Hidden SSID Security 2 Enhanced Network Protection
Hidden SSID security 2 isn’t just about hiding your Wi-Fi name; it’s about understanding the layers of protection (or lack thereof) it provides. This post dives deep into the realities of hiding your SSID, exploring its effectiveness against modern attacks and how it stacks up against other crucial security measures. We’ll cover everything from the simple act of hiding your network name to advanced techniques and best practices, helping you build a truly secure home or office network.
We’ll unpack the misconceptions surrounding hidden SSIDs, revealing how easily they can be bypassed by determined attackers with the right tools. You’ll learn why hiding your SSID is only one small piece of the puzzle and how other security practices like strong passwords, robust encryption, and regular updates are equally – if not more – vital. Prepare to rethink your Wi-Fi security strategy!
Understanding Hidden SSID Security
Hiding your Wi-Fi network’s SSID (Service Set Identifier), the name your network broadcasts, might seem like a strong security measure, but its effectiveness is often overstated. While it adds a small layer of obscurity, it’s crucial to understand its limitations and how it interacts with other security protocols.
Benefits of a Hidden SSID
A hidden SSID makes your network less visible to casual observers. Instead of seeing your network name in the list of available networks, potential attackers won’t immediately know your network exists. This slightly increases the difficulty for opportunistic attackers who might simply connect to the first open network they find. However, it’s important to note that this is a very minor hurdle for a determined attacker.
Vulnerabilities of a Hidden SSID
The primary vulnerability of a hidden SSID is that it’s easily bypassed. Malicious actors can use readily available tools to discover hidden networks. Once the SSID is known, the network is no different from an open network, meaning that all the same security risks still apply. In essence, hiding the SSID only provides a very minimal layer of obfuscation, offering virtually no real security.
It’s like hiding a key under a doormat; it might deter casual passersby, but anyone looking for it will easily find it.
Comparison with Other Security Measures
Strong passwords and robust encryption protocols, such as WPA3, are far more effective security measures than hiding the SSID. WPA3 uses advanced encryption algorithms and security protocols that make it significantly harder for attackers to gain unauthorized access. A strong, unique password is essential to prevent brute-force attacks. Hiding the SSID offers negligible protection compared to these crucial elements.
Think of it this way: a hidden SSID is like locking your front door with a flimsy latch while leaving the windows wide open; the latch offers minimal security, while the open windows completely negate any protection.
Hiding an SSID: A Step-by-Step Guide
The process of hiding your SSID is generally similar across different router brands, but the exact steps and menu locations may vary. The following table provides a general Artikel. Remember to consult your router’s manual for specific instructions.
| Step | Linksys | Netgear | TP-Link | Asus |
|---|---|---|---|---|
| 1. Access Router Settings | Open a web browser and enter the router’s IP address (usually 192.168.1.1 or 192.168.0.1). | Open a web browser and enter the router’s IP address (usually 192.168.1.1 or 192.168.0.1). | Open a web browser and enter the router’s IP address (usually 192.168.1.1 or 192.168.0.1). | Open a web browser and enter the router’s IP address (usually 192.168.1.1 or 192.168.50.1). |
| 2. Find Wireless Settings | Navigate to the Wireless or Wi-Fi settings section. | Navigate to the Wireless or Wi-Fi settings section. | Navigate to the Wireless settings section. | Navigate to the Wireless settings section. |
| 3. Locate SSID Setting | Find the option labeled “SSID” or “Network Name”. | Find the option labeled “SSID” or “Network Name”. | Find the option labeled “SSID” or “Wireless Network Name”. | Find the option labeled “SSID” or “Network Name”. |
| 4. Disable SSID Broadcast | Uncheck the box labeled “Enable SSID Broadcast” or similar. | Uncheck the box labeled “Enable SSID Broadcast” or similar. | Uncheck the box labeled “Enable SSID Broadcast” or similar. | Uncheck the box labeled “Broadcast SSID” or similar. |
| 5. Save Changes | Click “Apply” or “Save” to save the changes. | Click “Apply” or “Save” to save the changes. | Click “Save” to save the changes. | Click “Apply” or “Save” to save the changes. |
The Effectiveness of Hidden SSIDs in Real-World Scenarios: Hidden Ssid Security 2
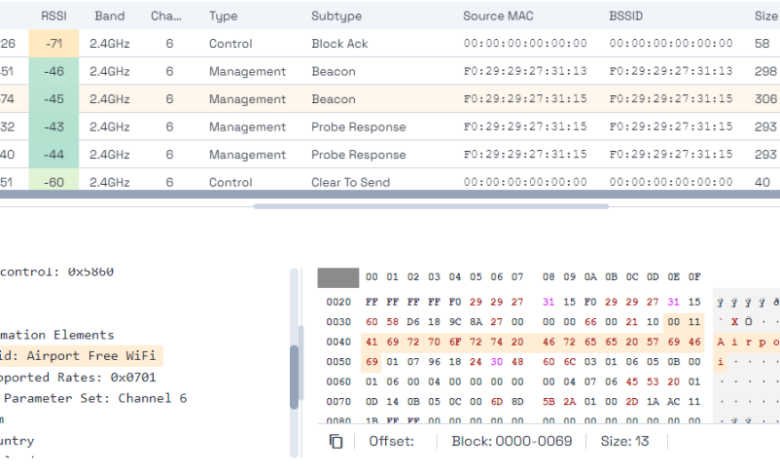
Hiding your SSID might seem like a clever way to boost your Wi-Fi security, but the reality is far more nuanced. While it adds a small layer of obscurity, relying solely on a hidden SSID is like locking your front door but leaving the windows wide open – it offers a false sense of security. Let’s delve into why this is the case.The limitations of a hidden SSID are significant because it doesn’t actually encrypt your data or prevent unauthorized access.
