How Can AI Be Used To Keep Customer Data Secure?
How can AI be used to keep customer data secure? It’s a question increasingly crucial in our digital age, where cyber threats are becoming more sophisticated and data breaches more frequent. AI isn’t just a futuristic concept; it’s a powerful tool actively shaping the landscape of data security, offering innovative solutions to protect sensitive customer information. From encrypting data with complex algorithms to detecting anomalies in real-time, AI is revolutionizing how businesses safeguard their valuable assets.
This post delves into the multifaceted ways AI enhances data security, exploring its applications in encryption, anomaly detection, access control, data loss prevention, and more. We’ll examine the practical implications of AI-powered security measures, discuss the advantages and limitations, and consider the future of AI in safeguarding customer data. Get ready to discover how this technology is transforming the fight against cybercrime and ensuring customer trust.
AI-Driven Data Encryption and Decryption
AI is revolutionizing data security, and its application in encryption and decryption is particularly exciting. Traditional methods often struggle with the sheer volume and complexity of modern data, but AI offers solutions that are both more efficient and more adaptable to evolving threats. This involves leveraging machine learning algorithms to enhance both the encryption process itself and the management of cryptographic keys.
AI algorithms are being integrated into encryption and decryption in several ways. Instead of relying solely on pre-defined algorithms, AI can dynamically adjust encryption parameters based on real-time threat analysis. This adaptive approach makes it much harder for attackers to crack the encryption, as the system is constantly evolving.
AI Algorithms for Encryption and Decryption
Several machine learning algorithms are finding application in this field. For instance, neural networks can be trained to generate highly complex and unpredictable encryption keys, making brute-force attacks exponentially more difficult. Similarly, deep learning models can analyze encrypted data to identify patterns and anomalies that might indicate a breach attempt. However, the effectiveness of these algorithms depends heavily on the quality and quantity of training data.
Overly simplistic training data can lead to vulnerabilities, and the computational cost of training complex neural networks can be substantial. Furthermore, the “black box” nature of some deep learning models can make it challenging to understand and verify their security properties.
Symmetric and Asymmetric Encryption with AI
AI can enhance both symmetric and asymmetric encryption methods. In symmetric encryption, the same key is used for both encryption and decryption. AI can optimize the key generation process, ensuring that keys are highly random and resistant to attacks. For example, an AI system could generate keys based on chaotic systems, making them practically impossible to predict.
Asymmetric encryption, on the other hand, uses a pair of keys: a public key for encryption and a private key for decryption. AI can be used to improve the efficiency of key generation and management in asymmetric systems, and also to detect potential weaknesses in the public key infrastructure. While symmetric encryption is generally faster, asymmetric encryption offers better key management and scalability for large networks.
The choice between them often depends on the specific security needs and the computational resources available.
AI in Encryption Key Management
The security of any encryption system rests heavily on the management of its keys. AI can automate and improve this process significantly. AI-powered systems can monitor key usage, detect anomalies that might suggest compromised keys, and automatically rotate keys on a schedule or based on risk assessments. This reduces the human element in key management, minimizing the risk of human error or malicious insider threats.
Furthermore, AI can help optimize key storage and retrieval, ensuring that keys are readily available when needed while maintaining robust protection against unauthorized access. For instance, AI can dynamically adjust access controls based on user behavior and risk profiles.
Hypothetical System Architecture for AI-Enhanced Encryption
Imagine a system where incoming data is first analyzed by an AI-powered anomaly detection module. This module uses machine learning algorithms to identify potentially malicious patterns or attempts at data manipulation. If an anomaly is detected, the data is routed to a more secure encryption pathway, perhaps using a more robust algorithm or a longer key. Clean data proceeds through a standard encryption pipeline.
A separate AI module manages the encryption keys, ensuring their rotation and secure storage. This module leverages blockchain technology for enhanced transparency and immutability in key management. The entire system is constantly monitored by AI for performance optimization and security vulnerabilities, adapting to evolving threats in real-time. This architecture uses a multi-layered approach, combining the speed of standard encryption with the adaptability and enhanced security provided by AI.
AI-Powered Anomaly Detection for Security Threats: How Can Ai Be Used To Keep Customer Data Secure
AI anomaly detection is revolutionizing cybersecurity by proactively identifying suspicious activities within customer data access logs that traditional rule-based systems often miss. These systems leverage machine learning to establish a baseline of “normal” behavior and then flag deviations as potential threats, providing a crucial layer of defense against sophisticated attacks.Machine learning models identify unusual access patterns or data breaches by analyzing vast amounts of data to identify patterns and deviations from established norms.
