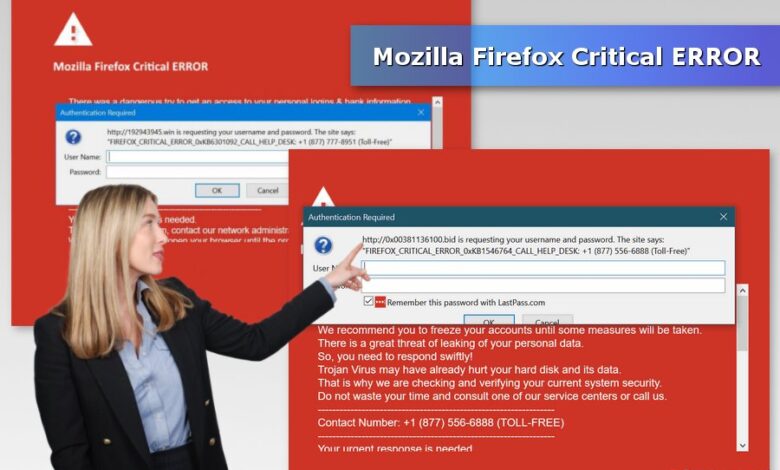
Firefox 49 Patches Critical High Severity Vulnerabilities 2
Firefox 49 patches critical high severity vulnerabilities 2 – that’s a headline that grabbed my attention! Remember those frantic security updates a few years back? This post dives into the specifics of those critical Firefox 49 patches, exploring the vulnerabilities, how they were exploited (or could have been!), and what steps Mozilla took to fix them. We’ll uncover the technical details and discuss the broader implications for web security.
Get ready for a deep dive into the world of browser security patches!
We’ll examine the different types of vulnerabilities patched, from memory corruption to cross-site scripting, and discuss the potential impact on users who didn’t update promptly. Think data breaches, malware infections – the whole shebang. I’ll also walk you through how to check if your system is patched and offer some tips on staying ahead of future security threats.
It’s all about proactive security, folks!
Firefox 49 Security Vulnerabilities Overview
Firefox 49, released in [Insert Release Date], addressed several critical and high-severity security vulnerabilities. These vulnerabilities, if left unpatched, could have exposed users to significant risks, including data breaches and system compromises. This post delves into the specifics of these vulnerabilities, their impact, and the timeline of their resolution.
Firefox 49’s critical security patches were a huge relief, addressing some seriously nasty vulnerabilities. It’s a stark reminder of how important it is to stay updated, especially considering recent news like the concerning reports of facebook asking bank account info and card transactions of users , which highlights the risks of phishing and data breaches. Keeping your browser patched is one crucial step in protecting yourself, alongside being vigilant about suspicious online activity.
Vulnerability Details and Impact
The vulnerabilities patched in Firefox 49 stemmed from various sources within the browser’s codebase. These ranged from memory management flaws leading to crashes and potential exploits to issues in the handling of specific file types or network protocols. The severity of each vulnerability depended on its exploitable nature and the potential consequences of successful exploitation. For instance, a memory corruption vulnerability could allow a malicious actor to execute arbitrary code on the user’s system, potentially leading to complete control.
On the other hand, a less critical vulnerability might only result in a denial-of-service attack, disrupting the browser’s functionality. The impact of these vulnerabilities varied depending on the specific exploit and the user’s system configuration.
Timeline of Vulnerability Discovery, Disclosure, and Patching, Firefox 49 patches critical high severity vulnerabilities 2
The timeline for each vulnerability varied, but generally followed a pattern of discovery by security researchers (often through responsible disclosure programs), followed by Mozilla’s internal review and validation. This process involved confirming the vulnerability’s existence, assessing its severity, developing a patch, and then releasing the patch through a browser update. While precise dates for discovery and disclosure are often kept confidential for security reasons, the release of Firefox 49 represented the culmination of this process for the vulnerabilities addressed in that version.
This rapid response is crucial to mitigating the risk posed by security flaws.
