Honeypots in Cybersecurity A Deceptive Defense
Honeypots in cybersecurity a deceptive defense – Honeypots in cybersecurity: a deceptive defense, these alluring traps are deceptively simple yet powerfully effective. They lure attackers away from valuable systems, providing invaluable insights into their tactics and techniques. Imagine a digital decoy, attracting malicious actors like moths to a flame, allowing security professionals to study their behavior and improve defenses. This exploration delves into the fascinating world of honeypots, from their humble beginnings to their sophisticated modern applications in thwarting cyber threats.
We’ll cover the various types of honeypots, from low-interaction decoys to high-interaction, immersive environments. We’ll examine deployment strategies, attack detection methods, and the crucial process of analyzing the data gathered from these digital traps. We’ll also discuss the ethical and legal considerations surrounding their use, ensuring responsible and effective implementation. Finally, we’ll look at advanced techniques, including virtualization and cloud-based honeypots, and how they’re used to combat the ever-evolving landscape of cyber threats.
Introduction to Honeypots
Honeypots are deceptive cybersecurity traps designed to lure and capture attackers, providing valuable insights into their tactics, techniques, and procedures (TTPs). They act as decoys, mimicking real systems or applications, tempting malicious actors to interact with them instead of genuine targets. By analyzing attacker behavior within the honeypot environment, security professionals can gain crucial intelligence, improve their defenses, and proactively address emerging threats.Honeypots are a crucial part of a layered security strategy, offering a proactive approach to threat detection and analysis.
They don’t replace traditional security measures like firewalls and intrusion detection systems (IDS), but rather supplement them, providing a deeper understanding of attacker motivations and capabilities. The information gathered from honeypots can significantly enhance incident response capabilities and inform the development of more effective security controls.
Types of Honeypots
Honeypots are broadly categorized based on their level of interaction with attackers. Low-interaction honeypots, also known as “low-interaction honeypots” or “static honeypots,” mimic the appearance of a system or application but offer limited functionality. They primarily focus on detecting intrusion attempts and gathering basic information about attackers. Their advantage lies in their ease of deployment and maintenance, making them suitable for organizations with limited resources.
However, they provide less detailed information about attacker behavior compared to high-interaction honeypots. High-interaction honeypots, also known as “high-interaction honeypots” or “dynamic honeypots,” offer a more realistic and interactive environment, allowing attackers to explore the system more extensively. This provides more detailed information about their activities and techniques. However, they require more resources to manage and maintain, posing a greater risk if compromised.
A middle ground exists with medium-interaction honeypots, offering a balance between the two extremes.
Historical Overview of Honeypot Usage
The concept of honeypots emerged in the early days of computing, with early examples appearing in the 1980s and 1990s. These initial honeypots were largely rudimentary, often consisting of simple systems with limited functionality. Significant advancements occurred with the development of more sophisticated honeypot technologies, including the introduction of virtual honeypots and the use of virtualization to create scalable and easily managed honeypot environments.
The rise of cloud computing has further accelerated the adoption of honeypots, with cloud-based honeypot services becoming increasingly prevalent. Furthermore, the development of automated honeypot management tools has significantly reduced the operational overhead associated with deploying and maintaining these systems. The continuous evolution of honeypots reflects the ongoing arms race between attackers and defenders in the cybersecurity landscape.
For instance, the use of honeytokens within larger systems allows for the detection of attacks on specific files or applications.
Honeypot Deployment Strategies

Deploying honeypots effectively requires careful planning and execution. Success hinges on seamlessly integrating the honeypot into your network architecture without compromising its deceptive nature. A poorly deployed honeypot can be easily detected and rendered useless, or worse, become a liability. Careful consideration of placement, camouflage, and the type of honeypot are all crucial factors.Deploying a honeypot involves strategically placing a seemingly vulnerable system within your network to attract and trap malicious actors.
The key is to make it appear as an attractive target while remaining completely under your control. This allows you to observe attacker techniques, gather intelligence, and potentially even identify vulnerabilities in your actual systems by observing how attackers try to exploit the honeypot. The level of interaction (low, medium, or high) significantly influences deployment and management complexity.
Honeypot Camouflage and Network Integration
Successful honeypot deployment relies heavily on camouflage and seamless integration within the existing network architecture. Attackers should not be able to distinguish the honeypot from legitimate systems. This requires careful configuration of network services, operating system settings, and even the data presented to the attacker. For instance, a honeypot mimicking a web server should respond with realistic web pages and potentially even include fake vulnerabilities to further enhance its believability.
