Google Asks Users Beware of Google Drive Phishing
Google asks users to be aware of phishing attacks on Google Drive – a stark warning highlighting the increasing sophistication of cyber threats targeting our cloud storage. These attacks aren’t just annoying inconveniences; they’re serious security breaches that can lead to data theft, financial loss, and identity theft. We’re talking about cleverly crafted emails and links designed to trick even the most cautious users into handing over their Google Drive credentials.
Let’s dive into how these attacks work, how to spot them, and what steps you can take to protect yourself.
The tactics employed are surprisingly diverse, ranging from seemingly legitimate emails requesting access to documents to malicious attachments promising exciting content. The common thread? Exploiting our trust in Google’s services. Google itself has responded with warnings and enhanced security measures, but ultimately, staying vigilant is our best defense. This post will equip you with the knowledge and strategies to navigate this increasingly dangerous digital landscape.
Understanding the Phishing Attacks
Google Drive phishing attacks are a significant threat, leveraging the trust users place in Google’s services to gain access to sensitive information or deploy malware. These attacks often appear legitimate, making them difficult to identify without careful scrutiny. Understanding the tactics employed is crucial for effective protection.Phishing attacks exploit the inherent trust users have in Google’s platform. The familiarity and widespread use of Google Drive create a sense of security, making users less likely to question suspicious emails or links.
Attackers cleverly mimic official Google communications, making their malicious content appear genuine and trustworthy. This deceptive tactic increases the likelihood of users falling victim to these scams.
Google’s warning about phishing attacks on Google Drive highlights a critical need for robust cloud security. Understanding how to protect your data becomes even more important when you consider the rise of solutions like Cloud Security Posture Management (CSPM), such as those offered by Bitglass – check out this article on bitglass and the rise of cloud security posture management to learn more.
Ultimately, staying vigilant against phishing attempts, coupled with strong cloud security practices, is key to keeping your files safe.
Malicious Content Used in Google Drive Phishing Attacks
The malicious content used in these attacks varies, but commonly involves deceptive links and attachments. These elements are designed to trick users into revealing their credentials or downloading malware onto their devices.
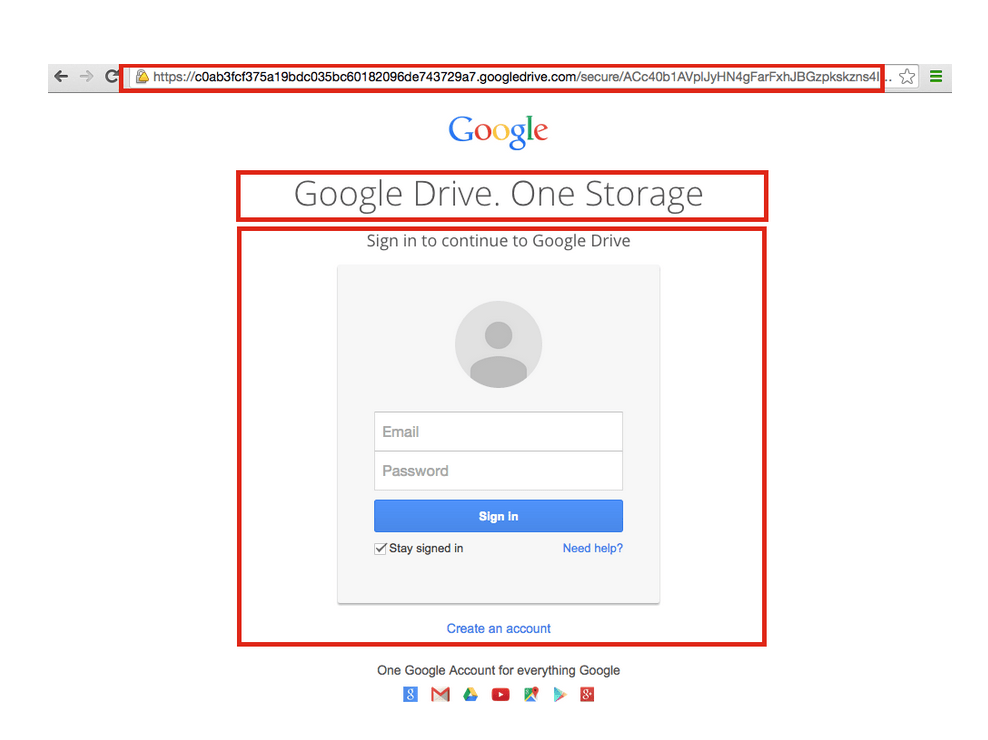
- Deceptive Links: These links often appear to lead to legitimate Google Drive folders or files, but instead redirect users to phishing websites that mimic the Google login page. These fake login pages capture user credentials, granting attackers access to their accounts.
