Need Digital Behavior Insights? Consider a Single Code Base Solution
Need digital behavior insights consider a single code base solution – Need digital behavior insights? Consider a single code base solution. In today’s data-driven world, understanding user behavior is paramount for success. But managing data from disparate systems – website analytics, app usage, CRM data – can feel like herding cats. A unified code base offers a powerful alternative, streamlining data collection, analysis, and visualization, ultimately leading to clearer, more actionable insights.
This approach offers significant advantages. Imagine a single, consistent view of your users’ journeys, allowing you to identify patterns and trends that would be invisible with fragmented data. This holistic perspective enables more effective marketing campaigns, improved product design, and enhanced user experience. We’ll explore the benefits, challenges, and best practices for building and maintaining such a system, covering everything from data integration strategies to security and scalability.
The Value Proposition of a Single Code Base for Digital Behavior Insights

The decision to adopt a single code base for collecting and analyzing digital behavior insights is a strategic one, offering significant advantages over maintaining multiple, disparate systems. A unified approach fosters efficiency, consistency, and scalability, ultimately leading to more accurate and actionable insights. This approach streamlines data management, reduces redundancies, and allows for a more holistic understanding of user behavior across various platforms and touchpoints.The advantages of a unified code base are numerous and impactful.
By centralizing data collection and analysis, organizations can eliminate the complexities and inconsistencies inherent in managing multiple, independent systems. This translates to improved data quality, reduced operational costs, and faster time-to-insights. Imagine trying to piece together a puzzle with mismatched pieces – that’s what working with disparate systems feels like. A single code base provides a complete, coherent picture.
Data Consistency and Reduced Integration Complexities
A single code base ensures data consistency across all platforms and channels. This is achieved through standardized data collection methods, unified data schemas, and a shared analytical framework. For example, instead of having different event tracking mechanisms on a website, mobile app, and CRM system, a single code base allows for a consistent definition and tracking of events, leading to a more accurate and reliable dataset.
Furthermore, the need for complex and often error-prone data integrations between disparate systems is significantly reduced, simplifying the overall data pipeline and minimizing data loss or corruption. The single source of truth minimizes the risk of discrepancies and allows for more accurate analysis and reporting. Consider a scenario where customer interactions are tracked across an e-commerce website, a mobile application, and a customer support system.
With a unified code base, a comprehensive view of the customer journey becomes readily available, enabling more effective personalization and targeted marketing campaigns.
Best Practices for Designing a Scalable and Maintainable Single Code Base Architecture
Designing a scalable and maintainable single code base requires careful planning and adherence to best practices. This involves utilizing a modular architecture, employing version control systems, and adopting agile development methodologies. A modular design allows for independent development and deployment of individual components, improving flexibility and reducing the risk of cascading failures. Version control, such as Git, enables efficient collaboration, facilitates code review, and simplifies the process of tracking changes and reverting to previous versions if needed.
Agile development, with its iterative approach, allows for continuous improvement and adaptation to evolving business needs. Furthermore, employing robust testing methodologies, including unit, integration, and end-to-end tests, is crucial to ensuring the quality and reliability of the code base. Regular code reviews and automated deployment pipelines further enhance maintainability and reduce the risk of errors. The choice of programming language and technology stack should also be carefully considered based on factors such as scalability, performance, and the availability of skilled developers.
A well-documented code base is also essential for long-term maintainability and ease of collaboration among developers.
Data Collection and Integration Strategies within a Single Code Base
Building a unified system for digital behavior insights requires a robust strategy for collecting and integrating data from diverse sources. This single code base approach offers significant advantages in terms of efficiency, maintainability, and data consistency, but careful planning is crucial for successful implementation. We’ll explore various data collection methods and integration techniques suitable for this architecture.
Data Collection Methods
A single code base for digital behavior insights necessitates a unified approach to data collection, encompassing various sources like website analytics, mobile app usage, and CRM systems. This allows for a holistic view of user behavior across all touchpoints. Each method presents unique challenges and opportunities.Web analytics platforms like Google Analytics provide valuable data on website traffic, user engagement, and conversion rates.
This data is often collected via JavaScript tracking libraries embedded within website code. Mobile app usage data, on the other hand, is typically gathered using SDKs (Software Development Kits) that integrate directly into the app’s codebase. This allows for tracking of in-app events, user interactions, and session details. Finally, CRM (Customer Relationship Management) systems store valuable information on customer interactions, purchase history, and demographics.
