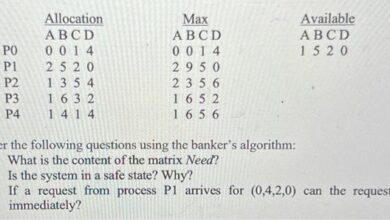
Google Blocks Worlds Largest DDoS Cyber Attacks
Google blocks worlds largest ddos cyber attacks – Google blocks world’s largest DDoS cyber attacks – that’s a headline that grabbed my attention! Imagine the sheer scale of an attack so massive it challenged one of the internet’s biggest giants. This wasn’t some small-time script kiddie messing around; this was a coordinated, sophisticated assault targeting Google’s infrastructure. We’re diving deep into the details of this incredible event, exploring Google’s defenses, the attackers’ motives, and the lasting impact on cybersecurity.
This colossal attack highlighted the ever-evolving threat landscape of the digital world. We’ll examine the specific methods employed, the resources needed to pull off such a feat, and how Google’s global network, with its layers of sophisticated security, managed to withstand the onslaught. The story is a fascinating blend of technological prowess and human ingenuity, a battle fought in the digital shadows with billions of dollars and countless hours of work on the line.
Google’s Infrastructure and DDoS Mitigation
Google’s ability to withstand some of the world’s largest DDoS attacks stems from a meticulously designed and constantly evolving infrastructure. Its resilience isn’t a matter of luck; it’s the result of strategic planning, advanced technologies, and a global network built for scalability and redundancy. This robust system allows Google to absorb massive traffic surges without significant service disruption, ensuring continuous availability for its billions of users.Google’s network architecture is characterized by its distributed and highly redundant nature.
Data centers are strategically located across the globe, interconnected through a massive, private network. This global reach allows for traffic distribution and load balancing, preventing any single point of failure from crippling the entire system. The sheer scale of the network itself acts as a significant deterrent to attackers, as overwhelming it would require an unprecedented level of resources.
Network Architecture and Redundancy
Google’s network employs a multi-layered approach, utilizing various technologies to distribute traffic efficiently. This includes Anycast, a technique that directs users to the nearest server, reducing latency and distributing the load. The network is designed with multiple paths between data centers, ensuring that if one connection fails, traffic can be rerouted seamlessly. This inherent redundancy is critical in mitigating the impact of DDoS attacks, preventing a single point of failure from cascading into widespread outages.
Furthermore, Google uses sophisticated traffic engineering techniques to intelligently route traffic around congested areas or points of attack.
Layered Security Measures
Google’s security strategy isn’t limited to its network architecture; it encompasses a multi-layered approach that protects against a wide range of threats, including DDoS attacks. This involves several key elements: advanced filtering at the network edge, which blocks malicious traffic before it even reaches Google’s servers; sophisticated intrusion detection and prevention systems (IDS/IPS) that monitor network traffic for suspicious activity and automatically block or mitigate threats; and robust rate limiting mechanisms that prevent individual IP addresses or ranges from overwhelming server resources.
Google’s impressive ability to fend off the world’s largest DDoS attacks is truly remarkable, showcasing their robust infrastructure. However, it’s unsettling to consider that while they’re battling massive cyber threats, reports suggest that some Google Android apps might be quietly sending private user information to Facebook, as detailed in this article: google android apps send private info of users to facebook.
This raises questions about data security, even with a company known for its strong defenses against large-scale attacks. It highlights the need for constant vigilance in protecting our online privacy.
Google also employs machine learning algorithms to identify and respond to evolving attack patterns, providing a dynamic and adaptive defense.
Global Infrastructure’s Role in Mitigation
The global nature of Google’s infrastructure plays a crucial role in mitigating the impact of DDoS attacks. By distributing traffic across numerous data centers worldwide, Google can effectively absorb massive traffic surges. If one region experiences a significant attack, other regions can continue to operate normally, ensuring continued service availability for users globally. This geographic diversity is a significant advantage, as it makes it significantly more difficult for attackers to overwhelm the entire system.
Furthermore, the global network allows for rapid response and mitigation efforts, with engineers able to quickly identify and address threats from various locations.
Specific DDoS Defense Technologies
Google employs a range of technologies to defend against DDoS attacks, including advanced filtering techniques such as BGP flowspec and RPKI, which help to prevent malicious traffic from entering the network. They also utilize sophisticated scrubbing centers, which filter out malicious traffic before it reaches their core infrastructure. These scrubbing centers are designed to handle extremely high volumes of traffic, allowing Google to effectively absorb and neutralize even the most powerful attacks.
