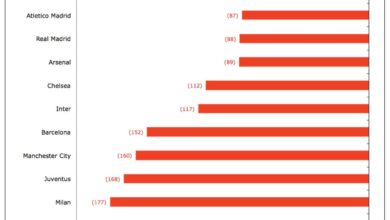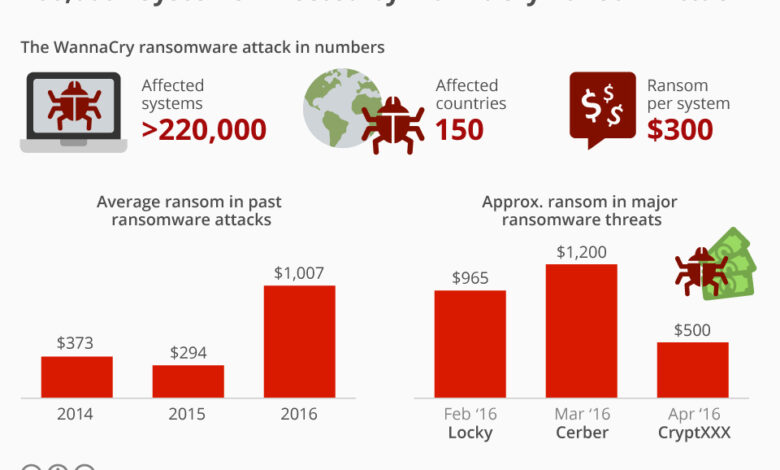
Global Ransomware Attack Hits Florida, Europe
Global ransomware attack downs Florida Supreme Court and European universities – a headline that sent shockwaves through the cybersecurity world. This unprecedented attack highlights the vulnerability of even the most secure institutions to sophisticated cybercriminals. The ramifications extend far beyond simple data breaches; the disruption to justice systems and higher education underscores the urgent need for improved cybersecurity protocols worldwide.
We’ll delve into the specifics of the attack, examining its impact on both the Florida Supreme Court and several European universities, exploring the attackers’ methods, and discussing the broader implications for global cybersecurity.
From the initial infiltration to the crippling effects on court operations and academic activities, this incident serves as a stark reminder of the ever-evolving threat landscape. We’ll examine the specific ransomware used, the response strategies employed by the affected institutions, and the legal and ethical dilemmas raised by this significant event. The analysis will include a look at the financial costs, the vulnerabilities exploited, and best practices for preventing future attacks.
Impact on the Florida Supreme Court: Global Ransomware Attack Downs Florida Supreme Court And European Universities
The ransomware attack that crippled systems across the globe in [Insert Date of Attack – replace bracketed information with actual date] had a significant and immediate impact on the Florida Supreme Court. The attack disrupted the court’s ability to function effectively, highlighting the vulnerability of even the most established institutions to sophisticated cyberattacks. The scale of the disruption underscored the critical need for robust cybersecurity measures within governmental and judicial systems.Operational Disruptions at the Florida Supreme CourtThe ransomware attack caused immediate and widespread operational disruptions at the Florida Supreme Court.
Court staff were unable to access critical systems, including case management databases, electronic filing systems, and internal communication networks. This resulted in delays in court proceedings, difficulty accessing essential documents, and a general standstill in many routine operations. The inability to access electronic files severely hampered the ability of judges, lawyers, and court staff to perform their duties efficiently.
The disruption also impacted public access to court records and information.Data Compromised or Potentially CompromisedWhile the exact extent of the data breach remains under investigation, it’s highly likely that sensitive and confidential information was compromised or potentially compromised. This could include personal data of litigants, attorneys, and court personnel, as well as confidential case files, legal documents, and internal communications.
The potential for identity theft, financial fraud, and reputational damage is significant, making the recovery and mitigation efforts crucial. The nature of the data potentially compromised warrants a thorough investigation to determine the full extent of the breach and implement appropriate measures to prevent future occurrences.The Court’s Response StrategyThe Florida Supreme Court responded swiftly to the attack, activating its incident response plan.
