
Hackers Are Turning Webcam Users Into Slaves A Deep Dive
Hackers are turning webcam users into slaves, leveraging various methods to gain control and exploit vulnerable individuals. This insidious practice ranges from simple surveillance to malicious actions, driven by motives like extortion, harassment, and espionage. Understanding the methods, impact, and potential consequences is crucial to protecting yourself and others from this disturbing trend.
This article delves into the complex issue of webcam hacking, exploring the motivations behind these attacks, the vulnerabilities targeted, and practical steps individuals can take to safeguard themselves. We’ll also examine the psychological, financial, and social repercussions of falling victim to such attacks, highlighting real-world examples and the importance of recognizing vulnerable populations.
Defining the Threat
The phrase “turning webcam users into slaves” in the context of hacking describes a scenario where malicious actors gain unauthorized control over a victim’s webcam, using it for various nefarious purposes. This goes beyond simple surveillance, often involving manipulation and exploitation of the victim. It encompasses a spectrum of intrusive actions, from subtle harassment to more severe forms of coercion.Hackers achieve this through a combination of sophisticated techniques.
Vulnerabilities in software, including webcam drivers and operating systems, can be exploited to install malware that grants remote access. Social engineering tactics, like phishing emails or deceptive websites, trick users into providing access or installing malicious software. These tactics exploit human psychology to bypass security measures.
It’s scary how hackers are turning webcam users into digital slaves, essentially controlling their devices remotely. Thankfully, the Department of Justice Offers Safe Harbor for MA Transactions ( Department of Justice Offers Safe Harbor for MA Transactions ) might offer some peace of mind to those in the area, but the underlying vulnerability to webcam hacking remains a serious issue.
We need better protection for all webcam users from these malicious actors.
Methods of Exploitation
Hackers utilize a range of methods to gain control over webcams. Malware, disguised as legitimate software, is a primary method. It can be downloaded unknowingly from infected websites or through malicious links. Once installed, this malware provides hackers with remote access to the victim’s system, allowing them to control the webcam. Social engineering, another crucial tactic, exploits human psychology.
Phishing attempts, for instance, might trick users into revealing their login credentials or downloading malware. Furthermore, vulnerabilities in webcam software or operating systems, left unpatched, can be exploited by hackers to gain access and control.
Types of Control
The control hackers exert over webcam users varies significantly. Some hackers might simply use the webcam for surveillance, recording and monitoring the victim’s activities. This could include observing their surroundings, recording conversations, or tracking their movements. More malicious actions could include blackmail, harassment, or even attempts to manipulate or coerce the victim. Extortion is another potential motive, where hackers demand money in exchange for not releasing compromising footage.
In more severe cases, hackers might attempt to manipulate or exploit the victim through psychological tactics.
Motivations Behind Attacks
The motivations behind these webcam attacks are diverse. Extortion, as previously mentioned, is a common driver. Hackers might record compromising material and threaten to release it unless the victim pays. Harassment is another significant motivation, where hackers use the webcam to cause distress or discomfort. Espionage is another potential driver, where hackers use the webcam to gather sensitive information or monitor individuals.
Finally, personal gain, such as financial or reputational damage, can be another significant factor.
Impact and Consequences

The chilling reality of webcam enslavement extends far beyond the initial act of intrusion. It leaves a trail of psychological trauma, financial devastation, and reputational damage that can profoundly impact victims’ lives. Understanding these consequences is crucial to appreciating the severity of this emerging threat.The psychological toll of being a target of a webcam attack is significant. Victims often experience profound anxiety, depression, and feelings of helplessness.
The constant fear of being observed, the knowledge that their private moments are being shared without consent, and the potential for public humiliation can lead to long-term psychological distress. This can manifest in insomnia, difficulty concentrating, and even post-traumatic stress disorder (PTSD). The breach of privacy and the violation of personal boundaries can leave lasting emotional scars.
