Future-Proofing Cybersecurity Automations Speed Advantage
Future proofing cybersecurity at the speed of threats with automation – Future-proofing cybersecurity at the speed of threats with automation is no longer a luxury; it’s a necessity. Cyberattacks are evolving at an alarming rate, becoming more sophisticated and frequent. Automation isn’t just speeding up attacks, it’s also offering a powerful defense. This post dives into how we can leverage automation to build resilient, adaptable cybersecurity strategies that can keep pace with – and even outpace – the ever-changing threat landscape.
We’ll explore the technologies, strategies, and ethical considerations involved in this crucial shift.
Think of it like this: the bad guys are using automation to break in faster and smarter, so we need to use it to defend even faster and smarter. This means integrating automated systems like SIEM, SOAR, and AI-powered tools into our security infrastructure, but also understanding the crucial role of human oversight and the importance of training our workforce to effectively manage these complex systems.
We’ll cover everything from building a step-by-step implementation plan to addressing the ethical considerations of using AI in cybersecurity. Get ready to future-proof your defenses!
The Evolving Threat Landscape
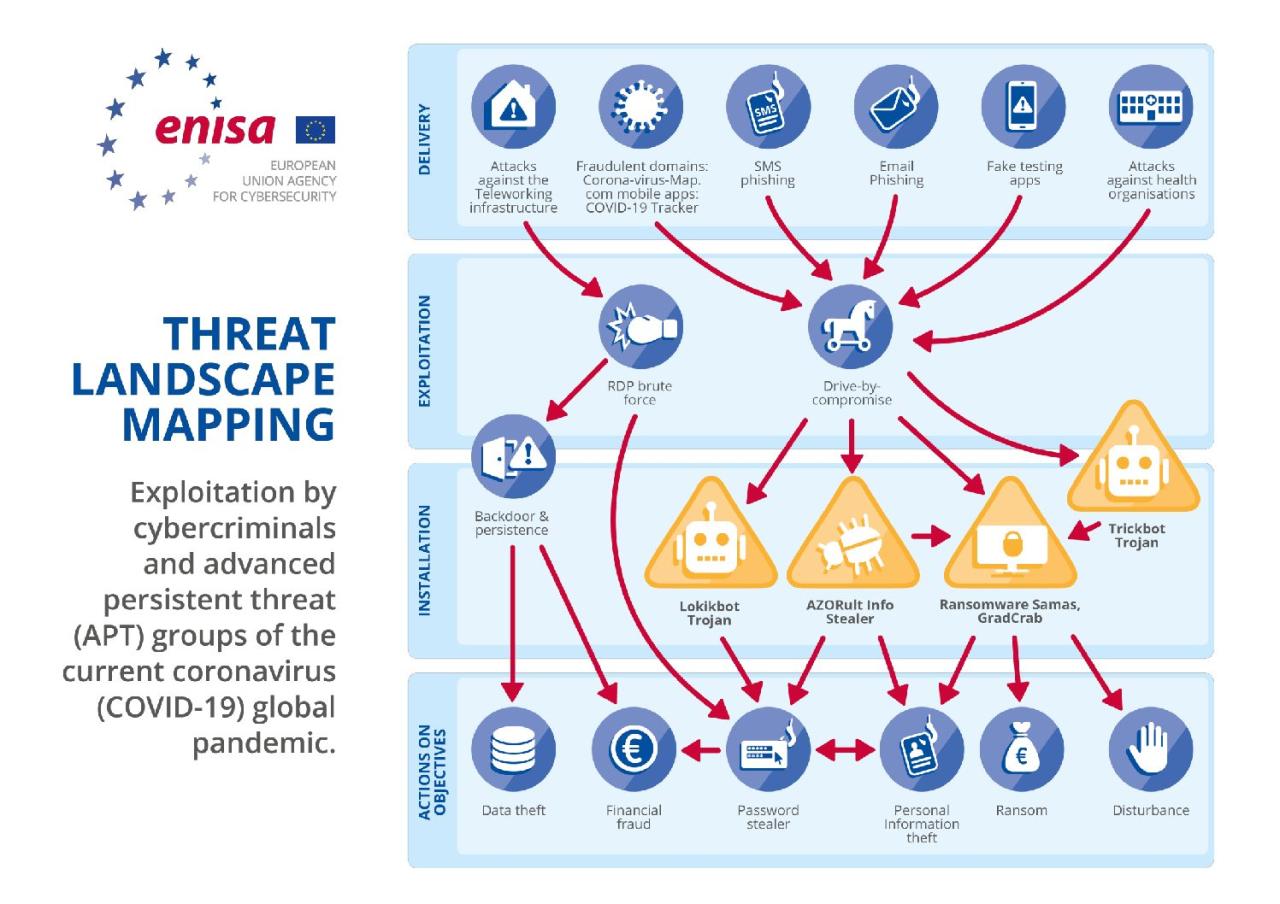
The cybersecurity threat landscape is a constantly shifting battlefield, characterized by an accelerating pace of change and ever-increasing sophistication in attacks. What was considered a cutting-edge attack just a few years ago is now commonplace, replaced by even more advanced and insidious techniques. This rapid evolution necessitates a proactive and adaptable approach to security, leveraging automation to keep pace with the threats.The frequency and sophistication of cyberattacks are rising exponentially.
