Heres How to Turn On Ransomware Protection on Windows 10
Heres how to turn on the ransomware protection on window 10 – Here’s how to turn on the ransomware protection on Windows 10 sets the stage for understanding a critical security measure. Ransomware is a serious threat, capable of locking you out of your files and demanding payment for their release. This guide walks you through the process of enabling robust ransomware protection on your Windows 10 system, covering both built-in Windows Defender and third-party options.
Knowing how to protect your data is essential in today’s digital world, and this guide is your first step.
Protecting your Windows 10 system from ransomware is crucial. This comprehensive guide explores the essential steps to safeguard your valuable data from cyber threats. We’ll dive into both the built-in Windows Defender features and popular third-party software options, comparing their strengths and weaknesses. You’ll gain a thorough understanding of ransomware protection settings and troubleshooting common issues.
Introduction to Ransomware Protection
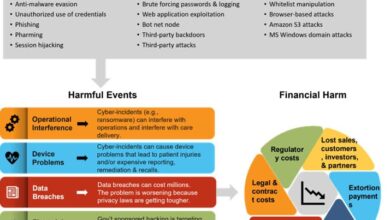
Ransomware is a type of malicious software that encrypts files on a computer system, rendering them inaccessible. Victims are then typically presented with a demand for payment to regain access to their data. This can lead to significant financial losses and operational disruptions, particularly for individuals and businesses relying on their data for daily operations.Ransomware attacks are a serious threat to Windows 10 systems.
Without adequate protection, sensitive information, including personal documents, financial records, and business data, can be compromised. Enabling ransomware protection is crucial to safeguarding your data and preventing significant financial and reputational damage.
Common Ransomware Attacks Targeting Windows 10
Ransomware attacks often exploit vulnerabilities in operating systems or software applications. Sophisticated methods, such as phishing emails containing malicious attachments or links, are frequently used to deliver ransomware payloads. These attacks can also target vulnerabilities in systems through exploits. Other common attack vectors include malicious websites and compromised software downloads. The increasing sophistication of ransomware makes proactive protection essential.
Importance of Ransomware Protection on Windows 10
Having ransomware protection enabled is a critical step in safeguarding your Windows 10 system. It provides a defense mechanism against various ransomware attacks, mitigating the potential for data loss and financial repercussions. This protection can block or detect malicious code, preventing infection and ensuring data integrity. The security measures in place help to limit the scope and impact of any potential attack.
General Steps for Enabling Ransomware Protection
Enabling ransomware protection on Windows 10 involves utilizing built-in security features or installing third-party software. The process typically involves configuring settings within the operating system, downloading and installing the chosen application, and following on-screen instructions. The exact steps may vary depending on the specific protection method used. The user must carefully follow the guidance to ensure proper setup and functionality.
Comparison of Ransomware Protection Methods
| Protection Method | Description | Pros | Cons |
|---|---|---|---|
| Windows Defender | Built-in security solution in Windows 10. | Free, readily available, often includes real-time protection. | May not offer the same level of customization or advanced features as some third-party solutions. Detection capabilities may vary depending on the type of ransomware. |
| Third-party Software (e.g., Bitdefender, Kaspersky) | Dedicated security software from vendors like Bitdefender or Kaspersky. | Offers a wider range of features and customization options. Often includes advanced threat detection and prevention capabilities. | Requires a subscription fee. Performance may impact system resources. May have a steeper learning curve. |
The table above provides a basic overview of the two common methods. Choosing the right approach depends on the user’s specific needs and budget.
Enabling Windows Defender Ransomware Protection
Windows Defender Ransomware Protection is a built-in security feature in Windows 10 designed to safeguard your system from ransomware attacks. It proactively monitors your system for suspicious activities and blocks potentially harmful actions. This protection layer can significantly reduce the risk of your valuable data being encrypted and held hostage. By understanding and implementing these settings, you can enhance the security of your Windows 10 system.Activating and configuring Windows Defender Ransomware Protection empowers your system to actively counter ransomware threats.