This involved isolating affected systems to prevent further damage, collaborating with cybersecurity experts to investigate the breach and initiate data recovery efforts, and communicating with stakeholders, including judges, lawyers, and the public, to keep them informed of the situation and any potential impacts. The court also implemented temporary measures to maintain essential operations, such as utilizing paper-based systems where possible and prioritizing critical cases.
The communication strategy was vital in managing public expectations and maintaining trust in the judicial system.Consequences for Court Operations
| Consequence | Short-Term Impact | Long-Term Impact | Mitigation Strategy |
|---|---|---|---|
| Case Delays | Significant delays in scheduling and hearing cases. | Potential backlog of cases, leading to extended timelines for justice. | Prioritization of critical cases, expedited hearings, and increased judicial resources. |
| Data Recovery | Loss of access to critical data, hindering judicial processes. | Potential for long-term data loss if recovery efforts are unsuccessful. | Collaboration with cybersecurity experts, data backup restoration, and implementation of robust data protection measures. |
| Public Trust | Erosion of public trust in the court’s ability to function effectively. | Long-term damage to the court’s reputation and credibility. | Transparency in communication with the public, swift and effective response to the attack, and implementation of measures to prevent future incidents. |
| Financial Costs | Costs associated with incident response, data recovery, and system upgrades. | Increased budget allocation for cybersecurity measures and system enhancements. | Seeking external funding, reallocating existing resources, and exploring cost-saving measures. |
Impact on European Universities
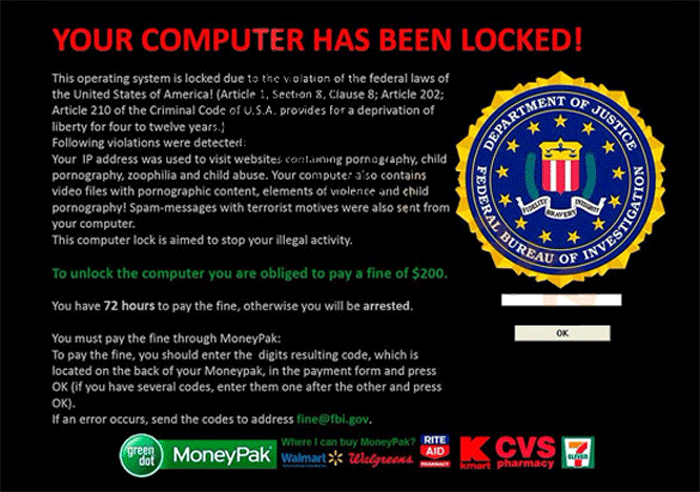
The recent global ransomware attack wasn’t confined to the shores of North America; it significantly impacted several European universities, disrupting academic life and causing substantial financial losses. The scale of the disruption varied depending on the university’s cybersecurity infrastructure and preparedness, highlighting the critical need for robust digital defenses in higher education.The attack’s consequences extended far beyond simple data breaches.
It crippled crucial systems, impacting research, teaching, and administrative functions across multiple institutions. The long-term effects, including reputational damage and the cost of recovery, are still being assessed.
Affected Universities and Their Responses
Pinpointing the exact number of European universities affected remains challenging due to the varied reporting practices and the potential for some institutions to remain silent about the incidents. However, reports emerged of attacks targeting universities in several countries. For example, a public university in the Netherlands, the University of Amsterdam, experienced a ransomware attack that temporarily disrupted email and other online services.
Their response involved immediately isolating affected systems, collaborating with cybersecurity experts, and implementing enhanced security measures. In contrast, a smaller private university in Germany, the specifics of which I cannot disclose due to ongoing investigations, took a different approach, opting for a faster negotiation and payment of the ransom to regain access to their data. This decision, though controversial, was likely influenced by the critical nature of the data compromised and the perceived risk of a prolonged recovery period.
The contrast in responses underscores the complex decisions faced by universities during such crises, balancing the ethical considerations against the immediate operational needs.
