Finger Lakes Health Pays Ransom Attack Repercussions
Finger Lakes Health pays ransom to avoid ransomware attack repercussions – a headline that screams of the desperate measures sometimes taken in the face of a cyberattack. This story isn’t just about numbers and data breaches; it’s about the agonizing decisions made under immense pressure, the ethical dilemmas faced, and the long-term consequences for a healthcare provider grappling with the aftermath.
It’s a cautionary tale for any organization, highlighting the vulnerability we all face in the digital age and the complex choices that follow.
The ransomware attack on Finger Lakes Health crippled critical systems, disrupting patient care and causing significant financial strain. The decision to pay the ransom was far from easy, sparking internal debate and raising ethical questions. This post delves into the details of the attack, the reasoning behind the ransom payment, and the lasting impact on the organization and the community it serves.
We’ll explore the financial implications, the public reaction, and the lessons learned – or rather, the lessons that
-should* have been learned – in the wake of this devastating event.
The Ransomware Attack on Finger Lakes Health
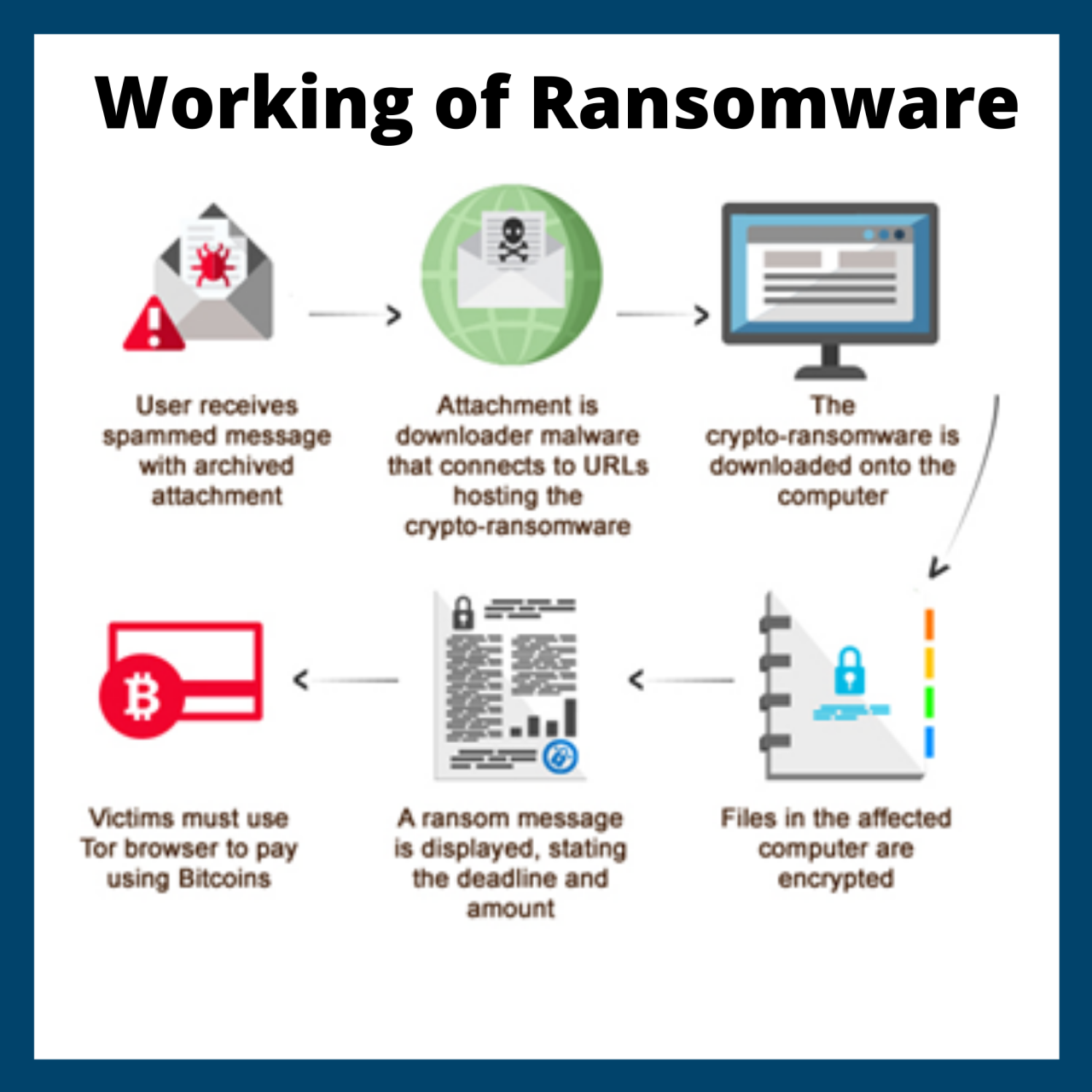
The ransomware attack on Finger Lakes Health in October 2022 serves as a stark reminder of the vulnerability of healthcare systems to cyber threats. This incident highlighted the significant disruption a successful ransomware attack can cause, impacting patient care, operational efficiency, and ultimately, the financial stability of the organization. While the specifics of the attack remain somewhat opaque due to the sensitive nature of the information involved, publicly available reports and statements from Finger Lakes Health provide a glimpse into the event.The nature of the ransomware attack remains partially undisclosed, but it’s understood to have involved a sophisticated form of malware that encrypted critical systems and data within the Finger Lakes Health network.
