How to Find and Apply for Cybersecurity Grants for Nonprofits
How to find and apply for cybersecurity grants for nonprofits? It’s a question many small, mission-driven organizations grapple with. Securing funding for vital cybersecurity upgrades can feel like navigating a maze, but it doesn’t have to be. This guide cuts through the jargon and provides a practical roadmap, helping nonprofits unlock crucial funding to protect their valuable data and resources.
We’ll explore where to find these grants, how to craft a winning proposal, and what to expect after you’ve secured the funding. Get ready to transform your nonprofit’s cybersecurity posture!
This post breaks down the entire grant application process into manageable steps, from identifying eligible grants and understanding application requirements to crafting a compelling proposal and building relationships with grant-making organizations. We’ll even delve into post-grant management and share examples of successful applications to inspire you. Think of this as your personal cybersecurity grant-seeking toolkit.
Identifying Eligible Cybersecurity Grants for Nonprofits
Securing funding for cybersecurity initiatives can be a significant hurdle for nonprofits, often operating on tight budgets. Fortunately, various government agencies and private foundations recognize the critical need for robust cybersecurity in the nonprofit sector and offer grants to help bridge this gap. Understanding where to look and how to apply effectively is key to success.
Government Agencies and Private Foundations Offering Cybersecurity Grants
Finding the right grant requires research. Many organizations offer grants with varying focuses and eligibility requirements. The following table provides a starting point, but it’s crucial to regularly check each agency’s website for the most up-to-date information, as grant programs and deadlines change frequently. Note that this is not an exhaustive list, and many smaller foundations may also offer relevant grants.
| Agency Name | Grant Focus | Eligibility Requirements | Application Deadline (Example) |
|---|---|---|---|
| National Institute of Standards and Technology (NIST) (Example) | Cybersecurity standards, frameworks, and best practices. Often supports research and development initiatives related to cybersecurity. | Typically requires collaboration with academic institutions or industry partners. Specific requirements vary per grant program. | Varies by grant program; check NIST website. |
| Department of Homeland Security (DHS) (Example) | Grants often focus on improving cybersecurity infrastructure and incident response capabilities. May prioritize critical infrastructure sectors. | Nonprofits must typically demonstrate a critical need and capacity to implement cybersecurity improvements. Specific eligibility criteria are Artikeld in each grant announcement. | Varies by grant program; check DHS website. |
| State and Local Governments (Example: California Cybersecurity Grant Program) | Funding often focuses on improving state and local government cybersecurity infrastructure, which may indirectly benefit nonprofits that work with them. | Eligibility criteria will vary by state and program. Often requires a demonstrated need and a strong plan for cybersecurity improvements. | Varies by state and program; check relevant state government websites. |
| Private Foundations (Example: The Kresge Foundation) | Focus varies widely depending on the foundation’s mission. Some foundations support digital inclusion initiatives which may include cybersecurity components. | Eligibility criteria vary significantly. Foundations often have specific geographic or programmatic focuses. | Varies by foundation and grant program; check individual foundation websites. |
Criteria for Assessing Cybersecurity Needs of Nonprofits
Grant-making organizations assess nonprofit applicants based on several key criteria. These often include:* Demonstrated Need: Applicants must clearly articulate their current cybersecurity vulnerabilities and the potential risks they face. This may involve documenting past incidents, assessing their existing infrastructure, and identifying critical assets.
Project Feasibility
A well-defined project plan is crucial. This should Artikel specific cybersecurity improvements, timelines, and measurable outcomes. Realistic budgets and a clear understanding of the resources required are essential.
Organizational Capacity
Grantors want to ensure the nonprofit has the internal capacity to implement and sustain the proposed cybersecurity improvements. This may involve demonstrating existing staff expertise or a plan for acquiring necessary skills.
Impact and Sustainability
The project should demonstrate a clear positive impact on the nonprofit’s operations and data security. Grantors often look for plans to ensure the project’s long-term sustainability beyond the grant period.
Compliance and Security Standards
Adherence to relevant cybersecurity standards and best practices (like NIST Cybersecurity Framework) is frequently a positive factor.
Types of Cybersecurity Grants Available
Cybersecurity grants cater to various needs. Some common types include:* Infrastructure Improvements: Funding for hardware and software upgrades, such as firewalls, intrusion detection systems, and endpoint protection.
Training and Awareness
Grants supporting cybersecurity awareness training for staff and volunteers, helping them identify and mitigate phishing attempts and other threats.
Incident Response Planning
Funding for developing and implementing incident response plans, enabling organizations to effectively manage and recover from security breaches.
Data Security and Privacy
Grants focusing on improving data security practices, including encryption, access controls, and data backup and recovery.
Understanding Grant Application Requirements
Securing cybersecurity grants for your nonprofit requires more than just identifying eligible programs; it demands a thorough understanding of the application process. Successfully navigating this process hinges on crafting a compelling proposal that clearly articulates your organization’s needs and demonstrates how the grant funds will be effectively utilized. This involves paying close attention to specific requirements and presenting a well-structured, persuasive case.
Grant applications, while varying in specifics depending on the funding organization, typically share common elements. A well-prepared application will showcase a clear understanding of your organization’s cybersecurity vulnerabilities, a well-defined plan for addressing those vulnerabilities, and a realistic budget that details how the grant funds will be spent. This detailed approach significantly increases your chances of securing the funding needed to strengthen your nonprofit’s digital defenses.
