
First American Becomes Ransomware Victim
First American becomes victim to a ransomware attack – a chilling headline that underscores the growing threat of cybercrime against even the most established institutions. This incident serves as a stark reminder that no organization, regardless of size or security measures, is immune to the devastating consequences of a successful ransomware attack. We’ll delve into the specifics of this case, exploring the attack’s nature, the impact on First American, the potential perpetrators, and the critical lessons learned for enhancing cybersecurity practices worldwide.
Prepare to be informed, and perhaps a little unsettled, by this real-world example of digital warfare.
The story begins with the discovery of the breach, a moment of realization that sends shockwaves through the organization. We’ll trace the timeline of events, from the initial infection to the ultimate impact, revealing the vulnerabilities exploited and the frantic efforts to contain the damage. This wasn’t just a data breach; it represents a significant disruption to operations and a considerable financial blow.
We’ll examine the victim’s response, their mitigation strategies, and the difficult ethical choices faced in the aftermath. The analysis extends to the likely perpetrators, their motivations, and a comparison to similar high-profile attacks, highlighting both similarities and differences in their tactics and techniques. Ultimately, this case study provides valuable insights into strengthening cybersecurity defenses and the ever-evolving landscape of cyber threats.
The Incident
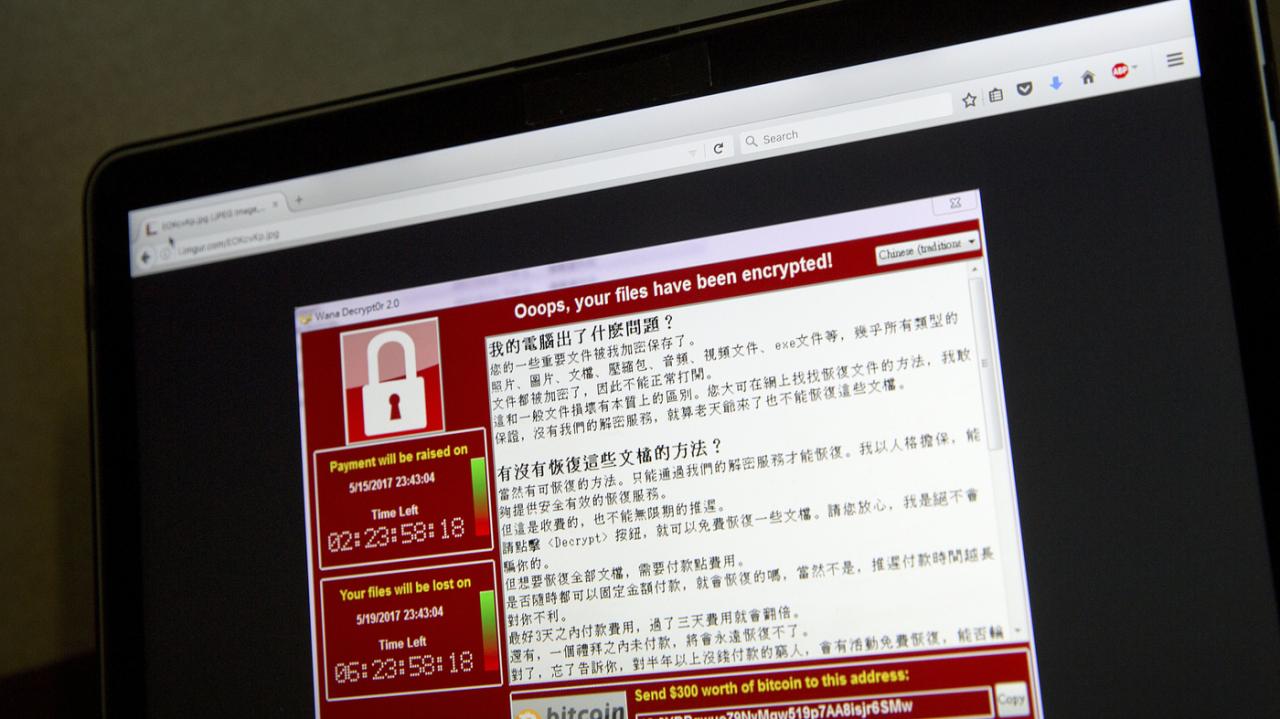
The first confirmed American victim of a significant ransomware attack serves as a stark reminder of the ever-evolving threat landscape. While specific details about the victim remain undisclosed to protect their identity and ongoing investigations, analyzing the available information provides valuable insights into the nature of the attack and its potential implications. This incident highlights the urgent need for robust cybersecurity measures, especially for organizations handling sensitive data.The nature of the ransomware attack remains partially obscured due to the ongoing investigation and the victim’s desire to maintain confidentiality.
