How to Analyze Malware in 5 Steps
How to analyze malware in 5 steps? It sounds daunting, right? But fear not, fellow digital sleuths! Uncovering the secrets of malicious code doesn’t require a PhD in cybersecurity. This guide breaks down the process into manageable steps, equipping you with the knowledge and techniques to safely examine malware samples and understand their behavior. We’ll cover everything from safely isolating a sample to generating a comprehensive report, making this complex process surprisingly straightforward.
We’ll delve into both static and dynamic analysis techniques, showing you how to use various tools to extract valuable information without risking your system. Learn to identify the type of malware, its infection method, and its ultimate goal. By the end, you’ll be better prepared to protect yourself and others from these digital threats. Let’s get started!
Initial Assessment & Containment: How To Analyze Malware In 5 Steps
Safe and effective malware analysis begins with proper containment. Failing to isolate a malicious sample can lead to significant damage to your system and potentially expose your network. This initial phase is crucial for preventing further infection and ensuring a controlled analysis environment.The primary goal here is to prevent the malware from spreading or modifying your system in any way while you prepare for a deeper analysis.
This involves creating a secure sandbox and capturing system memory for later review.
Isolating a Suspected Malware Sample
Before even thinking about opening a suspected malware file, you need to isolate it. The simplest method is to copy the file to a virtual machine (VM). VMs offer a completely isolated environment. Any actions the malware takes within the VM will be contained within that virtual environment and will not affect your host operating system. If a VM isn’t available, a dedicated, physically isolated machine, ideally disconnected from the network, can be used.
Remember to use a write-blocker if you’re working with a physical drive to prevent any accidental modification of the original sample.
Creating a Sandboxed Environment
Several tools and techniques facilitate creating a sandboxed environment. Virtual machines (VMs) using software like VirtualBox or VMware Workstation Player are the most common approach. These allow you to run a suspected malware sample in a controlled virtual environment, separated from your host system. Alternatively, specialized sandboxing solutions, like Cuckoo Sandbox or Joe Sandbox, offer advanced features like automated analysis and reporting.
These often provide network monitoring and system call tracing, giving you a much more comprehensive view of the malware’s behavior.
Capturing System Memory Before Analysis, How to analyze malware in 5 steps
Before starting the analysis within the sandbox, it’s vital to capture a memory snapshot of the virtual machine. This memory dump provides a record of the system’s state before the malware is executed. Tools like Volatility can be used to analyze this memory dump later, identifying malware processes, loaded libraries, and network connections, even if the malware attempts to erase its traces.
The process typically involves taking a snapshot using the VM’s built-in functionality (e.g., creating a snapshot in VirtualBox)before* running the malware. After running the malware, you take another snapshot. Then you can use tools like FTK Imager or dd to create a forensic image of the virtual disk for later analysis.
Comparison of Sandbox Solutions
| Sandbox Solution | Features | Pros | Cons |
|---|---|---|---|
| Cuckoo Sandbox | Automated analysis, reporting, network monitoring | Comprehensive analysis, easy to use | Can be resource-intensive |
| Joe Sandbox | Deep analysis, API monitoring, behavioral analysis | Detailed insights, advanced features | Steeper learning curve, more expensive |