It simply makes the network name invisible to casual observers. A determined attacker can still easily bypass this weak security measure.
Methods of Discovering Hidden SSIDs
Network scanning tools readily reveal hidden SSIDs, negating the intended security benefit. These tools don’t just passively listen for broadcast signals; many actively probe the network, identifying devices and SSIDs, even those configured to be hidden. This active probing technique is much more effective than relying on passive detection of broadcast packets. For example, tools like Aircrack-ng suite and Kismet can easily uncover hidden networks within a short timeframe, effectively rendering the hidden SSID feature useless.
Furthermore, many smartphones and operating systems will automatically detect and list available Wi-Fi networks, regardless of their hidden status, during a standard network scan.
Network Scanning Tools and Their Capabilities
A wide array of readily available tools can detect hidden SSIDs. These tools use various techniques, including sending probe requests to a range of addresses and analyzing the responses. Even free, open-source tools offer this functionality. The sophistication of these tools varies, with some offering advanced features like identifying the type of router, its firmware version, and even potential vulnerabilities.
The ease of use and wide availability of these tools make them a significant threat to the effectiveness of hidden SSIDs as a security measure.
Hypothetical Attack Scenario
Imagine a coffee shop using a hidden SSID for their Wi-Fi. An attacker, equipped with a laptop and a readily available network scanning tool like Nmap, sits within range. They initiate a network scan, and despite the SSID being hidden, the tool quickly identifies the network’s BSSID (Media Access Control address) and other details. The attacker then uses other tools within the Aircrack-ng suite to attempt to crack the WPA2/WPA3 password, a much more significant security concern.
Even if the password is strong, the attacker could potentially exploit vulnerabilities in the router’s firmware or attempt a man-in-the-middle attack, intercepting and potentially manipulating the network traffic. The hidden SSID offered no real protection against this sophisticated attack. The attack’s success stems from the attacker’s use of readily available tools and the inherent weakness of relying solely on SSID hiding as a security mechanism.
The actual vulnerability lies not in the hidden SSID itself, but in the lack of stronger security measures such as robust passwords, up-to-date firmware, and potentially a firewall.
Best Practices for Secure Wi-Fi Networks
Securing your home or office Wi-Fi network is crucial in today’s interconnected world. A poorly secured network leaves your devices and data vulnerable to theft, unauthorized access, and various cyber threats. Implementing strong security measures is essential to protect your privacy and maintain the integrity of your network. This section Artikels best practices for securing your Wi-Fi network, covering password management, encryption protocols, and common router misconfigurations.
Strong passwords and robust encryption protocols are the cornerstones of a secure Wi-Fi network. However, even with these in place, misconfigurations in your router settings can significantly weaken your security posture. Understanding and mitigating these vulnerabilities is paramount for comprehensive network protection.
Best Practices for Wi-Fi Security
Implementing these best practices will significantly improve the security of your wireless network. They cover a range of aspects, from password management to the selection of appropriate encryption protocols and regular updates.
- Use a Strong and Unique Password: Choose a password that is at least 12 characters long, combines uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays or pet names. Consider using a password manager to generate and securely store complex passwords.
- Enable WPA3 Encryption: WPA3 is the latest and most secure Wi-Fi encryption protocol, offering enhanced security features compared to its predecessors. If your router supports it, enable WPA3 immediately.
- Disable WPS (Wi-Fi Protected Setup): WPS is a feature designed for easy network connection, but it’s known to have security vulnerabilities. Disabling it is a crucial step in enhancing your network’s security.
