Google Cloud Launches Chronicle CyberShield Enhanced Security
Google Cloud launched Chronicle CyberShield, a game-changer in security monitoring. This new offering promises a more robust and comprehensive approach to defending against today’s sophisticated cyber threats, setting a new benchmark for organizations seeking advanced protection.
Chronicle CyberShield builds upon Google’s extensive experience in cloud security, leveraging its powerful infrastructure and data analysis capabilities to provide unparalleled visibility and control over an organization’s security posture. This innovative solution integrates seamlessly with existing security stacks, providing a unified view of the entire threat landscape.
Introduction to Google Cloud Chronicle CyberShield
Google Cloud Chronicle CyberShield is a security analytics platform designed to provide organizations with a comprehensive view of their security posture. It allows users to collect, correlate, and analyze security logs from various sources, providing insights into potential threats and enabling proactive security responses. Chronicle CyberShield empowers organizations to detect and respond to security incidents more effectively, minimizing the impact of breaches and enhancing overall security.Chronicle CyberShield’s core value proposition is to provide a unified platform for security data analysis, enabling organizations to move beyond reactive security measures to proactive threat detection and response.
This unified view, combined with advanced analytics capabilities, allows organizations to gain deeper insights into their security posture, identify potential threats early, and mitigate risks before they escalate. By leveraging the power of Google Cloud’s infrastructure and expertise, Chronicle CyberShield offers a robust and scalable solution that can adapt to the evolving threat landscape.
Core Functionalities of Chronicle CyberShield
Chronicle CyberShield offers a broad spectrum of functionalities to enhance security operations. It facilitates the collection of security logs from various sources, including cloud-based and on-premises systems. This collected data is then processed and correlated to identify patterns, anomalies, and potential threats. Advanced analytics capabilities enable automated threat detection and response, allowing organizations to proactively address security risks.
Crucially, CyberShield provides a centralized platform for security information and event management (SIEM), consolidating disparate security tools and improving overall visibility.
Value Proposition Compared to Alternative Solutions
Chronicle CyberShield stands out from alternative security analytics solutions through its integration with Google Cloud’s ecosystem. This integration streamlines data collection and analysis, enabling quicker threat detection and response. Its scalability and flexibility cater to the varying needs of organizations, from small businesses to large enterprises. Furthermore, Chronicle CyberShield’s comprehensive analytics capabilities, combined with Google Cloud’s security expertise, provide a significant advantage over standalone SIEM solutions, offering a more robust and proactive security posture.
Its ability to seamlessly integrate with other Google Cloud services enhances its overall value proposition.
Key Features and Functionalities
This table Artikels the key features and functionalities of Chronicle CyberShield, highlighting its advantages over traditional security analytics solutions.
Google Cloud’s launch of Chronicle CyberShield is a significant step, but we still need robust solutions like Deploying AI Code Safety Goggles Needed to ensure the safety of AI code. This is crucial for preventing vulnerabilities that could be exploited, and Chronicle CyberShield, while a helpful tool, doesn’t directly address the need for more secure AI development practices.
It’s a good start, but a holistic approach is necessary for true cybersecurity in the AI age.