Integrating this data provides a richer understanding of customer behavior and preferences.
Data Pipeline Architecture
Efficient data ingestion and processing are vital for a single code base solution. A well-designed data pipeline is essential. This pipeline typically involves several stages: data extraction, transformation, and loading (ETL). Data is extracted from various sources, transformed into a consistent format, and then loaded into a central data warehouse or data lake. This ensures data quality and consistency, allowing for effective analysis and reporting.
Real-time processing capabilities are often integrated to provide immediate insights. For example, a system could immediately flag unusual login attempts or track user activity during a specific marketing campaign.
Data Integration Techniques
Several data integration techniques can be applied within a single code base. The choice depends on factors like data volume, velocity, and complexity. Below is a comparison of four common techniques:
| Technique | Description | Advantages | Disadvantages |
|---|---|---|---|
| ETL (Extract, Transform, Load) | Data is extracted from various sources, transformed into a consistent format, and loaded into a central repository. | Robust, scalable, handles large datasets. | Can be complex to implement, may introduce latency. |
| ELT (Extract, Load, Transform) | Data is extracted and loaded into a data warehouse before transformation. | Faster initial data ingestion, allows for flexible transformation later. | Requires more powerful data warehouse infrastructure. |
| Real-time Data Streaming | Data is ingested and processed in real-time using technologies like Kafka or Apache Flink. | Provides immediate insights, enables real-time decision-making. | Requires specialized infrastructure and expertise, increased complexity. |
| API-based Integration | Data is exchanged between systems via APIs. | Relatively simple to implement, suitable for smaller datasets. | Can be less efficient for large datasets, dependent on API availability and performance. |
Data Analysis and Visualization Techniques
Unlocking the power of a unified digital behavior dataset hinges on effective analysis and visualization. By consolidating data from disparate sources into a single codebase, we gain the ability to identify patterns and trends that would remain hidden in siloed systems. This allows for a more holistic understanding of user behavior, leading to data-driven decisions that improve user experience and business outcomes.The richness of a unified dataset allows for a deep dive into various aspects of digital behavior.
Want deep digital behavior insights? A single code base is key for efficient analysis and updates. This is especially true when you consider the power of modern development approaches, like those explored in this fantastic article on domino app dev, the low-code and pro-code future , which highlights how streamlined development can improve data collection. Ultimately, a unified code base simplifies the process of gathering and interpreting the data you need for meaningful insights.
We can analyze user journeys, identify bottlenecks in conversion funnels, and pinpoint areas where user engagement is particularly high or low. This level of granularity allows for targeted interventions and optimization strategies.
Key Performance Indicators (KPIs) for Digital Behavior
Understanding digital behavior requires focusing on the right metrics. These KPIs provide a quantitative measure of success and allow us to track progress over time. A selection of relevant KPIs includes:
- Website Traffic: Unique visitors, page views, bounce rate, and session duration provide insights into overall website performance and user engagement.
- Conversion Rates: This measures the percentage of users completing a desired action, such as making a purchase, filling out a form, or signing up for a newsletter. Analyzing conversion rates at various stages of the user journey helps identify areas for improvement.
- User Engagement: Metrics like time on site, pages per visit, and scroll depth indicate how deeply users are interacting with the website content.
- Customer Acquisition Cost (CAC): This metric measures the cost of acquiring a new customer, which is crucial for evaluating the effectiveness of marketing campaigns.
- Customer Lifetime Value (CLTV): This represents the total revenue a customer is expected to generate throughout their relationship with the business. Understanding CLTV helps prioritize customer retention strategies.