Psychological Impact
The psychological impact of webcam attacks can be devastating. Victims may suffer from anxiety, depression, and PTSD due to the violation of their privacy, the exposure of personal moments, and the potential for public humiliation. The feeling of helplessness and powerlessness further exacerbates the psychological trauma. Constant monitoring and the knowledge that one’s private life is being shared without consent can severely impact mental well-being.
The fear of being observed can disrupt sleep patterns, daily routines, and overall quality of life.
Financial Losses
Webcam attacks can lead to substantial financial losses. Lost productivity is a significant factor, as victims may struggle to concentrate on work or other responsibilities due to the stress and anxiety caused by the attack. Reputational damage can also have substantial financial consequences, especially for individuals or businesses operating in a highly competitive environment. If the attack involves extortion, the victim may be forced to pay a ransom to prevent further exposure or dissemination of compromising material.
Comparison to Other Forms of Digital Harassment
While other forms of digital harassment, such as cyberbullying or online stalking, can cause significant distress, webcam attacks often carry a unique dimension of invasion and humiliation. The intimate nature of webcam interactions, the potential for the recording and distribution of private moments, and the possibility of being used for blackmail or extortion can amplify the impact.
Real-World Examples
Numerous real-world examples illustrate the severity of webcam attacks. For instance, cases have emerged where individuals were targeted for their political views, their religious beliefs, or their personal relationships. These attacks, often combined with blackmail or extortion, can have a profound impact on the victims’ lives, causing significant financial and psychological distress. In some instances, victims have faced severe repercussions, including job loss, social isolation, and a damaged reputation.
Such cases highlight the need for robust legal frameworks and preventative measures to combat this evolving threat.
Vulnerable Populations
The digital landscape presents unique challenges for various demographic groups, making them more susceptible to webcam exploitation. Understanding these vulnerabilities is crucial for developing effective preventative measures and support systems. Targeting specific groups can be a calculated strategy for cybercriminals, leveraging existing social structures and societal norms to increase their success rate.
Specific Demographic Groups
Certain demographic groups are disproportionately affected by webcam exploitation due to a combination of factors. These factors include varying levels of digital literacy, access to resources, and susceptibility to social engineering tactics.
- Elderly Individuals: Often less familiar with technology and online safety protocols, elderly individuals may be more vulnerable to scams and phishing attempts. Their reliance on online communication and support systems can make them easy targets. The fear of missing out (FOMO) on social interactions, combined with a lack of familiarity with online security, can leave them exposed to potential exploitation.
For example, a convincing email claiming to be from a grandchild in distress could lead to a compromised webcam.
- Teenagers and Young Adults: This group often prioritizes online interactions and social media presence, potentially leading to a lower awareness of online safety risks. They might be more inclined to engage with strangers online, making them vulnerable to manipulation and exploitation. The allure of social media validation and the desire to fit in can be exploited by malicious actors seeking to compromise their webcams.
- Individuals with Disabilities: Those with disabilities, including visual or cognitive impairments, may face unique challenges in navigating online safety issues. Limited access to technology support and training can exacerbate their vulnerability. The lack of digital literacy can lead to a misunderstanding of how to recognize and avoid online scams.
Role of Social Media
Social media platforms play a significant role in exposing individuals to webcam exploitation threats. The ease of interaction and the often-anonymous nature of these platforms can create an environment where individuals are more likely to engage with strangers. This increased interaction can create opportunities for malicious actors to target unsuspecting users.
- Social Engineering Tactics: Social media platforms are frequently used to deploy social engineering tactics, such as creating fake profiles or sending deceptive messages to gain access to user information or control over their webcam. These tactics often exploit existing relationships or social pressures to manipulate individuals into revealing sensitive information or performing actions that compromise their security.
- Misinformation and Disinformation: The rapid spread of misinformation and disinformation on social media can contribute to the vulnerability of certain demographic groups. Malicious actors can use these platforms to spread false information about online safety or to manipulate individuals into engaging in risky behaviors.
