Future-Proof Your Real-Time Apps Model Realtime 12.1
Future proof your real time application development introducing model realtime 12.1 – Future-Proof Your Real-Time Application Development Introducing Model Realtime 12.1 – sounds like a mouthful, right? But it’s actually the key to building apps that not only work flawlessly today but also stand the test of time. This post dives into the exciting new features of Model Realtime 12.1 and how they help you create robust, scalable, and secure real-time applications.
We’ll explore future-proofing strategies, security considerations, performance optimization, and integration with cutting-edge technologies. Get ready to level up your real-time development game!
We’ll be looking at everything from architectural best practices to minimize latency and maximize scalability, to the latest security protocols to protect your data. Think of this as your ultimate guide to building real-time applications that are not just fast and efficient, but also adaptable and resilient to the ever-changing technological landscape. We’ll even tackle the often-overlooked aspects like testing, deployment, and ongoing maintenance.
Introduction to Real-Time Application Development and Model Realtime 12.1
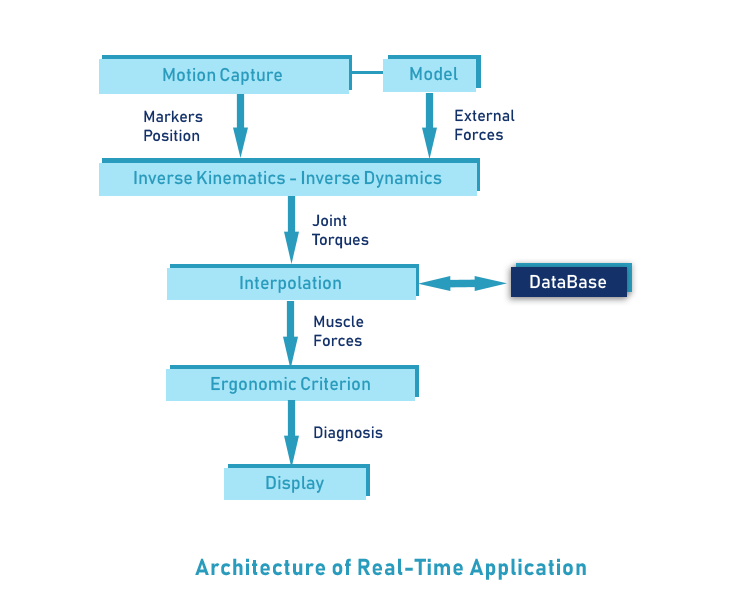
Real-time application development is a fascinating field focused on creating software that responds to events within strict time constraints. Unlike typical applications where slight delays are acceptable, real-time systems demand immediate and predictable responses. This is crucial in areas like industrial automation, robotics, and financial trading, where even minor delays can have significant consequences. Model Realtime 12.1 represents a significant leap forward in this critical area.
Core Principles of Real-Time Application Development
Real-time systems adhere to specific principles to guarantee timely responses. Determinism, the ability to predict the execution time of tasks, is paramount. This requires careful resource management and scheduling algorithms. Another key aspect is concurrency, the ability to handle multiple tasks simultaneously, often using techniques like multithreading or multiprocessing. Finally, robustness and fault tolerance are essential; real-time systems must be able to handle unexpected events and continue functioning correctly, even under stress.
These principles ensure the reliability and predictability necessary for mission-critical applications.
Key Features and Improvements in Model Realtime 12.1
Model Realtime 12.1 boasts several enhancements over its predecessors. Improved scheduling algorithms offer more precise control over task execution, leading to reduced latency and jitter. Enhanced debugging tools provide developers with more comprehensive insights into system behavior, simplifying the process of identifying and resolving performance bottlenecks. The new version also includes improved support for distributed systems, enabling the creation of more scalable and robust real-time applications across multiple machines.
Furthermore, Model Realtime 12.1 offers enhanced security features, protecting sensitive data and system integrity.
Comparison of Model Realtime 12.1 to Previous Versions
Model Realtime 12.1 builds upon the strengths of earlier versions while addressing limitations. Previous versions, while functional, often lacked the advanced scheduling capabilities and debugging tools found in 12.1. The improved support for distributed systems is a major advancement, allowing for the creation of far more complex and geographically dispersed real-time applications. The enhanced security features are also a critical improvement, addressing the growing concerns about the security of real-time systems.