Creating Interactive Dashboards and Reports
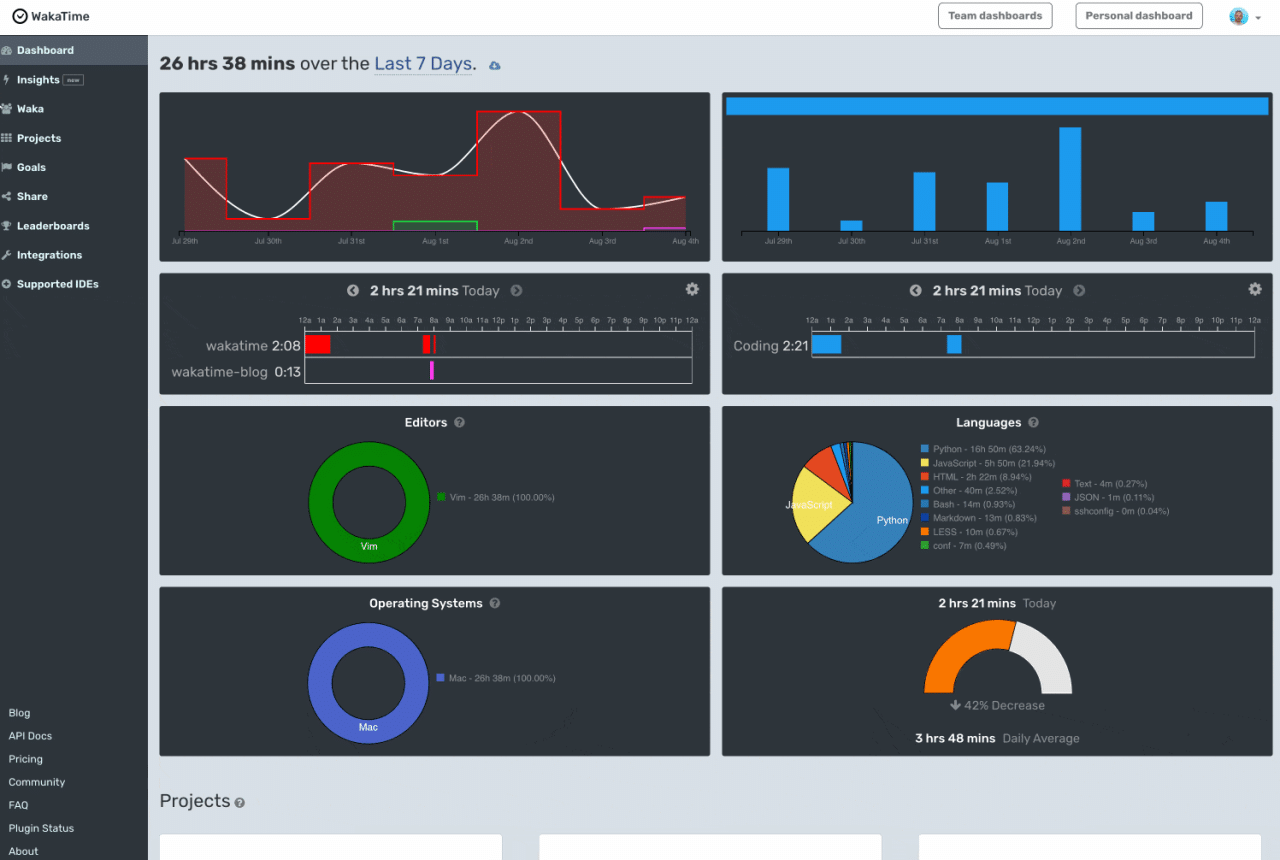
Interactive dashboards and reports are essential for visualizing the insights derived from a unified digital behavior dataset. A well-designed dashboard provides a clear, concise overview of key performance indicators, allowing stakeholders to quickly grasp the current state of digital engagement. For example, a dashboard could display real-time website traffic, conversion rates, and user engagement metrics using charts and graphs.To illustrate user engagement trends, we can create a line chart showing website traffic over time.
This chart would have “Date” on the x-axis and “Number of Unique Visitors” on the y-axis. The line itself would represent the daily or weekly traffic fluctuations. Adding a second line representing conversion rates would allow for a comparison of traffic and conversions. This visual representation quickly highlights periods of high traffic with low conversions, suggesting potential areas for optimization.
Further, interactive elements such as filtering by specific user segments or date ranges allow for deeper analysis and customized views. For example, segmenting the data by geographic location could reveal regional variations in user behavior, informing targeted marketing strategies.
Security and Privacy Considerations: Need Digital Behavior Insights Consider A Single Code Base Solution
Consolidating digital behavior data into a single codebase offers significant analytical advantages, but it also presents substantial security and privacy challenges. The potential for data breaches is amplified when a large volume of sensitive information resides in a centralized location. Robust security measures and a commitment to privacy compliance are paramount to mitigate these risks and maintain user trust.The increased risk of a single point of failure necessitates a multi-layered security approach.