This involves setting up real-time protection, adjusting protection levels, and understanding the specific features. By understanding these configurations, you can tailor the protection to your needs and ensure your system remains secure.
Enabling Real-Time Protection
Real-time protection is a crucial aspect of ransomware protection. It constantly monitors your system for suspicious activities, preventing potential threats from taking hold. This proactive approach significantly minimizes the risk of ransomware infections.
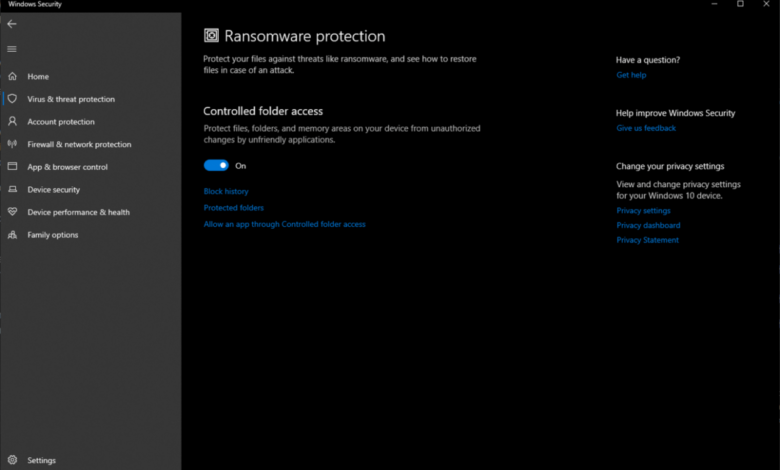
- Open the Windows Security app. This is typically found by searching for “Windows Security” in the Start Menu.
- Navigate to Virus & threat protection.
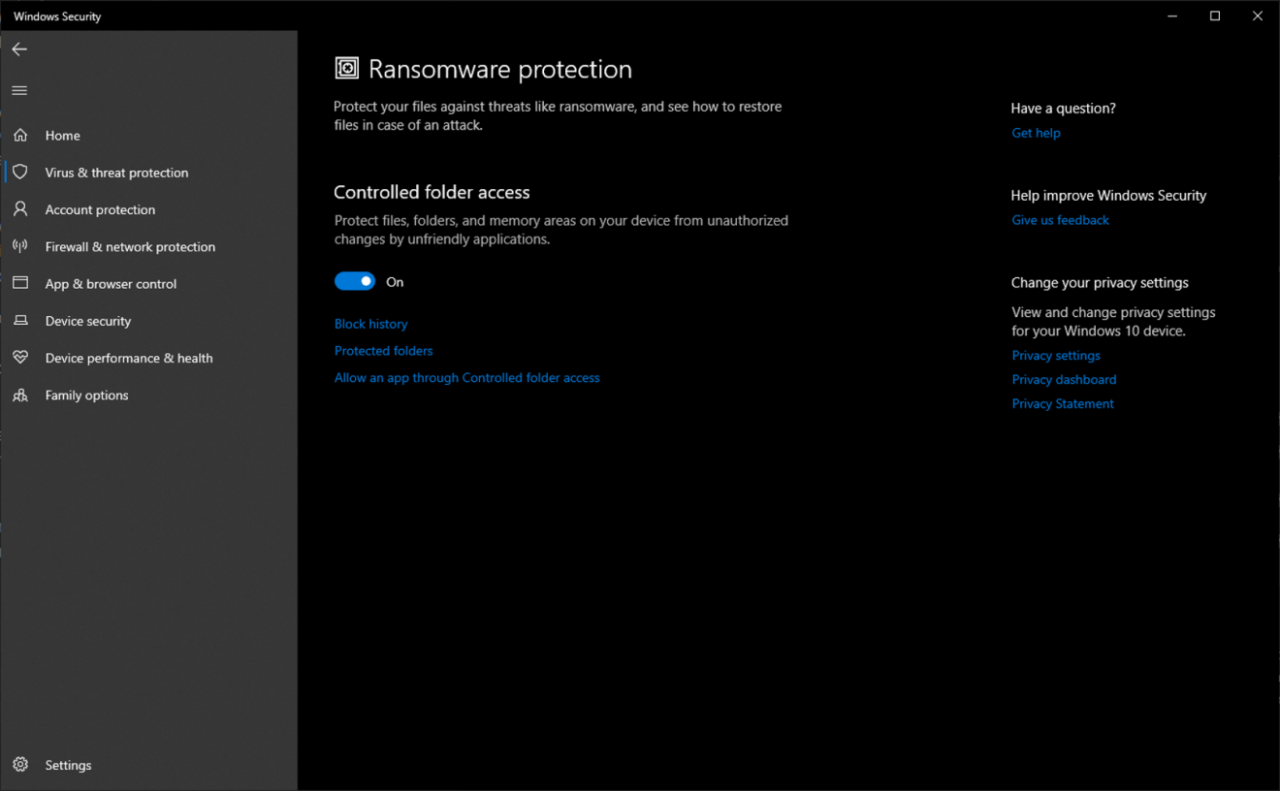
- Select Ransomware protection.
- Toggle the “Ransomware protection” switch to “On.” This enables the real-time protection component of Windows Defender.
Configuring Protection Levels for Files, Heres how to turn on the ransomware protection on window 10
Windows Defender Ransomware Protection allows you to adjust protection levels for different file types. This allows for a tailored approach to security, ensuring sensitive data is adequately protected without hindering productivity.
- In the Ransomware protection settings, click on “Protection history.”
- You’ll see a list of files that have been potentially targeted by ransomware. This history is a valuable tool for assessing the effectiveness of the protection.
- Click on “Manage settings” to further customize the protection level for different file types.
- Navigate through the available options to fine-tune protection for specific file types or locations.
Adjusting Ransomware Protection Level
The ransomware protection level can be adjusted to balance security with usability. A higher level provides greater protection, but might impact system performance. Conversely, a lower level may reduce the protection, but could potentially increase system responsiveness. The ideal setting is contingent upon individual needs and system specifications.
