Fortifying the Human Firewall Six Steps for Effective Security Awareness
Fortifying the human firewall six steps for an effective security awareness program – Fortifying the human firewall: six steps for an effective security awareness program – it sounds serious, right? But think of it this way: your employees are your first line of defense against cyberattacks. They’re the ones clicking links, opening emails, and interacting with potentially malicious content. This isn’t about blaming individuals; it’s about empowering them with the knowledge and tools to stay safe.
This post dives into a practical, six-step program to build a robust human firewall, transforming your team from potential vulnerabilities into your strongest security asset.
We’ll explore how to create engaging training, run realistic simulations, and foster a culture of security awareness that goes beyond simple compliance. We’ll cover everything from understanding common attack vectors to implementing effective incident response procedures. Get ready to level up your organization’s cybersecurity posture, one employee at a time!
Defining the Human Firewall
The human firewall isn’t a physical wall or a piece of software; it’s the collective awareness and responsible behavior of every individual within an organization regarding cybersecurity. It represents the last line of defense against sophisticated attacks that often bypass even the most robust technical security measures. Understanding its role is crucial for building a truly secure environment.In today’s interconnected world, relying solely on technical security controls like firewalls, intrusion detection systems, and antivirus software creates a false sense of security.
These systems, while essential, are not foolproof. Sophisticated phishing attacks, social engineering scams, and insider threats can easily circumvent technical barriers, highlighting the critical need for a strong human element in cybersecurity. A layered security approach, combining robust technology with a well-trained and vigilant workforce, is far more effective.
Comparison of Human and Technical Security Controls
Traditional technical security controls focus on preventing unauthorized access to systems and data through technological means. They act as the first line of defense, filtering traffic and blocking malicious activity. The human firewall, however, operates differently. It focuses on preventing threats from gaining a foothold by educating users about potential risks and empowering them to make informed decisions. While technical controls are reactive, often identifying threatsafter* they’ve occurred, the human firewall is proactive, preventing many attacks before they can even begin.
Think of it as a highly trained security guard who understands the threats and knows how to respond appropriately, rather than a static barrier.
Types of Human Error and Their Consequences
Understanding the common ways humans contribute to security breaches is critical for developing effective mitigation strategies. The table below illustrates several examples:
| Error Type | Description | Impact | Mitigation Strategy |
|---|---|---|---|
| Phishing susceptibility | Clicking on malicious links or opening attachments from unknown senders. | Malware infection, data breaches, identity theft, financial loss. | Security awareness training focusing on phishing recognition, email authentication, and safe browsing practices. |
| Weak password practices | Using easily guessable passwords, reusing passwords across multiple accounts, or failing to change passwords regularly. | Account compromise, data breaches, unauthorized access. | Password management training, enforcing strong password policies, and promoting the use of multi-factor authentication. |
| Social engineering vulnerability | Falling prey to manipulation tactics, such as pretexting or baiting, to obtain sensitive information. | Data breaches, identity theft, financial loss, system compromise. | Security awareness training focusing on recognizing social engineering tactics, understanding the importance of verifying requests, and reporting suspicious activity. |
| Negligence in data handling | Leaving sensitive data unsecured, sharing information inappropriately, or failing to follow data handling procedures. | Data breaches, regulatory fines, reputational damage. | Data security training, establishing clear data handling policies, and implementing access control measures. |
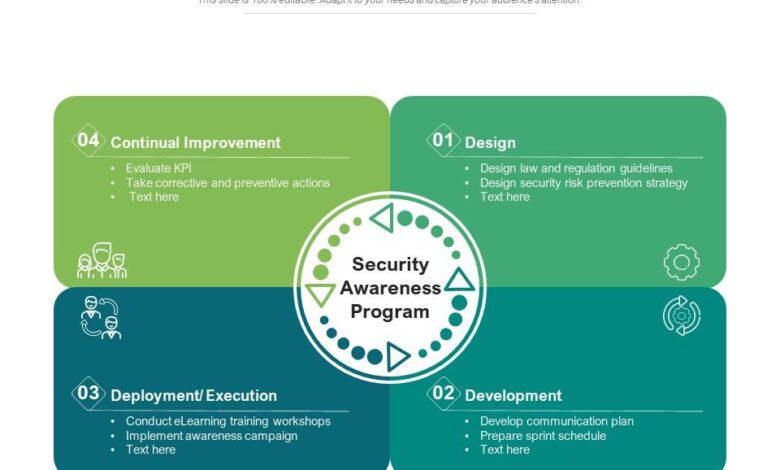
Building a Strong Foundation: Fortifying The Human Firewall Six Steps For An Effective Security Awareness Program
So, we’ve defined the human firewall – now let’s build it! A strong security awareness training program is the cornerstone of any effective cybersecurity strategy. It’s not just about ticking boxes; it’s about fostering a security-conscious culture where employees actively participate in protecting sensitive information. This requires a multi-faceted approach that goes beyond simple compliance training.A comprehensive security awareness training program needs a solid foundation built on clearly defined learning objectives, engaging content, and a variety of delivery methods.
