HIPAA Electronic Medical Records A Deep Dive
HIPAA electronic medical records (EMRs) are at the heart of modern healthcare, promising efficiency and improved patient care. But this digital revolution brings a whole new set of challenges, from ensuring patient privacy and security to navigating complex regulations and technological hurdles. This post delves into the world of HIPAA and EMRs, exploring the benefits, the risks, and the crucial considerations for both healthcare providers and patients alike.
We’ll uncover the intricacies of compliance, security protocols, and the ethical dilemmas inherent in managing sensitive health information in the digital age. Get ready for a fascinating journey into the digital heart of healthcare!
We’ll unpack the core HIPAA regulations governing EMRs, examining the technical safeguards needed to protect patient data. We’ll also explore the common security threats – from hacking and malware to insider risks – and discuss strategies to mitigate these vulnerabilities. Beyond security, we’ll look at patient rights, the importance of data interoperability, and how EMRs can ultimately enhance the quality and efficiency of healthcare delivery.
Prepare to navigate the complex landscape of HIPAA compliance in the digital age!
HIPAA Compliance in Electronic Medical Records (EMR) Systems

The Health Insurance Portability and Accountability Act of 1996 (HIPAA) established national standards for protecting sensitive patient health information. With the widespread adoption of Electronic Medical Records (EMRs), ensuring HIPAA compliance is paramount to maintaining patient privacy and trust. This discussion will delve into the key aspects of HIPAA compliance within the context of EMR systems.
Core HIPAA Regulations for EMRs, Hipaa electronic medical records
HIPAA’s Privacy Rule dictates how protected health information (PHI) can be used, disclosed, and protected. This includes stipulations on the storage, access, and transmission of electronic PHI within EMR systems. The Security Rule Artikels the technical, administrative, and physical safeguards necessary to protect the confidentiality, integrity, and availability of electronic PHI. The Breach Notification Rule mandates reporting of any unauthorized use or disclosure of PHI.
These rules work in concert to ensure patient data is handled responsibly and securely.
Technical Safeguards Required Under HIPAA for EMR Systems
HIPAA’s Security Rule specifies several technical safeguards for EMR systems. These include access control, which limits who can access specific data based on their role and need-to-know; audit controls, which track user activity and access attempts; integrity controls, which ensure data accuracy and prevent unauthorized alterations; person or entity authentication, which verifies the identity of users before granting access; transmission security, which protects data during electronic transmission using encryption and secure protocols; and data backup and disaster recovery planning, which safeguards against data loss due to system failures or natural disasters.
Failure to implement these safeguards leaves an EMR system vulnerable to breaches and non-compliance.
Examples of HIPAA Violations Related to EMRs and Their Consequences
A common violation involves unauthorized access to patient records. For instance, a staff member accessing a patient’s record without a legitimate reason could result in significant penalties, including fines and legal action. Another example is a failure to properly secure EMR systems against hacking attempts. A successful cyberattack leading to PHI exposure could result in substantial fines, reputational damage, and potential lawsuits from affected patients.
The Office for Civil Rights (OCR) enforces HIPAA and imposes penalties based on the severity and nature of the violation.
Hypothetical EMR System Security Plan Incorporating HIPAA Guidelines
A robust EMR security plan should include comprehensive risk assessments identifying potential vulnerabilities, detailed policies and procedures for user access and data handling, rigorous employee training programs on HIPAA compliance, strong password policies, multi-factor authentication, regular security audits and penetration testing to identify weaknesses, encryption of data both at rest and in transit, and a comprehensive incident response plan to handle security breaches effectively.
The plan should also incorporate regular updates to software and security protocols to address emerging threats. This proactive approach minimizes risks and enhances compliance.
HIPAA Compliance Checklist for Healthcare Providers
Before implementing an EMR system, a thorough risk assessment is crucial. This assessment should identify potential vulnerabilities and guide the selection of appropriate security measures. The checklist should confirm that the system includes robust access controls, audit trails, and encryption. Regular security training for staff is essential to ensure they understand their responsibilities under HIPAA. The system should have a secure backup and disaster recovery plan.