Poor camouflage can lead to the honeypot being quickly identified and ignored. Integration should involve appropriate routing, firewall rules, and network monitoring to ensure the honeypot interacts with the network in a way that doesn’t raise suspicion.
Honeypot Deployment Locations
The location of a honeypot within the network significantly impacts its effectiveness and the type of information gathered. Perimeter honeypots, placed at the edge of the network, are designed to detect external attacks and gather information about initial reconnaissance techniques. Internal honeypots, placed within the network, can provide insights into lateral movement and the techniques attackers use once they’ve gained initial access.
The choice of location depends on the specific security goals. A perimeter honeypot might be ideal for detecting initial scanning activity, while an internal honeypot might be more effective at capturing data exfiltration attempts. Consider deploying multiple honeypots in various locations to obtain a comprehensive view of attacker behavior.
Setting Up a Low-Interaction Honeypot
Low-interaction honeypots are relatively simple to set up and maintain, making them a good starting point for organizations new to honeypot deployment. They present a minimal attack surface, typically offering only a limited set of services. This reduces the risk of compromise and the administrative overhead.
| Step | Action | Considerations | Expected Outcome |
|---|---|---|---|
| 1 | Choose a suitable operating system image (e.g., a minimal Linux distribution). | Select a distribution known for security and stability. Consider an older, less patched version to mimic a vulnerable system (with appropriate ethical considerations). | A clean, minimal OS image ready for configuration. |
| 2 | Install necessary services (e.g., SSH, HTTP). | Only install services that you intend to use as part of the honeypot’s deception. | Selected services running and listening on configured ports. |
| 3 | Configure network settings (IP address, subnet mask, gateway). | Assign a static IP address outside of the main network range. | Honeypot reachable via its assigned IP address. |
| 4 | Configure firewall rules to allow only necessary traffic. | Restrict access to only the services running on the honeypot. | Only authorized traffic can reach the honeypot. |
| 5 | Install and configure honeypot monitoring software (e.g., Kippo, Cowrie). | Choose software that meets your specific needs and integrates with your existing security infrastructure. | Honeypot activity logged and monitored. |
| 6 | Regularly review and analyze honeypot logs. | Identify potential threats and adjust honeypot configuration as needed. | Improved security posture and valuable threat intelligence. |
Types of Honeypot Attacks and Detection: Honeypots In Cybersecurity A Deceptive Defense
Honeypots, while effective defensive tools, inevitably attract a range of attacks. Understanding the common attack vectors and developing robust detection methods are crucial for maximizing their effectiveness. This section delves into the types of attacks honeypots face, the techniques used to detect them, and real-world examples illustrating their value.Honeypots are designed to mimic real systems, making them attractive targets for various malicious activities.
The attacks range from simple probes to sophisticated, multi-stage intrusions. Effective detection relies on a combination of real-time monitoring, log analysis, and anomaly detection. By analyzing the attack methods, security professionals can gain valuable insights into attacker tactics, techniques, and procedures (TTPs), informing broader security strategies.
Common Honeypot Attack Vectors
The attractiveness of honeypots stems from their appearance as vulnerable systems. Attackers use various methods to probe and exploit them. Common attack vectors include port scanning, vulnerability scanning, brute-force attacks, malware injections, and social engineering attempts. For example, a low-interaction honeypot might attract numerous port scans as attackers try to identify open ports. A high-interaction honeypot, designed to mimic a specific application, might be targeted with sophisticated exploits targeting known vulnerabilities in that application.
Honeypot Attack Detection Methods
Detecting attacks on honeypots involves continuous monitoring and analysis of system logs and network traffic. System logs provide crucial information about login attempts, file access, and command execution. Network traffic analysis helps identify suspicious connections and data transfers. Anomaly detection systems can identify unusual patterns in network traffic or system behavior, alerting administrators to potential attacks. For example, a sudden spike in login attempts from a single IP address might indicate a brute-force attack.
Unusual file access patterns could suggest malware deployment.