Building a strong human firewall starts with a robust security awareness program – those six steps are crucial! But even the best training can’t completely negate the risks of cloud-based threats, which is why understanding solutions like bitglass and the rise of cloud security posture management is also vital. Ultimately, combining strong employee training with robust cloud security measures provides the most comprehensive protection.
We need to cater to different learning styles and ensure the training is relevant and memorable. Otherwise, it’s just another boring corporate training session that will quickly be forgotten.
Security Awareness Training Program Development
Developing a successful security awareness training program involves a structured, phased approach. First, we need to conduct a thorough needs assessment to identify specific vulnerabilities and knowledge gaps within the organization. This assessment should consider the roles and responsibilities of employees, the types of threats they face, and the level of their existing security awareness. Based on this assessment, we can define clear learning objectives that align with the organization’s overall security goals.
Next, we develop a training curriculum that covers key security topics, using a variety of engaging methods. Finally, we implement the training, track progress, and continuously evaluate and refine the program based on feedback and performance data. Regular updates and reinforcement are crucial to maintain effectiveness.
Designing Engaging and Effective Training Materials
Creating engaging training materials is paramount to successful security awareness training. Instead of lengthy, dry presentations, we should aim for interactive modules, short videos, and gamified elements. For example, a short video depicting a realistic phishing scenario followed by a quiz testing knowledge can be much more effective than a lengthy PowerPoint presentation. Real-life examples, case studies, and relatable scenarios resonate better with employees than abstract concepts.
The use of storytelling and humor can also significantly improve engagement and retention. Visual aids, such as infographics and memorable images, help simplify complex concepts and make them easier to understand and remember. For example, an infographic illustrating the different types of phishing attacks could be far more effective than a text-based explanation.
Incorporating Various Learning Styles and Modalities
People learn in different ways – visually, auditorily, or kinesthetically. A successful training program must cater to these diverse learning styles. Visual learners benefit from infographics, videos, and presentations with clear visuals. Auditory learners respond well to podcasts, webinars, and discussions. Kinesthetic learners, on the other hand, prefer hands-on activities, simulations, and interactive exercises.
By incorporating a variety of modalities, we can ensure that the training reaches a wider audience and maximizes learning outcomes. For instance, a module on password security could include a video explaining best practices, a quiz testing knowledge, and a hands-on exercise where participants create strong passwords.
Sample Training Module Agenda: Phishing, Passwords, and Social Engineering, Fortifying the human firewall six steps for an effective security awareness program
This sample agenda demonstrates how to structure a training module covering key security areas. The emphasis is on interactive elements and diverse learning methods.
| Topic | Activity | Learning Modality |
|---|---|---|
| Phishing Awareness | Interactive video depicting a phishing attempt, followed by a quiz. Discussion of real-world phishing examples. | Visual, Auditory, Kinesthetic (interactive quiz) |
| Password Security | Presentation on password best practices, followed by a password strength checker exercise. Group discussion on password management strategies. | Visual, Auditory, Kinesthetic (hands-on exercise) |
| Social Engineering Tactics | Role-playing scenarios simulating social engineering attempts. Discussion on recognizing and responding to social engineering tactics. | Kinesthetic (role-playing), Auditory (discussion) |
Practical Application
Making security awareness training truly effective requires more than just lectures and presentations. We need to move beyond passive learning and actively engage employees with realistic scenarios that mirror real-world threats. This is where simulations and real-world exercises become indispensable tools in fortifying the human firewall. By simulating threats and providing hands-on experience, we can significantly improve knowledge retention and build better security habits.Simulations and exercises allow employees to practice their security skills in a safe environment, learning from mistakes without real-world consequences.
This approach fosters a culture of proactive security, empowering individuals to become active participants in protecting company assets.