- Malicious Attachments: Phishing emails may contain attachments disguised as important documents or spreadsheets. These attachments often contain malware that, once opened, can infect the user’s device and steal data or gain control of the system. Examples include macros within Microsoft Office documents or executable files disguised as PDFs.
Examples of Phishing Emails Targeting Google Drive Users
Phishing emails targeting Google Drive users often share similar characteristics. They typically use a sense of urgency or create a scenario requiring immediate action from the user.
- Example 1: An email claiming a shared file has been updated and requires immediate access. The email includes a link to a seemingly legitimate Google Drive folder. This link, however, redirects to a fake login page designed to steal credentials.
- Example 2: An email claiming a large file has been uploaded to the user’s Google Drive, prompting the user to click a link to view it. This link could lead to a download of malware disguised as a legitimate file.
- Example 3: An email notifying the user of a violation of Google Drive’s terms of service, threatening account suspension unless the user clicks a link to verify their account information. This link leads to a fake Google Drive login page used to harvest credentials.
Google’s Response and User Awareness: Google Asks Users To Be Aware Of Phishing Attacks On Google Drive

Google Drive phishing attacks are a serious concern, impacting both individual users and organizations. Understanding Google’s response and fostering user awareness are crucial steps in mitigating this threat. This section will explore Google’s official stance on these attacks, the security measures they’ve implemented, and practical strategies for users to protect themselves.Google actively combats phishing attacks through a multi-pronged approach.
They regularly publish security advisories and blog posts detailing emerging threats and best practices. Furthermore, Google invests heavily in advanced technologies like machine learning to detect and block malicious emails and links before they reach users. Their Security Transparency report provides valuable insights into the types of attacks they encounter and the effectiveness of their countermeasures. While Google provides robust protection, individual user vigilance remains paramount.
Google’s Security Measures and Official Recommendations
Google’s official recommendations emphasize proactive security measures. They strongly advise users to enable two-factor authentication (2FA) for all Google accounts, including Google Drive. This adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain passwords. Regular software updates are also crucial, as these often include security patches that address vulnerabilities exploited by phishers.
Google’s Security Checkup tool provides a personalized assessment of account security and guides users through the process of strengthening their defenses. Finally, Google encourages users to report suspicious emails and links immediately. This helps Google’s security teams identify and neutralize threats more effectively. Google actively works to improve its detection systems and enhance user education to combat these evolving threats.
User Awareness Campaign: Identifying and Avoiding Google Drive Phishing Attempts
A proactive user awareness campaign is essential for combating phishing attacks. Educating users on how to identify and avoid these attacks can significantly reduce their vulnerability. The following table Artikels key indicators, examples, explanations, and recommended actions:
| Phishing Indicator | Example | Explanation | Action to Take |
|---|---|---|---|
| Suspicious Email Address or Sender Name | Email from “[email protected]” (instead of a verified Google address) | Phishers often use addresses that closely resemble legitimate ones to deceive users. | Hover over the sender’s name to see the actual email address. Report suspicious emails. |
| Urgent or Threatening Language | “Your Google Drive account has been compromised! Click here to verify your account immediately.” | Phishers often create a sense of urgency to pressure users into acting without thinking. | Do not click links in suspicious emails. Contact Google support directly through official channels. |
| Suspicious Links | A link that looks like a Google Drive link but has a slightly different URL (e.g., extra characters or a different domain). | Phishers often create fake links that redirect users to malicious websites. | Carefully examine the URL before clicking. Never click links from suspicious emails. |
| Grammar and Spelling Errors | Emails containing significant grammatical errors or misspellings. | Legitimate companies typically have professional-quality communication. | Be wary of emails with poor grammar or spelling. |
| Requests for Personal Information | Emails asking for your password, credit card details, or other sensitive information. | Google will never ask for your password or other sensitive information via email. | Never provide personal information in response to unsolicited emails. |
| Unusual Attachments | Unexpected attachments (e.g., .exe files) in emails claiming to be from Google Drive. | Malicious attachments can infect your computer with malware. | Never open attachments from unknown or untrusted senders. |
Impact and Consequences

Falling victim to a Google Drive phishing attack can have severe and far-reaching consequences, impacting both individuals and organizations. The potential damage extends beyond simple inconvenience, posing significant risks to personal and professional well-being. Understanding these risks is crucial for effective prevention.The consequences of a successful phishing attack targeting Google Drive can be devastating. Data breaches are a primary concern, exposing sensitive personal information such as financial details, medical records, and private communications.
This compromised data can then be used for identity theft, leading to fraudulent activities in the victim’s name, resulting in financial loss and reputational damage. For businesses, a data breach can lead to significant financial penalties due to regulatory non-compliance (like GDPR violations), loss of customer trust, and damage to brand reputation. In extreme cases, the consequences can even involve legal action.