- Online Interactions: The nature of online interactions, characterized by a lack of physical presence, can make it more difficult for individuals to recognize and respond to potential threats. The perceived anonymity of online interactions can embolden malicious actors, while the lack of face-to-face communication can mask their true intentions.
Importance of Awareness and Prevention
Recognizing and addressing these vulnerabilities is critical for protecting individuals from webcam exploitation. Educating vulnerable populations about online safety best practices, including identifying suspicious activity and reporting incidents, is crucial for reducing their risk. This includes educating them on how to recognize phishing attempts, the importance of strong passwords, and the potential dangers of engaging with strangers online.
Prevention and Mitigation Strategies
Protecting webcam users from malicious actors requires a multifaceted approach encompassing robust technical safeguards and responsible online behavior. A proactive strategy is crucial to minimize vulnerability and ensure a safer online experience. Ignoring these threats can lead to significant personal and financial consequences.Implementing strong security measures is not just a technical exercise; it’s a commitment to safeguarding personal information and maintaining digital well-being.
Understanding the potential threats and taking proactive steps to mitigate them is paramount.
Strong Passwords
Creating strong passwords is a fundamental step in protecting accounts and devices. Weak passwords are easily cracked, leaving users vulnerable to unauthorized access. A robust password strategy should incorporate complexity, length, and memorability.
- Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Employ a password manager to generate and store complex passwords securely.
- Avoid using easily guessable information, like birthdays, names, or pet names.
- Change passwords regularly, ideally every 3 months.
Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring a second verification method beyond a password. This significantly reduces the risk of unauthorized access even if a password is compromised.
- Enable 2FA for all online accounts, especially those associated with webcams and video conferencing.
- Use trusted authentication methods like SMS codes, authenticator apps, or security keys.
- Be cautious of phishing attempts that try to trick you into sharing your 2FA codes.
Regular Software Updates
Keeping software up-to-date is critical for patching security vulnerabilities. Cybercriminals often exploit known flaws in outdated software to gain unauthorized access.
- Enable automatic software updates whenever possible.
- Install security patches promptly when they become available.
- Check for updates regularly for operating systems, web browsers, and webcam applications.
Firewall Protection
Firewalls act as a barrier between a user’s device and the internet, monitoring and controlling network traffic. They can significantly reduce the risk of malicious connections.
- Ensure a firewall is enabled on all devices connected to the internet.
- Configure firewall settings to block suspicious or unwanted network traffic.
- Understand the specific features of your firewall software and how to use them effectively.
Best Practices for Safe Online Behavior
Responsible online behavior is crucial in preventing exploitation. Awareness and caution are essential elements in protecting oneself from webcam attacks.
- Avoid sharing personal information online, especially on unverified websites.
- Be wary of suspicious links, messages, or websites.
- Verify the identity of individuals before engaging in video calls or sharing personal information.
- Use a strong, unique password for every online account.
- Do not click on links or open attachments from unknown senders.
Security Measures Effectiveness Table
This table demonstrates the effectiveness of various security measures against webcam attacks. Higher ratings indicate greater effectiveness.
Legal and Ethical Considerations
The digital realm, while offering unprecedented opportunities, presents unique legal and ethical challenges. As technology evolves, so too must our understanding and application of laws and ethical principles to address emerging threats like webcam enslavement. This section explores the legal implications of such attacks, examines relevant legislation, and delves into the ethical responsibilities of individuals and organizations in preventing and responding to these crimes.The blurred lines between virtual and physical spaces demand a nuanced approach to legal frameworks and ethical considerations.
Traditional laws designed for physical interactions often struggle to adequately address the complexities of online harassment and cybercrime. Consequently, a careful examination of existing legal instruments and the development of new regulations are critical to ensuring accountability and protecting vulnerable individuals in the digital age.
