Four Ways to Make Yourself a Harder Target for Cybercriminals
Four Ways to Make Yourself a Harder Target for Cybercriminals – it sounds intense, right? But honestly, boosting your online security doesn’t have to be a Herculean task. We’re bombarded daily with scary headlines about data breaches and online scams, making it easy to feel overwhelmed. This post breaks down four simple yet powerful strategies you can implement today to significantly reduce your risk.
Think of it as building a personal digital fortress, one brick at a time.
We’ll cover everything from crafting seriously strong passwords (and remembering them!) to navigating the treacherous waters of phishing emails and public Wi-Fi. By the end, you’ll have a clearer understanding of the threats and the surprisingly straightforward ways to protect yourself. Let’s get started!
Strong Passwords and Authentication
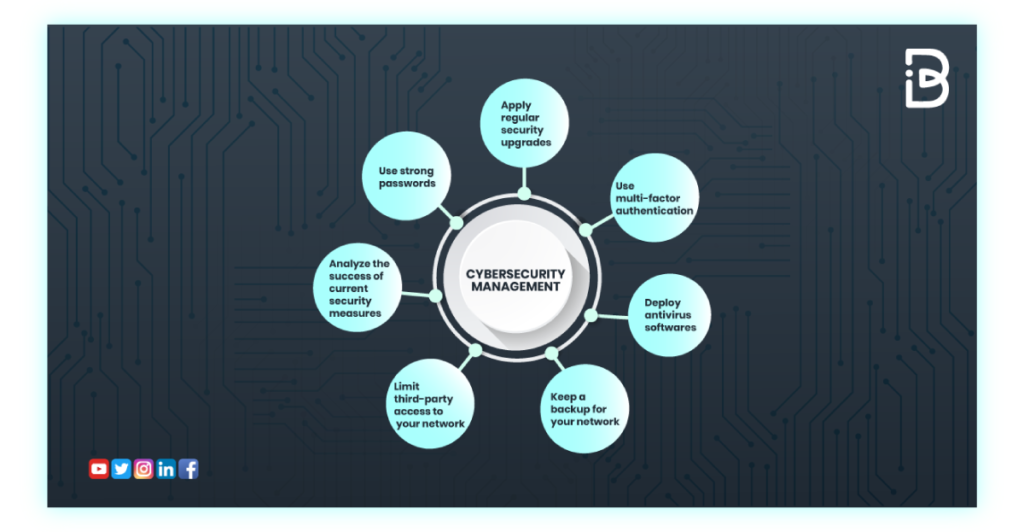
Protecting your digital life starts with a strong foundation: robust passwords and multi-factor authentication. In today’s interconnected world, weak passwords are an open invitation for cybercriminals. This section will delve into best practices for securing your accounts and minimizing your vulnerability.
The importance of using unique and complex passwords for every online account cannot be overstated. Reusing passwords across multiple platforms creates a cascading effect: if one account is compromised, all others using the same password are at risk. This is why employing strong passwords, coupled with effective password management and multi-factor authentication, is crucial for maintaining digital security.
Strong Password Creation Techniques
Creating strong passwords involves incorporating a variety of characters to make them difficult to guess or crack. Avoid using easily guessable information like birthdays, pet names, or common words. Instead, aim for passwords that are at least 12 characters long, and include a mix of uppercase and lowercase letters, numbers, and symbols. Consider using a passphrase – a memorable phrase – as a base, then modifying it with substitutions and additions to make it even stronger.
For example, “MyFavoriteDogIsFluffy123!” is stronger than “password123”.
Password Management Best Practices
Managing numerous unique and complex passwords can be challenging. Password managers are invaluable tools that generate, store, and manage your passwords securely. These applications encrypt your passwords, protecting them even if your device is compromised. Reputable password managers offer features like autofill, which simplifies the login process, and security alerts, notifying you of potential breaches affecting your accounts.
Choose a reputable password manager and enable its security features, such as two-factor authentication for the password manager itself.
Multi-Factor Authentication (MFA) Implementation
Multi-factor authentication (MFA) adds an extra layer of security by requiring more than just a password to access your accounts. Even if a hacker obtains your password, they’ll still need access to a second factor, such as a code from your phone or a security key, to gain entry. Implementing MFA across all your important accounts – email, banking, social media, etc.
– significantly reduces the risk of unauthorized access.