| Protection Level | Description | Impact |
|---|---|---|
| Block | Prevents all known ransomware activities. | Potentially blocks legitimate applications or operations. |
| Alert | Warns you of possible ransomware activity and allows you to decide how to proceed. | Allows more freedom but requires user vigilance. |
| Allow | Does not block ransomware activity. | Minimizes impact on system performance but provides the least protection. |
Features of Windows Defender Ransomware Protection
Windows Defender Ransomware Protection offers several features to bolster system security. These features work in concert to prevent and mitigate ransomware attacks.
- Real-time monitoring: Constantly scans for suspicious activity, blocking threats before they can cause damage.
- File-level protection: Protects files from encryption attempts, preserving data integrity.
- Protection history: Records instances of possible ransomware activity, enabling users to review and assess protection effectiveness.
- Ransomware attack prevention: Blocks known ransomware techniques from infecting your system, thus minimizing the likelihood of attacks.
Configuring Third-Party Ransomware Protection Software
Beyond Windows Defender’s robust ransomware protection, third-party solutions offer specialized features and advanced capabilities. These tools often provide additional layers of defense, proactive threat detection, and granular control over security settings, complementing the built-in protection. Understanding the options available and their respective functionalities empowers users to tailor their security posture to their specific needs.Third-party ransomware protection software solutions often include advanced threat detection mechanisms, enabling them to identify and respond to evolving ransomware tactics.
These solutions can detect suspicious activities and block malicious processes, helping prevent data breaches. They frequently feature real-time monitoring and automated response capabilities, allowing them to act quickly in the event of a potential attack.