- Regularly Update Your Router Firmware: Router manufacturers regularly release firmware updates that patch security vulnerabilities. Check for updates and install them promptly.
- Enable MAC Address Filtering (Optional): MAC address filtering allows you to restrict access to your network to only devices with specific MAC addresses. While this adds a layer of security, it can be cumbersome to manage, and advanced attackers can bypass it.
- Change the Default Router Admin Password: Most routers ship with default administrator passwords. Changing this to a strong, unique password is essential to prevent unauthorized access to your router’s settings.
Weaknesses in Wi-Fi Security Protocols and Mitigation Strategies
While modern Wi-Fi encryption protocols offer strong protection, they are not immune to vulnerabilities. Understanding these weaknesses and implementing appropriate mitigation strategies is crucial for maintaining a secure network.
WPA2, while widely used, has been shown to be vulnerable to certain attacks, particularly KRACK (Key Reinstallation Attack). The primary mitigation for this is to upgrade to WPA3, which addresses these vulnerabilities. Keeping your router firmware updated is also crucial, as updates often include patches for known vulnerabilities in older protocols.
Common Router Misconfigurations Compromising Security
Even with a hidden SSID and strong encryption, several router misconfigurations can significantly weaken your network’s security. Addressing these issues is essential for comprehensive protection.
- Default Router Settings: Failing to change the default administrator password and other default settings leaves your router vulnerable to attacks.
- Outdated Firmware: Using outdated firmware leaves your router susceptible to known vulnerabilities that have been patched in newer versions.
- Weak or Default SSID: While hiding the SSID provides a small measure of obscurity, using a weak or default SSID name provides little actual security.
- Enabled WPS: As previously mentioned, WPS is a convenient feature, but its vulnerabilities make it a significant security risk.
- Remote Management Enabled Without Proper Security: Enabling remote access to your router without strong authentication and encryption significantly increases the risk of unauthorized access.
Comparison of Wi-Fi Encryption Protocols
Choosing the right encryption protocol is crucial for securing your Wi-Fi network. This table compares the strengths and weaknesses of common protocols.
| Protocol | Strengths | Weaknesses | Recommendation |
|---|---|---|---|
| WPA2 | Widely supported, relatively secure if properly configured. | Vulnerable to KRACK attacks. | Upgrade to WPA3 if possible. Otherwise, ensure firmware is up-to-date. |
| WPA3 | More secure than WPA2, addresses KRACK vulnerabilities, uses stronger encryption. | Newer protocol, not supported by all devices. | Recommended for all new installations and upgrades if device compatibility allows. |
| WEP | Older protocol, widely supported. | Extremely weak and easily cracked. Should never be used. | Never use. |
Advanced Techniques and Considerations
Hiding your SSID is a basic step, but true Wi-Fi security requires a multi-layered approach. This section delves into more advanced techniques and considerations to bolster your network’s defenses beyond simply concealing the network name. Remember, a hidden SSID is only one piece of the puzzle; it doesn’t magically make your network impenetrable.
MAC Address Filtering as a Supplementary Security Measure
MAC address filtering allows you to create a whitelist of devices permitted to connect to your network. By combining this with a hidden SSID, you add another layer of protection. Only devices with MAC addresses explicitly added to the whitelist can connect, even if they know the SSID and password. However, MAC address filtering isn’t foolproof. Determined attackers can spoof MAC addresses, rendering this measure less effective than other, more robust methods.
Therefore, it should be considered a supplementary measure, not a primary security solution. It’s best used in conjunction with strong passwords, WPA3 encryption, and regular firmware updates.
Implications of Using a Hidden SSID in a Business Environment
In a business setting, a hidden SSID presents unique challenges. While it might offer a small degree of obscurity, it significantly complicates guest Wi-Fi access and network administration. Providing secure guest access often requires a captive portal, a landing page that requires users to accept terms of service or log in before gaining network access. Setting up a captive portal with a hidden SSID adds complexity to the configuration.
Furthermore, employees may find it inconvenient to manually connect to a hidden network, potentially leading them to use less secure alternatives. The benefits of a hidden SSID in a business environment are often outweighed by the logistical difficulties and potential security risks arising from hindered access and potential workarounds.
Configuring a Captive Portal for Guest Wi-Fi Access with a Hidden SSID
Creating a secure guest network while maintaining a hidden SSID for your main network requires careful configuration of your router or access point. The process generally involves setting up a separate SSID for guest access (which can be visible), then configuring a captive portal on your router. This portal will redirect guest users to a login page, where they might need to accept terms of service or enter a username and password.
