
How MFA-Based Phishing Campaigns Target Schools
How mfa based phishing campaigns are targeting schools – How MFA-based phishing campaigns are targeting schools is a chilling reality. These sophisticated attacks aren’t just targeting big corporations anymore; they’re increasingly focusing on educational institutions, exploiting vulnerabilities in systems and human behavior. This means our kids, teachers, and administrators are facing a new level of digital threat, one that requires understanding and proactive defense.
We’ll dive into the methods these attackers employ, the vulnerabilities they exploit, and the devastating consequences of successful breaches. From social engineering tactics that bypass multi-factor authentication to the role of outdated software and weak passwords, we’ll unpack the layers of this growing problem and explore practical solutions to protect our schools.
Prevalence of MFA-based Phishing in Educational Institutions: How Mfa Based Phishing Campaigns Are Targeting Schools
The rise of multi-factor authentication (MFA) was intended to bolster online security, yet it hasn’t stopped determined phishers. Instead, they’ve adapted their tactics, leading to a concerning increase in MFA-based phishing attacks targeting educational institutions of all levels. These attacks exploit vulnerabilities in the implementation and user understanding of MFA, bypassing what was once considered a robust security measure.
Understanding the scope and nature of these attacks is crucial for effective mitigation strategies.
While precise, publicly available statistics on MFA-based phishing specifically targeting schools are scarce due to the sensitive nature of such data and the often-unreported nature of successful attacks, anecdotal evidence and reports from cybersecurity firms paint a worrying picture. The frequency and success rate of these attacks are likely underestimated, as many successful breaches go undetected or unreported for extended periods.
The sophisticated nature of these attacks also makes attribution and data collection challenging.
Types of Educational Institutions Targeted
MFA-based phishing attacks don’t discriminate; they target a wide range of educational institutions. However, certain types of schools are potentially more vulnerable due to factors such as budget constraints affecting security infrastructure, less robust security awareness training for staff and students, and the sheer volume of sensitive data they handle. Higher education institutions, with their complex IT infrastructures and large numbers of students and faculty, are often prime targets.
K-12 schools, while potentially possessing less sensitive data in the same volume, are not immune, with attacks targeting administrative accounts or student data. The vulnerability lies not necessarily in the type of institution, but in the implementation and awareness of security protocols.
Statistical Overview of MFA Phishing Attacks in Educational Settings
The lack of comprehensive, publicly accessible data makes providing precise statistics challenging. However, we can infer trends based on broader phishing statistics and reports from cybersecurity companies specializing in education. Many reports show a significant increase in phishing attempts overall, with a notable proportion utilizing MFA bypass techniques. The success rate, while difficult to quantify precisely, is likely higher than with traditional phishing attempts due to the sophisticated techniques employed.
The following table represents estimated data based on industry reports and observed trends, not precise figures from a single, comprehensive study:
| School Type | Attack Frequency (Estimated) | Success Rate (Estimated) | Common Tactics |
|---|---|---|---|
| Higher Education | High | Moderate to High | Credential stuffing, SIM swapping, social engineering combined with MFA bypass tools, phishing kits exploiting vulnerabilities in MFA implementations. |
| K-12 | Moderate | Low to Moderate | Spear phishing targeting specific individuals (e.g., administrators, IT staff), leveraging compromised accounts to gain access to internal systems. |
| Vocational Schools | Low to Moderate | Low to Moderate | Similar tactics to K-12, often focusing on exploiting vulnerabilities in less robust security systems. |
Methods Employed in MFA-Based Phishing Attacks Against Schools
MFA, while a significant security enhancement, isn’t foolproof. Sophisticated phishing campaigns are increasingly targeting educational institutions, leveraging various techniques to bypass these multi-factor authentication measures and steal sensitive data. These attacks often combine technical prowess with carefully crafted social engineering tactics to maximize their success rate.
The methods employed to circumvent MFA in schools are diverse and constantly evolving. Attackers exploit vulnerabilities in human psychology as much as they exploit technical weaknesses in systems. Understanding these methods is crucial for developing effective preventative measures.