Legal Implications of Webcam Enslavement Attacks
The legal ramifications of webcam enslavement attacks are multifaceted and vary depending on the jurisdiction and specific actions taken by the perpetrators. Criminal charges might include, but are not limited to, extortion, blackmail, and online harassment. The severity of these charges often hinges on the degree of harm inflicted on the victim, the nature of the threat, and the evidence available to support the accusations.
Existing Laws and Regulations
Numerous laws and regulations exist to address online harassment and cybercrime, but they are often not explicitly designed for webcam enslavement. Examples include:
- Cyberstalking laws: Many jurisdictions have laws prohibiting the use of electronic means to harass or stalk another person. These laws can be applied to situations involving webcam enslavement if the perpetrator’s actions meet the statutory definition of stalking or harassment.
- Online harassment statutes: Some jurisdictions have specific laws addressing online harassment, which can be used to prosecute perpetrators of webcam enslavement attacks, particularly if the harassment includes threats, intimidation, or the dissemination of harmful information.
- Extortion and blackmail laws: These laws often criminalize the act of obtaining something of value (e.g., money, personal information) through coercion or threats. Webcam enslavement attacks, when involving demands for something in exchange for ceasing the abuse, can potentially fall under these legal frameworks.
- Data protection laws: Regulations like GDPR in Europe and CCPA in California address the collection, use, and sharing of personal data. If the perpetrators collect or use personal data in the course of an attack, these laws could potentially be invoked.
Ethical Responsibilities of Individuals and Organizations
Individuals and organizations have a crucial role to play in preventing and responding to webcam enslavement attacks. Ethical responsibilities encompass:
- Promoting digital literacy and awareness: Educating individuals about online safety practices, recognizing red flags, and understanding their rights can help prevent them from becoming victims. Organizations should implement training programs for their employees and clients.
- Establishing clear reporting mechanisms: Creating channels for victims to report attacks, ensuring confidentiality and providing support, is essential. Transparency about these reporting mechanisms should be communicated effectively.
- Encouraging proactive measures to prevent attacks: Implementing strong security protocols, including two-factor authentication and robust password policies, can reduce the likelihood of being targeted. Regular security audits can help to identify vulnerabilities.
- Providing resources and support to victims: Offering counseling, legal assistance, and emotional support to victims is vital for their recovery. Organizations should have procedures in place to assist individuals affected by these attacks.
Ethical Considerations in Different Jurisdictions
The ethical considerations surrounding webcam enslavement attacks vary across jurisdictions due to differing legal frameworks, cultural norms, and societal values. For instance, interpretations of privacy rights and the definition of harm might differ between countries.
Hackers turning webcam users into unwitting slaves is a serious concern. But, it’s crucial to understand that vulnerabilities in systems like Microsoft Azure Cosmos DB, as detailed in Azure Cosmos DB Vulnerability Details , can indirectly affect security practices. This means we need to be extra vigilant about our online habits, making sure we’re not unintentionally leaving ourselves open to becoming targets of such malicious actions.
It’s all about proactive security.