Types of Security Awareness Simulations
Security awareness simulations come in many forms, each designed to target specific threats and vulnerabilities. Phishing simulations, for example, mimic realistic phishing emails, testing employees’ ability to identify and report suspicious messages. These simulations can range from simple text-based emails to more sophisticated attacks incorporating malicious links and attachments. Social engineering scenarios involve simulated interactions with individuals attempting to manipulate employees into divulging sensitive information.
These scenarios can be conducted through phone calls, emails, or even in-person interactions. Another common simulation type involves testing employees’ response to malware infections or other cybersecurity incidents.
Gamification in Security Awareness Training
Gamification transforms security training from a tedious chore into an engaging and rewarding experience. By incorporating game mechanics such as points, badges, leaderboards, and challenges, we can significantly boost employee participation and knowledge retention. For example, awarding points for correctly identifying phishing emails or completing security training modules can create a sense of accomplishment and friendly competition. Leaderboards can further motivate employees to improve their security knowledge and skills.
This gamified approach makes learning more fun and memorable, ultimately leading to better security outcomes.
Realistic Security Scenarios
Employees face a wide range of security threats daily. Here are a few realistic scenarios that can be used in simulations and exercises:
- Receiving a phishing email disguised as a message from a known colleague or vendor.
- Encountering a suspicious link or attachment in an email or social media message.
- Being approached by a social engineer attempting to gain access to sensitive information.
- Losing a company device containing sensitive data.
- Observing suspicious activity on a company network or system.
- Accidentally downloading malware from an infected website.
- Failing to properly secure a personal device connected to the company network.
These scenarios, and many others, can be adapted to reflect the specific risks and vulnerabilities faced by your organization.
Simulation Types, Objectives, and Assessment Methods
| Simulation Type | Objective | Assessment Method |
|---|---|---|
| Phishing Simulation | Assess ability to identify and report phishing emails. | Track click-through rates, reporting rates, and responses to simulated phishing attacks. |
| Social Engineering Scenario | Assess ability to resist social engineering tactics. | Observe employee responses to simulated social engineering attempts, analyzing their ability to identify and resist manipulation. |
| Malware Simulation | Assess response to malware infection. | Evaluate the speed and effectiveness of incident reporting and remediation efforts. |
| Security Awareness Quiz | Assess knowledge retention. | Analyze quiz results to identify areas needing further training. |
| Vulnerability Scanning Simulation | Assess ability to identify and report security vulnerabilities. | Track the number and types of vulnerabilities identified and reported. |
Continuous Improvement
Building a truly effective human firewall requires more than a one-time training session. Continuous improvement is the key to maintaining a strong security posture and adapting to the ever-evolving threat landscape. Regularly evaluating your program’s effectiveness and making necessary adjustments is crucial for long-term success. This involves tracking key metrics, analyzing results, and updating your approach to keep pace with emerging threats.Regularly assessing your security awareness training program’s impact is paramount.
This involves more than simply delivering training; it requires a systematic approach to measuring its effectiveness and making necessary changes. Ignoring this crucial step could leave your organization vulnerable to attacks that could have been prevented with better, more targeted training.
Key Metrics for Evaluating Program Effectiveness
Measuring the success of your security awareness program requires a multifaceted approach. Focusing on isolated metrics can be misleading; a holistic view provides a more accurate assessment. We need to understand not only if employees
- know* the information, but also if they
- apply* it in their daily work.
- Phishing Simulation Results: Tracking the click-through rates on simulated phishing emails provides a direct measure of employee susceptibility to social engineering attacks. A high click-through rate indicates a need for more targeted training on recognizing phishing attempts.
- Security Incident Reports: Analyzing the number and type of security incidents can reveal vulnerabilities in employee knowledge and behavior. A decrease in incidents related to phishing or password vulnerabilities demonstrates the training’s positive impact.
- Employee Surveys and Quizzes: Regular assessments gauge employee understanding of security policies and procedures. Anonymous surveys can provide valuable feedback on training effectiveness and areas needing improvement.
- Data Loss Prevention (DLP) Metrics: Monitoring data loss incidents can indicate whether training is effectively preventing sensitive data breaches. A reduction in such incidents validates the training’s success in promoting responsible data handling.
Tracking Employee Engagement and Knowledge Retention
Simply delivering training isn’t enough; you need to ensure employees actively participate and retain the information. This requires ongoing monitoring and engagement strategies.Tracking employee engagement involves monitoring participation rates in training modules, quiz scores, and feedback provided through surveys. Knowledge retention can be assessed through periodic quizzes or simulated phishing campaigns. Regular reinforcement through short, engaging updates and reminders can significantly boost knowledge retention.