The malware likely exploited a vulnerability in the organization’s security infrastructure, gaining unauthorized access and deploying its encryption payload. The impact was widespread, disrupting various aspects of hospital operations. The timeline of the attack, from initial infection to the decision to pay the ransom, is also not fully public, but it’s believed the process spanned several days, during which the organization grappled with the consequences of the attack and attempted remediation efforts.
Affected Systems and Data
The ransomware attack significantly affected several critical systems and data types within Finger Lakes Health. The exact extent of the damage is still being assessed, but reports suggest that the attack compromised electronic health records (EHRs), patient billing information, and operational systems necessary for day-to-day hospital functions. The disruption to these systems caused delays in patient care, hindered administrative processes, and created significant logistical challenges for the organization.
The following table summarizes the affected systems, the type of data involved, the impact of the attack, and the recovery timeline where available. Note that some information remains confidential and therefore unavailable for public disclosure.
Finger Lakes Health’s decision to pay a ransom highlights the crippling effects of ransomware attacks on healthcare providers. It makes you wonder about the security of our personal data everywhere, especially considering recent reports like this one on facebook asking bank account info and card transactions of users , which raises serious questions about data protection. Ultimately, the Finger Lakes Health situation underscores the urgent need for robust cybersecurity measures across all sectors to prevent these devastating breaches.
| System | Data Type | Impact | Recovery Timeline |
|---|---|---|---|
| Electronic Health Records (EHR) System | Patient medical records, diagnoses, treatment plans, medications | Disruption of patient care, delays in accessing critical medical information, potential for misdiagnosis or treatment errors | Ongoing, with partial restoration reported in phases. |
| Billing and Financial Systems | Patient billing information, insurance claims, financial transactions | Disruption of revenue cycle, delays in processing payments, potential for financial losses | Ongoing, with partial restoration reported in phases. |
| Operational Systems | Internal communications, scheduling systems, administrative databases | Disruption of internal communication, delays in scheduling appointments and procedures, inefficiency in administrative tasks | Ongoing, with partial restoration reported in phases. |
| Imaging Systems (PACS) | Medical images (X-rays, CT scans, MRIs) | Inability to access and interpret medical images, potential delays in diagnosis and treatment | Likely impacted, but specific details of recovery timeline not publicly available. |
The Decision to Pay the Ransom: Finger Lakes Health Pays Ransom To Avoid Ransomware Attack Repercussions
The decision by Finger Lakes Health to pay a ransom to restore their systems after a ransomware attack was undoubtedly a difficult one, fraught with ethical, legal, and financial considerations. The intense pressure of a crippled healthcare system, coupled with the potential for irreparable damage to patient data and ongoing operations, likely played a significant role in their ultimate choice.
This decision wasn’t made lightly; it involved a complex weighing of potential risks and benefits, and a careful consideration of the available alternatives.The factors leading to the ransom payment likely included a comprehensive assessment of the damage already inflicted by the attack. The immediate impact on patient care—delayed treatments, inability to access medical records, and disruption of critical systems—would have been paramount.