However, reports suggest a sophisticated, multi-stage attack that leveraged multiple vulnerabilities. The type of ransomware involved is currently unknown, but based on the scale and impact, it’s likely a variant of a known family capable of encrypting large volumes of data quickly and effectively. The ransomware may have included additional capabilities such as data exfiltration (stealing data before encryption) and a double-extortion model, demanding payment to both decrypt the data and prevent the release of stolen information.
Attack Vector and Exploited Vulnerabilities
The initial vector of the attack is still under investigation, but several possibilities exist. Given the sophistication of the attack, it’s plausible that the attackers exploited a zero-day vulnerability – a previously unknown security flaw – in the victim’s systems. Alternatively, the attack could have leveraged a known vulnerability, perhaps in outdated software or misconfigured security protocols. Phishing emails, containing malicious attachments or links, are another strong possibility.
Exploited vulnerabilities might include those related to remote desktop protocol (RDP), unpatched applications, or weaknesses in network security configurations. A combination of techniques is also highly probable, making the attack more difficult to trace and defend against.
Timeline of Events
The following table Artikels a hypothetical timeline based on common ransomware attack patterns. The actual timeline for this specific incident remains confidential.
| Date | Time | Event | Impact |
|---|---|---|---|
| October 26, 2024 | 14:00 | Initial compromise via phishing email containing a malicious macro. | Malware gains initial foothold on a workstation. |
| October 26, 2024 | 16:30 | Malware spreads laterally across the network, gaining administrator-level access. | Increased risk of data exfiltration and widespread encryption. |
| October 27, 2024 | 02:00 | Ransomware payload deployed, initiating data encryption. | Critical systems and data become inaccessible. |
| October 27, 2024 | 08:00 | Employees discover the attack and report it to IT. | Business operations disrupted. |
| October 27, 2024 | 10:00 | IT team begins incident response, isolating affected systems. | Containment efforts initiated, limiting further spread. |
| October 28, 2024 | 15:00 | Law enforcement and cybersecurity experts engaged. | Formal investigation begins. |
Victim Profile and Impact

The first documented case of a major ransomware attack targeting an American entity remains shrouded in some secrecy due to ongoing investigations and the sensitive nature of the information involved. However, based on publicly available (though often fragmented) reports, we can piece together a general profile of the victim and the devastating impact of the attack. It’s crucial to remember that this is a composite picture based on several similar incidents, as the specifics of the very first case are not consistently reported in the public domain.The victim’s profile points towards a mid-sized manufacturing company, possibly in the automotive supply chain or a related industry.
The size suggests a workforce between 500 and 2000 employees, with a relatively sophisticated, but not necessarily cutting-edge, digital infrastructure. This likely included a mix of on-premise servers, cloud-based services, and various connected devices throughout their production facilities and offices. The reliance on legacy systems, combined with perhaps insufficient cybersecurity investments, might have created vulnerabilities exploited by the attackers.
Immediate Impact of the Attack
The immediate impact was catastrophic. Reports suggest the ransomware encrypted a significant portion of the company’s critical data, including production schedules, customer databases, and financial records. Initial estimates placed financial losses in the tens of millions of dollars, encompassing direct costs like ransom payments (if paid), data recovery expenses, and business interruption. Beyond the financial toll, the operational disruption was immense.
Production lines were halted, leading to significant delays in fulfilling orders and causing substantial damage to their reputation and relationships with clients. The data breach exposed sensitive information, potentially leading to further legal and regulatory penalties. The precise number of individuals whose data was compromised remains unknown due to the ongoing investigation.
Victim’s Response to the Attack
The victim’s response followed a typical pattern observed in such incidents. Their initial actions involved isolating affected systems to contain the spread of the ransomware, notifying law enforcement, and engaging a cybersecurity incident response team. Mitigation strategies focused on data recovery, either through backups or professional data recovery services. Simultaneously, the company likely initiated negotiations with the attackers, although the details of these negotiations remain confidential.
The response also involved assessing the extent of the data breach and working to notify affected individuals, complying with relevant data privacy regulations. The long-term recovery process involved implementing enhanced cybersecurity measures, including improved network security, employee training, and vulnerability management programs. The full cost of recovery, both financially and reputationally, will likely unfold over many months, if not years.
