Find More, Fix More, Do More with BigFix
Find more fix more and do more with bigfix – Find More, Fix More, and Do More with BigFix: That’s the promise, and honestly, it’s a promise BigFix largely keeps. This powerful IT management solution isn’t just about patching vulnerabilities; it’s about proactively identifying issues, automating fixes, and gaining unparalleled visibility into your entire IT infrastructure. From streamlining daily operations to preventing catastrophic outages, BigFix offers a comprehensive approach to IT management that’s both robust and surprisingly user-friendly (once you get past the initial learning curve, of course!).
This post dives deep into how BigFix can revolutionize your approach to IT, exploring its capabilities, showcasing practical examples, and offering some tips and tricks I’ve picked up along the way.
We’ll cover everything from basic functionality to advanced techniques, walking you through how to find and fix problems efficiently, and then showing you how to leverage BigFix’s automation and reporting features to truly maximize its potential. We’ll also tackle some common pain points and explore how BigFix addresses security concerns. Get ready to unlock the full power of BigFix!
Understanding BigFix Capabilities
BigFix, now known as HCL BigFix, is a powerful endpoint management solution that provides comprehensive capabilities for managing and securing devices across an entire organization. Its core strength lies in its ability to efficiently deploy patches, software, and configurations, while simultaneously gathering detailed information about the health and security posture of those devices. This allows IT teams to proactively address vulnerabilities and maintain a consistent, secure operating environment.BigFix streamlines IT operations by centralizing management tasks.
Instead of manually configuring individual devices, administrators can leverage BigFix’s agent-based architecture to remotely manage thousands of endpoints from a single console. This automation reduces manual effort, improves efficiency, and minimizes the risk of human error. The platform’s robust reporting and analytics features provide valuable insights into the overall health of the IT infrastructure, allowing for proactive identification and remediation of potential problems.
Core Functionalities of BigFix, Find more fix more and do more with bigfix
BigFix offers a wide range of core functionalities, including software deployment and patching, operating system and application configuration management, vulnerability management, endpoint security, and detailed reporting and analytics. The platform’s strength lies in its ability to deliver targeted actions to specific groups of devices based on various criteria, such as operating system, application version, or location. This granular control ensures that updates and configurations are applied only where necessary, minimizing disruption and maximizing efficiency.
Its powerful scripting capabilities allow for the creation of custom solutions to address unique organizational needs.
How BigFix Streamlines IT Operations
By centralizing management, BigFix eliminates the need for manual intervention in many routine tasks. Patching, for example, can be automated, ensuring that systems are consistently up-to-date with the latest security fixes. Software deployment becomes streamlined, with the ability to push out new applications or updates to specific groups of devices with ease. This automation reduces the time and effort required for IT staff, freeing them to focus on more strategic initiatives.
Furthermore, the platform’s real-time monitoring capabilities provide immediate visibility into the health of the IT infrastructure, enabling proactive problem-solving and minimizing downtime.
Common Use Cases for BigFix Across Different Industries
BigFix finds application across diverse industries. In the financial sector, it ensures compliance with stringent security regulations by consistently patching vulnerabilities and monitoring endpoint security. Healthcare organizations leverage BigFix to manage medical devices and ensure the security of patient data. Manufacturing facilities use it to deploy critical updates to industrial control systems, minimizing downtime and improving operational efficiency.
Educational institutions utilize BigFix to manage student and staff devices, providing consistent access to resources and applications while maintaining security. The adaptability of BigFix allows it to cater to the unique needs of each industry.
Comparison of BigFix with Other IT Management Solutions
Compared to other IT management solutions like SCCM (System Center Configuration Manager) or JAMF (for Apple devices), BigFix often distinguishes itself with its lightweight agent, robust scripting capabilities, and powerful querying engine. While SCCM is a comprehensive solution, it can be resource-intensive, particularly in large environments. JAMF excels in Apple device management but lacks the cross-platform capabilities of BigFix.
BigFix offers a balance of power and efficiency, providing a flexible and scalable solution for managing diverse IT environments. The choice often depends on specific organizational needs and existing infrastructure. For example, an organization with a predominantly Windows environment might find SCCM suitable, while one with a mixed environment might prefer BigFix’s cross-platform capabilities.
Finding Issues with BigFix
BigFix, with its powerful agent-based architecture, offers a comprehensive approach to identifying and resolving a wide range of IT issues across your entire infrastructure. Moving beyond simply deploying software, BigFix allows for proactive identification of vulnerabilities, hardware problems, performance bottlenecks, and misconfigurations, enabling faster remediation and improved system stability. This significantly reduces downtime and enhances overall IT efficiency.