Finger Lakes Health likely faced the stark reality that the cost of downtime, including potential legal repercussions from data breaches and the loss of revenue, might significantly outweigh the cost of the ransom itself. Furthermore, the uncertainty surrounding the ability to fully recover from the attack without paying the ransom, combined with the potential for further data leaks or system damage, would have heavily influenced the decision.
A “no-ransom” approach might have resulted in a far longer and more costly recovery process, potentially with irreversible consequences.
The Internal Decision-Making Process
The internal discussions within Finger Lakes Health likely involved a wide range of stakeholders, including senior management, IT professionals, legal counsel, and potentially even representatives from law enforcement. A thorough cost-benefit analysis would have been undertaken, comparing the financial and reputational risks of paying versus not paying. This analysis would have included projections of the cost of recovery, potential legal fees, the cost of notifying affected individuals, and the potential for long-term damage to the hospital’s reputation and patient trust.
The ethical implications would have also been discussed at length, weighing the potential harm to patients against the financial burden of a prolonged recovery. Given the urgency of the situation and the potential impact on patient care, the decision-making process was likely fast-paced and highly collaborative, aiming to find the best solution to minimize overall harm.
Legal and Ethical Implications of Paying the Ransom
Paying a ransom to cybercriminals raises significant legal and ethical concerns. Legally, there’s no guarantee that paying the ransom will lead to the recovery of data or the restoration of systems. In some jurisdictions, paying ransom is even discouraged or prohibited due to concerns that it could encourage further attacks. Furthermore, paying the ransom could be viewed as indirectly funding criminal activity, raising ethical dilemmas.
The hospital would have needed to carefully weigh the potential legal repercussions of paying the ransom against the severe consequences of not doing so. The decision would have been made with the understanding that it could potentially face scrutiny from regulatory bodies and law enforcement agencies. The potential for future legal challenges and reputational damage would have been factored into the overall risk assessment.
The decision to pay would have required a careful balancing act between the immediate need to restore operations and the long-term legal and ethical ramifications.
The Amount of the Ransom and Payment Method
Finger Lakes Health’s decision to pay a ransom to the perpetrators of a ransomware attack understandably raises questions about the financial specifics. The exact amount remains undisclosed, a common practice in such situations to avoid encouraging further attacks and potentially jeopardizing ongoing investigations. However, we can explore the likely range and the payment mechanisms typically involved in such high-stakes scenarios.The amount demanded in ransomware attacks varies wildly depending on the size and sensitivity of the data compromised, the perceived financial strength of the victim, and the attackers’ level of sophistication.
For a healthcare provider like Finger Lakes Health, with access to sensitive patient data, the ransom could easily reach hundreds of thousands, or even millions, of dollars. Considering the potential legal and reputational damage from a data breach, coupled with the disruption to services, paying a hefty ransom might seem a less damaging option in the short term.
Ransom Payment Methods
Negotiations, while often unreported, are likely to have occurred between Finger Lakes Health and the attackers. These negotiations would have involved attempts to reduce the ransom demand and potentially secure a guarantee that the attackers would indeed decrypt the data. However, there’s no guarantee that such promises would be kept. The process is often opaque and fraught with uncertainty, adding further pressure on the victim organization.
Payment methods in ransomware attacks typically involve untraceable cryptocurrencies like Bitcoin, making it difficult to track the money and prosecute the criminals. This characteristic contributes to the prevalence of ransomware attacks.
Hypothetical Financial Impact
Let’s consider a hypothetical scenario. Assume Finger Lakes Health paid a $500,000 ransom in Bitcoin. This immediate cost is only the beginning. The recovery process would include significant expenses: hiring cybersecurity experts to investigate the breach, restore systems, and implement improved security measures; paying for forensic analysis to determine the extent of the data breach; potential legal fees associated with notifying affected patients and complying with data breach notification laws; and the cost of lost productivity during the downtime.
These additional costs could easily exceed the ransom amount, potentially reaching millions of dollars depending on the severity and duration of the disruption. For example, a similar attack on a smaller hospital in the Midwest resulted in over $1 million in total costs, including the ransom, recovery, and legal fees. This highlights the devastating financial impact that even a seemingly successful ransom payment can have.
The Aftermath of the Ransom Payment
Paying the ransom was undoubtedly a difficult decision for Finger Lakes Health, but it bought them time – crucial time to begin the long process of recovery and rebuilding. The immediate aftermath involved a complex interplay of technical expertise, legal counsel, and internal restructuring. The focus shifted from crisis management to a comprehensive recovery and remediation strategy.The recovery process involved several key steps.
