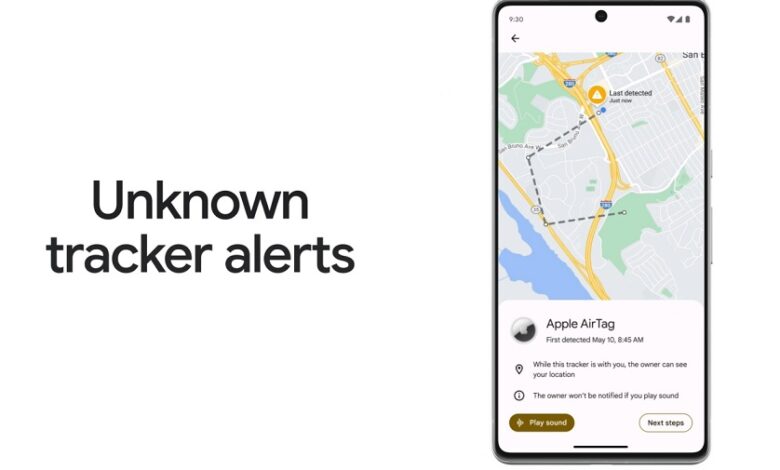
Google Find My Device Phone Security Deep Dive
Google Find My Device helps secure your information stored on the phone to the core. This comprehensive guide explores the robust security measures employed by Google Find My Device, delving into its core functionality and how it safeguards your phone’s data. We’ll examine the different ways this service enhances security, from encryption protocols to real-world use cases. Learn how your data is protected and how you can use this tool effectively to keep your information safe.
From the fundamental principles of data protection to the technical details behind the service, this exploration offers a complete picture of Google Find My Device’s capabilities. We’ll also discuss potential limitations and vulnerabilities, providing you with the knowledge to make informed decisions about your phone’s security.
Introduction to Google Find My Device
Google Find My Device is a powerful tool that allows users to locate, manage, and secure their lost or stolen Android devices. It leverages a network of Google servers and your device’s location services to provide real-time tracking and control. Beyond simple location, it offers critical security features that go far beyond just finding a phone.This service integrates seamlessly with other Google services, providing a unified platform for managing your digital footprint.
The fundamental principle behind Google Find My Device is the protection of your personal information, and the service empowers users to safeguard their data against potential threats.
Core Function of Find My Device
Find My Device’s primary function is to locate a missing or lost Android device. It does this by utilizing GPS and Wi-Fi signals to pinpoint the device’s location on a map. Beyond location, it offers options to remotely lock the device, erase its data, or make it ring, even if the device is offline. This multifaceted approach helps users reclaim their device or protect sensitive data from falling into the wrong hands.
Enhanced Security Features
Find My Device enhances security in several ways. Remote lock functionality allows you to instantly secure your device by locking the screen and preventing unauthorized access. Remote data wiping is another vital feature. This allows you to erase all data from your device, including personal photos, videos, contacts, and sensitive information, preventing it from falling into the wrong hands.
The ring feature, useful in crowded or hard-to-locate environments, emits a loud sound even if the device is in silent mode, enabling quick retrieval.
Integration with Other Google Services
Find My Device is deeply integrated with other Google services, providing a unified approach to managing your devices. This integration streamlines the process of securing and managing multiple devices, as actions taken through Find My Device often reflect in other Google services. For example, a locked device will often prevent unauthorized access to related Google accounts.
Data Protection and Security Principles
Google Find My Device prioritizes data protection and security. The service employs robust encryption protocols to safeguard your device’s location data and other information transmitted to Google servers. This encryption ensures that even if the data is intercepted, it remains unreadable to unauthorized individuals. The service adheres to strict privacy policies, with your data used solely for the intended purpose of device management and security.
Features and Benefits
| Feature | Description | Security Benefit |
|---|---|---|
| Remote Lock | Instantly locks the device, preventing unauthorized access. | Protects sensitive data and prevents misuse. |
| Remote Wipe | Deletes all data from the device. | Eradicates sensitive information from the device, preventing data breaches. |
| Ring | Makes the device ring, even if it’s in silent mode. | Helps locate the device in crowded or difficult-to-find environments. |
| Location Tracking | Provides real-time location tracking of the device. | Allows for the quick retrieval of the device. |
Data Security Mechanisms
Google Find My Device prioritizes the security of user data. Robust security protocols and encryption methods are crucial for protecting sensitive information from unauthorized access and ensuring the confidentiality and integrity of user accounts. This detailed explanation delves into the mechanisms employed to safeguard user information.Data security is paramount in the digital age. Protecting user information is paramount to building trust and maintaining the integrity of the service.