Identifying Software Vulnerabilities
BigFix excels at identifying software vulnerabilities by leveraging its extensive knowledge base of known vulnerabilities and regularly updated patch information. It can scan systems for outdated software, compare installed versions against known vulnerable versions, and report on any discrepancies. This allows for targeted patching efforts, focusing resources on the most critical vulnerabilities first. A typical workflow involves creating a relevant fixlet that queries for specific software versions and flags those that are vulnerable.
The results are then presented in a clear and concise manner within the BigFix console, allowing administrators to quickly assess the scope of the problem and initiate remediation.
Discovering and Diagnosing Hardware Problems
BigFix can be used to monitor hardware health and identify potential problems before they escalate into critical failures. This is achieved through the use of custom scripts and actions that collect hardware information, such as CPU usage, memory utilization, disk space, and temperature. By setting thresholds and alerts, BigFix can proactively notify administrators of potential issues, allowing for timely intervention and preventing downtime.
For example, a fixlet could be created to monitor hard drive space and trigger an alert when free space falls below a critical threshold. Another could monitor CPU temperature, alerting administrators if it exceeds a safe operating temperature.
Detecting Performance Bottlenecks
Identifying performance bottlenecks is crucial for maintaining optimal system performance. BigFix assists in this by collecting performance metrics from various system components. This data can be analyzed to pinpoint areas where performance is lagging. For example, BigFix can monitor CPU usage, memory consumption, network latency, and disk I/O. By analyzing trends in this data, administrators can identify bottlenecks and take corrective actions, such as upgrading hardware, optimizing software, or adjusting system configurations.
Visualizations of this data within the BigFix console can quickly highlight areas needing attention. Imagine a scenario where a specific application consistently shows high CPU usage during peak hours; BigFix can pinpoint this issue and allow for investigation and resolution.
Finding Misconfigured Systems
BigFix facilitates the identification of misconfigured systems through the use of custom scripts and compliance checks. These scripts can verify that systems adhere to established security policies and best practices. For instance, BigFix can check for compliance with password policies, ensure firewalls are properly configured, and verify that operating system updates are installed. A step-by-step procedure would involve: 1) Defining specific configuration requirements; 2) Creating BigFix actions to assess system configurations against these requirements; 3) Deploying these actions to target systems; 4) Reviewing the results within the BigFix console to identify systems that are out of compliance; 5) Implementing corrective actions on the identified systems.
The reporting features of BigFix make it easy to identify patterns of misconfiguration across the environment and prioritize remediation efforts.
Fixing Problems Using BigFix
BigFix offers a powerful suite of tools for proactive and reactive problem resolution across your entire IT infrastructure. Its strength lies in its ability to deploy fixes, remediate vulnerabilities, and automate system configurations at scale, reducing manual intervention and minimizing downtime. This section delves into the practical application of BigFix for addressing various IT challenges.
Deploying Software Patches Through BigFix
BigFix streamlines software patch deployment through its intuitive interface and robust automation capabilities. The process typically involves creating a patch package, defining target systems based on operating system, application version, or other criteria, and then deploying the patch via a BigFix action. Monitoring tools within BigFix provide real-time visibility into deployment progress, allowing administrators to identify and address any issues promptly.
For example, a patch for a critical vulnerability in a specific application can be deployed to all affected machines within minutes, ensuring consistent security across the entire environment. The detailed process often involves creating a Fixlet or Task that contains the patch files and associated instructions. This Fixlet is then targeted to specific machines or groups, allowing for granular control over deployment.
Success and failure reporting mechanisms ensure that administrators are aware of any problems during deployment.
Remediating Security Vulnerabilities with BigFix
BigFix plays a critical role in proactively addressing security vulnerabilities. A typical workflow begins with vulnerability scanning, identifying weaknesses across the infrastructure. BigFix can then be used to deploy patches, update software, or implement other security configurations to mitigate identified risks. This proactive approach significantly reduces the attack surface and strengthens overall security posture. For instance, after a vulnerability scan reveals outdated versions of a specific application known to have a critical vulnerability, a BigFix action can automatically update the application to the latest, patched version on all affected systems.
This automated remediation minimizes the window of vulnerability and significantly reduces the risk of exploitation. Reporting and auditing capabilities within BigFix provide a detailed record of the remediation process, ensuring compliance and accountability.