The overall performance improvements in 12.1, particularly in terms of reduced latency and jitter, make it a compelling upgrade for existing users.
Comparison of Real-Time Application Frameworks
The following table compares three popular real-time application frameworks: Model Realtime 12.1, FreeRTOS, and VxWorks. Each framework has its own strengths and weaknesses, making the choice dependent on the specific requirements of the application.
| Framework | Licensing | Real-time Capabilities | Ease of Use |
|---|---|---|---|
| Model Realtime 12.1 | Commercial | Advanced scheduling, low latency, high determinism | Moderate (requires specific expertise) |
| FreeRTOS | Open Source (GPL) | Good real-time capabilities, widely used | Relatively easy to learn and use |
| VxWorks | Commercial | High-performance real-time capabilities, suitable for demanding applications | Steeper learning curve, more complex |
Future-Proofing Strategies for Real-Time Applications

Building real-time applications is challenging enough, but ensuring they remain relevant and performant in the face of rapid technological advancements requires a proactive, future-proof approach. This means anticipating and adapting to emerging trends, adopting robust architectural patterns, and investing in scalable infrastructure. Ignoring these factors can lead to costly refactoring, system instability, and ultimately, application obsolescence.
Technological Trends Impacting Real-Time Application Development
Three major technological trends significantly influence the development and longevity of real-time applications. Understanding these trends is crucial for effective future-proofing.
- The Rise of Edge Computing: Processing data closer to its source (the “edge”) reduces latency and bandwidth consumption, crucial for real-time applications demanding immediate responses. This trend is evident in autonomous vehicles, where real-time decisions are made on-board, and in industrial IoT deployments requiring immediate feedback control. Edge computing necessitates architectural changes to distribute processing and data management.
- The Prevalence of Microservices Architecture: Breaking down monolithic applications into smaller, independent services improves scalability, maintainability, and resilience. This approach is particularly beneficial for real-time applications, allowing for independent scaling of individual components based on demand. Examples include financial trading platforms where different services handle order processing, risk management, and reporting independently.
- The Expansion of Serverless Computing: Serverless architectures abstract away server management, allowing developers to focus on code. This approach is cost-effective and scalable, particularly suited for real-time applications with fluctuating workloads. Examples include event-driven systems processing real-time sensor data, where resources are only consumed during actual event processing.
Challenges of Maintaining Real-Time Applications
Maintaining real-time applications in a dynamic technological environment presents several significant challenges.The need for continuous updates and upgrades to support new hardware, software, and protocols is a constant pressure. Furthermore, ensuring backward compatibility while integrating new features and technologies requires careful planning and execution. Legacy systems may pose integration challenges, requiring substantial refactoring efforts. Security vulnerabilities must be constantly addressed, demanding proactive security measures and regular penetration testing.
Finally, the ever-increasing volume of data generated by real-time applications requires sophisticated data management strategies to ensure performance and efficiency.
Architectural Patterns for Enhanced Longevity
Employing specific architectural patterns significantly enhances the longevity of real-time systems.
- Event-Driven Architecture: This pattern allows for loose coupling between components, making it easier to adapt to changes and integrate new technologies. Events are used to trigger actions, enabling asynchronous communication and improving system responsiveness. This is particularly relevant for high-volume, real-time data streams.
- Message Queues: Using message queues decouples components, allowing for asynchronous communication and improved resilience. Messages are stored in a queue, ensuring that even if a component is unavailable, the message is not lost. This pattern improves scalability and fault tolerance.
- Reactive Programming: Reactive programming models deal with asynchronous data streams effectively. It provides a declarative approach to handling events, making it easier to manage complexity and improve system responsiveness. This approach is well-suited for real-time applications dealing with high-velocity data streams.
Scalable Infrastructure for Future-Proof Applications
Scalable infrastructure is paramount for future-proof real-time applications. Applications must be capable of handling increasing workloads and data volumes without compromising performance.Cloud-based solutions offer inherent scalability, allowing for on-demand resource allocation. Auto-scaling features automatically adjust resources based on demand, ensuring optimal performance and cost-efficiency. Employing containerization technologies like Docker and Kubernetes enables efficient deployment and management of applications across various environments.
