Getting Started with BigFix
Getting Started with BigFix: So you’re diving into the world of BigFix, huh? That’s awesome! This powerful endpoint management system can seem daunting at first, but trust me, with a little guidance, you’ll be deploying Fixlets and managing your fleet like a pro in no time. This post will walk you through the essential steps, from installation and setup to creating your first Fixlet and managing your clients.
Prepare for a journey into efficient system administration!
We’ll cover everything from the basic installation process on a Windows server (with helpful screenshots, of course!) to navigating the BigFix console, building your first Fixlet, and managing your client machines effectively. We’ll also touch on essential security considerations and reporting features. By the end, you’ll have a solid foundation for leveraging BigFix’s power in your environment.
BigFix Installation and Setup
Getting BigFix up and running is the first crucial step in leveraging its powerful patch management and endpoint security capabilities. This guide will walk you through the installation process on a Windows server, covering prerequisites and post-installation configuration. Remember to always consult the official BigFix documentation for the most up-to-date information and best practices.
BigFix Server Prerequisites
Successful BigFix server installation hinges on meeting specific system requirements. These requirements vary slightly depending on the operating system you choose. Failure to meet these prerequisites can lead to installation failures or performance issues. The following table summarizes the minimum system requirements for different operating systems. Note that these are minimum requirements; more resources are recommended for larger deployments.
| Operating System | Processor | RAM | Hard Disk Space | Database |
|---|---|---|---|---|
| Windows Server 2019/2022 | 64-bit processor with at least 2 cores | 8 GB | 50 GB | SQL Server (supported version specified in BigFix documentation) |
| Linux (e.g., Red Hat Enterprise Linux, CentOS, Ubuntu) | 64-bit processor with at least 2 cores | 8 GB | 50 GB | PostgreSQL (supported version specified in BigFix documentation) or other supported databases |
BigFix Installation on Windows Server
The BigFix installation process on Windows is relatively straightforward. The following steps Artikel the procedure. Remember that the specific steps and screens might vary slightly depending on the BigFix version.
- Download the BigFix Installer: Download the appropriate installer package from the IBM BigFix website. Ensure you download the installer suitable for your Windows Server version.
- Run the Installer: Double-click the downloaded installer file to begin the installation process. The installer will guide you through a series of screens.
- Specify Installation Directory: Choose a suitable directory for the BigFix server installation. The default location is usually acceptable.
- Database Configuration: You will need to specify the database connection details (server name, instance name, database name, username, password). Ensure the database is properly configured and accessible before proceeding. This usually involves pre-installing and configuring a supported SQL Server instance.
- Review and Install: Review the installation settings and click “Install” to begin the installation. The installer will copy files and configure the necessary components.
- Post-Installation Tasks: After successful installation, the installer might prompt you to perform post-installation tasks, such as configuring the server’s web server and network settings.
A typical screenshot of the database configuration screen would show input fields for the SQL Server name, instance name, database name, username, and password. Error handling would be visible if the database connection details are incorrect. The installer usually provides helpful prompts and error messages to guide the user.
BigFix Server Configuration
After the installation is complete, several key configuration tasks need to be performed to ensure the BigFix server functions correctly. These tasks include:
- Web Server Configuration: Configure the built-in web server to allow clients to connect and communicate with the BigFix server. This usually involves checking the server’s firewall rules and ensuring the correct ports are open.
- Database Connection Verification: Verify that the BigFix server has successfully connected to the database and that data can be written and read correctly. Check the server logs for any connection errors.
- Initial Client Enrollment: Enroll at least one client computer to test the server’s functionality and verify that clients can successfully communicate with the server and receive tasks. This process usually involves generating a client installation package and installing it on a test client machine.
- Security Settings: Configure appropriate security settings to protect the BigFix server and its data from unauthorized access. This includes setting up user accounts and access control lists (ACLs).
Understanding the BigFix Console
So, you’ve successfully installed BigFix! Now comes the fun part – actually using it. The BigFix Console is your central command center for managing endpoints and deploying fixes. It can seem daunting at first, but with a little guidance, you’ll be navigating its features like a pro in no time. This section will walk you through the key components and functionalities.