Examples of Successful Honeypot Deployments
Numerous organizations have successfully used honeypots to detect and thwart cyberattacks. While specific details are often kept confidential for security reasons, publicly available information highlights their effectiveness. For instance, several reports detail how honeypots have helped organizations identify advanced persistent threats (APTs) by attracting attackers and providing valuable intelligence on their methods. This intelligence can then be used to improve overall security posture and enhance defenses against similar attacks on the organization’s actual systems.
Hypothetical Honeypot Scenario: Detecting a SQL Injection Attack
Imagine a honeypot designed to mimic a vulnerable web application with a poorly secured database connection. This honeypot contains a simple login form that interacts with a database. The honeypot’s database is specifically designed to record all queries, including those that attempt SQL injection. An attacker attempts a SQL injection attack by entering malicious code into the login form’s username field, such as ' OR '1'='1.
The honeypot’s database logs this query, alerting administrators to the attack attempt. The honeypot then might trigger additional responses, such as presenting a seemingly successful login while recording the attacker’s IP address and the malicious SQL query for further analysis and security improvements. The recorded information can be used to identify the attacker’s techniques, potentially revealing patterns and aiding in the development of more robust security measures for the organization’s production systems.
Honeypot Data Analysis and Reporting
Analyzing data from honeypots is crucial for understanding attacker behavior and improving your overall security posture. The wealth of information gathered provides invaluable threat intelligence that can be used to strengthen defenses and proactively mitigate future attacks. Without proper analysis, however, the honeypot remains a passive data collector, failing to fulfill its potential.Effective honeypot data analysis involves meticulous log examination and insightful interpretation.
This process transforms raw log entries into actionable intelligence, highlighting attack vectors, techniques, and tools used by malicious actors. By understanding these patterns, security teams can refine their detection systems, bolster their defenses against similar attacks, and even develop countermeasures tailored to specific threats.
Log Analysis and Data Interpretation
Honeypot logs are rich sources of information detailing attacker interactions. Careful analysis of these logs reveals attacker techniques, tools, and targets. This includes identifying the source IP addresses, the types of attacks attempted (e.g., brute-force login attempts, SQL injection, malware delivery), the specific tools or exploits used, and the timestamps of the events. Analyzing this data helps identify trends, such as peak attack times or favored attack methods, which inform defensive strategies.
For example, a surge in brute-force attacks during specific hours might indicate the need for stronger password policies and rate limiting measures.
Extracting Threat Intelligence from Honeypot Data
Honeypot data is a goldmine for threat intelligence. By analyzing attack patterns, we can identify emerging threats, understand attacker motivations, and predict future attacks. For instance, if a honeypot consistently detects attempts to exploit a specific vulnerability, this signals a potential widespread threat that needs immediate attention. Furthermore, correlating honeypot data with other security logs (e.g., firewall logs, intrusion detection system logs) can provide a more comprehensive understanding of the attack landscape and help pinpoint the source of attacks.
This holistic approach allows for better informed decision-making regarding security resource allocation and prioritization.
Sample Honeypot Log File Report
Consider a simplified honeypot log file containing the following entries:* Entry 1: 2024-10-26 10:00:00 – 192.168.1.100 – Brute-force SSH login attempt
Honeypots, those deceptive traps in cybersecurity, are a fascinating example of proactive defense. Building robust systems, like those discussed in this great article on domino app dev the low code and pro code future , requires similar forethought. Understanding vulnerabilities, whether in application design or network security, is key to effective protection; honeypots help us understand attacker behavior and refine our defenses accordingly.
Entry 2
2024-10-26 10:05:00 – 10.0.0.5 – Successful FTP login
Entry 3
2024-10-27 14:30:00 – 192.168.1.100 – Port scan
Entry 4
2024-10-28 09:15:00 – 172.16.0.1 – SQL injection attempt
Entry 5
2024-10-29 16:45:00 – 192.168.1.100 – Failed web application login attemptThis data can be organized into a report as follows:* Attacker IP Addresses: 192.168.1.100, 10.0.0.5, 172.16.0.1
Attack Types
Brute-force SSH, Successful FTP login, Port scan, SQL injection, Failed web application login
Frequency
192.168.1.100 shows multiple attempts, indicating persistent activity.
Timeline
Attacks occurred over a period of four days.
Conclusion
IP 192.168.1.100 requires further investigation due to multiple attempts. A variety of attack vectors were used.