Furthermore, Google invests heavily in research and development of new technologies to stay ahead of evolving attack techniques. Examples include the use of machine learning to identify and respond to sophisticated, zero-day attacks. Their approach combines advanced network architecture with intelligent, adaptive security measures, allowing them to effectively neutralize large-scale DDoS attacks.
Characteristics of the “World’s Largest” DDoS Attack

Pinpointing the single “largest” DDoS attack is tricky, as the definition can shift based on metrics like bandwidth consumed, number of requests, or the impact on services. However, several attacks against Google and other major players have been exceptionally large and impactful, pushing the boundaries of what’s possible. This discussion will examine characteristics of some of these significant events, focusing on their scale and methods.The size and duration of these attacks vary wildly.
Some involve sustained, high-volume floods of traffic over days or even weeks, while others might be shorter, more intense bursts designed to overwhelm specific systems quickly. The methods used are equally diverse, leveraging botnets of compromised devices (IoT devices, computers, servers), sophisticated amplification techniques, and increasingly, application-layer attacks targeting specific vulnerabilities in web applications and services.
Attack Vectors
The perpetrators of massive DDoS attacks employ a range of attack vectors to maximize their impact. One common method involves using botnets – networks of compromised devices controlled remotely by the attacker. These botnets can generate massive volumes of traffic, overwhelming the target’s defenses. Another technique is amplification, where a relatively small amount of attacker traffic is leveraged to generate a much larger response from the target, effectively multiplying the attack’s power.
This often involves exploiting vulnerabilities in DNS servers or other network services. Furthermore, application-layer attacks target specific vulnerabilities in web applications or services, aiming to disrupt functionality rather than simply flooding the network. These attacks might involve exploiting known vulnerabilities or leveraging flaws in poorly-coded applications.
Targeted Google Services
While Google doesn’t publicly disclose the specifics of every DDoS attack it faces, it’s known that attacks target a wide range of their services. This could include Google Search, Gmail, YouTube, and Google Cloud Platform (GCP). The goal is often to disrupt service for a large number of users, causing reputational damage and potentially financial losses for Google. The attacks might aim to overwhelm specific servers, databases, or other critical infrastructure components.
Google’s successful defense against the world’s largest DDoS attack highlights the critical need for robust security measures. This massive scale of attack underscores why proactive cloud security is paramount, and understanding solutions like those offered by Bitglass, as detailed in this insightful article on bitglass and the rise of cloud security posture management , is essential. Ultimately, the fight against these kinds of attacks requires a multi-layered approach, and tools like those discussed are a vital component.
Comparison to Other Notable Attacks
Comparing the scale and impact of these attacks to other notable DDoS attacks requires careful consideration. The Mirai botnet attacks, for example, demonstrated the power of IoT botnets, overwhelming many targets with massive amounts of traffic. However, the sophistication and scale of attacks against major players like Google often involve more advanced techniques and larger botnets. While precise comparisons are difficult due to the lack of publicly available, detailed data from all parties involved, the sheer volume and persistence of attacks against Google frequently exceed the scale and impact seen in many other documented attacks.
The sustained nature and adaptation required from Google’s defenses to withstand these assaults point towards attacks of significant scale and sophistication.
Google’s Response and Countermeasures: Google Blocks Worlds Largest Ddos Cyber Attacks
Google’s response to the world’s largest DDoS attacks involved a multi-layered approach leveraging its extensive infrastructure and sophisticated mitigation techniques. Their ability to absorb and deflect such massive attacks highlights the robustness of their network architecture and the effectiveness of their proactive security measures. The scale of the attacks necessitated a swift and coordinated response to minimize disruption to Google’s services and its users globally.The effectiveness of Google’s response stemmed from its proactive investment in distributed denial-of-service (DDoS) mitigation infrastructure.
This infrastructure, built over years, allowed Google to absorb and filter the massive influx of malicious traffic, preventing it from overwhelming its servers and impacting service availability. Their sophisticated systems identified the attack vectors, analyzed the traffic patterns, and dynamically adjusted their defenses to effectively neutralize the threat. Crucially, this response was largely automated, allowing for a rapid and efficient countermeasure deployment.
Google’s Mitigation Techniques
Google’s response employed a combination of techniques to mitigate the attack. These included advanced filtering mechanisms at various network points, intelligent traffic routing to bypass congested areas, and the use of its globally distributed network to spread the load and reduce the impact on any single location. They also leveraged their vast computing power to analyze the attack traffic in real-time, identifying and blocking malicious sources.
