DC Surveillance Cameras Hacker Ransomware Threat
Hackers use Washington DC security surveillance cameras to spread ransomware, exploiting vulnerabilities in these systems to deploy malicious software. This sophisticated tactic leverages the city’s extensive network of cameras, potentially compromising vital infrastructure and disrupting public services. Understanding the methods, motivations, and impacts of these attacks is crucial for bolstering security and mitigating future threats.
This article delves into the specifics of these attacks, examining the types of cameras and systems targeted, the ransomware delivery mechanisms, and the potential consequences for the city and its citizens. We’ll also explore best practices for enhancing security protocols and mitigating the risk of future attacks.
Introduction to Surveillance Camera Hacking and Ransomware: Hackers Use Washington Dc Security Surveillance Cameras To Spread Ransomware
Security surveillance systems, ubiquitous in public spaces and private establishments, often present vulnerabilities that hackers exploit. These vulnerabilities, coupled with the increasing sophistication of hacking techniques, can lead to significant security breaches, including the deployment of ransomware. This article explores the methods employed in such attacks, focusing on the case of Washington D.C. security systems.Surveillance camera systems are frequently targeted because of their interconnected nature.
They often rely on outdated or poorly maintained software and hardware, leaving them susceptible to known exploits. Furthermore, the sheer volume of these systems across a city like Washington D.C. makes individual patching and security upgrades challenging and prone to delays.
Vulnerabilities in Security Surveillance Systems
Security cameras, especially those integrated into larger networks, are often poorly secured. This can range from default passwords on network devices to insufficient firewall protection. Lack of regular security updates and outdated operating systems are common weaknesses. Compromised systems can be used as stepping stones for broader network intrusions, leading to the theft of sensitive data.
Methods of Compromising Surveillance Systems
Hackers employ various methods to gain access to surveillance systems. Common attack vectors include exploiting known vulnerabilities in the camera firmware, exploiting weak passwords on network devices, and phishing attacks targeting system administrators. Social engineering plays a critical role in these attacks, often leveraging human error or lack of security awareness.
Ransomware Deployment
Once hackers gain access to a surveillance system, they can deploy ransomware. This involves encrypting the system’s data or functionality, demanding payment for its release. This can affect not just the cameras themselves, but also the entire network to which they are connected. In the case of Washington D.C., this could affect multiple government agencies, and possibly even the wider public if data transmission is interrupted.
Motivations Behind Targeting Washington D.C. Security Systems
The motivations behind targeting Washington D.C.’s security systems are likely multifaceted. Financial gain is a prime motivator, with hackers potentially seeking to extort money from the city government. Ideological motivations, such as disrupting public services or causing reputational damage, may also play a role. The sensitive nature of the data held by Washington D.C. government agencies could also attract hackers seeking to exploit this information.
Attack Methodologies
| Attack Method | Vulnerability Exploited | Target System Component | Impact on Surveillance |
|---|---|---|---|
| Exploiting default passwords | Weak authentication | Network devices (routers, switches) | Loss of camera access, potential network compromise |
| SQL injection | Database vulnerabilities | Camera management software | Data breaches, unauthorized access to camera recordings |
| Malware injection | Operating system vulnerabilities | Camera firmware | Camera malfunction, data encryption, system denial |
| Brute-force attacks | Weak passwords | Camera accounts | Unauthorized access, potential data breaches |
Specifics of Washington D.C. Security Systems

Washington, D.C., a city of immense historical and political significance, relies heavily on sophisticated security systems to protect its critical infrastructure and citizens. Understanding the specific types of cameras and systems used, along with their vulnerabilities, is crucial for assessing potential risks and developing robust mitigation strategies. This analysis examines the potential weaknesses within the city’s security architecture, considering the geographical factors that may impact the ease of exploitation.
Common Surveillance Camera Types and Systems
Washington D.C. likely employs a variety of surveillance technologies, including IP cameras, dome cameras, and PTZ (pan-tilt-zoom) cameras. These systems often integrate with access control systems, intrusion detection systems, and other security infrastructure. The use of cloud-based storage and video management systems (VMS) is also common. This diversity of systems, while offering comprehensive coverage, can introduce interconnected vulnerabilities if not properly managed.
Vulnerabilities of Specific Systems
Security systems, despite their sophistication, are not impenetrable. IP cameras, for instance, are often susceptible to network-based attacks. Vulnerable firmware, outdated software, and weak passwords can create avenues for hackers to gain unauthorized access. Similarly, poorly configured VMS can expose sensitive data and allow for unauthorized video access. Even seemingly secure access control systems can be compromised through social engineering tactics or sophisticated phishing attacks.