Visual Representation of Honeypot Activity, Honeypots in cybersecurity a deceptive defense
Imagine a bar chart visualizing honeypot activity over a month. The x-axis represents the days of the month, and the y-axis represents the number of attacks. Each bar is segmented to represent different attack types (e.g., brute-force, SQL injection, port scan). The height of each segment indicates the number of attacks of that type on that day.
For example, a tall, segmented bar for October 26th might show a large number of brute-force attacks, a smaller number of port scans, and zero SQL injections. A legend would clearly identify each color representing a specific attack type. This visualization quickly highlights attack frequency, the prevalence of various attack types, and potential trends over time. The chart would clearly show peaks in attack frequency and the dominant attack types for the month.
Ethical and Legal Considerations
Deploying honeypots, while offering significant security benefits, raises complex ethical and legal questions. The very nature of a honeypot – attracting and potentially trapping malicious actors – necessitates careful consideration of the data collected and its potential misuse. Balancing the need for proactive security with the rights and privacy of individuals is crucial.The ethical implications revolve primarily around informed consent and data privacy.
While attackers are generally not considered to have any expectation of privacy, the honeypot operator still needs to handle the collected data responsibly. This includes adhering to relevant data protection regulations, anonymizing data where possible, and limiting data collection to what is strictly necessary for security purposes. Furthermore, the potential for entrapment needs to be carefully considered; a honeypot should not be used to deliberately lure individuals into committing crimes they wouldn’t otherwise have considered.
Data Privacy and Informed Consent
The collection of data from attackers via honeypots must comply with data protection laws such as GDPR (in Europe) and CCPA (in California). This means obtaining consent (where applicable) and ensuring the data is processed lawfully, fairly, and transparently. The type of data collected should be limited to what is necessary and proportionate to the security objective. For instance, collecting personally identifiable information (PII) should be avoided unless absolutely essential for investigations.
Data minimization and anonymization techniques are vital to reduce the risk of privacy violations.
Legal Liability and Potential for Misuse
Deploying a honeypot improperly can expose the organization to legal liability. For example, if a honeypot is configured to trigger automated responses that could be considered harmful or illegal (such as sending malicious code back to the attacker), the organization could face legal repercussions. Similarly, if the honeypot data is mishandled or leaked, leading to privacy violations, the organization could face fines and lawsuits.
Furthermore, using honeypots to collect data beyond the scope of legitimate security investigations could lead to legal challenges.
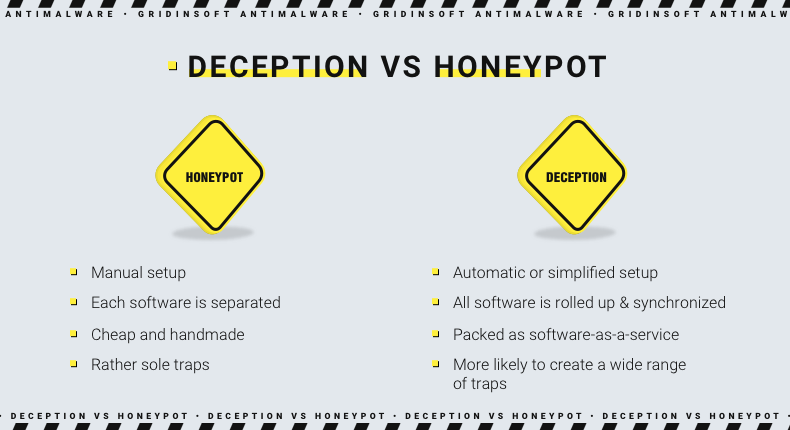
Honeypots Compared to Intrusion Detection Systems (IDS)
Both honeypots and intrusion detection systems (IDS) are valuable security tools, but they operate differently. An IDS passively monitors network traffic for suspicious activity, generating alerts when anomalies are detected. Honeypots, on the other hand, actively engage attackers, providing detailed information about their techniques and tools. While an IDS provides a broad overview of network security, a honeypot offers deep insights into specific attacks.
The choice between using honeypots or IDS depends on the specific security needs and resources available. Often, a combination of both approaches provides the most comprehensive security posture.
Examples of Legally Questionable Honeypot Deployments
Deploying a honeypot that mimics a critical infrastructure system and intentionally lures attackers into causing significant damage could be legally problematic. Similarly, using a honeypot to gather intelligence beyond legitimate security purposes, such as collecting data for commercial purposes or for law enforcement without proper warrants, would be considered a violation of privacy and potentially illegal. Another example would be deploying a honeypot that traps individuals into committing crimes they might not have otherwise considered, effectively constituting entrapment.
