Get Hands-On with AppScans Next Virtual Workshop
Get hands on with appscans next virtual workshop api discovery secret+key vulnerable components scanning – Get hands-on with AppScan’s next virtual workshop: API discovery, secret & key vulnerable components scanning! This workshop isn’t just another tech talk; it’s your chance to dive deep into the world of API security. We’ll cover everything from identifying hidden APIs and exposed secrets to understanding the vulnerabilities lurking within your applications. Prepare for a hands-on experience that will leave you equipped to tackle real-world API security challenges.
We’ll explore practical techniques for API discovery using AppScan, comparing different methods and showcasing common vulnerabilities. You’ll learn how to identify exposed secrets and API keys, understand the associated risks, and develop strategies for mitigation. We’ll also delve into vulnerable component scanning, contrasting static and dynamic analysis, and provide a detailed walkthrough of a scenario-based analysis using AppScan.
Finally, we’ll cover best practices for secure API development and deployment, along with remediation strategies for discovered vulnerabilities.
AppScan Virtual Workshop Overview
AppScan’s virtual workshops offer a highly effective and convenient way to master the intricacies of application security testing. These interactive sessions provide in-depth training, hands-on experience, and valuable insights from industry experts, all without the need for travel. The flexibility of a virtual format allows participants to learn at their own pace and engage with the material in a comfortable environment.The primary benefit lies in the practical application of AppScan’s capabilities.
Participants aren’t just passively absorbing information; they actively participate in simulated security assessments, gaining a deep understanding of how to identify and mitigate vulnerabilities. This practical experience significantly enhances knowledge retention and translates directly into improved security practices.
Target Audience for AppScan Virtual Workshops
These workshops cater to a broad spectrum of professionals involved in software development and security. This includes software developers, security engineers, QA testers, penetration testers, and IT managers. Regardless of their specific role, anyone responsible for ensuring the security of applications will find these workshops invaluable. The training is tailored to provide relevant information and practical skills applicable to various experience levels.
API Discovery Workshop Agenda and Learning Objectives
An API discovery workshop typically covers the fundamental principles of API security testing, focusing on identifying and analyzing potential vulnerabilities within application programming interfaces. The agenda usually includes modules on automated API discovery techniques, leveraging AppScan’s capabilities to map out the application’s API landscape, and identifying common API vulnerabilities such as injection flaws, authentication weaknesses, and insecure data handling.
Participants learn to effectively use AppScan to uncover hidden endpoints and assess their security posture.The primary learning objective is to equip participants with the practical skills to perform comprehensive API security assessments using AppScan. Upon completion, attendees should be able to independently discover APIs, identify security vulnerabilities, and generate detailed reports for remediation. This empowers them to proactively address security risks associated with APIs, contributing to the overall security of the application ecosystem.
API Discovery Techniques
Uncovering the hidden APIs within an application is the crucial first step in securing it. AppScan provides several powerful methods for this discovery, allowing you to identify potential vulnerabilities before they can be exploited. This section will guide you through the process, highlighting the strengths and weaknesses of each approach.AppScan’s API discovery capabilities are multifaceted, leveraging various techniques to comprehensively map out the application’s exposed APIs.
Understanding these techniques and their outputs is key to effectively using AppScan for security testing. The different methods employed offer varying levels of depth and breadth in their analysis, allowing for a tailored approach depending on the complexity and nature of the target application.
AppScan’s API Discovery Workflow
The process of discovering APIs using AppScan typically involves these steps: First, you’ll define the scope of your scan, specifying the target URL(s) and any authentication requirements. Then, AppScan will initiate its automated crawling and analysis. During this phase, AppScan employs various techniques to identify potential API endpoints, including analyzing HTTP traffic, examining HTML source code for clues such as links and forms, and utilizing its built-in knowledge base of common API patterns.