Vulnerable User Groups
Certain user groups are more susceptible to Google Drive phishing attacks due to various factors. Individuals with limited technical knowledge or experience with online security are particularly vulnerable. They may be less likely to recognize the warning signs of a phishing email or link, making them easy targets for malicious actors. Similarly, older adults, who may be less familiar with sophisticated online threats, are also at higher risk.
Google’s warning about phishing attacks on Google Drive got me thinking about secure app development. Building robust, secure apps is crucial, and that’s why I’ve been researching the advancements in domino app dev, the low-code and pro-code future , which offers potential solutions for creating more secure applications. Ultimately, strong security practices, whether in cloud storage or app development, are essential to protect against these increasingly sophisticated phishing schemes.
Employees within organizations who lack regular security awareness training are also a prime target, as a single compromised account can provide access to an entire company’s data. Finally, users who frequently interact with unknown senders or open suspicious attachments are more likely to fall victim.
Google’s warning about phishing attacks on Google Drive is a timely reminder to stay vigilant online. It’s shocking to see how these scams evolve; for instance, I recently read about a disturbing trend where Facebook is reportedly requesting bank account details and card transaction information, as detailed in this article: facebook asking bank account info and card transactions of users.
This highlights the importance of carefully scrutinizing any request for sensitive information, no matter the source, to avoid becoming a victim of these increasingly sophisticated phishing attempts on platforms like Google Drive.
Effectiveness of Security Awareness Training
The effectiveness of security awareness training varies significantly depending on the method employed. Simple email campaigns with general security tips often prove ineffective, as they lack engagement and fail to provide practical, scenario-based learning. On the other hand, interactive training modules, simulations, and gamified learning experiences have shown much higher success rates in improving user awareness and behavior.
These methods create a more engaging and memorable learning experience, helping users retain information and apply it to real-world scenarios. Regular refresher training, combined with real-time phishing simulations, can further enhance the effectiveness of these programs. Organizations should consider incorporating multiple training methods to cater to diverse learning styles and maximize impact. For example, a combination of interactive modules and regular phishing simulations can create a comprehensive and effective training program.
Technical Aspects and Prevention
Google Drive phishing attacks leverage sophisticated techniques to trick users into revealing sensitive information or installing malware. Understanding these mechanisms is crucial for effective prevention. These attacks often exploit vulnerabilities in human psychology, relying on urgency, fear, or curiosity to manipulate victims.The technical underpinnings of these attacks often involve spoofing legitimate Google Drive links or email addresses. Attackers might create websites that closely mimic the Google Drive interface, complete with logos and branding, designed to deceive unsuspecting users.
These fake sites often contain malicious code or prompt users to enter their Google credentials, which are then harvested by the attacker. Another common tactic is to embed malicious links within seemingly harmless emails or documents, leading to malware downloads or compromised accounts.
Spoofing and Malware Delivery Mechanisms
Phishing attacks targeting Google Drive frequently use sophisticated spoofing techniques. Attackers might create near-identical copies of legitimate Google Drive URLs, subtly altering characters or using shortened links to mask the true destination. These URLs can lead to fake login pages designed to steal credentials or websites hosting malware. Malware delivered through these attacks can range from keyloggers that record user activity to ransomware that encrypts files and demands a ransom for their release.
In some cases, the malware might install itself as a browser extension, allowing persistent access to the user’s Google Drive account and data. For example, a phishing email might appear to be from a colleague sharing an important document, containing a link that leads to a cleverly disguised malicious website.
Mitigating Risk with Two-Factor Authentication and Security Settings
Implementing robust security measures significantly reduces the risk of successful phishing attacks. Two-factor authentication (2FA) adds an extra layer of security, requiring a second form of verification (such as a code sent to your phone) in addition to your password. Even if an attacker obtains your password, they will be unable to access your account without the second factor.
Beyond 2FA, regularly reviewing your Google account’s security settings is crucial. This includes checking for any unfamiliar devices or applications with access to your account, enabling advanced protection features offered by Google, and regularly updating your passwords. Actively monitoring your Google Drive activity for any unauthorized changes is another essential step. For instance, a sudden increase in file sharing activity or the appearance of unknown files could signal a compromise.
Reporting Suspected Phishing Attempts, Google asks users to be aware of phishing attacks on google drive
If you suspect a phishing attempt targeting your Google Drive account, promptly reporting it to Google is vital. This helps Google identify and remove malicious content and protect other users. Here’s a step-by-step guide on how to report a suspected phishing attempt:
- Identify the suspicious email or link: Carefully examine the sender’s email address, the URL, and any unusual language or requests within the communication. Look for inconsistencies in branding or grammar.