Comparison of MFA Methods
Various MFA methods offer different levels of security and convenience. The best choice depends on your specific needs and risk tolerance.
| Method | Security Level | Convenience | Cost |
|---|---|---|---|
| Time-Based One-Time Password (TOTP) | High | Medium | Low (often free through app) |
| Biometrics (fingerprint, facial recognition) | Medium to High | High | Low (often built into devices) |
| Security Keys (U2F, FIDO2) | Very High | Medium | Low to Medium (depending on key type) |
| SMS Codes | Low to Medium | High | Low (usually included in phone plans) |
Software Updates and Security Patches

Outdated software is a gaping hole in your digital defenses. Think of it like leaving your front door unlocked – it’s an open invitation for trouble. Cybercriminals constantly scan for vulnerabilities in older software, using them to gain access to your personal information, steal your data, or even take control of your devices. Keeping your software up-to-date is a fundamental step in bolstering your online security.Software updates aren’t just about adding new features; they’re crucial for patching security flaws.
These flaws, often called vulnerabilities, are weaknesses in the software’s code that malicious actors can exploit. Neglecting updates leaves your system exposed to attacks like malware infections, data breaches, and ransomware. For example, the WannaCry ransomware attack in 2017 crippled hospitals and businesses worldwide because many systems were running outdated versions of Windows, failing to patch a known vulnerability.
Similarly, the Equifax data breach in 2017, which exposed the personal information of millions, was partly attributed to the company’s failure to promptly patch a known vulnerability in its Apache Struts software.
Automatic Update Mechanisms
Enabling automatic updates is the simplest and most effective way to ensure your software is always current. This eliminates the need for manual checks and installations, which many people often forget to do. The process varies slightly depending on the software, but the general principle is the same.For your operating system (e.g., Windows, macOS, Linux), navigate to the system settings or preferences.
Look for an option related to “Updates,” “Software Update,” or “Windows Update.” Typically, you can select an option to automatically download and install updates, or schedule updates for a specific time. Some systems offer options for choosing whether to automatically restart your computer after updates are installed.For other applications like web browsers (Chrome, Firefox, Safari, Edge), antivirus software (Norton, McAfee, Bitdefender), and other frequently used programs, the update mechanism is usually built-in.
So, you want to be a tougher nut to crack for cybercriminals? Four ways to boost your security include strong passwords, regular software updates, being wary of phishing scams, and using multi-factor authentication. Understanding the bigger picture of cloud security is crucial too, which is why I’ve been diving into the world of cloud security solutions like learning about bitglass and the rise of cloud security posture management ; it really helps put things into perspective.
Ultimately, combining personal vigilance with robust cloud security strategies is the best way to stay protected.
Check the application’s settings or menu. There’s often a section dedicated to “Updates,” “Check for Updates,” or “About.” Clicking this will usually initiate a check for available updates and prompt you to install them. Many applications will automatically download updates in the background, requiring only a quick confirmation or restart to complete the installation.
Software Requiring Regular Updates
Regular updates are essential for a variety of software. Failing to update leaves significant security gaps.
- Operating System (Windows, macOS, Linux)
- Web Browser (Chrome, Firefox, Safari, Edge)
- Antivirus Software (Norton, McAfee, Bitdefender, etc.)
- Office Suites (Microsoft Office, LibreOffice, Google Workspace)
- PDF Readers (Adobe Acrobat Reader)
- Java Runtime Environment (JRE)
- Flash Player (though increasingly less relevant due to its end-of-life)
Safe Browsing Habits and Phishing Awareness: Four Ways To Make Yourself A Harder Target For Cybercriminals
Navigating the digital world safely requires a proactive approach to security. Understanding and avoiding phishing attempts is crucial to protecting your personal information and online accounts. Phishing is a type of cyberattack where malicious actors try to trick you into revealing sensitive data like passwords, credit card numbers, or social security numbers. This is often done through deceptive emails, websites, or messages.
Let’s explore how to identify and avoid these threats.
Phishing Techniques and Examples
Phishing attacks utilize various techniques to deceive users. A common tactic is to impersonate legitimate organizations, such as banks, online retailers, or social media platforms. These fraudulent communications often create a sense of urgency, claiming there’s a problem with your account or a need for immediate action. For example, a phishing email might mimic a notification from your bank, warning of suspicious activity and prompting you to click a link to verify your account details.