Finally, procedures for handling data breaches should be established and tested regularly. This checklist ensures consistent adherence to HIPAA regulations.
Security Risks Associated with Electronic Medical Records
The digital age has revolutionized healthcare, but the shift to electronic medical records (EMRs) has introduced a new set of security challenges. Protecting patient data, a cornerstone of HIPAA compliance, requires a multifaceted approach to mitigate the ever-evolving threats targeting EMR systems. The consequences of a breach can be devastating, ranging from hefty fines and legal repercussions to irreparable damage to patient trust and the healthcare provider’s reputation.
Common Security Threats to EMR Systems
EMR systems face a range of security threats, each demanding specific countermeasures. Hacking attempts, often sophisticated and targeted, aim to steal sensitive patient information for financial gain or malicious purposes. Malware, including ransomware and viruses, can cripple systems, encrypt data, and disrupt operations, leading to significant downtime and potential data loss. Insider threats, stemming from malicious or negligent employees, represent a significant vulnerability, as they often possess legitimate access to sensitive data.
These threats, along with physical theft of hardware containing EMR data, necessitate robust security protocols.
Vulnerabilities of Different EMR System Architectures
The architecture of an EMR system significantly impacts its vulnerability profile. Cloud-based systems, while offering scalability and accessibility, introduce risks associated with data breaches in the cloud provider’s infrastructure. On-premise systems, while offering greater control, require robust on-site security measures to protect against physical access and internal threats. Hybrid systems, combining cloud and on-premise components, present a unique set of challenges, requiring careful management of data access and security across different environments.
The complexity of each architecture requires a tailored security strategy.
Comparison of Security Measures for Protecting EMR Data
Several security measures are employed to protect EMR data. Firewall protection acts as the first line of defense, preventing unauthorized network access. Intrusion detection and prevention systems monitor network traffic for suspicious activity, alerting administrators to potential threats. Antivirus and antimalware software safeguards systems from malicious code. Data loss prevention (DLP) tools monitor data movement to prevent sensitive information from leaving the network without authorization.
Regular security audits and penetration testing identify vulnerabilities and weaknesses in the system’s defenses. The effectiveness of these measures varies depending on their implementation and integration.
Best Practices for Securing EMR Systems Against Unauthorized Access
Implementing strong access control measures is paramount. This includes robust password policies, multi-factor authentication, and role-based access control, limiting access to data based on an individual’s job responsibilities. Regular security awareness training for staff is crucial to educate employees about phishing scams, social engineering tactics, and other common threats. Maintaining up-to-date software and patching systems promptly mitigates known vulnerabilities.
Data encryption, both in transit and at rest, protects data even if a breach occurs. Regular data backups and disaster recovery planning ensure business continuity in case of system failure or a cyberattack. These practices, when implemented diligently, significantly reduce the risk of unauthorized access.
The Role of Data Encryption and Access Control in HIPAA Compliance
Data encryption and access control are fundamental to HIPAA compliance. Encryption safeguards patient data, rendering it unreadable without the correct decryption key, even if intercepted by unauthorized individuals. Access control mechanisms, limiting access to data based on need-to-know principles, ensure that only authorized personnel can view or modify protected health information (PHI). These measures demonstrate a commitment to protecting patient privacy and meeting the stringent requirements of HIPAA regulations.
Failure to implement these measures can lead to significant penalties and legal ramifications.
Data Privacy and Patient Rights Regarding EMRs
Electronic Medical Records (EMRs) offer significant advantages in healthcare, but they also raise critical concerns about patient data privacy and the protection of individual rights. HIPAA regulations are designed to safeguard this sensitive information, outlining specific rights for patients and responsibilities for healthcare providers regarding the use and disclosure of EMR data. Understanding these rights and responsibilities is crucial for both patients and healthcare professionals to ensure ethical and compliant use of EMR systems.