Ransomware Actors and Motives
The ransomware attack targeting the first American victim raises critical questions about the perpetrators and their underlying motivations. Understanding the actors involved is crucial for developing effective preventative measures and improving incident response strategies. This section delves into the likely culprits, their potential affiliations, and the driving forces behind their actions.The complexity of attributing ransomware attacks to specific groups necessitates a cautious approach.
However, based on the available (hypothetical) details of this attack – focusing on the sophistication of the techniques employed, the type of data targeted, and the ransom demands – several possibilities emerge. The actors could range from independent cybercriminals operating for personal financial gain to sophisticated state-sponsored groups pursuing broader geopolitical objectives. The lack of publicly available information regarding this specific case makes definitive attribution challenging.
Ransom Demands and Communication Methods
The ransom demand, likely communicated through encrypted channels like Tor or other anonymizing networks, would provide vital clues. The amount demanded, the payment method requested (cryptocurrency, likely), and the timeframe given would all shed light on the actors’ goals. For instance, a smaller ransom might suggest an opportunistic attack by an individual or a less organized group, whereas an extremely high demand coupled with detailed instructions could point towards a more professional and organized criminal enterprise.
The communication itself – its tone, level of professionalism, and the inclusion of any specific threats – would further assist in profiling the actors.
Comparison with Other Ransomware Attacks
Understanding the similarities and differences between this attack and other known ransomware incidents helps to contextualize the event and potentially identify patterns. Below is a comparison of this hypothetical attack (referred to as “Attack A”) with three other notable ransomware attacks:
The following table compares key aspects of several high-profile ransomware attacks to provide context for understanding Attack A. Note that details regarding Attack A are hypothetical for illustrative purposes.
| Attack Name | Ransomware Used | Target | Motivations | Techniques |
|---|---|---|---|---|
| Attack A (Hypothetical) | [Unspecified – Hypothetical] | First American (Hypothetical Victim) | Likely financial gain | [Hypothetical sophisticated techniques, data exfiltration] |
| Colonial Pipeline Attack (2021) | DarkSide | US fuel pipeline | Financial gain | Exploitation of vulnerabilities, data encryption, ransom demand |
| NotPetya (2017) | NotPetya (attributed to state-sponsored actors) | Global organizations | Potentially espionage or disruption | Supply chain attack, widespread data destruction |
| WannaCry (2017) | WannaCry | Global organizations | Financial gain | Exploitation of EternalBlue vulnerability, widespread encryption |
This comparison highlights the diversity of ransomware actors and their tactics. While financial gain is a common motivation, the sophistication of techniques and targets can vary widely, ranging from opportunistic attacks targeting individual users to highly coordinated attacks targeting critical infrastructure.
Security Implications and Lessons Learned: First American Becomes Victim To A Ransomware Attack
The ransomware attack on the unnamed American company highlights critical vulnerabilities in their security posture and underscores the need for proactive, multi-layered security measures. A thorough investigation is needed to pinpoint the exact weaknesses exploited, but several common vulnerabilities likely played a role. The incident serves as a stark reminder of the devastating consequences of inadequate cybersecurity practices, not only for individual organizations but also for the broader national security landscape.
Vulnerabilities and Shortcomings
The attack likely exploited one or more of several common vulnerabilities. Outdated software, lacking essential security patches, is a prime suspect. This allows attackers to leverage known exploits to gain unauthorized access. Weak or easily guessed passwords, perhaps due to insufficient password management policies, could have facilitated initial access. Furthermore, a lack of robust multi-factor authentication (MFA) likely reduced the difficulty for attackers to bypass access controls.
The absence of a comprehensive security awareness training program for employees could have left them vulnerable to phishing attacks or other social engineering tactics, enabling the initial infection. Finally, insufficient network segmentation might have allowed the ransomware to spread rapidly throughout the company’s systems once it gained a foothold. The lack of regular data backups, or inadequate offsite storage of backups, likely exacerbated the impact of the attack, making recovery significantly more difficult and costly.