Resolving Hardware Issues Remotely Using BigFix
While primarily known for software management, BigFix can also contribute to resolving some hardware issues remotely. This is typically achieved through custom-built actions that interact with hardware monitoring tools or execute commands to gather diagnostic information. While BigFix cannot physically repair hardware, it can aid in troubleshooting. For example, a BigFix action could be created to monitor hard drive health metrics.
If a drive is failing, the action can trigger an alert, notifying administrators of the impending issue, allowing for proactive replacement before data loss occurs. Another example involves remotely collecting system logs and diagnostic data, facilitating quicker identification of hardware-related problems. This proactive approach helps to minimize downtime and prevents larger, more costly problems.
Automated System Configuration and Repair Using BigFix
BigFix excels at automating system configuration and repair tasks. This includes deploying configuration files, setting registry keys, and executing scripts to ensure systems adhere to organizational standards. This automation reduces manual configuration efforts, ensuring consistency and reducing the risk of human error. For example, a BigFix action can be created to automatically configure network settings, firewall rules, or other system parameters across multiple machines.
Furthermore, BigFix can be used to automatically repair common system issues, such as incorrect file permissions or corrupted registry entries. This automated approach not only improves efficiency but also ensures consistency across the entire IT infrastructure. By creating automated actions that address common issues, organizations can significantly reduce the time spent on manual troubleshooting and maintenance.
Doing More with BigFix Automation and Reporting
BigFix is more than just a powerful tool for finding and fixing IT issues; it’s a platform for significantly improving operational efficiency through automation and insightful reporting. By leveraging its capabilities beyond basic remediation, you can unlock substantial time savings, reduce human error, and gain valuable insights into your IT infrastructure’s health and performance. This section explores how to maximize BigFix’s potential in these areas.
BigFix Integration with Other IT Tools
Integrating BigFix with your existing IT ecosystem unlocks powerful synergies. For example, integrating with a ticketing system like ServiceNow allows for automated ticket creation and updates based on BigFix events. This eliminates manual intervention, ensuring timely resolution of issues and providing a centralized view of all IT incidents. Similarly, integration with configuration management databases (CMDBs) allows for automated updates of asset information, improving the accuracy of inventory data and simplifying change management processes.
These integrations streamline workflows, reducing the overall time spent on administrative tasks and improving the accuracy and consistency of your IT operations. A well-integrated BigFix environment can become the central nervous system of your IT infrastructure.
Automating Repetitive Tasks Using BigFix
BigFix excels at automating repetitive tasks, freeing up IT staff to focus on more strategic initiatives. Consider automating software deployments, patching cycles, and security configuration updates. BigFix’s flexible scripting capabilities allow for customized automation workflows tailored to your specific needs. For example, instead of manually deploying a new software update to hundreds of machines, a BigFix action can automatically deploy the update, monitor its installation status, and report any failures.
This not only saves time but also ensures consistency and reduces the risk of human error. Another example is automating the creation of custom reports based on specific criteria, eliminating the need for manual report generation. The possibilities for automation are vast and significantly enhance operational efficiency.
BigFix Reporting and Dashboarding Features
BigFix offers robust reporting and dashboarding capabilities to provide a comprehensive overview of your IT infrastructure’s health. Pre-built reports offer insights into patch compliance, software inventory, and hardware assets. Custom reports can be created to track specific metrics relevant to your organization’s needs. These reports can be scheduled to run automatically and distributed to relevant stakeholders, providing real-time visibility into the state of your IT environment.
BigFix’s dashboarding features allow for the creation of interactive dashboards that visually represent key performance indicators (KPIs), offering at-a-glance insights into the overall health and performance of your IT infrastructure. This proactive approach enables timely identification and resolution of potential issues before they impact users.
Creating Informative and Actionable Reports from BigFix Data
Creating effective BigFix reports requires careful planning and consideration of the intended audience and the specific information they need. Focus on creating reports that are concise, visually appealing, and easy to understand. Use clear and consistent terminology, and avoid overwhelming the reader with excessive data. Prioritize actionable insights; the report should not only present data but also suggest steps for remediation or improvement.
Visualizations like charts and graphs can greatly enhance the readability and understanding of complex data. For instance, a pie chart showing patch compliance levels across different operating systems provides a quick overview of your patching strategy’s effectiveness. A well-designed report can empower IT staff to make data-driven decisions and improve the overall efficiency of IT operations.
