How Social Media Scams Drain Bank Accounts
How social media scams are draining bank accounts of victims is a chilling reality. We’re all connected online, sharing our lives and often, unknowingly, our financial details. This seemingly harmless act opens the door to sophisticated scams designed to exploit our trust and steal our hard-earned money. From cleverly disguised phishing emails to elaborate romance schemes, the methods are constantly evolving, making it crucial to understand how these scams work and how to protect ourselves.
This post delves into the dark underbelly of social media, exploring the tactics employed by scammers, the psychological vulnerabilities they exploit, and the devastating consequences for victims. We’ll examine different types of scams, from investment fraud to fake giveaways, and uncover the steps scammers take to gain access to your bank accounts. Ultimately, we’ll equip you with the knowledge and strategies to safeguard your finances in the digital age.
Types of Social Media Scams Targeting Bank Accounts
Social media’s vast reach and personal nature make it a fertile ground for scammers. They exploit our trust and connections to gain access to our financial information and ultimately, our bank accounts. Understanding the common tactics employed is crucial to protecting ourselves and our finances. This post will delve into five prevalent social media scams that lead to significant financial losses.
Five Common Social Media Scams Leading to Financial Loss
Several types of scams consistently target social media users, leading to substantial financial losses. These scams often rely on exploiting human emotions like greed, fear, or loneliness to manipulate victims. Understanding these methods is the first step towards effective prevention.
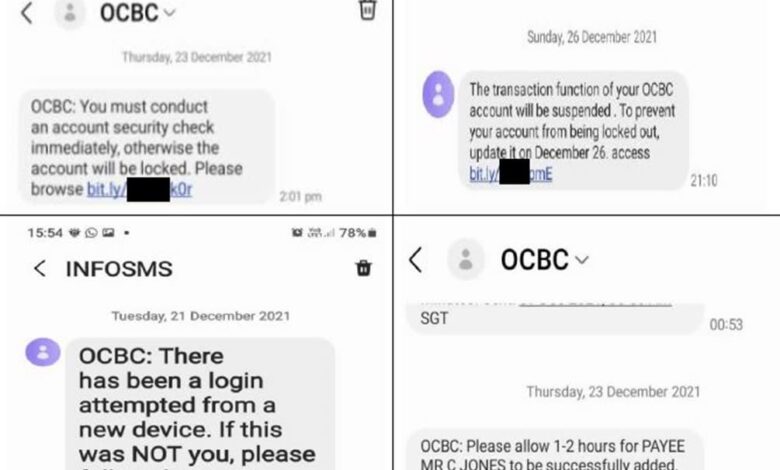
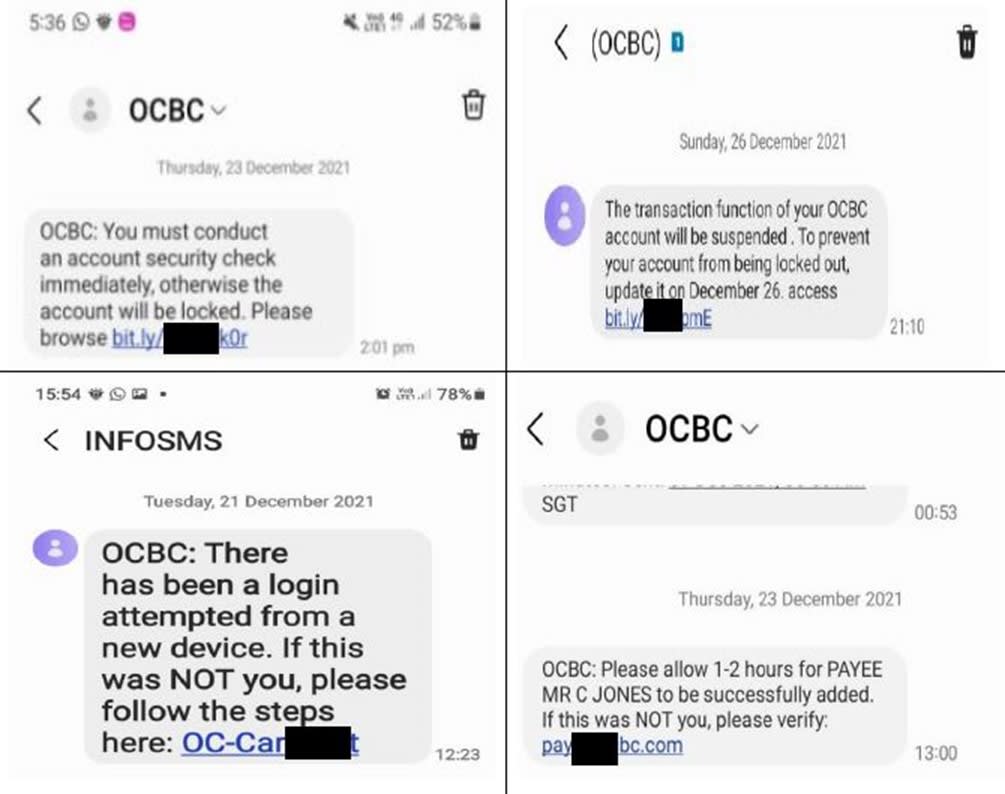
- Phishing Scams: These scams involve deceptive emails, messages, or links disguised as legitimate communications from banks, social media platforms, or other trusted entities. The goal is to trick users into revealing their login credentials, credit card details, or other sensitive information. For example, a scammer might send a message claiming your account has been compromised and direct you to a fake website that looks identical to your bank’s site to “verify” your details.