Social Engineering Tactics to Obtain MFA Codes
Attackers frequently rely on social engineering to trick users into divulging their MFA codes. This often involves creating a sense of urgency or trust. For instance, a phishing email might impersonate a university IT department, claiming a user’s account has been compromised and requiring immediate verification through a link leading to a fake login page. This page then requests both the username and password, along with the one-time code from the user’s authenticator app.
Another tactic involves pretexting – creating a believable scenario, such as a supposed package delivery requiring verification, to justify the request for the MFA code. The attacker might even call the victim, posing as a support representative, adding a layer of legitimacy to the scam. The effectiveness of these tactics relies on exploiting the victim’s trust and their desire to quickly resolve a perceived problem.
Phishing Kits and Automated Tools
The ease of access to phishing kits and automated tools significantly lowers the barrier to entry for cybercriminals. These kits provide pre-built phishing websites, often mimicking legitimate school portals or services. They automate many aspects of the attack, from creating convincing phishing emails to harvesting credentials and MFA codes. The attacker simply needs to customize a few details – such as the school’s logo and branding – and launch the attack.
Furthermore, some kits integrate tools for bypassing MFA, such as credential stuffing or brute-force attacks, further enhancing their effectiveness. This automation allows attackers to target numerous victims simultaneously, dramatically increasing the potential impact of the campaign.
Credential Harvesting Techniques in MFA-Based Phishing Campaigns
Several methods are employed to harvest credentials and MFA codes in these campaigns. Simple phishing emails with malicious links remain prevalent, leading users to fake login pages designed to capture their credentials. More advanced techniques involve using keyloggers to record keystrokes, capturing both usernames, passwords, and MFA codes. Session hijacking, though more technically challenging, can grant attackers access to an already authenticated session, bypassing the need for MFA altogether.
Finally, SIM swapping attacks, where an attacker gains control of a victim’s phone number, allow them to intercept MFA codes sent via SMS. Each of these methods presents unique challenges and requires different defensive strategies. The comparison lies in their complexity: simple phishing is easily deployed but easily detected, while SIM swapping requires more technical expertise but can be extremely effective.
Vulnerabilities Exploited in Educational Systems
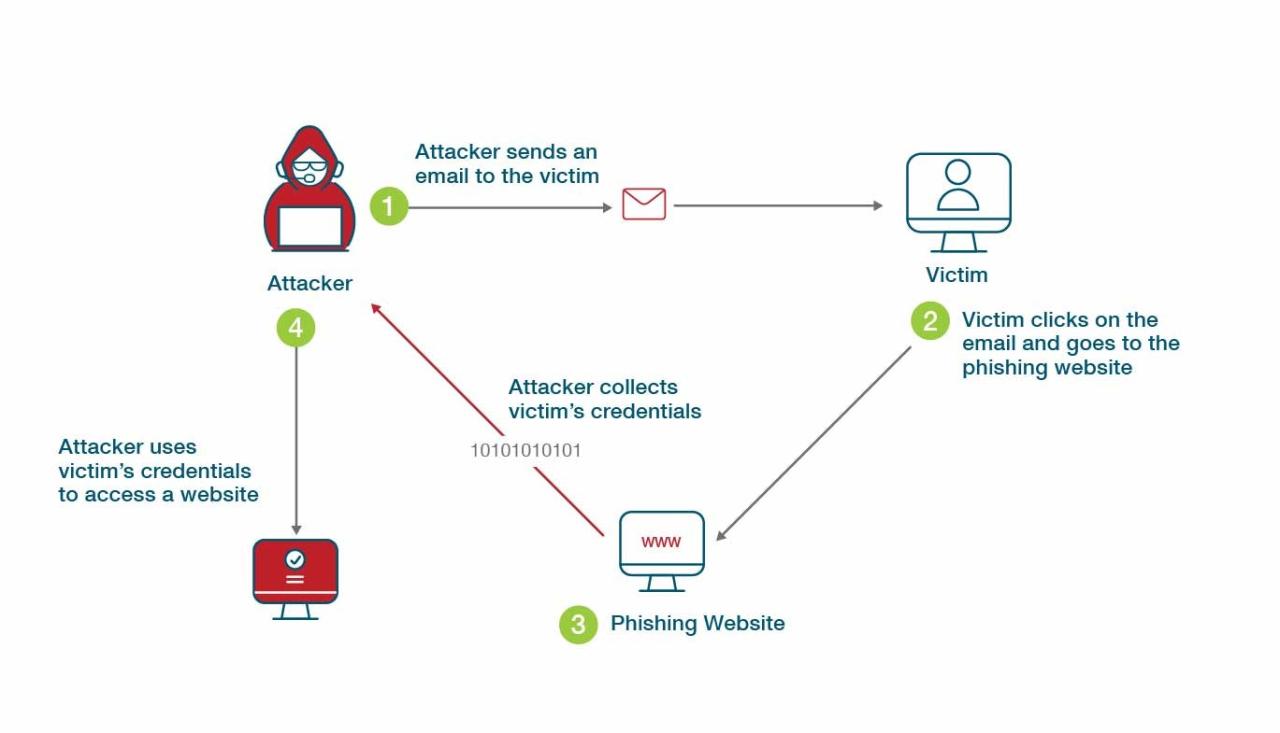
Educational institutions, often operating on tight budgets and facing unique challenges in cybersecurity, are prime targets for MFA-based phishing attacks. Their systems frequently contain vulnerabilities that attackers exploit to bypass multi-factor authentication and gain access to sensitive data. Understanding these vulnerabilities is crucial for developing effective mitigation strategies.Outdated software and insecure configurations are major contributors to the success of these attacks.