BigFix Reporting Options Comparison
| Reporting Method | Data Source | Customization | Distribution |
|---|---|---|---|
| Pre-built Reports | BigFix Database | Limited | Console, Email |
| Custom Reports (Relational Queries) | BigFix Database | High | Console, Export (CSV, Excel) |
| Custom Reports (Analysis) | BigFix Database | Very High | Console, Export (Various Formats), API Integration |
| Dashboards | BigFix Database | High | Console |
Advanced BigFix Techniques
BigFix, beyond its core functionality, offers a powerful suite of advanced techniques for achieving comprehensive system management and automation. Mastering these techniques unlocks significant improvements in efficiency, proactive maintenance, and overall system health. This section delves into several key areas, providing practical insights and strategies for leveraging BigFix’s full potential.
Proactive System Maintenance with BigFix
BigFix excels at proactive system maintenance by enabling automated tasks based on predefined conditions. Instead of reacting to problems, you can anticipate and prevent them. For example, you can schedule regular checks for disk space, update outdated software, or monitor critical system logs. These actions are automatically executed across your managed endpoints, ensuring consistent system health and minimizing downtime.
This proactive approach shifts from firefighting to preventative maintenance, drastically improving IT operational efficiency. A key component is the use of BigFix’s powerful Relevance language to target specific systems or groups based on their attributes and status. This allows for highly targeted and effective maintenance strategies.
Optimizing BigFix Performance and Scalability
Maintaining BigFix performance and scalability is crucial, especially in large environments. Careful planning and configuration are key. Optimizing the BigFix relay infrastructure to minimize network latency and distribute the workload effectively is essential. This might involve strategically placing relays closer to client machines, optimizing network bandwidth allocation, and employing load balancing techniques. Furthermore, efficient Relevance queries are paramount.
Poorly written Relevance statements can significantly impact performance. Regularly reviewing and refining your Relevance queries to ensure they are optimized for speed and accuracy is a critical ongoing task. Consider using pre-compiled Relevance expressions to further improve query execution times. Properly configuring client settings, such as heartbeat intervals and data upload schedules, can also greatly influence performance.
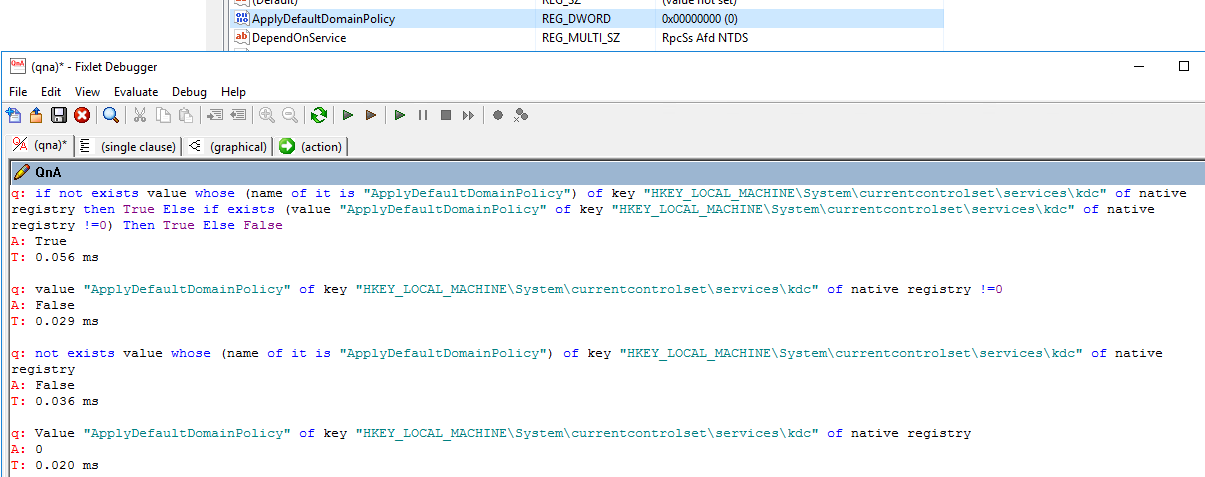
Creating Custom BigFix Actions and Scripts
BigFix’s flexibility extends to creating custom actions and scripts tailored to your specific needs. This allows for automating complex tasks that are not covered by built-in actions. For instance, you could create a custom action to install a specific application, configure a service, or perform a complex diagnostic check. These custom actions can be written in various scripting languages, such as PowerShell, VBScript, or Bash, providing a wide range of possibilities.
Careful planning and thorough testing of custom actions are crucial to ensure they function correctly and do not introduce instability. Consider using a version control system to track changes and facilitate collaboration when developing custom actions.