Database selection is also critical; choosing a database technology capable of handling high-throughput, low-latency operations is essential for maintaining real-time performance. For example, NoSQL databases are often preferred over relational databases for high-volume, real-time data.
Security Considerations in Real-Time Application Development
Building secure real-time applications is paramount, especially given the often sensitive nature of the data they handle and their continuous operation. A breach in a real-time system can have far-reaching and immediate consequences, impacting everything from financial transactions to critical infrastructure control. Model Realtime 12.1, with its focus on speed and efficiency, requires a robust security strategy to prevent exploitation.Real-time applications, by their very nature, demand a different approach to security than traditional applications.
The constant flow of data and the need for low latency introduce unique challenges. A layered security approach, combining multiple strategies, is essential for mitigating risks effectively. This involves careful consideration of the application architecture, data protection mechanisms, and robust access control policies.
Designing a Secure Architecture for Real-Time Applications using Model Realtime 12.1
A secure architecture for a real-time application built using Model Realtime 12.1 begins with a principle of least privilege. This means granting only the necessary permissions to each component of the system. Microservices architecture can be beneficial here, allowing for independent security management of individual services. Furthermore, secure communication channels, such as TLS/SSL, are crucial for protecting data in transit.
Data at rest should be encrypted using strong encryption algorithms, and regular security audits and penetration testing should be part of the development lifecycle. Employing a robust logging and monitoring system enables timely detection and response to security incidents. The use of containerization and orchestration technologies, such as Docker and Kubernetes, can enhance security by providing isolation and control over application deployments.
Best Practices for Data Protection and Access Control in Real-Time Environments
Data protection in real-time applications necessitates a multi-faceted strategy. This includes implementing strong authentication mechanisms, such as multi-factor authentication (MFA), to verify user identities. Authorization controls, using role-based access control (RBAC) or attribute-based access control (ABAC), are essential for restricting access to sensitive data based on user roles or attributes. Data encryption, both in transit and at rest, is a cornerstone of data protection.
Regular security updates and patching of the underlying infrastructure and application components are vital to address known vulnerabilities. Input validation and sanitization are crucial to prevent injection attacks. Finally, implementing data loss prevention (DLP) mechanisms helps prevent sensitive data from leaving the system unintentionally.
Potential Vulnerabilities and Mitigation Strategies for Real-Time Applications
Real-time applications are susceptible to various vulnerabilities. Denial-of-service (DoS) attacks can overwhelm the system, rendering it unavailable. Injection attacks, such as SQL injection or cross-site scripting (XSS), can compromise data integrity and system security. Man-in-the-middle (MitM) attacks can intercept communication between components. Improper error handling can expose sensitive information.
Race conditions and timing attacks can exploit vulnerabilities in concurrent processes. Mitigation strategies include implementing rate limiting and intrusion detection systems to prevent DoS attacks; robust input validation and output encoding to prevent injection attacks; secure communication protocols to prevent MitM attacks; comprehensive error handling and logging; and careful design and testing to avoid race conditions.
Security Considerations Specific to Model Realtime 12.1
- Secure Configuration: Model Realtime 12.1’s configuration files should be protected and accessed only by authorized personnel. Incorrect configuration can expose vulnerabilities.
- Authentication and Authorization: Implement robust authentication and authorization mechanisms, integrating with existing security infrastructure wherever possible.
- Data Integrity: Utilize checksums or digital signatures to verify data integrity during transmission and storage.
- Resource Management: Proper resource management is crucial to prevent resource exhaustion attacks that could lead to system instability.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and address potential vulnerabilities proactively.
- Compliance: Ensure compliance with relevant industry regulations and standards, such as HIPAA or PCI DSS, depending on the application’s purpose.
Performance Optimization Techniques
Real-time application development demands meticulous attention to performance. Even minor delays can significantly impact user experience and the overall system’s effectiveness. Optimizing database interactions, minimizing communication latency, and employing efficient code are crucial for building robust and responsive real-time applications using Model Realtime 12.1. This section delves into key strategies to achieve optimal performance.
Database Interaction Optimization
Efficient database interactions are paramount for real-time performance. Excessive database queries can lead to bottlenecks and slow response times. To mitigate this, several techniques can be employed. First, consider using caching mechanisms to store frequently accessed data in memory, reducing the load on the database. Second, optimize database queries themselves.