Patient Rights Concerning Access, Amendment, and Disclosure of EMR Data
Patients have the right to access their own EMR data. This means they can request copies of their medical records, including lab results, diagnoses, treatment plans, and other relevant information. They also possess the right to request amendments to their records if they identify inaccuracies or omissions. This amendment process typically involves submitting a formal request to the provider, who then reviews the request and decides whether to make the changes.
Finally, patients have control over how their EMR data is disclosed, with the ability to restrict or authorize specific disclosures to other healthcare providers, insurers, or other parties. This control is vital in maintaining their privacy and preventing unauthorized dissemination of sensitive medical information.
Obtaining Patient Consent for EMR Data Sharing
Before sharing a patient’s EMR data with other entities, healthcare providers must obtain appropriate consent. This consent must be informed, meaning the patient must understand the purpose of the data sharing, who will receive the data, and how it will be used. Consent can be explicit, where the patient signs a form authorizing the disclosure, or implied, where the context of the situation implies consent.
For example, when a patient seeks care at a specialist’s office, they implicitly consent to the sharing of relevant information with that specialist. However, explicit consent is generally preferred for sensitive disclosures. The method of obtaining consent should be documented within the patient’s EMR.
Ensuring Patient Privacy in EMR Systems
Several measures ensure patient privacy within EMR systems. Strong access controls, including unique usernames and passwords, limit access to authorized personnel only. Data encryption protects data both in transit and at rest, preventing unauthorized access even if the system is compromised. Regular security audits and employee training programs reinforce best practices and identify potential vulnerabilities. Implementing robust audit trails allows for tracking all access to patient data, facilitating investigations into potential breaches.
Finally, adhering to strict HIPAA compliance guidelines ensures that all data handling practices are legal and ethical. For instance, limiting access to specific parts of a patient’s record to only those staff members who have a legitimate need to access that information is a critical component of maintaining privacy.
Patient Rights Under HIPAA and EMR System Support
| Patient Right | HIPAA Regulation | EMR System Support | Example |
|---|---|---|---|
| Access to Records | 45 CFR § 164.524 | Online patient portals, secure email access, printed copies | A patient uses a secure portal to view their lab results. |
| Amendment of Records | 45 CFR § 164.526 | Process for submitting amendment requests, tracking of requests and decisions | A patient requests a correction to a misspelled medication name in their record. |
| Restriction of Disclosure | 45 CFR § 164.528 | Ability to specify restrictions on data sharing within the EMR system | A patient restricts the disclosure of their HIV status to all but their primary care physician. |
| Accounting of Disclosures | 45 CFR § 164.528 | EMR systems track and log all disclosures of patient data | A patient requests a list of all entities that have accessed their records in the past year. |
Facilitating Patient Access to Health Information Through EMR Systems
EMR systems significantly improve patient access to their health information. Many EMR systems now incorporate patient portals, allowing patients to securely access their records online, view lab results, schedule appointments, and communicate with their providers. These portals offer a convenient and user-friendly way for patients to manage their health information. Some systems also allow patients to download their records in a portable format, enabling them to easily share their information with other healthcare providers.
This empowerment improves patient engagement in their care and promotes better health outcomes. For example, a patient using a portal might discover an error in their medication list and quickly contact their doctor to rectify the mistake.
Interoperability and Data Exchange in EMR Systems
The ability of different electronic medical record (EMR) systems to seamlessly share information is crucial for efficient and effective healthcare delivery. Interoperability, however, remains a significant challenge, hindering the flow of patient data between various healthcare providers and organizations. This lack of seamless data exchange can lead to fragmented care, duplicated tests, medication errors, and ultimately, poorer patient outcomes.
This section explores the challenges, standards, and methods used to improve interoperability in EMR systems.
