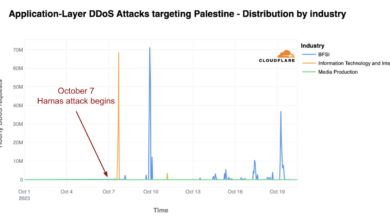
Ransomwares Healthcare Impact A Deep Dive
How ransomware impacts healthcare organizations is a critical issue demanding immediate attention. The digital systems of hospitals and clinics are increasingly vulnerable to cyberattacks, disrupting patient care, and jeopardizing sensitive data. This in-depth look examines the multifaceted challenges posed by ransomware, from financial losses and operational disruptions to patient safety concerns and legal ramifications.
Understanding the specific vulnerabilities of healthcare organizations, the various attack methods, and the financial and operational impacts is paramount to developing effective prevention and mitigation strategies. This exploration will cover the crucial steps in a robust cybersecurity plan, emphasizing the importance of employee training, regular backups, and well-defined incident response procedures.
Ransomware in Healthcare: A Growing Threat
Ransomware, a type of malicious software, encrypts digital systems, demanding payment in exchange for decryption keys. This disruption can have catastrophic consequences, particularly in critical infrastructure sectors like healthcare. The sensitive nature of patient data and the essential services provided make healthcare organizations especially vulnerable to these attacks. Data breaches can lead to compromised patient records, operational disruptions, and even loss of life.The digital infrastructure of healthcare organizations is complex and interconnected, making them prime targets for cybercriminals.
This interconnectedness, while essential for efficiency, creates pathways for malicious actors to exploit vulnerabilities and disrupt services. Furthermore, the constant need to update and maintain systems often leaves organizations with unpatched vulnerabilities, which attackers can easily exploit.
Vulnerabilities of Healthcare Organizations
Healthcare organizations face unique vulnerabilities due to their reliance on interconnected systems and the sensitive data they handle. These systems often contain a large volume of confidential patient data, including medical records, financial information, and personal details. The constant need to integrate new technologies and maintain existing systems creates a complex environment with potential entry points for attackers.
Types of Ransomware Attacks
Ransomware attacks targeting healthcare organizations can take various forms. These attacks often aim to disrupt critical services and extract financial gain. One common type is encrypting critical patient data, rendering it inaccessible until a ransom is paid. Another type involves encrypting the entire network, disrupting all operations. A third type may involve exfiltrating sensitive data before encrypting it, increasing the threat of data breaches and further financial losses.
Examples of Successful Attacks
Numerous successful ransomware attacks have targeted healthcare facilities. These attacks have resulted in significant disruptions to patient care, financial losses, and reputational damage. One example involved a hospital whose systems were crippled, delaying critical surgeries and potentially jeopardizing patient lives. Another example illustrates how attackers not only encrypted the data but also stole it, creating a dual threat of financial and reputational damage.
The threat of data breaches, and even the potential for blackmailing, creates a very dangerous situation.
Methods of Infiltration
Understanding how ransomware infiltrates healthcare systems is crucial for developing effective security measures. The following table Artikels common methods used by attackers.
| Method | Description | Impact | Example |
|---|---|---|---|
| Phishing | Malicious emails or websites tricking users into revealing credentials or downloading malware. | Compromises user accounts, granting attackers access to sensitive data and systems. | An employee clicks a malicious link in an email pretending to be from the IT department, leading to malware infection. |
| Malware | Malicious software designed to infiltrate systems and gain unauthorized access. | Allows attackers to encrypt data, steal information, or disrupt operations. | A compromised software update installs ransomware, encrypting critical servers. |
| Exploiting vulnerabilities | Targeting known weaknesses in software or systems to gain unauthorized access. | Allows attackers to bypass security measures and gain control of systems. | A healthcare facility uses outdated software with known vulnerabilities, allowing attackers to exploit them. |
Financial and Operational Impacts: How Ransomware Impacts Healthcare Organizations
Ransomware attacks are not merely digital inconveniences for healthcare organizations; they inflict significant financial and operational damage, impacting patient care and straining resources. The costs extend far beyond the ransom payment, encompassing recovery efforts, lost productivity, and the erosion of public trust. Understanding these multifaceted impacts is crucial for developing effective mitigation strategies.The financial and operational repercussions of a ransomware attack on a healthcare facility can be devastating.
