Gartner Expects $93 Billion in Security Spend, But Whats Missing? 2
Gartner expects 93 billion in security spend but whats missing 2 – Gartner Expects $93 Billion in Security Spend, But What’s Missing? 2 This massive projected investment in cybersecurity highlights a crucial point: money alone isn’t the solution. While $93 billion is a staggering sum, Gartner’s report also points to significant gaps in our current approach. We’re spending big, but are we spending
-smart*? This post dives into the critical areas where investment is falling short, exploring the skills shortage, emerging threats, and the crucial role of AI and automation.
Let’s unpack what’s really needed to secure our digital future.
The sheer scale of Gartner’s prediction underscores the growing importance of cybersecurity in today’s interconnected world. Businesses are facing increasingly sophisticated threats, from ransomware attacks to data breaches, forcing them to invest heavily in protection. However, simply throwing money at the problem isn’t enough. This post analyzes where these investments are falling short, focusing on critical areas like the persistent skills gap and the need for more strategic approaches to security.
We’ll explore the reasons behind these shortcomings and suggest solutions to bridge the gap between spending and effective security.
Gartner’s $93 Billion Security Spending Prediction

Gartner’s prediction of $93 billion in global cybersecurity spending for 2023 signifies a substantial investment by organizations worldwide to protect themselves against increasingly sophisticated cyber threats. This figure reflects a growing awareness of the financial and reputational risks associated with data breaches and other security incidents. Understanding the drivers behind this surge and its implications is crucial for businesses of all sizes.Gartner’s prediction reflects several key factors driving increased security investment.
The rise of cloud computing, with its inherent security complexities, is a major contributor. Organizations are increasingly migrating their data and applications to the cloud, necessitating robust cloud security solutions. The growing sophistication of cyberattacks, including ransomware and supply chain attacks, also forces organizations to enhance their defenses. Furthermore, evolving regulations and compliance requirements, such as GDPR and CCPA, compel businesses to invest in security measures to ensure data privacy and protection.
Finally, the increasing reliance on remote work and the expanding attack surface it creates contribute to the rising security spending.
Comparison to Previous Years’ Spending and Significant Trends
Gartner’s $93 billion prediction represents a significant increase compared to previous years. While precise year-over-year comparisons require access to Gartner’s full reports, publicly available information indicates a consistent upward trend in cybersecurity spending over the past decade. This reflects a shift from a reactive approach to security, where organizations primarily responded to incidents, to a more proactive approach focused on prevention and risk mitigation.
This trend is further fueled by the increasing awareness of the long-term costs associated with security breaches, including legal fees, regulatory fines, and reputational damage. The focus is shifting towards preventative measures and building a robust security posture.
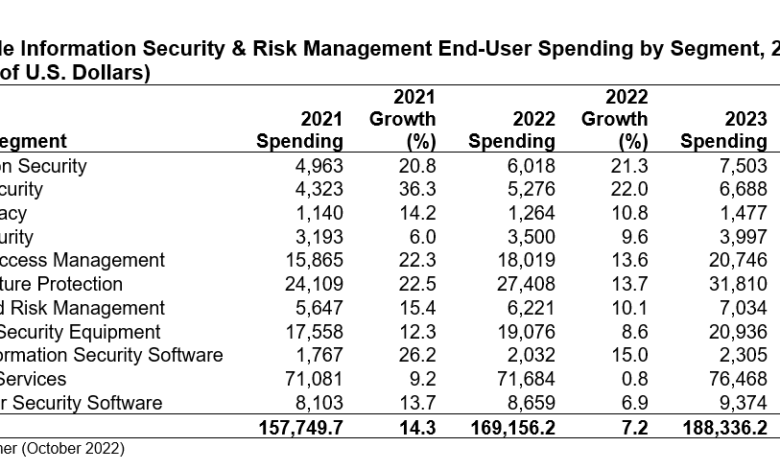
Predicted Spending Across Different Security Sectors
The $93 billion is not evenly distributed across all security sectors. Gartner’s reports (though access to precise breakdowns requires subscription) typically segment the market into various areas. The following table provides a hypothetical breakdown, reflecting general market trends, to illustrate the distribution of spending. Note that these figures are estimates and may vary depending on the specific methodology and data used.
