servers, etc.). | Identifies and responds to malware and other threats on endpoints. | High (software licensing and management) |
| Security Information and Event Management (SIEM) | Collects and analyzes security logs from various sources to identify and respond to security incidents. | Provides comprehensive security monitoring and incident response capabilities. | High (software licensing, hardware requirements, and expertise) |
| Regular Security Audits | Periodic assessments of security vulnerabilities and controls. | Identifies weaknesses and helps prioritize remediation efforts. | Moderate (cost of audit services) |
| Employee Security Training | Educates employees about cybersecurity threats and best practices. | Reduces the risk of human error in security incidents. | Low to Moderate (training materials and time commitment) |
Securing critical infrastructure requires a multi-layered approach focused on resilience and redundancy. The following best practices should be implemented.
Critical Infrastructure Security
- Redundancy and Failover Systems: Implement redundant systems and failover mechanisms to ensure continuous operation in case of a failure or attack.
- Physical Security: Implement robust physical security measures to protect critical infrastructure from unauthorized access and damage.
- Network Segmentation: Segment networks to limit the impact of a breach. This prevents attackers from easily moving laterally across the network.
- Access Control: Implement strong access control measures, including strict authentication and authorization policies.
- Regular Vulnerability Assessments: Conduct regular vulnerability assessments and penetration testing to identify and address security weaknesses.
- Incident Response Plan: Develop and regularly test an incident response plan to ensure a swift and effective response to security incidents.
- Supply Chain Security: Secure the supply chain by carefully vetting vendors and partners and ensuring that all software and hardware used are secure.
Multi-factor authentication (MFA) significantly enhances security by adding an extra layer of verification beyond a simple password. Here’s a step-by-step guide.
Multi-Factor Authentication Implementation
- Enable MFA on your account: Navigate to your account settings and locate the MFA settings. Most services provide clear instructions on how to enable it.
- Choose your MFA method: Common methods include authenticator apps (like Google Authenticator or Authy), security keys, or SMS codes. Choose the method that best suits your needs and security preferences.
- Set up your chosen method: Follow the instructions provided by your service provider to set up your chosen MFA method. This typically involves scanning a QR code with an authenticator app or registering a security key.
- Test your MFA setup: After setting up MFA, test it by attempting to log in. You should be prompted for your password and the additional verification code from your chosen MFA method.
- Keep your MFA method secure: Protect your authenticator app, security key, or phone number used for SMS codes. If you lose access to your MFA method, you may need to contact your service provider to regain access to your account.
The Role of Government and Private Sector Collaboration
The escalating complexity and frequency of cyberattacks necessitate a robust collaborative approach between government agencies and the private sector. Neither entity can effectively combat this threat alone; a unified front is crucial for bolstering national cybersecurity resilience and protecting critical infrastructure. This requires a clear understanding of each party’s responsibilities and a commitment to seamless information sharing.Government Responsibilities in Addressing Cyber Threats encompass establishing and enforcing cybersecurity standards, providing resources and funding for research and development in cybersecurity technologies, and fostering a culture of cybersecurity awareness among citizens and businesses.
The FBI’s cybersecurity alert is a stark reminder of how vulnerable we all are. This highlights the critical need for robust security measures, especially with the increasing reliance on cloud services. Learning more about solutions like bitglass and the rise of cloud security posture management is crucial in this climate. Ultimately, proactive security, not just reactive responses, is what will protect us from the ever-evolving cyber threats highlighted by the FBI warning.
Furthermore, governments play a vital role in coordinating national responses to major cyber incidents, leveraging their intelligence capabilities to identify and neutralize threats. This includes proactive measures like vulnerability disclosure programs and reactive measures such as incident response teams and legal frameworks for prosecuting cybercriminals. A strong regulatory environment, coupled with effective enforcement, is essential to deter malicious actors and incentivize proactive cybersecurity practices across all sectors.
Effective Public-Private Partnerships in Cybersecurity
Successful collaborations often involve joint cybersecurity exercises, where government agencies and private companies simulate real-world attacks to test their preparedness and response capabilities. For example, the U.S. Department of Homeland Security’s National Cybersecurity and Communications Integration Center (NCCIC) regularly partners with private sector organizations to conduct these exercises, sharing threat intelligence and best practices. Another effective model involves the establishment of Information Sharing and Analysis Centers (ISACs), which are industry-specific groups that facilitate the secure exchange of threat information between member organizations and government agencies.