Illustrative Examples
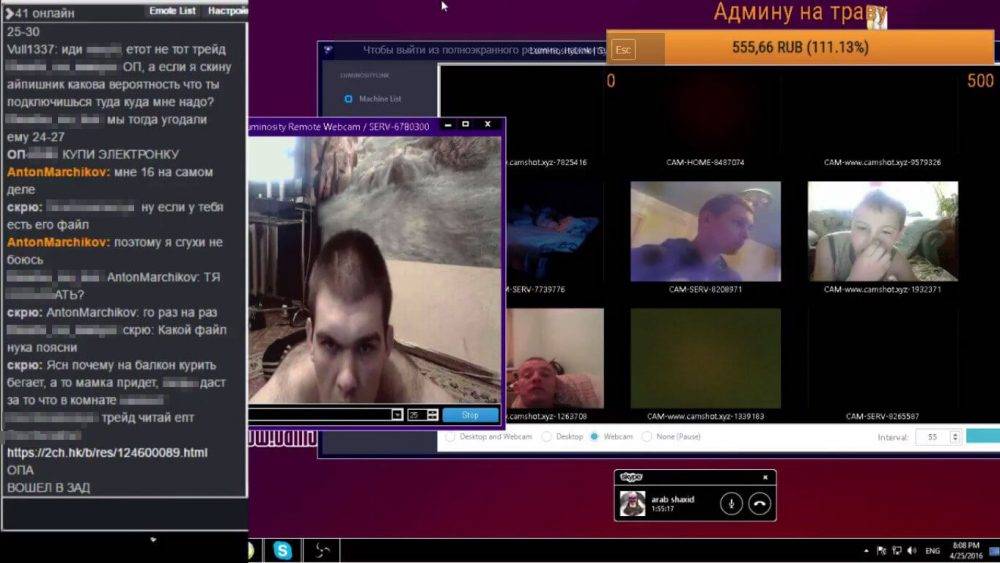
The chilling reality of webcam enslavement isn’t just a theoretical threat. Real-world cases demonstrate the disturbing potential for hackers to exploit vulnerabilities and inflict significant harm on individuals. Understanding these examples is crucial for recognizing the tactics employed and formulating effective defenses.
Hypothetical Webcam Attack Scenario
A young graphic designer, Sarah, enjoys live streaming her work progress to her online community. Unbeknownst to her, a sophisticated hacker, known only as “Spectre,” has been monitoring her webcam activity for weeks. Spectre identifies a security vulnerability in Sarah’s webcam software, allowing him remote access.
Steps a Hacker Might Take
- Exploiting a known vulnerability in Sarah’s webcam software, Spectre gains unauthorized access.
- Installing malicious software on Sarah’s computer, enabling remote control.
- Taking control of Sarah’s webcam and microphone, allowing him to monitor her activities, record her conversations, and even manipulate her surroundings.
- Using the webcam to capture sensitive data, such as passwords, financial information, or personal documents. This could include screenshots of sensitive documents or recordings of conversations.
- Attempting to extort or blackmail Sarah by threatening to publicly release the compromising footage.
Steps a Victim Could Take to Recover
- Immediately disconnect the webcam and any other devices that might be affected by the attack.
- Run a full system scan with reputable antivirus and anti-malware software.
- Change all passwords, especially those associated with online accounts that were accessed.
- Contact a cybersecurity professional for further assistance in removing any malicious software and restoring the system.
- Report the incident to the relevant authorities if sensitive information was compromised.
Emotional Toll of a Webcam Attack
Imagine the profound emotional impact on Sarah. The violation of her privacy, the potential for humiliation and embarrassment, and the knowledge that someone has intimate access to her personal space would be devastating. Beyond the technical aspects of the attack, there is a profound emotional and psychological cost. Fear, anxiety, and distrust are likely to follow such an event.
She might struggle to trust others, experience sleep disturbances, and even develop symptoms of post-traumatic stress. The damage extends far beyond the immediate technical breach. The emotional trauma can have long-lasting effects on mental well-being.
Technological Countermeasures

Protecting webcam users from malicious actors requires a multifaceted approach. Beyond user awareness and robust security policies, technological solutions play a crucial role in detecting and mitigating attacks. These solutions can range from simple software additions to complex encryption protocols, each designed to bolster security and safeguard user privacy.
Security Software Solutions
Effective security software is essential for preventing webcam hijacking attempts. These programs, often integrated into operating systems or available as standalone applications, monitor webcam activity in real-time. They can identify suspicious behaviors, such as unusual access attempts or data transmission patterns, triggering alerts or blocking unauthorized access. Advanced security software often includes machine learning algorithms that can adapt to evolving attack techniques.
By constantly learning and identifying new threats, these programs enhance the protection of webcam users.
- Real-time Monitoring: Security software constantly observes webcam activity, scrutinizing any unusual patterns that might indicate an intrusion. These programs can detect and flag attempts to gain unauthorized control over the webcam.