The attack’s ripple effect often extends beyond immediate financial losses, impacting the very essence of patient care. From the initial disruption of critical systems to the protracted recovery process, the damage is multifaceted and profound. This section delves into the detailed financial and operational consequences, offering practical insights into calculating the total impact and illustrating potential costs.
Financial Losses Associated with Ransomware Attacks
Healthcare organizations face substantial financial losses from ransomware attacks. These losses extend beyond the ransom itself, encompassing the costs of data recovery, system restoration, and downtime. The immediate financial blow can cripple a facility’s ability to function, impacting its financial health and long-term sustainability. Ransomware attacks can lead to substantial revenue loss, as operational disruptions and patient care delays can significantly reduce income streams.
Operational Disruption Caused by Ransomware Attacks
Ransomware attacks cause significant operational disruptions within healthcare facilities. Critical systems, such as electronic health records (EHR) and medical devices, are often targeted, disrupting the smooth flow of patient care. This disruption can lead to delays in diagnoses, treatments, and administrative processes. Consequently, patient safety and quality of care are compromised, leading to a cascade of negative consequences.
Costs Associated with Data Recovery and System Restoration
Recovering data and restoring systems after a ransomware attack involves significant costs. These costs include the expenses of specialized cybersecurity personnel, forensic investigations, and data recovery tools. The complexity of healthcare systems often leads to higher restoration costs compared to other industries. The costs of developing and implementing new security protocols to prevent future attacks should also be included.
Implications of Downtime on Patient Care
Downtime resulting from a ransomware attack can have serious implications for patient care. Delays in accessing patient records, scheduling appointments, and providing treatments can jeopardize patient safety and lead to adverse health outcomes. The impact of downtime can be especially critical in emergency situations where immediate access to patient information is crucial. The potential for negative consequences on patient health and well-being necessitates robust mitigation strategies.
Calculating the Financial Impact of a Ransomware Attack
Calculating the financial impact of a ransomware attack involves assessing various cost components. These components include the ransom payment (if made), the costs of data recovery, system restoration, and downtime, along with the cost of lost productivity and potential legal liabilities. A comprehensive assessment requires a thorough understanding of the organization’s specific vulnerabilities and the extent of the attack’s impact.
Potential Costs of Different Types of Ransomware Attacks
The financial impact of a ransomware attack varies depending on the type of attack and the organization’s vulnerability. The table below provides an illustrative overview of potential costs for different attack types. These costs are estimates and can vary based on specific circumstances.
| Attack Type | Data Recovery Cost | System Restoration Cost | Downtime Cost |
|---|---|---|---|
| Targeted Attack (Specific vulnerabilities exploited) | $50,000 – $500,000 | $25,000 – $250,000 | $10,000 – $100,000 per day |
| Phishing Attack (Vulnerable employees) | $20,000 – $200,000 | $10,000 – $100,000 | $5,000 – $50,000 per day |
| Supply Chain Attack (Third-party vendor compromise) | $100,000 – $1,000,000 | $50,000 – $500,000 | $20,000 – $200,000 per day |
Patient Safety and Privacy Concerns

Ransomware attacks on healthcare organizations pose significant risks beyond financial losses. The sensitive nature of patient data and the critical role healthcare plays in maintaining patient well-being necessitate a careful examination of the potential for harm. Compromised systems can disrupt critical operations, leading to delays in treatment, medication errors, and ultimately, jeopardizing patient safety. Beyond the immediate risks, the long-term effects on patient trust and the healthcare system’s reputation can be profound.The implications of a ransomware attack extend far beyond the immediate disruption.