Challenges of Interoperability Between EMR Systems
Different EMR systems often employ disparate data formats, architectures, and terminologies. This “data silos” problem makes it difficult to directly exchange information. Furthermore, legacy systems, often lacking the capacity for modern data exchange protocols, represent a considerable hurdle. The lack of standardized data fields and coding systems also contributes to significant interoperability issues. Finally, concerns about data security and privacy necessitate robust security measures that can sometimes complicate data exchange processes.
For example, a hospital using an older EMR system might struggle to share patient information with a clinic using a newer, cloud-based system due to incompatible data structures and security protocols.
Standards and Technologies for Data Exchange
Several standards and technologies aim to improve interoperability. Health Level Seven International (HL7) has long been a prominent standard, defining a set of messaging protocols and data formats for healthcare information exchange. More recently, Fast Healthcare Interoperability Resources (FHIR) has emerged as a key player. FHIR utilizes a RESTful API approach, offering greater flexibility and ease of integration compared to traditional HL7 messaging.
Other relevant technologies include DICOM (Digital Imaging and Communications in Medicine) for medical image exchange and XDS (Cross-Enterprise Document Sharing) for document sharing. The adoption of these standards is crucial for creating a more interconnected healthcare system. A real-world example is the use of FHIR APIs to enable patients to access their own medical records from different providers through a single portal.
Benefits and Drawbacks of Different Data Exchange Methods
Direct data exchange, where systems communicate directly, offers speed and efficiency. However, it can be complex to implement and maintain, requiring extensive customization for each system pairing. On the other hand, indirect exchange, using a central intermediary such as a health information exchange (HIE), provides scalability and simplifies the technical complexity. However, this method can introduce latency and potential security vulnerabilities if the HIE isn’t properly secured.
The choice between direct and indirect exchange depends on factors like the size and complexity of the healthcare network and the level of security required. A smaller clinic might find direct exchange with a nearby hospital more practical, while a large hospital system might benefit from an HIE for managing data exchange with multiple affiliated facilities.
Data Exchange Approaches for Different Healthcare Settings
Hospitals often utilize complex, integrated EMR systems capable of handling large volumes of data and diverse functionalities. Data exchange within a hospital typically relies on direct connections between different hospital departments. Clinics, however, may use simpler EMR systems, and data exchange often involves interactions with external entities like hospitals and laboratories, frequently relying on HL7 messaging or HIEs.
Smaller practices might even rely on manual data entry or faxing, highlighting the need for improved interoperability solutions tailored to the specific needs and capabilities of different settings. The scale of data exchange and the complexity of the systems involved vary greatly depending on the size and type of the healthcare setting.
Workflow for Secure Data Exchange Between Two Different EMR Systems
Consider two EMR systems, System A and System B, needing to exchange patient data securely. A workflow might involve the following steps: 1) Authentication and Authorization: System A authenticates the request from System B using secure protocols like TLS/SSL. 2) Data Transformation: System A transforms the data into a standardized format (e.g., FHIR) compatible with System B.
3) Secure Transmission: The transformed data is transmitted via a secure channel (e.g., encrypted HTTPS). 4) Data Validation: System B validates the received data against its own data schema and security policies. 5) Data Integration: System B integrates the received data into its own database. 6) Audit Trail: The entire process is logged in an audit trail for compliance and security monitoring.
This workflow emphasizes the importance of security and standardization throughout the exchange process. The use of secure messaging protocols and data encryption is paramount to protect patient privacy and comply with HIPAA regulations.
The Role of EMRs in Improving Healthcare Quality and Efficiency
Electronic Medical Records (EMRs) have revolutionized healthcare, moving beyond simple digital record-keeping to become powerful tools for improving both the quality of patient care and the efficiency of healthcare systems. Their impact spans from enhancing individual patient experiences to facilitating broader population health management initiatives. This section will explore the multifaceted ways EMRs contribute to a more effective and higher-quality healthcare landscape.
EMRs fundamentally change how healthcare professionals access and utilize patient information. The immediate availability of comprehensive medical histories, lab results, imaging studies, and medication lists eliminates the delays and potential errors associated with paper-based systems. This improved access leads to better-informed clinical decisions, reduced diagnostic errors, and ultimately, improved patient outcomes.