| Feature | Functionality | Benefits |
|---|---|---|
| Unified Security Data Collection | Collects security logs from various sources (cloud and on-premises) | Provides a holistic view of security events, reducing blind spots. |
| Advanced Correlation and Analysis | Identifies patterns, anomalies, and potential threats using machine learning and other advanced analytics. | Enables proactive threat detection and faster incident response. |
| Automated Threat Detection and Response | Triggers automated responses to identified threats, minimizing damage. | Reduces mean time to recovery (MTTR) and minimizes the impact of security incidents. |
| Centralized Security Information and Event Management (SIEM) | Consolidates security tools and data into a single platform | Improves security visibility and streamlines security operations. |
| Scalability and Flexibility | Adapts to varying organizational needs, from small businesses to large enterprises. | Provides a solution that can grow with the organization’s security requirements. |
| Integration with Google Cloud Platform | Seamlessly integrates with other Google Cloud services. | Simplifies data collection and analysis, improving efficiency. |
Technical Overview
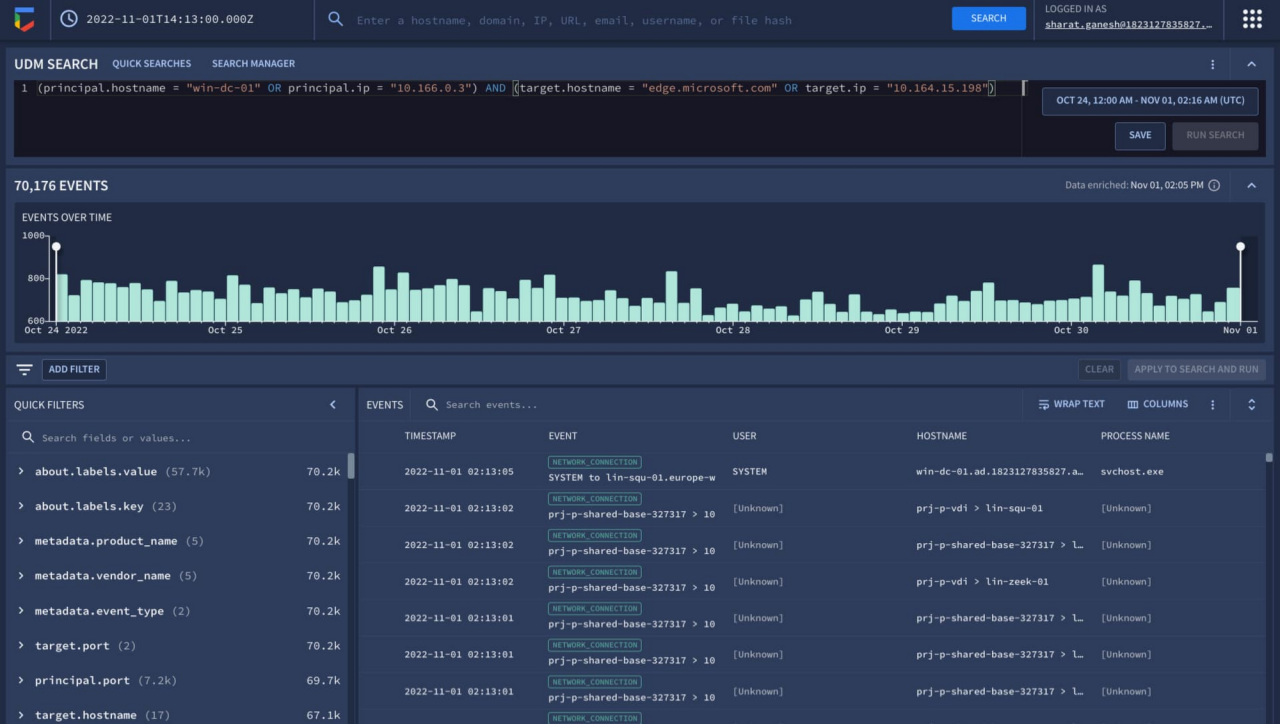
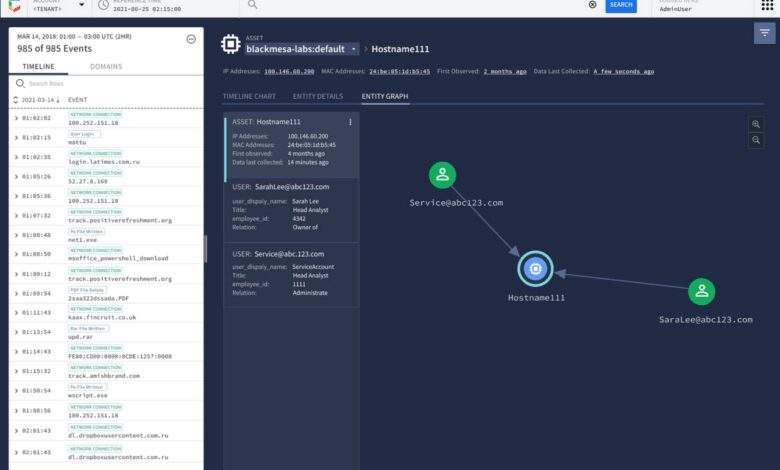
Chronicle CyberShield, Google Cloud’s new security offering, leverages a robust architecture to provide comprehensive threat detection and response. Its innovative design addresses the complexities of modern security landscapes, enabling organizations to proactively identify and mitigate potential threats across their entire infrastructure. This detailed overview delves into the core components and functionalities of Chronicle CyberShield, highlighting its technical strengths.