We’re seeing a significant increase in the volume of attacks, driven by factors like the expanding attack surface resulting from the increasing reliance on interconnected devices and cloud services. Criminals are also becoming more organized and well-funded, employing advanced techniques like AI-powered malware and sophisticated social engineering tactics. The motivations behind these attacks are also diversifying, ranging from financial gain to espionage and state-sponsored attacks.Automation plays a dual role in this evolving landscape.
While it offers powerful tools for defenders to automate security processes and improve response times, it also accelerates the speed and scale of attacks. Attackers are increasingly leveraging automation to launch large-scale distributed denial-of-service (DDoS) attacks, rapidly spread malware, and personalize phishing campaigns at an unprecedented rate. This automation allows them to overwhelm traditional security defenses and execute attacks with far greater efficiency than ever before.
Emerging Threats Requiring Immediate Attention
The current threat landscape is punctuated by several emerging threats that demand immediate attention. These include the rise of AI-powered malware, which can adapt and evolve to evade detection, making traditional signature-based antivirus solutions less effective. Supply chain attacks, which target vulnerabilities in software development and distribution chains, are also becoming increasingly prevalent, allowing attackers to compromise numerous organizations simultaneously.
Ransomware attacks continue to be a major concern, with attackers demanding ever-larger ransoms and employing increasingly sophisticated encryption techniques. Furthermore, the convergence of operational technology (OT) and information technology (IT) creates new attack vectors, potentially leading to disruptions in critical infrastructure. For example, the Colonial Pipeline ransomware attack in 2021 highlighted the devastating consequences of successful ransomware attacks on critical infrastructure, resulting in fuel shortages across the eastern United States.
Future-proofing cybersecurity requires rapid response, and automation is key to keeping pace with evolving threats. The recent news about facebook asking bank account info and card transactions of users highlights the urgent need for robust, automated security measures. This incident underscores how crucial it is to invest in systems that can identify and neutralize threats before they cause significant damage.
Ultimately, automation is the only way to truly stay ahead of the curve.
This incident demonstrated the real-world impact of sophisticated cyberattacks and the urgent need for robust cybersecurity measures. The NotPetya ransomware attack in 2017, disguised as a tax software update, also serves as a stark example of the far-reaching consequences of supply chain compromises, causing billions of dollars in damage globally.
Automation in Cybersecurity Defense
The sheer volume and velocity of modern cyber threats make manual defense practically impossible. Automation is no longer a luxury; it’s a necessity for organizations aiming to effectively protect their digital assets. By automating key security processes, businesses can significantly improve their threat detection capabilities, speed up response times, and ultimately reduce the impact of successful attacks. This shift towards automated defense is crucial for staying ahead of the ever-evolving threat landscape.Automation plays a vital role in enhancing threat detection and response by enabling faster identification of malicious activities, quicker isolation of compromised systems, and more efficient remediation efforts.
This leads to reduced dwell time – the period between an attacker gaining access and being detected – a key metric in minimizing damage. Automated systems can analyze vast amounts of data far exceeding human capacity, identifying subtle anomalies that might otherwise go unnoticed. This proactive approach shifts the focus from reactive damage control to preventative security measures.
SIEM, SOAR, and AI-Powered Tools in Cybersecurity Automation, Future proofing cybersecurity at the speed of threats with automation
Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources, providing a centralized view of security events across an organization’s infrastructure. These systems can be configured to automatically trigger alerts based on predefined rules, notifying security teams of potential threats. Security Orchestration, Automation, and Response (SOAR) platforms take this a step further by automating incident response procedures.