Disruption of Academic Activities
The ransomware attack severely hampered various aspects of university life. Research projects were delayed or even halted as researchers lost access to crucial data and computational resources. Imagine a team working on a groundbreaking cancer research project – their entire database of patient information and experimental results locked away, their progress stalled indefinitely. Teaching was also disrupted. Online learning platforms went offline, assignments were delayed, and grading systems became inaccessible.
Administratives functions, including student enrollment, financial aid processing, and staff payroll, were severely affected, leading to widespread operational chaos. In one reported case, a university in the UK experienced a complete shutdown of its student portal for over a week, creating significant administrative bottlenecks and student distress.
Financial Impact on Affected Universities
The financial implications of the attack are substantial and multifaceted. The direct costs include paying the ransom (in some cases), hiring cybersecurity experts for incident response and recovery, restoring damaged systems, and purchasing new software and hardware. Indirect costs include lost productivity, reputational damage leading to decreased enrollment and research funding, and potential legal liabilities. While precise figures are often kept confidential, estimates suggest that the costs can range from hundreds of thousands to millions of euros, depending on the size of the university and the extent of the damage.
The long-term financial burden is likely to be felt for years to come as universities invest in more robust cybersecurity measures to prevent future attacks.
The Ransomware Group’s Tactics and Techniques

The recent global ransomware attack targeting the Florida Supreme Court and several European universities highlights the sophisticated and evolving nature of modern cybercrime. Understanding the attackers’ methods is crucial for improving cybersecurity defenses and preventing future incidents. This section delves into the likely tactics and techniques employed by the ransomware group, analyzing their approach from initial infiltration to ransom demands.
We will examine the ransomware itself, the infiltration methods, communication strategies, and a likely timeline of the attack. It’s important to note that precise details regarding specific ransomware strains and attack vectors are often withheld for operational security reasons, so this analysis will rely on common ransomware techniques and observed patterns.The ransomware used in this attack likely leveraged a combination of tried-and-true techniques alongside more novel approaches.
While the specific variant remains unknown, it probably employed advanced encryption methods to render data inaccessible. Common encryption algorithms used in ransomware attacks include AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), often in combination for increased security. The ransomware likely also included features to hinder recovery efforts, such as data deletion or overwriting. Moreover, the attackers may have implemented self-propagating capabilities, allowing the malware to spread rapidly throughout the compromised networks.
Ransomware Capabilities and Encryption Methods
The ransomware likely employed strong encryption algorithms, such as AES-256 or RSA-4096, making decryption without the decryption key extremely difficult. The encryption process probably targeted various file types, including documents, databases, and backups, rendering critical systems and data unusable. The ransomware likely included a mechanism to generate a unique encryption key for each victim, further complicating the decryption process.
It’s plausible that the attackers implemented a double-extortion tactic, exfiltrating data before encryption and threatening to publicly release it if the ransom wasn’t paid. This adds significant pressure on victims to comply with the attackers’ demands.
Methods of System Infiltration
The attackers likely exploited vulnerabilities in the targeted systems to gain initial access. This could have involved phishing emails containing malicious attachments or links, exploiting known software vulnerabilities (zero-day or otherwise), or leveraging compromised credentials obtained through previous breaches. Once inside the network, the attackers likely moved laterally, gaining access to sensitive data and critical systems. Techniques like credential harvesting and lateral movement tools might have been used to spread the ransomware throughout the network.
The attackers’ expertise likely allowed them to evade detection by security software, potentially using custom malware or obfuscation techniques.
Communication Strategy and Ransom Demands
The ransomware group likely communicated with victims through encrypted channels, possibly using the Tor network or dedicated communication platforms. The ransom demands would have been presented in a clear and concise manner, specifying the amount required for decryption and potentially including a deadline. Negotiation tactics might have involved offering reduced ransom amounts for quicker payment or providing partial decryption as a demonstration of their capabilities.
The attackers may have also employed intimidation tactics, threatening to leak data or cause further damage if the demands weren’t met. The communication likely included instructions on how to pay the ransom, possibly using cryptocurrency to maintain anonymity.