Finally, AppScan presents the discovered APIs in a clear, organized report, detailing their characteristics and any identified vulnerabilities. The level of detail and the specific APIs discovered will depend on the chosen discovery method and the complexity of the application.
Comparison of API Discovery Methods in AppScan
AppScan offers several distinct API discovery methods, each with its own strengths and limitations. A crucial aspect of successful API security testing is selecting the appropriate method or combination of methods based on the characteristics of the target application.
| Method | Description | Strengths | Weaknesses |
|---|---|---|---|
| Static Analysis | Examines application code and configuration files to identify API endpoints. | Can discover APIs not readily apparent through dynamic analysis. Useful for identifying APIs hidden behind complex authentication schemes. | Requires access to application source code or build artifacts. May not discover dynamically generated APIs. |
| Dynamic Analysis | Analyzes network traffic and application behavior during runtime to identify API endpoints. | Can discover dynamically generated APIs and those hidden behind complex authentication. | Requires the application to be running and accessible. Can be slower than static analysis. |
| Hybrid Analysis | Combines static and dynamic analysis for a more comprehensive discovery. | Offers the broadest coverage, combining the strengths of both static and dynamic analysis. | Requires access to application source code or build artifacts and requires the application to be running. Can be resource-intensive. |
Examples of Common API Vulnerabilities Identified Through Discovery
API discovery is not merely about locating endpoints; it’s about identifying potential vulnerabilities. AppScan’s discovery process often uncovers security flaws such as:
- Missing Authentication: APIs lacking proper authentication mechanisms can be accessed and manipulated by unauthorized users.
- Broken Authentication: Weak or improperly implemented authentication schemes allow attackers to bypass security controls.
- Insufficient Authorization: APIs may grant excessive permissions, allowing users to perform actions they shouldn’t be able to.
- Sensitive Data Exposure: APIs might expose sensitive data, such as personally identifiable information or credentials, in their responses.
- Cross-Site Scripting (XSS): Vulnerabilities that allow attackers to inject malicious scripts into API responses, potentially compromising user sessions or data.
- SQL Injection: Flaws that allow attackers to manipulate database queries, potentially leading to data breaches or manipulation.
Discovering these vulnerabilities early in the development lifecycle allows for timely remediation, preventing costly security breaches and ensuring the overall security of the application. AppScan’s reporting capabilities provide detailed information on each vulnerability, making it easier to understand the risk and prioritize remediation efforts.
Secret and Key Vulnerability Identification: Get Hands On With Appscans Next Virtual Workshop Api Discovery Secret+key Vulnerable Components Scanning
AppScan’s robust security analysis extends beyond basic API discovery to actively hunt for exposed secrets and API keys, crucial components often overlooked in standard security assessments. These vulnerabilities, if left unaddressed, can severely compromise your application’s security and potentially expose sensitive data. This section delves into the methods AppScan utilizes to identify these weaknesses and the associated risks.AppScan employs several techniques to detect exposed secrets and API keys within your application’s codebase and configurations.
These techniques include static analysis, which examines the source code for hardcoded credentials or patterns indicative of sensitive information leakage. Dynamic analysis, on the other hand, monitors the application’s runtime behavior, identifying requests that transmit sensitive data without proper protection. Machine learning algorithms play a significant role, helping AppScan to identify patterns and anomalies that might indicate the presence of leaked secrets, even if they are obfuscated or encoded.
The system cross-references findings with known patterns of exposed secrets and API keys from its extensive database to improve accuracy and speed.
API Key Vulnerabilities and Associated Risks
Compromised API keys can lead to a multitude of security breaches. Unauthorized access to your APIs, data breaches, account takeovers, and service disruptions are just some of the potential consequences. Attackers can leverage leaked keys to perform actions such as manipulating data, deleting records, making unauthorized transactions, or even launching denial-of-service attacks. The severity of the impact depends heavily on the type of API key and the level of access it grants.