They can automatically investigate alerts, contain threats, and remediate vulnerabilities, significantly reducing the time and resources required to handle security incidents. Finally, Artificial Intelligence (AI)-powered tools leverage machine learning algorithms to identify patterns and anomalies in data, enabling more accurate threat detection and prediction. AI can analyze network traffic, user behavior, and system logs to identify potential threats before they escalate.
For example, AI can detect unusual login attempts from unfamiliar geographical locations or identify malware based on its behavior patterns.
Comparing Automation Approaches for Threat Mitigation
Different automation approaches offer varying levels of sophistication and effectiveness. Rule-based systems, a foundational element of many automation tools, rely on predefined rules to trigger actions. While effective for known threats, they struggle with novel or zero-day attacks. Machine learning-based systems, on the other hand, can adapt to new threats by learning from past data. They can identify patterns and anomalies that rule-based systems might miss.
A hybrid approach, combining rule-based and machine learning techniques, often offers the best balance of speed and accuracy. For instance, rule-based systems can provide immediate alerts for known threats, while machine learning algorithms can analyze the data further to identify more subtle or sophisticated attacks. The choice of approach depends on factors such as the organization’s risk tolerance, technical expertise, and budget.
Automated Incident Response System for the Finance Industry
A hypothetical automated incident response system for a financial institution would need to be highly robust and responsive due to the sensitive nature of the data involved. The system could integrate SIEM, SOAR, and AI-powered tools to detect and respond to various threats, such as malware infections, phishing attacks, and denial-of-service attacks. Upon detection of a suspicious event, the system would automatically isolate the affected system, preventing further spread of the threat.
It would then initiate a comprehensive investigation, analyzing logs and network traffic to identify the source and scope of the attack. Based on the findings, the system could automatically execute remediation actions, such as deleting malicious files, patching vulnerabilities, and resetting compromised accounts. The system would also automatically notify relevant personnel, providing them with detailed information about the incident and recommended actions.
Crucially, this system would maintain a detailed audit trail of all actions taken, ensuring compliance with regulatory requirements and facilitating post-incident analysis. For example, a suspicious transaction exceeding a predefined threshold could trigger an immediate alert, automatically freezing the account and initiating a fraud investigation. The system could also correlate data from multiple sources, such as network security logs, transaction records, and user behavior data, to identify more complex attacks that might otherwise go unnoticed.
Building a Future-Proof Cybersecurity Strategy
A truly future-proof cybersecurity strategy isn’t about implementing the latest technology; it’s about building resilience and adaptability into your organization’s DNA. This means proactively anticipating emerging threats, automating defenses, and fostering a culture of security awareness. It’s a continuous process of evolution, not a one-time fix.
Key Elements of a Resilient and Adaptable Cybersecurity Strategy
A resilient cybersecurity strategy requires a multi-layered approach, encompassing people, processes, and technology. It should be designed to withstand a range of attacks and adapt to the ever-changing threat landscape. This includes regular security assessments, robust incident response plans, and a strong focus on employee training. Furthermore, a commitment to continuous improvement and proactive threat hunting is essential for staying ahead of the curve.
Best Practices for Integrating Automation into Existing Security Infrastructure
Integrating automation into existing security infrastructure requires a phased approach. Begin by identifying areas where automation can deliver the greatest impact, such as vulnerability scanning, incident response, and threat detection. Prioritize solutions that integrate seamlessly with your existing tools and processes. Ensure that automated systems are properly monitored and managed to prevent unintended consequences. Regularly review and update your automation strategies to keep pace with evolving threats and technologies.
For example, automating the patching process reduces the window of vulnerability significantly, minimizing the risk of exploitation.
Step-by-Step Plan for Implementing Automated Security Measures
Implementing automated security measures requires a well-defined plan. The following table Artikels a phased approach, detailing tasks, technologies, and timelines:
| Phase | Task | Technology | Timeline |
|---|---|---|---|
| Assessment & Planning | Identify critical assets and vulnerabilities. Define automation goals. | Vulnerability scanners, security information and event management (SIEM) systems. | 1-2 months |
| Proof of Concept (POC) | Pilot automated security solutions in a controlled environment. | Automated vulnerability management tools, security orchestration, automation, and response (SOAR) platforms. | 2-3 months |
| Deployment & Integration | Integrate automated solutions into existing security infrastructure. | API integrations, scripting languages (e.g., Python), cloud-based security platforms. | 3-6 months |
| Monitoring & Optimization | Continuously monitor automated systems for performance and effectiveness. Refine processes based on performance data. | Monitoring dashboards, SIEM systems, log analysis tools. | Ongoing |
Successful implementation relies heavily on clear communication and collaboration across teams.
