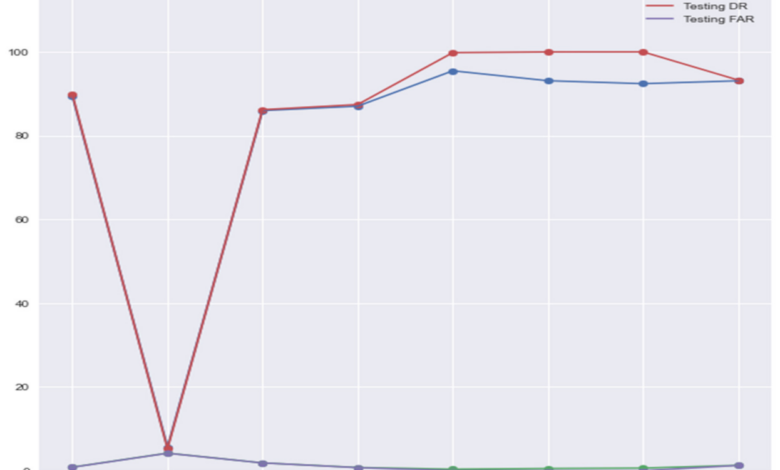
How DPI Sensors Improve Network Forensics
How DPI sensors improve network forensics is a crucial aspect of modern cybersecurity. DPI, or Deep Packet Inspection, sensors delve deep into network traffic, revealing details often missed by traditional monitoring methods. This detailed analysis empowers investigators to pinpoint malicious activity, understand attack sequences, and ultimately improve the efficiency and accuracy of forensic investigations. This exploration dives into the capabilities and limitations of DPI sensors, demonstrating how they transform network forensics from reactive to proactive.
Traditional network logs provide a basic snapshot of activity. DPI sensors, however, offer a far more comprehensive view, enabling security professionals to understand the context and intent behind network traffic. This deeper understanding leads to more effective incident response and a stronger overall security posture. We’ll explore how DPI enhances forensic investigations, from data extraction to advanced analysis and integration with existing systems.
Introduction to DPI Sensors and Network Forensics: How Dpi Sensors Improve Network Forensics
Deep Packet Inspection (DPI) sensors are crucial components in modern network security and monitoring. They act as sophisticated traffic analyzers, delving deeper into network packets than traditional methods. This in-depth examination reveals the contents of network communication, providing valuable insights into the nature and intent of the traffic flowing through the network. This ability to understand the actual data being exchanged, rather than just the destination and source, makes DPI sensors invaluable tools for network forensics.DPI sensors are integral to security operations because they can detect malicious activities, such as malware distribution, denial-of-service attacks, and unauthorized data exfiltration.
By analyzing the payload of network packets, DPI sensors can identify patterns and anomalies that traditional firewalls or intrusion detection systems might miss. This proactive approach to security allows organizations to mitigate risks before they escalate into significant incidents.
DPI Sensor Functionality
DPI sensors operate by capturing and inspecting network packets. This process involves intercepting network traffic, extracting data from the packets, and then applying various analysis techniques. The captured data is stored and analyzed for patterns, anomalies, and malicious activities. Crucially, this analysis is performed on the actual content of the packets, not just metadata like source and destination IP addresses.
This allows for a more nuanced understanding of network activity.
Capturing Network Traffic Data
DPI sensors employ specialized hardware and software to capture network traffic. The hardware components typically involve network interface cards (NICs) configured for packet capture. Software components then process the captured packets, extracting relevant information and applying analysis algorithms. This combined hardware and software approach allows for real-time monitoring and analysis of network traffic. The efficiency and accuracy of capturing network traffic data depend on the chosen sensor architecture and the underlying network infrastructure.