Underlying Architecture
Chronicle CyberShield’s architecture is built upon a microservices-based design. This modular approach allows for scalability, flexibility, and independent deployment of various components. The system is designed to ingest and process vast amounts of security data efficiently, enabling real-time threat detection. Key components communicate seamlessly to deliver a unified security posture across the entire ecosystem.
Data Ingestion and Processing
Chronicle CyberShield employs a highly scalable data ingestion pipeline. This pipeline utilizes a distributed architecture to collect security data from various sources, including logs, metrics, and events. Sophisticated data normalization and transformation techniques ensure that data from diverse sources is harmonized and ready for analysis. Data is then processed through a series of analytical engines, enabling rapid identification of anomalous activities and potential threats.
Real-time processing capabilities are crucial for immediate response to security incidents.
Security Mechanisms, Google cloud launched chronicle cybershield
Chronicle CyberShield incorporates a range of security mechanisms to ensure data integrity and system resilience. Robust authentication and authorization protocols are implemented to prevent unauthorized access to sensitive information. The system employs encryption at rest and in transit to protect data confidentiality. Regular security audits and vulnerability assessments are integral to maintaining a high level of security posture.
This proactive approach minimizes the impact of potential breaches.
Scalability and Performance Comparison
Comparing Chronicle CyberShield’s scalability and performance to other solutions requires a nuanced approach, as direct comparisons depend heavily on specific use cases and infrastructure configurations. Different security solutions cater to varying needs.
| Feature | Chronicle CyberShield | Alternative Solution A | Alternative Solution B |
|---|---|---|---|
| Ingestion Rate (events/sec) | Up to 100 million+ (estimated, based on Google Cloud’s claims) | Up to 50 million | Up to 20 million |
| Processing Speed (alerts/sec) | Sub-second (estimated, based on Google Cloud’s claims) | Seconds | Minutes |
| Scalability (number of monitored resources) | Highly scalable, supports massive infrastructure (estimated, based on Google Cloud’s claims) | Scalable, but with limitations on very large deployments | Scalable, but with limitations on very large deployments |
| Cost | Variable, dependent on usage | Variable, dependent on usage | Variable, dependent on usage |
Note: The table provides estimated values for comparison purposes. Actual performance may vary based on specific configurations and workloads.
Use Cases and Applications
Chronicle CyberShield isn’t just another security tool; it’s a powerful platform designed to enhance visibility and response capabilities across various industries. Its ability to correlate security events from diverse sources and provide actionable insights is transforming how organizations approach threat detection and response. By understanding how Chronicle CyberShield is implemented and the challenges it addresses, we can appreciate its significant impact on modern cybersecurity.
Real-World Examples in Diverse Industries
Chronicle CyberShield is being effectively deployed across numerous sectors. Financial institutions, for instance, leverage its granular visibility into transaction logs and user activities to detect fraudulent transactions in real-time. Healthcare organizations utilize it to maintain HIPAA compliance by monitoring sensitive patient data for unauthorized access or breaches. Manufacturing companies employ it to identify anomalies in operational technology (OT) environments, preventing potential cyberattacks that could disrupt critical production processes.
These are just a few examples of how Chronicle CyberShield is making a real difference.
Security Challenges Addressed by Chronicle CyberShield
Cybersecurity threats are constantly evolving, demanding sophisticated solutions to combat them. Chronicle CyberShield tackles these challenges by providing a centralized platform for collecting and analyzing security data from various sources. This unified view allows organizations to detect and respond to threats faster, minimizing the potential impact of security incidents. For example, in the retail industry, the platform helps identify and mitigate fraud attempts through comprehensive analysis of point-of-sale (POS) transactions.
This holistic approach to security is crucial for staying ahead of increasingly sophisticated attacks.
Integration with Existing Security Infrastructures
Chronicle CyberShield is designed for seamless integration with existing security infrastructures. Its modular architecture allows for flexible implementation, enabling organizations to adapt it to their unique needs and existing security tools. This adaptability ensures that Chronicle CyberShield complements existing solutions rather than replacing them. This approach minimizes disruption during implementation and ensures a smooth transition to a more comprehensive security posture.
