Global Cyber Threats Government Action Plan
Government cybersecurity is a global problem heres how agencies can address it. The digital age has brought unprecedented opportunities, but also a new wave of threats. Governments worldwide face a complex web of cyberattacks, from sophisticated espionage campaigns to disruptive sabotage attempts. This isn’t just a matter of national security; it impacts economies, critical infrastructure, and public trust.
Understanding the scope of these threats and the collaborative solutions needed is crucial for protecting our digital future.
This article explores the multifaceted nature of government cybersecurity threats, from the interconnectedness of global vulnerabilities to the specific tools used by cybercriminals. It also delves into crucial strategies for international cooperation, strengthening infrastructure, employee training, and developing comprehensive strategies to address emerging threats. Ultimately, a robust cybersecurity posture requires a multifaceted approach involving governments, international organizations, and the private sector.
Introduction to Global Cybersecurity Challenges: Government Cybersecurity Is A Global Problem Heres How Agencies Can Address It

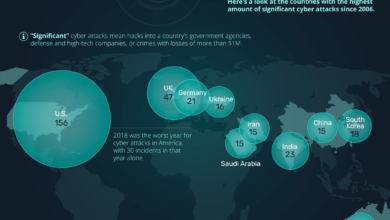
The digital age has intertwined national security with global interconnectedness, creating a complex web of vulnerabilities. Government entities worldwide face a constantly evolving threat landscape, encompassing a multitude of sophisticated cyberattacks. These attacks are no longer isolated incidents but rather a pervasive and multifaceted challenge that demands proactive and collaborative responses.Global cyber vulnerabilities are interconnected, enabling cybercriminals to exploit weaknesses in one country to target others.
A breach in one nation’s infrastructure can have cascading effects, impacting critical services and potentially destabilizing international relations. The interconnected nature of global systems makes it crucial for nations to work together to enhance cybersecurity defenses and mitigate risks.
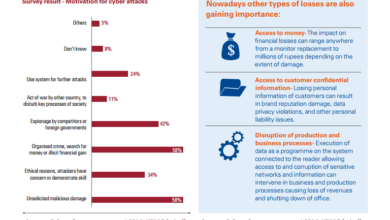
Types of Cyberattacks Targeting Governments
Governments are targeted by a wide range of cyberattacks, each with unique objectives and methods. These attacks often aim to steal sensitive information, disrupt critical services, or cause damage to national infrastructure. The spectrum of attacks ranges from subtle espionage operations to destructive cyber warfare tactics.
Common Tools and Techniques Employed by Cybercriminals
Cybercriminals employ a variety of tools and techniques to infiltrate government systems. These include malware, phishing campaigns, denial-of-service attacks, and social engineering tactics. The sophistication of these methods is constantly increasing, making it essential for governments to stay ahead of the curve in terms of cybersecurity defenses.
Government Cyber Threats Categorization
The diverse nature of cyber threats against governments necessitates a structured approach to understanding and addressing them. Categorizing these threats helps in developing targeted defense strategies.
| Threat Category | Description | Examples |
|---|---|---|
| Espionage | Acquisition of sensitive information, such as classified documents, intellectual property, or personal data. | Data breaches targeting government databases, unauthorized access to diplomatic communications, industrial espionage targeting defense contractors. |
| Sabotage | Disruption or destruction of critical infrastructure or services. | Disrupting power grids, water supplies, or communication networks; compromising financial systems; damaging critical government websites. |
| Extortion | Threatening to release sensitive information or disrupt services unless a ransom is paid. | Encrypting government data and demanding payment for decryption; disrupting government operations until demands are met; threatening to expose embarrassing information. |
| Cyber Warfare | State-sponsored attacks that aim to damage or disrupt another nation’s critical infrastructure or capabilities. | Large-scale denial-of-service attacks targeting government websites or critical services; compromising national defense systems; disseminating disinformation campaigns to undermine public trust. |
International Collaboration and Information Sharing
Global cybersecurity threats transcend national borders, demanding a collaborative response. Isolated efforts by individual nations are insufficient to combat sophisticated cyberattacks, and the sharing of intelligence and best practices across borders is crucial for effective defense. This collaborative approach allows for a more comprehensive understanding of threats and the development of coordinated responses.International cooperation isn’t just a desirable outcome; it’s a necessity.