The main network, with its hidden SSID, remains separate and protected. The specific steps vary depending on your router’s model and firmware, but most modern routers offer this functionality through their administrative interface. Consult your router’s documentation for precise instructions. A poorly configured captive portal can present its own security vulnerabilities, so careful configuration is crucial.
Example of a Robust Security Policy for a Home or Small Office Network
A robust security policy should encompass multiple layers of protection. For a home or small office network, this could include: a strong, unique password for the main network (using WPA3 encryption); a hidden SSID for the main network; MAC address filtering (used cautiously as a supplementary measure); a separate, visible SSID for guest access with a captive portal; regular firmware updates for all network devices; a firewall; and strong password policies for all connected devices.
This multi-layered approach provides a significantly more secure network than relying solely on a hidden SSID. Regularly reviewing and updating this policy is crucial to maintain security as threats evolve. Consider enabling features like intrusion detection or prevention if your router supports them.
Visual Representation of Network Security with Hidden SSID
Understanding the security implications of a hidden SSID requires visualizing the data flow and potential vulnerabilities. While hiding the SSID adds a small layer of obscurity, it doesn’t fundamentally enhance security. Let’s examine this through visual representations.
Network with Hidden SSID: Data Flow and Vulnerabilities
Imagine a diagram depicting a typical wireless network with a hidden SSID. We have several nodes: a Wireless Access Point (WAP) – the central device broadcasting the Wi-Fi signal; several client devices (laptops, smartphones, etc.) attempting to connect; and potentially malicious actors (intruders) actively scanning for networks. The WAP, configured with a hidden SSID, doesn’t broadcast its network name.
However, clients who know the SSID can still connect.Data flows between the client devices and the WAP, encrypted using a chosen security protocol (ideally WPA3). The encryption protects the data in transit. However, potential vulnerabilities exist. Malicious actors, even without knowing the SSID, can still discover the network through passive scanning techniques, detecting the beacon frames that the WAP sends out (even if the SSID is hidden, the WAP still transmits beacon frames for clients who already know the SSID).
Once discovered, they can attempt to crack the password through brute-force attacks or exploit vulnerabilities in the encryption protocol. Man-in-the-middle attacks remain a threat, where an attacker intercepts and manipulates the communication between the client and the WAP, even with encryption if the attacker manages to compromise the client device or the WAP’s security.
Comparison: Hidden SSID vs. Visible SSID, Hidden ssid security 2
A comparative diagram would show two networks: one with a visible SSID and another with a hidden SSID. Both diagrams would include the WAP, client devices, and potential attackers.The key difference lies in the network discovery phase. In the visible SSID network, the network name is broadcast, making it easily discoverable by both legitimate clients and malicious actors.
In the hidden SSID network, the network name is not broadcast, requiring clients to manually enter the SSID to connect. This slightly reduces the chance of accidental connection by unauthorized devices. However, the attacker can still use tools to detect the network’s presence, even if the SSID is hidden, through the aforementioned passive scanning methods.Both networks, to be secure, rely heavily on strong passwords and robust encryption protocols (like WPA3).
The actual security posture is almost identical, as both are vulnerable to the same attack vectors. The hidden SSID only offers a small degree of obfuscation, but doesn’t offer any real security advantages over a network with a visible SSID. The stronger security comes from robust password policies, regular firmware updates on the WAP, and the use of strong encryption protocols.
A strong password is far more effective than hiding the SSID.
Closure
So, is hiding your SSID worth it? The answer, as with most security questions, is nuanced. While it adds a small layer of obscurity, it’s far from a silver bullet. True Wi-Fi security relies on a multi-layered approach, combining a strong password, the latest encryption protocols, regular firmware updates, and a healthy dose of awareness. Don’t rely solely on hiding your SSID; instead, build a robust security fortress around your network to protect your data and your peace of mind.
Remember, a truly secure network is a proactive network!
Clarifying Questions
What’s the difference between a hidden SSID and an open SSID?
A hidden SSID doesn’t broadcast its network name, making it less visible to casual searches. An open SSID broadcasts its name, making it easily discoverable. However, neither inherently offers strong security; both require strong passwords and encryption.
Can a hidden SSID prevent all attacks?
No. A hidden SSID only adds a small layer of obscurity. Determined attackers can still discover your network using network scanning tools. Strong passwords and encryption are far more critical.
Is MAC address filtering a good addition to a hidden SSID?
MAC address filtering can add a layer of security, but it’s not foolproof. Attackers can spoof MAC addresses, rendering this method ineffective on its own. It’s best used in conjunction with other security measures.
How often should I update my router’s firmware?
Regularly! Outdated firmware contains vulnerabilities that attackers can exploit. Check your router manufacturer’s website for updates at least every few months.