For example, a monthly email highlighting a specific security best practice can help reinforce key learnings from the initial training. A gamified approach, incorporating points or rewards for participation and successful completion of assessments, can also boost engagement and retention.
Analyzing Training Results and Identifying Areas for Improvement
Analyzing the data collected from various metrics allows for a targeted approach to improvement. For instance, if phishing simulation results reveal a high click-through rate on emails mimicking a specific type of attack, this indicates a need for more focused training on identifying that particular threat vector. Similarly, low scores on quizzes related to password security might suggest a need for revised training materials or supplementary resources.By carefully analyzing the data, organizations can pinpoint specific areas where their security awareness program falls short and implement targeted improvements.
This could involve revising training materials, developing supplementary resources, or implementing more effective engagement strategies. For example, if data reveals a lack of understanding regarding safe browsing habits, the program could be updated to include interactive modules specifically addressing this issue.
Fortifying the human firewall is crucial, and a strong security awareness program is key. We need to train users to spot phishing attempts like the recent scare where, as reported by facebook asking bank account info and card transactions of users , many fell victim. That’s why implementing those six steps for an effective security awareness program is so vital in preventing future attacks.
Regularly Updating Training Materials
The threat landscape is constantly evolving, so training materials must be updated regularly to reflect the latest threats and vulnerabilities. This ensures employees are equipped to handle the latest challenges. Outdated information can be counterproductive, creating a false sense of security and leaving employees vulnerable to newer, more sophisticated attacks.For example, new phishing techniques emerge regularly. Training should incorporate these techniques, showcasing real-world examples of recent attacks.
Building a strong human firewall requires a comprehensive security awareness program, and a key part of that is empowering employees with the right tools. Understanding how to leverage technology for security is crucial, which is why I’ve been exploring the exciting advancements in domino app dev, the low-code and pro-code future , to see how it can streamline our security processes.
Ultimately, though, even the best tech is only as good as the people using it, reinforcing the need for that six-step security awareness training.
Similarly, changes in software or hardware security protocols necessitate updates to training materials to ensure employees are using the latest security best practices. Regular reviews of training content and alignment with current threat intelligence feeds are essential for maintaining the effectiveness of the human firewall.
Promoting a Security Culture
Building a strong human firewall isn’t just about training; it’s about fostering a culture where security is everyone’s responsibility. This proactive approach shifts the mindset from passive compliance to active participation, significantly strengthening your organization’s defenses. A security-conscious culture isn’t born overnight; it requires consistent effort, clear communication, and visible leadership support.A culture of security awareness thrives on proactive behavior.
Employees who understand the “why” behind security protocols are more likely to adhere to them and even report potential threats. This proactive approach goes beyond simply following rules; it encourages critical thinking and a sense of ownership over the organization’s security posture. This section will explore how to cultivate this vital element of a robust human firewall.
Leadership’s Role in Promoting Security Best Practices
Leadership plays a pivotal role in setting the tone for security awareness. When senior management actively champions security initiatives, it sends a clear message that security is a top priority, not just an afterthought. This visible commitment inspires trust and encourages employees at all levels to take security seriously. For example, a CEO publicly acknowledging and rewarding employees for reporting a phishing attempt demonstrates a tangible commitment to security.
This visible support translates into increased employee engagement and a stronger security culture overall. Without active leadership buy-in, security awareness programs often lack the necessary momentum and impact.
Effective Communication Strategies for Security Information Dissemination
Effective communication is crucial for disseminating security information to employees. Simple email blasts often fail to engage employees. Instead, consider diverse approaches. Short, engaging videos explaining security concepts, interactive quizzes testing employee knowledge, and gamified training modules can significantly improve information retention and engagement. Regular security newsletters highlighting recent threats and best practices keep the topic relevant and top-of-mind.
Town hall meetings, where employees can ask questions and receive direct answers from security experts, foster a sense of transparency and build trust. Tailoring communication to different departments and roles ensures relevance and maximizes impact. For instance, the security message for the IT department would differ from that for the marketing department, reflecting their specific roles and potential vulnerabilities.
Incentives and Recognition Programs for Proactive Participation
Recognizing and rewarding employees for their proactive security contributions is essential for reinforcing positive behavior. A simple “thank you” goes a long way, but tangible rewards can significantly boost engagement. Consider implementing a tiered reward system, offering increasingly valuable prizes for reporting serious vulnerabilities or participating in security awareness training. These rewards could include gift cards, extra vacation days, public acknowledgment in company newsletters, or even nominations for company awards.