The interconnected nature of the digital world means that a cyberattack in one country can quickly ripple across the globe, affecting critical infrastructure and economies. Sharing information, developing joint strategies, and harmonizing security standards are essential steps toward building a more secure global digital ecosystem.
Importance of International Cooperation
Effective international cooperation in cybersecurity is vital for mitigating the impact of cyberattacks. Shared intelligence enables early detection and response, reducing the potential for widespread damage. Furthermore, coordinated efforts can help identify and disrupt malicious actors operating across borders. This cooperation can also facilitate the development and implementation of common cybersecurity standards, fostering a more secure digital environment for all.
Mechanisms for Fostering Collaboration
Various mechanisms facilitate international collaboration in cybersecurity. Bilateral agreements between nations are one key approach. These agreements allow for direct information exchange and joint operations. Multilateral forums, such as the UN Group of Governmental Experts (GGE) on Cybersecurity, offer a platform for broader discussion and consensus-building among numerous countries. International organizations like the Organization for Economic Co-operation and Development (OECD) also play a crucial role by providing guidelines and best practices.
Examples of Successful International Cybersecurity Partnerships
Several successful international cybersecurity partnerships have demonstrated the efficacy of collaboration. For instance, collaborations between intelligence agencies in different countries have been crucial in disrupting major cybercrime operations and exposing sophisticated hacking groups. Joint exercises and training programs have also helped enhance the preparedness and response capabilities of various nations. Moreover, the sharing of threat intelligence between countries has significantly improved the ability to detect and mitigate emerging cyber threats.
Challenges and Obstacles to Effective Information Sharing
Despite the benefits, significant challenges impede effective international information sharing. Trust and confidence between nations are crucial; concerns about the potential misuse of shared information, or the perception of espionage, can be significant barriers. Different legal frameworks, varying levels of technical expertise, and differing priorities can further complicate efforts to share information effectively. Confidentiality and data protection concerns, along with concerns about potential political sensitivities, are also critical factors.
Government cybersecurity is a serious global issue, requiring coordinated international efforts. A great example of a local solution that can be scaled up is the Department of Justice’s new Safe Harbor policy for Massachusetts transactions, Department of Justice Offers Safe Harbor for MA Transactions. This approach could be adapted to other states and countries, potentially leading to a more unified and effective approach to cybersecurity globally.
Ultimately, tackling this global problem requires a multifaceted strategy encompassing international cooperation and local initiatives.
Different Approaches to Information Sharing
| Approach | Strengths | Weaknesses |
|---|---|---|
| Bilateral Agreements | Direct, tailored information exchange; focused cooperation; faster response to specific threats. | Limited scope; can exclude crucial perspectives from other nations; potentially biased towards the involved parties. |
| Multilateral Forums | Broader scope, encompassing a wide range of perspectives; increased consensus and standardization. | Slower response times due to extensive negotiation processes; potential for conflicting priorities among diverse members. |
| International Organizations | Establishment of common standards and guidelines; promotion of best practices; facilitation of information exchange. | Limited enforcement mechanisms; potential for differing interpretations of guidelines. |
Strengthening Cybersecurity Infrastructure
Government agencies face a constant barrage of cyber threats, demanding robust and adaptable cybersecurity infrastructure. This necessitates a multi-faceted approach that goes beyond simply installing security software; it requires a fundamental shift in how agencies approach security, prioritizing prevention and resilience. A strong infrastructure is not just a technical solution, but a cultural imperative.Robust security protocols and procedures are essential to mitigating vulnerabilities.
These protocols should be comprehensive, encompassing everything from access controls and authentication methods to data encryption and incident response plans. Regular security assessments and penetration testing are crucial to identify and address potential weaknesses before they can be exploited.
Improving Cybersecurity Infrastructure of Government Agencies
Government agencies need to prioritize regular security audits and penetration testing. These assessments identify weaknesses in existing systems, helping agencies patch vulnerabilities before they become exploitable. Implementing a security information and event management (SIEM) system can provide centralized monitoring and analysis of security events, enabling faster incident response and threat detection.