| VirtualBox/VMware | Virtual machine creation and management | Flexible, widely available, free options | Requires manual analysis, less automation |
| Any.Run | Cloud-based sandbox, automated analysis | Convenient, no local setup needed | Relies on internet connection, potential privacy concerns |
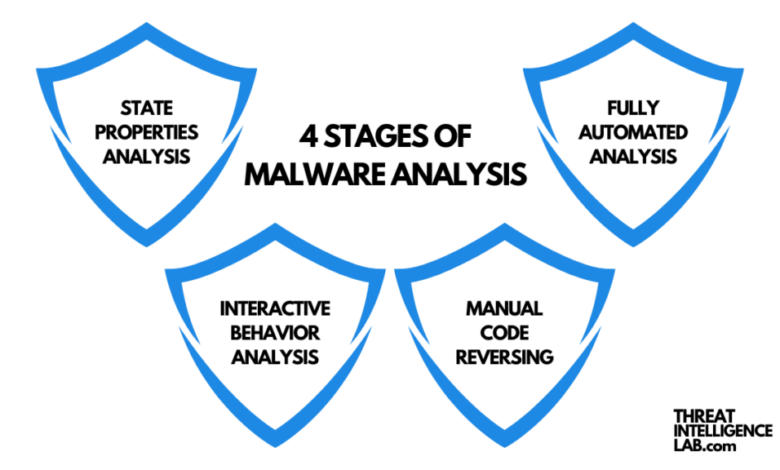
Static Analysis
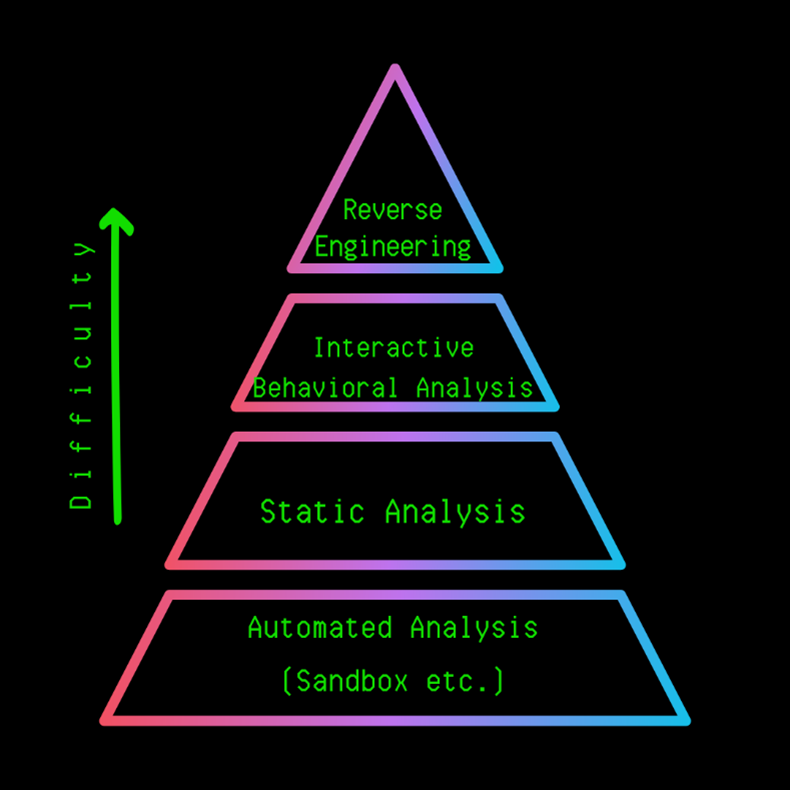
Static analysis is the first crucial step after containing a suspected malware sample. It involves examining the malware file without actually running it, minimizing the risk of infection or damage to your system. This process allows us to gather valuable information about the malware’s structure, behavior, and potential capabilities before proceeding to more risky dynamic analysis techniques. By carefully inspecting the file’s properties and contents, we can build a foundational understanding of the threat.Static analysis leverages various tools and techniques to dissect the malware’s inner workings.
We examine the file’s metadata, code, and resources to uncover clues about its functionality, origins, and intended targets. This non-intrusive approach provides a safe and effective way to learn about the malware’s nature and potential dangers.
Common Malware File Types and Characteristics
Malware manifests itself in various file types, each with its own characteristics. Executable files (.exe, .dll, .sys) are common, as they contain the malware’s code ready to be executed. Script files (.js, .vbs, .ps1) can also harbor malicious code, often relying on the host system’s scripting engine to run. Document files (.doc, .docx, .pdf) can be weaponized to deliver malware through embedded macros or malicious links.
Archives (.zip, .rar, .7z) often serve as containers for malware, concealing the malicious payload within. Identifying the file type is the first step in understanding the malware’s delivery mechanism and potential impact. For example, a .exe file might indicate a more directly executable threat, while a .docx file might suggest a social engineering approach relying on user interaction.
Utilizing Static Analysis Tools
Several powerful tools aid in static analysis. PEiD, for instance, is a popular tool that identifies the packer or compiler used to create the executable file. Knowing the packer can help in unpacking the malware for further analysis, as different packers employ different obfuscation techniques. The strings command (available in most operating systems) extracts all printable strings from a file.
These strings often contain valuable information such as file paths, URLs, registry keys, or even strings directly related to the malware’s purpose (e.g., “ransomware,” “keylogger”). Analyzing these strings can provide significant clues about the malware’s behavior and targets.
Key Information Extracted from Static Analysis
The importance of meticulously collecting information during static analysis cannot be overstated. The data gathered forms the basis for all subsequent analysis steps.
- File Type and Size: Provides initial clues about the malware’s nature and potential capabilities.
- File Metadata: Includes creation date, modification date, author, and other attributes that can offer insights into the malware’s origin and history.
- Packing Information (using PEiD): Reveals whether the malware is packed or obfuscated, and what type of packer was used. This is crucial for unpacking and further analysis.
- Imported Functions: Identifies the system APIs and libraries the malware relies on, revealing potential actions such as network communication, file system access, or registry manipulation.
- Extracted Strings (using strings): Uncovers potentially revealing text within the malware, including URLs, file paths, registry keys, and potentially even comments left by the malware authors.
- Resources: Embedded files, images, or other data within the malware that can provide clues about its purpose or functionality.