Timeline of the Attack
The attack likely unfolded in several stages:
1. Initial Access
The attackers gained initial access to the networks of the Florida Supreme Court and European universities, potentially through phishing or exploiting vulnerabilities.
2. Lateral Movement
The attackers moved laterally within the networks, gaining access to sensitive data and critical systems.
3. Data Exfiltration
The attackers exfiltrated sensitive data, potentially as a backup in case the encryption failed or as part of a double-extortion tactic.
4. Ransomware Deployment
The ransomware was deployed, encrypting critical data and rendering systems unusable.
5. Ransom Demand
The attackers contacted the victims, presenting their ransom demands and threatening to release or destroy the data.
6. Negotiation (Optional)
Negotiations might have occurred between the attackers and victims, potentially involving a reduction in the ransom amount.
7. Payment (Optional)
The victims may have paid the ransom, leading to the decryption of their data.
Global Implications and Broader Cybersecurity Concerns
The ransomware attack targeting the Florida Supreme Court and European universities highlights a critical vulnerability in our increasingly interconnected world. This isn’t just a localized incident; it’s a stark reminder of the escalating global threat posed by sophisticated cybercriminals and the urgent need for proactive cybersecurity measures across all sectors. The implications extend far beyond the immediate victims, impacting public trust, economic stability, and national security.The attack underscores the interconnected nature of our digital infrastructure.
The disruption caused by the ransomware demonstrates how a successful breach in one institution can have cascading effects on others, impacting critical services and potentially leading to widespread chaos. Furthermore, the attack exposes the vulnerability of seemingly secure institutions to sophisticated attacks, highlighting the limitations of existing security protocols in the face of evolving cyber threats.
Vulnerabilities Exploited and Mitigation Strategies
The attackers likely exploited known vulnerabilities in software or systems used by the affected institutions. Common vulnerabilities include outdated software, weak passwords, insufficient user training, and lack of multi-factor authentication. These vulnerabilities, while individually manageable, can create significant weaknesses when combined. Mitigation involves a multi-pronged approach. Regular software updates are crucial to patch known vulnerabilities.
The recent global ransomware attack crippling the Florida Supreme Court and European universities highlights the urgent need for robust, secure systems. Building resilient applications is key, and that’s where exploring options like domino app dev the low code and pro code future becomes incredibly relevant. Investing in secure development practices, regardless of the approach, is crucial to preventing future widespread disruptions from similar attacks.
Implementing strong password policies and multi-factor authentication significantly reduces the risk of unauthorized access. Comprehensive security awareness training for all users is essential to prevent phishing attacks and other social engineering tactics. Finally, regular security audits and penetration testing can identify and address potential weaknesses before they can be exploited by attackers.
Importance of Robust Cybersecurity Measures for Governmental and Educational Institutions
Governmental and educational institutions hold vast amounts of sensitive data, including personal information, intellectual property, and critical infrastructure details. Robust cybersecurity measures are not merely a best practice; they are a necessity to protect this data and maintain the integrity of their operations. The consequences of a successful ransomware attack on these institutions can be devastating, ranging from financial losses and reputational damage to disruption of essential services and erosion of public trust.
Investing in advanced cybersecurity technologies, implementing stringent security protocols, and providing ongoing training for staff are essential steps to safeguard these institutions from cyber threats. The cost of inaction far outweighs the cost of proactive security measures.
Best Practices for Preventing and Responding to Ransomware Attacks
Effective ransomware prevention and response require a proactive and layered approach. The following best practices are essential for all organizations, but especially for those holding sensitive data:
Robust preventative measures are crucial to minimize the risk of a ransomware attack. These measures should be part of a comprehensive cybersecurity strategy:
- Regularly update all software and operating systems.
- Implement strong password policies and multi-factor authentication.
- Conduct regular security awareness training for all staff.
- Back up data regularly to an offline location.
- Segment networks to limit the impact of a breach.
- Employ intrusion detection and prevention systems.