| Security Sector | Estimated Spending (Billions USD) |
|---|---|
| Cloud Security | 20 |
| Endpoint Security | 15 |
| Network Security | 18 |
| Data Security & Privacy | 12 |
| Security Services | 10 |
| Identity and Access Management (IAM) | 8 |
| Other | 10 |
Unmet Needs in Cybersecurity
Gartner’s prediction of $93 billion in global cybersecurity spending highlights a significant investment in digital security. However, simply throwing money at the problem doesn’t guarantee effective protection. A closer look reveals crucial areas where current spending falls short, leaving organizations vulnerable to increasingly sophisticated threats. Understanding these unmet needs is vital for improving overall security posture and achieving a truly robust defense.The disparity between projected spending and actual security effectiveness stems from several factors.
A significant portion of the budget often gets allocated to reactive measures, such as incident response and remediation, rather than proactive prevention. Furthermore, a lack of skilled cybersecurity professionals and a persistent skills gap hinder the effective implementation and management of security solutions. Finally, the rapidly evolving threat landscape, characterized by new attack vectors and techniques, necessitates continuous adaptation and investment in emerging technologies, which often lags behind the pace of innovation.
Neglecting these unmet needs can lead to significant financial losses, reputational damage, legal repercussions, and even operational disruption.
Insufficient Investment in Proactive Security Measures
Many organizations prioritize reactive security measures, such as incident response and data breach remediation, over proactive prevention strategies. This reactive approach is costly and inefficient, as it addresses problems after they have occurred, rather than preventing them in the first place. Proactive measures like robust threat intelligence platforms, advanced threat detection systems, and comprehensive security awareness training programs are often underfunded, leaving organizations exposed to preventable attacks.
For example, a company might spend heavily on antivirus software but neglect to invest in employee security awareness training, leaving them vulnerable to phishing attacks. The consequence is a higher likelihood of successful breaches, resulting in significant financial and reputational damage. Addressing this gap requires a strategic shift in resource allocation, prioritizing investments in proactive security technologies and strategies.
This includes adopting solutions like Security Information and Event Management (SIEM) systems for threat detection and response, and implementing Zero Trust Network Access (ZTNA) to secure access to sensitive resources.
Lack of Skilled Cybersecurity Professionals
The cybersecurity industry faces a severe shortage of skilled professionals. Organizations struggle to find and retain qualified personnel to manage and maintain their security infrastructure, leaving them vulnerable to exploitation. This skills gap contributes to inadequate implementation of security solutions, delayed incident response, and increased risk of successful attacks. For instance, a small business might lack the resources to hire a dedicated cybersecurity expert, relying instead on undertrained staff to manage their security.
This can lead to misconfigurations, vulnerabilities, and ultimately, successful attacks. Investing in cybersecurity training programs, offering competitive salaries and benefits to attract and retain talent, and leveraging automation technologies to address the skills shortage are crucial steps to mitigate this risk.
Inadequate Focus on Emerging Threats and Technologies
The cybersecurity landscape is constantly evolving, with new threats and attack vectors emerging regularly. Organizations often struggle to keep pace with these advancements, leading to vulnerabilities in their security posture. For example, the rise of ransomware-as-a-service has made it easier for less sophisticated attackers to launch devastating attacks. Many organizations lack the resources and expertise to effectively address these emerging threats, relying on outdated technologies and strategies.
Investing in advanced threat detection technologies, such as artificial intelligence (AI) and machine learning (ML)-powered security solutions, and staying abreast of the latest threat intelligence is critical to staying ahead of the curve. Regular security audits and penetration testing can also help identify and address vulnerabilities before they are exploited by attackers.
The Skills Gap in Cybersecurity: Gartner Expects 93 Billion In Security Spend But Whats Missing 2
The cybersecurity industry is booming, with Gartner predicting a staggering $93 billion will be spent on security in However, this massive investment is hampered by a critical and widening gap: a severe shortage of skilled cybersecurity professionals. This skills gap isn’t just a minor inconvenience; it’s a major vulnerability that leaves organizations exposed to increasingly sophisticated cyber threats.