These ISACs, such as the Financial Services ISAC (FS-ISAC), provide a crucial platform for early warning systems and coordinated responses to emerging threats. Finally, government grants and incentives can encourage private sector investment in cybersecurity research and development, leading to innovative solutions and improved defenses against sophisticated attacks.
The Importance of Information Sharing
Timely and accurate information sharing is paramount in mitigating cyber threats. The government possesses unique intelligence capabilities and access to threat data that the private sector often lacks. Conversely, private sector organizations often have firsthand experience with specific attacks and vulnerabilities, which they can share to help inform government strategies and improve national cybersecurity defenses. This two-way street of information exchange is crucial for developing effective countermeasures and preventing future attacks.
The establishment of secure channels for information sharing, coupled with clear protocols for data handling and privacy protection, is crucial to building trust and fostering collaboration. Delayed or incomplete information sharing can significantly hamper response efforts, allowing attackers to exploit vulnerabilities for longer periods and cause greater damage.
Potential Areas for Improvement in Collaboration Efforts, Fbi puts whole of us on a cyber security alert
While significant progress has been made, there remain areas for improvement in government-private sector collaboration. One key challenge is overcoming the reluctance of some private sector organizations to share sensitive information due to concerns about competitive disadvantage or legal liability. Addressing these concerns through clear legal frameworks, incentives for information sharing, and robust data protection mechanisms is crucial.
Another area for improvement is the need for more standardized cybersecurity frameworks and protocols to facilitate seamless information exchange across different sectors and organizations. A lack of standardization can hinder interoperability and make it difficult to share threat intelligence effectively. Finally, enhanced training and education programs are needed to equip both government and private sector personnel with the necessary skills and knowledge to effectively collaborate and respond to cyber threats.
A skilled workforce is essential to maximizing the benefits of these collaborative efforts.
Potential Long-Term Impacts

The recent FBI cybersecurity alert underscores a critical reality: the escalating frequency and sophistication of cyberattacks pose significant long-term risks, extending far beyond immediate financial losses and operational disruptions. Understanding these potential long-term impacts is crucial for developing effective mitigation strategies and fostering resilience across all sectors. The consequences ripple across economic stability, national security, public trust, and societal structures.The interconnected nature of our digital world means that even seemingly isolated incidents can have cascading effects, leading to widespread instability.
This section will delve into the potential long-term economic, security, and societal ramifications of persistent and evolving cyber threats.
Long-Term Economic Consequences
The economic impact of significant cyberattacks can be devastating and long-lasting. Consider the NotPetya ransomware attack in 2017, which caused billions of dollars in damages globally, impacting businesses ranging from multinational corporations to small enterprises. Beyond direct financial losses from data breaches, ransomware payments, and business interruption, there are significant indirect costs. These include: diminished investor confidence, increased insurance premiums, the expense of enhanced cybersecurity measures, and the potential loss of competitive advantage.
Furthermore, prolonged recovery periods can stifle economic growth and hinder innovation. A prolonged period of heightened cyber threat could lead to a chilling effect on investment in digital technologies and infrastructure, potentially slowing overall economic advancement. The costs associated with rebuilding trust and reputation following a major cyber incident can also be substantial.
Impact on National Security and Public Trust
Cyberattacks targeting critical infrastructure (power grids, water systems, transportation networks) can have severe consequences for national security, potentially leading to widespread disruption and even loss of life. Furthermore, successful attacks against government agencies or sensitive data repositories can undermine public trust in institutions and erode confidence in the ability of authorities to protect citizens. This erosion of trust can have far-reaching political and social ramifications, potentially leading to instability and societal fragmentation.
The theft of sensitive national security information can compromise strategic advantages and provide adversaries with valuable intelligence, significantly impacting national defense capabilities. The psychological impact of a widespread and successful cyberattack, creating a sense of vulnerability and fear, should also be considered a serious aspect of national security.
Changes in Cybersecurity Legislation and Policy
The ongoing threat of cyberattacks is likely to drive significant changes in cybersecurity legislation and policy at both national and international levels. We can anticipate stricter data protection regulations, increased penalties for cybersecurity negligence, and potentially greater government oversight of critical infrastructure. There will likely be a stronger emphasis on proactive cybersecurity measures, including mandatory cybersecurity standards for various industries and improved information sharing between the public and private sectors.
International cooperation will also become increasingly important in addressing transnational cybercrime and developing common standards and frameworks for cybersecurity. Examples of this trend already include the GDPR (General Data Protection Regulation) in Europe and the increasing focus on critical infrastructure protection in many countries.
Societal Changes in Response to Increased Cyber Threats
The escalating threat landscape is prompting several key societal adaptations:
- Increased cybersecurity awareness and education: Individuals and organizations are becoming more aware of cyber threats and are investing more in training and education to improve their cybersecurity posture.