- Conduct regular security audits and penetration testing.
- Develop and test an incident response plan.
Responding effectively to a ransomware attack is critical to minimize damage and ensure a swift recovery. A well-defined incident response plan is essential:
- Isolate infected systems immediately.
- Contact law enforcement and cybersecurity experts.
- Do not pay the ransom (in most cases).
- Restore data from backups.
- Conduct a thorough post-incident analysis to identify vulnerabilities and improve security measures.
Legal and Ethical Considerations
The recent global ransomware attack targeting the Florida Supreme Court and European universities highlights a critical intersection of legal and ethical complexities. The actions taken—or not taken—by both victims and attackers have far-reaching consequences, impacting not only individual institutions but also the broader landscape of cybersecurity and international law. Understanding the legal ramifications of ransomware attacks and the ethical dilemmas faced by affected organizations is crucial for developing effective preventative measures and response strategies.The legal implications of paying ransoms to cybercriminals are multifaceted and often murky.
While some argue that paying ransoms encourages further attacks, others contend that it’s a necessary evil to prevent significant data loss or operational disruption. The legality of ransom payments varies depending on jurisdiction and specific circumstances. In some countries, paying ransoms may be considered a violation of anti-terrorism or sanctions laws, particularly if the attackers are known to be linked to criminal organizations or hostile states.
Furthermore, even if a ransom payment is not illegal per se, it may be subject to scrutiny if it involves funds derived from illicit activities or if it violates internal policies or regulations.
Legal Implications of Ransom Payments
Paying ransoms to cybercriminals carries significant legal risks. Depending on the jurisdiction and the specific facts of the case, organizations might face investigations for violating sanctions laws, money laundering regulations, or even aiding and abetting criminal activity. The act of paying a ransom might be seen as funding terrorism or organized crime, leading to severe legal consequences. Furthermore, internal investigations may be launched to determine if the organization’s security practices were adequate and if there was any negligence leading to the attack.
For example, if an organization fails to implement basic security measures, such as multi-factor authentication or regular software updates, they might face legal challenges from victims of the data breach. This legal risk is compounded by the increasing regulatory pressure on organizations to maintain robust cybersecurity practices, as evidenced by regulations like the GDPR in Europe and the CCPA in California.
Ethical Dilemmas Faced by Targeted Institutions, Global ransomware attack downs florida supreme court and european universities
Institutions targeted by ransomware attacks often face difficult ethical choices. The decision of whether or not to pay a ransom involves weighing the potential financial and reputational damage of a data breach against the moral implications of rewarding criminal behavior. Paying the ransom could be perceived as encouraging future attacks, potentially harming other organizations. On the other hand, refusing to pay could result in significant data loss, potentially leading to legal liabilities and reputational harm.
The ethical considerations extend beyond the immediate decision of paying the ransom; they also encompass the organization’s responsibility to its stakeholders, including employees, customers, and the public. Transparency about the attack and its aftermath is crucial to maintain trust and demonstrate accountability. The ethical dilemma also involves balancing the need for immediate remediation with the long-term implications of establishing a precedent for paying ransoms.
Legal Precedents Related to Ransomware Attacks and Data Breaches
Several legal precedents have emerged in response to ransomware attacks and data breaches. The 2017 NotPetya ransomware attack, attributed to the Russian government, resulted in billions of dollars in damages globally. While there have been numerous lawsuits filed, the legal landscape remains complex and evolving. Many cases focus on issues of negligence, contractual breaches, and data protection laws.
Cases related to data breaches often center around the organization’s failure to adequately protect sensitive information, leading to legal actions from affected individuals and regulatory bodies. These precedents highlight the increasing legal accountability for organizations in managing cybersecurity risks. The courts are increasingly holding organizations responsible for data breaches, even if the attack was sophisticated and seemingly unavoidable.