These models learn from historical data, building a profile of typical user behavior, including login times, locations, access frequencies, and the types of data accessed. Any significant departure from this profile triggers an alert, indicating a potential security incident.
Effective AI Algorithms for Anomaly Detection
Several AI algorithms are particularly effective at detecting anomalies in customer data access logs. These algorithms excel at identifying subtle deviations from normal patterns that might indicate a breach or insider threat. For instance, unsupervised learning algorithms like One-Class SVM (Support Vector Machine) are well-suited for anomaly detection because they can model the normal behavior of a system without needing labeled examples of malicious activity.
Autoencoders, a type of neural network, are also effective at reconstructing normal data patterns and flagging data points that deviate significantly from the reconstruction. Finally, Isolation Forest algorithms excel at identifying anomalies by isolating them quickly in the data. Each algorithm has strengths and weaknesses, and the best choice depends on the specific dataset and security requirements.
AI’s role in securing customer data is huge, from anomaly detection to predictive threat modeling. Building robust, scalable systems to handle this data requires efficient development, which is where the advancements in domino app dev, the low-code and pro-code future , become incredibly valuable. These platforms allow for faster development of secure applications, ultimately strengthening AI’s ability to protect sensitive customer information.
This streamlined development process is crucial for staying ahead of evolving threats.
Case Study: AI Anomaly Detection Preventing a Data Breach
A major financial institution implemented an AI-based anomaly detection system to monitor its customer data access logs. The system, utilizing a combination of One-Class SVM and autoencoder algorithms, detected unusual login attempts originating from an unfamiliar geographic location. Further investigation revealed a sophisticated phishing campaign targeting employees. The AI system’s early warning allowed the institution to block the suspicious logins, prevent a data breach, and mitigate potential financial losses and reputational damage.
The quick response prevented what could have been a catastrophic loss of customer data. The successful mitigation also highlighted the value of real-time threat detection and rapid response capabilities.
Implementing an AI-Based Anomaly Detection System
Implementing an AI-based anomaly detection system for customer data involves several key steps. First, a robust data collection pipeline is essential to gather comprehensive access logs and other relevant security data. This data needs to be pre-processed and cleaned to ensure its quality and consistency. Next, an appropriate machine learning model needs to be selected and trained on the historical data.
The model’s performance should be rigorously evaluated to ensure its accuracy and efficiency. Following this, the system should be integrated into the existing security infrastructure to enable real-time monitoring and alert generation. Finally, a process for investigating and responding to alerts is crucial to ensure that potential threats are addressed promptly and effectively. Regular monitoring and retraining of the model are essential to maintain its effectiveness over time.
AI in Access Control and Authentication
AI is revolutionizing how we secure access to sensitive data and systems. Traditional methods, while effective to a degree, are increasingly vulnerable to sophisticated attacks. AI offers a powerful new layer of defense, enhancing existing security measures and providing more robust protection against unauthorized access. This enhanced security is achieved through improved authentication processes and more intelligent access control systems.AI’s role in bolstering access control and authentication is multifaceted, leveraging its capabilities to analyze vast datasets, identify patterns, and adapt to evolving threats in real-time.
This allows for a more dynamic and responsive security posture, significantly improving the overall security landscape.
AI Enhancement of Multi-Factor Authentication
Multi-factor authentication (MFA) significantly strengthens security by requiring users to provide multiple forms of verification before granting access. AI enhances MFA by analyzing user behavior patterns to detect anomalies and prevent unauthorized access even when some factors are compromised. For instance, AI can detect unusual login locations or times, prompting for additional verification steps. This goes beyond simple time-based or location-based restrictions, employing machine learning to identify subtle behavioral deviations indicative of a potential breach.
AI can also dynamically adjust the MFA requirements based on risk assessment, demanding stronger authentication for higher-risk transactions or access attempts from unfamiliar devices. This adaptive approach provides a flexible and highly secure authentication process.
AI Improvement of Biometric Authentication Security
Biometric authentication, using unique biological traits like fingerprints or facial recognition, offers a convenient and secure alternative to passwords. However, traditional biometric systems are susceptible to spoofing attacks using fake fingerprints or manipulated images. AI significantly improves biometric security by detecting these spoofing attempts. AI algorithms can analyze biometric data with far greater precision than traditional methods, identifying subtle inconsistencies that indicate a forgery.