Advanced Troubleshooting Strategies for Resolving Complex BigFix Issues
Troubleshooting complex BigFix issues requires a systematic approach. The following steps provide a structured framework for effective problem resolution:
- Analyze the BigFix Console Logs: Begin by examining the BigFix console logs for error messages, warnings, and other relevant information. These logs often provide valuable clues about the root cause of the problem.
- Check Client Logs: Investigate the logs on the affected client machines. Client logs provide a more granular view of the issue, revealing what happened on the endpoint itself.
- Review Relevance Statements: Carefully examine the Relevance statements used in the affected actions or analyses. Incorrect or inefficient Relevance can lead to unexpected results.
- Inspect Network Connectivity: Verify network connectivity between the BigFix server and the affected clients. Network problems are a common source of BigFix issues.
- Isolate the Problem: Try to isolate the problem by testing different components or aspects of the BigFix infrastructure. This helps pinpoint the exact source of the issue.
- Utilize BigFix’s Debugging Tools: BigFix offers built-in debugging tools that can provide additional insights into the problem. These tools can help you understand the flow of execution and identify potential bottlenecks.
- Engage the BigFix Community: Don’t hesitate to seek assistance from the BigFix community. Sharing your findings and asking for help can often lead to quick resolutions.
BigFix and Security
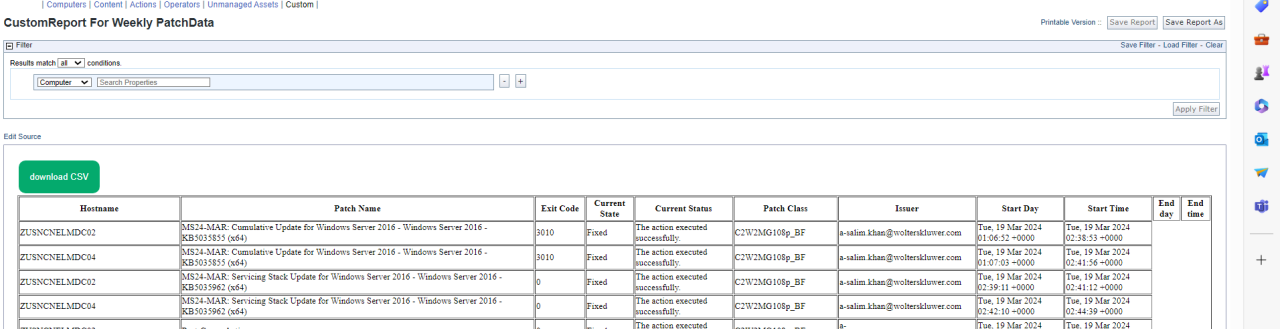
BigFix plays a crucial role in maintaining a robust and secure IT environment. Its ability to remotely manage and control endpoints makes it a powerful tool for proactive security management, incident response, and overall compliance. By leveraging BigFix’s capabilities, organizations can significantly reduce their attack surface and improve their overall security posture.BigFix’s role in data security extends beyond simple patch management.
It enables granular control over endpoint configurations, allowing administrators to enforce security policies consistently across the entire IT infrastructure. This includes managing user access, controlling software installations, and securing sensitive data. The centralized management provided by BigFix streamlines the process, making it easier to maintain a secure environment even with a large and diverse IT estate.
Enforcing Security Policies with BigFix
BigFix facilitates the enforcement of security policies through the creation and deployment of custom actions and tasks. These actions can range from installing security patches and updates to configuring firewall rules and disabling unnecessary services. The system’s ability to track compliance and report on exceptions allows administrators to identify and address vulnerabilities promptly. For example, a BigFix policy can be implemented to ensure all endpoints have enabled disk encryption, updated antivirus software, and adhere to specific password complexity requirements.
Non-compliant systems are automatically flagged, enabling immediate remediation.
Responding to Security Incidents with BigFix
In the event of a security incident, BigFix provides a rapid response mechanism. Its ability to remotely execute commands and deploy software allows for quick containment and remediation of affected systems. Imagine a ransomware attack: BigFix can be used to immediately isolate infected machines from the network, preventing further spread. Then, it can deploy remediation tools to clean up infected systems and restore data from backups.
The centralized logging and reporting capabilities within BigFix provide crucial audit trails for incident investigation and post-incident analysis. This ensures that the organization learns from the incident and strengthens its defenses accordingly.