- Investment Scams: These scams promise high returns on investments with minimal risk. Scammers often create fake profiles on social media, posing as financial experts or successful investors. They lure victims into investing in non-existent or fraudulent schemes, promising quick profits. An example would be a social media influencer promoting a cryptocurrency investment opportunity with guaranteed returns, which turns out to be a pump-and-dump scheme.
- Romance Scams: These scams involve building a false romantic relationship online to gain the victim’s trust and eventually obtain money. Scammers create fake profiles, often using stolen photos, and engage in seemingly genuine interactions. They may invent elaborate stories to explain their need for financial assistance, gradually increasing their requests for money over time. A common example is a scammer posing as a foreign military personnel stationed overseas, needing money for emergency expenses or travel.
- Fake Charity Scams: These scams prey on people’s generosity by posing as legitimate charities or relief organizations, often leveraging current events to solicit donations. Scammers use social media to spread their message quickly and widely, creating fake websites and social media pages to appear authentic. A common example is a fake charity soliciting donations for disaster relief, where the funds never reach the intended recipients.
- Fake Job Scams: These scams involve offering attractive employment opportunities, often remotely, to lure victims. The scammer requests personal information or upfront fees for processing the application or for training materials. The promised job never materializes, and the victim loses both their money and personal data. An example is a social media ad promising a high-paying work-from-home position, requiring an upfront payment for training materials before starting.
Comparison of Phishing, Investment, and Romance Scams
| Scam Type | Method of Deception | Target Audience | Example |
|---|---|---|---|
| Phishing | Deceptive emails, messages, or links leading to fake websites to steal login credentials or financial information. | Anyone with online accounts and financial assets. | A fake email appearing to be from a bank, urging users to update their account details through a malicious link. |
| Investment | Promises of high returns with minimal risk, often involving fake investment opportunities or cryptocurrencies. | Individuals seeking financial gain, often those unfamiliar with investment risks. | A social media influencer promoting a guaranteed high-return cryptocurrency investment that turns out to be a scam. |
| Romance | Building a fake romantic relationship online to gain trust and obtain money from the victim. | Individuals seeking companionship or relationships, particularly those feeling lonely or isolated. | A scammer posing as a foreign military personnel, claiming to need money for emergency expenses or travel. |
The Psychology Behind Social Media Scam Success

Social media scams thrive not just because of technological vulnerabilities, but also because they expertly exploit human psychology. Scammers leverage sophisticated social engineering techniques to manipulate victims into handing over their financial information, often with surprising ease. Understanding these psychological tactics is crucial to protecting ourselves and others from falling prey to these schemes.Social engineering principles form the backbone of many successful social media scams.
These principles revolve around manipulating people’s emotions and behaviors to gain their trust and compliance. Scammers carefully craft their messages to target specific vulnerabilities, creating a sense of urgency, fear, or excitement that overrides rational thought. They often impersonate trusted individuals or organizations, leveraging the pre-existing trust victims have in those entities. This tactic exploits the inherent human tendency to trust familiar names and authority figures.
Exploitation of Psychological Vulnerabilities
Social media scams effectively exploit several key psychological vulnerabilities. One prominent vulnerability is the desire for quick riches or easy solutions. Scammers prey on this desire by promising unrealistic returns on investments, offering miraculous cures, or advertising seemingly too-good-to-be-true opportunities. Another vulnerability is the fear of missing out (FOMO), often exploited through limited-time offers or exclusive opportunities.