BigFix Console User Interface Components
The BigFix Console’s interface is designed to provide a comprehensive overview of your managed endpoints and allow for efficient task management. Understanding its key components is crucial for effective use. The following table breaks down the major sections:
| Component | Description | Functionality | Example |
|---|---|---|---|
| Navigation Pane | The left-hand sidebar, providing access to different sections of the console. | Allows quick switching between tasks, such as viewing computers, creating actions, or managing reports. | Clicking “Computers” displays a list of all managed endpoints; clicking “Actions” shows active and completed tasks. |
| Main Workspace | The central area where the selected content is displayed. | Shows the details of the selected item from the navigation pane, such as computer properties, action details, or report data. | Viewing the properties of a specific computer, such as its operating system and last check-in time. |
| Toolbar | A row of icons and buttons at the top, providing quick access to common functions. | Provides shortcuts for actions like creating new actions, running reports, or refreshing the view. | The “New Action” button initiates the process of creating a new task. |
| Status Indicators | Visual cues, such as colors and icons, used to display the status of different elements. | Provides at-a-glance information about the health of your system and the progress of tasks. | Green checkmarks indicate successful actions, while red crosses indicate failures. |
Navigating the BigFix Console
Efficient navigation is key to maximizing your BigFix experience. Follow these steps to access various functionalities:
- Log in: Access the BigFix Console through your web browser using the provided URL and credentials.
- Select a Section: Use the navigation pane on the left to choose the desired section (e.g., Computers, Actions, Reports).
- Filter and Sort: Utilize the filtering and sorting options within each section to refine your view and find specific information.
- Drill Down: Click on specific items to view detailed information. For example, selecting a computer from the “Computers” section will show its properties and actions.
- Use Search: The search bar allows you to quickly find specific computers, actions, or other elements.
Creating a New Action in the BigFix Console
Creating actions is how you deploy fixes and manage your endpoints. This process involves defining the task, targeting specific computers, and scheduling execution.
- Access the Actions Section: Navigate to the “Actions” section in the BigFix Console.
- Click “New Action”: Locate and click the “New Action” button (usually in the toolbar).
- Select Action Type: Choose the type of action you want to perform (e.g., run a script, install software, collect data).
- Define Action Details: Provide the necessary information for your chosen action type. This might include specifying the script to run, the software package to install, or the data to collect.
- Target Computers: Specify the computers or groups of computers that should receive this action. You can use filters to target specific operating systems, versions, or other criteria.
- Schedule Execution: Determine when the action should run (immediately, scheduled for a specific time, or recurring).
- Review and Submit: Review all the details to ensure accuracy before submitting the action. Once submitted, BigFix will begin to deploy the action to the targeted computers.
Creating and Deploying a Simple Fixlet

So, you’ve got BigFix up and running, and you’re ready to start automating tasks. The heart of BigFix lies in its Fixlets – these are the scripts that allow you to remotely manage and control your endpoints. Let’s create a simple Fixlet to install a software package, walking through the process step-by-step. We’ll then explore best practices and deployment strategies.
Our example Fixlet will install 7-Zip, a popular file archiver. This process is easily adaptable to other software packages, requiring only adjustments to the download URL and installation commands.
Fixlet Code and Explanation
Here’s the Fixlet code. We’ll break down each section afterwards.
Install 7-Zip
Installs the 7-Zip archiving utility.
true
Download and Install 7-Zip
Let’s dissect this Fixlet:
<title>Install 7-Zip</title>: This is the human-readable name of the Fixlet. Keep it concise and descriptive.<description>Installs the 7-Zip archiving utility.</description>: Provides a more detailed explanation of the Fixlet’s purpose.<relevance>true</relevance>: This determines which clients the Fixlet applies to. “true” means it applies to all clients. We’ll modify this later for targeted deployment.<actions>: This section contains the actions the Fixlet performs.<action>: Defines a single action.<script>: Contains the actual BigFix script. This uses BigFix’s built-in functions:download_file(): Downloads the 7-Zip installer to the temporary directory.wait: Pauses execution until the download completes.run_command(): Executes the installer with the /S switch for silent installation. Adjust this based on your installer’s command-line options.delete_file(): Removes the installer from the temporary directory after installation.
Best Practices for Writing Effective and Efficient Fixlets
Writing robust and maintainable Fixlets is crucial for effective endpoint management. Here are some key best practices:
- Use descriptive names and descriptions: Makes it easy to understand the Fixlet’s purpose.