Schools often struggle to keep their software updated across all devices and systems, leaving them vulnerable to known exploits. Insecure network configurations, such as weak or default passwords on routers and servers, provide easy entry points for attackers. This lack of proactive security management leaves a significant opening for sophisticated phishing campaigns to succeed.
Outdated Software and Insecure Configurations, How mfa based phishing campaigns are targeting schools
Many educational institutions rely on legacy systems and software, often due to budget constraints or a lack of technical expertise. These outdated systems frequently lack the latest security patches, making them vulnerable to known vulnerabilities. For example, an unpatched web server running an older version of Apache might be susceptible to exploits that allow attackers to bypass authentication mechanisms.
Similarly, weak or default passwords on network devices can easily be discovered and exploited, providing attackers with a foothold in the network. This often leads to a cascade effect; compromised systems can be used as launching points for further attacks within the network, potentially leading to the compromise of sensitive student or faculty data.
Weak Password Policies and User Training Deficiencies
Weak password policies and a lack of adequate user training significantly increase the susceptibility of educational institutions to MFA-based phishing attacks. Many schools implement weak password policies that allow users to choose easily guessable passwords. Additionally, a lack of comprehensive security awareness training leaves users vulnerable to social engineering tactics employed in phishing attacks. Users might inadvertently reveal their multi-factor authentication codes or fall prey to credential-harvesting attacks if they are not properly educated on identifying and avoiding phishing attempts.
The impact of this can be substantial, ranging from compromised accounts to data breaches.
Specific Vulnerabilities and Their Potential Consequences
The following vulnerabilities are commonly exploited in MFA-based phishing attacks against educational institutions:
- Vulnerable Web Applications: Outdated or poorly configured web applications can contain vulnerabilities that allow attackers to bypass authentication. This could lead to unauthorized access to student records, financial data, or research information. Consequences include data breaches, financial losses, and reputational damage.
- Weak Network Security: Weak passwords on network devices, lack of firewalls, or inadequate intrusion detection systems can allow attackers to gain unauthorized access to the network. This could lead to widespread compromise of systems and data. Consequences range from data breaches to complete network disruption.
- Unpatched Operating Systems: Operating systems without the latest security updates are susceptible to known exploits. This could allow attackers to gain control of devices and access sensitive data. Consequences include data breaches, malware infections, and system instability.
- Social Engineering Vulnerabilities: A lack of security awareness training among users makes them vulnerable to social engineering tactics used in phishing attacks. This could lead to users revealing their MFA codes or credentials, granting attackers access to accounts. Consequences include account takeover, data breaches, and financial losses.