It’s terrifying how easily social media scams empty people’s bank accounts; one minute you’re scrolling, the next, your savings are gone. Building secure, reliable apps is crucial, and that’s where learning about domino app dev the low code and pro code future becomes vital. Understanding secure app development could help prevent these devastating financial losses caused by sophisticated social media scams targeting unsuspecting users.
This creates a sense of urgency and pressure to act quickly, bypassing careful consideration. Furthermore, scammers often target individuals’ emotions, such as empathy or compassion, through fabricated stories of hardship or distress, manipulating victims into sending money to help a person in need. These emotional appeals bypass logical reasoning, leading to impulsive actions.
The Role of Trust and Urgency in Social Media Scams
Trust is paramount in the success of social media scams. Scammers often meticulously build trust through carefully crafted profiles, engaging interactions, and seemingly genuine communications. They may spend time building relationships with their victims before making their pitch, creating a sense of familiarity and rapport that makes the victim more susceptible to their manipulations. This slow and steady approach contrasts with the sudden and forceful demands often seen in traditional scams.Urgency is the other critical element.
Scammers create a sense of immediacy by using phrases like “act now,” “limited-time offer,” or “this is your last chance.” They often combine urgency with scarcity, emphasizing limited availability of the opportunity, further intensifying the pressure to act without hesitation. This pressure to act quickly prevents victims from critically evaluating the situation and seeking advice from trusted sources.
For example, a scammer might claim a limited-time investment opportunity with guaranteed high returns, creating a false sense of urgency that overrides any doubts the victim might have. The pressure to act before the “opportunity” disappears often leads to impulsive decisions and financial losses.
How Scammers Access and Drain Bank Accounts: How Social Media Scams Are Draining Bank Accounts Of Victims
Social media scams are frighteningly effective because they leverage the trust we place in our online connections. Once a scammer gains your confidence, they employ a range of techniques to access and drain your bank accounts, often leaving you financially devastated and emotionally drained. Understanding these methods is crucial to protecting yourself.Scammers utilize several insidious methods to obtain victims’ banking information.
These methods exploit vulnerabilities in online security and human psychology, making even the most cautious individuals susceptible. The process often begins with a seemingly innocuous interaction on social media, quickly escalating into a sophisticated operation designed to extract your financial data.
Methods of Obtaining Banking Information
The acquisition of banking details is the cornerstone of any successful social media scam. This involves a multi-pronged approach, often combining psychological manipulation with technical expertise.
- Phishing Links: These malicious links, disguised as legitimate websites or documents, are often embedded within seemingly harmless messages or posts. Clicking these links redirects victims to fake login pages designed to steal usernames, passwords, and other sensitive information. The fake pages meticulously mimic the appearance of real banking websites, making it difficult for unsuspecting users to identify the deception.
- Malware and Viruses: Scammers may distribute malware through infected attachments or links. Once downloaded, this malware can secretly record keystrokes (keyloggers), steal cookies containing login credentials, or even directly access banking applications. The malware often operates silently in the background, making detection difficult.
- Social Engineering: This involves manipulating victims into divulging their banking information through deceptive tactics. This could range from impersonating a bank representative requesting account details to creating a false sense of urgency, pressuring victims to act quickly without verifying the request’s legitimacy.
A Typical Bank Account Compromise Flowchart, How social media scams are draining bank accounts of victims
Imagine a scenario where a scammer impersonates a friend on Facebook. The following flowchart illustrates how a typical bank account compromise might unfold: (Visual representation would go here. Imagine a flowchart with boxes and arrows. The boxes would include: 1. Scammer creates fake profile; 2. Scammer contacts victim via fake profile; 3. Scammer gains victim’s trust; 4. Scammer sends phishing link/malware; 5. Victim clicks link/downloads malware; 6. Banking credentials stolen; 7. Scammer accesses bank account; 8. Scammer withdraws funds.)
Money Laundering Techniques
After successfully accessing a bank account, scammers employ money laundering techniques to obscure the origin of the stolen funds. This is a crucial step in their operation, as it helps them avoid detection and prosecution.
- Smurfing: This involves breaking down large sums of money into smaller, less suspicious transactions. For example, the scammer might deposit small amounts of money into multiple accounts, making it harder to trace the origin of the funds.