Potential Infrastructure Impacts
Compromised security systems can have far-reaching consequences for Washington D.C.’s infrastructure. Disruption of surveillance feeds can impede law enforcement efforts and create blind spots in critical areas. Unauthorized access to sensitive data, such as building blueprints or security protocols, can jeopardize physical security and potentially lead to significant damage. Further, a ransomware attack targeting critical infrastructure components could cripple essential services like transportation or utilities.
Geographical Factors and Ease of Hacking
The density of surveillance cameras in high-traffic areas and the location of critical infrastructure (like government buildings or power grids) could influence the ease of hacking. High camera density might increase the potential for large-scale disruption, while strategic placement of critical infrastructure could provide an attractive target for targeted attacks. The interconnected nature of the city’s systems and the reliance on shared networks could also amplify the impact of a breach.
Examples of Similar Security Breaches
Several incidents around the world demonstrate the potential for similar security breaches in urban environments. In one case, a city’s surveillance network was compromised, leading to disruption of traffic management and hindering emergency response. Other examples involve hackers exploiting vulnerabilities in building management systems, impacting critical infrastructure operations.
| System Type | Vulnerability | Potential Impact on City Infrastructure | Mitigation Strategies |
|---|---|---|---|
| IP Cameras | Outdated firmware, weak passwords, network vulnerabilities | Disruption of surveillance feeds, unauthorized access to sensitive data | Regular firmware updates, strong passwords, robust network security |
| VMS | Poor configuration, lack of access controls | Unauthorized access to video footage, data breaches | Strong access controls, regular security audits, encrypted data storage |
| Access Control Systems | Social engineering, phishing attacks, weak authentication | Unauthorized access to buildings, disruption of normal operations | Multi-factor authentication, security awareness training, regular penetration testing |
| Network Infrastructure | Shared vulnerabilities, inadequate security protocols | Broader network disruption, compromise of multiple systems | Segmentation of networks, robust firewalls, intrusion detection systems |
Ransomware Delivery Mechanisms
After successfully compromising surveillance cameras in Washington D.C., hackers employ various sophisticated methods to deploy ransomware. This often involves exploiting vulnerabilities in connected systems, leveraging the initial access gained to propagate the malicious code throughout the network. Understanding these mechanisms is crucial for organizations to implement robust security measures and prevent such attacks.
Ransomware Delivery Methods
The delivery of ransomware payloads often follows a multi-stage process, beginning with initial access through compromised surveillance cameras. This initial foothold allows attackers to deploy additional malware, move laterally through the network, and ultimately deliver the ransomware. Common methods include exploiting vulnerabilities in software applications, using stolen credentials, or exploiting weak security configurations. The attackers meticulously plan their approach, choosing the most effective method for maximizing their chances of success and minimizing the risk of detection.
Ransomware Types
Various ransomware types exist, each with unique characteristics and impact. Some popular types include encrypting ransomware, which renders data inaccessible, and locker ransomware, which locks users out of their systems. The selection of a particular ransomware type often depends on the attacker’s objectives and target. For example, encrypting ransomware is often used to extract a ransom payment, while locker ransomware may be employed for disruption or as a preliminary step in a larger attack.
Encryption Process
The encryption process employed by ransomware varies depending on the specific type and its complexity. The process usually involves identifying target files, encrypting them using a strong encryption algorithm, and then making the encrypted data inaccessible. Advanced ransomware often uses sophisticated encryption techniques to make decryption difficult without the correct decryption key. The encryption process can be remarkably fast, depending on the size of the data being encrypted and the computational resources available to the attacker.
Ransomware Payloads and Impact
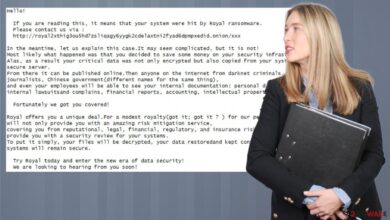
Ransomware payloads can range from simple scripts to complex programs with advanced features. These payloads often contain instructions for encrypting files, contacting command-and-control servers, and displaying ransom notes. The impact of a ransomware attack can be devastating, causing significant financial losses, operational disruptions, and reputational damage. For example, a healthcare organization hit by ransomware could experience delays in patient care, while a financial institution could face significant operational issues.