Importance of Robust Security Protocols and Procedures
Strong security protocols and procedures are the bedrock of a resilient cybersecurity infrastructure. Clear guidelines for password management, access controls, and data handling are essential. Regular security awareness training for employees is vital, empowering them to recognize and report suspicious activities. The implementation of a formal incident response plan is critical, outlining the steps to be taken in case of a cyberattack.
Such plans need to be regularly tested and updated to ensure their effectiveness.
Role of Advanced Technologies in Bolstering Defenses
Advanced technologies play a critical role in bolstering defenses against evolving cyber threats. Employing next-generation firewalls with advanced threat intelligence can significantly improve protection against sophisticated attacks. Intrusion detection and prevention systems (IDS/IPS) can identify and block malicious traffic in real-time, offering an additional layer of protection. Cloud security solutions can enhance data protection and accessibility while providing scalability.
Using artificial intelligence (AI) and machine learning (ML) to detect anomalies and predict potential threats can further improve proactive defense capabilities.
Potential Vulnerabilities Within Existing Government Systems
Outdated software and hardware can create significant vulnerabilities. A lack of consistent patching and updates leaves systems susceptible to known exploits. Poorly configured systems, lacking adequate security measures, represent another key vulnerability. Insufficient employee training and awareness contribute significantly to the risk profile. Inadequate access controls can allow unauthorized individuals to gain access to sensitive data.
Mitigation strategies must address these vulnerabilities. These strategies should include regular software updates, implementing strong access control policies, comprehensive employee training, and the implementation of robust incident response protocols.
Comparing Cybersecurity Technologies
| Technology | Description | Effectiveness Against Various Threats |
|---|---|---|
| Firewalls | Control network traffic based on predefined rules. | Effective against basic network attacks, but less effective against sophisticated attacks. |
| Intrusion Detection Systems (IDS) | Monitor network traffic for malicious activity. | Can detect and alert on suspicious activity, but may not always prevent attacks. |
| Intrusion Prevention Systems (IPS) | Actively block malicious traffic detected by IDS. | More effective than IDS in preventing attacks, but can sometimes block legitimate traffic. |
| Endpoint Detection and Response (EDR) | Monitor and respond to threats on individual devices. | Effective in detecting and responding to threats at the endpoint level, particularly malware and ransomware. |
Implementing a layered security approach, combining multiple technologies, provides a more comprehensive defense against various threats.
Training and Education Initiatives

Government cybersecurity is not just about sophisticated technology; it’s fundamentally about people. Effective training and education are crucial for building a resilient cybersecurity posture, empowering both government employees and citizens. Without well-trained personnel and informed citizens, even the most advanced systems are vulnerable. This section will delve into the importance of ongoing training, effective programs, and public awareness initiatives.
Significance of Cybersecurity Training for Government Employees
Government employees handle sensitive data, often dealing with national secrets and critical infrastructure information. Thorough cybersecurity training equips them with the knowledge and skills to identify and mitigate threats. This includes understanding various attack vectors, recognizing phishing attempts, and adhering to secure data handling procedures. Well-trained employees act as a critical first line of defense against cyberattacks, reducing the risk of data breaches and operational disruptions.
Need for Ongoing Professional Development
The cybersecurity landscape is constantly evolving. New threats and attack techniques emerge regularly, necessitating ongoing professional development for government employees. Training programs should be dynamic, adapting to emerging threats and incorporating new technologies. This ensures that employees maintain a strong skillset and can effectively address evolving cyber challenges. Regular updates and refreshers keep their knowledge current, mirroring the ever-changing nature of cyber threats.
Government cybersecurity is a serious global challenge, and agencies need robust strategies to protect sensitive data. A recent vulnerability in Azure Cosmos DB, detailed in Azure Cosmos DB Vulnerability Details , highlights the need for constant vigilance and proactive patching. This underscores the importance of international cooperation and shared best practices in addressing these growing threats to ensure national and global security.