Types of DPI Sensors, How dpi sensors improve network forensics
Different DPI sensors cater to diverse needs and network environments. Understanding the different types and their unique features is essential for selecting the appropriate sensor for a particular organization.
| Type of DPI Sensor | Features |
|---|---|
| Application-layer DPI | Focuses on identifying specific applications and protocols. Can analyze HTTP, SMTP, FTP, and other application-level protocols, enabling detection of malicious activities like phishing and malware dissemination. |
| Protocol-layer DPI | Examines network protocols, such as TCP and UDP. Useful for detecting anomalies in protocol usage, like unusual port scans or denial-of-service attacks targeting specific protocols. |
| Content-layer DPI | Analyzes the actual content of the packets. Capable of detecting malicious code, unauthorized data transfers, and other harmful activities embedded within the data itself. This allows for a deeper understanding of the payload of the packet, revealing details like malware or phishing attempts. |
| Network-based DPI | Deployed within the network infrastructure, allowing for comprehensive monitoring of all traffic flowing through the network. This centralized approach provides a broader view of network activities, enabling early detection of threats and anomalies. |
| Host-based DPI | Installed on individual hosts within the network. Provides detailed insights into the traffic impacting specific machines. This granular view allows for the identification of targeted attacks or compromised systems. |
Enhancing Forensics with DPI Data
Deep Packet Inspection (DPI) sensors are revolutionizing network forensics by providing a granular view of network traffic that traditional methods simply can’t match. This granular view allows for a more accurate and comprehensive understanding of malicious activity, often revealing patterns and intentions hidden within the raw data of traditional logs. By going beyond the surface-level information, DPI enables investigators to reconstruct the full picture of an attack, leading to faster incident response and more effective prevention strategies.Traditional network logs, such as those from firewalls or intrusion detection systems, primarily capture basic information like source and destination IP addresses, ports, and protocol types.
This data, while useful, often lacks the context needed to fully understand the complexities of modern network attacks. DPI, on the other hand, delves deeper into the payload of network packets, revealing application-level details like the content of web requests, file types transferred, and even command-and-control (C&C) communication. This deeper understanding is crucial for effective forensic analysis.
DPI Data vs. Traditional Network Logs
DPI data significantly surpasses traditional network logs in its ability to provide a comprehensive view of network traffic. Traditional logs are primarily focused on basic network events, such as connection establishment and termination. DPI data, however, provides detailed insights into the actual content of network packets. This includes application-layer data, such as the specific commands used in a malware attack, or the parameters of a malicious request.
This difference is akin to looking at a traffic accident from afar (traditional logs) versus examining the contents of the vehicles and the drivers’ actions (DPI data).
Deeper Insights from DPI Sensors
DPI sensors enable a deeper understanding of network traffic by extracting contextual information from the packet payload. For instance, a malicious file transfer might be detected as simply a large file transfer in traditional logs. DPI data, however, could reveal the file type (e.g., a malicious executable), the destination (e.g., a compromised server), and even the encryption method used to conceal the malicious activity.
This detailed information is critical for forensic analysis and incident response. Furthermore, DPI can pinpoint the exact moment of an attack, the duration, and the specific applications used in the attack, which is vital for tracing the attack’s origin and scope.
Specific Attacks Better Detected with DPI Data
DPI data significantly improves the detection of various network attacks. For example:
- Application-layer attacks: DPI excels in identifying attacks targeting specific applications, such as web applications, email servers, or databases. Traditional logs might not capture the intricate details of these attacks, making them difficult to identify and trace. For example, an attacker might use a sophisticated SQL injection attack that bypasses simple intrusion detection mechanisms; DPI can uncover the SQL commands used in the attack and help trace its execution.
- Malware and botnet activity: DPI can uncover hidden communication channels used by malware and botnets to communicate with command-and-control servers. This allows investigators to identify the infected systems and the scope of the infection. This is crucial for isolating the affected systems and preventing further damage.
- Advanced persistent threats (APTs): APTs often employ sophisticated evasion techniques to avoid detection by traditional security systems. DPI data, with its detailed analysis of application-layer protocols, provides critical insights into these attacks, allowing investigators to understand the attack’s tactics and methodology.
Comparison of DPI Data and Traditional Logs
| Feature | Traditional Network Logs | DPI Data |
|---|---|---|
| Granularity | Low-level; limited to basic network events | High-level; includes application-layer details |
| Attack Detection | Limited detection of complex attacks | Enhanced detection of complex attacks, especially application-layer attacks |
| Contextual Information | Lacks context; difficult to reconstruct attack | Provides detailed context, allowing for better attack reconstruction |
| Incident Response | Slower incident response | Faster incident response due to deeper insights |
| Cost | Generally lower | Generally higher |
Improving Forensic Investigations with DPI
Deep Packet Inspection (DPI) sensors provide a wealth of data that significantly enhances network forensics investigations. This detailed information, often unavailable with traditional network monitoring tools, allows investigators to delve deeper into security incidents, identify malicious actors, and reconstruct attack sequences with greater precision. By analyzing the contents of network packets, DPI sensors reveal the true nature of communication, going beyond simple source and destination IP addresses.DPI data offers a crucial advantage in security incident investigations.