For example, AI can analyze the texture and pressure of a fingerprint to determine its authenticity, or detect minute variations in facial expressions that indicate a live person versus a photograph or video. Furthermore, AI can continuously learn and adapt to new spoofing techniques, ensuring the system remains effective against evolving threats.
Comparison of AI-Powered Access Control Systems, How can ai be used to keep customer data secure
Several AI-powered access control systems exist, each with its strengths and weaknesses. Some systems rely primarily on behavioral biometrics, analyzing user typing patterns or mouse movements to verify identity. Others incorporate sophisticated risk scoring models that assess the likelihood of an unauthorized access attempt based on various factors, including location, device, and time of day. Still others integrate multiple authentication methods, combining biometrics with password-based authentication and one-time codes.
The effectiveness of these systems depends on the specific algorithms used, the quality of the data used to train the AI models, and the overall security architecture in which they are implemented. A robust system will incorporate multiple layers of security and employ a continuous learning approach to stay ahead of emerging threats.
Comparison of Traditional and AI-Enhanced Access Control Methods
| Method | Description | Security Level | AI Integration |
|---|---|---|---|
| Password-based authentication | Users authenticate using a username and password. | Low to Moderate | None |
| Multi-factor authentication (Traditional) | Users provide multiple forms of verification (e.g., password, one-time code). | Moderate to High | Limited (e.g., time-based restrictions) |
| Biometric authentication (Traditional) | Users authenticate using biometric data (e.g., fingerprint, facial recognition). | Moderate to High | Limited (e.g., simple threshold checks) |
| AI-enhanced MFA | MFA with AI-powered anomaly detection and adaptive risk assessment. | High | Behavioral biometrics, anomaly detection, risk scoring |
| AI-enhanced Biometric Authentication | Biometric authentication with AI-powered liveness detection and spoofing prevention. | Very High | Liveness detection, spoofing prevention, anomaly detection |
| AI-powered Access Control System | Integrated system using AI for multiple authentication methods and access control decisions. | Very High | Comprehensive AI integration across all aspects of access control. |
AI for Data Loss Prevention (DLP)

Data loss prevention (DLP) is crucial for any organization handling sensitive information. Traditional DLP methods often struggle to keep pace with sophisticated data exfiltration techniques. AI, however, offers a powerful new layer of defense, enabling proactive identification and prevention of data breaches. By leveraging machine learning and advanced analytics, AI-powered DLP systems can detect anomalies, classify data, and respond to threats in real-time, significantly improving an organization’s security posture.AI techniques enhance DLP by automating processes that were previously manual and time-consuming, allowing security teams to focus on more strategic tasks.
This proactive approach minimizes the risk of data breaches and reduces the impact of successful attacks.
AI Techniques for Data Loss Prevention
AI employs several techniques to prevent sensitive data from leaving the organization’s network. These techniques analyze various data streams, identifying patterns indicative of data exfiltration attempts. Machine learning algorithms are trained on historical data to recognize normal user behavior and network traffic patterns. Deviations from these patterns trigger alerts, enabling security teams to investigate potential threats. Natural language processing (NLP) is used to analyze textual data, identifying sensitive information such as personally identifiable information (PII) or intellectual property.
Anomaly detection algorithms flag unusual activities, such as large file transfers or access attempts outside of normal working hours. These combined techniques provide a multi-layered approach to data loss prevention.
AI-Driven Detection and Prevention of Data Exfiltration
AI can detect and prevent data exfiltration attempts across various channels, including email, cloud storage, and removable media. For example, AI can analyze email content for sensitive information, flagging suspicious attachments or links. It can monitor cloud storage services for unauthorized access or data downloads, and it can detect the use of unauthorized removable media. AI algorithms can also identify unusual communication patterns, such as an employee communicating with a known malicious actor.
Furthermore, AI can analyze network traffic for unusual data flows, identifying attempts to exfiltrate data through unconventional channels. Real-time threat detection and response capabilities are a critical component of this process, allowing immediate action to be taken when a potential breach is detected.
AI-Based Data Classification and Categorization
AI significantly enhances data classification and categorization based on sensitivity levels. Machine learning models can be trained to automatically classify data based on s, data types, and contextual information. This automated classification process improves accuracy and efficiency compared to manual methods, reducing the risk of misclassification. AI can also analyze the context of data usage, determining its sensitivity level based on who is accessing it and how it is being used.
This allows organizations to implement more granular access controls, further reducing the risk of data loss. For example, a document containing customer financial information would be automatically classified as highly sensitive and subjected to stricter access controls.