For instance, a key with administrative privileges poses a far greater risk than one with read-only access. The financial and reputational damage resulting from such breaches can be substantial.
Types of API Keys and Their Vulnerabilities
Understanding the different types of API keys and their associated vulnerabilities is crucial for effective mitigation. The following table provides a breakdown:
| Key Type | Vulnerability | Example | Mitigation Strategy |
|---|---|---|---|
| API Key (Simple String) | Easily stolen if hardcoded or exposed in client-side code. Susceptible to brute-force attacks if poorly implemented rate limiting is in place. | abcdef123456 |
Use strong, randomly generated keys. Store keys securely (never hardcode). Implement robust rate limiting and input validation. Utilize HTTPS for all API communication. |
| OAuth 2.0 Access Token | Vulnerable if refresh tokens are not properly secured or if the authorization server is compromised. | eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9... |
Use short-lived access tokens. Securely store refresh tokens. Implement robust authentication and authorization mechanisms. Regularly rotate tokens. |
| JWT (JSON Web Token) | Vulnerable to various attacks if not properly signed and verified. Exposure of the private key used for signing is catastrophic. | eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c |
Use strong algorithms for signing. Protect the private key. Validate the token’s signature and claims on every request. Implement token revocation mechanisms. |
| API Secret Key | Allows unauthorized access to resources and modification of data if compromised. Often used with HMAC-based signature authentication. | ThisIsASecretKey123! |
Use strong, randomly generated keys. Never expose in client-side code or logs. Implement secure key rotation and storage. Use HTTPS. |
Vulnerable Component Scanning
AppScan’s power lies not just in discovering APIs and identifying exposed secrets, but also in its ability to pinpoint vulnerable components within those APIs. Understanding these vulnerabilities is crucial for securing your application, and AppScan provides the tools to do just that. This section will delve into how AppScan identifies these weaknesses and the comparative strengths of different analysis methods.AppScan utilizes a combination of static and dynamic analysis techniques to identify vulnerable components.
Static analysis examines the application’s code without actually running it, looking for potential vulnerabilities based on coding patterns and library usage. Dynamic analysis, on the other hand, involves running the application and observing its behavior in a controlled environment to detect vulnerabilities during runtime. The combination of these approaches provides a more comprehensive view of the application’s security posture.
For example, static analysis might identify a known vulnerability in a specific library used by the API, while dynamic analysis could uncover unexpected behavior or runtime errors that lead to vulnerabilities.
Static and Dynamic Analysis Comparison
Static analysis is faster and can be performed earlier in the development lifecycle, often identifying vulnerabilities before deployment. However, it might miss vulnerabilities that only appear during runtime or are dependent on specific user inputs or environmental factors. Dynamic analysis, while slower and requiring a running application, provides a more realistic view of how the application behaves in real-world scenarios, revealing vulnerabilities that static analysis might overlook.
The ideal approach is often a combination of both, leveraging the strengths of each to achieve maximum coverage.
Common API Vulnerabilities
Understanding the types of vulnerabilities commonly found in APIs is vital for effective security testing. The following list Artikels some key vulnerabilities AppScan is designed to detect:
- SQL Injection: Occurs when malicious SQL code is injected into API inputs, potentially allowing attackers to access or modify database data. For example, an attacker might craft a request that includes SQL commands to retrieve sensitive information.
- Cross-Site Scripting (XSS): Allows attackers to inject malicious scripts into API responses, which are then executed by the user’s browser. This can lead to session hijacking or other attacks. A classic example is an API returning user data that includes unsanitized input from a user profile.
- Cross-Site Request Forgery (CSRF): Tricks a user into performing unwanted actions on a website they are already authenticated to. An API vulnerable to CSRF could allow an attacker to make unauthorized changes on behalf of a logged-in user.
- Broken Authentication and Session Management: Weak or improperly implemented authentication mechanisms can allow unauthorized access to API resources. This includes vulnerabilities like easily guessable passwords or insecure session handling.