Find My Device employs multiple layers of security to mitigate potential threats and safeguard user data.
Encryption Methods
Find My Device utilizes advanced encryption techniques to protect data at rest and in transit. This multi-layered approach involves both symmetric and asymmetric encryption methods. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption uses separate keys for these processes. This combination ensures data confidentiality and integrity.
Data Protection Protocols
Google employs robust protocols to safeguard user data from unauthorized access. These protocols include stringent authentication measures, access controls, and regular security audits. These protocols are designed to deter unauthorized access attempts and respond effectively to any potential security breach.
Safeguarding User Information
To safeguard user information, Google implements multi-factor authentication (MFA). This adds an extra layer of security by requiring users to provide multiple verification methods, such as a code sent to their phone or an authentication app. This further strengthens the security posture of the service.
Data Integrity and Confidentiality
Data integrity ensures that information remains accurate and consistent throughout its lifecycle. Data confidentiality, on the other hand, protects sensitive information from unauthorized disclosure. These two principles are crucial in maintaining trust and ensuring the reliability of the service. Find My Device is committed to upholding both data integrity and confidentiality.
Security Threats and Countermeasures
| Security Threat | Google Find My Device Countermeasure |
|---|---|
| Unauthorized access attempts | Multi-factor authentication, rigorous access controls, and continuous security monitoring |
| Malware infections | Regular security updates, threat detection systems, and user awareness programs |
| Phishing attacks | User education on phishing tactics, robust email authentication, and secure account management |
| Data breaches | Security audits, incident response plans, and encryption technologies to protect data at rest and in transit |
| Denial-of-service attacks | Robust infrastructure, distributed network architecture, and advanced threat detection systems |
Phone Data Protection
Protecting the data on your phone is paramount in today’s digital world. Google Find My Device goes beyond just locating a lost phone; it plays a crucial role in safeguarding the sensitive information stored on it. This section delves into the mechanisms employed by the service to secure your data, and the steps you can take to further bolster its protection.Google Find My Device employs a layered approach to data security, incorporating encryption and access controls to prevent unauthorized access.
This multi-faceted strategy is designed to protect various types of data, from personal communications to financial records. The strength of these measures is often compared to other comparable device management services.
Security Mechanisms for Stored Data
The security of your phone’s data hinges on robust encryption protocols and strict access controls. Google leverages industry-standard encryption methods to safeguard your information. These methods ensure that even if the device is compromised, the data remains unreadable without the proper decryption keys.
Steps to Ensure Data Protection
Implementing a multi-layered approach to data security is crucial. Enabling device encryption, setting strong passwords, and regularly updating your phone’s software are essential preventative measures. Enabling two-factor authentication further adds an extra layer of protection.
Google Find My Device is a powerful tool for securing your phone’s data. It’s crucial for protecting your information, and a similar concept, like the Department of Justice Offers Safe Harbor for MA Transactions here , emphasizes the importance of safeguarding sensitive data. Ultimately, keeping your phone secure with tools like Find My Device is key to maintaining peace of mind about your personal information.
Examples of Protected Data Types
Google Find My Device protects a wide range of data types. This includes, but is not limited to, contacts, messages, photos, videos, documents, and financial data. Protecting this diverse range of data is critical to ensuring your personal and financial well-being.
Google Find My Device is a fantastic tool for securing your phone’s data. It’s incredibly helpful for retrieving lost or stolen devices, and the core function of protecting your stored information is invaluable. However, recent vulnerabilities in other cloud storage systems, like those highlighted in the Azure Cosmos DB Vulnerability Details , remind us that robust security measures are essential everywhere, even on your personal devices.
Ultimately, Find My Device remains a powerful asset in protecting your phone’s contents.
Comparison with Other Services
Compared to other device management services, Google Find My Device excels in its comprehensive approach to data protection. While other services may focus on specific data types or have less robust encryption, Find My Device prioritizes a multi-layered approach. The strength of this multifaceted approach is a key differentiator.