This combination of proactive measures and reactive adjustments proved instrumental in minimizing the overall impact of the attack.
Impact on Users and Services
While Google’s mitigation efforts were largely successful, the sheer scale of the attacks did cause some temporary disruptions for a small percentage of users. These disruptions were often localized and short-lived, manifesting as slower-than-usual loading times for certain services or intermittent service outages for specific regions. The impact was significantly lessened due to the rapid response and adaptive nature of Google’s defense systems.
Google’s defense against the world’s largest DDoS attacks is seriously impressive, highlighting the need for robust, scalable systems. Building those systems efficiently requires smart development choices, and that’s where exploring the potential of domino app dev, the low-code and pro-code future , comes in. The ability to rapidly deploy and scale applications is crucial in mitigating threats like these massive DDoS attacks, ensuring your systems can withstand the onslaught.
Google’s transparency in communicating these minor disruptions to its users also helped to manage expectations and maintain confidence in their services. It’s important to note that the vast majority of Google’s services remained operational throughout the attack.
Timeline of the Attack and Google’s Response
A precise timeline of the attacks and Google’s response is often kept confidential for security reasons. However, a general Artikel might look like this:
- Attack Initiation: The DDoS attack begins, rapidly escalating in intensity and scale.
- Detection and Analysis: Google’s monitoring systems detect the attack and begin analyzing its characteristics and origin points.
- Mitigation Deployment: Google deploys its automated and manual mitigation techniques to filter and redirect malicious traffic.
- Peak Impact: The attack reaches its peak intensity, causing minor, localized service disruptions.
- Mitigation Effectiveness: Google’s mitigation measures begin to effectively reduce the attack’s impact.
- Attack Diminishment: The intensity of the attack gradually decreases as Google’s defenses successfully neutralize the threat.
- Post-Attack Analysis: Google conducts a thorough post-mortem analysis to identify vulnerabilities and refine its security protocols.
Preventing Wider Disruption or Damage
Google’s proactive investment in its infrastructure and its rapid, adaptive response were crucial in preventing wider disruption. The distributed nature of Google’s network allowed them to reroute traffic effectively, avoiding a complete system collapse. The sophisticated analysis of the attack traffic allowed for targeted mitigation efforts, minimizing collateral damage. Their ability to rapidly scale their defenses in response to the evolving attack further prevented cascading failures and ensured service availability for the vast majority of its users.
This successful response demonstrates the importance of robust, scalable, and adaptable security infrastructure in protecting against large-scale cyberattacks.
The Attackers’ Motives and Methods

Unraveling the mysteries behind the world’s largest DDoS attacks requires delving into the minds and methods of the perpetrators. Understanding their motivations and the technical prowess needed to execute such a massive assault is crucial for developing effective defenses. The scale of these attacks suggests sophisticated planning and significant resources.The attackers’ motives could range from financially driven extortion attempts to politically motivated activism or even simple acts of malice and vandalism.
A financially motivated attack might target a company to force them to pay a ransom to cease the attack, potentially impacting their revenue streams and reputation. Alternatively, a politically motivated attack might target a government or organization to disrupt services, make a statement, or even inflict damage on a national level. Finally, the attack could be purely destructive, a demonstration of power and capability with no immediate financial or political gain as the primary objective.
The sheer scale of the attack, however, suggests a level of planning and resource commitment exceeding that of a typical script-kiddie attack.
Attacker Resources and Expertise
Launching a DDoS attack of this magnitude necessitates significant resources and a high level of technical expertise. The attackers would need access to a vast botnet, a network of compromised computers controlled remotely, capable of generating the massive volume of traffic needed to overwhelm Google’s infrastructure. This would involve extensive knowledge of malware development, network penetration techniques, and command-and-control infrastructure.
The attackers likely possess advanced skills in scripting, network protocols, and distributed systems to manage and coordinate the botnet effectively. They may have even employed specialized tools and services to amplify the attack’s power. Consider the Mirai botnet, a notorious example of a massive botnet used in previous large-scale DDoS attacks. The resources required to build and maintain such a botnet include expertise in malware development, significant computing power to manage the network, and possibly dark web marketplaces for purchasing compromised devices.