- Automated Blocking: When a threat is identified, security software can automatically block the malicious activity, preventing the attacker from gaining access or exfiltrating data.
- Intrusion Detection Systems: Advanced security software often incorporates intrusion detection systems that analyze network traffic and identify suspicious patterns associated with webcam hijacking. These systems can trigger alerts to administrators and help them prevent potential attacks.
- Whitelisting: Some security programs utilize whitelisting to restrict webcam access to only trusted sources. This approach prevents unauthorized applications from interacting with the webcam, effectively creating a firewall for the webcam connection.
Encryption Technologies for Webcam Communications, Hackers are turning webcam users into slaves
Encryption is a cornerstone of secure webcam communications. By encrypting the data transmitted during webcam sessions, it becomes unreadable to unauthorized parties. This protects sensitive information and prevents malicious actors from accessing or tampering with the stream. Different encryption algorithms offer varying levels of security and performance. Robust encryption methods are crucial to safeguard the privacy and integrity of webcam data.
- End-to-End Encryption: This approach ensures that only the intended recipient can decipher the data. It provides the highest level of security, as the data remains encrypted throughout its transmission, making it impervious to eavesdropping or manipulation.
- Transport Layer Security (TLS): TLS is a widely used protocol that encrypts the connection between the webcam and the recipient. This ensures that data transmitted over the network is secure and prevents unauthorized interception.
- HTTPS: When using webcams for video conferencing or other online activities, ensuring that the connection is over HTTPS is crucial. HTTPS encrypts the communication channel, protecting data from unauthorized access.
Secure Webcam System Diagram
The following diagram illustrates the flow of data in a secure webcam system, highlighting the role of encryption.
It’s terrifying how hackers are turning webcam users into unwitting slaves, controlling their devices remotely. This highlights the critical need for proactive security measures, like those discussed in “Deploying AI Code Safety Goggles Needed” Deploying AI Code Safety Goggles Needed. Stronger defenses are essential to prevent these kinds of digital enslavements from happening. We need to prioritize security measures in our digital world to stop these types of intrusions.
| Component | Description |
|---|---|
| Webcam | Captures video and transmits data. |
| Encryption Module | Encrypts the data before transmission. |
| Network | Facilitates secure data transfer. |
| Decryption Module | Decrypts the data upon reception. |
| Recipient Device | Receives and displays the decrypted video stream. |
[Diagram Placeholder: A simple diagram showing the webcam, an encryption module, the network, a decryption module, and the recipient device, with arrows indicating the encrypted data flow.]
Note: The diagram would visually depict the data flowing through each component, clearly indicating the encryption and decryption process.
Last Recap: Hackers Are Turning Webcam Users Into Slaves
In conclusion, the insidious nature of webcam hacking demands a multifaceted approach to prevention and mitigation. By understanding the various methods hackers employ, the vulnerabilities they exploit, and the potential consequences of these attacks, we can empower individuals to take proactive steps to protect themselves. This requires a combination of technical safeguards, responsible online behavior, and a heightened awareness of the potential risks involved.
Remember, vigilance and proactive measures are essential in safeguarding your digital security and well-being in the face of evolving cyber threats.
FAQ Summary
What are some common methods hackers use to gain access to webcams?
Hackers employ various tactics, including malware disguised as legitimate software, social engineering techniques to trick users into revealing login credentials, and exploiting vulnerabilities in outdated software or operating systems.
What are the psychological effects of being a victim of a webcam attack?
Victims often experience feelings of violation, anxiety, paranoia, and a loss of trust. The constant surveillance can lead to significant emotional distress.
How can I protect myself from webcam hacking?
Employ strong passwords, enable two-factor authentication, keep software updated, and use a firewall. Be cautious of suspicious emails or links, and avoid sharing personal information online.
What legal recourse is available to victims of webcam hacking?
Legal options vary depending on the jurisdiction and specific circumstances. Reporting the incident to law enforcement and documenting all evidence is crucial.