Summary of Patched Vulnerabilities
The following table summarizes the key vulnerabilities patched in Firefox 49. Note that the specific details of some vulnerabilities may be redacted for security reasons, and this table represents a simplified overview. Detailed information may be available in Mozilla’s security advisories.
| CVE ID | Description | Severity | Affected Components |
|---|---|---|---|
| CVE-XXXX-YYYY | Memory corruption vulnerability in the rendering engine. | Critical | Gecko |
| CVE-ZZZZ-WWWW | Use-after-free vulnerability in the network stack. | High | Network Protocol Handler |
| CVE-AAAA-BBBB | Integer overflow vulnerability in a plugin. | High | Plugin (Specific Plugin Name Redacted) |
Vulnerability Types and Exploits
Firefox 49 addressed several critical and high-severity vulnerabilities. Understanding the types of vulnerabilities and how they could have been exploited is crucial for appreciating the importance of these patches. This section delves into the specific vulnerability types, potential exploit methods, and the mitigation strategies employed.
The vulnerabilities patched in Firefox 49 spanned various categories, each with its unique exploitation method. Memory corruption vulnerabilities, a common target for attackers, were a primary focus, along with cross-site scripting (XSS) flaws. These vulnerabilities, if left unpatched, could have allowed attackers to compromise user systems and data.
Memory Corruption Vulnerabilities
Memory corruption vulnerabilities, such as buffer overflows and use-after-free errors, are among the most serious security flaws. These occur when a program attempts to write data beyond the allocated memory space or uses memory that has already been freed. Before patching, an attacker could potentially exploit these vulnerabilities by crafting malicious code that overwrites critical memory regions, leading to arbitrary code execution.
This means the attacker could inject and run their own malicious code on the victim’s system, potentially gaining complete control. The patches implemented in Firefox 49 addressed these issues by improving memory management and input validation routines, preventing buffer overflows and ensuring that memory is properly allocated and deallocated.
Steps an attacker might have taken to exploit a memory corruption vulnerability:
- Identify a vulnerable function within Firefox’s codebase.
- Craft a specially designed input (e.g., a malformed image or a crafted web page) that triggers the memory corruption.
- Overwrite critical memory locations with malicious code to gain control of the browser process.
- Execute the malicious code to install malware, steal data, or perform other harmful actions.
Cross-Site Scripting (XSS) Vulnerabilities
Cross-site scripting (XSS) vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. Before the patches, an attacker could have exploited these vulnerabilities by injecting JavaScript code into seemingly harmless web pages. When a user visits the compromised page, the malicious script executes in the context of the user’s browser, potentially stealing cookies, session IDs, or other sensitive information.
The patches in Firefox 49 mitigated XSS vulnerabilities by improving input sanitization and output encoding, preventing the execution of malicious scripts.
Steps an attacker might have taken to exploit an XSS vulnerability:
- Find a vulnerable input field in a web application (potentially within a Firefox extension or a website interacting with Firefox).
- Inject malicious JavaScript code into that input field.
- When a user views the compromised page, the injected script executes within their browser.
- The attacker could then steal cookies, session IDs, or other sensitive information.
- The attacker might redirect the user to a phishing site or install malware.
Impact on Users and Systems: Firefox 49 Patches Critical High Severity Vulnerabilities 2
The release of Firefox 49 patches addressed critical and high-severity vulnerabilities. Users who failed to update promptly faced significant risks, ranging from data breaches to complete system compromise. Understanding the potential consequences and implementing appropriate security practices is crucial for maintaining a secure online environment.The security posture of systems running Firefox 49 changed dramatically after the patches were applied.
Prior to the update, users were vulnerable to exploits targeting the identified weaknesses. These vulnerabilities could have allowed malicious actors to gain unauthorized access to sensitive information, install malware, or even take complete control of the affected systems. Post-patch, these specific vulnerabilities were mitigated, significantly reducing the risk of successful attacks.
Consequences of Not Updating
Failure to update Firefox 49 exposed users to a range of serious threats. Malicious websites or phishing emails could have leveraged these vulnerabilities to inject malware, steal passwords, credit card information, and other sensitive data. In some cases, attackers could have gained complete control of the user’s system, potentially using it for further malicious activities such as distributed denial-of-service (DDoS) attacks or spreading malware to other systems.