Breaches of patient data can have devastating consequences, not only for the individual patients whose information is compromised, but also for the entire healthcare system. The potential for identity theft, fraud, and emotional distress is substantial, demanding proactive measures to protect patient privacy and ensure data security.
Potential Risks to Patient Safety During a Ransomware Attack
Ransomware attacks can lead to the disruption of essential services, impacting patient care in various ways. Delayed or canceled appointments, unavailability of medical records, and interruptions in vital monitoring systems are all possible outcomes. For instance, if a hospital’s electronic health records (EHR) system is compromised, clinicians may struggle to access crucial patient information, potentially leading to medication errors or inappropriate treatment decisions.
Further, if the attack targets a facility’s laboratory or imaging systems, critical diagnostic results may be unavailable, hindering timely and accurate diagnoses. These disruptions can have a direct impact on the ability to provide timely and effective care, increasing the risk of adverse health outcomes.
Privacy Implications of Sensitive Patient Data Breaches
The sensitive nature of patient data makes it a prime target for malicious actors. Information like medical history, diagnoses, treatment plans, and financial details is extremely valuable and can be used for fraudulent activities. Compromised data can lead to identity theft, insurance fraud, and financial exploitation. The psychological toll on patients whose privacy has been violated can be significant, potentially affecting their trust in the healthcare system.
Legal and Regulatory Consequences for Healthcare Organizations
Healthcare organizations face significant legal and regulatory ramifications when patient data is compromised due to a ransomware attack. Regulations like HIPAA (Health Insurance Portability and Accountability Act) in the United States mandate stringent data security measures. Failure to comply with these regulations can lead to substantial fines and penalties. The severity of penalties is often tied to the scale of the breach and the extent of the harm caused to affected individuals.
Legal repercussions may also include lawsuits from affected patients, adding to the financial and reputational damage.
Comparison of Data Security Standards Relevant to Healthcare
Numerous data security standards exist, each with specific requirements for healthcare organizations. NIST Cybersecurity Framework, ISO 27001, and HITRUST CSF are examples of standards often used by healthcare providers. These standards offer guidance on implementing robust security controls, including access controls, data encryption, and incident response plans. The choice of standards will depend on the specific needs and resources of each healthcare organization.
It’s crucial to understand the nuances of each standard and to tailor the implementation to the unique characteristics of the healthcare environment.
Potential HIPAA Violations Due to Ransomware Attacks
Ransomware attacks can lead to various HIPAA violations, potentially exposing organizations to severe penalties.
| Violation | Description | Impact |
|---|---|---|
| Unauthorized Access | Unauthorized individuals gaining access to protected health information (PHI). | Significant fines, potential lawsuits, damage to reputation. |
| Use, Disclosure, or Acquisition Without Authorization | Improper use, disclosure, or acquisition of PHI without proper authorization. | Fines, legal action, patient distrust. |
| Failure to Implement Safeguards | Failure to implement adequate security measures to protect PHI. | Significant fines, legal repercussions, potential criminal charges. |
| Breach Notification | Failure to notify affected individuals and regulatory bodies within the required timeframe. | Heavy penalties, legal action, loss of trust. |
Prevention and Mitigation Strategies
Ransomware attacks are a significant threat to healthcare organizations, jeopardizing patient care, financial stability, and operational efficiency. Proactive measures are crucial to minimize the risk and ensure business continuity. A robust cybersecurity plan, coupled with employee training and a strong incident response strategy, can significantly reduce the likelihood of successful attacks.Effective prevention strategies require a multi-faceted approach encompassing technical safeguards, employee education, and a well-defined incident response plan.
This includes implementing strong security measures, regularly backing up critical data, and having a clear protocol for handling security incidents.