- Do not click any links or open any attachments: Avoid interacting with the suspicious communication in any way. This prevents potential malware infection or credential theft.
- Forward the email to Google’s phishing reporting address: Google provides a dedicated email address for reporting phishing attempts. The exact address may vary slightly depending on the region but usually involves a “reportphishing” or similar term. Check Google’s help resources for the most up-to-date address.
- Report the suspicious website (if applicable): If the phishing attempt involves a website, you can also report it to Google using their web reporting mechanism. Look for the appropriate reporting link on the Google Safety Center webpage.
- Change your Google password: As a precautionary measure, change your Google password immediately after reporting the suspected phishing attempt. This helps secure your account even if your credentials were compromised.
Best Practices and Future Outlook
Protecting your Google Drive from phishing attacks requires a proactive and multi-layered approach. While Google implements robust security measures, individual vigilance remains crucial in preventing successful attacks. Understanding best practices and anticipating future trends are key to safeguarding your data and maintaining your online security.
The following best practices significantly reduce your vulnerability to Google Drive phishing attempts.
Best Practices for Google Drive Security
Implementing these practices will bolster your defense against phishing attacks targeting your Google Drive.
- Verify Sender Identity: Always scrutinize email addresses and links before clicking. Hover over links to see the actual URL – legitimate Google links will typically start with `drive.google.com`. Look for inconsistencies in the sender’s name and email address compared to their usual communication style.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security, requiring a code from your phone or another device in addition to your password. Even if a phisher obtains your password, they won’t be able to access your account without the 2FA code.
- Regularly Review Permissions: Check the sharing settings of your Google Drive files and folders. Remove access for individuals or applications you no longer trust or need to share your files with.
- Be Wary of Suspicious Emails and Links: Don’t click on links or open attachments from unknown senders. If you’re unsure about an email’s legitimacy, contact the supposed sender directly through a known, verified channel (e.g., their official website or phone number) to confirm.
- Keep Software Updated: Ensure your operating system, web browser, and any other relevant software are updated with the latest security patches. Outdated software can contain vulnerabilities that phishers exploit.
- Report Phishing Attempts: If you receive a phishing email, report it to Google immediately. This helps them identify and block malicious activity.
- Educate Yourself: Stay informed about the latest phishing techniques and scams. Regularly check Google’s security blog and other reputable cybersecurity sources for updates.
Lifecycle of a Google Drive Phishing Attack
Understanding the stages of a typical attack helps you identify and prevent them.
The attack begins with a Phishing Email, often disguised as a legitimate communication from Google or a trusted contact. This email contains a Malicious Link, designed to look authentic. Clicking this link redirects the user to a Fake Login Page, visually similar to the real Google Drive login page. On this fake page, the user enters their Credentials (username and password), which are then stolen by the phisher.
The phisher then gains Unauthorized Access to the user’s Google Drive account, potentially stealing, modifying, or deleting files. Finally, the phisher might use the account for Further Malicious Activities, such as spreading malware or launching further phishing attacks.
Future Trends in Google Drive Phishing Attacks
Phishing attacks are constantly evolving, and we can expect several trends in the future.
We can anticipate more sophisticated phishing techniques, such as highly realistic fake login pages using advanced spoofing methods. Attacks will likely leverage social engineering tactics to exploit emotional vulnerabilities and increase the likelihood of users falling victim. The use of AI-powered tools to create personalized and targeted phishing emails will also become more prevalent. Furthermore, the integration of phishing attacks with other types of cyber threats, like ransomware, will likely increase.
To prepare, users should prioritize continuous learning about new phishing tactics, strengthening their password security, and utilizing advanced security tools like multi-factor authentication and security awareness training.
Wrap-Up
In the ever-evolving world of online security, staying informed is paramount. Google Drive phishing attacks are a serious threat, but by understanding the tactics used and implementing the preventative measures discussed, you can significantly reduce your risk. Remember, skepticism and a healthy dose of caution are your best allies in the fight against cybercrime. Don’t hesitate to report suspicious activity – your vigilance protects not only yourself but also the broader online community.
Stay safe out there!
FAQ Corner
What happens if I fall victim to a Google Drive phishing attack?
The consequences can range from unauthorized access to your files and data to identity theft and financial loss, depending on the nature of the attack.
How can I tell if an email is a phishing attempt?
Look for suspicious links, grammatical errors, urgent requests for action, and emails from unknown senders. Always verify the sender’s identity before clicking any links or opening attachments.
What should I do if I suspect a phishing attempt?
Do not click any links or open attachments. Report the email to Google and change your Google Drive password immediately.
Are there any browser extensions that can help protect me from phishing attacks?
Yes, several browser extensions are designed to detect and block phishing websites. Research reputable options and choose one that suits your needs.