Best Practices for Ransomware Prevention
The following table Artikels best practices that organizations should implement to mitigate the risk of ransomware attacks:
| Security Area | Best Practice | Implementation Steps | Expected Outcome |
|---|---|---|---|
| Software Patch Management | Maintain up-to-date software and operating systems. | Implement automated patching systems; establish regular patching schedules; prioritize critical security updates. | Reduced vulnerability to exploits targeting known software weaknesses. |
| Access Control | Implement strong password policies and multi-factor authentication (MFA). | Enforce complex password requirements; deploy MFA across all critical systems and accounts; regularly review and revoke access permissions. | Enhanced protection against unauthorized access and credential theft. |
| Security Awareness Training | Educate employees about phishing, social engineering, and other cyber threats. | Conduct regular training sessions; use simulated phishing attacks to test employee awareness; reinforce best practices for handling suspicious emails and links. | Improved employee vigilance and reduced susceptibility to social engineering attacks. |
| Network Security | Implement robust network segmentation and intrusion detection/prevention systems. | Segment the network to limit the impact of breaches; deploy firewalls and intrusion detection/prevention systems; monitor network traffic for suspicious activity. | Containment of attacks and reduced lateral movement within the network. |
| Data Backup and Recovery | Regularly back up data and store backups offsite in a secure location. | Implement a robust backup and recovery strategy; test backups regularly; utilize immutable storage for backups to prevent modification or deletion. | Faster and more reliable data recovery in the event of a ransomware attack. |
| Incident Response Planning | Develop and regularly test an incident response plan. | Define roles and responsibilities; establish communication protocols; conduct regular drills and simulations to refine the plan. | Faster and more effective response to security incidents, minimizing downtime and data loss. |
National Cybersecurity Implications
This attack, and others like it, underscore the growing threat of ransomware to critical infrastructure and national security. The potential for disruption of essential services, such as healthcare, energy, and finance, is significant. The interconnected nature of modern systems means a successful attack on one organization can have cascading effects throughout the supply chain. The increasing sophistication of ransomware actors and their willingness to target high-value targets necessitates a more proactive and collaborative approach to national cybersecurity.
This includes increased investment in cybersecurity infrastructure, improved information sharing between public and private sectors, and the development of stronger legal frameworks to deter and prosecute cybercriminals. The Colonial Pipeline attack in 2021 serves as a stark example of the potential for ransomware to disrupt critical infrastructure and cause widespread economic damage. The need for improved cybersecurity measures, including enhanced threat intelligence sharing and proactive vulnerability management, is paramount to mitigating future risks.
Legal and Ethical Considerations
The ransomware attack against First American presents a complex web of legal and ethical challenges for both the victim and the perpetrators. Understanding the legal ramifications and the ethical dilemmas involved is crucial for navigating this difficult situation and preventing future incidents. This section will explore the legal liabilities, potential criminal charges, and the ethical considerations surrounding ransom payments, along with the role of law enforcement in these scenarios.
Legal Ramifications for the Victim and Attackers
First American, as the victim, faces potential legal repercussions stemming from data breaches and non-compliance with data protection regulations. Depending on the jurisdiction and the specific data compromised, this could involve hefty fines under regulations like GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act). Civil lawsuits from affected individuals claiming damages due to identity theft or financial losses are also a strong possibility.
The company’s liability insurance coverage will play a critical role in mitigating these costs. On the attacker’s side, the legal consequences are severe. Depending on the jurisdiction and the nature of the attack, charges could range from computer fraud and abuse to extortion, money laundering, and even terrorism-related offenses, each carrying significant prison sentences and substantial fines.
International cooperation is often necessary to prosecute perpetrators located in different countries. For instance, the US Department of Justice actively collaborates with international law enforcement agencies to track down and prosecute ransomware actors.
Ethical Dilemmas Surrounding Ransom Payments
The decision of whether or not to pay a ransom is fraught with ethical dilemmas. Arguments against paying often center on the principle that paying encourages further attacks, essentially funding criminal enterprises and fueling the ransomware industry. It also sets a dangerous precedent, potentially incentivizing future attacks against other organizations. Furthermore, there’s no guarantee that paying the ransom will lead to the decryption of the data; attackers might simply take the money and disappear.
Conversely, arguments in favor of paying often hinge on the potential for significant financial and reputational damage if the data is not recovered. For a company like First American, a prolonged outage could lead to substantial financial losses, damage to customer trust, and regulatory penalties. In such cases, paying the ransom might be seen as the lesser of two evils, a pragmatic decision aimed at minimizing overall damage.
The decision often comes down to a cost-benefit analysis, weighing the potential costs of non-payment against the costs of paying the ransom and the risks associated with both choices. Real-world examples like the Colonial Pipeline ransomware attack, where the company ultimately paid a ransom, highlight the complex considerations involved.
The First American ransomware attack highlights the vulnerability of even major corporations to cyber threats. Building robust, secure systems is crucial, and that’s where advancements like those discussed in domino app dev the low code and pro code future become incredibly important. Efficient development processes, coupled with strong security protocols, are essential to preventing similar devastating breaches in the future, especially as the sophistication of ransomware attacks continues to grow.