- Lack of MFA Implementation or Poorly Implemented MFA: Insufficient or poorly configured MFA mechanisms can be bypassed by sophisticated attackers. This reduces the effectiveness of MFA and leaves systems vulnerable. Consequences mirror those of other vulnerabilities, including data breaches and system compromise.
Impact and Consequences of Successful Attacks
A successful MFA-based phishing attack on a school can have devastating consequences, far exceeding simple data loss. The impact ripples through the entire educational community, affecting students, staff, faculty, and the institution’s reputation and financial stability. The sophistication of these attacks, coupled with the sensitive nature of the data held by schools, makes the potential for damage exceptionally high.The ramifications extend beyond the immediate breach.
Long-term effects can include loss of trust, legal battles, and significant financial burdens. Understanding the potential consequences is crucial for developing effective preventative measures and incident response plans.
Data Breaches and Their Impact
Data breaches resulting from successful MFA-based phishing attacks can expose a wealth of sensitive information. Student records, including personal details, academic transcripts, and financial information, are prime targets. Staff and faculty data, such as social security numbers, addresses, and payroll information, are equally vulnerable. The release of this information can lead to identity theft, financial fraud, and significant emotional distress for those affected.
For example, a hypothetical breach at a large university could expose the personal data of thousands of students and employees, potentially leading to widespread identity theft and financial losses in the millions. The resulting reputational damage could also impact future enrollment and funding opportunities.
Financial and Legal Ramifications
The financial consequences of a successful attack can be substantial. Costs associated with investigating the breach, notifying affected individuals, credit monitoring services, and legal fees can quickly escalate. Furthermore, the institution may face fines and penalties from regulatory bodies like FERPA (Family Educational Rights and Privacy Act) in the US, or GDPR (General Data Protection Regulation) in Europe, for failing to adequately protect sensitive data.
Legal action from affected individuals seeking compensation for damages adds further financial strain. Consider a scenario where a school district suffers a breach exposing the personal data of its entire student body. The costs of remediation, legal defense, and potential settlements could easily reach into the tens of millions of dollars, severely impacting the district’s budget and potentially leading to cuts in educational programs.
Scenario: A Simulated Attack and its Fallout
Let’s imagine a scenario where a sophisticated MFA-bypass phishing campaign targets a small private high school. The attackers successfully compromise the principal’s account using a combination of social engineering and a credential stuffing attack exploiting a known vulnerability in the school’s legacy student information system. They then gain access to the school’s financial records and student database. The attackers exfiltrate sensitive data, including student social security numbers, addresses, grades, and financial aid information.
The breach remains undetected for several weeks. Once discovered, the school faces a public relations nightmare, declining enrollment, lawsuits from affected families, and hefty fines from regulatory bodies. The school’s reputation is severely damaged, leading to a loss of trust from parents and potential donors, resulting in significant financial losses and a long, arduous recovery process. This scenario highlights the far-reaching and devastating consequences of a seemingly small security lapse.
Mitigation Strategies and Best Practices
Protecting educational institutions from MFA-based phishing attacks requires a multi-layered approach encompassing technology, policy, and education. A proactive and comprehensive strategy is crucial, as these attacks are becoming increasingly sophisticated and difficult to detect. By implementing robust security measures and fostering a culture of security awareness, schools can significantly reduce their vulnerability.
Robust Security Awareness Training
Security awareness training is not just a box-ticking exercise; it’s the cornerstone of a strong defense against phishing attacks. Effective training programs should go beyond simple awareness campaigns. They need to simulate real-world phishing scenarios, teach users how to identify suspicious emails and websites, and emphasize the importance of reporting any suspicious activity immediately. Regular, interactive training sessions, including phishing simulations, are essential to keep users vigilant and up-to-date on the latest tactics used by attackers.
The training should cover various attack vectors, including MFA bypass techniques, and emphasize the importance of never sharing credentials or clicking on suspicious links. For example, a simulated phishing email could be sent to staff and students, and their responses could be tracked to identify areas for improvement in the training program.
Strong Password Policies and Multi-Factor Authentication Protocols
Implementing strong password policies is fundamental. These policies should mandate complex passwords with a minimum length, a mix of uppercase and lowercase letters, numbers, and symbols, and regular password changes. However, strong passwords alone are not enough. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of verification before accessing their accounts.