Available Third-Party Software Options
Various third-party software options cater to different user needs and technical expertise levels. Popular choices include Bitdefender Antivirus Plus, Kaspersky Anti-Virus, and Malwarebytes Premium. Each offers a unique approach to ransomware protection, often with varying levels of integration and user interface complexity. These options provide comprehensive protection beyond the standard Windows Defender suite.
Comparison of Features and Functionalities
Different third-party solutions offer distinct functionalities. Some focus on proactive threat prevention, while others emphasize real-time monitoring and incident response. This section provides a brief overview of the features offered by these tools:
- Bitdefender Antivirus Plus: This solution typically includes advanced heuristics to identify and block malicious files, real-time scanning, and scheduled scans. It often boasts an intuitive interface for users familiar with the Bitdefender product line. Furthermore, it frequently offers a cloud-based threat detection system, enabling rapid updates and identification of emerging threats.
- Kaspersky Anti-Virus: Kaspersky’s products often prioritize a multi-layered approach to security, combining signature-based detection with behavior analysis to identify malicious activity. This is coupled with a robust threat database to recognize known and unknown ransomware variants. A key feature is its often comprehensive system monitoring, providing users with insights into potential vulnerabilities and threats.
- Malwarebytes Premium: Malwarebytes frequently focuses on proactive threat detection, including advanced threat protection that monitors for suspicious activity, including ransomware attempts. A notable feature is its often robust remediation capabilities, helping users quickly clean up and recover from infections. Its reputation for detecting zero-day threats and sophisticated malware is often considered a strong advantage.
Installation and Setup Procedures
The installation and setup procedures for third-party ransomware protection software generally follow a similar pattern. After downloading the installer, users typically follow on-screen instructions to complete the installation. This usually involves selecting the desired installation options and accepting the license agreement. Post-installation, users often need to configure the software settings to tailor the protection to their specific needs.
Performance and Reliability Comparison
| Software | Performance (Speed and Resource Usage) | Reliability (Detection Rate and False Positives) |
|---|---|---|
| Bitdefender Antivirus Plus | Generally considered efficient with minimal resource impact. | High detection rate, with a relatively low rate of false positives. |
| Kaspersky Anti-Virus | May experience slightly higher resource usage compared to others. | Demonstrates a high detection rate, often with a moderate rate of false positives. |
| Malwarebytes Premium | Often regarded as efficient and lightweight in terms of resource consumption. | High detection rate, with a generally low rate of false positives. |
Configuration Settings
After installation, third-party software typically offers configuration settings to customize the protection. Users can adjust scanning schedules, enable real-time monitoring, configure exclusions for specific files or folders, and customize the level of protection. These settings are critical for tailoring the software’s actions to specific needs and environments.
Understanding Ransomware Protection Settings: Heres How To Turn On The Ransomware Protection On Window 10
Ransomware protection settings in Windows Defender or third-party software are crucial for safeguarding your system against malicious attacks. These settings dictate how the system monitors and responds to potential threats, impacting both security and performance. Proper understanding of these settings empowers you to configure the optimal balance between protection and system responsiveness.Effective ransomware protection isn’t a one-size-fits-all solution.
Different settings cater to various needs and risk profiles. By understanding their implications, you can tailor the protection to your specific environment, ensuring maximum security without undue performance sacrifices.
File Filtering
File filtering is a core component of ransomware protection. It involves monitoring file system activities, particularly file creation, modification, and deletion. This allows the system to detect suspicious patterns indicative of ransomware behavior. The protection software can be configured to identify and block these actions, preventing the encryption of sensitive data.
- Impact on System Performance: File filtering can slightly impact system performance, especially on systems with a large number of files or frequent file operations. Increased monitoring and verification procedures require additional processing power. A more aggressive filtering approach can noticeably impact performance, potentially slowing down file-intensive tasks like video editing or large file transfers.
- Impact on Security: A well-configured file filter significantly enhances security by preventing ransomware from encrypting files. The more comprehensive the filter, the better the protection against ransomware, but at the cost of performance.