Future-proofing cybersecurity demands speed and automation to keep pace with evolving threats. A key element in this race is robust cloud security, and that’s where understanding tools like Bitglass comes in. Check out this insightful article on bitglass and the rise of cloud security posture management to see how it helps. Ultimately, leveraging such solutions is crucial for achieving truly automated and proactive cybersecurity defenses.
Addressing the Skills Gap and Training
The rapid advancement of cybersecurity threats and the increasing reliance on automation necessitate a significant upskilling and reskilling effort within the cybersecurity workforce. Failing to address this skills gap leaves organizations vulnerable, unable to effectively manage and leverage the very automation designed to protect them. The complexity of modern automated security systems demands a workforce proficient in not only traditional security practices but also in the intricacies of AI, machine learning, and the specific tools employed.The importance of specialized training programs cannot be overstated.
These programs must bridge the gap between theoretical knowledge and practical application, equipping cybersecurity professionals with the skills to effectively monitor, manage, and troubleshoot automated security systems. Furthermore, a curriculum focusing on the ethical implications and potential biases inherent in AI-driven security solutions is crucial. This ensures responsible and effective deployment of these powerful technologies.
Training Programs Focused on Automation and AI in Cybersecurity
Effective training must encompass a blend of theoretical understanding and hands-on experience. A successful curriculum should cover areas such as AI algorithms used in threat detection, the implementation and management of Security Information and Event Management (SIEM) systems, the interpretation of automated threat alerts, and the development of automated incident response playbooks. Furthermore, training should address the ethical considerations of using AI in security, including bias detection and mitigation strategies.
Real-world case studies of successful and unsuccessful automation implementations can significantly enhance learning and provide valuable insights into practical application. For example, a module could analyze a specific incident where an automated system successfully mitigated a sophisticated attack, highlighting the system’s strengths and the analyst’s role in its management. Conversely, a study of a failed automation could demonstrate how human oversight and skilled intervention are crucial even in highly automated environments.
Example Training Module: SIEM Platform
This module focuses on the Splunk SIEM platform, a widely used tool. The training would begin with an introduction to the core functionalities of Splunk, including data ingestion, indexing, searching, and reporting. Trainees would then learn to develop and utilize Splunk searches to identify security events, correlating them to identify potential threats. A significant portion of the module would cover the creation and implementation of custom dashboards and alerts, allowing for proactive threat detection.
Hands-on exercises would involve analyzing simulated security logs to identify malicious activities and developing automated responses to specific threat scenarios. Finally, the module would address the management and maintenance of the Splunk environment, including user access control and data retention policies. The assessment would involve practical exercises requiring trainees to analyze real-world or simulated security data using Splunk, identify threats, and implement appropriate responses.
Successful completion would demonstrate competency in using Splunk to proactively manage and respond to security incidents.
Future-proofing cybersecurity demands rapid response, and automation is key to keeping pace with evolving threats. Building robust, scalable security solutions often involves leveraging modern development approaches, which is why understanding the advancements in application development, like those discussed in this insightful article on domino app dev the low code and pro code future , is crucial. This understanding allows us to create more agile and secure systems, ultimately strengthening our defenses against the ever-present cyber risks.
The Human Element in Automated Cybersecurity
Automation is rapidly transforming cybersecurity, offering faster response times and increased efficiency. However, a completely automated security system is a dangerous illusion. Human expertise remains a critical component, providing the crucial context, judgment, and adaptability that machines currently lack. Over-reliance on automation without adequate human oversight can leave organizations vulnerable to sophisticated attacks and unforeseen circumstances.The Importance of Human Oversight and Intervention in Automated Security SystemsEffective cybersecurity requires a blend of human intelligence and automated tools.
While automation excels at handling repetitive tasks like threat detection and log analysis, humans are essential for interpreting complex situations, making critical decisions, and adapting to evolving threats. Automated systems can generate alerts, but a human analyst is needed to prioritize these alerts, investigate false positives, and understand the broader context of a potential breach. For example, an automated system might flag unusual login activity from a specific IP address.
A human analyst, however, can determine if this activity is legitimate (e.g., a user traveling internationally) or malicious. This human-in-the-loop approach is crucial for minimizing false positives and ensuring accurate responses to real threats.