- Digital Signatures: If present, can verify the authenticity of the software and help identify potential forgeries.
Dynamic Analysis
Dynamic analysis is where the rubber meets the road. We take our malware sample, which we’ve already assessed statically, and observe its behavior in a controlled environment. This is crucial for understanding how the malware interacts with the system and the network, revealing functionalities that static analysis might miss. This involves running the malware within a virtual machine (VM), meticulously monitoring its actions, and analyzing the resulting data.Dynamic analysis within a virtual machine provides a safe and isolated environment for observing malware behavior without risking damage to your primary system.
The VM acts as a sandbox, allowing us to execute the malware and analyze its actions without fear of infection. This process allows for a deeper understanding of the malware’s capabilities and its potential impact on a system.
Virtual Machine Setup and Malware Execution
Setting up a VM for malware analysis requires careful consideration. We need a snapshot of a clean virtual machine image to revert to in case of unforeseen complications. The VM should have minimal software installed, only the necessary tools for monitoring system activity and network traffic. The malware sample is then executed within this controlled environment, and its actions are closely monitored.
This might involve using tools like Process Monitor to track system calls, Wireshark to capture network traffic, and a debugger to step through the malware’s code execution. The choice of operating system for the VM should mirror the target environment of the malware, ensuring realistic behavior. For example, if the malware is suspected to target a Windows system, a Windows-based VM should be used.
Malware Behavior Observations
During execution, we observe the malware’s behavior, noting any suspicious activities. This includes registry modifications, file creations or deletions, network connections, and attempts to access system resources. The timing of these actions is also important. For example, does the malware immediately connect to a command-and-control server, or does it wait for a specific trigger? Does it attempt to encrypt files, or does it install additional components?
A detailed log of these events is maintained for later analysis. An example of a concerning observation might be the malware creating a scheduled task to run itself persistently at system startup, indicating an attempt to establish persistence on the infected system.
Network Traffic Analysis
Network traffic generated by the malware is a key indicator of its malicious intent and functionality. Using tools like Wireshark, we capture and analyze all network communication. We look for connections to known malicious IP addresses or domains, unusual communication patterns, and the types of data being transmitted. The volume of data transferred, the protocols used (HTTP, HTTPS, DNS, etc.), and the destination addresses all provide valuable insights.
For instance, if the malware communicates with a known botnet server, it suggests involvement in a distributed denial-of-service (DDoS) attack or other coordinated malicious activities.
Dynamic Analysis Report
The findings from the dynamic analysis are compiled into a structured report. Key observations are highlighted using blockquotes to emphasize their importance.
The malware established a persistent connection to the IP address 192.0.2.10, likely a command-and-control server.
The malware attempted to download and execute a file from the URL hxxp://maliciousdomain.com/payload.exe.
Significant registry modifications were observed, including the creation of a new autorun key, indicating an attempt to achieve persistence.
So you want to learn how to analyze malware in 5 steps? It’s a fascinating process, starting with identifying the infection vector. But building secure apps is equally crucial, and that’s where understanding the future of app development comes in, as detailed in this great article on domino app dev, the low code and pro code future.
After securing your app development, you can move on to the next step in malware analysis: static analysis of the malicious code itself.
The malware exhibited behavior consistent with data exfiltration, transferring large amounts of data to a remote server.
Malware Behavior Identification
Understanding a malware sample’s behavior is crucial for effective analysis. This step goes beyond simply identifying the file type; it delves into how the malware interacts with the system, its propagation methods, and its ultimate goal. By carefully observing its actions, we can accurately classify the malware and develop effective mitigation strategies.This section details the process of identifying the type of malware, tracing its infection and propagation methods, analyzing its payload and system impact, and pinpointing any command and control (C&C) servers.
Malware Classification
Categorizing malware is the first step in understanding its capabilities and potential threat. Common malware types include viruses, trojans, worms, ransomware, and spyware. Viruses often attach themselves to other files, replicating upon execution. Trojans disguise themselves as legitimate software, often carrying hidden malicious payloads. Worms self-replicate and spread across networks without requiring user interaction.
Ransomware encrypts data and demands a ransom for its release. Spyware secretly monitors user activity and collects sensitive information. Analyzing the malware’s actions within a sandboxed environment provides crucial clues for accurate classification. For example, if the malware encrypts files and demands a ransom, it’s likely ransomware. If it replicates itself across a network, it’s probably a worm.
Infection and Propagation Methods
Understanding how the malware infected the system and its propagation mechanisms is critical for preventing future infections. Methods include phishing emails containing malicious attachments, exploiting software vulnerabilities, using social engineering techniques, or spreading through removable media. Analyzing network traffic and registry entries can reveal the infection vector. For example, observing the malware attempting to connect to external IP addresses may indicate a network-based propagation method.
Examining the system’s startup processes might reveal the malware’s persistence mechanism.