- Default vs. Advanced Settings: Default settings typically provide a good balance between security and performance. Advanced settings allow for more granular control over file types, locations, and actions to be monitored, enabling enhanced security for specific use cases. For instance, a user handling sensitive financial data might set more restrictive filters on their local drive.
Behavior Monitoring
Behavior monitoring observes the actions of applications, searching for suspicious behaviors that could indicate ransomware activity. This approach often involves analyzing process creation, file access patterns, and registry modifications.
- Impact on System Performance: Behavior monitoring can impose a noticeable performance overhead, especially when dealing with complex applications. The more comprehensive the monitoring, the greater the performance impact.
- Impact on Security: Robust behavior monitoring significantly increases security by detecting unusual activities before ransomware can encrypt data. A well-implemented monitoring system helps catch malicious code that might not be flagged by file filtering alone.
- Default vs. Advanced Settings: Default settings typically provide a basic level of behavior monitoring. Advanced settings allow for customization to identify specific behaviors or processes that are deemed suspicious. A user working with untrusted software might set more extensive monitoring to protect against unknown threats.
Visual Representation of Ransomware Protection Settings
(Diagram – A simple diagram depicting a flow chart showing the various stages of file filtering and behavior monitoring in relation to the ransomware protection software. The diagram should include different levels of detection and response based on the ransomware protection settings.)Imagine a flow chart with three stages: File Access, Application Activity, and Threat Detection. The first stage, File Access, shows files being accessed.
The middle stage, Application Activity, illustrates programs executing and interacting with the file system. The final stage, Threat Detection, shows the system analyzing actions to determine whether they’re malicious. The diagram would demonstrate how different settings (e.g., high, medium, low) influence the triggers and responses at each stage. Different colors can highlight different levels of security or threat detection.
Examples of Crucial Ransomware Protection Settings
- Sensitive Data Protection: For users with sensitive financial data, a high level of file filtering and behavior monitoring on specific drives (e.g., local drives containing financial records) would be crucial. This prevents ransomware from encrypting sensitive files.
- Regular Users: For general use, medium-level settings can balance security and performance, providing effective protection against common ransomware tactics.
- High-Risk Environments: In environments with a high probability of encountering sophisticated ransomware attacks (e.g., a business handling highly confidential information), aggressive behavior monitoring and potentially more comprehensive file filtering are recommended to catch advanced attacks.
Troubleshooting Ransomware Protection Issues
Ransomware protection, while crucial, isn’t foolproof. Users might encounter snags when setting it up or keeping it running smoothly. Understanding these potential problems and how to fix them can prevent frustrating delays and ensure your system remains secure. This guide provides a structured approach to troubleshooting common issues.
Common Problems and Solutions
Often, conflicts with other software or system errors can interfere with ransomware protection. Identifying these conflicts and resolving them is key to maintaining a robust security posture. A systematic approach is vital in addressing these challenges.
Figuring out how to turn on ransomware protection on Windows 10 is a pretty straightforward process. However, understanding broader security vulnerabilities like those found in Azure Cosmos DB, for example, is equally important. Knowing about potential weaknesses, like those detailed in Azure Cosmos DB Vulnerability Details , helps you take a more comprehensive approach to security.
Ultimately, ensuring your Windows 10 system is protected against ransomware is crucial.