Data Protection Mechanisms Table
| Data Type | Security Mechanism | Explanation |
|---|---|---|
| Personal Contacts | End-to-End Encryption | Data is encrypted both in transit and at rest, meaning it cannot be read by unauthorized parties even if the device is compromised. |
| Financial Data (e.g., bank accounts) | Secure Storage and Access Control | Financial data is typically stored separately from other data and access is restricted to authorized personnel and/or specific applications. |
| Photos and Videos | Data Encryption and Access Control | Images and videos are encrypted, and access to them is controlled by user passwords and permissions. |
| App Data | App-Specific Security Measures | Individual applications often have their own security mechanisms to protect data specific to the app. |
Real-World Use Cases: Google Find My Device Helps Secure Your Information Stored On The Phone To The Core
Google Find My Device isn’t just a theoretical tool; it’s a powerful, practical resource with real-world applications that help individuals and businesses safeguard their sensitive information. Its effectiveness in preventing data breaches and recovering lost devices is demonstrably high, and understanding its practical applications can empower users to leverage its potential.The service’s efficacy in protecting data extends beyond simple device recovery.
It serves as a vital layer of security, acting as a deterrent and a robust response mechanism in the event of theft or loss. By enabling remote actions like location tracking, device locking, and data erasure, Find My Device transforms a potentially catastrophic situation into a manageable one. This proactive approach to data protection is critical for both personal and professional contexts.
Preventing Data Breaches
Effective data protection is not just about reacting to a breach; it’s about proactively minimizing the risk. Find My Device helps achieve this by allowing immediate action to prevent unauthorized access to sensitive data. If a phone is lost or stolen, the ability to remotely lock it and erase data is crucial in mitigating the potential for a data breach.
This proactive measure significantly reduces the damage caused by a security incident. Remote data wiping ensures that sensitive information, including personal documents, financial records, and confidential business communications, remains inaccessible to unauthorized individuals.
Recovering Lost or Stolen Phones
Real-world scenarios demonstrate the significant impact of Find My Device in recovering lost or stolen phones. A user might accidentally leave their phone on a train or lose it in a crowded area. The ability to track the device’s location and remotely lock it, preventing unauthorized use, can make the difference between recovering the phone and losing valuable data.
In cases of theft, this capability allows law enforcement to assist in retrieving the device and potentially identifying the perpetrators. Moreover, the remote locking feature helps prevent the thief from accessing sensitive information or using the phone for malicious activities.
Practical Applications in Various Scenarios
Find My Device’s practical applications span a broad range of scenarios, demonstrating its value in everyday life. Imagine a scenario where a parent loses track of their child’s phone. Real-time location tracking through Find My Device allows for quick and easy recovery. For business users, the service can help track company-owned devices in case of loss or theft, preventing unauthorized access to confidential data.
Furthermore, the service is valuable in cases of emergency, enabling quick location identification and assistance.
Data Protection in Personal and Business Contexts
Data protection is fundamental for both individuals and businesses. Protecting personal information, such as financial details, medical records, and personal contacts, is crucial to maintain privacy and prevent identity theft. Similarly, for businesses, the protection of sensitive data, including client information, intellectual property, and financial records, is critical for maintaining reputation and operational continuity. Breaches can have significant financial and reputational consequences.
Find My Device acts as a critical safeguard in both these contexts.