The consequences of such attacks extend beyond the immediate financial losses, encompassing the long-term implications for the victim organization.
Example Ransomware Attacks
The following table illustrates some ransomware types, their delivery methods, target systems, and encryption processes. It’s important to note that these are simplified examples, and real-world attacks can be far more complex.
| Ransomware Type | Delivery Method | Target Systems | Encryption Process |
|---|---|---|---|
| CryptoLocker | Malicious email attachments, infected websites | Windows-based computers | Symmetric encryption using RSA public key infrastructure |
| WannaCry | Exploiting vulnerabilities in outdated systems | Windows-based systems | AES encryption with a unique key for each victim |
| LockBit | Exploiting vulnerabilities in systems, using compromised credentials | Various operating systems | Advanced encryption algorithms, often with multiple layers of protection |
| REvil | Exploiting vulnerabilities in systems, using compromised credentials | Various operating systems | Advanced encryption algorithms, often with custom-built components for encryption |
Impact and Consequences of the Attacks

Ransomware attacks targeting Washington D.C.’s security surveillance cameras represent a significant threat to the city’s public safety and infrastructure. The potential consequences extend far beyond simple disruption, impacting financial stability, critical services, and potentially even jeopardizing the safety of residents. These attacks, if successful, could have cascading effects on the city’s operations and the trust placed in its systems.The consequences of such attacks are multifaceted and severe, affecting various aspects of the city’s functioning.
From compromised security systems to potential disruptions in vital services, the impact is wide-ranging and demands careful consideration. Understanding these potential impacts is crucial to developing effective preventative and response strategies.
Potential Consequences on Public Safety and Security
Compromised surveillance systems directly impact public safety. Critically, if the attackers gain access to real-time camera feeds, they could potentially disrupt emergency response efforts, obstruct investigations into criminal activities, and compromise the security of public spaces. This lack of real-time surveillance could potentially lead to increased crime rates and hinder the city’s ability to maintain a safe environment for its residents.
Financial Implications for the City and Affected Organizations
The financial implications of ransomware attacks are substantial. Beyond the immediate ransom demands, the cost of recovery, including data restoration, system remediation, and potential legal fees, can be astronomical. For example, the city or affected organizations may face significant financial burdens if they have to restore data, rebuild systems, and compensate for lost productivity. Furthermore, reputational damage can lead to lost business opportunities and public distrust.
Impact on Critical Infrastructure and Public Services
Ransomware attacks on critical infrastructure, such as water or electricity systems, can have devastating consequences. Imagine a scenario where a cyberattack disrupts the city’s water supply. This would not only lead to significant financial losses but also severely impact public health and safety. Similar disruptions to other essential services like electricity, transportation, or communication networks could cripple the city’s ability to function effectively.
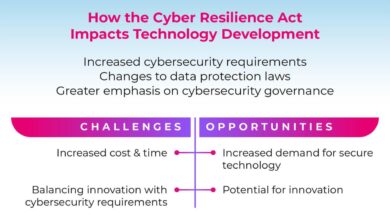
Potential Legal and Regulatory Responses
Legal and regulatory responses to ransomware attacks are evolving. The city and affected organizations may face legal ramifications if they fail to comply with data protection regulations or adequately secure their systems. This includes potential civil lawsuits and criminal investigations, depending on the severity of the breach and the nature of the attack. Furthermore, increased regulatory scrutiny and the development of new legislation are likely outcomes, aimed at preventing future attacks and holding perpetrators accountable.
Damage to Critical City Services
Disruptions to critical city services, such as water, electricity, or transportation, could have significant consequences. A ransomware attack targeting a water treatment facility, for instance, could lead to widespread contamination and health risks. Similarly, an attack on an electricity grid could result in widespread power outages, impacting essential services and potentially causing widespread economic damage. The city would face immense challenges in restoring services, potentially requiring significant financial investment and extended recovery times.
Potential Impacts: Table
| Infrastructure Affected | Type of Damage | Recovery Time Estimates | Cost Implications |
|---|---|---|---|
| Water Treatment Plant | Disruption of water supply, potential contamination | Weeks to months | High (remediation, public health response, lost revenue) |
| Electricity Grid | Widespread power outages, disruption of essential services | Days to weeks | Very High (infrastructure repair, business disruption) |
| Transportation Systems | Disruption of public transportation, traffic congestion | Days to weeks | High (system restoration, lost revenue) |
| City Surveillance Systems | Loss of real-time surveillance, potential security risks | Days to weeks | Moderate to High (system restoration, security enhancements) |
Security Best Practices and Mitigation Strategies
The recent ransomware attacks targeting Washington D.C.’s surveillance systems highlight a critical vulnerability in modern infrastructure. Effective security protocols are paramount to prevent future incidents and protect sensitive data. These attacks underscore the need for proactive measures to bolster security and ensure the reliable operation of critical systems.Strengthening security protocols for surveillance systems requires a multi-faceted approach, addressing both technical vulnerabilities and human factors.