Another example could be a fraudulent email appearing to come from a popular online retailer, offering an enticing discount or refund, but leading to a fake login page. These emails often contain grammatical errors, misspellings, or inconsistencies in branding, which can be red flags.
So, you want to be a tougher nut to crack for online creeps? Four ways to up your security game include strong passwords, two-factor authentication, regular software updates, and being super wary of phishing attempts. Seriously, don’t fall for scams like the one described in this article about facebook asking bank account info and card transactions of users , which highlights how easily personal info can be stolen.
Remember those four tips and you’ll be much safer online!
Identifying Suspicious Emails, Websites, and Links, Four ways to make yourself a harder target for cybercriminals
Several key indicators can help you identify suspicious emails, websites, and links. First, carefully examine the sender’s email address. Legitimate organizations typically use professional-looking email addresses that match their domain name. Be wary of emails from unfamiliar addresses or those with unusual characters or misspellings. Second, hover your mouse over links before clicking them.
This will reveal the actual URL destination in the bottom left corner of your browser window. If the link looks suspicious or doesn’t match the expected website, do not click it. Third, scrutinize the website’s security certificate. Look for a padlock icon in the address bar, indicating a secure HTTPS connection. Fourth, check the website’s design and content for inconsistencies.
Legitimate websites usually have professional-looking designs and accurate information. Finally, be cautious of websites that request excessive personal information.
So, you want to beef up your cybersecurity? Four ways to make yourself a harder target include strong passwords, two-factor authentication, regular software updates, and being mindful of phishing scams. Thinking about app development security? Check out this insightful article on domino app dev the low code and pro code future which touches upon secure coding practices.
Ultimately, remember that robust security is a multifaceted approach, covering everything from your personal habits to the apps you use.
Verifying Website Authenticity
Before entering any personal information on a website, it’s crucial to verify its authenticity. Start by checking the website’s URL carefully. Look for common misspellings or slight variations from the legitimate website’s address. Next, research the website independently. Search for the company’s name and website address online to see if you can find any information about its legitimacy.
Look for reviews, contact information, and other indicators of authenticity. If you’re unsure, contact the organization directly through a known and verified contact method, such as a phone number listed on their official website, to confirm the website’s authenticity before proceeding.
Avoiding Social Engineering Tactics
Social engineering involves manipulating individuals into divulging confidential information or performing actions that compromise security. These tactics often exploit human psychology, such as creating a sense of urgency or trust. To avoid social engineering, be skeptical of unsolicited requests for personal information, verify the identity of anyone requesting sensitive data, and never feel pressured to act quickly without due consideration.
Think before you click, and if something feels off, it probably is.
Red Flags Indicating a Potential Phishing Attempt
Several red flags can indicate a potential phishing attempt. Here’s a list of common indicators:
- Urgent or threatening language demanding immediate action.
- Generic greetings (e.g., “Dear Customer” instead of your name).
- Suspicious email addresses or links.
- Grammatical errors and poor spelling.
- Requests for personal information (passwords, credit card details, etc.).
- Suspicious attachments or links.
- Unusual or unexpected emails from unfamiliar senders.
- Website design inconsistencies or lack of security indicators (HTTPS).
- Unusually high discounts or promotions.
- Threats to close accounts or cancel services.
Anatomy of a Phishing Email
Imagine a phishing email. The header shows a seemingly legitimate sender’s name and address, often mimicking a known brand. The subject line creates a sense of urgency, such as “Urgent Security Alert!” or “Your Account Has Been Compromised!”. The body of the email contains a compelling narrative, often including a false sense of urgency or a tempting offer.
It might contain grammatical errors and misspellings. Crucially, it includes a malicious link, often disguised to appear legitimate. This link, when clicked, redirects the user to a fake website designed to steal their information. The footer may contain disclaimers or contact information that is either vague or inconsistent with the sender’s supposed identity. The overall impression is designed to be convincing but subtly flawed upon closer inspection.
Secure Network Practices and Data Protection
Protecting your data starts with securing the networks you use. A robust network security strategy is crucial in preventing cybercriminals from accessing your sensitive information. This involves understanding the risks associated with different network environments and implementing appropriate protective measures.The security of your home and public Wi-Fi networks is paramount. Weak or unsecured networks are easily exploited by malicious actors, allowing them to intercept your data and potentially install malware on your devices.
Similarly, public Wi-Fi hotspots, often found in cafes, airports, and hotels, are notorious for their lack of security and increased vulnerability to attacks.