Workflow Diagram Illustrating AI’s Role in DLP
Imagine a workflow diagram. The first box represents “Data Ingestion,” where all relevant data streams (email, network traffic, cloud storage activity, etc.) are collected. This flows into a “Data Analysis” box, where AI algorithms analyze the data for anomalies, sensitive information, and suspicious activities. The results then feed into a “Threat Assessment” box, where the AI system determines the severity of the threat.
This leads to a “Response” box, where automated actions are taken, such as blocking suspicious emails, quarantining files, or alerting security personnel. Finally, a “Monitoring and Reporting” box shows ongoing system monitoring and generation of reports on DLP effectiveness. This illustrates how AI automates and enhances each stage of the DLP process.
AI in Data Masking and Anonymization
Data masking and anonymization are crucial for protecting sensitive customer information while still allowing for data analysis, testing, and sharing. AI significantly enhances these processes, offering more sophisticated and effective techniques than traditional methods. By leveraging machine learning, AI can identify and mask sensitive data points with greater accuracy and efficiency, minimizing the risk of re-identification.AI-based techniques for masking and anonymization go beyond simple data replacement or shuffling.
They employ advanced algorithms to intelligently transform data while preserving its utility for specific purposes. This allows organizations to share data for research or collaboration without compromising individual privacy.
AI Algorithms for Data De-identification
Several AI algorithms are employed for data de-identification. These include techniques like differential privacy, which adds carefully calibrated noise to the data to prevent individual records from being easily identified while still preserving statistical properties. Another approach involves using generative adversarial networks (GANs). GANs consist of two neural networks, a generator and a discriminator, that compete against each other.
The generator creates synthetic data that resembles the original data but is not directly linked to any individual, while the discriminator tries to distinguish between real and synthetic data. This process iteratively refines the synthetic data, making it increasingly realistic and privacy-preserving. Furthermore, k-anonymity and l-diversity are also used; k-anonymity ensures that each record is indistinguishable from at least k-1 other records on quasi-identifiers (attributes that could potentially be used to identify individuals), while l-diversity ensures sufficient diversity within each group of k-anonymous records on sensitive attributes.
Comparison of Data Masking Techniques
Different data masking techniques offer varying levels of protection. Simple techniques like data swapping (exchanging values between records) or generalization (replacing specific values with broader categories) offer basic protection but can be easily reversed with sufficient background knowledge. More advanced techniques, such as tokenization (replacing sensitive data with unique tokens), offer stronger protection. AI-driven techniques like those employing GANs provide the strongest protection, generating synthetic data that is statistically similar to the original but cannot be linked to specific individuals.
The effectiveness depends heavily on the complexity of the data and the sophistication of the attack. For instance, if a data set contains unique identifiers that are easily correlated with other attributes, even advanced techniques might not offer complete protection.
Benefits and Limitations of AI-Driven Data Masking and Anonymization
The following points highlight the advantages and disadvantages of employing AI in data masking and anonymization:
- Benefits:
- Improved accuracy and efficiency in identifying and masking sensitive data.
- Enhanced privacy protection compared to traditional methods.
- Ability to create synthetic data that preserves statistical properties while protecting individual privacy.
- Scalability to handle large datasets.
- Limitations:
- High computational cost for complex algorithms like GANs.
- Potential for bias in AI models if training data is not representative.
- Difficulty in guaranteeing complete anonymity; sophisticated attacks might still be able to re-identify individuals.
- Requires specialized expertise to implement and manage AI-driven solutions.
AI for Security Auditing and Compliance
AI is revolutionizing security auditing and compliance, moving beyond manual processes to provide faster, more thorough, and insightful assessments. This allows organizations to proactively identify and mitigate risks, ensuring they meet regulatory requirements and maintain a strong security posture. The automation and analytical capabilities of AI significantly reduce the time and resources needed for compliance efforts, freeing up security teams to focus on strategic initiatives.AI can automate the tedious and time-consuming tasks associated with security audits.
Instead of relying on manual checks and log analysis, AI algorithms can analyze vast amounts of data from various sources, including network logs, security information and event management (SIEM) systems, and cloud platforms. This comprehensive analysis allows for the identification of subtle patterns and anomalies that might indicate vulnerabilities or security breaches that would be easily missed by human auditors.
AI-Driven Vulnerability Identification
AI algorithms, particularly machine learning models, are trained on massive datasets of known vulnerabilities and attack patterns. This allows them to identify potential weaknesses in systems and applications with a high degree of accuracy. For instance, an AI system can analyze code repositories to identify potential vulnerabilities before they are deployed, significantly reducing the risk of exploitation. Furthermore, AI can assess the severity of identified vulnerabilities, prioritizing remediation efforts based on potential impact.