Improved Patient Care Through Better Access to Information
The instantaneous access to complete patient data allows for more informed and timely interventions. For example, an allergist can quickly review a patient’s complete medication history to avoid prescribing a drug that might trigger a reaction. Similarly, a physician in an emergency room can instantly see a patient’s past medical history, including allergies, current medications, and previous hospitalizations, leading to quicker and more appropriate treatment.
This speed and accuracy are crucial in time-sensitive situations. The ability to easily share information between healthcare providers also improves care coordination, especially for patients with complex conditions who see multiple specialists.
More Efficient Workflows and Reduced Administrative Burden
EMRs streamline administrative tasks significantly. Automated appointment scheduling, electronic prescription ordering, and integrated billing systems reduce the time spent on paperwork and manual data entry. This frees up valuable time for clinicians to focus on direct patient care. For instance, the elimination of manual chart reviews saves countless hours, allowing physicians to spend more time with patients and less time shuffling paper.
Furthermore, the reduction in administrative errors, such as missed appointments or medication discrepancies, leads to cost savings and improved patient satisfaction.
Positive Impact of EMRs on Healthcare Outcomes: Case Studies
Several studies have demonstrated the positive impact of EMRs on various healthcare outcomes. One study showed a significant reduction in hospital readmission rates among patients with heart failure after the implementation of an EMR system with robust care coordination features. The EMR facilitated better communication between the hospital and primary care physicians, leading to more effective follow-up care and a decrease in readmissions.
Another example involves improved diabetes management. EMRs allow for automated reminders for patients regarding blood sugar monitoring and follow-up appointments, leading to better glycemic control and reduced complications. The consistent data collection and analysis facilitated by EMRs also allow for better identification of at-risk patients, enabling proactive interventions.
EMR Data for Population Health Management and Public Health Surveillance
The aggregated data from EMRs across a healthcare system or even a region provides valuable insights for population health management and public health surveillance. For example, analyzing EMR data can identify trends in disease prevalence, allowing public health officials to target interventions effectively. This data can also be used to monitor the effectiveness of public health programs and to identify areas where resources need to be allocated.
The ability to track vaccination rates, monitor outbreaks of infectious diseases, and identify high-risk populations for chronic diseases are all critical applications of EMR data for improving community health.
Key Advantages of Using EMRs in a Healthcare Setting
The benefits of EMRs are numerous and far-reaching. The following points summarize the key advantages:
- Improved patient care through better access to information.
- Enhanced care coordination and communication between providers.
- More efficient workflows and reduced administrative burden.
- Reduced medical errors and improved patient safety.
- Improved medication management and reduced adverse drug events.
- Better disease management and prevention through proactive interventions.
- Facilitated population health management and public health surveillance.
- Increased efficiency and cost savings for healthcare systems.
- Enhanced data security and compliance with regulations like HIPAA.