- Sensitive Data Exposure: APIs might expose sensitive data such as passwords, API keys, or personally identifiable information (PII) without proper protection. This could be due to inadequate encryption or insecure storage.
- XML External Entities (XXE): This vulnerability allows attackers to read arbitrary files on the server or execute external code by manipulating XML input to the API. This often exploits the XML parser’s ability to access external resources.
- Insecure Deserialization: Occurs when an API deserializes untrusted data, potentially allowing attackers to execute arbitrary code. This is particularly dangerous if the deserialization process isn’t properly secured.
Practical Application
Let’s put AppScan’s API security analysis capabilities to the test with a practical example. We’ll examine a hypothetical, vulnerable API and walk through the scanning process, interpreting the results and formulating a remediation report. This will solidify your understanding of how to effectively leverage AppScan in real-world scenarios.This exercise uses a simplified, yet representative, API mimicking common vulnerabilities found in real-world applications.
The goal is not to analyze a complex, production-ready system, but rather to illustrate the workflow and interpretation of AppScan’s findings. We’ll focus on identifying vulnerabilities and understanding their severity, and suggest practical remediation steps.
Vulnerable API Scenario
Our hypothetical API, “ExampleAPI,” exposes endpoints for user authentication and data retrieval. It’s built using a common framework and includes several known vulnerabilities, such as SQL injection in the authentication endpoint and insecure direct object references (IDOR) in the data retrieval endpoint. We’ll use AppScan to identify these vulnerabilities. The API documentation (which would typically be available for a real API) details the available endpoints and their functionalities, allowing AppScan to systematically test each endpoint for vulnerabilities.
AppScan Scanning Process
First, we configure AppScan to target the ExampleAPI endpoints. This involves specifying the base URL and potentially providing authentication credentials if needed. AppScan’s automated scanning engine then begins its analysis. It will systematically crawl the API, following links and interacting with various endpoints. During this process, AppScan employs various techniques, such as fuzzing, to test for common vulnerabilities.
This automated process dramatically reduces the time and effort required compared to manual testing.
Results Interpretation and Reporting
Once the scan completes, AppScan presents a detailed report outlining identified vulnerabilities. Each vulnerability is categorized by severity (critical, high, medium, low), type, and location within the API. For example, the SQL injection vulnerability in the authentication endpoint might be flagged as “Critical,” indicating a high risk of data breach. The IDOR vulnerability, on the other hand, might be classified as “High,” signifying a potential risk of unauthorized data access.
The report will also provide detailed descriptions of each vulnerability, including the affected code segment (if available), the exploitability, and suggested remediation steps.
Remediation Report Example
| Vulnerability | Severity | Description | Remediation |
|---|---|---|---|
| SQL Injection (Authentication Endpoint) | Critical | Vulnerable to SQL injection attacks via the username parameter. | Implement parameterized queries or stored procedures to prevent SQL injection. Sanitize all user inputs. |
| Insecure Direct Object Reference (Data Retrieval Endpoint) | High | Allows unauthorized access to data based on manipulated object IDs. | Implement proper authorization checks and validation of object IDs before accessing data. |
The remediation report serves as a valuable guide for developers to address the identified vulnerabilities, thereby enhancing the overall security posture of the API. It is crucial to prioritize the remediation of critical and high-severity vulnerabilities first, given their potential impact. By following the suggested remediation steps, the identified weaknesses can be mitigated, reducing the risk of exploitation.
Security Best Practices for APIs
Building secure APIs is paramount in today’s interconnected world. Neglecting API security can lead to significant data breaches, financial losses, and reputational damage. This section Artikels crucial security best practices to help developers build robust and resilient APIs. These practices cover secure coding, authentication, authorization, and a secure development lifecycle.