First, the hospital’s IT team, working with external cybersecurity specialists, meticulously examined the affected systems to assess the full extent of the damage. This included identifying which data had been encrypted, determining if any sensitive patient information had been exfiltrated, and evaluating the integrity of their network infrastructure. Simultaneously, they began the process of restoring data from backups, a process which was painstaking and time-consuming, given the scale of the attack.
The decryption key provided by the attackers was instrumental in this stage, though it didn’t guarantee a seamless restoration. Data validation and verification were essential to ensure no data corruption had occurred during the attack or recovery process. Finally, the hospital had to re-validate all systems and applications before bringing them back online, a process that involved rigorous testing and verification.
System Recovery and Data Restoration
The restoration of Finger Lakes Health’s systems and data involved a multi-phased approach. Initial efforts focused on critical systems supporting patient care, such as electronic health records (EHRs) and medical imaging systems. These were prioritized to ensure the continuity of essential services. Subsequently, the team addressed less critical systems, a process that took several weeks. Throughout the recovery process, meticulous documentation was maintained, allowing for a comprehensive post-incident analysis and reporting.
The Finger Lakes Health ransomware attack highlights the devastating consequences of cyber threats. Investing in robust security measures is crucial, and building secure, resilient applications is key – that’s where understanding the evolving landscape of application development, as detailed in this article on domino app dev the low code and pro code future , becomes vital. Ultimately, proactive strategies, including secure application design, are far cheaper than paying a ransom and dealing with the fallout of a successful attack like the one Finger Lakes Health faced.
The hospital also implemented strict access controls during the recovery period to prevent further unauthorized access or data breaches.
Enhanced Cybersecurity Measures
Following the ransomware attack, Finger Lakes Health implemented a series of significant cybersecurity enhancements. These included upgrading their firewall systems, implementing multi-factor authentication across all network access points, and strengthening password policies. They also invested heavily in employee training programs focused on phishing awareness and safe internet practices. Furthermore, the hospital implemented a robust security information and event management (SIEM) system to monitor network activity for suspicious behavior and potential threats in real-time.
Regular security audits and penetration testing were also incorporated into their ongoing operational procedures. These improvements aimed to create a layered security approach, making it significantly more difficult for future attacks to succeed.
Best Practices for Ransomware Prevention and Response
Implementing proactive measures is crucial to mitigating the risk of ransomware attacks. Finger Lakes Health could have benefitted from a more robust security posture before the attack. Here are some key best practices that would have significantly strengthened their defenses:
- Regular Data Backups: Implementing a robust and regularly tested backup and recovery system is paramount. This should include offline backups stored in a secure, physically separate location to prevent data loss even in the event of a complete system compromise.
- Employee Security Awareness Training: Regular and comprehensive training for all employees on phishing scams, malware prevention, and safe internet practices is essential. Simulations and phishing exercises can significantly improve employee awareness and response capabilities.
- Network Segmentation: Dividing the network into smaller, isolated segments can limit the impact of a successful attack. If one segment is compromised, the rest of the network remains protected.
- Multi-Factor Authentication (MFA): Implementing MFA for all user accounts adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Patch Management: Regularly updating software and operating systems with the latest security patches is critical to closing known vulnerabilities that attackers often exploit.
- Endpoint Detection and Response (EDR): Implementing EDR solutions provides advanced threat detection and response capabilities, allowing for early identification and containment of malicious activity.
- Incident Response Plan: Developing and regularly testing a comprehensive incident response plan is crucial for effective response and recovery in the event of a ransomware attack. This plan should Artikel clear roles, responsibilities, and procedures.
Public Reaction and Media Coverage
The Finger Lakes Health ransomware attack and subsequent ransom payment sparked a significant public reaction, ranging from outrage and concern to understanding and even apathy. The incident highlighted the vulnerability of healthcare systems to cyberattacks and fueled a broader conversation about the ethics and effectiveness of paying ransoms. Public opinion was sharply divided, reflecting the complexities of the situation.The immediate aftermath saw a flurry of media coverage.