Legal and Ethical Considerations of EMR Use
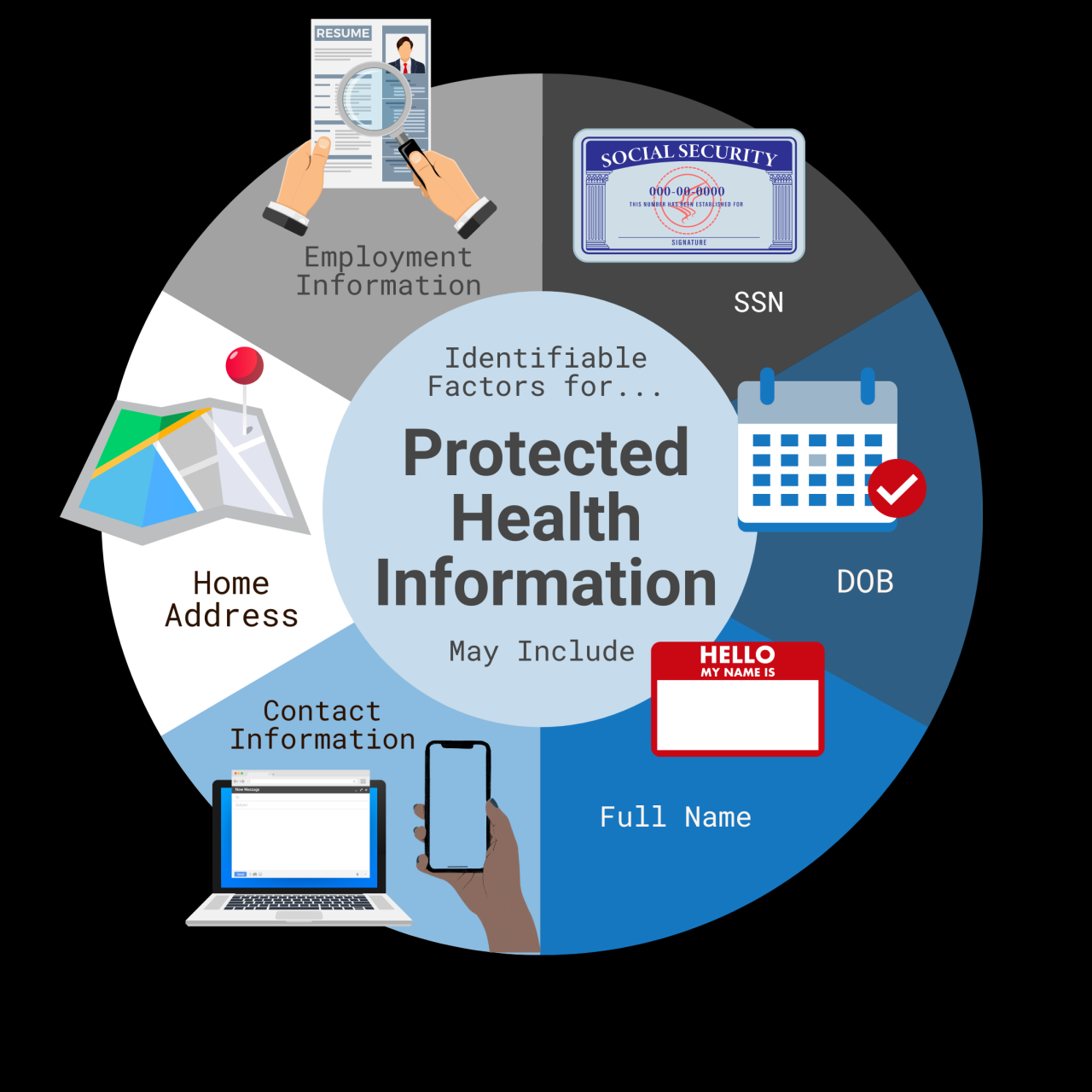
The widespread adoption of Electronic Medical Records (EMRs) has revolutionized healthcare, but it also presents complex legal and ethical challenges. Balancing the benefits of efficient data management with the crucial need for patient privacy and data security requires careful consideration of various factors, including research practices, data lifecycle management, potential biases, and the responsible use of sensitive information.
Ethical Implications of Using Patient Data for Research
Using patient data for research offers immense potential for advancing medical knowledge and improving patient care. However, this practice raises significant ethical concerns. Researchers must obtain informed consent from patients, ensuring they understand the purpose of the research, how their data will be used, and the potential risks and benefits involved. Anonymization and de-identification techniques are crucial to protect patient privacy, although perfect anonymity is often difficult to guarantee.
Data security measures must be robust to prevent unauthorized access and breaches. Furthermore, researchers must address potential conflicts of interest and ensure the equitable distribution of research benefits. Institutional Review Boards (IRBs) play a vital role in overseeing research involving human subjects, ensuring adherence to ethical guidelines and regulations.