This involves using appropriate indexes, avoiding unnecessary joins, and leveraging database features like stored procedures for frequently executed operations. Third, employ connection pooling to reuse database connections, minimizing the overhead of establishing new connections for each request. Finally, consider using asynchronous database operations to prevent blocking operations and maintain responsiveness. For instance, instead of waiting for a database query to complete before proceeding, you can initiate the query and continue processing other tasks, handling the query’s result later.
Minimizing Latency in Real-Time Communication
Latency, the delay between sending and receiving data, is a critical factor in real-time applications. Minimizing latency requires a multi-pronged approach. Choosing the right communication protocol is essential. WebSockets, for example, provide a persistent connection, minimizing the overhead associated with establishing new connections for each message. Furthermore, data compression techniques can reduce the size of messages transmitted, thereby reducing transmission time.
Efficient data serialization formats, like Protocol Buffers or Avro, can also contribute significantly. Careful selection of server infrastructure, including proximity to users and efficient network configuration, is equally vital. Finally, consider using techniques like message batching to group multiple messages into a single transmission, reducing the number of network round trips.
Code Optimization Strategies in Model Realtime 12.1
Model Realtime 12.1 offers several features that aid in code optimization. One key aspect is its support for asynchronous programming. Asynchronous operations allow concurrent execution of multiple tasks without blocking the main thread, improving responsiveness. For example, using asynchronous I/O operations for network communication or database access prevents the application from freezing while waiting for these operations to complete.
Another important aspect is efficient memory management. Avoiding memory leaks and using appropriate data structures can significantly impact performance. Model Realtime 12.1 provides tools and features for monitoring memory usage, allowing developers to identify and address memory-related performance bottlenecks. Finally, profiling tools within Model Realtime 12.1 can pinpoint performance hotspots in your code, allowing targeted optimization efforts.
This allows developers to identify sections of code that consume the most resources and focus their optimization efforts on those specific areas.
Load Balancing Approaches in Real-Time Systems
Load balancing is crucial for distributing the workload across multiple servers in a real-time system, ensuring high availability and responsiveness. Several approaches exist, each with its strengths and weaknesses.
| Load Balancing Approach | Description | Advantages | Disadvantages |
|---|---|---|---|
| Round Robin | Distributes requests sequentially to each server. | Simple to implement. | Doesn’t account for server load differences. |
| Least Connections | Directs requests to the server with the fewest active connections. | Effectively handles varying server loads. | Requires monitoring of server connections. |
| Weighted Round Robin | Distributes requests based on server capacity. | Allows prioritizing servers with higher capacity. | Requires careful configuration of weights. |
| IP Hashing | Distributes requests based on the client’s IP address. | Ensures consistent server assignment for a given client. | Less effective in handling uneven server loads. |
Testing and Deployment Strategies for Real-Time Applications
Building and deploying a robust real-time application using Model Realtime 12.1 requires a meticulous approach to testing and deployment. Ignoring these crucial phases can lead to significant performance issues, instability, and ultimately, application failure. A well-defined strategy ensures the application meets its stringent real-time constraints and delivers a reliable user experience.
Comprehensive Testing Strategy for Real-Time Applications
Testing a real-time application differs significantly from testing traditional applications. The focus shifts from functional correctness to verifying timing constraints, resource utilization, and responsiveness under various load conditions. A multi-faceted approach is necessary to guarantee reliability and performance. This involves unit testing individual components, integration testing the interaction between components, and system testing the entire application under realistic scenarios.
Furthermore, performance testing, stress testing, and load testing are crucial to identify bottlenecks and ensure the application can handle expected and unexpected surges in activity. Finally, rigorous testing of the application’s security features is paramount.
Challenges of Deploying and Managing Real-Time Applications in Production
Deploying real-time applications presents unique challenges. Maintaining low latency and high availability demands careful consideration of infrastructure, network configuration, and deployment methodologies. The need for continuous monitoring and rapid response to potential issues requires dedicated tools and expertise. Furthermore, scaling real-time applications to accommodate growing user bases and data volumes necessitates a scalable architecture and efficient resource management strategies.
Unexpected spikes in activity can overwhelm systems, highlighting the need for robust failover mechanisms and disaster recovery plans. Finally, ensuring security in a production environment is critical, requiring constant vigilance against potential threats and vulnerabilities.