A breach of this central database could expose a vast amount of user data, leading to significant legal and reputational damage. Therefore, proactive measures are crucial to protect against unauthorized access, data loss, and misuse.
Data Encryption and Secure Storage
Data encryption is essential to protect sensitive information both in transit and at rest. This involves using strong encryption algorithms like AES-256 to scramble data, rendering it unreadable without the correct decryption key. Secure storage mechanisms, such as employing cloud providers with robust security certifications (like ISO 27001 and SOC 2) or using on-premise solutions with rigorous physical and logical security controls, are equally crucial.
For example, implementing database encryption at the field level ensures that even if a database is compromised, individual data points remain protected.
Compliance with Data Privacy Regulations
Adherence to regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) is non-negotiable. These regulations dictate how personal data should be collected, processed, stored, and protected. Compliance necessitates implementing mechanisms for data subject access requests (DSARs), allowing users to access, correct, or delete their data. Data minimization, only collecting the data absolutely necessary, and purpose limitation, using data only for its intended purpose, are key principles to follow.
Regular privacy impact assessments (PIAs) should be conducted to identify and mitigate potential risks. Failure to comply can result in substantial fines and reputational harm. For instance, a company failing to implement appropriate data security measures under GDPR could face fines up to €20 million or 4% of annual global turnover.
Data Access Control and User Authentication
Implementing robust access control mechanisms is vital to prevent unauthorized access to sensitive data. This involves using role-based access control (RBAC), where users are granted access privileges based on their roles and responsibilities within the organization. Strong authentication methods, such as multi-factor authentication (MFA), should be employed to verify user identities before granting access. Regular security audits and penetration testing should be conducted to identify and address vulnerabilities in the system.
For example, limiting access to production databases to only authorized personnel with appropriate security credentials and logging all access attempts can significantly reduce the risk of unauthorized data access.
Scalability and Maintainability of the Single Code Base
Building a single code base for digital behavior insights offers significant advantages, but its success hinges on careful planning for scalability and maintainability. Ignoring these aspects can lead to a monolithic system that’s difficult to update, expand, and ultimately, maintain, negating the initial benefits of a unified approach. This section Artikels strategies for ensuring our single code base remains robust and adaptable as data volumes and user traffic increase.We need a proactive approach to ensure our system scales efficiently and remains manageable.
This involves strategic planning for handling increased data, designing robust performance monitoring, and implementing effective maintenance strategies. Ignoring these aspects can lead to performance bottlenecks, increased development time, and ultimately, a system that fails to meet its objectives.
Scaling the Single Code Base
A well-defined scaling strategy is crucial. We should anticipate future growth and design the system to accommodate it gracefully. This involves several key considerations. Firstly, we’ll employ a microservices architecture, breaking down the monolithic codebase into smaller, independent services. Each service can be scaled independently based on its specific needs.
For example, the data ingestion service might require more resources than the data visualization service. This allows for efficient resource allocation and prevents performance bottlenecks in one area from impacting others. Secondly, we’ll leverage cloud-based infrastructure, utilizing services like AWS, Azure, or GCP to easily scale our resources up or down based on demand. This dynamic scaling ensures optimal performance during peak usage while minimizing costs during periods of low activity.
Finally, we’ll implement database sharding to distribute data across multiple databases. This approach prevents performance degradation as the data volume grows, allowing for faster query times and improved overall system responsiveness. For example, we might shard user data based on geographical location, ensuring that queries targeting a specific region only access the relevant database shard.
Performance Monitoring and Management
Real-time performance monitoring is essential for identifying and addressing potential issues before they impact users. We’ll implement a comprehensive monitoring system that tracks key metrics such as response times, error rates, resource utilization (CPU, memory, network), and database query performance. Tools like Prometheus and Grafana can provide real-time dashboards visualizing these metrics, allowing for proactive identification of performance bottlenecks.
Automated alerts will notify the development team of significant deviations from established baselines, enabling rapid response and mitigation of potential issues. Regular performance testing, including load testing and stress testing, will simulate real-world scenarios to identify potential weaknesses and ensure the system can handle expected and unexpected surges in traffic.
Maintaining the Single Code Base
Maintaining a large code base requires a structured approach. We’ll utilize a robust version control system like Git, employing a branching strategy that allows for parallel development and seamless integration of new features and bug fixes. This ensures that changes are tracked, allowing for easy rollback if necessary. Regular code reviews will ensure code quality and consistency, minimizing the risk of introducing bugs or inconsistencies.