Secure coding practices are fundamental to preventing API vulnerabilities. By adhering to these practices, developers significantly reduce the attack surface of their APIs, making them more resistant to exploitation. Robust authentication and authorization mechanisms are equally crucial for controlling access to API resources and preventing unauthorized access. A well-defined secure development lifecycle ensures that security is considered at every stage of the API’s development, from design to deployment and beyond.
Secure Coding Practices
Secure coding practices encompass a wide range of techniques designed to minimize vulnerabilities in API code. These practices help prevent common API security flaws such as injection attacks, cross-site scripting (XSS), and insecure direct object references (IDOR). Examples include input validation, output encoding, and the use of parameterized queries to prevent SQL injection. Regular code reviews and security testing are also essential parts of this process.
For instance, always validate user inputs to ensure they conform to expected formats and lengths. This prevents malicious code from being injected into the application. Sanitize all outputs to prevent cross-site scripting attacks. Employ parameterized queries to prevent SQL injection vulnerabilities by separating data from SQL code. Regularly conduct code reviews to identify potential security flaws early in the development process.
Employ static and dynamic application security testing (SAST and DAST) tools to automatically identify vulnerabilities.
Authentication and Authorization Mechanisms, Get hands on with appscans next virtual workshop api discovery secret+key vulnerable components scanning
Robust authentication and authorization are crucial for controlling access to API resources. Authentication verifies the identity of the client requesting access, while authorization determines what actions the authenticated client is permitted to perform. Common authentication mechanisms include OAuth 2.0, OpenID Connect (OIDC), and API keys. Authorization can be implemented using roles, permissions, or attribute-based access control (ABAC).
OAuth 2.0 is a widely used authorization framework that allows third-party applications to access user data without requiring the user to share their credentials. API keys provide a simpler authentication method, but they require careful management to prevent unauthorized access. Implementing robust authorization mechanisms, such as role-based access control (RBAC), ensures that only authorized users can access specific API resources and perform certain actions.
For example, a system administrator might have full access, while a regular user might only have read-only access.
Secure API Development and Deployment Flowchart
The following describes a flowchart illustrating a secure API development and deployment process:
The flowchart begins with the Requirements Gathering phase, where security requirements are defined. This is followed by API Design, incorporating security best practices from the outset. The Development phase includes secure coding practices and regular security testing. Testing involves both unit and integration tests focusing on security aspects. Deployment includes secure configuration of servers and infrastructure.
Finally, Monitoring and Maintenance involves continuous monitoring for security threats and regular updates to address vulnerabilities. Each phase feeds into the next, creating a continuous cycle of secure API development and maintenance. This iterative process ensures that security is built into the API from its inception and maintained throughout its lifecycle.
Remediation Strategies for Discovered Vulnerabilities

Addressing API vulnerabilities is crucial for maintaining the security and integrity of your applications. A proactive approach to remediation, involving careful planning and execution, is essential to minimize risk and ensure the long-term stability of your systems. This involves understanding the nature of the vulnerability, selecting the appropriate fix, and thoroughly testing the implemented solution.Identifying and fixing vulnerabilities is a multi-step process.
It’s not just about patching code; it’s about understanding the underlying weaknesses in your API design and implementation. This section details the strategies for effectively addressing discovered API vulnerabilities.
Patching Vulnerable Components and Updating Dependencies
Patching vulnerable components involves applying security updates provided by vendors or developers to address known vulnerabilities. This often requires updating libraries, frameworks, and other dependencies used within your API. The process typically involves identifying the outdated components, downloading the latest versions from trusted sources, and then integrating them into your application’s codebase. Thorough testing after patching is vital to ensure the updates haven’t introduced new issues or broken existing functionality.
A robust version control system, such as Git, is essential for tracking changes and reverting to previous versions if problems arise.