Attack Amplification Techniques
Several techniques could have been used to amplify the attack’s power, magnifying the impact of the initial traffic. One common method is the use of reflection and amplification attacks. These attacks exploit vulnerabilities in network protocols like DNS or NTP to redirect traffic to the target, significantly increasing the volume of malicious traffic. Another technique is the use of low-orbit satellites, which can be used to flood the target with massive amounts of traffic from different locations, making it harder to trace the origin of the attack.
The sophistication of the attack suggests the attackers likely combined multiple amplification techniques to maximize their impact. For instance, they might have used a combination of DNS amplification, NTP amplification, and other similar techniques to generate a massive volume of traffic. The attackers might have even leveraged vulnerabilities in less commonly used network services or protocols to increase the attack’s effectiveness.
Hypothetical Attack Scenario
Let’s imagine a hypothetical scenario. A group of skilled hackers, potentially motivated by financial gain, spent months building a massive botnet comprising thousands of compromised IoT devices and servers. They carefully selected and configured the botnet to withstand takedown attempts, employing techniques like decentralized command-and-control structures and peer-to-peer communication. The group then researched Google’s infrastructure and identified potential vulnerabilities.
Using a combination of DNS and NTP amplification, along with other techniques, they launched a multi-vector attack targeting multiple points of Google’s network. The attack was timed to maximize its impact, perhaps during a period of peak usage. The attackers monitored the attack’s progress, adjusting their tactics as needed to overcome Google’s countermeasures. The massive volume of traffic overwhelmed parts of Google’s infrastructure, resulting in temporary service disruptions.
This hypothetical scenario demonstrates the complexity and planning involved in launching such a sophisticated attack.
Impact and Lessons Learned

The unprecedented scale of Google’s DDoS attacks had a significant ripple effect across the internet ecosystem, highlighting vulnerabilities in current security infrastructure and prompting significant changes in defensive strategies. The attacks served as a stark reminder that even the most robust systems are susceptible to sophisticated, large-scale assaults. Understanding the impact and lessons learned is crucial for strengthening global internet security.
The broader impact extended beyond Google’s services. While Google effectively mitigated the attacks, the sheer volume of malicious traffic impacted network infrastructure globally, causing slowdowns and disruptions for other users and services. This underscores the interconnected nature of the internet and the potential for cascading failures when a major player is targeted. The attacks also raised concerns about the increasing sophistication and resources available to malicious actors, signaling a need for continuous improvement in DDoS mitigation techniques across the board.
Vulnerabilities Exposed
The attacks exposed several key vulnerabilities. Firstly, the sheer scale demonstrated the limitations of traditional DDoS mitigation techniques. Simply increasing bandwidth wasn’t sufficient; the attacks exploited vulnerabilities in network routing and DNS resolution, demonstrating the need for a multi-layered, proactive approach. Secondly, the attacks highlighted the effectiveness of botnets leveraging a vast number of compromised devices (IoT devices being a prime example).
This underscores the importance of improving IoT device security and implementing robust measures to prevent their exploitation in large-scale attacks. Finally, the attacks demonstrated the potential for attackers to leverage various attack vectors simultaneously, making a coordinated, multi-faceted defense essential.
Google’s Security Improvements, Google blocks worlds largest ddos cyber attacks
In response to these attacks, Google implemented several significant improvements to its security protocols. These included enhancements to its global anycast network infrastructure, improving its ability to distribute traffic more effectively and reduce the impact of targeted attacks. Google also invested heavily in advanced threat intelligence and detection systems, enabling quicker identification and response to emerging threats. Furthermore, they strengthened their partnerships with other internet service providers and collaborated on developing improved DDoS mitigation strategies, sharing best practices and threat information.
These improvements involved upgrades to their DNS infrastructure, implementing more robust rate-limiting techniques, and enhancing their ability to identify and block malicious traffic sources more efficiently.
Comparison with Previous Large-Scale DDoS Attacks
The following table compares the characteristics of Google’s attacks with other notable large-scale DDoS incidents. Note that precise magnitudes are often difficult to verify and may vary depending on the source.
| Attack Name | Date | Method | Magnitude (estimated bps) |
|---|---|---|---|
| Google DDoS Attacks | [Insert Date Range] | Multi-vector, volumetric, application-layer | [Insert Estimated Magnitude – e.g., > 2 Tbps] |
| Mirai Botnet Attacks (various targets) | 2016-2017 | IoT botnet, UDP floods | > 1 Tbps (in some cases) |
| GitHub DDoS Attack | 2018 | Memcached reflection/amplification | |
| Dyn DDoS Attack | 2016 | Mirai botnet, DNS amplification |
Future Implications and Predictions
The unprecedented scale of the recent DDoS attacks against Google underscores a chilling truth: the threat landscape is constantly evolving, and future attacks will likely be even more sophisticated and devastating. The sheer volume and complexity of these attacks highlight the urgent need for proactive measures and a fundamental shift in how we approach cybersecurity.