This allows security teams to focus their resources on the most critical issues.
AI-Facilitated Compliance with Data Privacy Regulations
Meeting the requirements of regulations like GDPR and CCPA is complex and requires meticulous record-keeping and data handling practices. AI can significantly assist in this process. AI-powered systems can monitor data access, usage, and transfer, ensuring that all activities comply with the relevant regulations. For example, AI can automatically identify and flag any instances of unauthorized data access or transfer, triggering alerts and enabling prompt remediation.
Moreover, AI can help organizations demonstrate compliance by automatically generating reports that detail their data handling practices and adherence to regulations.
AI-Generated Compliance Reports
AI streamlines the generation of compliance reports by automating the collection and analysis of relevant data. This eliminates the manual effort involved in compiling reports, reducing the risk of errors and ensuring that reports are generated in a timely manner. The reports generated by AI systems can be customized to meet specific regulatory requirements and can include detailed information on data processing activities, security measures, and incident responses.
This facilitates efficient audits and demonstrates the organization’s commitment to compliance.
Checklist for Implementing AI in Security Audits and Compliance
Before implementing AI for security audits and compliance, a structured approach is crucial. The following steps Artikel a practical roadmap:
- Define Objectives and Scope: Clearly identify the specific security and compliance objectives that AI will address.
- Data Collection and Preparation: Gather relevant data from various sources and prepare it for AI processing.
- AI Model Selection and Training: Choose appropriate AI algorithms and train them on relevant datasets.
- Integration with Existing Systems: Integrate the AI system with existing security and compliance tools.
- Testing and Validation: Thoroughly test the AI system to ensure accuracy and reliability.
- Deployment and Monitoring: Deploy the AI system and continuously monitor its performance.
- Regular Updates and Refinement: Regularly update the AI system with new data and refine its algorithms to improve accuracy.
AI-Powered Threat Intelligence and Response
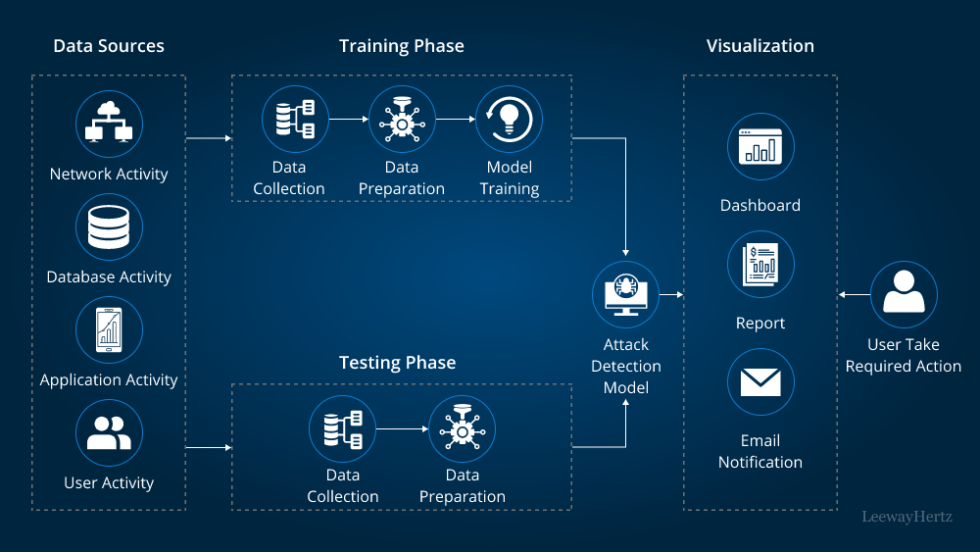
AI is revolutionizing cybersecurity, and its impact on threat intelligence and response is particularly significant. By leveraging machine learning and advanced analytics, AI systems can proactively identify and mitigate threats, significantly reducing the risk of data breaches and improving overall security posture for customer data. This allows organizations to move from a reactive to a proactive security model, significantly improving their ability to protect sensitive information.AI analyzes threat intelligence data from various sources, including internal security logs, external threat feeds, and open-source intelligence, to identify patterns and predict potential attacks.
This proactive approach allows for timely mitigation strategies, preventing threats before they can compromise customer data. The speed and scale at which AI can process this data far surpasses human capabilities, making it an invaluable asset in today’s complex threat landscape.