- Shell Corporations: Scammers often use shell corporations – businesses with little to no legitimate activity – to funnel the stolen money. These corporations provide a layer of anonymity, obscuring the true source of the funds.
- Online Payment Platforms: Services like cryptocurrency exchanges or peer-to-peer payment systems are used to transfer money quickly and anonymously across borders, making it extremely difficult to track the flow of funds.
Protecting Yourself from Social Media Scams
Social media has become an indispensable part of our lives, connecting us with friends, family, and the wider world. However, this interconnectedness also makes us vulnerable to a growing number of sophisticated scams designed to steal our money and personal information. Understanding how these scams work and taking proactive steps to protect yourself is crucial in today’s digital landscape.
This section Artikels practical strategies to help you safeguard your bank accounts and personal data from social media-based fraud.
Staying safe online requires vigilance and a healthy dose of skepticism. Don’t let the seemingly friendly nature of social media lull you into a false sense of security. Criminals often exploit our trust and emotions to achieve their goals. Remember, if something seems too good to be true, it probably is.
Practical Tips for Identifying and Avoiding Social Media Scams
The following tips provide a strong foundation for protecting yourself from social media scams. Implementing these measures significantly reduces your risk of becoming a victim.
- Verify the legitimacy of requests: Never click on links or respond to messages from unknown sources requesting personal information, such as bank details, passwords, or social security numbers. Legitimate organizations will never ask for such sensitive data through social media.
- Examine URLs carefully: Before clicking on any link, hover your mouse over it to see the full URL. Look for misspellings or unusual characters that might indicate a fraudulent website. A legitimate website will have a secure connection (HTTPS).
- Be wary of unsolicited offers: Scammers often use tempting offers, such as free gifts, prize draws, or investment opportunities, to lure victims. Be suspicious of any unsolicited messages promising unrealistic returns or requiring immediate action.
- Enable two-factor authentication: This adds an extra layer of security to your accounts, making it much harder for scammers to access them even if they obtain your password. Most social media platforms and banking apps offer this feature.
- Report suspicious activity: If you encounter a suspicious profile, message, or post, report it to the social media platform immediately. This helps protect other users and assists platforms in identifying and removing fraudulent accounts.
The Role of Social Media Platforms in Scam Prevention and Resolution
Social media companies have a significant responsibility in protecting their users from scams. While individual vigilance is crucial, platforms must also actively implement measures to prevent and address these threats.
Platforms should enhance their algorithms to detect and flag suspicious accounts and posts more effectively. This includes identifying accounts using fake profiles, suspicious links, or engaging in coordinated scam attempts. Improved reporting mechanisms, making it easier for users to report suspicious activity, are also essential. Proactive measures, such as educating users about common scams through in-app notifications and educational materials, are crucial for building user awareness and resilience.
Finally, platforms should actively collaborate with law enforcement agencies to investigate and prosecute perpetrators of social media scams. Transparency regarding their efforts to combat scams, including statistics on scams detected and accounts banned, can build user trust and confidence.
The Impact of Social Media Scams on Victims
Social media scams inflict significant damage, extending far beyond the immediate financial loss. The emotional toll and long-term consequences for victims can be devastating, impacting their financial stability, mental health, and overall well-being. Understanding these impacts is crucial for both prevention and support.The financial repercussions of social media scams can be severe. Victims often lose substantial sums of money, sometimes their life savings.
This can lead to immediate hardship, such as difficulty paying bills, struggling to afford necessities, and even facing homelessness. The long-term impact can include damaged credit scores, difficulty obtaining loans, and years of financial instability as victims work to rebuild their finances. For example, a retiree scammed out of their retirement fund faces not only immediate financial ruin but also the devastating prospect of an insecure and impoverished old age.
Financial Consequences of Social Media Scams
The financial impact of social media scams is multifaceted and often long-lasting. Immediate losses can range from relatively small amounts to life savings, depending on the scam and the victim’s vulnerability. Beyond the initial loss, victims may incur additional expenses, such as fees associated with credit repair, legal counsel, and financial counseling. The inability to meet financial obligations can lead to debt accumulation, impacting credit scores and future financial opportunities.
For instance, a victim might struggle to secure a mortgage or auto loan due to their compromised credit history. The cumulative effect can be years of financial instability and hardship.
Psychological Distress Resulting from Social Media Scams
Beyond the financial burden, victims often experience significant psychological distress. The betrayal of trust, feelings of shame, guilt, and anger are common. Many victims experience a loss of self-esteem, feeling foolish or naive for falling prey to the scam. This can lead to anxiety, depression, and even post-traumatic stress disorder (PTSD). The isolation and reluctance to disclose the scam to friends and family can exacerbate these feelings.