We are entering an era where the line between physical and digital infrastructure is increasingly blurred, making the consequences of successful attacks far-reaching.The future of DDoS attacks will be shaped by several key trends. We can expect to see a rise in attacks leveraging emerging technologies, a greater reliance on botnets comprised of IoT devices, and an increase in the use of sophisticated evasion techniques to bypass existing mitigation strategies.
Furthermore, the motivations behind these attacks will likely diversify, ranging from financially motivated actors to state-sponsored cyber warfare. The resulting impact could be catastrophic, disrupting critical infrastructure, crippling essential services, and causing significant economic damage.
Emerging DDoS Attack Techniques
The sophistication of DDoS attacks is rapidly increasing. We are already witnessing a move beyond simple volumetric attacks towards more targeted and complex methods. For example, application-layer attacks that exploit vulnerabilities in specific applications are becoming increasingly prevalent. These attacks are harder to detect and mitigate because they often appear as legitimate traffic. Another emerging trend is the use of encrypted traffic to mask malicious activity, making it difficult for security systems to identify and block the attack.
This requires a paradigm shift in detection mechanisms, moving beyond simple signature-based detection to more sophisticated behavioral analysis. Finally, the increasing use of AI and machine learning by both attackers and defenders will lead to an arms race in the development of more advanced techniques.
Evolution of Mitigation Strategies
The cybersecurity industry is responding to these escalating threats by developing more advanced mitigation strategies. This includes a shift towards AI-powered security solutions that can analyze traffic patterns and identify malicious activity in real-time. Cloud-based security solutions are also gaining popularity, offering scalable and flexible protection against DDoS attacks. Moreover, closer collaboration between industry players, government agencies, and researchers is crucial for sharing threat intelligence and developing effective countermeasures.
This collaborative approach is essential for staying ahead of the constantly evolving threat landscape. Improved network architectures, including the implementation of more robust routing protocols and the use of distributed denial-of-service mitigation systems, are also vital.
Potential Future Threats and Impact
The potential impact of future DDoS attacks is substantial. Consider the interconnected nature of modern infrastructure: a successful attack on a critical node could trigger a cascading failure across multiple systems.
- Increased reliance on critical infrastructure: Attacks targeting power grids, financial institutions, and healthcare systems could have devastating consequences, causing widespread disruption and potentially loss of life.
- Exploitation of IoT devices: The ever-growing number of IoT devices connected to the internet provides a massive pool of potential botnet participants, making larger and more distributed attacks easier to launch.
- Advanced evasion techniques: Sophisticated techniques like encrypted traffic and polymorphic malware make it harder to detect and mitigate attacks, increasing the likelihood of successful breaches.
- State-sponsored attacks: Nation-state actors may leverage DDoS attacks as a tool for cyber warfare, targeting critical infrastructure or disrupting the operations of rival nations.
- Financial losses: Successful DDoS attacks can lead to significant financial losses due to business disruption, data breaches, and reputational damage.
Closure
The “world’s largest” DDoS attack against Google serves as a stark reminder of the constant threat facing online services. While Google successfully repelled this massive assault, it underscores the need for continuous innovation in cybersecurity. The scale and sophistication of this attack push us to consider the future of online security and the potential for even larger, more devastating attacks.
It’s a wake-up call for everyone, from tech giants to individual users – we all need to be more vigilant and proactive in protecting ourselves in this increasingly interconnected world. The battle for online security is far from over, and this incident is just one chapter in a continuing saga.
Questions and Answers
What specific Google services were targeted in the attack?
While the exact services haven’t been publicly disclosed, it’s likely that the attack aimed for high-traffic services to maximize disruption.
Were any user data compromised during the attack?
There’s no indication that user data was compromised. DDoS attacks primarily target infrastructure, aiming to disrupt service availability, not steal information.
What are some of the emerging trends in DDoS attack mitigation?
Emerging trends include AI-powered threat detection, improved network segmentation, and the use of cloud-based DDoS mitigation services.
How can individuals protect themselves from DDoS attacks?
Individuals can’t directly defend against large-scale DDoS attacks, but they can practice good online hygiene, such as using strong passwords and keeping software updated.