Traditional methods often rely on signatures or anomalies in network traffic volume. However, DPI enables a more comprehensive understanding of the activities occurring within network communications. This granular view of network activity is invaluable in identifying the specific tactics, techniques, and procedures (TTPs) used by attackers. It allows investigators to move beyond superficial observations and gain insight into the true nature of the threats.
Benefits of DPI for Investigating Security Incidents
DPI data empowers investigators by revealing the specific malicious payloads, protocols, and applications used in an attack. This goes beyond simple network traffic analysis and provides critical context for understanding the attacker’s intent and methods. DPI data enables a much more detailed picture of the attack sequence.
How DPI Data Aids in Identifying Malicious Activity
DPI data facilitates the identification of malicious activity by enabling the analysis of application layer protocols and payloads. By examining the content of network packets, DPI can detect malicious code, commands, or data being exchanged. This capability goes beyond traditional signature-based detection, which often relies on known patterns. DPI enables detection of zero-day exploits and unknown threats.
For example, DPI can identify a suspicious file being transferred or a command being executed on a target system.
How DPI Helps Correlate Events and Reconstruct Attack Sequences
DPI’s ability to capture and record detailed packet information is essential for correlating events and reconstructing attack sequences. By examining the timestamps and flow of data within the network, investigators can trace the progression of an attack. This allows for a detailed reconstruction of the attacker’s actions, from initial reconnaissance to exploitation and exfiltration. Furthermore, the analysis of communication patterns can provide insights into the attacker’s objectives.
Examples of Real-World Cases Where DPI Data Helped Solve Security Breaches
Numerous security breaches have been successfully investigated and resolved with the assistance of DPI data. For example, in one case, a financial institution used DPI data to identify a sophisticated phishing campaign. The DPI data revealed the specific emails used in the attack, the IP addresses involved, and the flow of sensitive data. This allowed the institution to quickly block the attackers and prevent further losses.
Another instance involved a manufacturing company that used DPI to discover unauthorized access attempts to its industrial control system. DPI data provided detailed information about the communication between the attackers and the targeted systems, enabling the company to mitigate the threat and strengthen its security posture.
DPI sensors are crucial for enhancing network forensics by providing a detailed view of network traffic. This granular data allows analysts to pinpoint suspicious activity, but a crucial next step involves using tools like those discussed in Deploying AI Code Safety Goggles Needed to analyze the code itself. Ultimately, this sophisticated approach will help ensure that the underlying code driving the network is secure, further improving the overall accuracy of network forensics investigations.
Steps in Using DPI Data to Investigate a Security Incident
| Step | Description |
|---|---|
| 1. Data Collection | Gathering DPI logs and relevant network traffic data. |
| 2. Data Filtering and Preparation | Identifying and selecting relevant data points for analysis. |
| 3. Event Correlation | Connecting events and activities across different network segments and systems. |
| 4. Analysis and Interpretation | Determining the nature and scope of the attack, reconstructing the attack sequence, and identifying the attackers’ objectives. |
| 5. Reporting and Mitigation | Documenting findings and implementing measures to prevent future attacks. |
DPI Sensor Capabilities and Limitations
DPI sensors, or Deep Packet Inspection sensors, are powerful tools for network forensics. They provide granular insights into network traffic, allowing investigators to dissect the contents of packets, identify malicious activity, and reconstruct events leading to security breaches. This detailed view of network communication offers significant advantages over traditional network monitoring tools. However, their capabilities are not without limitations.
Understanding these strengths and weaknesses is crucial for effective utilization in forensic investigations.
Key Capabilities of Modern DPI Sensors
Modern DPI sensors offer a wealth of capabilities relevant to network forensics. They can identify various types of malicious traffic, including malware, phishing attempts, and denial-of-service attacks. By analyzing the payloads of network packets, they can pinpoint specific malicious commands or data. This deep analysis is often impossible with simpler network monitoring tools. Furthermore, DPI sensors can track the flow of communication between various endpoints, creating a comprehensive picture of the attack path.