In all these scenarios, the legal ramifications could be severe.
Advanced Honeypot Techniques
Deploying effective honeypots in today’s complex threat landscape requires leveraging advanced techniques to enhance their realism and detection capabilities. This involves careful consideration of the underlying infrastructure, the type of honeypot deployed, and the specific threats being targeted. Moving beyond simple, low-interaction honeypots opens up a world of possibilities for sophisticated threat hunting and analysis.Virtualization and cloud-based environments have revolutionized honeypot deployment, offering scalability, flexibility, and ease of management previously unavailable.
The choice of virtualization technology significantly impacts the honeypot’s effectiveness and resource consumption.
Virtualization Technologies for Honeypots
The selection of a virtualization technology for honeypot deployment is crucial. Different hypervisors offer varying levels of performance, security, and resource management. For example, using VMware vSphere provides robust features like resource allocation and snapshotting, ideal for managing multiple honeypots and quickly restoring them after compromise. Alternatively, KVM (Kernel-based Virtual Machine) offers a lightweight, open-source solution well-suited for resource-constrained environments.
However, KVM may require more manual configuration compared to commercial solutions. The choice depends on the specific needs and resources available. A comparison of these technologies reveals trade-offs between ease of use, performance, and cost.
Low-Interaction vs. High-Interaction Honeypots for Advanced Persistent Threats (APTs)
Low-interaction honeypots, which present a limited attack surface, are effective at detecting basic reconnaissance and scanning activities. However, they often fail to capture the nuances of sophisticated attacks employed by APTs. High-interaction honeypots, offering a more realistic environment, can lure attackers deeper, revealing more advanced tactics and techniques. The increased interaction, however, also presents a higher risk of compromise and requires more careful monitoring and management.
In the case of APT detection, high-interaction honeypots, while riskier, offer a significantly greater chance of observing complex attack sequences and data exfiltration attempts. For example, a high-interaction honeypot mimicking a critical database server might reveal an APT’s attempts to bypass security controls and gain persistent access.
Designing Honeypots to Mimic Specific Server Types
Creating realistic honeypots requires meticulous design to accurately mimic the target system. A honeypot designed to emulate a web server, for instance, would need to respond to HTTP requests, present realistic web pages, and potentially even include vulnerable applications (carefully controlled, of course). Similarly, a database server honeypot would need to emulate the functionality of a specific database system (e.g., MySQL, PostgreSQL), responding to connection attempts and SQL queries.
The level of detail and complexity directly impacts the effectiveness of the honeypot in attracting and engaging attackers. Failure to accurately mimic the target system can lead to attackers quickly identifying the honeypot and abandoning the attack. A poorly designed honeypot might inadvertently reveal its artificial nature through inconsistencies in its responses or behavior.
Wrap-Up
Honeypots, while seemingly simple in concept, offer a surprisingly potent layer of defense in the complex world of cybersecurity. By actively attracting and analyzing attacker behavior, they provide unparalleled threat intelligence, enabling proactive security measures and a deeper understanding of the ever-shifting landscape of cyberattacks. While ethical and legal considerations are paramount, the strategic deployment of honeypots can significantly enhance an organization’s overall security posture, transforming a reactive approach to a more proactive and informed defense strategy.
The future of cybersecurity is undoubtedly intertwined with the clever and evolving use of these digital decoys.
FAQ Guide
What are the risks of deploying honeypots?
Improperly configured honeypots can expose vulnerabilities within your network if compromised. They also require careful monitoring and analysis to prevent false positives and ensure compliance with relevant regulations.
Can honeypots be used for legal purposes?
Yes, but careful consideration of local laws and ethical guidelines is crucial. Documenting everything and obtaining appropriate consent where necessary is essential to avoid legal issues.
How much does it cost to set up a honeypot?
Costs vary widely depending on the type of honeypot, complexity, and resources required. Simple low-interaction honeypots can be relatively inexpensive, while advanced high-interaction systems may involve significant investment.
Are honeypots effective against all types of attacks?
No. Honeypots are most effective against opportunistic attackers. Sophisticated, targeted attacks may bypass them, but they still provide valuable intelligence even in those cases.