- Keep Fixlets focused on a single task: Avoid creating overly complex Fixlets that perform multiple unrelated actions. This improves maintainability and debugging.
- Use appropriate relevance statements: Target Fixlets to specific groups of machines to avoid unnecessary deployments.
- Handle errors gracefully: Include error handling in your scripts to prevent unexpected behavior. Log errors for debugging purposes.
- Test thoroughly: Before deploying to production, test your Fixlets in a test environment to ensure they work as expected.
- Use version control: Track changes to your Fixlets over time. This helps manage different versions and roll back if necessary.
Deploying a Fixlet to a Specific Group, Getting started with bigfix
Deploying a Fixlet to a specific group involves targeting the Fixlet to a specific computer group within the BigFix console. This ensures only the selected machines receive the Fixlet.
In the BigFix console, navigate to the Fixlet you’ve created. You’ll see options to specify target groups. These groups are typically defined based on operating system, location, or other relevant criteria. Select the appropriate group and deploy the Fixlet. You can monitor the deployment status within the console, observing which machines have successfully received and executed the Fixlet.
Managing Client Computers with BigFix
Getting your client machines smoothly integrated into the BigFix infrastructure and maintaining their compliance is crucial for effective system management. This section delves into the practical aspects of onboarding new clients and managing their compliance status, along with troubleshooting common problems.
Onboarding New Client Machines
Adding new machines to your BigFix environment is straightforward, primarily achieved through the installation of the BigFix client agent. This agent acts as the communication bridge between the individual client machine and the BigFix server. There are several methods for deployment, each with its own advantages depending on your infrastructure and scale.
- Manual Installation: This involves downloading the BigFix client installer from the BigFix server and running it directly on each machine. This method is best suited for small deployments or situations where automated deployment isn’t feasible. It provides granular control over the installation process but lacks scalability.
- Automated Deployment via Group Policy (Windows): Leveraging Active Directory Group Policy, you can deploy the BigFix client installer silently to all machines within a specific organizational unit. This method is highly efficient for large Windows-based environments and ensures consistent client installation across multiple machines. Configuration requires familiarity with Group Policy settings.
- Automated Deployment via SCCM (Windows): System Center Configuration Manager (SCCM) can be used to deploy the BigFix client as an application. This provides a centralized management point for both software distribution and client agent deployment. This method integrates well with existing SCCM infrastructure.
- BigFix Relay Deployment: For large or geographically dispersed environments, using BigFix relays is crucial. Relays act as intermediary points, improving communication between clients and the main server, especially in environments with unreliable network connections. This approach minimizes latency and improves reliability of communication.
Managing Client Compliance
Monitoring and enforcing compliance with deployed Fixlets is a core function of BigFix. Different approaches offer varying levels of control and automation.
| Method | Description | Advantages | Disadvantages |
|---|---|---|---|
| Relevance Evaluation | BigFix regularly evaluates the relevance of Fixlets on each client. This determines whether a Fixlet applies to a given machine. | Provides a real-time view of compliance. | Doesn’t enforce compliance; only reports the status. |
| Action Scheduling | Fixlets can be scheduled to run at specific times or intervals. | Allows for automated remediation at convenient times. | Requires careful scheduling to avoid conflicts or disruptions. |
| Forced Actions | Administrators can manually trigger actions on specific clients or groups. | Provides immediate remediation for critical issues. | Less efficient for large-scale deployments; requires manual intervention. |
| Compliance Reporting | BigFix provides comprehensive reporting on client compliance status. | Allows for proactive identification of compliance issues. | Requires regular review and analysis of reports. |
Troubleshooting Common Client Issues
Several factors can hinder the proper functioning of BigFix clients. Addressing these issues proactively ensures smooth operation.
- Communication Problems: Verify network connectivity between the client and the BigFix server (or relay). Check firewalls for any blocking rules. Ensure the BigFix port (typically 52311) is open.
- Agent Status: Regularly monitor the BigFix client agent status on each machine. Look for error messages in the agent logs. Restarting the agent can often resolve temporary issues.
- Fixlet Relevance: Ensure that the Fixlet’s relevance statement accurately targets the intended client machines. Incorrect relevance can lead to Fixlets not applying when they should.
- Action Failures: Examine the detailed logs for failed actions to identify the root cause. Common causes include insufficient permissions, missing prerequisites, or conflicts with other software.