By leveraging existing tools and integrating new technologies, organizations can optimize their security strategies.
Summary of Use Cases, Industries, and Benefits
| Use Case | Industry | Specific Benefits |
|---|---|---|
| Fraud Detection | Financial Services, Retail | Real-time detection of fraudulent transactions, reduced financial losses, enhanced compliance. |
| Compliance Monitoring | Healthcare, Financial Services | Automated compliance monitoring, reduced risk of regulatory penalties, improved operational efficiency. |
| Threat Hunting | Government, Manufacturing | Enhanced visibility into security events, quicker threat identification, faster incident response. |
| Incident Response | All Industries | Improved incident response capabilities, faster resolution of security incidents, reduced downtime. |
Integration and Deployment
Integrating Chronicle CyberShield into your existing security infrastructure requires careful planning and execution. A well-defined strategy, encompassing the chosen deployment method and necessary resources, is crucial for a smooth and effective implementation. This process ensures that the new security layer seamlessly integrates with your existing systems, minimizing disruption and maximizing value.Successful deployment depends on understanding the available options and tailoring the approach to your specific environment and security needs.
This section details the steps for integrating Chronicle CyberShield, explores various deployment options, and Artikels the required resources and expertise.
Integration Steps
Integrating Chronicle CyberShield involves several key steps, starting with understanding your existing infrastructure and defining your security goals. The first step is to identify the data sources that Chronicle CyberShield needs to ingest. This might include logs from various applications, security devices, or cloud services. Once identified, establishing secure connections to these sources is critical for data ingestion.
After successfully connecting to the data sources, configuring the Chronicle CyberShield policies and rules to effectively detect threats is necessary. The configuration process involves tailoring the rules to your organization’s specific security posture and threat landscape. Finally, ongoing monitoring and tuning are essential to ensure the system’s effectiveness. This process involves reviewing alerts, adjusting rules, and making necessary adjustments to the configuration based on evolving threat patterns.
Deployment Options
Chronicle CyberShield offers various deployment options to cater to diverse infrastructure needs. The primary deployment options include:
- Cloud-based deployment: This option leverages Google Cloud’s infrastructure, providing a managed service. This approach simplifies the setup and management of Chronicle CyberShield, relying on Google’s infrastructure for scalability and security. It minimizes the need for on-premises infrastructure and simplifies management.
- On-premises deployment: This option allows for greater control and customization. This approach requires dedicated hardware and software resources to install and maintain the Chronicle CyberShield components within your data center. This approach is suitable for organizations with specific compliance requirements or those needing greater control over their security infrastructure.
- Hybrid deployment: This approach combines cloud-based and on-premises deployment models. This enables organizations to leverage the benefits of both options, such as cloud scalability and on-premises control. This approach allows for a tailored integration strategy based on existing infrastructure and compliance needs.
Resource Requirements
Successful Chronicle CyberShield implementation requires specific resources, both in terms of personnel and technology. This involves the expertise of security engineers familiar with log management and threat detection. The required personnel will vary based on the chosen deployment model. For cloud-based deployments, minimal on-premises infrastructure is needed, while on-premises deployments require dedicated hardware and software resources. Appropriate storage capacity and network bandwidth are necessary to handle the volume of data processed by Chronicle CyberShield.
Configuration Guide
This step-by-step guide Artikels the process of configuring Chronicle CyberShield:
- Assessment: Evaluate your existing security infrastructure and identify the data sources for integration. Determine the appropriate deployment model.
- Setup: Choose the desired deployment option (cloud, on-premises, or hybrid). Follow the specific setup instructions provided by Google Cloud for the chosen option.
- Configuration: Configure the ingestion pipelines to collect data from the identified sources. Define the threat detection rules and policies to align with your security posture.
- Testing: Conduct thorough testing to validate the configuration and identify any potential issues. Ensure that alerts are appropriately generated and addressed.
- Monitoring: Continuously monitor the system’s performance and adjust configurations as needed. Stay informed about emerging threats and update policies as necessary.