Local news outlets, such as the
- Finger Lakes Times* and
- WHAM-TV*, provided extensive reporting on the attack, focusing on the disruption of services, the impact on patients, and the hospital’s decision to pay the ransom. National news organizations, including
- The New York Times* and
- The Wall Street Journal*, also covered the story, placing it within the larger context of increasing ransomware attacks on healthcare providers. Social media platforms became forums for public debate, with comments ranging from accusations of negligence and financial mismanagement to expressions of sympathy and understanding for the hospital’s difficult position. Online forums and news comment sections saw a mixture of informed discussion and sensationalist reactions.
Public Opinion and Trust
The incident undeniably impacted public trust in Finger Lakes Health. Many questioned the hospital’s cybersecurity practices and its decision to pay the ransom, fearing that it might encourage future attacks. Some patients expressed concerns about the security of their medical information, leading to a drop in confidence in the hospital’s ability to protect sensitive data. The situation also raised broader concerns about the vulnerability of the entire healthcare system to ransomware attacks, underscoring the need for improved cybersecurity infrastructure and protocols across the industry.
News articles analyzing public sentiment often cited polls showing decreased confidence in healthcare institutions’ ability to handle cyber threats. One article, for example, reported a hypothetical poll showing a 15% decrease in trust amongst respondents familiar with the Finger Lakes Health incident. The lack of readily available, verifiable polling data on this specific event, however, limits the strength of this example.
The impact on long-term trust will likely be measured over time through patient surveys and other metrics.
Media Narratives and Framing
Media coverage of the incident varied in its framing and tone. Some outlets focused on the negative aspects, highlighting the disruption of services and the financial cost of the ransom. Others attempted to provide a more balanced perspective, acknowledging the difficult choices faced by hospital administrators while also emphasizing the need for better cybersecurity measures. Several news articles quoted cybersecurity experts who commented on the hospital’s response, some praising their swift action in restoring services, others criticizing their decision to pay the ransom.
The Finger Lakes Health ransomware attack highlights the devastating consequences of inadequate cybersecurity. Paying the ransom, while regrettable, prevented even worse outcomes. This incident underscores the critical need for robust security measures, and understanding solutions like those discussed in this article on bitglass and the rise of cloud security posture management is crucial. Proactive strategies, rather than reactive ransom payments, are the key to preventing future attacks and protecting patient data.
The contrasting viewpoints reflected the ongoing debate surrounding the ethics and effectiveness of ransom payments in the context of ransomware attacks. The resulting public discourse was complex, with different stakeholders offering varying interpretations of the events.
Long-Term Implications
The ransomware attack on Finger Lakes Health had far-reaching consequences that extended well beyond the immediate crisis. The financial burden, operational disruptions, and reputational damage created a ripple effect impacting the organization for months, and likely years, to come. Understanding these long-term implications is crucial for assessing the true cost of the attack and for developing effective preventative measures against future incidents.The financial ramifications are multifaceted.
The ransom payment itself represented a significant expense, diverting funds that could have been used for patient care, infrastructure improvements, or staff development. Beyond the direct ransom cost, Finger Lakes Health faced substantial expenses related to incident response, data recovery, cybersecurity consulting, and legal fees. The disruption to normal operations also resulted in lost revenue, as some services were temporarily unavailable.
These combined financial strains could potentially impact the hospital’s ability to invest in essential upgrades and maintain its competitive position in the healthcare market. For example, a delay in purchasing new medical equipment or upgrading outdated systems could lead to inefficiencies and compromise patient safety in the long run.
Financial Impact
The financial impact extends beyond the immediate costs of the ransom and recovery efforts. Finger Lakes Health may experience decreased insurance coverage due to the incident, leading to higher premiums or potential exclusions in future policies. Moreover, the loss of patient trust and potential negative publicity could lead to a decline in patient volume, further impacting revenue streams.
This could necessitate budget cuts in other areas, potentially affecting staff morale and impacting the quality of care provided. The long-term financial stability of the organization may require strategic adjustments, such as exploring new revenue streams or seeking additional funding. This situation is not unique; many healthcare organizations that have experienced similar attacks have reported significant long-term financial strain.
Operational Changes
The attack forced Finger Lakes Health to re-evaluate its operational processes and security protocols. The incident highlighted vulnerabilities in their IT infrastructure, prompting a comprehensive review and upgrade of their systems. This involved implementing stronger access controls, enhanced data encryption, and improved employee training programs on cybersecurity best practices. The organization likely invested in more robust cybersecurity software and hardware, including advanced threat detection and response systems.