Identifying Effective Strategies for Preventing Ransomware Attacks
Healthcare organizations need to employ a layered security approach to prevent ransomware attacks. This involves implementing multiple security controls, each addressing a specific threat vector. Regular security assessments and penetration testing are essential to identify vulnerabilities and weaknesses in the current security posture. A proactive approach is crucial to stay ahead of evolving ransomware tactics.
Ransomware attacks are a serious threat to healthcare organizations, disrupting critical services and potentially endangering patient safety. Protecting sensitive data and ensuring uninterrupted operations is paramount. This necessitates a proactive approach to security, like exploring solutions such as deploying AI code safety goggles, which can help identify vulnerabilities in software early in the development process. Deploying AI Code Safety Goggles Needed highlights the importance of secure coding practices.
Ultimately, bolstering cybersecurity measures across the board remains crucial to mitigate the damage ransomware can inflict on healthcare facilities.
Designing a Robust Cybersecurity Plan for Healthcare Organizations
A comprehensive cybersecurity plan is a cornerstone of preventing ransomware attacks. This plan should Artikel specific security controls, policies, and procedures for data protection and incident response. It should include a detailed risk assessment to identify potential threats and vulnerabilities, outlining mitigation strategies. This plan should be regularly reviewed and updated to adapt to emerging threats and technological advancements.
Importance of Employee Training and Awareness Programs
Employee training plays a critical role in preventing ransomware attacks. Employees are often the weakest link in an organization’s security posture. Regular training programs should focus on identifying phishing attempts, recognizing suspicious emails, and understanding proper password management practices. These programs should be ongoing, updated regularly to address evolving threats, and should include simulated phishing exercises to reinforce learning.
Different Types of Security Measures for Healthcare Systems
Healthcare systems require a combination of security measures to protect sensitive data. These include firewalls, intrusion detection systems, antivirus software, and strong access controls. Data encryption at rest and in transit is vital, ensuring confidentiality even if data is compromised. Multi-factor authentication adds an extra layer of security, demanding multiple verification methods for user access. Regular patching and updates for software and systems are also crucial to address known vulnerabilities.
Importance of Regular System Backups and Data Recovery Plans
Regular backups are essential for data recovery in case of a ransomware attack. Implementing a robust backup and recovery plan, including off-site backups, is vital. This ensures that critical data can be restored quickly and efficiently, minimizing downtime and financial losses. Testing the recovery process regularly is essential to verify its effectiveness and identify any potential issues.
Best Practices for Incident Response in the Event of a Ransomware Attack, How ransomware impacts healthcare organizations
A well-defined incident response plan is critical in the event of a ransomware attack. This plan should Artikel the steps to take to contain the attack, isolate affected systems, and restore critical data. It should also include communication protocols to inform stakeholders and patients about the situation. This plan should be tested regularly to ensure that the organization can respond effectively and minimize the impact of an attack.
Comparison of Security Software and Tools for Healthcare Organizations
| Software | Features | Benefits | Drawbacks |
|---|---|---|---|
| Sophos Intercept X | Endpoint protection, cloud threat prevention, and incident response | Comprehensive protection against malware, including ransomware | Potential for high cost compared to other solutions |
| CrowdStrike Falcon | Advanced threat detection, response, and prevention | Strong protection against advanced persistent threats (APTs) | Requires significant expertise for effective implementation |
| Palo Alto Networks | Network security, cloud security, and endpoint protection | Comprehensive security across different platforms | May have a steeper learning curve for implementation and management |
Recovery and Response Procedures

Navigating a ransomware attack requires a swift and well-orchestrated response. A healthcare organization’s ability to recover quickly and effectively is paramount, impacting not only financial stability but also patient safety and trust. A robust recovery plan minimizes disruption, mitigates damage, and ensures a return to normal operations as swiftly as possible.
Steps to Take During a Ransomware Attack
Immediately recognizing the attack is crucial. Suspected compromise of systems necessitates a rapid, coordinated response. The initial steps involve isolating affected systems to prevent further data exfiltration or damage. This includes disconnecting networks, shutting down vulnerable devices, and preventing the spread of malicious code. Security professionals should immediately begin a forensic investigation to understand the scope of the attack and the nature of the threat.