Best Practices for Monitoring and Maintaining Real-Time System Performance
Continuous monitoring is essential for maintaining the performance of real-time systems. Key metrics to track include latency, throughput, resource utilization (CPU, memory, network), and error rates. Real-time dashboards provide immediate visibility into system health and allow for prompt identification and resolution of performance issues. Automated alerts based on predefined thresholds enable proactive intervention, preventing minor issues from escalating into major outages.
Regular performance testing under simulated load conditions helps identify potential bottlenecks and areas for optimization. Furthermore, detailed logging and tracing mechanisms are crucial for diagnosing and resolving complex issues. Finally, implementing a robust change management process minimizes the risk of introducing new bugs or performance regressions during updates and deployments.
Step-by-Step Guide for Deploying a Real-Time Application Using Model Realtime 12.1
Deploying a real-time application using Model Realtime 12.1 involves several key steps. Careful planning and execution are crucial to ensure a smooth and successful deployment.
- Prepare the Deployment Environment: This involves setting up the necessary hardware and software infrastructure, including servers, network devices, and any required middleware. Configuration of the environment should adhere to best practices for real-time systems, including network optimization and resource allocation.
- Build and Package the Application: Model Realtime 12.1 provides tools to build and package the application for deployment. This process involves compiling the code, linking libraries, and creating a deployable artifact. The packaging process should be optimized for minimal size and efficient loading.
- Deploy the Application: The deployment process involves transferring the packaged application to the target environment and initiating the application. Model Realtime 12.1 may offer specific deployment tools and methodologies. This stage often involves careful consideration of the deployment strategy (e.g., rolling updates, blue-green deployments) to minimize downtime and disruption.
- Configure Monitoring and Logging: Integrate monitoring and logging tools to track key performance metrics and system events. This allows for proactive identification and resolution of issues. Effective logging provides valuable data for debugging and performance analysis.
- Test and Validate: After deployment, conduct thorough testing to validate the application’s functionality and performance in the production environment. This involves verifying that the application meets its real-time constraints and that all features are working as expected.
Integration with Emerging Technologies
Model Realtime 12.1, with its robust real-time capabilities, offers a powerful foundation for building next-generation applications. Seamless integration with emerging technologies is key to unlocking its full potential and creating truly future-proof solutions. This section explores the synergistic benefits of combining Model Realtime 12.1 with cloud platforms, AI/ML, IoT, and edge computing.Integrating Model Realtime 12.1 with these technologies allows developers to create applications that are scalable, intelligent, and responsive to the demands of a rapidly evolving digital landscape.
The possibilities are vast, spanning from autonomous vehicles and industrial automation to smart cities and personalized healthcare.
Cloud Platform Integration
Leveraging cloud platforms significantly enhances the scalability and resilience of real-time applications built using Model Realtime 12.1. Cloud services provide on-demand resources, allowing applications to handle fluctuating workloads efficiently. This eliminates the need for significant upfront investment in hardware and reduces the complexity of managing infrastructure. Moreover, cloud platforms offer geographically distributed data centers, ensuring low latency for users across different regions.
AI and Machine Learning Integration
The integration of AI and machine learning (ML) capabilities into real-time applications developed with Model Realtime 12.1 unlocks powerful new functionalities. Real-time data streams can be fed into ML models for immediate analysis and prediction, enabling proactive responses to changing conditions. For instance, in a manufacturing setting, real-time sensor data analyzed by an ML model could predict equipment failure before it occurs, minimizing downtime and preventing costly repairs.
Similarly, in a financial application, real-time market data could be used to trigger automated trades based on predictive models.
IoT and Edge Computing Integration
Model Realtime 12.1’s ability to handle high-volume, low-latency data streams makes it ideally suited for integration with IoT devices and edge computing. This allows for the processing of data closer to its source, reducing latency and bandwidth requirements. Imagine a smart city application where real-time data from traffic sensors is processed at the edge, enabling immediate adjustments to traffic light timings to optimize traffic flow.
This kind of responsiveness is critical for many real-time applications. The integration of edge computing also improves the resilience of the system, as processing is not solely reliant on a central cloud server.
Integrating Model Realtime 12.1 with AWS
- Data Transfer: Utilize AWS Kinesis or other similar services to stream real-time data from Model Realtime 12.1 to the cloud for further processing and storage. This allows for scalable and reliable data ingestion.