The lack of qualified personnel directly impacts an organization’s ability to effectively implement and manage security solutions, ultimately hindering their ability to protect sensitive data and maintain operational continuity.The current cybersecurity skills shortage is significant and multifaceted. Demand far outpaces supply across all levels of expertise, from entry-level analysts to seasoned security architects. For example, while the demand for cloud security engineers continues to rise exponentially due to the increasing reliance on cloud infrastructure, the number of qualified professionals capable of securing these complex environments remains drastically insufficient.
Gartner predicts a whopping $93 billion will be spent on cybersecurity this year, but where’s the real impact? It seems like even with all that investment, basic security practices are still lacking, as evidenced by the recent news of Facebook requesting bank account and card details from users, as reported here: facebook asking bank account info and card transactions of users.
This highlights a critical gap: spending money doesn’t automatically translate to better security; a focus on user education and fundamental protections is equally crucial.
Similarly, the specialized skills required to combat advanced persistent threats (APTs) and respond to ransomware attacks are in extremely short supply, leaving many organizations ill-equipped to handle these critical incidents. This disparity between the need for skilled professionals and the available talent pool creates a dangerous situation where organizations are forced to operate with inadequate security postures, leaving them vulnerable to exploitation.
Addressing the Cybersecurity Skills Gap Through Training Initiatives
Addressing the cybersecurity skills gap requires a multi-pronged approach that focuses on both training existing employees and attracting new talent. Organizations can invest in comprehensive training programs that cover a range of cybersecurity disciplines, from network security and incident response to cloud security and security awareness training. These programs should be tailored to the specific needs of the organization and should incorporate hands-on exercises and simulations to provide practical experience.
For instance, a program could include modules on ethical hacking, penetration testing, and vulnerability assessment, providing employees with the skills to identify and mitigate security weaknesses. Furthermore, organizations should prioritize continuous learning and development by providing employees with access to online courses, certifications, and conferences to stay abreast of the latest threats and technologies. This commitment to ongoing training demonstrates a value in employee development and fosters a culture of security awareness.
Attracting and Retaining Cybersecurity Talent
Attracting and retaining top cybersecurity talent is crucial. Organizations need to offer competitive salaries and benefits packages to compete with other companies vying for the same limited pool of skilled professionals. Creating a positive and supportive work environment, fostering a culture of collaboration and learning, and offering opportunities for career advancement are equally important. Focusing on employee well-being and work-life balance can also be a significant differentiator in attracting and retaining talent in this high-pressure field.
Gartner’s prediction of $93 billion in security spending is huge, but are we focusing on the right things? A key area often overlooked is consistent cloud security, which is where solutions like Bitglass shine. Check out this article on bitglass and the rise of cloud security posture management to see how they address this gap. Ultimately, effective cloud security management is crucial to making that massive security budget truly effective.
Additionally, organizations can partner with universities and colleges to develop specialized cybersecurity programs and offer internships and apprenticeships to cultivate the next generation of cybersecurity professionals. This proactive approach helps to build a pipeline of skilled individuals entering the workforce, thereby alleviating the existing shortage.
A Sample Cybersecurity Training Program
A comprehensive training program should address multiple skill sets. For example, a program designed to upskill existing IT staff could include modules on:
- Fundamentals of Network Security: Covering topics such as firewalls, intrusion detection/prevention systems, and VPNs.
- Security Information and Event Management (SIEM): Training on SIEM tools and techniques for log analysis and threat detection.
- Incident Response: Practical exercises and simulations on handling security incidents, including malware analysis and containment.
- Cloud Security: Specific training on securing cloud environments, including identity and access management (IAM) and data encryption.
- Security Awareness Training: Educating employees on common threats like phishing and social engineering.
This program would combine online learning modules with hands-on workshops and simulations to provide a comprehensive and practical learning experience. The program’s curriculum should be regularly updated to reflect the ever-evolving threat landscape and advancements in cybersecurity technologies. This ensures that employees receive training on the most current threats and best practices. The program could also incorporate certifications, such as CompTIA Security+, Certified Ethical Hacker (CEH), or Certified Information Systems Security Professional (CISSP), to validate employee skills and enhance their career prospects.