Examples of Effective Cybersecurity Training Programs for Government Agencies
Numerous government agencies worldwide have implemented successful cybersecurity training programs. These programs often incorporate interactive simulations, real-world case studies, and hands-on exercises to reinforce learning. For example, some programs use simulated phishing attacks to test employee responses and identify vulnerabilities. Other programs focus on specific technologies or regulations, like the handling of Personally Identifiable Information (PII). Effective programs incorporate a variety of methods to ensure retention and practical application.
Importance of Raising Awareness Among Citizens About Cybersecurity Best Practices
A robust cybersecurity posture requires a multi-faceted approach, encompassing not just government employees but also the general public. Educating citizens about cybersecurity best practices is crucial for reducing the overall attack surface. This includes educating citizens on password management, safe browsing habits, and recognizing social engineering tactics. Cybersecurity awareness campaigns can significantly decrease the number of successful attacks that exploit public vulnerabilities.
Training Modules and Target Audiences
| Training Module | Target Audience | Description |
|---|---|---|
| Phishing Awareness | All government employees | Recognizing phishing emails, suspicious links, and phone calls. Focuses on identifying red flags and reporting suspicious activity. |
| Password Management | All government employees | Creating strong, unique passwords, utilizing password managers, and avoiding common password pitfalls. Covers the importance of password complexity and multi-factor authentication. |
| Social Engineering Awareness | All government employees, and citizens | Understanding social engineering tactics, such as pretexting and baiting. Focuses on recognizing manipulation techniques and resisting pressure. |
| Data Security Best Practices | Government employees handling sensitive data | Implementing secure data handling procedures, protecting sensitive information, and complying with data protection regulations (e.g., GDPR). |
| Secure Device Usage | All government employees | Properly configuring devices, recognizing and mitigating risks associated with using personal devices for work, and maintaining secure network connections. |
Developing a Comprehensive Strategy

Building a robust government cybersecurity strategy requires a meticulous and multi-faceted approach. It’s not just about acquiring the latest technology; it’s about establishing a culture of security that permeates every level of the organization. This involves understanding and mitigating risks, allocating resources effectively, and fostering continuous improvement through regular assessments and incident response plans. A comprehensive strategy is essential for safeguarding sensitive information and maintaining public trust.
Framework for a Comprehensive Strategy
A successful cybersecurity strategy needs a well-defined framework. This framework should be adaptable and scalable, able to adjust to evolving threats and emerging technologies. It should encompass all aspects of the organization, from the smallest departmental unit to the highest leadership. The strategy must be clearly documented and readily accessible to all stakeholders. A solid framework lays the groundwork for effective implementation and long-term sustainability.
Risk Assessment and Threat Modeling, Government cybersecurity is a global problem heres how agencies can address it
Thorough risk assessment and threat modeling are critical components of any effective cybersecurity strategy. Understanding potential vulnerabilities and the likelihood of attacks is essential for prioritizing mitigation efforts. This involves identifying assets, analyzing potential threats, and evaluating the impact of successful attacks. A clear understanding of the organization’s risk profile enables informed decision-making and targeted resource allocation.
Realistic threat modeling helps predict potential attacks and prepare appropriate defenses.
Prioritizing Resources and Allocating Budgets
Efficient resource allocation is vital for a successful cybersecurity strategy. This involves understanding the relative value of different assets and the potential cost of breaches. A strategic approach prioritizes critical systems and data, allocating budgets accordingly. For example, systems handling sensitive personal information or national security data should receive higher budgetary allocations compared to less sensitive systems.
Effective prioritization ensures that resources are deployed where they have the greatest impact.
Regular Audits and Security Assessments
Regular audits and security assessments are crucial for maintaining a strong cybersecurity posture. These assessments identify vulnerabilities and help organizations stay ahead of emerging threats. Examples include penetration testing, vulnerability scanning, and security audits. These activities provide a baseline understanding of current security controls and allow for the implementation of corrective actions to improve the overall security posture.
Government cybersecurity is a serious global issue, and agencies need innovative solutions. One crucial step is recognizing the need for better code security. This means proactively deploying AI tools like those discussed in “Deploying AI Code Safety Goggles Needed” Deploying AI Code Safety Goggles Needed to identify and fix vulnerabilities in software before they can be exploited.