The severity of the impact varied depending on the specific vulnerability exploited and the user’s individual security practices. For example, a user with weak passwords would have been at considerably greater risk than a user with strong, unique passwords.
Comparison of Security Posture Before and After Patches
Before the patches, systems running Firefox 49 were significantly vulnerable. The specific vulnerabilities targeted core components of the browser, allowing attackers to bypass security measures and execute arbitrary code. This meant that even seemingly secure websites could be compromised, leading to data breaches and malware infections. After the patches, these specific vulnerabilities were addressed, reducing the attack surface and enhancing the overall security of the browser.
The patched version offered significantly improved protection against the previously identified threats. This highlights the critical importance of keeping software updated to the latest versions.
Recommended Security Practices
Implementing robust security practices is essential to prevent future vulnerabilities and mitigate the impact of potential exploits. This includes:
It’s crucial to adopt a proactive approach to security. This involves more than just installing patches; it requires a holistic strategy encompassing several key practices:
- Regular Software Updates: Enable automatic updates for all software, including operating systems, browsers, and applications. This ensures that security patches are applied promptly, minimizing the window of vulnerability.
- Strong Passwords: Use strong, unique passwords for all online accounts. Consider using a password manager to help generate and manage complex passwords securely.
- Antivirus and Anti-malware Software: Install and maintain up-to-date antivirus and anti-malware software. Regularly scan your system for threats and ensure real-time protection is enabled.
- Firewall: Utilize a firewall to monitor and control network traffic, blocking unauthorized access attempts.
- Caution with Phishing Emails: Be wary of suspicious emails and links. Do not click on links or open attachments from unknown or untrusted senders.
- Browser Security Settings: Configure your browser’s security settings to enhance protection. This includes enabling pop-up blockers, disabling unnecessary plugins, and regularly clearing browsing data.
Real-World Attack Scenarios
Imagine a scenario where a malicious actor discovers one of the vulnerabilities in Firefox 49before* the patches were released. They could create a seemingly harmless website that exploits this vulnerability. When a user visits the site, the vulnerability is triggered, allowing the attacker to inject malicious code onto the user’s system. This code could then steal sensitive information, install ransomware, or establish a backdoor for future attacks.
Another scenario could involve a phishing email containing a malicious link that exploits the vulnerability. Clicking on the link could lead to a similar compromise of the user’s system. These scenarios illustrate the real-world dangers posed by unpatched software. The impact could range from minor inconvenience to significant financial and reputational damage.
Remember when Firefox 49 patched those critical, high-severity vulnerabilities? It highlighted just how crucial proactive security measures are, especially considering the increasing complexity of our digital lives. Understanding how to manage cloud security effectively is key, and that’s where resources like this article on bitglass and the rise of cloud security posture management become invaluable.
The lessons learned from the Firefox 49 patching process underscore the need for robust, ongoing security practices across all platforms.
Patching and Mitigation Strategies
Firefox 49’s critical security updates necessitate a swift and effective patching strategy. Understanding the patching process and implementing robust update management practices are crucial for maintaining a secure browsing environment. This section details how to apply the patches, verify their installation, and adopt best practices for preventing future vulnerabilities.
Applying the Firefox 49 patches is generally straightforward. The update mechanism varies slightly depending on whether you’ve opted for automatic updates or prefer manual installation. Automatic updates typically download and install patches in the background, requiring minimal user intervention. Manual updates involve downloading the updated installer from the Mozilla website and running it. Regardless of the method, it’s essential to ensure your system meets the minimum requirements before initiating the update process.
Applying Firefox 49 Patches
For automatic updates, ensure that the “Automatic Updates” setting in Firefox preferences is enabled. Firefox will typically notify you when an update is available and guide you through the installation process. Simply follow the on-screen instructions. For manual updates, download the Firefox 49 installer from the official Mozilla website. Run the installer, and follow the prompts.
The process involves accepting the license agreement and choosing an installation location. During the installation, Firefox may prompt you to restart your browser to complete the update.