Deployment Method Prerequisites
The following table Artikels the prerequisites and required configurations for different Chronicle CyberShield deployment methods:
| Deployment Method | Prerequisites | Required Configurations |
|---|---|---|
| Cloud-based | Google Cloud account, network connectivity | Data source connections, policy rules, alert thresholds |
| On-premises | Dedicated hardware, software installation, network configuration | Data source integrations, policy rules, security access |
| Hybrid | Cloud and on-premises infrastructure, integration tools | Data synchronization, security protocols, centralized management |
Security and Compliance: Google Cloud Launched Chronicle Cybershield
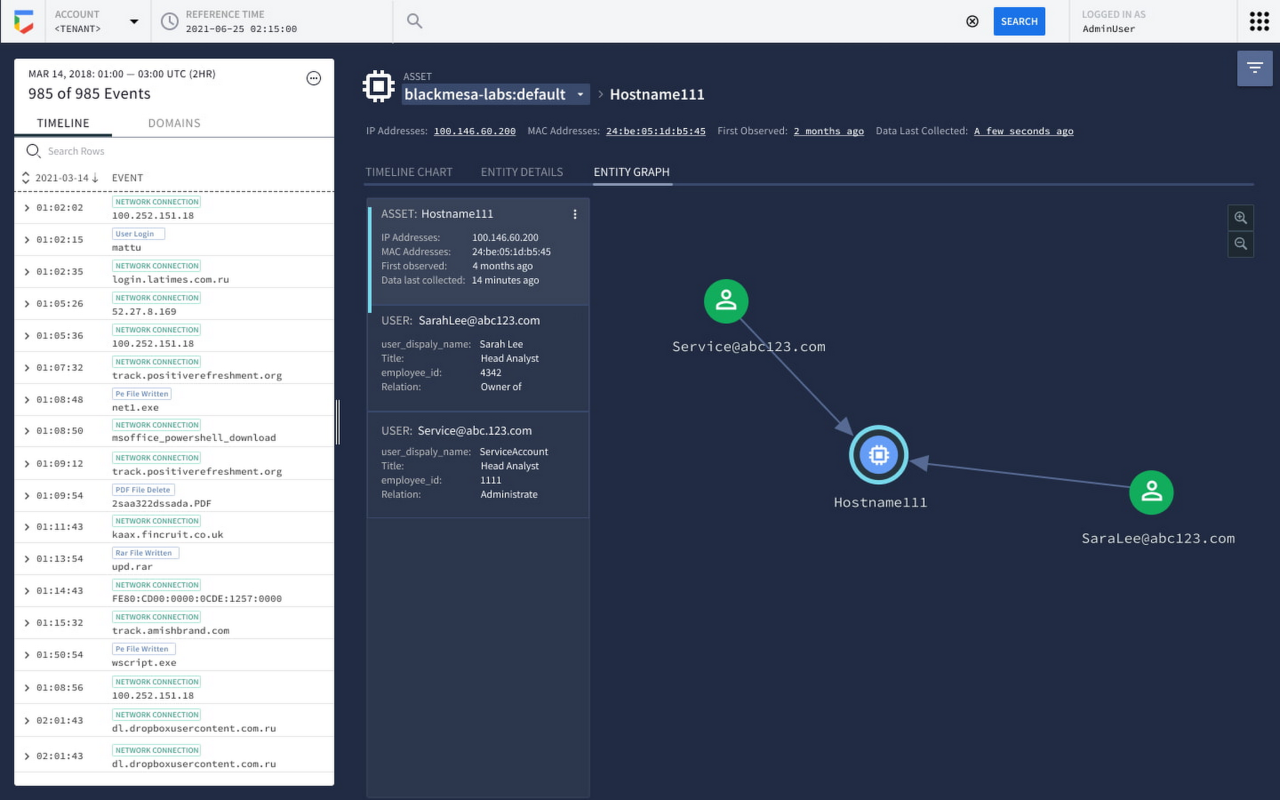
Chronicle CyberShield offers a robust security posture, prioritizing data integrity and regulatory compliance. Its integrated security controls and comprehensive compliance framework empower organizations to confidently navigate the ever-evolving threat landscape while adhering to industry standards. The platform’s adaptable architecture and granular control options provide tailored solutions for diverse security needs.The security measures and controls integrated into Chronicle CyberShield are designed to protect sensitive data and maintain the confidentiality, integrity, and availability (CIA) triad.