Potential Risks and Limitations of Solely Relying on Automation
Relying solely on automated security systems presents several significant risks. Sophisticated attackers are constantly developing new techniques to evade detection, and automated systems may struggle to adapt to these evolving tactics. Furthermore, automation can be vulnerable to adversarial attacks, such as poisoning datasets or exploiting vulnerabilities in the automation system itself. The lack of human oversight can lead to delayed responses, missed threats, and ultimately, successful breaches.
A real-world example is the Stuxnet worm, which exploited vulnerabilities in industrial control systems, highlighting the limitations of relying solely on automated defenses. The sophisticated nature of the attack required human analysis to understand its mechanism and impact.
Scenarios Where Human Expertise is Crucial Despite Automation
Several scenarios highlight the irreplaceable role of human expertise in cybersecurity. Dealing with zero-day exploits, where vulnerabilities are unknown until they are exploited, necessitates human ingenuity and analysis to understand the attack and develop a response. Similarly, handling complex, multi-vector attacks that involve a combination of techniques requires the ability to piece together various pieces of information and form a holistic understanding of the threat.
Moreover, investigating advanced persistent threats (APTs), which often involve prolonged and stealthy intrusions, necessitates human expertise to analyze patterns, uncover hidden indicators, and develop a tailored response strategy. Finally, incident response requires careful human judgment to determine the scope of a breach, prioritize remediation efforts, and communicate effectively with stakeholders.
Designing a System that Balances Automation and Human Expertise
Creating an effective cybersecurity system requires a carefully designed balance between automation and human expertise. This involves selecting automation tools that complement human capabilities, rather than replacing them. For instance, automation can be used for repetitive tasks such as vulnerability scanning and malware detection, freeing up human analysts to focus on more complex investigations. The system should also incorporate mechanisms for human oversight, such as alert prioritization and escalation procedures, ensuring that human analysts are involved in critical decisions.
Furthermore, robust training and development programs are essential to equip security personnel with the skills needed to effectively manage and interpret data from automated systems. This balanced approach leverages the strengths of both humans and machines, creating a more resilient and effective cybersecurity posture.
Cost-Effectiveness and ROI of Automated Cybersecurity: Future Proofing Cybersecurity At The Speed Of Threats With Automation

The escalating costs of cyberattacks and the increasing complexity of threat landscapes are forcing organizations to re-evaluate their security strategies. Manual security processes, while offering a degree of control, are often slow, inefficient, and prone to human error. Automated cybersecurity solutions offer a compelling alternative, promising significant cost savings and a strong return on investment (ROI) by streamlining operations, improving response times, and enhancing overall security posture.
This analysis explores the financial benefits of implementing automation and provides a framework for evaluating its cost-effectiveness.Implementing automated cybersecurity solutions presents a compelling financial case. While initial investment costs might seem significant, the long-term benefits often outweigh these expenses considerably. A comparison of manual versus automated processes reveals substantial differences in efficiency and cost-effectiveness.
Cost Comparison: Manual vs. Automated Security Processes
Manual security processes rely heavily on human analysts to monitor alerts, investigate incidents, and implement remediation strategies. This approach is labor-intensive, requiring significant staffing and training investments. Furthermore, human error is a significant factor, leading to delayed responses, missed threats, and increased financial losses. Automated solutions, on the other hand, leverage machine learning and artificial intelligence to automate many of these tasks, reducing the need for extensive human intervention and minimizing the risk of human error.
This results in lower operational costs, faster response times, and improved overall security.
Return on Investment (ROI) of Specific Automation Technologies
Several automation technologies offer significant ROI. Security Information and Event Management (SIEM) systems, for example, automate log collection, analysis, and correlation, reducing the time and resources required for threat detection and incident response. This leads to faster remediation and reduced downtime, translating to direct cost savings. Similarly, automated vulnerability scanning and penetration testing tools can identify and address security weaknesses proactively, preventing costly breaches.
The ROI of these technologies can be calculated by comparing the cost of implementation with the cost savings achieved through reduced incidents, improved efficiency, and avoided losses. For example, a company might invest $50,000 in a SIEM system, but this investment could save them $100,000 annually by reducing the time spent on incident response and avoiding the costs associated with a major data breach.