Strong Home Wi-Fi Security
Securing your home Wi-Fi network involves several key steps. First, choose a strong and unique password, ideally employing a combination of uppercase and lowercase letters, numbers, and symbols. Enable WPA3 encryption, the most secure protocol currently available, to protect your data transmitted over the network. Regularly change your password and consider using a strong passphrase instead of a simple password.
Furthermore, regularly update your router’s firmware to patch security vulnerabilities. A firewall, built into most routers, should be enabled to block unauthorized access attempts. Finally, regularly check your router’s logs to detect any unusual activity. A strong, well-maintained home network acts as the first line of defense against many cyber threats.
VPN Usage for Enhanced Privacy and Security
A Virtual Private Network (VPN) creates an encrypted connection between your device and the internet. This encryption masks your IP address and encrypts your data, making it much harder for hackers or your internet service provider to monitor your online activity. VPNs are particularly useful when using public Wi-Fi, as they provide an extra layer of security against eavesdropping.
Different VPN providers offer varying levels of security and privacy features, including encryption protocols (like OpenVPN or WireGuard), server locations, and no-logs policies. Some providers are more expensive than others, reflecting differences in their server infrastructure, features, and security guarantees. For example, ExpressVPN is known for its strong security and fast speeds but comes at a higher price point than ProtonVPN, which prioritizes privacy and open-source software.
The choice of VPN depends on individual needs and priorities.
Data Protection Measures: Encryption and Backups
Protecting your data involves employing both preventative and recovery strategies. Encryption transforms your data into an unreadable format, protecting it even if it’s intercepted. Full-disk encryption, for example, protects all data on your computer’s hard drive. File encryption protects individual files. Regular data backups are essential for data recovery in case of accidental deletion, hardware failure, or ransomware attacks.
Backups should be stored securely, ideally in a separate location (cloud storage or external hard drive) to protect against physical damage or theft. Using a combination of encryption and regular backups significantly reduces the risk of data loss and ensures business continuity.
Public Wi-Fi Risks and Mitigation Strategies
Using public Wi-Fi networks exposes you to several risks. These networks are often unsecured, allowing hackers to intercept your data. Malicious hotspots, designed to mimic legitimate networks, can also steal your credentials. To mitigate these risks, avoid accessing sensitive information (banking, emails) on public Wi-Fi. Always use a VPN to encrypt your data and mask your IP address.
Be cautious of websites that ask for personal information on unsecured networks. Consider using a mobile hotspot from your phone for a more secure connection if possible. It’s crucial to remain vigilant and avoid engaging in activities that require high security on public Wi-Fi.
Securing Your Home Network: A Flowchart
The following flowchart Artikels the steps to secure a home network:[Imagine a flowchart here. It would start with a box labeled “Start,” then branch to boxes for “Choose a strong password,” “Enable WPA3 encryption,” “Update router firmware,” “Enable firewall,” “Regularly check router logs,” and finally end with a box labeled “Secure Home Network.”] Each box would have arrows connecting it to the next step in the process.
This visual representation clearly shows the sequential steps involved in setting up a secure home network.
Concluding Remarks
So, there you have it – four practical steps to fortify your digital defenses. Remember, online security is an ongoing process, not a one-time fix. Regularly reviewing your passwords, updating your software, and staying vigilant against phishing attempts are key to staying ahead of the curve. By adopting these habits, you’ll not only protect your personal information but also enjoy greater peace of mind knowing you’re taking proactive steps to safeguard yourself in the digital world.
Stay safe out there!
Frequently Asked Questions
What’s a password manager, and why should I use one?
A password manager is a tool that securely stores and manages all your online passwords. It generates strong, unique passwords for each account and automatically fills them in, eliminating the need to remember complex strings. This significantly reduces your risk of password reuse and improves overall security.
How often should I update my software?
Ideally, enable automatic updates whenever possible. However, at minimum, check for and install updates at least once a month for your operating system, web browser, and antivirus software.
What are some telltale signs of a phishing email?
Look for grammatical errors, suspicious links (hover over them to see the actual URL), urgent requests for personal information, and emails from unknown senders. If something feels off, don’t click anything!
Is a VPN really necessary?
A VPN (Virtual Private Network) encrypts your internet traffic, making it harder for others to snoop on your activity, especially on public Wi-Fi. While not strictly necessary for everyone, it’s highly recommended for anyone who regularly uses public Wi-Fi or handles sensitive information online.