Use Case Examples
| Scenario | Action | Outcome |
|---|---|---|
| Phone lost in a crowded market | Use Find My Device to track the phone’s location. | Phone is recovered, preventing data loss. |
| Employee’s company phone stolen | Remotely lock the phone and erase data. | Data is protected, minimizing potential damage. |
| Child’s phone misplaced | Track the phone’s location and remotely send a message. | Child’s phone is found, and important communication is facilitated. |
| Remote work device lost | Use Find My Device to locate the device and remotely lock it. | Device is recovered and sensitive company data is protected. |
Security Considerations and Limitations
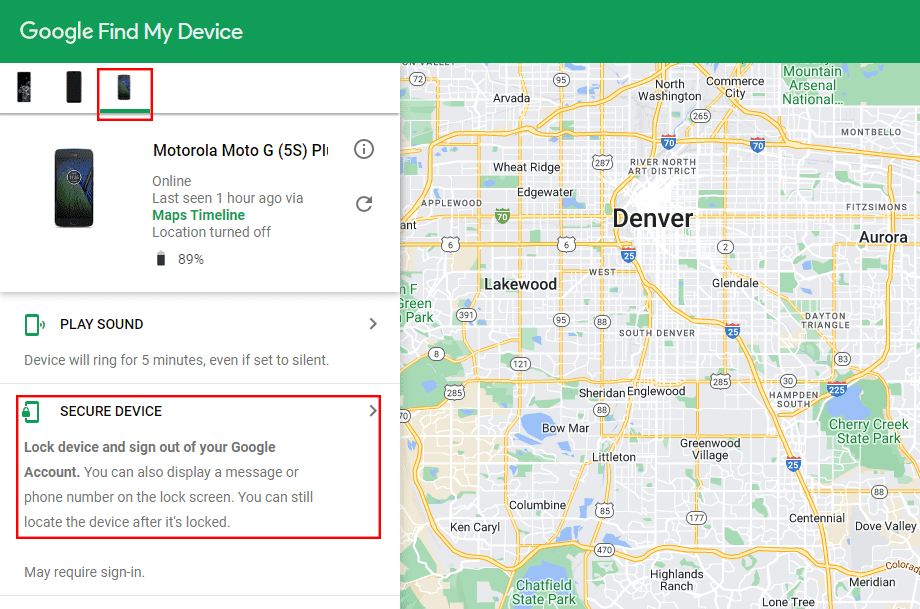
Google Find My Device, while a powerful tool, isn’t invulnerable. Understanding its potential vulnerabilities and limitations is crucial for responsible use. Its effectiveness depends not only on the service itself, but also on the user’s proactive security measures.While Google employs robust security mechanisms, inherent limitations exist. These limitations can stem from the inherent nature of the technology or external factors, and users need to be aware of these to protect their devices and data.
Potential Vulnerabilities
Google Find My Device relies on network connectivity to function. A compromised network connection, whether due to malicious actors or a flawed configuration, can potentially expose the device to security risks. Similarly, if the account associated with the device is compromised, unauthorized access to the device’s location and data becomes a possibility.
Account Security
Strong password management and two-factor authentication are paramount. Regular account reviews and prompt password changes upon suspicion of compromise are essential security measures. Users should be wary of phishing attempts and avoid clicking on suspicious links or downloading attachments from unknown sources. Actively monitoring account activity and reporting any unusual patterns is critical.
User Responsibility in Maintaining Security
User vigilance plays a significant role in maintaining the security of their accounts and devices. Regular updates and maintenance of the operating system on the target device and on the user’s own devices are crucial. Keeping software updated mitigates known vulnerabilities and helps protect against evolving threats. Awareness of the service’s limitations and potential risks is essential.
Steps to Protect Accounts
Using strong, unique passwords for each online account, especially the one linked to Find My Device, is vital. Activating two-factor authentication (2FA) adds an extra layer of security, requiring a second verification method beyond a password. Regularly reviewing account activity and promptly reporting any suspicious login attempts or other unusual patterns is essential. Maintaining updated anti-virus software on personal devices is also critical.
Google Find My Device is a lifesaver for securing your phone’s data, but what about the code behind the apps and services you use? Protecting your data on your phone goes beyond just location tracking; it also means thinking about the safety of the code itself. For example, consider the need for “AI Code Safety Goggles” as discussed in Deploying AI Code Safety Goggles Needed.
Ultimately, robust code protection, like Find My Device, is crucial for safeguarding all your information stored on your phone.
Summary of Potential Threats, Vulnerabilities, and Mitigation Strategies
| Potential Threat | Vulnerability | Mitigation Strategy |
|---|---|---|
| Compromised Network | Unauthorized access to device location and data | Use a secure Wi-Fi network, avoid public Wi-Fi when possible, and use a VPN for added security |
| Compromised Account | Unauthorized access to device location and data | Strong passwords, two-factor authentication (2FA), regular account reviews, and reporting suspicious activity |
| Phishing Attempts | Compromised account | Be cautious of suspicious emails, links, and attachments. Verify the legitimacy of requests before providing personal information. |
| Outdated Software | Exploitable vulnerabilities | Regularly update the operating system and applications on both the target device and user devices. |
Technical Details (Advanced)
Google Find My Device relies on a complex network infrastructure to locate and manage lost or stolen devices. This intricate system involves various components, from the device itself to Google’s global servers. Understanding the technical underpinnings provides a deeper appreciation for the service’s capabilities and limitations.The core of Find My Device’s functionality revolves around a robust data protection system.