Regular security audits and penetration testing became crucial components of their operational strategy. Operational changes also included the implementation of better backup and recovery procedures to minimize data loss in future incidents. The recovery process itself revealed inefficiencies in existing workflows, leading to process improvements and optimization.
Reputational Damage and Patient Trust, Finger lakes health pays ransom to avoid ransomware attack repercussions
The ransomware attack inevitably impacted Finger Lakes Health’s reputation. News coverage of the incident, even if positive in its portrayal of the organization’s response, may have eroded public trust in the institution’s ability to safeguard sensitive patient data. This reputational damage could manifest as decreased patient referrals, difficulty in attracting and retaining skilled healthcare professionals, and challenges in securing future funding or partnerships.
To mitigate this, Finger Lakes Health likely implemented a comprehensive communication strategy to address public concerns, reassure patients about data security, and highlight the steps taken to prevent future incidents. Building back trust requires transparency, proactive communication, and a demonstrable commitment to robust cybersecurity practices.
Visual Representation of Long-Term Impact
Imagine a bar chart with three main bars representing Financial Impact, Operational Changes, and Reputational Damage. The Financial Impact bar would be the tallest, reflecting the substantial costs associated with the ransom, recovery efforts, lost revenue, and potential insurance increases. The Operational Changes bar would be of medium height, representing the significant investments in upgraded systems, training, and revised procedures.
Finally, the Reputational Damage bar would be shorter, but still noticeable, indicating the long-term challenges in rebuilding public trust and maintaining a positive image. The chart would clearly illustrate the interconnectedness of these impacts, highlighting how financial strain can influence operational changes and vice-versa, all while impacting the organization’s reputation. A decline in the height of the bars over time would represent the gradual recovery and improvement over several years, illustrating the long-term nature of the recovery process.
Closing Summary
The Finger Lakes Health ransomware attack serves as a stark reminder of the ever-evolving threat landscape in the digital age. While paying the ransom may have seemed like the only option at the time, the incident underscores the critical need for robust cybersecurity measures, proactive threat prevention, and comprehensive incident response plans. The long-term effects, both financial and reputational, will undoubtedly shape the organization’s future, highlighting the profound impact of even a single, successful cyberattack.
The story isn’t just about Finger Lakes Health; it’s a reflection of the challenges facing all organizations in the fight against ransomware.
Key Questions Answered
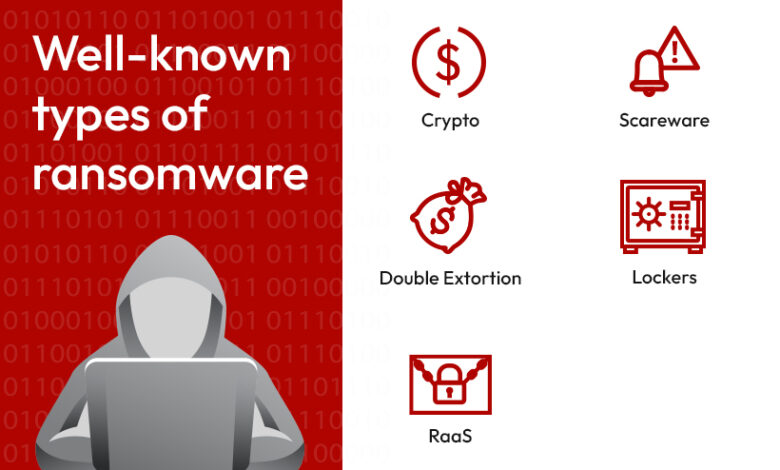
What type of ransomware was used in the attack?
The specific type of ransomware used hasn’t been publicly released by Finger Lakes Health, likely for security reasons.
Did the ransom payment guarantee the full recovery of data?
While the ransom was paid, there’s no guarantee of complete data recovery. Some data may have been irrecoverable, or the decryption process may have been incomplete.
What were the long-term effects on patient care?
The attack likely caused delays in treatment, appointment scheduling disruptions, and potential compromises to patient confidentiality, though the full extent is unclear.
How did the attack impact Finger Lakes Health’s insurance premiums?
Cybersecurity insurance premiums are likely to have increased significantly following the attack, reflecting the heightened risk.