Ultimately, a multi-faceted approach to cybersecurity is key for protecting sensitive data and systems globally.
Regular assessments and audits help organizations stay compliant with relevant regulations and industry best practices.
Incident Response Planning and Management
A comprehensive cybersecurity strategy must include a well-defined incident response plan. This plan should Artikel procedures for identifying, containing, and recovering from security incidents. The plan should detail roles and responsibilities, communication protocols, and escalation procedures. A strong incident response plan ensures that organizations are prepared to handle security incidents effectively and minimize their impact. This includes clear communication channels and well-defined protocols for responding to breaches, data leaks, or other security incidents.
Key Components of a Comprehensive Cybersecurity Strategy
| Component | Description |
|---|---|
| Policy | Clear guidelines, procedures, and standards for cybersecurity practices across the organization. |
| Technology | Implementation of security tools and infrastructure (firewalls, intrusion detection systems, etc.) to protect critical systems and data. |
| Training | Providing employees with the necessary knowledge and skills to identify and mitigate security threats. |
| Incident Response | Developing and implementing a plan to effectively manage and respond to security incidents. |
Addressing Emerging Threats
The digital landscape is constantly evolving, and with it, so are the methods and motivations behind cyberattacks. Government agencies must be proactive in understanding and adapting to these evolving threats to maintain the integrity and security of critical infrastructure and sensitive data. The sophistication of attacks is increasing, requiring a shift from reactive measures to proactive strategies.Cyber threats are no longer confined to simple phishing scams or malware infections.
Modern threats exploit vulnerabilities in complex systems, often targeting specific individuals or organizations with tailored attacks. The speed at which new attack vectors emerge demands a constant vigilance and a commitment to continuous learning and adaptation.
Evolution of Cyberattack Tactics, Techniques, and Procedures (TTPs)
The sophistication of cyberattacks has evolved dramatically over the years. Early attacks often relied on simple malware and brute-force techniques. However, modern attackers leverage advanced tools and techniques to gain access to sensitive systems. Understanding this evolution is critical for developing effective defenses.
| Era | Tactics, Techniques, and Procedures (TTPs) | Examples |
|---|---|---|
| Early 2000s | Simple malware, phishing, denial-of-service (DoS) attacks | Email spam campaigns, basic password cracking |
| Mid-2000s – 2010s | Advanced persistent threats (APTs), spear phishing, exploit kits | Targeted attacks against specific organizations, sophisticated phishing campaigns, automated exploitation of software vulnerabilities |
| 2010s – Present | Ransomware, supply chain attacks, nation-state sponsored attacks, advanced malware with evasion techniques, AI-powered attacks | Widespread ransomware outbreaks, attacks targeting critical infrastructure, attacks leveraging vulnerabilities in software and hardware supply chains, attacks employing artificial intelligence for sophisticated evasion techniques |
Emerging Threats Targeting Government Agencies
Government agencies are increasingly becoming targets for a variety of sophisticated cyberattacks. These attacks often leverage vulnerabilities in software, exploit human error, and utilize complex techniques to bypass traditional security measures. A few examples include:
- Ransomware-as-a-Service (RaaS): This model allows even less-skilled actors to launch sophisticated ransomware attacks, targeting government systems and demanding substantial sums for data recovery. Agencies must ensure robust backup and recovery procedures, as well as rigorous security protocols for software and hardware.
- Supply Chain Attacks: Targeting vulnerabilities in third-party vendors or software components used by government agencies allows attackers to gain access to sensitive data and systems. Stricter vetting procedures for vendors and increased scrutiny of software updates are critical in countering this threat.
- Nation-State Sponsored Attacks: These attacks often target specific government agencies with the intent of espionage or disruption. Agencies must enhance their intelligence gathering capabilities to detect and counter these advanced attacks.
Continuous Adaptation to Evolving Cyberattacks
Cybersecurity is not a one-time fix; it’s an ongoing process of adaptation. The constant evolution of cyberattacks demands a continuous effort to stay informed about new threats and develop strategies to mitigate risks. Regular security assessments, vulnerability scanning, and penetration testing are critical for identifying and addressing weaknesses.