This involves implementing robust security measures, establishing clear incident response plans, and fostering a culture of security awareness among all personnel. By implementing these strategies, Washington D.C. can significantly reduce the risk of similar attacks and safeguard its vital infrastructure.
Strengthening Surveillance System Security
Robust security measures are essential for protecting surveillance systems. This involves multiple layers of defense, from network-level security to device-level encryption. Implementing strong authentication protocols, regular software updates, and intrusion detection systems are crucial steps. Regular security audits and penetration testing help identify and address potential vulnerabilities before attackers exploit them.
Implementing Strong Authentication Protocols
Implementing multi-factor authentication (MFA) is a critical security measure. Requiring both a password and a one-time code from a mobile device adds an extra layer of protection, making it significantly harder for unauthorized individuals to access the system. This enhanced authentication significantly reduces the risk of unauthorized access and subsequent malicious activities.
So, hackers are using DC security cameras to spread ransomware, which is a serious concern. This reminds me of recent vulnerabilities, like the one affecting Azure Cosmos DB. Understanding those vulnerabilities, like the ones detailed in Azure Cosmos DB Vulnerability Details , is crucial for securing our systems against similar attacks. Knowing how hackers exploit weaknesses in seemingly unrelated areas, like cloud databases, can help us better protect our physical security systems, like those in Washington D.C.
It all connects back to the potential for ransomware attacks using unexpected entry points.
Regular Software Updates and Patching
Maintaining up-to-date software is paramount. Vulnerabilities in outdated software are frequently exploited by attackers. Proactive patching and software updates ensure that systems are protected against known vulnerabilities, preventing attackers from leveraging these weaknesses to gain unauthorized access. Implementing automated patching processes and adhering to a rigorous update schedule are key to maintaining a robust defense.
Hackers exploiting DC security cameras to spread ransomware highlights a critical need for better security protocols. This isn’t just about physical security; it’s about the potential for vulnerabilities in software code. That’s why deploying AI code safety tools, like those discussed in Deploying AI Code Safety Goggles Needed , is crucial. Ultimately, preventing this kind of cyberattack requires a multi-faceted approach, encompassing both physical and digital security measures.
Protecting against hackers using DC surveillance cameras in this way demands attention to both the hardware and the software.
Network Segmentation and Isolation
Segmenting the network isolates surveillance systems from other critical infrastructure, limiting the impact of a breach. This strategic approach ensures that a compromise in one segment does not automatically lead to a compromise of other systems. It’s a crucial measure to contain the potential damage of an attack.
Intrusion Detection and Prevention Systems (IDPS)
Implementing IDPS helps identify and respond to malicious activity in real-time. These systems monitor network traffic for suspicious patterns and behaviors, alerting administrators to potential threats. By proactively detecting and mitigating threats, organizations can prevent unauthorized access and the deployment of ransomware.
Incident Response Plan
Developing a comprehensive incident response plan is crucial for effectively handling security breaches. This plan should Artikel the steps to be taken in case of a cyberattack, including containment procedures, data recovery strategies, and communication protocols. The plan must also detail how to report incidents to relevant authorities.
Security Awareness Training
Training staff on security best practices is essential. Educating employees about phishing attacks, social engineering tactics, and other potential threats helps them recognize and avoid potential vulnerabilities. Regular training reinforces the importance of security awareness and promotes a culture of security vigilance.
So, hackers are using DC security cameras to spread ransomware, which is pretty concerning. It highlights the vulnerability of even seemingly robust security systems. Fortunately, the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions is a positive step to address similar vulnerabilities in a different context, but it doesn’t really offer a direct solution to the issue of hackers using surveillance cameras for ransomware.
This whole situation just underscores the constant battle against sophisticated cyberattacks.