Common Vulnerabilities and Remediation Techniques
The following table summarizes common API vulnerabilities and their corresponding remediation techniques. Understanding these techniques is key to effectively mitigating risks.
| Vulnerability | Severity | Remediation Steps | Example |
|---|---|---|---|
| SQL Injection | Critical | Use parameterized queries or prepared statements; validate and sanitize all user inputs; employ an ORM (Object-Relational Mapper) to abstract database interactions. | An attacker crafts a malicious SQL query to access sensitive data by injecting it into an input field. Remediation involves using parameterized queries to prevent the injection of malicious code. |
| Cross-Site Scripting (XSS) | High | Encode or escape all user-supplied data before displaying it on the web page; use a Content Security Policy (CSP) to restrict the execution of untrusted scripts; validate and sanitize all user inputs. | An attacker injects malicious JavaScript code into a web page, allowing them to steal cookies or redirect users to malicious websites. Remediation involves encoding user inputs to prevent the execution of malicious scripts. |
| Broken Authentication and Session Management | High | Use strong password policies; implement multi-factor authentication (MFA); regularly rotate API keys and secrets; use secure session management techniques; properly handle session timeouts. | An attacker guesses or cracks passwords to gain unauthorized access to the API. Remediation involves implementing strong password policies and MFA to prevent unauthorized access. |
| Sensitive Data Exposure | High | Encrypt sensitive data both in transit and at rest; use strong encryption algorithms; avoid storing sensitive data unnecessarily; implement access control mechanisms to restrict access to sensitive data. | An attacker gains access to sensitive data such as credit card numbers or personally identifiable information (PII). Remediation involves encrypting sensitive data to protect it from unauthorized access. |
| Lack of Authorization | High | Implement role-based access control (RBAC); use access tokens and authorization headers to verify user permissions; validate user roles and permissions before granting access to resources. | An attacker gains access to resources they are not authorized to access. Remediation involves implementing RBAC to restrict access to resources based on user roles. |
| Broken Object Level Authorization | Medium | Validate user permissions for each specific resource accessed; avoid relying on client-side validation; use server-side validation to enforce access control. | An attacker manipulates object IDs to access resources they are not authorized to access. Remediation involves implementing server-side validation to ensure users only access resources they are authorized to access. |
Post-Workshop Resources and Continued Learning
The AppScan virtual workshop provided a solid foundation in API security. However, the field is constantly evolving, so continued learning and staying updated with the latest threats and best practices is crucial for any security professional. This section Artikels resources to help you further your knowledge and expertise in API security. We also detail the ongoing support available to workshop participants.This section details resources for continued learning, support options following the workshop, and relevant industry standards and best practices.
These resources are designed to empower you to effectively protect your APIs from evolving threats.
Available Support Options
Following the workshop, participants have access to a dedicated online forum where they can connect with instructors and fellow participants to ask questions, share experiences, and discuss challenges encountered in implementing the learned techniques. This forum provides a collaborative environment for continued learning and problem-solving. Additionally, we offer a limited period of email support for any technical queries or clarification requests related to the workshop materials.
This ensures you have the support you need to successfully apply what you’ve learned.