AI’s Role in Proactive Threat Protection
AI algorithms analyze vast amounts of threat intelligence data to identify anomalies and patterns indicative of malicious activity. This includes identifying suspicious network traffic, unusual user behavior, and potential vulnerabilities in systems. For example, an AI system might detect a sudden surge in login attempts from an unusual geographic location, indicating a potential brute-force attack. Based on this analysis, the system can proactively block the malicious traffic, alert security personnel, and even automatically implement countermeasures, such as temporarily locking accounts or adjusting firewall rules.
This proactive approach significantly reduces the window of vulnerability and minimizes the potential impact of a successful attack.
AI-Driven Automation of Incident Response
In the event of a data breach or security incident, AI can significantly accelerate and improve the incident response process. AI-powered systems can automatically triage alerts, prioritize incidents based on severity, and even initiate automated remediation steps. For instance, an AI system could automatically isolate an infected system from the network, preventing the spread of malware. It can also analyze the breach to determine its scope and impact, providing crucial information for incident response teams to effectively contain the damage and recover from the attack.
This automation not only speeds up the response but also reduces the risk of human error during critical moments.
Examples of AI-Powered SIEM Systems
Several vendors offer AI-powered Security Information and Event Management (SIEM) systems that leverage machine learning to detect and respond to security threats. These systems typically incorporate features such as: user and entity behavior analytics (UEBA) to identify anomalous activities, machine learning-based threat detection to identify previously unknown threats, and automated incident response capabilities to quickly contain and remediate security incidents.
Examples include IBM QRadar Advisor with Watson, Splunk Enterprise Security, and Exabeam. These platforms integrate threat intelligence feeds, analyze security logs, and use AI to correlate events, identify patterns, and prioritize alerts for efficient investigation and response.
AI-Driven Threat Response Process Flowchart
The following describes a flowchart illustrating the AI-driven threat response process. Imagine a flowchart with the following stages:
1. Threat Detection
AI analyzes security logs and threat intelligence feeds for suspicious activity. This could be represented visually by a box with incoming data streams flowing into a central processing unit.
2. Threat Analysis
The AI system uses machine learning algorithms to analyze the detected activity, identifying patterns and determining the severity of the threat. This could be represented by a decision diamond, branching based on threat level (high, medium, low).
3. Alert Generation
If the threat is deemed significant, the system generates an alert, notifying security personnel. This could be a box showing an alert being sent.
4. Automated Response
Based on pre-defined rules and policies, the system automatically initiates response actions, such as blocking malicious traffic or isolating infected systems. This could be a box showing automated actions being taken.
5. Incident Investigation
Security personnel investigate the incident to determine its root cause and scope. This could be represented by a box showing human intervention and analysis.
6. Remediation
Appropriate remediation steps are taken to address the vulnerability and prevent future occurrences. This could be a box showing actions taken to fix the problem.
7. Reporting
A report is generated documenting the incident, its impact, and the actions taken. This could be a box showing a report being generated.This flowchart visualizes the continuous loop of threat detection, analysis, response, and remediation, demonstrating how AI accelerates and improves the overall security posture.
Conclusive Thoughts
In conclusion, the integration of AI into data security strategies is no longer a luxury but a necessity. The ability of AI to analyze vast amounts of data, identify patterns, and respond to threats in real-time offers an unprecedented level of protection for customer information. While challenges remain, the continuous advancements in AI and its growing sophistication promise a future where data breaches are significantly mitigated, and customer trust is reinforced through robust, AI-powered security systems.
The journey towards a safer digital world is powered, in no small part, by the innovative applications of artificial intelligence.
Question Bank
What are the ethical considerations of using AI for data security?
Ethical concerns include potential bias in algorithms, the risk of misuse of AI capabilities, and ensuring transparency and accountability in AI-driven security decisions. Careful consideration of these issues is crucial for responsible implementation.
How expensive is it to implement AI-powered data security solutions?
The cost varies greatly depending on the complexity of the system, the size of the organization, and the specific AI solutions implemented. Smaller businesses might opt for cloud-based solutions, while larger enterprises might invest in custom-built systems. Consultations with security experts are recommended to determine the best fit and cost-effectiveness.
Can AI completely eliminate data breaches?
No, AI is a powerful tool but not a foolproof solution. Human error, sophisticated attacks, and unforeseen vulnerabilities can still lead to breaches. AI significantly reduces the risk but doesn’t eliminate it entirely. A multi-layered approach to security is always recommended.