- Client Agent Version: Keep the BigFix client agent updated to the latest version. Outdated agents can have compatibility issues and security vulnerabilities.
Reporting and Analysis in BigFix: Getting Started With Bigfix
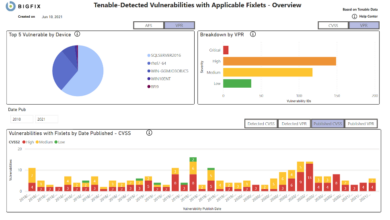
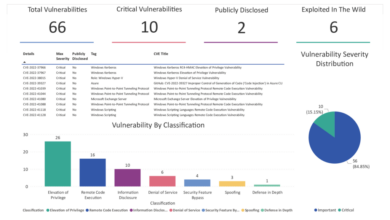
BigFix’s robust reporting capabilities are crucial for understanding the health and security posture of your managed endpoints. By leveraging its reporting features, you can gain valuable insights into software deployments, patch compliance, and overall system health, allowing for proactive remediation and improved IT efficiency. This section will explore the creation, customization, and various types of reports available within the BigFix console.
Generating a Compliance Report for a Specific Fixlet
To illustrate report generation, let’s create a report showing the compliance status of client machines for a specific Fixlet – let’s assume it’s a Fixlet designed to ensure the installation of a critical security patch. First, navigate to the “Reports” section within the BigFix console. Then, select “Create Report.” You’ll be presented with a report builder. Choose the “Compliance” report type.
In the “Fixlet” selection field, choose the specific Fixlet (the security patch Fixlet in this case). You can further refine the report by selecting specific computer groups or using advanced filtering options. Once your criteria are set, run the report. The resulting report will display a list of all managed computers, indicating whether they are compliant or non-compliant with the selected Fixlet.
The report might include details like the computer name, operating system, last check-in time, and the status of the relevant action. For example, a report might show 95% compliance, listing the non-compliant machines and reasons for non-compliance.
Customizing BigFix Reports
Customizing BigFix reports allows tailoring them to meet your organization’s specific needs and reporting requirements. This ensures that the reports provide the precise information necessary for effective decision-making.
- Selecting Relevant Data Points: Choose which attributes of your endpoints to include in the report. For instance, you might only need to see the computer name and compliance status, or you might want to include operating system version, patch level, and last login time.
- Filtering and Grouping: Filter results based on various criteria, such as operating system, computer group, or compliance status. You can also group results by these criteria for easier analysis. For example, group computers by OS version to see patch compliance rates for each version.
- Report Scheduling: Automate report generation and delivery on a schedule (daily, weekly, etc.). This allows for regular monitoring of compliance and proactive identification of potential issues.
- Exporting Reports: Export reports in various formats (CSV, PDF, HTML) for easy sharing and integration with other systems. This facilitates sharing of compliance data with relevant stakeholders.
- Using Advanced Query Language: BigFix’s powerful query language enables creating highly customized reports to meet very specific requirements. This allows you to retrieve and display data that isn’t readily available in standard reports.
Types of BigFix Reports and Their Uses
BigFix offers a variety of report types, each serving a distinct purpose in managing and analyzing your endpoint environment.
| Report Type | Description | Use Cases |
|---|---|---|
| Compliance | Shows the compliance status of clients against specific Fixlets or tasks. | Monitoring patch compliance, software deployment success, security policy adherence. |
| Inventory | Provides a detailed inventory of software, hardware, and operating system information on managed endpoints. | Software license management, hardware asset tracking, capacity planning. |
| Custom Reports | Allows for the creation of reports tailored to specific organizational needs using BigFix’s query language. | Tracking specific metrics, analyzing custom data points, generating reports for auditing purposes. |
| Action History | Tracks the execution history of actions performed on client computers. | Troubleshooting issues, auditing changes made to endpoints, verifying successful deployments. |
| Computer Status | Provides an overview of the overall health and status of managed computers. | Identifying problematic machines, monitoring system performance, proactive maintenance. |
BigFix Security Considerations
Securing your BigFix infrastructure is paramount to maintaining the integrity of your managed systems. A compromised BigFix server could grant attackers extensive control over your entire network. This section Artikels crucial security best practices and mitigation strategies to help you build a robust and secure BigFix environment.
Effective security relies on a multi-layered approach, encompassing server hardening, client protection, and meticulous access control. By implementing these measures, you significantly reduce the risk of unauthorized access and malicious activity.