This detailed tracing helps investigators understand the sequence of events and the actors involved in a cyber incident. This detailed analysis of network traffic patterns can also reveal anomalous behavior, potentially pointing to insider threats or other suspicious activities.
Accuracy and Reliability of Different DPI Sensor Types
The accuracy and reliability of DPI sensors vary depending on the type and implementation. For example, commercial DPI solutions often provide more sophisticated analysis capabilities compared to open-source alternatives. The accuracy of a sensor also depends on the sophistication of the algorithms used for pattern recognition. More advanced algorithms generally yield higher accuracy in identifying malicious traffic.
Reliability is also impacted by factors like the volume of traffic being analyzed, the presence of noisy or complex data, and the speed of the sensor. Sophisticated DPI solutions designed for high-volume traffic can maintain higher accuracy and reliability than less robust systems.
Limitations of DPI Sensors in Network Forensics
While powerful, DPI sensors have limitations. One significant limitation is the potential for false positives. The algorithms used to detect malicious traffic can sometimes misclassify legitimate traffic as malicious. This can lead to wasted time and resources investigating non-malicious activity. Another limitation is the computational cost associated with deep packet analysis.
Processing massive amounts of network traffic requires significant computing resources, which can be a challenge for less sophisticated or resource-constrained systems. Finally, DPI sensors might not be able to detect advanced persistent threats (APTs). These sophisticated attacks often employ techniques that are difficult for DPI sensors to detect, as the attacks may be hidden within seemingly normal traffic patterns.
Potential Challenges and Risks in Using DPI Data for Investigations
Using DPI data for investigations presents several challenges. The sheer volume of data generated by DPI sensors can be overwhelming. Effective data management and analysis tools are essential to extract meaningful insights from this data deluge. Additionally, ensuring the integrity and authenticity of the data is critical. Any tampering or corruption of the data can compromise the validity of the investigation.
Another challenge is the potential for bias in the algorithms used by DPI sensors. These biases can lead to misinterpretations or skewed results. Finally, legal and ethical considerations are crucial when handling sensitive data captured by DPI sensors. Proper authorization and adherence to data privacy regulations are paramount.
Table Contrasting DPI Sensor Features and Their Impact on Forensics
| DPI Sensor Feature | Description | Impact on Forensics |
|---|---|---|
| Packet Analysis Depth | Level of detail in examining packet contents | Higher depth allows identification of subtle malicious activity but increases computational needs. |
| Traffic Volume Handling | Ability to process high volumes of network traffic | Impacts the accuracy and reliability of analysis on large networks. |
| Algorithm Sophistication | Complexity and accuracy of pattern recognition algorithms | Improved accuracy in identifying malicious activity but can lead to false positives. |
| False Positive Rate | Percentage of legitimate traffic misclassified as malicious | Higher rates lead to wasted investigation time and resources. |
Data Extraction and Analysis
DPI sensor logs, a treasure trove of network activity, are invaluable in network forensics. Extracting the right data and employing the correct analytical methods are crucial to uncovering malicious activity. This process transforms raw log data into actionable intelligence, enabling security analysts to understand attack patterns, identify compromised systems, and ultimately mitigate future threats.
DPI sensors are crucial for enhancing network forensics by capturing detailed packet information. This allows for deeper analysis of network traffic, helping identify suspicious activity. Knowing how these vulnerabilities manifest in the context of a service like Azure Cosmos DB, for example, Azure Cosmos DB Vulnerability Details , is critical for developing robust security protocols. This deeper understanding of potential weaknesses further strengthens the effectiveness of DPI sensor-based threat detection and response.
Data Extraction Process
The process of extracting relevant data from DPI sensor logs involves several key steps. First, the logs need to be collected and stored in a secure location. This is often done using specialized log management tools. Second, the data needs to be filtered to isolate the events of interest. This filtering process can involve specifying time ranges, IP addresses, or specific protocols.
Finally, the extracted data needs to be transformed into a format that is suitable for analysis, often involving normalization or aggregation. This transformation step is crucial to ensure consistency and usability in subsequent analysis stages.
Methods for Analyzing DPI Data
Several methods can be used to analyze the extracted DPI data, depending on the specific security concerns. Statistical analysis can reveal unusual patterns in network traffic volumes or protocol usage. Correlation analysis identifies relationships between different events, helping to understand the context of an attack. Pattern recognition algorithms can be used to find recurring patterns of malicious activity, which may signal a more complex or sophisticated attack.