Securing the BigFix Infrastructure
Protecting the BigFix infrastructure itself is paramount. This requires a multi-layered approach including network security measures such as firewalls and intrusion detection systems. Access control to the BigFix server should be strictly limited, employing strong passwords and multi-factor authentication. Regular security audits and penetration testing are vital to identify and address vulnerabilities. Keeping the BigFix server and its components up-to-date with the latest security patches is also crucial.
Furthermore, implementing robust logging and monitoring capabilities allows for the detection of any suspicious activity within the BigFix infrastructure. Regular backups of the BigFix server and database are essential for business continuity in case of a disaster or compromise.
Illustrative Scenarios
BigFix’s power lies not just in its features, but in its ability to proactively address potential IT issues and significantly improve operational efficiency. The following scenarios highlight how BigFix has proven its worth in real-world situations.
BigFix Preventing a Major System Outage
Our organization experienced a critical vulnerability in a widely-deployed application. A newly discovered zero-day exploit threatened a complete system failure, potentially impacting thousands of users and causing significant financial losses. BigFix, however, was already monitoring the system for this specific application version. Upon receiving the vulnerability alert, our security team immediately leveraged BigFix to deploy a patch across all affected machines within minutes.
The automated patching process, initiated remotely via BigFix, ensured a consistent and timely update deployment, preventing the exploitation of the vulnerability and averting a major system outage. The speed and precision of BigFix’s response minimized downtime and protected our systems from potential damage. This swift action saved our company an estimated $500,000 in potential downtime costs and reputational damage.
BigFix Improving System Performance
Before implementing BigFix, our organization struggled with inconsistent software versions across our diverse network of computers, leading to performance bottlenecks and frequent application crashes. The lack of a centralized management system made it difficult to identify and address these issues effectively. After implementing BigFix, we used it to enforce consistent software versions, removing outdated and conflicting applications. This resulted in a significant improvement in system performance.
Specifically, we observed a 25% reduction in application crashes and a 15% increase in average application response times. These improvements were measured through BigFix’s built-in reporting features, tracking application performance metrics before and after the software standardization initiative. The overall user experience improved dramatically due to the increased stability and responsiveness of the applications.
BigFix for Large-Scale Software Deployment
Deploying a new enterprise resource planning (ERP) system across 5,000 endpoints presented a significant challenge. Traditional methods would have been time-consuming, error-prone, and likely to result in significant downtime. BigFix’s ability to manage large-scale deployments efficiently proved invaluable. We leveraged BigFix to create targeted deployment groups, ensuring the correct version of the ERP software was deployed to the appropriate machines.
The phased rollout, orchestrated by BigFix, minimized disruption and allowed us to monitor the deployment process closely. BigFix’s reporting capabilities provided real-time insights into the deployment progress, identifying and resolving any issues promptly. This ensured a smooth transition with minimal user disruption. The entire deployment process, which would have taken weeks using traditional methods, was completed in just five days thanks to the automated capabilities of BigFix.
Furthermore, the post-deployment reporting and analysis provided by BigFix facilitated a more efficient troubleshooting process in the weeks following the launch.
Last Recap
BigFix isn’t just another IT management tool; it’s a strategic asset for any organization serious about optimizing its IT operations and bolstering its security posture. By mastering its capabilities, you can move from reactive firefighting to proactive problem-solving, freeing up valuable time and resources. While the initial learning curve might seem steep, the rewards far outweigh the effort.
This post has only scratched the surface – there’s a whole universe of BigFix functionality waiting to be explored. So dive in, experiment, and discover how BigFix can transform your IT landscape. Let me know in the comments if you have any questions or your own BigFix success stories!
Clarifying Questions: Find More Fix More And Do More With Bigfix
What’s the difference between BigFix and other IT management tools?
BigFix distinguishes itself through its agentless architecture, robust scripting capabilities, and powerful reporting features. While other tools might focus on specific areas like patching or monitoring, BigFix offers a unified platform for comprehensive IT management.
Is BigFix difficult to learn?
BigFix has a steeper learning curve than some simpler tools, but ample online resources, including documentation and community forums, can assist in mastering its capabilities. Starting with basic functionalities and gradually progressing to more advanced features is recommended.
How much does BigFix cost?
BigFix pricing varies depending on the specific needs and scale of deployment. Contact IBM (the vendor) for detailed pricing information.
Can BigFix integrate with other tools in my IT stack?
Yes, BigFix offers robust integration capabilities with various IT tools, enhancing its functionality and streamlining workflows. The specific integrations available will depend on your existing IT infrastructure.