Malware Payload and System Impact
The malware’s payload is the destructive or malicious action it performs. This could range from data theft and system corruption to denial-of-service attacks and the installation of backdoors. Analyzing the malware’s behavior reveals its impact on the system. For example, if the malware modifies system files, it could lead to system instability or crashes. If it deletes files, it could cause data loss.
If it steals sensitive information, it could lead to identity theft. Careful observation of system logs and registry changes helps determine the full extent of the malware’s impact.
Command and Control (C&C) Server Identification and Control
Many malware samples communicate with remote C&C servers to receive instructions or send stolen data. Identifying and controlling these servers is essential for disrupting the malware’s operation and preventing further infections. Network monitoring tools can reveal connections to suspicious IP addresses or domains. Analyzing the malware’s code may reveal hardcoded C&C server addresses or domain generation algorithms (DGAs).
Blocking these connections can effectively neutralize the malware’s ability to communicate with its controllers. For example, identifying a suspicious domain name used by the malware allows for its blocking through DNS filtering or firewall rules. A DGA, on the other hand, requires more sophisticated techniques to identify and block the dynamically generated domains.
Report Generation
The final, and arguably most crucial, step in malware analysis is generating a comprehensive report. This report acts as a permanent record of your findings, providing actionable intelligence for remediation and prevention efforts. It should be meticulously crafted, clearly presenting complex technical information in a digestible format for both technical and non-technical audiences. A well-structured report ensures that the results of your analysis are effectively communicated and acted upon.This stage involves consolidating the data gathered during the previous steps – initial assessment, static and dynamic analysis, and behavioral identification – into a clear and concise narrative.
The report should not only detail the malware’s characteristics but also offer specific recommendations for mitigating the threat and preventing future infections.
Key Findings Presentation
A well-organized table is an effective way to present key findings. This allows for a quick overview of critical information. The table should be designed for readability and accessibility, even for those unfamiliar with technical jargon. Using responsive design principles will ensure the table remains user-friendly across various devices.
| Finding Category | Specific Finding | Source/Evidence | Impact |
|---|---|---|---|
| Infection Vector | Phishing email containing malicious attachment | Email headers, attachment analysis | Compromised user credentials, data exfiltration |
| Payload | Data exfiltration to a remote server (IP address: 192.0.2.1) | Network traffic analysis, dynamic analysis logs | Loss of sensitive information, potential financial damage |
| Impact | System slowdown, data breach, potential ransomware deployment | Performance monitoring, system logs, dynamic analysis | Operational disruption, financial losses, reputational damage |
Remediation and Prevention Recommendations
This section Artikels the steps necessary to eliminate the malware and prevent future infections. This should include specific, actionable steps, such as removing infected files, updating software, and implementing security controls. The recommendations should be tailored to the specific malware and the environment it affected. For instance, if the infection vector was a phishing email, the report should include recommendations for improving employee security awareness training.For example, remediation might involve removing malicious files identified during the analysis, restoring affected system files from backups, and implementing a robust endpoint detection and response (EDR) solution.
Prevention could include patching vulnerabilities, enabling multi-factor authentication (MFA), and implementing stricter email filtering policies.
Clear and Concise Communication for Non-Technical Audiences
When communicating findings to non-technical audiences, avoid using technical jargon. Instead, use plain language and analogies to explain complex concepts. For example, instead of saying “the malware utilized a polymorphic engine,” you might say “the malware constantly changes its appearance to avoid detection.” Visual aids, such as flowcharts or diagrams, can also be helpful in simplifying complex information.
The goal is to convey the essence of the threat and the necessary actions without overwhelming the reader with technical details. Focus on the business impact and the steps needed to recover and prevent future incidents.
Final Conclusion
Analyzing malware can feel like navigating a digital minefield, but by following these five steps – containment, static analysis, dynamic analysis, behavior identification, and report generation – you can systematically uncover the secrets of malicious code. Remember, safety is paramount. Always analyze in a controlled environment. This process isn’t just about technical skills; it’s about understanding the adversary’s tactics and building a stronger defense against future threats.
So, grab your tools, and let’s stay one step ahead of the bad guys!
Expert Answers
What if I accidentally infect my system during analysis?
Always use virtual machines and sandbox environments. Never analyze malware directly on your primary operating system.
What are some free tools for malware analysis?
Many free and open-source tools are available, including Cuckoo Sandbox (for dynamic analysis), PEiD (for identifying packers), and strings (for extracting text strings).
How do I deal with obfuscated malware?
Obfuscation makes analysis more challenging. Techniques like decompilation, emulation, and using specialized tools designed for handling obfuscated code are often necessary.
Where can I find practice malware samples for safe analysis?
Several reputable sources offer benign malware samples for educational purposes. Always exercise caution and only download from trusted sources.