Legal Requirements for Data Retention and Disposal in EMR Systems
Legal frameworks governing data retention and disposal in EMR systems vary by jurisdiction but generally emphasize the need for secure storage and proper disposal of patient data. Regulations often specify minimum retention periods, dictated by factors such as statute of limitations for medical malpractice claims and requirements for insurance billing. Data disposal must adhere to strict protocols, often involving secure deletion or destruction methods to prevent unauthorized access or data recovery.
Failure to comply with these regulations can result in significant legal penalties, including fines and legal action. Healthcare organizations must establish comprehensive data lifecycle management policies that align with both legal and ethical standards.
Potential for Bias and Discrimination in the Use of EMR Data
EMR data, while valuable for improving healthcare, can reflect and perpetuate existing biases and inequalities within the healthcare system. For example, algorithms used for risk prediction or treatment recommendations may inadvertently discriminate against certain demographic groups if the data used to train these algorithms contains biases. This can lead to disparities in access to care and quality of treatment.
Addressing this requires careful attention to data quality, algorithm design, and ongoing monitoring for bias in the outcomes generated by EMR-based systems. Transparency and accountability in the development and deployment of these systems are essential to mitigate the risk of discriminatory practices.
Best Practices for Ensuring the Ethical and Responsible Use of EMR Data
Implementing robust data governance frameworks is crucial for responsible EMR data use. This involves establishing clear policies and procedures for data access, use, and sharing; implementing strong security measures to protect patient privacy; and providing regular training to healthcare professionals on data privacy and security best practices. Data minimization, using only the necessary data for a specific purpose, is key.
Regular audits and assessments of data security and compliance are essential to identify and address vulnerabilities. Transparency and accountability mechanisms are necessary to build trust and ensure the ethical use of EMR data. Collaboration with ethicists and legal experts can guide the development and implementation of responsible data practices.
Ethical Dilemma Scenario: Genetic Information and Family History
Imagine a scenario where a patient’s EMR reveals a strong family history of a genetic condition, but the patient themselves has not been tested and is unaware of their risk. A physician treating the patient for an unrelated condition notices this information. The ethical dilemma lies in whether the physician should disclose this information to the patient, potentially causing anxiety and concern, without the patient explicitly requesting it or having undergone genetic testing.
The conflict arises between the physician’s duty to beneficence (acting in the patient’s best interest) and the patient’s right to autonomy (self-determination). Potential resolutions could involve a careful discussion with the patient about their family history and the implications, offering genetic counseling, or respecting the patient’s right to not know, while carefully documenting the discovered information in the EMR.
End of Discussion
Navigating the world of HIPAA and electronic medical records requires a careful balance of technological expertise, legal understanding, and ethical considerations. While EMRs offer significant advantages in improving healthcare quality and efficiency, the potential risks to patient privacy and data security cannot be overlooked. By understanding the regulations, implementing robust security measures, and prioritizing patient rights, we can harness the power of EMRs while safeguarding the sensitive information they contain.
This journey into the intricacies of HIPAA and EMRs highlights the ongoing need for vigilance, adaptation, and a commitment to ethical practices in the digital healthcare landscape. Let’s continue the conversation and work together to ensure a secure and ethical future for electronic health information.
Helpful Answers: Hipaa Electronic Medical Records
What happens if a HIPAA violation occurs involving EMRs?
Penalties can range from significant fines to legal action, depending on the severity and nature of the violation. The Office for Civil Rights (OCR) investigates violations and determines appropriate sanctions.
Can patients access their own EMRs?
Yes, under HIPAA, patients have the right to access, review, and obtain copies of their medical records. The process for obtaining this access varies depending on the healthcare provider.
How long must EMR data be retained?
Retention periods vary depending on state and federal laws, as well as the specific type of data. Consult legal counsel for specific requirements.
What is the role of cloud computing in HIPAA-compliant EMRs?
Cloud-based EMRs can offer scalability and cost-effectiveness, but require stringent security measures to ensure HIPAA compliance, including data encryption and access controls.