- Serverless Computing: Deploy Model Realtime 12.1 components as AWS Lambda functions to process data asynchronously and scale on demand. This reduces operational overhead and cost.
- Database Integration: Integrate with AWS services like Amazon DynamoDB or Amazon RDS for persistent storage of real-time data. This enables historical analysis and reporting.
- Monitoring and Logging: Leverage AWS CloudWatch to monitor the performance and health of the Model Realtime 12.1 application deployed on AWS. This ensures system stability and enables proactive issue resolution.
Case Studies of Successful Real-Time Applications
Real-time applications are the backbone of many modern systems, impacting everything from finance to healthcare. Understanding their successes provides valuable insights for future development. This section delves into a specific example, examining its architecture, development process, challenges, and key success factors.
Air Traffic Control Systems
Air traffic control systems are a prime example of a mission-critical real-time application. These systems require incredibly low latency and high reliability to ensure the safe and efficient movement of aircraft. Failure is not an option.
System Architecture, Future proof your real time application development introducing model realtime 12.1
The architecture of a modern air traffic control system is complex and distributed. A simplified representation would show several key components:
Imagine a diagram. At the center is a large, centralized server cluster (the “Core System”). This cluster handles the primary functions of tracking aircraft, managing airspace, and communicating with air traffic controllers. Radiating outwards from this core are several smaller systems. These include: Radar systems (feeding real-time location data), communication systems (voice and data links with aircraft), and display systems (providing controllers with a visual representation of the airspace).
Each of these smaller systems connects to the core system via high-speed, redundant networks, ensuring high availability and fault tolerance. The entire system is designed for modularity, allowing for upgrades and expansion without disrupting operations. Data flows constantly between these components, with the core system acting as the central hub. The entire system is highly redundant, with backups and failover mechanisms in place to ensure continuous operation.
Development Process and Challenges
Developing such a system is an immense undertaking, requiring highly specialized expertise in software engineering, networking, and air traffic control procedures. The development process typically follows a rigorous, iterative approach, with extensive testing and validation at each stage. Challenges include: maintaining data consistency across the distributed system, ensuring real-time performance under heavy load, and complying with stringent safety and security regulations.
The integration of legacy systems with newer technologies also presents significant challenges. Furthermore, continuous updates and maintenance are crucial to address evolving airspace management requirements and technological advancements.
Factors Contributing to Success
The success of air traffic control systems relies on several key factors: robust architecture, rigorous testing, continuous monitoring, and a highly skilled workforce. The modular design allows for incremental improvements and upgrades without requiring a complete system overhaul. Redundancy ensures high availability and fault tolerance, crucial for a system where even brief outages can have severe consequences.
Strict adherence to safety and security standards is paramount, ensuring the safety of passengers and crew. Finally, continuous investment in research and development is essential to keep pace with technological advancements and maintain a high level of performance and reliability.
Ultimate Conclusion: Future Proof Your Real Time Application Development Introducing Model Realtime 12.1
Building truly future-proof real-time applications requires a proactive approach, encompassing robust architecture, proactive security measures, and continuous optimization. Model Realtime 12.1 provides a solid foundation, but mastering the strategies discussed here – from choosing the right architectural patterns to integrating emerging technologies – will be your key to success. By embracing these techniques, you’ll create applications not only capable of meeting today’s demands but also equipped to thrive in the ever-evolving world of real-time technology.
Ready to get started?
Common Queries
What are the biggest challenges in maintaining real-time applications?
Maintaining real-time applications is tricky because of constant technological advancements, scaling issues as user base grows, and the need for continuous security updates to prevent vulnerabilities.
How does Model Realtime 12.1 improve upon previous versions?
Model Realtime 12.1 typically boasts enhanced performance, improved security features, better scalability options, and often includes new features or integrations with other technologies.
What’s the best way to test a real-time application?
Testing real-time applications needs a multi-faceted approach including unit tests, integration tests, performance tests under load, and rigorous security testing.
Is Model Realtime 12.1 suitable for all types of real-time applications?
While versatile, the suitability of Model Realtime 12.1 depends on specific application requirements. Factors like scalability needs, security sensitivity, and integration requirements will influence the choice.