Furthermore, creating a secure reporting mechanism, where employees feel comfortable reporting security concerns without fear of reprisal, is critical. This could involve anonymous reporting systems or designated security champions within teams who can act as intermediaries. A successful program builds a culture where reporting security issues is not only encouraged but also celebrated.
Responding to Incidents
A robust security awareness program isn’t complete without a well-defined incident response plan. Knowing what to doafter* a breach is just as crucial as preventing one in the first place. A swift and effective response can minimize damage, maintain business continuity, and ultimately, strengthen your overall security posture. This involves a structured approach encompassing reporting, investigation, containment, remediation, and post-incident analysis.The process of responding to a security incident is a critical component of any organization’s overall security strategy.
A well-defined plan ensures a coordinated and efficient response, minimizing the impact of a breach and facilitating a faster recovery. This section details the essential steps involved, from initial detection to post-incident review.
Incident Reporting and Investigation
Effective incident response begins with a clear and efficient reporting mechanism. Employees should be trained to recognize suspicious activity and report it immediately through designated channels, such as a dedicated email address, a ticketing system, or a hotline. The reporting process should be straightforward and non-punitive to encourage prompt reporting. Following a report, a thorough investigation is crucial to understand the nature and scope of the incident.
This involves gathering evidence, identifying affected systems, and determining the potential impact. Tools such as security information and event management (SIEM) systems can greatly assist in this process. The investigation should aim to answer key questions: What happened? When did it happen? How did it happen?
Who was affected? What data was compromised (if any)?
Containing and Remediating Security Breaches
Once the nature of the incident is understood, the focus shifts to containment and remediation. Containment involves isolating affected systems to prevent further damage or spread of the threat. This may involve disconnecting infected machines from the network, blocking malicious IP addresses, or implementing temporary access restrictions. Remediation involves addressing the root cause of the breach and restoring affected systems to a secure state.
This might include patching vulnerabilities, removing malware, restoring data from backups, and implementing stronger security controls. The speed and effectiveness of containment and remediation are paramount in minimizing the overall impact of the incident. For example, a timely response to a ransomware attack can significantly reduce the amount of data lost and the cost of recovery.
Post-Incident Analysis and Lessons Learned
After the immediate threat is neutralized, a comprehensive post-incident analysis is vital. This involves reviewing the entire incident timeline, identifying weaknesses in the security controls, and determining what could have been done differently. The goal is not to assign blame but to learn from the experience and improve future security measures. A formal report documenting the incident, the response, and the lessons learned should be created and shared with relevant stakeholders.
This information should be used to update security policies, procedures, and training programs. For instance, if a phishing attack succeeded due to insufficient employee training, the post-incident analysis would highlight the need for improved phishing awareness training.
Incident Response Process Flowchart
Start --> Incident Detection --> Incident Reporting --> Initial Assessment --> Containment --> Eradication --> Recovery --> Post-Incident Analysis --> Lessons Learned --> System Updates/Policy Changes --> EndThe flowchart above provides a simplified representation. In reality, there may be iterations and feedback loops between different stages. For example, the initial assessment may reveal the need for additional containment measures, or the eradication phase may uncover new vulnerabilities requiring further investigation. The process is iterative and adaptive.
Closing Notes

Building a strong human firewall isn’t a one-time project; it’s an ongoing process of education, reinforcement, and adaptation. By implementing these six steps – defining the human firewall, building a strong training foundation, using practical simulations, measuring effectiveness, promoting a security culture, and establishing robust incident response – you can significantly reduce your organization’s vulnerability to cyber threats. Remember, your employees are your greatest strength, and empowering them with security awareness is an investment that pays dividends in peace of mind and protected data.
Expert Answers
What if my employees resist security training?
Make it engaging! Gamification, real-world scenarios, and clear explanations of
-why* security matters are key. Incentivize participation and highlight success stories.
How often should we update our security awareness training?
Regularly! Cyber threats evolve constantly. Aim for at least annual updates, with more frequent refreshes on specific topics as needed (e.g., new phishing techniques).
What’s the best way to measure the effectiveness of our program?
Track key metrics like phishing simulation success rates, reported suspicious activities, and employee knowledge retention through quizzes and assessments. Analyze these results to identify areas for improvement.
How do we deal with employees who repeatedly ignore security protocols?
Progressive discipline is necessary. Start with reminders and retraining, then escalate to more formal measures if the behavior persists. Document everything.