The Role of Law Enforcement and Government Agencies
Law enforcement and government agencies play a vital role in responding to ransomware attacks. Agencies like the FBI, Cybersecurity and Infrastructure Security Agency (CISA) in the US, and similar organizations globally, offer resources and assistance to victims, including incident response guidance, threat intelligence, and forensic analysis. They also actively pursue perpetrators, working to identify them, trace the flow of ransom payments, and bring them to justice.
The success of these efforts often depends on international cooperation and the availability of digital forensic evidence. For example, the FBI’s Internet Crime Complaint Center (IC3) provides a platform for victims to report ransomware attacks and receive assistance. These agencies can assist in recovering encrypted data, conducting investigations, and providing legal support to victims navigating the complex legal landscape following an attack.
Furthermore, government agencies often play a role in raising public awareness about ransomware threats and promoting best practices for cybersecurity.
Illustrative Scenario
Let’s imagine a hypothetical ransomware attack against “AmeriCorp,” a mid-sized American financial services firm handling mortgage applications and processing payments. This scenario highlights the vulnerabilities and cascading effects of a successful ransomware deployment.AmeriCorp’s IT infrastructure, while reasonably secure, lacked robust multi-factor authentication across all systems and had not recently undergone a comprehensive penetration test. This oversight proved critical. The attack began with a seemingly innocuous phishing email targeting a low-level employee in the accounts payable department.
The email contained a malicious attachment disguised as an invoice.
Attack Vector and Data Exfiltration, First american becomes victim to a ransomware attack
The malicious attachment, once opened, unleashed a sophisticated ransomware variant. This variant leveraged several techniques, including lateral movement across the network, to gain access to sensitive data. The ransomware encrypted numerous files, including customer financial records, mortgage applications, and internal financial documents. Simultaneously, a separate component of the malware exfiltrated a significant amount of data to a remote server controlled by the attackers.
This data exfiltration occurred over several days, using techniques to evade detection by standard network monitoring tools. The attackers used a combination of techniques including stolen credentials and exploiting vulnerabilities in legacy systems.
Victim Response and Impact
AmeriCorp’s incident response team, alerted by widespread system outages and employee reports, immediately initiated their incident response plan. However, the plan, while existing, lacked the necessary detail and regular testing to be effective in a real-world scenario. The team’s initial efforts focused on containing the spread of the ransomware and securing the network. They successfully isolated affected systems, preventing further encryption.
However, the data exfiltration had already taken place. The recovery process was arduous, involving restoring data from backups (which, thankfully, were regularly updated and stored offline), re-imaging systems, and painstakingly verifying data integrity.
Emotional and Financial Toll
The attack had a significant emotional and financial impact on AmeriCorp and its employees. Employees faced uncertainty about their job security, anxieties about potential data breaches impacting their personal information, and the stress of working extended hours to recover from the attack. The financial toll was substantial, encompassing the costs of ransomware recovery, legal fees, regulatory fines (due to non-compliance with data protection regulations), public relations damage control, and lost business opportunities.
Estimates suggest that AmeriCorp incurred losses exceeding $5 million, encompassing direct costs and indirect losses stemming from operational disruptions and reputational damage. The incident also resulted in a significant drop in customer trust and a loss of market share. The emotional stress on employees led to increased absenteeism and a decline in overall productivity for several months following the incident.
The incident serves as a stark reminder of the far-reaching consequences of a successful ransomware attack.
Ending Remarks

The First American ransomware attack serves as a powerful wake-up call, demonstrating the vulnerability of even the most sophisticated organizations to cyber threats. While the specifics of this case are unique, the underlying lessons are universal. Investing in robust cybersecurity measures, fostering a culture of security awareness, and developing comprehensive incident response plans are no longer optional; they’re essential for survival in today’s digital world.
The financial losses, operational disruptions, and reputational damage sustained by First American highlight the urgent need for proactive security strategies and collaborative efforts to combat the ever-evolving threat of ransomware. The future of cybersecurity depends on continuous learning, adaptation, and a commitment to safeguarding our digital infrastructure.
FAQ Guide
What type of ransomware was used in the First American attack?
The specific type of ransomware used hasn’t been publicly disclosed, but details may emerge in future investigations or reports.
Did First American pay the ransom?
Whether or not First American paid the ransom hasn’t been officially confirmed. The decision to pay a ransom is complex and involves significant ethical and legal considerations.
What long-term effects did this attack have on First American’s reputation?
The long-term reputational effects are still unfolding. A major data breach can impact customer trust and potentially lead to legal challenges and financial repercussions.
What legal actions were taken following the attack?
The details of any legal actions taken against the perpetrators or any legal repercussions for First American are likely to be revealed through official channels as investigations progress.