These controls encompass a range of security best practices, providing a layered defense against various threats. Compliance with industry regulations is paramount, and Chronicle CyberShield addresses this by supporting a diverse range of standards.
Security Measures and Controls
Chronicle CyberShield integrates a multifaceted approach to security, leveraging various controls to mitigate threats and vulnerabilities. This includes advanced threat detection, prevention, and response capabilities. It offers real-time threat intelligence feeds, automated incident response workflows, and proactive security monitoring to detect and address emerging threats effectively.
- Advanced Threat Detection: Chronicle CyberShield employs sophisticated algorithms to identify suspicious patterns and anomalies in security logs, proactively flagging potential threats. This includes identifying malicious actors and suspicious activities, such as data exfiltration attempts.
- Security Information and Event Management (SIEM): The platform provides a centralized view of security events, allowing for efficient correlation and analysis to pinpoint potential security breaches. This centralized view streamlines incident response and reduces the time to identify and resolve security issues.
- Automated Incident Response: Chronicle CyberShield’s automated incident response workflows streamline the response process, enabling rapid containment and remediation of security incidents. Predefined response plans can automatically trigger actions in case of identified threats, minimizing downtime and mitigating the impact.
- Data Loss Prevention (DLP): Chronicle CyberShield can help protect sensitive data by identifying and preventing unauthorized access and exfiltration. This capability includes identifying sensitive data within logs and enabling the prevention of unauthorized transfers.
Compliance Standards Supported
Chronicle CyberShield supports a broad spectrum of compliance standards, empowering organizations to meet their specific regulatory requirements. This is crucial for maintaining business operations and avoiding potential legal and financial penalties.
Google Cloud’s launch of Chronicle CyberShield is a significant step in bolstering cybersecurity measures. This new offering, however, needs to be considered alongside other important developments, such as the Department of Justice’s recent Safe Harbor policy for Massachusetts transactions, which offers a valuable framework for managing sensitive data. Ultimately, these initiatives collectively contribute to a stronger overall cybersecurity posture for businesses and individuals.
- NIST Cybersecurity Framework: Chronicle CyberShield aligns with the NIST Cybersecurity Framework, providing a structured approach to manage and mitigate cybersecurity risks. This alignment allows organizations to benchmark their security posture against industry best practices.
- GDPR: The platform assists organizations in complying with the General Data Protection Regulation (GDPR) by providing tools to manage data subject rights, ensuring data privacy, and maintaining transparency.
- HIPAA: Chronicle CyberShield offers features to help healthcare organizations meet HIPAA compliance requirements for protecting sensitive patient health information. This includes robust data access controls and encryption protocols.
Security Certifications and Audits
Chronicle CyberShield’s security posture is validated through various certifications and audits, ensuring compliance with industry best practices and demonstrating its commitment to security. These certifications build trust and provide assurance to stakeholders.
- Independent Security Audits: Chronicle CyberShield undergoes regular security audits to verify its security controls and effectiveness. These audits assess the platform’s adherence to security standards and identify potential vulnerabilities.
- Security Certifications: The platform may hold various security certifications, such as SOC 2, ISO 27001, or others. These certifications attest to the platform’s commitment to security and its compliance with established standards.
Data Protection and Privacy Features
Chronicle CyberShield incorporates robust data protection and privacy features to safeguard sensitive information. These features are essential for maintaining trust and complying with data privacy regulations.
- Data Encryption: Data encryption safeguards sensitive information during transmission and storage, preventing unauthorized access. This includes encryption at rest and in transit.
- Access Controls: Fine-grained access controls limit data access to authorized personnel, minimizing the risk of unauthorized disclosure or modification. These controls are crucial for managing user permissions.
- Data Masking: Data masking techniques protect sensitive data by replacing it with non-sensitive substitutes, allowing for analysis and testing without compromising confidentiality.