| Potential Issue | Solution |
|---|---|
| Windows Defender Ransomware Protection conflicts with third-party security software. | Ensure Windows Defender is set as the primary ransomware protection. Disabling or uninstalling conflicting third-party applications might be necessary. Consult the documentation for both Windows Defender and any third-party software to understand the optimal configuration for co-existence. It is often advisable to use only one dedicated anti-malware application at a time to avoid conflicts and ensure optimal performance. |
| System error preventing the activation or proper functioning of Ransomware Protection. | Check for pending Windows updates. Corrupted system files can lead to issues. Run a System File Checker scan (SFC) to identify and repair these issues. If the error persists, consider performing a clean boot to isolate potential conflicts with startup programs. In the event that none of these actions resolves the issue, it may be prudent to contact Microsoft support for further assistance. |
| Ransomware protection fails to detect or block potential threats. | Verify that ransomware protection is enabled and configured correctly. Ensure real-time protection is active. Sometimes, the detection engine needs to be updated. Check for updates and restart the system to ensure the updated components are functional. If the issue persists, run a malware scan with a reputable antivirus program to ensure that no malware is interfering with the protection. |
| Ransomware protection is constantly triggering false positives. | Review the definitions of the detection engine. Verify that legitimate applications or files are not being flagged as threats. Adjust the security settings if necessary, but exercise caution as overly permissive settings can compromise security. Consider updating the definitions and re-scanning your system. If the false positives persist, contact Microsoft support to investigate the issue further. |
Specific Error Messages and Causes
Troubleshooting ransomware protection issues often involves recognizing specific error messages. Understanding the root causes allows for more effective resolution.
- “Ransomware protection service failed to start.” This error often indicates a problem with system services or corrupted files. Rebooting the system and running the System File Checker (SFC) scan can often resolve this issue.
- “Ransomware protection cannot be enabled due to a conflict with other security software.” This message clearly indicates a conflict. Disabling or uninstalling the conflicting software is usually the solution. Ensure compatibility with Windows Defender Ransomware Protection before enabling other security programs.
- “Error code 0xXXXX” Specific error codes often contain clues to the problem. Searching online for the error code along with “Windows Defender” or “Ransomware Protection” will often lead to community forums or support articles detailing potential causes and resolutions. These error codes are crucial for pinpointing the issue.
Best Practices for Ransomware Protection
Robust ransomware protection requires a multi-layered approach that goes beyond simply enabling software. A proactive strategy encompassing user education, software updates, and regular backups is essential to mitigate the risk of infection and data loss. This involves not only technical measures but also a shift in user mindset toward heightened security awareness.Implementing strong security practices is crucial to prevent ransomware attacks.
A proactive and layered approach will significantly reduce the likelihood of successful infiltration. This proactive stance, coupled with user vigilance, builds a stronger overall security posture.
Implementing Multi-Layered Security
A multi-layered approach combines various security controls to create a robust defense against ransomware. This approach involves more than just one solution. Employing multiple layers of security makes it significantly harder for attackers to penetrate your system. This approach strengthens the overall security posture.
- Strong Passwords and Multi-Factor Authentication (MFA): Implementing strong passwords and enabling MFA significantly reduces the risk of unauthorized access. Complex passwords, combined with MFA, make it much more difficult for attackers to gain access to accounts and systems.
- Regular Software Updates: Keeping operating systems and applications up-to-date is critical. Updates often include crucial security patches that address vulnerabilities attackers might exploit. Failing to update software leaves systems exposed to known threats.
- Antivirus and Anti-malware Protection: Reliable antivirus and anti-malware software is essential. Regular scans and real-time monitoring can detect and block malicious software, including ransomware. Without this software, systems remain vulnerable to known threats.
Regular Data Backups
Regular backups are crucial for restoring data in case of a ransomware attack. The importance of backups cannot be overstated. They are the most critical line of defense against data loss from ransomware.
Figuring out how to turn on ransomware protection on Windows 10 is a crucial step for cybersecurity. While basic steps like enabling Windows Defender are important, modern threats require more advanced solutions. For instance, consider the need for proactive code security measures, like those discussed in Deploying AI Code Safety Goggles Needed. Ultimately, strengthening your Windows 10 defenses against evolving ransomware tactics is key to a robust security posture.
- Offline Backups: Storing backups offline safeguards data from infections. Offline backups are crucial in case of an attack. These backups should be stored in a secure location separate from the primary system.
- Regular Backup Schedules: Establish and maintain regular backup schedules. The frequency of backups should be determined based on the criticality of data and the risk tolerance. Regular backups are essential for data recovery.