Finally, machine learning algorithms can be used to identify new and emerging threats based on the analysis of vast amounts of DPI data.
Tools for Analyzing DPI Data
A variety of tools are available to facilitate the analysis of DPI sensor data. Their capabilities vary depending on the specific needs of the investigation.
| Tool | Description | Strengths | Limitations |
|---|---|---|---|
| Wireshark | A widely used network protocol analyzer. | Excellent for deep packet inspection, protocol analysis, and traffic visualization. | Can be resource-intensive for large datasets; not specifically designed for bulk DPI data analysis. |
| Splunk | A powerful log management and analytics platform. | Excellent for complex searches, visualizations, and dashboards. | Requires significant setup and configuration for effective use with DPI data. |
| Elasticsearch, Logstash, Kibana (ELK stack) | A powerful open-source log management and analytics stack. | Flexible, scalable, and capable of handling massive amounts of data. | Requires more technical expertise to set up and configure compared to some simpler tools. |
| Network Security Monitoring (NSM) tools | Specialized tools designed for network security monitoring. | Often integrated with other security tools, providing a holistic view of network activity. | May have a steeper learning curve and require specific licenses. |
Example Attack Scenario
Imagine a scenario where a malicious actor is attempting a Distributed Denial-of-Service (DDoS) attack. DPI data can reveal the attack’s characteristics. By analyzing the volume and frequency of malicious traffic from various IP addresses, security analysts can identify the source and nature of the attack. They can also correlate this with other events, like login attempts or file access anomalies, to gain a deeper understanding of the attacker’s intent.
Furthermore, DPI data can help identify the specific types of malicious traffic being used in the attack.
Step-by-Step Analysis Procedure
Analyzing a sample DPI dataset requires a structured approach. A hypothetical example involving a suspected insider threat is presented here:
- Data Collection and Preparation: Collect the relevant DPI logs from the specified time frame. Ensure data integrity and consistency by verifying data formats.
- Filtering and Selection: Filter the logs based on specific criteria (e.g., IP addresses, protocols, ports). Focus on potentially suspicious activities.
- Pattern Identification: Use appropriate tools to identify recurring patterns in the filtered data. Look for unusual traffic volumes, anomalous protocol usage, or specific patterns associated with known attacks.
- Correlation Analysis: Correlate the identified patterns with other events, such as user activity, login attempts, or file access anomalies. This correlation can reveal a potential insider threat.
- Visualization and Reporting: Use visualization tools to present the analysis results in a clear and concise manner. Generate reports summarizing the findings and recommendations.
Improving Efficiency and Accuracy
DPI data, while rich in detail, can be overwhelming for manual analysis. Efficient and accurate extraction and interpretation are crucial for effective network forensics. Leveraging automation and employing proper analysis techniques dramatically enhance the value of DPI data in uncovering security threats and incident patterns.Improving the efficiency of using DPI data for network forensics involves streamlining the process from data collection to actionable insights.
Automation plays a critical role in this aspect, reducing the manual effort required for large-scale analysis and enabling rapid identification of potential issues. Proper data structuring and organization also contribute significantly to efficient data handling and analysis.
Improving Efficiency of DPI Data Usage
Automation tools are essential for efficient DPI data analysis. These tools automate tasks like data collection, filtering, and report generation. This automation frees up analysts to focus on complex analysis and interpretation, leading to faster incident response and improved overall efficiency. For example, scripting languages like Python, coupled with libraries specifically designed for network analysis, can be used to automate data extraction and filtering from DPI logs.
This allows analysts to quickly focus on anomalies and critical events, reducing the time required to identify security threats.
Enhancing Accuracy of DPI Data Analysis
Accuracy in DPI data analysis hinges on meticulous data interpretation and contextualization. Applying standardized methodologies, employing specific rules for event correlation, and using proven statistical techniques are crucial. For instance, using machine learning algorithms to identify patterns and anomalies in the data can significantly enhance the accuracy of the analysis. By training models on known attacks and network behaviors, the system can predict and identify subtle anomalies that might be missed by traditional methods.
DPI sensors are crucial for enhancing network forensics, allowing investigators to meticulously examine network traffic for malicious activity. This detailed analysis becomes even more critical when considering recent developments like the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions , which highlights the growing importance of secure data handling.