- Greater reliance on cybersecurity technologies: There is a growing demand for advanced cybersecurity solutions, including intrusion detection systems, endpoint protection, and threat intelligence platforms.
- Shifting attitudes towards data privacy and security: Individuals are becoming more cautious about sharing personal information online and are demanding greater transparency and accountability from organizations regarding data protection.
- Development of new cybersecurity professions and skills: The demand for cybersecurity professionals is growing rapidly, leading to the development of new educational programs and training initiatives.
- Increased collaboration between public and private sectors: There is a growing recognition of the need for greater collaboration between government agencies and private sector organizations to address cyber threats effectively.
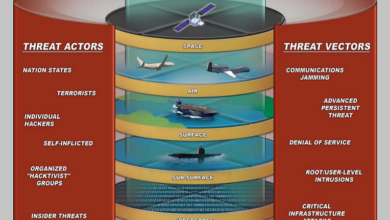
Visual Representation of Threat Landscape
Understanding the cyber threat landscape requires visualizing its complexity. A static image can’t fully capture the dynamic nature of cyberattacks, but a well-designed illustration can help clarify the various attack vectors, targets, and their interconnectedness. We’ll explore two visual representations to better grasp this intricate web of threats.The first illustration depicts the threat landscape as a dark, stormy ocean.
The ocean itself represents the vast digital space, its turbulent waves symbolizing the constant flow of cyberattacks. Different shades of grey and dark blue represent varying levels of threat severity, with deeper, darker hues indicating more dangerous attacks. Sharp, jagged rocks protruding from the ocean floor symbolize critical infrastructure points like power grids, financial institutions, and government systems – these are the primary targets.
Ships, representing various organizations and individuals, navigate this treacherous sea. Some ships are well-armored and equipped with advanced cybersecurity measures (represented by brighter, more vibrant colors), while others are more vulnerable (depicted in duller, weaker colors). Above the ocean, dark, swirling clouds represent advanced persistent threats (APTs) and sophisticated hacking groups, constantly seeking vulnerabilities to exploit. Lightning bolts striking the ships illustrate successful cyberattacks.
The overall image conveys the unpredictable and ever-present danger lurking in cyberspace.
Interconnected Critical Infrastructure
This visual representation focuses on the interconnectedness of critical infrastructure. Imagine a network diagram, where nodes represent key infrastructure components – power plants, water treatment facilities, hospitals, transportation networks, and communication systems. These nodes are connected by brightly colored lines, representing the digital and physical links between them. Thicker, brighter lines indicate stronger, more robust connections, while thinner, dimmer lines represent weaker points of vulnerability.
Each node is shaded differently to represent its criticality; darker shades indicate higher criticality and potential impact if compromised. Vulnerabilities are highlighted by small, red flags placed near the nodes or connecting lines, representing potential entry points for attackers. For example, a red flag on a line connecting a power plant and a water treatment facility could represent a vulnerability in the communication system between the two.
The overall image emphasizes the cascading effect of a single successful attack, showing how a compromise in one area can quickly spread through the interconnected network, causing widespread disruption. This visual reinforces the importance of robust cybersecurity measures throughout the entire system, not just at individual nodes.
Ending Remarks
The FBI’s cybersecurity alert is a stark reminder that we all live in a hyper-connected world vulnerable to cyberattacks. While the threat landscape may seem daunting, understanding the risks and taking proactive steps is key. From implementing multi-factor authentication to staying informed about the latest threats, empowering yourself with knowledge is your best defense. Let’s work together to build a more secure digital future, one click at a time.
Remember, vigilance and proactive security measures are essential – your digital safety is in your hands!
FAQ Explained
What specific types of attacks are mentioned in the FBI alert?
The alert often covers a range of attacks, from ransomware and phishing to more sophisticated techniques targeting specific vulnerabilities in software and systems. The specifics vary depending on the alert.
How can I tell if my systems are vulnerable?
Regularly update your software, use strong passwords, and consider employing security software with vulnerability scanning capabilities. Staying informed about current threats is also crucial.
What should I do if I think I’ve been a victim of a cyberattack?
Immediately disconnect from the internet, report the incident to the authorities (potentially including the FBI’s Internet Crime Complaint Center – IC3), and consult with a cybersecurity professional.
Is my personal data at risk?
Depending on the nature of the attack and your online habits, your personal data could be at risk. Strong passwords, two-factor authentication, and avoiding suspicious links are crucial preventative measures.