Hypothetical Scenario Illustrating Potential Legal Ramifications
Imagine a regional hospital, “Hopewell Medical Center,” fails to implement regular security updates on its medical record system. A ransomware attack encrypts patient data, leading to delays in treatment, loss of revenue, and potential harm to patients. The hospital’s failure to maintain adequate cybersecurity measures could be seen as negligence, opening them up to lawsuits from patients whose data was compromised, as well as potential regulatory fines for violating HIPAA regulations in the United States.
Furthermore, the hospital could face reputational damage, loss of public trust, and potentially, criminal charges depending on the severity of the consequences. This scenario illustrates how a failure to protect data can lead to a cascade of legal and financial repercussions.
Last Word
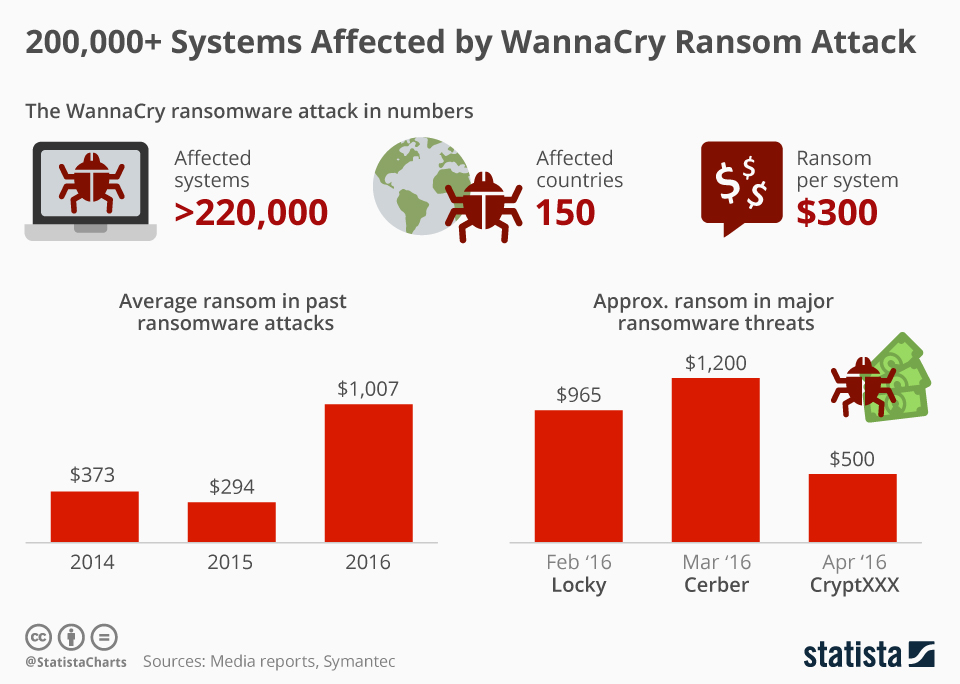
The global ransomware attack targeting the Florida Supreme Court and European universities isn’t just another headline; it’s a wake-up call. The scale and impact of this attack underscore the critical need for proactive and robust cybersecurity measures across all sectors, particularly in government and education. While the immediate consequences are devastating, the long-term effects will shape cybersecurity strategies for years to come.
The lessons learned from this incident must be heeded to prevent similar catastrophes from occurring in the future. The vulnerability exposed isn’t just technological; it’s a systemic weakness that demands a comprehensive and collaborative response from institutions, governments, and cybersecurity experts alike.
FAQs
What type of ransomware was used in the attack?
Specific details about the ransomware are often withheld during investigations to prevent further attacks. However, analysis will likely reveal the type of encryption used and the group responsible, if identified.
Were student records compromised?
The extent of data compromise varies depending on the university. Some may have had student data affected, while others might have suffered primarily administrative or research data losses. The full picture will emerge as investigations progress.
Did the Florida Supreme Court pay the ransom?
Whether or not the ransom was paid is often kept confidential for security and legal reasons. Paying ransoms is a complex ethical and legal issue with no easy answers.
What long-term effects might this have on the universities?
Long-term effects could include reputational damage, increased insurance premiums, and the need for significant investment in enhanced cybersecurity infrastructure and training.