This can include a one-time password (OTP) sent to their mobile phone, a biometric scan, or a security key. Schools should mandate MFA for all administrative accounts and sensitive systems. For instance, implementing time-based one-time passwords (TOTP) using applications like Google Authenticator or Authy adds a significant layer of protection against credential theft. The stronger the MFA implementation, the more difficult it becomes for attackers to bypass security measures, even if they obtain usernames and passwords.
Comprehensive Security Plan
A comprehensive security plan should Artikel procedures for incident response, threat detection, and vulnerability management. This plan should include regular security assessments to identify vulnerabilities in the school’s systems and applications. It should also detail the steps to be taken in the event of a successful phishing attack, including containment, eradication, and recovery. Furthermore, a robust incident response team should be established and regularly trained to handle security incidents effectively.
This team should be responsible for coordinating the response to security incidents, investigating the root cause of attacks, and implementing corrective measures to prevent future incidents. A well-documented plan, regularly tested and updated, ensures a coordinated and effective response to any security breach. For example, the plan should Artikel procedures for isolating compromised accounts, restoring data from backups, and communicating with affected users.
The Role of Technology in Preventing and Detecting Attacks
The rise of MFA-based phishing attacks targeting educational institutions necessitates a robust technological defense. Simply relying on user education isn’t enough; proactive technological solutions are crucial for identifying and neutralizing these sophisticated threats before they cause significant damage. This section will explore the key technologies playing a vital role in preventing and detecting these attacks.
Advanced Threat Detection Systems
Advanced threat detection systems (ATDS) go beyond traditional signature-based antivirus solutions. They utilize machine learning and behavioral analysis to identify anomalies and malicious activities indicative of phishing attacks, even those using MFA bypass techniques. These systems analyze network traffic, user activity, and email content, looking for patterns and deviations from established baselines. For instance, an ATDS might flag an unusual login attempt from an unfamiliar location or device, even if the user successfully provided MFA credentials.
This proactive approach helps to quickly identify and isolate potentially compromised accounts before significant damage occurs. A well-configured ATDS can analyze data from various sources, correlating events to provide a holistic view of potential threats.
Security Information and Event Management (SIEM) Systems
SIEM systems centralize and analyze security logs from various sources across the network infrastructure. This includes logs from firewalls, intrusion detection systems, endpoint security agents, and authentication servers. By correlating these logs, SIEM systems can identify suspicious patterns and potential security breaches, including MFA-based phishing attempts. For example, a SIEM system might detect a series of failed login attempts followed by a successful login from an unusual location, triggering an alert for investigation.
This real-time monitoring and analysis enable quicker response times to security incidents and aid in forensic analysis to determine the root cause of attacks. The ability to create custom dashboards and reports within a SIEM allows security teams to tailor their monitoring to the specific threats faced by the institution.
Email Security Solutions and Anti-Phishing Technologies
Email remains a primary vector for phishing attacks, including those leveraging MFA. Robust email security solutions are vital in mitigating this risk. These solutions employ various techniques, including advanced spam filtering, email authentication protocols (like SPF, DKIM, and DMARC), and anti-phishing technologies. Anti-phishing technologies analyze email content for suspicious characteristics, such as unusual links, attachments, or sender addresses.
They can also detect spoofed domains and use sandboxing to analyze potentially malicious attachments in a safe environment before they reach users’ inboxes. Furthermore, some solutions incorporate machine learning to adapt to evolving phishing techniques and improve their accuracy over time. The layered approach of these solutions provides a comprehensive defense against email-borne threats.