Importance of a Well-Defined Incident Response Plan
A well-structured incident response plan (IRP) is a critical component of any recovery strategy. An IRP acts as a roadmap, outlining the steps to follow during a ransomware attack. It details roles, responsibilities, communication protocols, and data recovery procedures. The plan should be regularly reviewed and updated to reflect evolving threats and best practices.
Ransomware attacks are a serious threat to healthcare organizations, disrupting critical services and potentially endangering patient safety. Understanding vulnerabilities like those detailed in the Azure Cosmos DB Vulnerability Details is crucial for proactive defense strategies. These vulnerabilities, if exploited, can be a significant factor in a ransomware attack’s success, highlighting the interconnectedness of various digital components in a healthcare system.
Ultimately, the impact on healthcare organizations from ransomware remains a significant concern, demanding continuous vigilance and robust security measures.
Roles and Responsibilities of Different Teams During a Crisis
Effective communication and clear delineation of responsibilities among various teams are essential. The IT team plays a central role in isolating affected systems and initiating data recovery. The security team investigates the incident, identifies the attack vector, and works to contain the threat. The legal team assesses legal implications and regulatory compliance. The communications team manages stakeholder relations, informing patients and the public.
A dedicated crisis management team should oversee the entire response, ensuring coordination and communication among all stakeholders.
Comprehensive Plan for Data Recovery and System Restoration
A comprehensive data recovery plan is crucial for restoring systems and data. This involves identifying and backing up critical data regularly. Implementing robust backup and recovery systems, ensuring data redundancy, and using a robust disaster recovery plan are essential. Testing the backup and recovery systems regularly is paramount to ensure successful restoration. Consider using cloud-based solutions for redundancy and off-site backups to safeguard against data loss.
Communication with Patients and Stakeholders During a Crisis
Transparency and clear communication with patients and stakeholders are vital. Patients should be informed of the situation promptly and accurately, assuring them of ongoing efforts to restore services and data security. Stakeholders, including regulatory bodies, insurers, and the media, also require regular updates. Maintaining open channels of communication fosters trust and confidence.
Flowchart Illustrating Steps for Restoring Systems After a Ransomware Attack
A flowchart is a visual representation of the steps to follow during ransomware recovery.
| Step | Action |
|---|---|
| 1 | Identify Incident: Recognize signs of ransomware attack. |
| 2 | Isolate Affected Systems: Disconnect affected systems from the network. |
| 3 | Contain the Threat: Prevent further spread of malware. |
| 4 | Notify Stakeholders: Alert patients, staff, and relevant authorities. |
| 5 | Forensic Investigation: Determine the scope of the attack and the nature of the threat. |
| 6 | Data Recovery: Implement the recovery plan, restoring critical data and systems. |
| 7 | System Restoration: Restore affected systems to their previous state. |
| 8 | Post-Incident Review: Evaluate the response and identify areas for improvement. |
Cybersecurity Insurance and Legal Considerations
Navigating the complex world of ransomware attacks requires healthcare organizations to proactively address not only the technical aspects but also the crucial legal and financial implications. Cybersecurity insurance plays a critical role in mitigating the financial fallout, while adherence to legal obligations is essential for safeguarding patient trust and reputation. Understanding these interconnected elements is vital for creating a comprehensive defense strategy.
The Role of Cybersecurity Insurance
Cybersecurity insurance is increasingly vital for healthcare organizations. It provides financial protection against the significant costs associated with a ransomware attack, including ransom payments, data restoration, legal fees, and reputational damage. This protection can be crucial in helping organizations recover and resume operations quickly. Furthermore, a robust policy can help mitigate the financial burden of compliance with legal obligations following a breach.