Cost-Benefit Analysis of Automation Strategies
The financial impact of different automation strategies varies depending on the specific needs and circumstances of an organization. A cost-benefit analysis should consider various factors, including the initial investment costs, ongoing maintenance expenses, and the potential cost savings from reduced incidents, improved efficiency, and compliance adherence.
| Automation Strategy | Initial Investment | Annual Operating Costs | Estimated Annual Cost Savings | ROI (Years) |
|---|---|---|---|---|
| SIEM Implementation | $50,000 | $10,000 | $20,000 | 2.5 |
| Automated Vulnerability Scanning | $15,000 | $5,000 | $10,000 | 1.5 |
| Security Orchestration, Automation, and Response (SOAR) | $75,000 | $15,000 | $30,000 | 2.5 |
Note: These figures are illustrative examples and may vary significantly depending on the specific organization, the chosen technology, and the scale of implementation. A thorough cost-benefit analysis should be conducted for each specific scenario.
Ethical Considerations and Responsible Automation
The increasing reliance on AI and automation in cybersecurity presents a complex ethical landscape. While these technologies offer significant advantages in speed and efficiency, they also introduce potential risks related to bias, privacy, and accountability. Understanding and mitigating these risks is crucial for building a truly secure and responsible digital future.AI-powered security systems, while powerful, are not immune to the biases present in the data they are trained on.
This can lead to discriminatory outcomes, such as unfairly targeting certain groups or neglecting vulnerabilities affecting specific populations. For example, a system trained primarily on data from one geographical region might be less effective at identifying threats originating from other regions, potentially creating security gaps.
Bias in Automated Security Systems and Mitigation Strategies
Algorithmic bias in cybersecurity automation can manifest in various ways. A facial recognition system used for access control might exhibit higher error rates for individuals with darker skin tones due to a lack of diversity in the training data. Similarly, a system designed to detect malicious network activity might be less sensitive to attacks originating from less-common protocols or geographical locations if its training data predominantly reflects more typical attack vectors.
Mitigation strategies involve carefully curating diverse and representative datasets for training, employing rigorous testing and validation procedures to identify and correct biases, and implementing ongoing monitoring and auditing processes to detect and address bias as it emerges in real-world operation. Transparency in the algorithms and data used is also critical for accountability and building trust.
Data Privacy and Security in Automated Systems
Automated cybersecurity systems often process vast amounts of sensitive data, raising significant privacy concerns. The collection, storage, and use of this data must adhere to strict privacy regulations like GDPR and CCPA. Implementing robust data anonymization and encryption techniques is paramount. Furthermore, access control mechanisms must be rigorously enforced to prevent unauthorized access and misuse of sensitive information.
Regular security audits and penetration testing should be conducted to identify and address vulnerabilities. A clear and concise privacy policy outlining how data is collected, used, and protected is essential for building user trust and demonstrating responsible data handling practices.
Examples of Responsible AI Practices in Cybersecurity Automation
Responsible AI in cybersecurity necessitates a human-centered approach. This includes designing systems that are transparent, explainable, and accountable. For example, instead of relying solely on automated decisions, a system could provide human analysts with contextual information and potential explanations for flagged events, allowing them to override automated decisions if necessary. Another example is the use of differential privacy techniques, which add carefully calibrated noise to datasets to protect individual privacy while still allowing for useful statistical analysis.
Finally, regular ethical reviews and impact assessments should be integrated into the development lifecycle of any AI-powered cybersecurity system to proactively identify and address potential ethical concerns.
Outcome Summary

In a world where cyber threats are constantly evolving, relying solely on manual security processes is simply unsustainable. Building a future-proof cybersecurity strategy requires embracing automation, but doing so responsibly. This means integrating cutting-edge technologies like SIEM and SOAR, investing in skilled professionals capable of managing these systems, and always maintaining a crucial human-in-the-loop element. By strategically combining automation with human expertise, we can create a robust and adaptable security posture that’s ready to face whatever the future throws our way.
The key is proactive planning, continuous learning, and a commitment to ethical practices. Let’s build a safer digital future, together.
FAQ Guide
What are the biggest risks of relying solely on automated cybersecurity?
Over-reliance on automation can lead to blind spots, missed threats, and difficulty adapting to novel attack techniques. Human oversight is essential for critical decision-making and addressing unforeseen circumstances.
How can I measure the ROI of investing in automated cybersecurity?
Measure ROI by comparing the costs of manual processes (labor, incident response time, etc.) to the costs of automated solutions, factoring in reduced downtime, improved threat detection rates, and minimized data breaches.
What ethical considerations are important when using AI in cybersecurity?
Key ethical considerations include bias in algorithms, potential for misuse, data privacy concerns, and the need for transparency and accountability in automated decision-making.
How do I choose the right automation tools for my organization?
Consider your specific needs, budget, existing infrastructure, and the skills of your team. Start with a needs assessment and research different vendors and solutions before making a decision.