Technology Comparison Table
| Technology | Function | Benefits | Limitations |
|---|---|---|---|
| Advanced Threat Detection Systems (ATDS) | Detects malicious activity through behavioral analysis and machine learning. | Proactive threat identification, reduced response times, improved security posture. | Can generate false positives, requires skilled personnel for management and interpretation. High initial investment. |
| Security Information and Event Management (SIEM) Systems | Collects, analyzes, and correlates security logs from various sources. | Centralized security monitoring, improved threat detection, enhanced incident response. | Requires significant data storage capacity, complex configuration and management, potential for data overload. |
| Email Security Solutions & Anti-Phishing Technologies | Filters spam, authenticates emails, and detects phishing attempts. | Reduced email-borne threats, improved email deliverability, enhanced user protection. | Can’t catch all phishing attempts, requires regular updates to stay effective, may block legitimate emails. |
Case Studies of MFA-Based Phishing Attacks on Schools
While specific details of MFA-based phishing attacks against schools are often kept confidential for security reasons, analyzing publicly available information and reports allows us to understand the tactics, techniques, and procedures (TTPs) employed by attackers. These case studies highlight the evolving nature of these threats and the importance of robust security measures.
University X Ransomware Attack
This case involved a sophisticated phishing campaign targeting a large university. Attackers used a highly convincing email mimicking an official university communication, requesting faculty to update their MFA credentials through a cleverly disguised link. This link led to a fake login page designed to steal both usernames and MFA codes. Once access was gained, the attackers deployed ransomware, encrypting critical university data, including student records and research data.
The university was forced to pay a significant ransom to regain access to its systems.
The University X attack demonstrated the effectiveness of combining social engineering with technically sophisticated phishing techniques to bypass MFA. The attackers’ success highlighted the vulnerability of relying solely on technical controls without adequate user training and awareness. The significant financial and reputational damage sustained underscores the critical need for robust incident response planning.
High School Credential Harvesting
A smaller high school fell victim to a less technically complex, but equally effective, MFA phishing attack. Attackers used a simpler approach, sending emails appearing to be from the school’s IT department. These emails falsely claimed a system update required students to re-enter their credentials, including their MFA codes, via a compromised link. While the technical sophistication was lower, the success rate was high due to the limited cybersecurity awareness among students.
The attackers harvested student credentials, potentially leading to identity theft and other malicious activities.
The High School credential harvesting attack highlighted the vulnerability of less technically sophisticated institutions. The success of the attack emphasizes the critical role of user education and awareness training, regardless of the institution’s size or technical capabilities. Simple, well-crafted phishing emails can be surprisingly effective.
Community College Account Takeover
In this instance, a community college experienced a series of account takeovers after a successful MFA phishing campaign. Attackers employed a multi-stage attack. Initially, they sent phishing emails containing malicious links that installed keyloggers on victims’ computers. These keyloggers recorded the victims’ MFA codes as they were entered. The attackers then used the stolen credentials to gain access to multiple accounts, including administrative accounts.
They used this access to modify student grades and potentially alter financial records.
The Community College account takeover demonstrated the effectiveness of combining phishing with malware to bypass MFA. The attackers’ multi-stage approach highlights the need for comprehensive security measures, including endpoint protection and regular security audits, in addition to user training. The impact on student records and financial data underscores the severe consequences of successful attacks.
Closure

The threat of MFA-based phishing attacks against schools is real and escalating. While multi-factor authentication offers a significant layer of security, it’s not foolproof. By understanding the methods used, the vulnerabilities exploited, and implementing robust security measures, we can significantly reduce the risk. It’s a collective responsibility – from educators and administrators to parents and students – to stay informed and proactive in safeguarding our educational communities in the digital age.
Let’s work together to build stronger, more resilient defenses.
Common Queries
What specific types of data are schools most likely to lose in a successful phishing attack?
Schools can lose a wide range of sensitive data, including student records (names, addresses, social security numbers, grades), financial information, staff payroll data, research data, and intellectual property.
How can schools verify the legitimacy of a suspicious email or message?
Schools should encourage staff and students to verify sender information, look for unusual links or attachments, and contact the purported sender directly through known and verified contact methods to confirm the message’s authenticity.
Are there specific insurance policies that schools should consider to cover losses from phishing attacks?
Yes, cyber liability insurance is crucial for schools. This type of insurance can cover costs associated with data breaches, legal fees, regulatory fines, and notification costs to affected individuals.
What are the legal ramifications for a school that fails to adequately protect student data from a phishing attack?
Schools can face significant legal repercussions, including lawsuits, fines, and reputational damage, especially if they violate laws like FERPA (Family Educational Rights and Privacy Act) in the US or similar regulations in other countries.