Automated testing, including unit tests, integration tests, and end-to-end tests, will provide a safety net, verifying the correctness of the code and detecting regressions early in the development process. Finally, we’ll dedicate resources to ongoing code refactoring, improving code structure and readability over time. This proactive approach prevents technical debt from accumulating, ensuring the code base remains maintainable and adaptable in the long term.
For example, we might refactor sections of code to improve modularity, making it easier to understand, modify, and extend the functionality of the system.
Case Studies and Real-World Examples
While the theoretical advantages of a single code base for digital behavior insights are compelling, real-world applications provide the most convincing evidence. Examining successful implementations allows us to understand the practical benefits, challenges encountered, and valuable lessons learned during the process. This section presents case studies highlighting the successes and challenges of organizations adopting this approach.
Several organizations across various sectors have embraced the single code base strategy for digital behavior insights. These case studies illustrate the diverse applications and the significant impact achievable through a unified approach to data collection, analysis, and visualization. The common thread among these examples is a commitment to streamlined processes and efficient resource allocation, leading to more effective insights and improved decision-making.
Case Study: A Large E-commerce Platform, Need digital behavior insights consider a single code base solution
This multinational e-commerce company implemented a single code base for its digital behavior insights platform to improve customer experience and personalize recommendations. The transition involved migrating disparate data sources and analytical tools onto a unified platform. Benefits included reduced data silos, improved data quality, and faster processing times, resulting in more timely and relevant recommendations to customers. Challenges included integrating legacy systems and ensuring data consistency across the new platform.
The key takeaway is the importance of thorough planning and a phased implementation approach to minimize disruption and maximize success.
Case Study: A Global Financial Institution
A major global bank adopted a single code base to enhance its fraud detection capabilities. By centralizing data from various banking systems, the institution was able to build a more comprehensive and accurate fraud detection model. This resulted in a significant reduction in fraudulent transactions and improved overall security. The primary challenge was ensuring data security and compliance with strict regulatory requirements.
A crucial lesson learned was the need for robust security measures and rigorous testing throughout the development and deployment process.
The following list summarizes key takeaways from these and similar case studies:
- Careful Planning is Crucial: Thorough planning and a well-defined implementation strategy are essential for a successful transition to a single code base.
- Phased Rollout Minimizes Disruption: A phased approach allows for incremental improvements and reduces the risk of significant disruptions to ongoing operations.
- Data Quality is Paramount: Ensuring data quality and consistency across the entire platform is vital for accurate insights and reliable decision-making.
- Security and Compliance are Non-Negotiable: Robust security measures and adherence to relevant regulations are crucial, especially when dealing with sensitive data.
- Continuous Monitoring and Improvement are Necessary: Regular monitoring and iterative improvements are necessary to maintain the effectiveness and efficiency of the single code base.
Closing Notes
Building a single code base for digital behavior insights isn’t a quick fix, but the long-term benefits are undeniable. By consolidating your data and streamlining your analysis, you gain a powerful advantage in understanding your users and optimizing your digital presence. While challenges exist, particularly in data security and scalability, careful planning and a well-designed architecture can mitigate these risks.
The resulting clarity and actionable intelligence will make the effort worthwhile, providing a competitive edge in today’s fast-paced digital landscape.
Query Resolution
What are the biggest challenges in implementing a single code base solution?
The biggest challenges often involve data migration, ensuring data consistency across different sources, maintaining data security and privacy, and scaling the system to handle increasing data volumes. Careful planning and choosing the right technologies are crucial.
What programming languages are best suited for a single code base solution?
The best language depends on your team’s expertise and the specific requirements of your project. Popular choices include Python (for data analysis and machine learning), Java (for scalability and enterprise applications), and JavaScript (for front-end interactions and data visualization).
How much does it cost to implement a single code base solution?
The cost varies significantly depending on the complexity of your project, the size of your data, the number of data sources, and the expertise of your development team. A detailed cost analysis is essential before starting the project.
What are some examples of open-source tools that can help?
Many open-source tools can assist, including databases like PostgreSQL and MySQL, data processing frameworks like Apache Kafka and Apache Spark, and visualization libraries like D3.js and Plotly.
