Google to Use Apple iPhones and Android Devices to Block Phishing Attacks
Google to Use Apple iPhones and Android Devices to Block Phishing Attacks – that headline alone grabbed my attention! Imagine a world where Google collaborates with Apple, transcending the usual tech rivalry to fight a common enemy: phishing scams. This isn’t just about improved security; it’s about a potential paradigm shift in how we approach online safety. This post dives into the exciting possibilities, the technical hurdles, and the potential privacy implications of this ambitious project.
The idea is revolutionary. Google’s proposed system would leverage the vast data streams from both iOS and Android devices to identify and neutralize phishing attempts before they even reach users. This means a unified front against a threat that impacts everyone, regardless of their preferred operating system. But how will they pull this off technically? What data will be shared?
And what are the implications for user privacy? Let’s explore.
Google’s Motivation for Cross-Platform Phishing Block

Google’s expansion into a cross-platform anti-phishing solution, encompassing both Apple iOS and Android devices, is a strategic move driven by multiple factors, primarily aiming to enhance user trust and strengthen its own ecosystem. This initiative transcends simple security improvements; it represents a significant investment in user experience and brand reputation.The benefits for Google are multifaceted. A more secure online environment directly translates to increased user confidence in Google services.
If users feel safer using Google products, they are more likely to rely on them for browsing, email, and other crucial online activities, bolstering Google’s market share and potentially attracting new users who prioritize security. Furthermore, a robust cross-platform phishing defense could enhance Google’s image as a responsible technology leader, improving its public relations and brand perception.
Potential Benefits for Google
A successful cross-platform phishing block would solidify Google’s position as a leader in online security. Increased user trust would lead to greater engagement with Google services, resulting in increased advertising revenue and potentially higher subscription rates for premium services. This would also improve Google’s reputation and attract more users seeking a secure online experience. By effectively combating phishing across platforms, Google could also gain a competitive advantage over other tech companies.
Technical Challenges in Cross-Platform Anti-Phishing
Creating a cross-platform solution presents considerable technical challenges. iOS and Android utilize different operating systems, programming languages, and security architectures. Google would need to develop compatible mechanisms to integrate its anti-phishing technology seamlessly with both platforms without compromising the user experience or device performance. This involves navigating Apple’s strict App Store policies and ensuring compatibility with a wide range of Android devices and versions.
Data synchronization and real-time threat updates across different operating systems also pose significant logistical hurdles. Consider the difficulty in developing a system that can consistently and accurately identify phishing attempts across diverse browser types and applications on both platforms.
Security Implications: Google-Led Initiative vs. OS-Level Solutions
A Google-led initiative offers the potential for a unified and comprehensive approach to phishing prevention, but it also raises concerns about centralized control and potential vulnerabilities. While OS-level solutions offer strong security at the device level, they might lack the broad reach and data-sharing capabilities of a cross-platform solution. A Google-led initiative could leverage its vast data resources to identify and neutralize phishing threats more effectively, but it could also lead to a single point of failure.
If Google’s system is compromised, the impact could be widespread and severe. In contrast, OS-level solutions distribute the security responsibility, making the system more resilient to large-scale attacks, although coordination between different OS developers is less efficient.
Potential Impact on User Privacy
The potential for increased user privacy concerns is a critical aspect to consider. A cross-platform solution necessitates access to user data across different platforms. Google would need to carefully balance the need for data collection to effectively identify phishing attacks with the protection of user privacy. Transparent data handling practices, strong encryption protocols, and robust privacy policies are crucial to mitigate potential risks.
For example, Google could anonymize user data as much as possible while retaining the information needed to detect malicious patterns, thus ensuring privacy while maintaining the efficacy of the anti-phishing system. Failure to address these privacy concerns could lead to user distrust and regulatory scrutiny.