Emerging Threats and Their Impact on Security Spending
Gartner’s prediction of $93 billion in security spending highlights a crucial reality: the cybersecurity landscape is evolving at an alarming rate, driven by increasingly sophisticated and impactful emerging threats. These threats aren’t just theoretical risks; they represent real-world challenges that are forcing organizations to significantly increase their investments in security solutions. The sheer volume and complexity of these threats are demanding a proactive and adaptive approach, pushing the boundaries of traditional security measures.The challenges posed by these emerging threats are multifaceted.
They require a blend of technical expertise, strategic planning, and a continuous cycle of adaptation and improvement. Simply purchasing the latest security tools isn’t enough; organizations must also cultivate a security-conscious culture, invest in employee training, and develop robust incident response plans. The failure to adequately address these emerging threats can lead to significant financial losses, reputational damage, and legal repercussions.
The Rise of AI-Powered Attacks
Artificial intelligence is rapidly transforming the cybersecurity landscape, impacting both offensive and defensive capabilities. Attackers are leveraging AI to automate tasks such as phishing campaign creation, vulnerability scanning, and malware development, making attacks more efficient and harder to detect. This necessitates a shift towards AI-driven security solutions that can proactively identify and respond to these sophisticated threats. For example, AI-powered threat intelligence platforms can analyze vast amounts of data to identify patterns and predict potential attacks before they occur.
Furthermore, AI-driven security information and event management (SIEM) systems can automate threat detection and response, reducing the burden on security teams. The increasing use of AI by malicious actors necessitates a corresponding increase in investment in AI-based security technologies to maintain a balanced equilibrium.
The Expanding Threat of IoT Devices
The proliferation of Internet of Things (IoT) devices presents a significant challenge to cybersecurity. These devices, often lacking robust security features, represent a vast attack surface for malicious actors. A single compromised IoT device can serve as an entry point into an entire network, potentially leading to widespread data breaches and system disruptions. The challenge lies in securing a diverse ecosystem of devices with varying levels of security capabilities.
This requires a multi-layered approach that includes secure device management, network segmentation, and robust authentication protocols. For instance, the Mirai botnet, which leveraged compromised IoT devices to launch massive DDoS attacks, demonstrated the devastating potential of insecure IoT devices. Mitigation strategies need to focus on improving the security of IoT devices themselves, alongside network-level security measures.
Sophisticated Ransomware Attacks
Ransomware attacks continue to evolve, becoming more targeted, sophisticated, and impactful. Attackers are now leveraging techniques such as double extortion (stealing data before encrypting it) and targeting critical infrastructure, increasing the pressure on organizations to pay ransoms. This requires a multi-pronged approach, encompassing robust data backups, employee training to prevent phishing attacks, and advanced threat detection systems capable of identifying and neutralizing ransomware before it can encrypt data.
The Colonial Pipeline ransomware attack in 2021 serves as a stark reminder of the devastating consequences of successful ransomware attacks, underscoring the need for significant investment in prevention and response capabilities.
- Emerging Threat: AI-powered attacks. Mitigation Strategy: Invest in AI-driven threat intelligence and security information and event management (SIEM) systems.
- Emerging Threat: The expanding threat of IoT devices. Mitigation Strategy: Implement secure device management, network segmentation, and robust authentication protocols.
- Emerging Threat: Sophisticated ransomware attacks. Mitigation Strategy: Maintain robust data backups, provide comprehensive employee training, and deploy advanced threat detection systems.
- Emerging Threat: Supply chain attacks. Mitigation Strategy: Implement rigorous vendor risk management programs and strengthen security throughout the supply chain.
- Emerging Threat: Cloud security vulnerabilities. Mitigation Strategy: Adopt a zero trust security model and leverage cloud-native security tools.
The Role of Automation and AI in Cybersecurity
The cybersecurity landscape is rapidly evolving, with increasingly sophisticated threats demanding more efficient and effective defense mechanisms. The predicted $93 billion in security spending highlights the industry’s awareness of this challenge, but simply throwing money at the problem isn’t enough. Automation and Artificial Intelligence (AI) are crucial components of a modern, robust security posture, offering the potential to significantly improve response times, reduce human error, and proactively identify and mitigate threats.AI and automation are transforming how organizations approach cybersecurity, moving away from reactive, manual processes towards proactive, intelligent systems.