For example, an elderly person who has been scammed out of their savings may feel intense shame and isolation, leading to a decline in their mental and physical health.
Legal Recourse for Victims of Social Media Scams
Victims of social media scams have several avenues for legal recourse. Reporting the scam to law enforcement is crucial. Local police departments, the FBI’s Internet Crime Complaint Center (IC3), and the Federal Trade Commission (FTC) are valuable resources for reporting and investigating these crimes. While recovering the stolen funds is not always guaranteed, reporting the scam helps law enforcement track perpetrators and prevent future crimes.
Furthermore, victims may be able to pursue civil action against the scammers, though this can be complex and expensive. It’s advisable to consult with an attorney specializing in fraud and cybercrime to explore all available legal options. Documenting all communications, transactions, and any other relevant information is essential for building a strong case.
Illustrative Examples of Successful and Unsuccessful Scams
Social media scams, unfortunately, are a growing problem, with both sophisticated and surprisingly simple tactics employed by fraudsters. Examining both successful and unsuccessful examples helps illustrate the techniques used and the vulnerabilities exploited. Understanding these case studies allows us to better protect ourselves and others from falling victim.
A Successful Romance Scam
This scam targeted middle-aged women on Facebook. The scammer created a meticulously crafted profile of a handsome, successful, and charming man – a widowed doctor working overseas with a young child. He engaged with numerous women, building relationships over several months through private messages, video calls (using pre-recorded videos or cleverly manipulated live ones), and seemingly heartfelt conversations. He gradually built trust, eventually expressing a need for financial assistance for his child’s medical expenses or business ventures.
The scammer was adept at weaving believable narratives, playing on the victims’ emotions and desire for companionship. Over a period of six months, he defrauded at least 20 women out of an estimated $200,000 total. The victims, often lonely or vulnerable, were reluctant to report the scam due to embarrassment or shame. The success of this scam hinged on the scammer’s patience, his ability to build rapport, and his exploitation of the victims’ emotional needs.
The consistent and personalized communication, coupled with believable fabricated circumstances, proved highly effective.
A Failed Phishing Attempt
A group attempted a large-scale phishing scam targeting Instagram users. They created numerous fake accounts impersonating popular influencers, promising exclusive merchandise giveaways or early access to products in exchange for personal information, including bank details. The scam was poorly executed. The fake accounts had low-quality profile pictures, inconsistent posting histories, and grammatically incorrect messages. Furthermore, the links provided for the “giveaway” redirected to obviously fake websites with suspicious URLs and unprofessional designs.
Many users immediately recognized the scam due to these inconsistencies. Instagram also swiftly identified and removed the fake accounts, significantly limiting the scam’s reach. The attempt failed due to a lack of sophistication in the scam’s execution. The obvious flaws in the fake accounts and phishing links alerted users to the fraud, preventing any significant financial losses. This highlights the importance of maintaining a professional and consistent online presence when running legitimate campaigns and the efficiency of social media platforms in identifying and removing fraudulent accounts.
Closing Notes
In the ever-evolving landscape of online threats, protecting yourself from social media scams requires constant vigilance and a healthy dose of skepticism. While the methods used by scammers are becoming increasingly sophisticated, understanding their tactics and implementing simple preventative measures can significantly reduce your risk. Remember, your financial security is paramount; don’t hesitate to report suspicious activity and stay informed about the latest scam trends.
Staying alert and educated is your best defense against becoming another statistic in this growing crisis.
General Inquiries
What should I do if I think I’ve been scammed?
Immediately contact your bank to report the fraudulent activity and freeze your accounts. Then, file a report with the appropriate law enforcement agencies and the Federal Trade Commission (FTC).
How can I spot a fake profile on social media?
Look for inconsistencies in profile information, limited friend connections, suspicious links, and generic or stolen photos. Be wary of profiles that aggressively solicit personal information or financial details.
Are there any apps or tools that can help me detect scams?
Several reputable antivirus and security software programs offer features to detect phishing links and malicious websites. However, remember that no tool is foolproof; always exercise caution.
What is the best way to protect my banking information online?
Use strong, unique passwords for all your online accounts. Enable two-factor authentication wherever possible. Never click on suspicious links or download attachments from unknown senders. Regularly review your bank statements for unauthorized transactions.