Technical Approaches to Cross-Platform Phishing Detection: Google To Use Apple Iphones And Android Devices To Block Phishing Attacks
Building a robust, cross-platform phishing detection system requires a multi-faceted approach combining cloud-based intelligence with on-device processing. This ensures both speed of response for immediate user protection and the ability to leverage vast datasets for improved accuracy over time. The system needs to be lightweight enough to not significantly impact device performance, while remaining effective in identifying a wide range of sophisticated phishing techniques.
System Architecture for Cross-Platform Phishing Detection
The proposed system architecture utilizes a client-server model. On-device components, tailored for both iOS and Android, perform initial checks for suspicious indicators. These components then forward potentially malicious URLs or emails to a cloud-based analysis engine for more in-depth processing. The cloud engine uses machine learning models trained on extensive datasets to classify the threat level. Results are then sent back to the device, prompting appropriate user alerts or actions like blocking access.
This distributed approach balances real-time responsiveness with the power of centralized analysis. The system also incorporates feedback loops, allowing the cloud engine to learn from user interactions and improve its accuracy over time. For example, if a user frequently dismisses alerts for a particular website that is later confirmed as benign, the system can adjust its sensitivity accordingly.
Data Points for Cross-Platform Phishing Detection
The effectiveness of phishing detection hinges on analyzing a diverse range of data points. The following table summarizes key data points, their sources, and their relevance to identifying phishing attempts.
| Data Point | Source | Relevance to Phishing Detection | Example |
|---|---|---|---|
| URL Pattern | URL of website or link in email | Suspicious characters, unusual length, typosquatting, use of IP addresses instead of domain names | http://googIe.com (typo in Google) |
| Email Headers | Email message headers | Sender information discrepancies, forged headers, unexpected routing information | Sender address not matching the displayed name |
| Certificate Information | Website SSL certificate | Invalid or self-signed certificates, mismatched domain names, certificate expiration dates | Certificate issued to a different domain than the visited website |
| Content Analysis | Website content, email body | Presence of suspicious s, grammar errors, unusual urgency, requests for personal information | Email demanding immediate action to avoid account suspension |
| Domain Reputation | Cloud-based reputation databases | Blacklisting of known malicious domains, historical phishing activity | Domain listed on multiple phishing threat intelligence feeds |
| Visual Similarity | Website visuals, email design | Comparison with legitimate websites to detect imitation attempts | Website closely mimicking a bank’s login page |
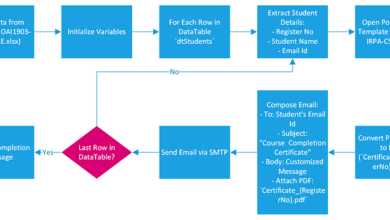
Procedure for Flagging and Reporting Phishing Attempts
1. On-device detection
The on-device component analyzes the URL or email using pre-defined rules and heuristics (e.g., checking for suspicious patterns in the URL or email headers).
2. Risk assessment
Based on the initial analysis, the device assigns a risk score to the suspected phishing attempt.
3. Threshold trigger
If the risk score exceeds a pre-defined threshold, the device flags the attempt as suspicious.
4. User notification
The user is presented with a warning indicating a potential phishing attempt.
Google’s plan to leverage iPhones and Androids against phishing is a huge step forward in online security. This collaborative approach highlights the importance of cross-platform solutions, reminding me of the flexibility offered in modern app development, like what’s discussed in this insightful article on domino app dev the low code and pro code future. Ultimately, this broader security initiative, mirrors the need for adaptable and robust solutions across all tech platforms.
5. Data transmission
The device securely transmits relevant data (URL, email headers, screenshots, etc.) to Google’s servers. This transmission is encrypted to protect user privacy.
6. Cloud analysis
Google’s cloud-based system performs more comprehensive analysis, leveraging machine learning models and threat intelligence databases.
7. Feedback loop
The results of the cloud analysis are sent back to the device to refine the risk assessment and improve future detection accuracy.