Table of Security Measures
| Security Measure | Implementation Steps | Cost Estimates | Effectiveness |
|---|---|---|---|
| Multi-factor authentication (MFA) | Implement MFA for all user accounts. | Moderate | High |
| Regular software updates | Establish a schedule for software updates and patches. | Low | High |
| Network segmentation | Segment the network to isolate surveillance systems. | High | High |
| Intrusion Detection/Prevention System (IDPS) | Deploy and configure IDPS. | High | High |
| Incident Response Plan | Develop and test an incident response plan. | Moderate | High |
| Security Awareness Training | Conduct regular security awareness training. | Low | Moderate |
Illustrative Case Studies (Hypothetical)

A hypothetical ransomware attack on a Washington D.C. surveillance system can expose critical vulnerabilities in urban security infrastructure. Analyzing such a scenario helps in identifying potential weaknesses and formulating effective mitigation strategies. Understanding the progression, impact, and potential solutions is crucial for bolstering the resilience of security systems in similar environments.
Hypothetical Ransomware Attack on a D.C. Surveillance System
A sophisticated cybercriminal group targets a less-than-fully-updated surveillance system in a D.C. government building. They exploit a known vulnerability in the system’s network management software, gaining unauthorized access. Their initial reconnaissance reveals the system’s critical role in monitoring public spaces and responding to emergencies.
Progression of the Attack
The attackers gain initial access by exploiting a known vulnerability in the network management software. They then move laterally within the network, escalating privileges to gain control over the entire surveillance system. This includes gaining access to cameras, recording devices, and control systems. Next, they encrypt the system’s data, rendering it unusable. Finally, they issue a ransom demand for its restoration, threatening to release sensitive footage if the demand is not met.
Consequences of the Attack
The attack’s consequences are severe. The surveillance system, crucial for public safety and law enforcement, becomes completely unusable. Emergency response is significantly hampered, as vital video footage becomes inaccessible. Potential criminal activity goes undetected, potentially escalating the risk of violent crimes. The release of sensitive footage could compromise privacy and potentially damage the reputation of the affected agency.
Furthermore, financial losses from lost productivity and potential legal ramifications are considerable.
Mitigation Strategies, Hackers use washington dc security surveillance cameras to spread ransomware
Proactive security measures could prevent such an attack. Implementing robust multi-factor authentication, regular software updates, and penetration testing are crucial. Network segmentation to isolate the surveillance system from other sensitive networks and installing intrusion detection systems to detect malicious activity are also essential steps.
Lessons Learned
The hypothetical scenario highlights the importance of proactive security measures. Regular vulnerability assessments, penetration testing, and employee training are critical in preventing successful attacks. The interdependence of surveillance systems with public safety mandates a strong security posture.
| Phase | Action | Impact | Mitigation Strategy |
|---|---|---|---|
| Initial Access | Exploitation of known vulnerability in network management software. | Unauthorized access to the system. | Regular software updates and vulnerability patching. |
| Lateral Movement | Moving within the network to gain control over more components. | Increased control over the surveillance system. | Network segmentation to isolate the surveillance system from other networks. |
| Encryption | Encrypting the system’s data. | System becomes unusable. | Regular backups of critical data, preferably offline. |
| Ransom Demand | Issuing a ransom demand. | Financial losses, potential reputational damage, and disruption of public safety operations. | Strong incident response plan and negotiation strategy. |
Conclusion
In conclusion, the vulnerability of Washington D.C.’s security surveillance systems to ransomware attacks highlights the critical need for robust cybersecurity measures. This threat underscores the importance of proactive security strategies and the need for ongoing vigilance in protecting critical infrastructure. By understanding the tactics employed by hackers, and implementing preventative measures, we can better safeguard our cities from such sophisticated cyberattacks.
Q&A
What are some common vulnerabilities in security surveillance systems that hackers exploit?
Weak passwords, outdated software, lack of multi-factor authentication, and inadequate security protocols are common vulnerabilities. Hackers often exploit these weaknesses to gain unauthorized access.
What types of ransomware are used in these attacks?
Various ransomware types can be employed, each with its unique encryption and extortion methods. Some examples include encrypting files, locking systems, and demanding payment for decryption keys.
What are the potential impacts on public safety and security in Washington D.C.?
Compromised surveillance systems could lead to a loss of situational awareness, impacting public safety and emergency response capabilities. Disruption of critical services, such as water or electricity, is also a significant concern.
What are some mitigation strategies to prevent future attacks?
Implementing strong passwords, regularly updating software, implementing multi-factor authentication, and employing intrusion detection systems are crucial steps. Training personnel on cybersecurity best practices is also vital.