By automating repetitive tasks and leveraging AI’s analytical capabilities, security teams can focus on more strategic initiatives and complex threats, improving overall efficiency and effectiveness. This shift is particularly critical given the ongoing skills shortage in the cybersecurity field.
AI-Powered Security Tools and Their Capabilities, Gartner expects 93 billion in security spend but whats missing 2
Several AI-powered security tools are already available, each offering unique capabilities to enhance security operations. Examples include Security Information and Event Management (SIEM) systems enhanced with machine learning algorithms to detect anomalies and prioritize alerts, intrusion detection systems that use AI to identify sophisticated attacks, and endpoint detection and response (EDR) solutions leveraging AI for threat hunting and automated remediation.
These tools don’t just react to known threats; they learn from past incidents and adapt to emerging attack vectors, providing a more dynamic and resilient defense.
Improving Efficiency and Effectiveness of Security Operations
The integration of AI and automation significantly streamlines security operations. Automated threat detection and response systems reduce the time it takes to identify and neutralize threats, minimizing the potential impact of breaches. AI-powered vulnerability management tools can automatically scan systems for weaknesses and prioritize patching efforts, reducing the attack surface. Furthermore, AI can analyze vast amounts of security data to identify patterns and predict potential threats, enabling proactive security measures.
This proactive approach is far more effective than relying solely on reactive measures.
A Text-Based Visual Representation of AI Enhancing Security Operations
Imagine a diagram. On the left, we have a chaotic scene representing traditional security operations: a overwhelmed security analyst surrounded by flashing alerts, struggling to prioritize incidents amidst a sea of data. Arrows point to various sources of alerts – firewalls, intrusion detection systems, etc. – all generating a constant stream of information. This represents the reactive, inefficient nature of manual security operations.Now, on the right, we see a much calmer scene.
The same security analyst is now focused on strategic tasks, overseeing a streamlined system. Arrows now point to an AI-powered security operations center (SOC). This SOC acts as a central hub, processing and analyzing data from various sources. AI algorithms filter out noise, prioritize critical alerts, and even automatically initiate response actions (e.g., blocking malicious IP addresses). The analyst is empowered to focus on investigating complex threats and developing proactive security strategies, rather than being bogged down in routine tasks.
This visually represents how AI enhances efficiency and effectiveness by automating routine tasks and prioritizing critical alerts, freeing up security personnel to focus on higher-level tasks. The difference in the level of stress and efficiency is stark, highlighting the transformative potential of AI in cybersecurity.
Gartner’s prediction of $93 billion in security spending is staggering, but are we focusing on the right things? A key area often overlooked is secure application development, and that’s where understanding the potential of platforms like Domino, as explained in this insightful article on domino app dev: the low-code and pro-code future , becomes crucial. Ultimately, robust, secure apps are essential to truly leverage that massive security investment.
Measuring the ROI of Cybersecurity Investments
Gartner’s prediction of $93 billion in global cybersecurity spending highlights the massive investment organizations are making to protect themselves. However, proving the value of this expenditure is a significant challenge. Many organizations struggle to demonstrate a clear return on investment (ROI) for their security initiatives, leading to budget constraints and difficulty justifying future investments. This section explores the challenges in measuring cybersecurity ROI, best practices for tracking effectiveness, key metrics, and a framework for assessment.
Challenges in Measuring Cybersecurity ROI
Quantifying the return on cybersecurity investments presents unique difficulties. Unlike tangible assets, the value of security often lies in preventing negative outcomes – breaches, data loss, reputational damage – which are difficult to precisely measure in monetary terms. Furthermore, the effectiveness of security measures is often only apparent in their absence; a successful security program is one where nothing bad happens.
This makes demonstrating success challenging, relying on indirect evidence and potentially subjective assessments. Another significant hurdle is the attribution problem: pinpointing the exact impact of a specific security control on preventing a specific threat is rarely straightforward. For example, did a firewall prevent an attack, or did the attacker simply choose a different method? Finally, the constantly evolving threat landscape necessitates ongoing adaptation, making long-term ROI projections difficult.