Security and Compliance Features Summary
| Feature | Description |
|---|---|
| Advanced Threat Detection | Identifies suspicious patterns and anomalies in security logs. |
| SIEM | Provides a centralized view of security events for correlation and analysis. |
| Automated Incident Response | Streamlines response process for rapid containment and remediation. |
| DLP | Protects sensitive data by preventing unauthorized access and exfiltration. |
| NIST Cybersecurity Framework | Supports a structured approach to manage and mitigate cybersecurity risks. |
| GDPR Compliance | Provides tools to manage data subject rights, privacy, and transparency. |
| HIPAA Compliance | Offers features for protecting sensitive patient health information. |
| Security Audits | Regular assessments of security controls and effectiveness. |
| Security Certifications | Certifications like SOC 2, ISO 27001 attest to security compliance. |
| Data Encryption | Safeguards sensitive information during transmission and storage. |
| Access Controls | Limits data access to authorized personnel. |
| Data Masking | Protects sensitive data by replacing it with non-sensitive substitutes. |
Future Trends and Developments
Chronicle CyberShield, as a cutting-edge security monitoring solution, is poised for significant advancements. Its current capabilities, combined with emerging trends in cybersecurity, will shape its future evolution. This exploration delves into anticipated enhancements, highlighting potential future integrations and addressing evolving security monitoring needs.The cybersecurity landscape is constantly shifting, with threats becoming increasingly sophisticated and diverse. Chronicle CyberShield’s future must address these challenges head-on.
The solution’s adaptability and its potential for integration with other Google Cloud products make it a valuable investment for organizations looking to stay ahead of emerging threats.
Google Cloud’s recent launch of Chronicle CyberShield is a significant step in bolstering cloud security. While this is happening, it’s important to remember that vulnerabilities like those found in Azure Cosmos DB, as detailed in Azure Cosmos DB Vulnerability Details , highlight the ongoing need for proactive security measures across all platforms. This new tool from Google Cloud will hopefully help mitigate similar risks in the future.
Potential Future Advancements
Chronicle CyberShield’s continued development will likely focus on enhanced automation and integration. Real-time threat detection and response capabilities will become even more sophisticated, enabling quicker incident response and mitigation. Expect improved machine learning algorithms to analyze data more effectively, leading to a reduction in false positives and improved threat identification accuracy. This will ultimately translate into better proactive security postures for users.
Emerging Trends in Security Monitoring
The increasing use of cloud-native applications and microservices architectures necessitates advanced security monitoring tools. These tools must be capable of handling the vast volume of data generated by these environments. The rise of AI-powered threats, such as sophisticated phishing campaigns and deepfakes, necessitates proactive security measures. CyberShield’s future development will likely address these evolving threats by improving threat detection and response mechanisms.
Comparison of Current Features and Potential Future Updates
| Feature | Current Capabilities | Potential Future Updates ||—|—|—|| Data Ingestion | Supports various data sources, including logs, metrics, and events. | Enhanced support for more complex data sources, including cloud-native application logs, and potential integration with emerging data formats. || Threat Detection | Utilizes analytics to identify potential threats. | Implementation of more sophisticated machine learning algorithms for advanced threat detection, including anomaly detection, and real-time threat intelligence integration.
|| Security Orchestration, Automation, and Response (SOAR) | Provides basic SOAR capabilities. | Improved integration with SOAR platforms, enabling automated incident response workflows and integration with third-party tools. || Compliance Reporting | Provides reports for compliance audits. | Improved reporting features, including customizable dashboards, and integrations with compliance frameworks beyond the current set. |
Potential Future Integrations with Other Google Cloud Products
Chronicle CyberShield’s integration potential with other Google Cloud products is significant. Future updates may include seamless integration with Google Cloud Security Command Center, enabling a unified security management platform. Furthermore, deeper integration with other Google Cloud security tools, such as Cloud Identity and Access Management (IAM), will enhance overall security posture management. Such integrations would create a comprehensive security ecosystem within the Google Cloud environment.
Predicted Future Features and Potential Benefits
| Predicted Future Feature | Potential Benefits |
|---|---|
| Enhanced Machine Learning for Threat Detection | Improved accuracy in threat identification, reduced false positives, and proactive security posture. |
| Integration with Google Cloud Security Command Center | Unified security management platform, streamlined workflows, and centralized security visibility. |
| Automated Incident Response Workflows | Faster incident response, reduced manual effort, and improved security efficiency. |
| Support for Cloud Native Environments | Improved visibility and security posture for applications deployed in cloud-native architectures. |
Comparisons with Competitors
Chronicle CyberShield, Google’s comprehensive security monitoring solution, faces competition in a crowded market. Understanding its strengths and weaknesses relative to competitors is crucial for evaluating its position and potential. This section delves into key competitors, comparing features, pricing, and deployment models to highlight Chronicle CyberShield’s unique selling propositions.