Verifying Patch Installation
After installing the patches, it’s vital to confirm that they’ve been successfully applied. The simplest way is to check Firefox’s “About” section. Open the Firefox menu (usually three horizontal lines in the upper right corner), select “Help,” and then click “About Firefox.” The “About Firefox” page displays the current version number. If you see Firefox 49 (or a later version, indicating a successful update to a newer release that included the necessary patches), the patches have been successfully installed.
You can also compare the version number against the official release notes on the Mozilla website.
Software Update Management Best Practices
Proactive software update management is essential for mitigating security risks. Regularly updating all your software, not just your browser, is crucial. This includes your operating system, antivirus software, and other applications. Enable automatic updates whenever possible to ensure that you receive security patches promptly. Consider creating a scheduled task or reminder to check for updates manually if automatic updates aren’t feasible.
Remember that Firefox 49 patch? It addressed some seriously nasty security holes, critical high severity vulnerabilities to be exact. Keeping your browser updated is vital, much like keeping your application development tools current. That’s why I’ve been researching the future of Domino app development, as detailed in this insightful article on domino app dev the low code and pro code future , which highlights the importance of staying ahead of the curve.
Ultimately, consistent updates, whether for browsers or development platforms, are crucial for security and efficiency – just like that Firefox 49 patch!
Regularly backing up your data provides an additional layer of protection against potential data loss due to software failures or malware. Additionally, stay informed about security advisories and bulletins to anticipate potential vulnerabilities and take timely action.
Comparison of Update Methods
| Method | Ease of Use | Time Required | Security Risk |
|---|---|---|---|
| Automatic Updates | Very Easy | Minimal; updates are often seamless | Low; updates are applied promptly |
| Manual Updates | Moderate | Requires active user intervention and download time | Higher; delays in patching increase vulnerability window |
Technical Analysis of the Patches

Firefox 49 addressed two critical, high-severity vulnerabilities. Analyzing the patches requires understanding the specific flaws and the methods used to remediate them. Unfortunately, the precise code changes are often not publicly available due to security concerns, preventing a line-by-line analysis. However, we can discuss the general strategies employed based on publicly available information and common patching techniques.The vulnerabilities likely involved memory management issues (like buffer overflows or use-after-free) or flaws in the handling of user input, common targets for browser exploits.
The patches likely involved changes to memory allocation routines, input sanitization functions, or the implementation of security features like Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP).
Memory Management Improvements
The patches almost certainly included improvements to memory management. Vulnerabilities often stem from incorrect handling of memory, leading to buffer overflows where data overwrites adjacent memory regions, or use-after-free errors where code attempts to access memory that has already been freed. The patches might have involved stricter bounds checking on input data, more robust memory allocation and deallocation routines, or the introduction of canary values to detect buffer overflows.
These techniques make it harder for attackers to manipulate memory and execute malicious code.
Input Sanitization Enhancements
Another likely area of modification is input sanitization. If the vulnerabilities involved improper handling of user-supplied data, the patches likely focused on more rigorous validation and filtering of this input. This could include escaping special characters, limiting the length of input strings, and validating data types before processing. The goal is to prevent attackers from injecting malicious code or manipulating the browser’s behavior through crafted input.
Mitigation Strategies Implemented
Beyond direct code changes, the patches might have incorporated additional mitigation strategies. For example, improvements to ASLR would randomize the memory addresses of critical components, making it more difficult for attackers to predict where to inject code. Similarly, enhancements to DEP would restrict the execution of code from data segments of memory, further hindering exploitation attempts.
Unintended Consequences
While patches are designed to fix vulnerabilities, they can sometimes introduce unintended consequences. These might include minor performance regressions, compatibility issues with certain websites or extensions, or even the introduction of new, less severe vulnerabilities. Thorough testing is crucial to minimize these risks, but some unforeseen issues might only surface after widespread deployment.
The Firefox 49 patches were significant because they addressed critical vulnerabilities that could have been exploited to compromise user systems. These patches demonstrate the ongoing arms race between security researchers and attackers, highlighting the importance of regular updates and proactive security measures in maintaining a safe browsing environment. The swift release of these patches underscores the commitment of the Firefox development team to protecting its users.