Machine Learning Algorithms for Phishing Detection
Several machine learning algorithms can enhance phishing detection accuracy. For example, Random Forest can effectively handle high-dimensional data and provide feature importance insights, helping to identify the most crucial indicators of phishing. Support Vector Machines (SVMs) are excellent for classification tasks and can efficiently distinguish between legitimate and phishing websites. Recurrent Neural Networks (RNNs), particularly Long Short-Term Memory (LSTM) networks, are suitable for analyzing sequential data like email content and URL sequences to detect patterns indicative of phishing attacks.
These algorithms are continuously trained and updated using a vast dataset of both legitimate and malicious samples to adapt to evolving phishing techniques.
User Experience and Adoption
Seamless integration of a cross-platform anti-phishing system is crucial for widespread adoption and a positive user experience. The goal is to make the protection invisible, working quietly in the background to keep users safe without disrupting their workflow. This requires careful consideration of user privacy concerns and a robust communication strategy to build trust and understanding.The success of any cross-platform anti-phishing system hinges on its transparency and ease of use.
Users should not feel burdened by complicated settings or intrusive notifications. Instead, the system should work silently, providing protection without demanding constant attention. The system should also be adaptable to various user tech literacy levels.
Seamless Integration and Enhanced User Experience
A truly seamless integration would mean that users experience no noticeable change in their browsing or app usage. The anti-phishing protection would operate in the background, silently analyzing URLs and identifying potentially malicious links. On both iOS and Android, this could involve a subtle visual cue, perhaps a small checkmark or shield icon next to a safe URL in the browser or app, providing reassurance without interrupting the user’s flow.
For identified phishing attempts, a clear and concise warning would be presented, offering the user the option to proceed with caution or abandon the link entirely. This would improve the user experience by reducing the risk of falling victim to phishing attacks without requiring extra steps or hindering usability. Consider the improved experience of a user who regularly uses banking apps; the added security layer would provide peace of mind without disrupting their routine.
User Concerns Regarding Data Privacy and Security, Google to use apple iphones and android devices to block phishing attacks
A key concern for users will be the sharing of data across platforms. The system will require some level of data sharing between Google’s servers, iOS devices, and Android devices to effectively identify and block phishing attempts. This data sharing must be transparent and clearly defined in a privacy policy that emphasizes the security measures in place to protect user data.
Users need assurance that only necessary data, such as URL patterns and potentially suspicious website elements (but not browsing history or personal information), is shared and that this data is encrypted during transmission and stored securely. The system should be designed to minimize data collection and only retain data for as long as necessary. Transparency regarding data usage and security measures will build user trust and encourage adoption.
Examples of similar systems with strong privacy policies, like those used by major antivirus software companies, could be used to reassure users.
Communication Strategies to Educate Users
Effective communication is key to addressing user concerns and promoting adoption. A multi-pronged approach is necessary:
- Clear and Concise Explainer Videos: Short, easily digestible videos explaining the system’s functionality and privacy protections.
- Interactive Tutorials: Step-by-step guides demonstrating how the system works and how to interpret warnings.
- FAQ Section on Google’s Support Website: A comprehensive FAQ addressing common user questions about data privacy, security, and system functionality.
- Social Media Campaign: Engaging social media posts highlighting the benefits of the system and addressing common concerns.
- In-App Notifications: Subtle, non-intrusive notifications introducing the system and linking to further information.
Mockup of a Phishing Attempt Warning
Imagine a user clicks a suspicious link. Instead of loading the website, a full-screen warning appears. The top half features a large, bold red exclamation mark within a yellow triangle, immediately grabbing attention. Below, a clear, concise message reads: “Warning: Potential Phishing Attempt Detected. This link may be trying to steal your information.” The text is easy to read, using a large, sans-serif font.
A smaller text section below provides further details, such as “The URL contains suspicious patterns often associated with phishing attacks.” Two buttons are prominently displayed at the bottom: “Go Back” (in green) and “Proceed with Caution” (in a muted grey). The overall design is clean and uncluttered, focusing on conveying the urgency and seriousness of the situation while providing clear options to the user.
The color scheme uses universally understood warning colors, creating an immediate visual impact.