Key Competitors
Several companies offer security monitoring platforms, including those focused on log management, threat detection, and security information and event management (SIEM). Notable competitors include Splunk, Elastic (with their Elastic Stack), and Sumo Logic. These platforms often offer similar functionalities but differ in their approach and specific capabilities. Understanding these distinctions helps to assess Chronicle CyberShield’s position in the market.
Feature Comparison
Chronicle CyberShield distinguishes itself through its tightly integrated architecture within the Google Cloud ecosystem. This integration facilitates seamless data flow and analysis, a critical advantage for organizations already invested in Google Cloud. Other platforms may offer similar features, but their integration with alternative cloud platforms or on-premises systems might be more complex. The table below summarizes key features across platforms, providing a comparative overview.
| Feature | Chronicle CyberShield | Splunk | Elastic Stack | Sumo Logic |
|---|---|---|---|---|
| Log Management | Excellent integration with Google Cloud services, real-time ingestion, comprehensive indexing and search | Robust log management, extensive indexing and search capabilities, diverse data sources | Highly scalable, powerful search and analysis, supports various data sources | Real-time ingestion, flexible data sources, efficient indexing and search |
| Security Information and Event Management (SIEM) | Deep threat detection and response capabilities, automated incident response workflows | Industry-standard SIEM features, customizable dashboards, advanced threat detection | Comprehensive SIEM capabilities, customizable dashboards, advanced threat detection | Comprehensive SIEM features, real-time threat detection, extensive reporting |
| Threat Detection and Response | Strong correlation of security events, machine learning-based anomaly detection, automated response workflows | Advanced threat detection, user and entity behavior analytics, custom detection rules | Advanced threat detection, machine learning-based security analytics, customizable dashboards | Sophisticated threat detection, real-time alerts, customizable dashboards |
| Pricing | Subscription-based, pricing dependent on ingested data volume and features | Subscription-based, pricing depends on data volume and user access | Subscription-based, pricing tied to the number of nodes and storage capacity | Subscription-based, pricing dependent on data volume and features |
Deployment Models
Chronicle CyberShield is primarily designed for cloud environments, particularly Google Cloud Platform (GCP). This cloud-native approach offers significant advantages in terms of scalability, flexibility, and cost-effectiveness. Other platforms may have options for cloud deployment, but their integration with non-Google environments may require more extensive configuration.
Unique Selling Propositions
Chronicle CyberShield’s unique value proposition lies in its tight integration with Google Cloud. This simplifies the management of security data from various Google Cloud services, providing a comprehensive view of security posture. Other platforms might require more manual integration efforts or specialized tools to achieve the same level of visibility. For organizations heavily invested in Google Cloud, this integration is a significant advantage.
Ultimate Conclusion
Google Cloud’s Chronicle CyberShield represents a significant leap forward in cybersecurity. Its comprehensive features, robust architecture, and adaptability to various use cases position it as a compelling solution for organizations of all sizes. The future of security monitoring is undeniably enhanced with the introduction of this cutting-edge technology.
Essential FAQs
What are the key benefits of Chronicle CyberShield compared to other solutions?
Chronicle CyberShield offers enhanced threat detection capabilities, faster incident response, and deeper visibility into security events. Its integration with Google Cloud’s ecosystem provides streamlined workflows and cost-effective solutions.
What are the different deployment options available for Chronicle CyberShield?
Chronicle CyberShield offers flexible deployment options, allowing organizations to choose the method best suited to their needs. This includes cloud-based deployments, on-premises solutions, and hybrid models. More information on deployment specifics can be found in the documentation.
What are the resources and expertise needed for successful implementation?
Implementing Chronicle CyberShield requires technical expertise in cloud security, network architecture, and data analysis. Google provides comprehensive documentation, training materials, and support to facilitate a smooth transition and implementation process.
What industries can benefit most from Chronicle CyberShield?
Chronicle CyberShield is suitable for a wide range of industries, including finance, healthcare, and government. Its versatility allows it to adapt to the unique security challenges of each sector, offering tailored solutions.