BigFix Server and Client Infrastructure Hardening Best Practices
Protecting your BigFix server and clients requires a proactive approach, encompassing both software and physical security. The following best practices minimize the attack surface and enhance overall security.
- Regular Software Updates: Keep the BigFix server and all clients patched with the latest security updates. This addresses known vulnerabilities and reduces the risk of exploitation.
- Strong Passwords and Authentication: Enforce strong, unique passwords for all BigFix accounts, and utilize multi-factor authentication (MFA) wherever possible. Consider password managers to assist with this.
- Network Segmentation: Isolate the BigFix server on a dedicated, secure network segment, limiting its exposure to external threats. Restrict network access using firewalls.
- Regular Security Audits and Penetration Testing: Conduct periodic security audits and penetration testing to identify and address potential vulnerabilities before attackers can exploit them. These assessments should include both the server and client components.
- Firewall Configuration: Configure firewalls to restrict access to the BigFix server and only allow necessary ports and protocols. This prevents unauthorized access attempts.
- Intrusion Detection/Prevention System (IDS/IPS): Implement an IDS/IPS to monitor network traffic for malicious activity and block potential attacks targeting the BigFix server and clients.
- Regular Backups: Implement a robust backup and recovery strategy for the BigFix server and database. This ensures business continuity in case of a disaster or security breach.
Access Control and User Permissions
Implementing granular access control is essential to prevent unauthorized modifications and actions within the BigFix environment. Properly configured permissions ensure that only authorized personnel can perform specific tasks.
BigFix allows for the creation of different user roles with varying levels of permissions. These roles can be assigned to specific users or groups, allowing for fine-grained control over access to actions such as creating fixlets, deploying actions, and viewing reports. The BigFix console provides a user-friendly interface for managing these roles and permissions. For instance, you might create a role for administrators with full access, a role for help desk personnel with limited access to only deploy pre-approved fixlets, and a role for read-only access for reporting purposes.
These roles should be carefully designed to adhere to the principle of least privilege, granting only the necessary access for each role.
BigFix Security Vulnerabilities and Mitigation Strategies
While BigFix is a robust platform, it’s crucial to be aware of potential vulnerabilities and implement appropriate mitigation strategies. The following table Artikels some common vulnerabilities and their corresponding mitigations.
| Vulnerability | Mitigation Strategy |
|---|---|
| Unpatched BigFix Server/Client Software | Implement a robust patching schedule and utilize automated patching mechanisms to ensure all components are up-to-date with the latest security updates. |
| Weak Passwords | Enforce strong password policies, including password complexity requirements, regular password changes, and the use of multi-factor authentication (MFA). |
| Lack of Network Segmentation | Isolate the BigFix server on a dedicated network segment with restricted access to prevent unauthorized access from other parts of the network. |
| Improper Access Control | Implement granular access control using roles and permissions to limit user access to only necessary functionalities. Regularly review and update access rights as needed. |
| Unsecured Communication Channels | Use HTTPS for all communication between the BigFix server and clients to encrypt data in transit and protect against eavesdropping. |
Final Summary
Embarking on your BigFix journey is like unlocking a powerful toolkit for managing your IT infrastructure. While the initial learning curve might seem steep, remember the rewarding experience of streamlining your system administration tasks and improving overall efficiency. From installing the server to crafting and deploying Fixlets, each step brings you closer to mastering this invaluable tool. Don’t hesitate to explore the advanced features and dive deeper into BigFix’s capabilities – your efficient IT management future awaits!
FAQ Compilation
What are the minimum hardware requirements for a BigFix server?
The exact requirements depend on your environment’s scale, but generally, a reasonably modern server with sufficient RAM and disk space will suffice. Check the official BigFix documentation for detailed specifications.
How often should I update my BigFix server?
Regular updates are crucial for security and performance. Follow IBM’s recommended update schedule and patch releases diligently.
What if a client machine fails to connect to the BigFix server?
Troubleshooting involves checking network connectivity, firewall rules, and the client’s BigFix agent configuration. Review BigFix logs for error messages to pinpoint the problem.
Can I use BigFix to manage non-Windows machines?
Yes, BigFix supports various operating systems including macOS, Linux, and others. You’ll need to use appropriate Fixlets and configurations for each platform.