This includes encryption mechanisms, secure communication channels, and access controls designed to safeguard user data. The service is built with a meticulous approach to preventing unauthorized access and maintaining data integrity.
Technical Infrastructure Overview
The Google Find My Device infrastructure is a distributed system spanning multiple data centers globally. This distributed architecture enhances reliability and scalability. Individual devices register with Google’s servers, sharing location information and other relevant data. These servers, through a complex network of communication protocols, consolidate and process the data to provide the user interface. The system is designed to handle a massive volume of device registrations and location updates, ensuring smooth operation even under peak demand.
This global network is vital for locating devices in various time zones and geographical regions.
Data Protection Mechanisms
Data protection in Find My Device is multi-layered. Encryption plays a crucial role in securing the data transmitted between the device and Google’s servers. The service employs industry-standard encryption algorithms to protect the confidentiality of location data and other sensitive information. Access to this data is strictly controlled through authentication protocols and authorization policies, preventing unauthorized access.
Regular security audits and penetration testing are integral parts of the maintenance process to ensure the service’s resilience against evolving threats.
Security Standards Adhered To
Google Find My Device adheres to a rigorous set of security standards. These standards encompass data privacy regulations (like GDPR and CCPA) and industry best practices. The service undergoes regular security assessments to identify and mitigate potential vulnerabilities. Security audits ensure compliance with established industry security standards, providing an extra layer of protection for user data. The commitment to security standards demonstrates Google’s dedication to safeguarding user information.
Comparison with Similar Services
Comparing Find My Device with other similar services reveals a blend of common and unique approaches. While several services use GPS location data, Find My Device often leverages additional signals for enhanced accuracy, including Wi-Fi and cellular networks. The data protection measures employed by Find My Device are comparable to those in other prominent location-based services, emphasizing the importance of securing user information.
However, specific implementation details and the extent of integration with other Google services may vary.
Core Security Algorithms
Find My Device utilizes a combination of cryptographic algorithms for secure data transmission and storage. These include Advanced Encryption Standard (AES) for encrypting location data and other sensitive information. The use of asymmetric encryption ensures secure communication between the device and Google servers. Hashing algorithms are employed for data integrity checks, further enhancing the security posture. These algorithms, combined with robust access controls, form the foundation of Find My Device’s data protection.
Future Trends and Developments
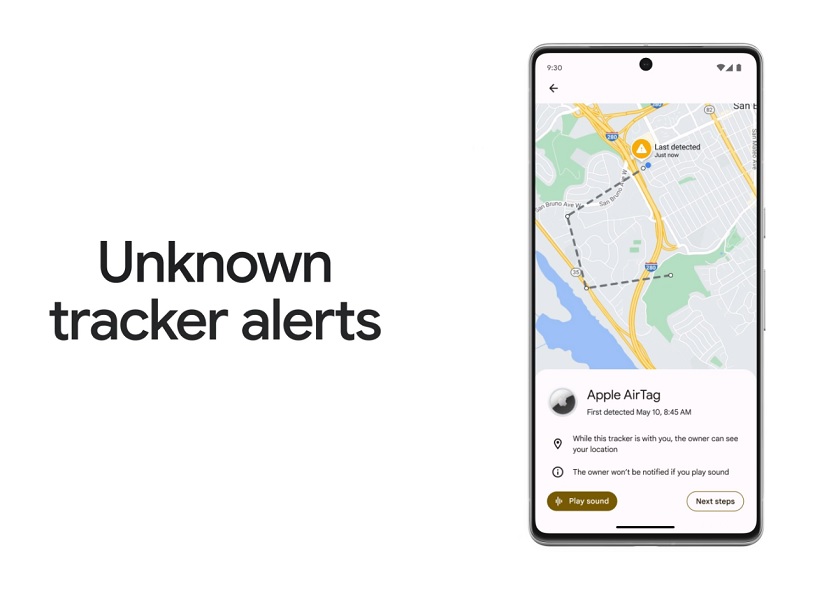
Google Find My Device, a cornerstone of mobile security, is poised for continued evolution. Anticipating future trends in mobile technology and evolving threats is crucial for maintaining the service’s effectiveness and user trust. This section explores potential future enhancements and adaptations.