Ultimately, DPI sensors provide the foundation for effective network security investigations by offering a deeper understanding of network behavior and identifying potential threats.
Automation Tools for Analyzing DPI Data
Several automation tools can aid in analyzing DPI data. Commercial security information and event management (SIEM) systems often include DPI data ingestion and analysis capabilities. Open-source tools like Splunk and ELK stack provide robust platforms for log management and analysis, which can also be used for DPI data. These tools facilitate complex searches, correlations, and visualizations, providing valuable insights into network behavior.
Data Visualization Techniques for DPI Data
Different visualization techniques can be used to present DPI data, allowing for more efficient identification of trends and anomalies. Line graphs can effectively display network traffic patterns over time, enabling the identification of sudden spikes or unusual dips in traffic volume. Heat maps can highlight areas of high activity or potential threats, providing a visual representation of network behavior.
Using interactive dashboards, analysts can drill down into specific events and gain a deeper understanding of the network activity, facilitating better understanding of network patterns.
Table of Tools and Techniques to Improve DPI Sensor Data Analysis
| Tool/Technique | Description | Benefits |
|---|---|---|
| Python scripting with network libraries | Automate data extraction, filtering, and report generation. | Increased efficiency, reduced manual effort, faster incident response. |
| Machine learning algorithms | Identify patterns and anomalies in the data. | Improved accuracy, identification of subtle anomalies, proactive threat detection. |
| SIEM systems | Ingest and analyze DPI data alongside other security logs. | Comprehensive security view, correlation of events, centralized analysis. |
| Splunk/ELK stack | Log management and analysis platforms for DPI data. | Complex searches, correlations, and visualizations. |
| Line graphs | Display network traffic patterns over time. | Identify trends, spikes, and unusual dips in traffic. |
| Heat maps | Highlight areas of high activity or potential threats. | Visual representation of network behavior, identification of potential anomalies. |
| Interactive dashboards | Enable drill-down into specific events. | Deep understanding of network activity, identification of critical events. |
Integrating DPI with Existing Systems
DPI sensors, providing granular network visibility, are powerful tools for network forensics. However, their value is significantly enhanced when integrated into existing security infrastructure, especially Security Information and Event Management (SIEM) systems. This integration allows for a unified view of security events, facilitating faster incident response and more comprehensive threat analysis.Integrating DPI data into existing systems requires careful planning and execution to ensure seamless data flow and efficient analysis.
The process involves connecting DPI sensors to existing forensic workflows, normalizing the data for effective correlation, and establishing secure data pipelines. This holistic approach leverages the strengths of both DPI and existing systems, creating a more robust and responsive security posture.
Connecting DPI Sensors to Existing Forensic Workflows
Effective integration hinges on a clear understanding of existing forensic processes. A crucial step is mapping DPI data fields to relevant SIEM fields. This ensures that DPI-derived information seamlessly integrates with existing alerts and investigations. This alignment allows analysts to quickly identify and correlate network events with other security incidents.
Data Normalization for Integrating DPI Data
DPI sensors generate vast amounts of data, often in diverse formats. Normalization is essential for efficient integration into existing systems. This involves transforming the raw DPI data into a standardized format that is compatible with the SIEM system’s data model. Normalization ensures consistency and accuracy in analysis, preventing inconsistencies and facilitating effective correlations between network events and other security incidents.
Designing a Secure Data Pipeline for Transferring DPI Data
A secure data pipeline is critical for transferring DPI data from sensors to SIEM systems. The pipeline should employ encryption to protect sensitive data during transmission. This prevents unauthorized access and ensures data integrity. Implementing a secure data pipeline with robust authentication and authorization measures ensures that only authorized personnel can access and process the DPI data.
Utilizing a dedicated network segment for DPI data transmission can also improve security and performance.
Case Study: Integrating DPI into a SIEM for Enhanced Malware Analysis
Consider a scenario where a company uses a network security appliance with DPI capabilities. The organization utilizes a commercial SIEM system for threat detection and incident response. The company’s current workflow involves manual analysis of network logs for malware detection.To integrate DPI into the existing workflow, a dedicated data pipeline was established using encrypted HTTPS connections. The DPI sensor sends the network traffic data to a central log repository, which is then processed by a custom script to normalize the data.