Collaboration and Partnerships
Pulling off a cross-platform phishing block requires a monumental effort, and Google can’t do it alone. Success hinges on strategic partnerships with key players across the tech ecosystem. Building trust and forging agreements with competitors will be crucial to achieving a truly effective system.This ambitious project necessitates a multi-faceted approach to collaboration, encompassing various stakeholders and careful consideration of potential hurdles.
The benefits of a collaborative approach far outweigh the challenges, particularly when dealing with a threat as pervasive as phishing.
Key Stakeholders and Their Roles
Effective implementation demands collaboration with several key stakeholders. Apple, as a major mobile operating system provider, is paramount. Their participation would allow Google’s system to protect a significant portion of the mobile user base. Android device manufacturers also play a vital role, ensuring consistent implementation across diverse hardware and software versions. Security researchers, with their expertise in identifying and analyzing phishing techniques, are essential for ongoing system improvement and adaptation to evolving threats.
Finally, regulatory bodies and standards organizations will be important in navigating the legal and compliance landscape. Their input will be crucial in ensuring the system respects user privacy and complies with relevant laws.
Benefits and Challenges of Collaborating with Competitors
Collaborating with a direct competitor like Apple presents both significant benefits and substantial challenges. The primary benefit is the potential for a dramatically increased level of security across the mobile landscape, protecting a far greater number of users from phishing attacks. This collaborative effort would lead to a more secure internet for everyone. However, challenges include potential conflicts of interest, differing corporate cultures, and the difficulty of agreeing on technical specifications and data-sharing protocols.
Trust-building will be a continuous process, requiring open communication and a shared commitment to the overarching goal of user security. Successful examples of competitor collaboration in security initiatives, such as the joint efforts to combat malware, could serve as a guide.
Collaboration Models: Open Source vs. Proprietary Solutions
The choice between an open-source and a proprietary solution significantly impacts collaboration and long-term sustainability. An open-source approach promotes transparency, allows for community contributions, and fosters rapid innovation. However, it might require more effort in coordinating updates and ensuring consistent implementation across different platforms. A proprietary solution, while potentially offering more control and faster initial deployment, could limit participation and hinder innovation.
The optimal model might involve a hybrid approach, leveraging open-source components for certain parts of the system while maintaining proprietary aspects for sensitive functionalities like data processing and threat intelligence sharing. This would balance the benefits of community involvement with the need for robust security and data protection.
Legal and Regulatory Considerations
Sharing user data across platforms and jurisdictions necessitates careful consideration of legal and regulatory frameworks. Compliance with data privacy regulations like GDPR and CCPA is crucial. Transparency about data collection, usage, and sharing practices is essential to maintain user trust. International data transfer agreements must adhere to relevant laws and regulations in each jurisdiction involved. Establishing clear legal agreements between Google, Apple, and other stakeholders regarding data ownership, access, and liability is vital to mitigate potential legal risks.
Seeking guidance from legal experts specializing in data privacy and cross-border data transfers is essential to ensure compliance and avoid potential legal disputes.
Epilogue
The potential for a Google-Apple anti-phishing alliance is truly game-changing. While challenges remain – particularly around data privacy and the complexities of cross-platform integration – the benefits of a more secure online experience are undeniable. The success of this initiative will depend on transparency, robust security measures, and a commitment to user privacy. If done right, it could mark a new era of collaborative security, where competitors put aside differences for the greater good of internet safety.
It’s a bold move, and one I’ll be watching very closely.
Question Bank
How will this affect my battery life?
The impact on battery life is expected to be minimal, as the system will likely utilize efficient background processes.
Will this system slow down my phone?
Google aims to minimize performance impact through optimized algorithms and efficient data handling.
What if I don’t want Google to have access to my data?
Transparency regarding data collection and usage will be crucial. Users should have the option to opt out or control the level of data sharing.
Will this work with all apps?
The effectiveness will depend on the level of integration with different apps. It’s likely to be most effective with web browsers and email clients initially.