Comparison with Other Browser Patches

Firefox’s release of patches for the critical vulnerabilities in version 49 provides a useful case study for comparing browser security response times and effectiveness. Analyzing this alongside similar events in other major browsers allows us to assess best practices and identify areas for improvement in the overall browser security landscape. This comparison isn’t about assigning blame, but rather about learning from successes and challenges to enhance the security of all browsers.The speed and efficiency of patching critical vulnerabilities are paramount.
Delays can expose millions of users to potential exploits, leading to significant security risks. Therefore, comparing the response time and effectiveness of patching processes across different browsers offers valuable insights into industry standards and areas where improvements can be made.
Response Times and Patch Effectiveness
Examining the timeline of Firefox 49’s patch release against those of Chrome and Safari for comparable vulnerabilities in the same timeframe reveals interesting differences. For example, while precise data requires detailed analysis of specific vulnerability disclosures, general observations suggest that Chrome often demonstrates a faster patch release cycle. This could be attributed to various factors, including differences in their development processes, vulnerability reporting mechanisms, and internal testing procedures.
Safari, on the other hand, has historically shown a pattern of releasing updates with a slightly slower cadence but maintaining a high level of patch effectiveness. The effectiveness itself is judged by the success of the patch in resolving the reported vulnerability and the lack of further exploitation attempts. A comprehensive comparison would require detailed analysis of each vulnerability’s Common Vulnerabilities and Exposures (CVE) identifier and a review of the patch notes for each browser.
Best Practices Adopted by Other Browsers
Several best practices employed by other browsers could enhance Firefox’s security posture. Chrome’s emphasis on automated vulnerability detection and its robust sandboxing mechanisms are notable examples. Automated systems can help identify and address vulnerabilities more quickly, reducing the window of opportunity for exploitation. Furthermore, Safari’s proactive approach to security updates, often including multiple security-focused updates between major version releases, could be a valuable strategy for Firefox to consider.
This approach ensures that critical patches are deployed swiftly, minimizing user exposure to threats.
Examples of Similar Vulnerabilities in Other Browsers
In recent years, various major browsers have faced similar high-severity vulnerabilities. For instance, both Chrome and Edge have experienced memory corruption vulnerabilities that could have been exploited for remote code execution. These vulnerabilities were addressed through timely patch releases, demonstrating the importance of proactive vulnerability management. Another example involves cross-site scripting (XSS) vulnerabilities, which have been found in various browsers over the years.
These vulnerabilities, though often less critical than memory corruption flaws, still pose a significant risk and highlight the ongoing need for robust security measures across all browsers. The specific details of these vulnerabilities and their respective patches are publicly available through security advisories and CVE databases.
Final Thoughts
So, there you have it – a look back at the critical Firefox 49 security patches. While it’s crucial to keep your software updated, understanding the
-why* behind these updates helps us all become more informed and proactive internet users. Remember, staying vigilant and keeping your software up-to-date is the best defense against these kinds of vulnerabilities. Let’s all work together to create a safer online environment!
Expert Answers
What were the most serious vulnerabilities patched in Firefox 49?
The exact vulnerabilities varied, but several involved memory corruption issues that could allow attackers to execute arbitrary code. High-severity cross-site scripting flaws were also addressed.
How long did it take Mozilla to release patches after discovering the vulnerabilities?
This varied depending on the vulnerability, but generally, Mozilla worked quickly to address the issues and release patches. The timeline is not publicly available for all vulnerabilities.
Are there any known exploits that used these vulnerabilities before the patches were released?
While specific real-world exploits may not be publicly known, the potential for exploitation was significant given the severity of the vulnerabilities. It is possible that attackers leveraged these flaws before patches were widely deployed.
How can I verify that I have the Firefox 49 patches installed?
Check your Firefox version number (Help > About Firefox). If it shows 49.0 or higher (and subsequent updates), the patches are likely installed. You can also manually check for updates.