Potential Future Enhancements
The mobile security landscape is dynamic, with new threats and vulnerabilities constantly emerging. Google Find My Device must adapt to these changes to remain a reliable tool for users. Anticipating these future needs is vital for proactive security measures.
- Enhanced Location Tracking Accuracy: Integration with cutting-edge location technologies, such as improved GPS, Wi-Fi triangulation, and potentially even cellular network triangulation, will enhance location accuracy, potentially enabling real-time tracking in more challenging environments. This refinement would prove invaluable for locating lost or stolen devices, particularly in urban settings with high signal density.
- Predictive Security Measures: Leveraging machine learning and AI, Google Find My Device could predict potential threats to a user’s device. For example, if unusual activity is detected on a device (e.g., multiple login attempts from unknown locations), the service could issue an alert or automatically implement security measures. This proactive approach would minimize the window of opportunity for malicious actors.
- Integration with Wearable Devices: Find My Device could seamlessly integrate with smartwatches and other wearable devices. This would allow users to initiate tracking and security measures from their wrist, potentially increasing the speed and ease of device recovery.
- Improved Cross-Platform Compatibility: Enhanced compatibility across different operating systems and devices (including IoT devices) will enable more comprehensive device management and location tracking. This will broaden the scope of device protection for a broader user base.
Future Trends in Mobile Security, Google find my device helps secure your information stored on the phone to the core
Emerging trends in mobile security have a significant impact on Google Find My Device. The proliferation of IoT devices, the increasing sophistication of cyberattacks, and the rise of cloud-based services all influence the evolving nature of mobile threats.
- Rise of IoT Threats: The increasing connectivity of devices beyond smartphones (e.g., smart home devices, wearables) creates new avenues for attack. Google Find My Device might need to expand its capabilities to secure and manage these connected devices, potentially through dedicated security protocols and alerts.
- Sophisticated Phishing Attacks: The growing sophistication of phishing attacks requires more robust authentication and verification methods. Find My Device might need to incorporate more advanced security protocols, such as multi-factor authentication or biometric verification, to mitigate the risk of unauthorized access.
- Cloud-Based Data Security: The increasing reliance on cloud services for data storage and processing necessitates improved security protocols within the Find My Device platform. Robust encryption and access controls are essential to safeguard user data. A recent example of this is the increased concern over cloud storage breaches and the subsequent importance of strong encryption protocols.
Emerging Technologies and their Influence
Several emerging technologies hold the potential to reshape mobile security and influence Google Find My Device.
- Blockchain Technology: Blockchain’s inherent security features, such as immutability and transparency, could potentially enhance the security and integrity of data transmitted and stored within Find My Device. This could increase user confidence and trust in the system’s security.
- AI-Powered Threat Detection: Artificial intelligence and machine learning algorithms can analyze vast amounts of data to identify patterns and anomalies indicative of potential security threats. This allows for faster and more accurate detection of malicious activity, ultimately leading to more timely responses to potential threats.
- Quantum Computing: While still in its nascent stages, quantum computing has the potential to revolutionize data encryption. This might necessitate the development of quantum-resistant encryption methods to protect user data from future threats.
Conclusion
In conclusion, Google Find My Device provides a powerful layer of security for your phone and its stored information. Understanding its security mechanisms, real-world applications, and potential limitations empowers you to use the service effectively. By prioritizing security and adopting proactive measures, you can significantly enhance the protection of your valuable data. Remember that responsible use and awareness of potential risks are key components in maintaining a secure digital environment.
Helpful Answers
What types of data does Google Find My Device protect?
Google Find My Device protects a wide range of data stored on your phone, including personal information, financial records, photos, videos, and sensitive documents. It also safeguards data from apps and services you use.
What are some common security threats to my phone data?
Common threats include unauthorized access through hacking, malware, or physical theft. Data breaches and loss of your device can compromise your personal information.
How does Google Find My Device protect against data breaches?
Google Find My Device utilizes encryption and other security protocols to protect your data. It also provides features to locate and remotely wipe your phone if lost or stolen, minimizing the impact of a potential breach.
What steps should I take to further protect my account?
Use strong passwords, enable two-factor authentication, and regularly review your account activity for suspicious activity. Be mindful of phishing scams and protect your device from physical theft.