The normalized data is then ingested into the SIEM system, allowing for enhanced correlations between malware activity and other security events. For instance, analysts can now observe the network communication patterns of malicious actors alongside other security indicators, enabling more effective malware identification and containment.This integration significantly enhanced the company’s malware analysis capabilities. Analysts could correlate DPI data with other security events, such as user login attempts, system intrusions, and suspicious file transfers, to identify potential threats more quickly.
This improved analysis efficiency led to quicker identification of malicious activity, resulting in reduced attack impact. Moreover, the integration minimized manual analysis time, allowing analysts to focus on higher-level investigations.
Advanced DPI Features and Applications

DPI sensors are no longer confined to basic network packet inspection. Modern DPI systems boast sophisticated features, allowing for deeper analysis and broader applications beyond traditional forensics. This advanced capability unlocks valuable insights into network performance, security, and overall health. The ability to detect anomalies and patterns in network traffic empowers proactive threat detection and optimization strategies.Advanced DPI features go beyond simply identifying malicious traffic.
They provide a more comprehensive understanding of the network’s behavior, facilitating deeper investigation and more effective incident response. This capability is crucial in today’s complex and dynamic network environments.
Anomaly Detection
Modern DPI sensors incorporate sophisticated anomaly detection mechanisms. These systems analyze network traffic patterns, identifying deviations from established norms. This proactive approach is critical in preventing attacks, as anomalies often precede malicious activity. For example, a sudden surge in traffic from an unusual IP address, or a pattern of unusual protocol usage, might be flagged as an anomaly.
Such signals can trigger alerts, allowing security teams to investigate and potentially mitigate threats before they escalate.
Applications Beyond Basic Forensics
DPI data extends its utility beyond traditional network forensics. It can be leveraged for various purposes, including network performance analysis and security monitoring. Analyzing DPI data reveals bottlenecks and inefficiencies in network operations. By pinpointing these issues, network administrators can optimize performance and resource allocation, leading to significant cost savings.
Network Performance Analysis
DPI provides a detailed view of network traffic, allowing for precise performance analysis. The comprehensive data allows identification of bottlenecks, slowdowns, and other performance issues. For instance, by analyzing traffic patterns, administrators can pinpoint which applications or protocols are consuming the most bandwidth, potentially leading to optimization strategies. Detailed analysis reveals the source of congestion and allows for tailored solutions, leading to improved network performance and user experience.
Network Security Monitoring