A security investment that is highly effective today might be obsolete tomorrow.
Best Practices for Tracking and Measuring Security Investment Effectiveness
Effective tracking requires a proactive, data-driven approach. Begin by clearly defining objectives and aligning security investments with specific business goals. For example, an objective might be to reduce the average time to detect and respond to security incidents by 50%. This quantifiable goal allows for direct measurement of progress. Establish a robust system for collecting and analyzing security data.
This includes logs from firewalls, intrusion detection systems, endpoint protection, and security information and event management (SIEM) tools. Regularly review and analyze this data to identify trends, vulnerabilities, and the effectiveness of implemented controls. Conduct regular security assessments and penetration testing to identify weaknesses and measure the effectiveness of mitigation strategies. Finally, document all security investments, including costs, implementation timelines, and expected outcomes.
This documentation is crucial for tracking ROI and demonstrating the value of security programs to stakeholders.
Key Metrics for Assessing Cybersecurity ROI
Several key metrics can help assess the ROI of security initiatives. These include:
- Mean Time To Detect (MTTD): The average time it takes to identify a security incident.
- Mean Time To Respond (MTTR): The average time it takes to resolve a security incident.
- Cost of a Data Breach: This includes direct costs (e.g., investigation, remediation, legal fees) and indirect costs (e.g., reputational damage, lost business). Industry benchmarks can provide a starting point for estimation, but organizations should tailor these figures to their specific circumstances.
- Return on Security Investment (ROSI): This is calculated by subtracting the total cost of security incidents from the total cost of security investments, then dividing by the total cost of security investments. A positive ROSI indicates that the security investments are generating a return.
- Reduction in Security Incidents: Tracking the number and severity of security incidents over time can demonstrate the effectiveness of security controls.
It’s crucial to remember that these metrics should be tailored to the specific goals and context of each organization.
Framework for Measuring the ROI of Cybersecurity Investments
A robust framework for measuring cybersecurity ROI should encompass the following stages:
- Define Objectives: Clearly articulate the specific business goals that the security investments aim to achieve.
- Identify Key Metrics: Select the metrics that will be used to track progress towards the defined objectives. These metrics should be measurable, achievable, relevant, and time-bound (SMART).
- Establish a Baseline: Measure the current state of security before implementing any new controls. This provides a benchmark against which to compare future performance.
- Implement Security Controls: Invest in and implement the chosen security controls.
- Monitor and Measure: Regularly collect and analyze data to track progress towards the defined objectives and measure the effectiveness of the implemented controls.
- Report and Analyze: Regularly report on the results and analyze the ROI of the security investments. This information should be used to inform future investment decisions.
By implementing this framework, organizations can gain a clearer understanding of the value of their cybersecurity investments and make more informed decisions about how to allocate their resources. This data-driven approach is crucial for demonstrating the importance of security to stakeholders and securing ongoing budget support.
Wrap-Up
So, while Gartner’s $93 billion security spending prediction is impressive, the real story lies in understanding where that money needs to go. It’s not just about bigger budgets; it’s about smarter investments. Addressing the skills gap, proactively mitigating emerging threats with AI and automation, and focusing on measurable ROI are crucial for effective cybersecurity. Investing in these areas won’t just protect against financial losses; it will safeguard reputations, maintain customer trust, and ultimately, secure the future of businesses in the digital age.
Let’s move beyond simply increasing spending and focus on building a truly resilient cybersecurity posture.
Detailed FAQs
What specific sectors will see the largest portion of the $93 billion investment, according to Gartner?
Gartner’s report likely breaks down the spending across various sectors like cloud security, endpoint security, and others. You’d need to access the full report for the precise breakdown.
How does Gartner’s prediction compare to previous years’ cybersecurity spending?
The report should provide a year-over-year comparison, showcasing the growth trend in cybersecurity investment and highlighting any significant shifts in spending priorities.
What are some examples of AI-powered security tools mentioned in Gartner’s report?
To find specific examples, you will need to consult the full Gartner report. It likely features case studies or mentions of specific vendors and their AI-driven security solutions.