- Version Control and Recovery Points: Implement version control and recovery points to revert to previous versions of files in case of corruption or accidental deletion. This enables recovery from various data-related issues.
User Education and Awareness
User education is a crucial component of ransomware protection. Users need to understand the risks and how to identify suspicious emails, links, and attachments. Educating users about common tactics used by attackers can greatly reduce the risk of successful attacks.
- Phishing Awareness Training: Regular training programs should be conducted to raise awareness about phishing attacks. Phishing emails often contain malicious links or attachments that can infect systems. Understanding phishing tactics is critical to protecting systems.
- Recognizing Suspicious Files and Links: Users should be trained to recognize suspicious files and links. Malicious files or links can be disguised to look legitimate. This awareness can prevent unintentional infections.
- Reporting Suspicious Activity: Users should be encouraged to report any suspicious activity or emails to the appropriate IT staff. This allows for immediate action and prevents potential infections from spreading.
Maintaining Protection Over Time
Maintaining ransomware protection requires ongoing effort. Ongoing vigilance is essential to keeping systems secure. Regular review and updates of security measures ensure systems remain protected.
- Regular Security Audits: Regular security audits help identify vulnerabilities and weaknesses in security measures. Regular audits ensure systems remain strong.
- Software Updates and Patching: Keep software updated to address security vulnerabilities. This practice ensures that protection systems remain effective. Keeping systems updated is crucial.
- Reviewing and Updating Security Policies: Review and update security policies regularly to reflect evolving threats. Policies should be reviewed and updated as needed.
Examples of User Actions that Might Disable Ransomware Protection
Certain user actions can inadvertently disable ransomware protection.
Figuring out how to turn on ransomware protection on Windows 10 is a crucial step in safeguarding your digital assets. While protecting your data is important, it’s also good to know about legal considerations like the Department of Justice Offers Safe Harbor for MA Transactions, a policy that might affect how you approach certain transactions. Ultimately, taking the time to enable those robust Windows 10 security features is a smart move to keep your digital life secure.
- Disabling Security Software: Disabling security software, such as antivirus or ransomware protection, compromises the system’s defenses. This is a common mistake that can lead to infections.
- Downloading Files from Untrusted Sources: Downloading files from untrusted sources can introduce malicious software, including ransomware. Users should only download from verified sources.
- Clicking on Suspicious Links or Attachments: Clicking on suspicious links or attachments can trigger malicious actions, leading to infections. User vigilance is paramount.
Creating a Comprehensive Security Plan
A comprehensive security plan addresses all aspects of ransomware protection.
- Establish Clear Roles and Responsibilities: Clearly define roles and responsibilities for security measures. This ensures accountability and effective implementation.
- Develop a Detailed Incident Response Plan: Develop a detailed plan to handle ransomware incidents. This plan Artikels steps to take in case of an attack.
- Regular Security Training: Implement regular security training to keep users updated on the latest threats and best practices. Regular training is essential to maintaining a high level of security awareness.
Summary
In conclusion, securing your Windows 10 system against ransomware requires a proactive approach. By following the steps Artikeld in this guide, you’ll equip your system with robust protection. Remember, staying informed about evolving threats and regularly updating your security measures is vital. This guide provides a solid foundation, empowering you to take control of your digital security.
Answers to Common Questions
What is ransomware?
Ransomware is malicious software that encrypts your files, making them inaccessible until a ransom is paid. It can significantly disrupt your work and personal life.
Why is ransomware protection important?
Ransomware protection is essential to prevent data loss and financial harm. It safeguards your valuable files and prevents you from being forced to pay a ransom.
Can I use multiple ransomware protection methods?
Yes, while Windows Defender offers built-in protection, using a third-party solution in addition to Windows Defender can enhance your security posture. This often offers specialized features that Defender might lack.
What if I encounter a ransomware attack despite having protection enabled?
While protection significantly reduces risk, no method is foolproof. If you suspect a ransomware attack, immediately disconnect from the internet and contact a cybersecurity professional for assistance.