Legal Obligations Regarding Data Breaches
Healthcare organizations are subject to stringent legal obligations regarding data breaches, particularly under regulations like HIPAA (Health Insurance Portability and Accountability Act). These regulations mandate prompt notification of breaches to affected individuals and regulatory bodies. Failure to comply with these obligations can lead to substantial penalties and legal ramifications.
Ransomware attacks are a serious threat to healthcare organizations, disrupting vital services and potentially endangering patient safety. Fortunately, the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions which may provide some level of protection for healthcare organizations dealing with sensitive data. This is a positive development, but the constant threat of ransomware remains a significant concern for the industry.
Key Elements of a Robust Cybersecurity Insurance Policy
A robust cybersecurity insurance policy should include comprehensive coverage for various aspects of a ransomware attack. Essential components include:
- Coverage for ransom payments: This is often a critical component, allowing organizations to pay the ransom without jeopardizing their financial stability.
- Data restoration services: The policy should cover the cost of recovering encrypted data and restoring systems to a functional state.
- Legal and regulatory compliance support: This aspect covers legal fees and expert guidance during the breach response and notification process.
- Crisis management and public relations assistance: A robust policy should include support for handling the public relations aspect of a breach, helping maintain patient trust and reputation.
Legal Implications of Failing to Report a Data Breach
Failure to report a data breach promptly and accurately can have severe legal consequences. Penalties can range from significant fines to lawsuits by affected individuals, potentially leading to substantial financial losses and reputational damage. It’s crucial to establish clear procedures for reporting and notification.
Comparison of Cybersecurity Insurance Providers
Choosing the right cybersecurity insurance provider is crucial. A thorough evaluation is necessary, considering various factors such as coverage, premiums, and reputation.
| Provider | Coverage | Premiums | Reputation |
|---|---|---|---|
| Provider A | Comprehensive coverage, including ransom payments and data restoration | Competitive premiums | Strong reputation for handling complex cases |
| Provider B | Limited coverage for ransom payments, but strong in data breach response | Lower premiums | Good reputation, but less experience with large-scale incidents |
| Provider C | Excellent coverage for crisis management and public relations | Higher premiums | Known for its expertise in healthcare-specific data breaches |
Conclusion
In conclusion, ransomware poses a significant threat to the healthcare sector. Protecting sensitive patient data, maintaining operational continuity, and minimizing financial losses requires a multi-pronged approach encompassing robust cybersecurity measures, comprehensive incident response plans, and adequate insurance coverage. By proactively addressing these issues, healthcare organizations can safeguard their operations and ensure the well-being of their patients.
Clarifying Questions
What are the most common methods used to infiltrate healthcare systems?
Common methods include phishing emails, malware downloads, and exploiting software vulnerabilities. Phishing attacks often target employees with seemingly legitimate communications to trick them into revealing sensitive information or clicking malicious links. Malware can be disguised as legitimate software, secretly infecting systems. Exploiting vulnerabilities in outdated or poorly maintained software allows attackers to gain unauthorized access.
What are the financial implications of a ransomware attack on a healthcare facility?
Financial losses can be substantial, encompassing data recovery costs, system restoration expenses, and lost revenue from disrupted operations. The downtime directly impacts patient care and can lead to significant financial penalties. Furthermore, reputational damage and legal fees can also add to the financial burden.
How can healthcare organizations prevent ransomware attacks?
Implementing strong security measures, like multi-factor authentication, regular software updates, and employee training programs, is crucial. Robust security awareness training can equip employees to identify and avoid phishing attempts. Regular backups and data recovery plans are essential to minimize data loss in the event of an attack. Incident response plans, detailing the steps to take during an attack, can significantly limit the damage.
What are the legal and regulatory consequences for healthcare organizations?
Failure to comply with data protection regulations like HIPAA can result in substantial fines and legal action. Ransomware attacks that lead to data breaches may violate HIPAA regulations, which Artikel the security and privacy requirements for handling protected health information. These violations can result in penalties, legal battles, and damage to the organization’s reputation.