DPI data is instrumental in proactive security monitoring. By analyzing network traffic patterns, DPI can detect suspicious activity and anomalies that might indicate a security breach. Real-time alerts on suspicious activity allow security teams to quickly respond to potential threats, minimizing damage and downtime. This early warning system empowers proactive measures, ensuring a stronger security posture.
Advanced DPI Features Comparison
| Application | Feature | Description |
|---|---|---|
| Anomaly Detection | Statistical Analysis | Identifies deviations from normal traffic patterns. |
| Machine Learning | Leverages algorithms to learn and identify patterns. | |
| Rule-Based Detection | Utilizes predefined rules to identify suspicious activity. | |
| Network Performance Analysis | Traffic Profiling | Detailed analysis of network traffic to identify bottlenecks. |
| Bandwidth Monitoring | Tracks bandwidth usage to identify areas of high consumption. | |
| Network Security Monitoring | Intrusion Detection | Identifies malicious activities like DDoS attacks. |
| Malware Detection | Recognizes and flags malicious software within traffic. | |
| Vulnerability Assessment | Identifies vulnerabilities in network configurations. |
Closing Notes
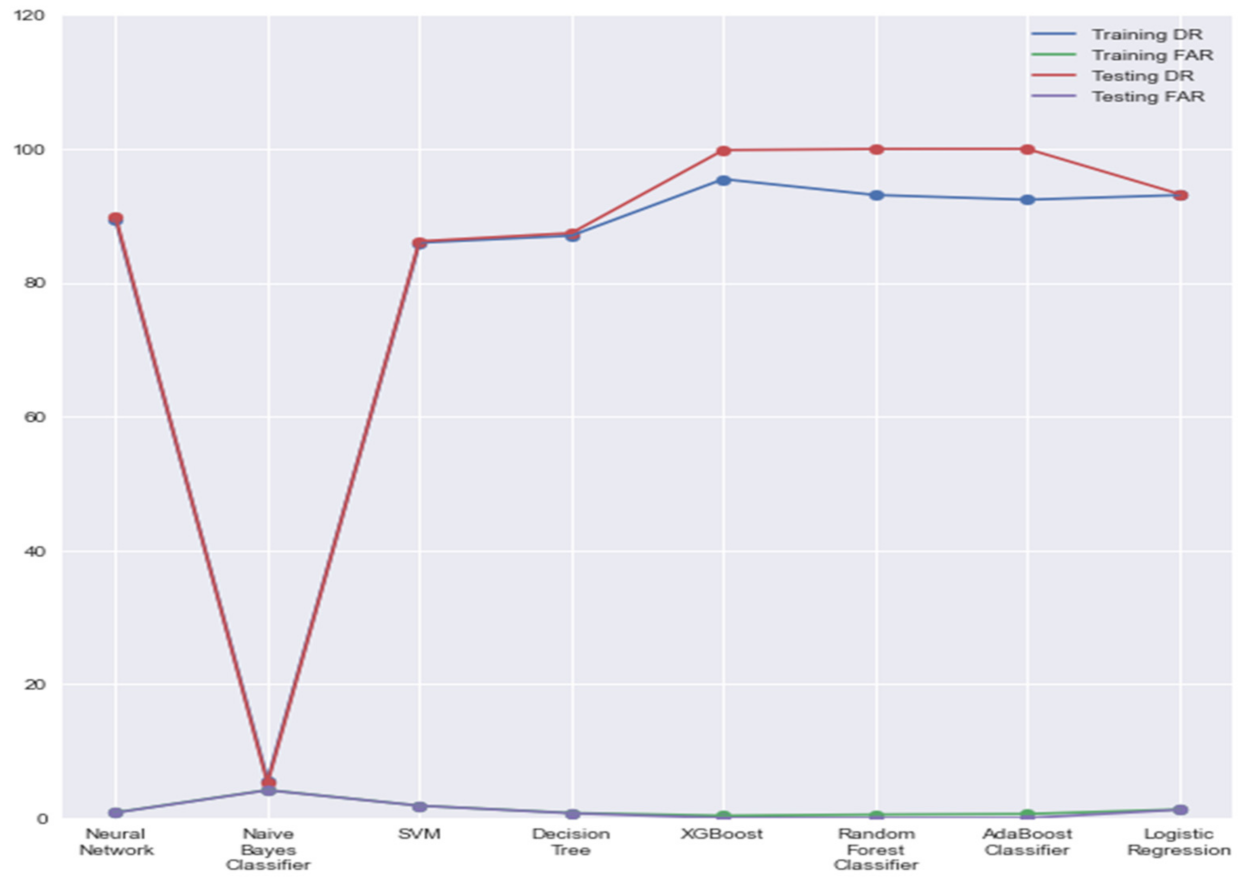
In conclusion, DPI sensors are revolutionizing network forensics. Their ability to provide detailed insights into network traffic empowers security teams to identify malicious activity, understand attack patterns, and ultimately improve the speed and accuracy of incident response. From enhanced data analysis to seamless integration with existing systems, DPI sensors are essential for modern network security. While challenges exist, the potential benefits of DPI in network forensics are substantial and will continue to evolve as technology advances.
User Queries
What are the limitations of DPI sensors in network forensics?
DPI sensors, while powerful, have limitations. Processing massive amounts of data can be computationally intensive, potentially impacting network performance. Additionally, the complexity of some attacks can make accurate identification difficult, requiring advanced analysis techniques. False positives are also a concern, needing careful filtering and validation during investigation.
How does DPI data differ from traditional network logs?
Traditional network logs capture basic information like source and destination IP addresses. DPI sensors go further, analyzing the actual content of network packets, allowing for deeper insights into application-level activity and potential malicious intent. This granular level of detail significantly enhances the effectiveness of forensic analysis.
What are some common tools for analyzing DPI sensor data?
Several tools facilitate the analysis of DPI sensor data, including specialized forensic analysis platforms and open-source tools. These tools vary in complexity and features, catering to different needs and budgets. Choosing the right tool depends on the specific analysis requirements and existing infrastructure.
How can DPI be integrated with existing SIEM systems?
Integrating DPI data with existing Security Information and Event Management (SIEM) systems is crucial for comprehensive security monitoring. This integration involves standardized data formats, often requiring custom scripts or integrations, to effectively correlate DPI data with other security logs.