Staying Informed About Cybersecurity Trends
Staying abreast of the latest cybersecurity trends and developments is paramount for effective defense. Government agencies must leverage various resources to keep their personnel informed about new threats and vulnerabilities. This includes industry publications, security advisories, and participation in professional development opportunities.
Building Public-Private Partnerships
Cybersecurity threats are no longer confined to the digital realm; they impact critical infrastructure and the economy as a whole. Effective defense requires a collaborative approach that transcends traditional boundaries between government and industry. A strong public-private partnership is vital to bolstering cybersecurity defenses, leveraging the specialized expertise and resources of both sectors.Public-private partnerships (PPPs) are strategic alliances between government agencies and private sector organizations to address shared challenges.
This collaboration leverages the government’s regulatory power and the private sector’s technological innovation and operational knowledge. These partnerships are crucial for achieving a comprehensive and robust cybersecurity posture.
The Value of Public-Private Partnerships
Public-private partnerships offer a multitude of benefits, significantly enhancing cybersecurity capabilities. These partnerships allow for the sharing of sensitive information and threat intelligence in a secure and controlled environment. This collaboration fosters innovation by encouraging the development of advanced security technologies and solutions. Critically, it also provides a platform for the rapid implementation of new security measures, preventing potential breaches and maintaining a proactive stance against evolving threats.
Enhancing Cybersecurity Capabilities Through Partnerships
These partnerships facilitate the rapid dissemination of cybersecurity best practices across different sectors. Government agencies can leverage the expertise of private sector companies, while private companies gain insights into government security standards and procedures. By combining resources and knowledge, these partnerships enhance the overall resilience of the nation’s cybersecurity posture. This synergistic approach creates a more robust and adaptive system to counter sophisticated and evolving threats.
Industry Best Practices in Improving Government Defenses
Private sector organizations frequently develop and implement innovative cybersecurity practices. Sharing these best practices with government agencies is invaluable. This transfer of knowledge can significantly improve the government’s defenses, allowing them to adopt cutting-edge security measures and stay ahead of emerging threats. Examples of best practices include advanced threat detection systems, robust incident response plans, and stringent data security protocols.
Examples of Successful Public-Private Partnerships
Numerous successful public-private partnerships have demonstrated the effectiveness of this collaborative approach. One example involves government agencies partnering with technology companies to develop and deploy advanced cybersecurity tools to protect critical infrastructure. Another model showcases partnerships between government agencies and financial institutions to bolster financial sector defenses against cyberattacks. These partnerships have shown positive results in reducing vulnerabilities and enhancing the overall cybersecurity posture.
A Table Illustrating Sector Contributions
| Sector | Potential Contribution to National Cybersecurity Strategy |
|---|---|
| Finance | Developing robust security protocols for online transactions, implementing advanced fraud detection systems, and sharing threat intelligence among financial institutions. |
| Healthcare | Protecting patient data and medical records, implementing encryption protocols, and training healthcare professionals on cybersecurity best practices. |
| Technology | Developing advanced security tools and technologies, conducting penetration testing and vulnerability assessments, and providing cybersecurity training and awareness programs. |
Final Summary
In conclusion, government cybersecurity is a global challenge requiring a collaborative and proactive approach. International partnerships, robust infrastructure, ongoing training, and a comprehensive strategy are essential to combat the evolving threats. By working together, governments can mitigate risks, protect critical systems, and foster a more secure digital environment for all.
Popular Questions
What are some common types of cyberattacks targeting governments?
Common cyberattacks include espionage (stealing sensitive information), sabotage (disrupting services), and extortion (demanding payment to prevent attacks or release of data).
How can governments improve their cybersecurity infrastructure?
Improving cybersecurity infrastructure involves implementing robust security protocols, using advanced technologies like firewalls and intrusion detection systems, and identifying and mitigating potential vulnerabilities within existing systems.
Why is international cooperation important in cybersecurity?
International cooperation is vital because cyber threats often transcend national borders. Sharing information and coordinating efforts are crucial for effectively combating these threats.
What role do public-private partnerships play in government cybersecurity?
Public-private partnerships can leverage the expertise and resources of the private sector to enhance government cybersecurity capabilities. This collaboration can lead to better defenses and faster incident response.