Relevant Industry Standards and Best Practices
Adhering to industry standards and best practices is paramount for ensuring the security of your APIs. These standards provide a framework for building secure and reliable APIs, mitigating risks, and promoting interoperability. Here are some key standards and best practices to consider:
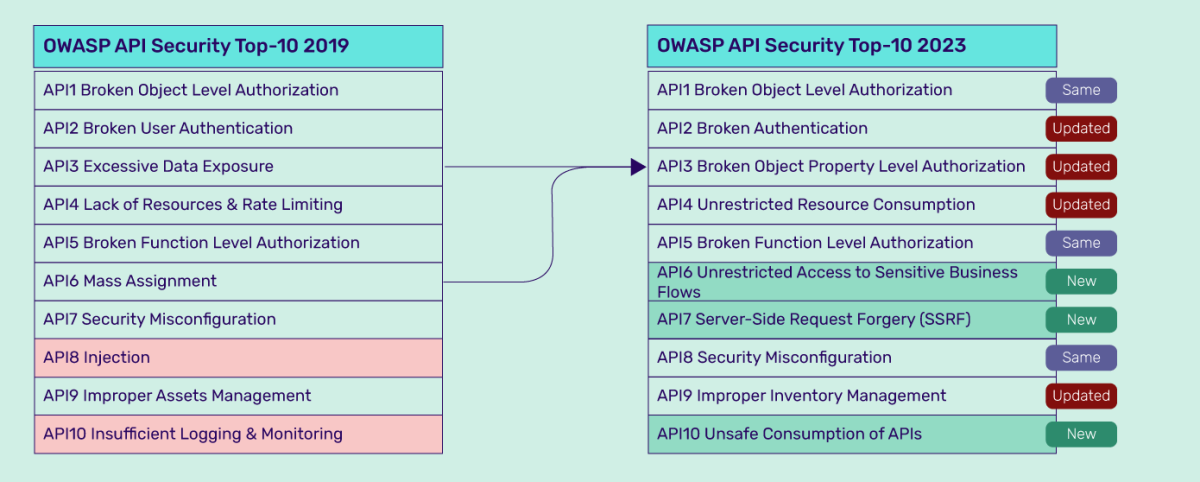
- OWASP API Security Top 10: This widely recognized list Artikels the most critical security risks associated with APIs. Understanding and addressing these risks is crucial for building secure APIs. The OWASP API Security Top 10 is regularly updated to reflect the latest threats and vulnerabilities.
- NIST Cybersecurity Framework: The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a comprehensive approach to managing cybersecurity risk. Its principles and guidelines can be applied to secure API development and deployment.
- OAuth 2.0 and OpenID Connect: These open standards provide a robust framework for secure authorization and authentication of API users, mitigating risks related to unauthorized access.
- HTTPS: Always use HTTPS to encrypt communication between clients and APIs. This protects sensitive data from eavesdropping and tampering.
- Input Validation and Sanitization: Thoroughly validate and sanitize all input received by your APIs to prevent injection attacks such as SQL injection and cross-site scripting (XSS).
Resources for Continued Learning
Numerous resources are available to further your knowledge of API security. These include online courses, certifications, books, and industry conferences.
- Online Courses: Platforms like Coursera, edX, and Udemy offer various courses on API security, covering topics from basic principles to advanced techniques.
- Certifications: Obtaining relevant certifications, such as the Certified Information Systems Security Professional (CISSP) or the Offensive Security Certified Professional (OSCP), demonstrates expertise in the field and enhances career prospects.
- Books: Several books delve into the intricacies of API security, providing in-depth knowledge and practical guidance.
- Industry Conferences: Attending industry conferences like Black Hat, RSA Conference, and OWASP AppSec conferences offers opportunities to network with experts, learn about the latest trends, and stay updated on emerging threats.
Last Point
By the end of this AppScan virtual workshop, you won’t just understand API security—you’ll be able to actively protect your applications. You’ll walk away with practical skills, a deeper understanding of API vulnerabilities, and the confidence to implement robust security measures. This isn’t just about theory; it’s about gaining the hands-on experience you need to make a real difference in securing your APIs.
So, buckle up and get ready to level up your API security game!
Frequently Asked Questions
What prior knowledge is needed to attend this workshop?
Basic understanding of APIs and web application security concepts is helpful but not mandatory. The workshop is designed to be accessible to a broad audience.
Will there be opportunities for Q&A during the workshop?
Absolutely! There will be dedicated Q&A sessions throughout the workshop to address your questions and concerns.
What kind of tools will be used during the workshop?
The primary tool used will be AppScan. No other specialized software is required.
Will I receive a certificate of completion?
Yes, participants will receive a certificate upon successful completion of the workshop.
What if I miss a part of the workshop?
Workshop materials and recordings will be provided to attendees, allowing you to catch up on any missed sessions.