Common Elements of Cybersecurity Grant Applications
Most grant applications for cybersecurity improvements will require similar information. A strong application meticulously addresses each requirement, demonstrating a comprehensive understanding of both the need and the proposed solution. Failure to address these elements thoroughly can significantly reduce the likelihood of your application’s success.
- Executive Summary: A concise overview of your organization, the cybersecurity challenges you face, and your proposed solution. This section should immediately grab the reviewer’s attention and highlight the key aspects of your proposal.
- Needs Assessment: A detailed analysis of your current cybersecurity posture, identifying specific vulnerabilities and risks. This should include evidence of existing problems and their potential impact on your organization’s operations and mission.
- Project Description: A comprehensive explanation of your proposed cybersecurity improvements, including specific technologies, services, and training programs. This section should clearly Artikel the steps you’ll take to address the vulnerabilities identified in your needs assessment.
- Project Timeline: A realistic schedule outlining the key milestones and deadlines for implementing your proposed cybersecurity improvements. This demonstrates your organizational capacity and planning skills.
- Budget Justification: A detailed breakdown of all proposed expenses, clearly linking each cost to a specific project activity. This section must convincingly demonstrate the cost-effectiveness of your proposed solution.
- Evaluation Plan: A description of how you will measure the success of your project, including specific metrics and reporting mechanisms. This demonstrates your commitment to accountability and responsible use of funds.
- Organizational Information: Information about your nonprofit, including its mission, history, and financial stability. This section establishes credibility and demonstrates your organization’s capacity to manage the grant funds effectively.
The Importance of a Strong Needs Assessment and Budget Justification
The success of your grant application heavily relies on a robust needs assessment and a meticulously prepared budget justification. These two components work in tandem to create a convincing narrative that demonstrates the necessity of the grant and the responsible management of funds.
A strong needs assessment goes beyond simply stating that you need better cybersecurity. It requires a detailed analysis of your current systems, identifying specific vulnerabilities, quantifying the potential risks (e.g., financial losses from a data breach, disruption of services), and demonstrating the impact these vulnerabilities could have on your mission. For example, a needs assessment might highlight the lack of multi-factor authentication, leading to a risk of unauthorized access to sensitive donor information, thereby jeopardizing trust and potentially impacting fundraising efforts.
This type of specific and impactful language is crucial.
The budget justification is equally important. It shouldn’t just list expenses; it should explain why each expense is necessary and how it directly contributes to achieving the project goals Artikeld in your proposal. Vague or unsupported requests for funding are likely to be rejected. Each line item should be meticulously justified, demonstrating value for money and aligning directly with the needs assessment.
Sample Grant Budget
Here’s a sample budget for a hypothetical nonprofit seeking to improve its cybersecurity. This is a simplified example and the actual budget will depend on the specific needs of the organization and the scope of the project.
| Expense Category | Description | Amount |
|---|---|---|
| Security Software | Purchase and licensing of endpoint protection software, intrusion detection system, and anti-spam filters. | $5,000 |
| Hardware Upgrades | Replacement of outdated servers and network equipment. | $10,000 |
| Security Training | Cybersecurity awareness training for staff. | $2,000 |
| Security Audits | Regular security assessments and penetration testing to identify vulnerabilities. | $3,000 |
| Incident Response Plan | Development and implementation of an incident response plan. | $1,000 |
| Total | $21,000 |
Crafting a Compelling Grant Proposal
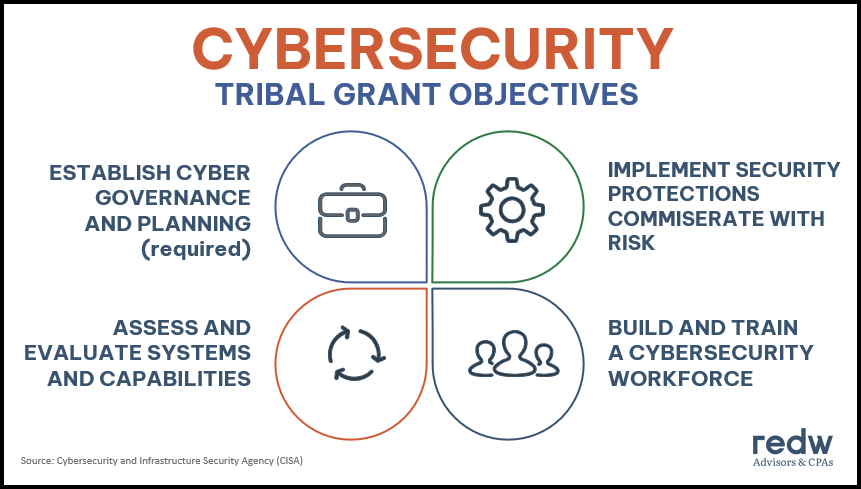
Securing funding for cybersecurity improvements is crucial for nonprofits, and a well-crafted grant proposal is the key. A compelling proposal isn’t just about listing needs; it’s about painting a picture of the impact your project will have. It needs to resonate with the grantor, showcasing your organization’s dedication and the urgency of the situation. Think of it as a persuasive business plan focused on security.
Grant Proposal Template
A successful grant proposal follows a clear structure. This template provides a framework for a compelling application. Remember to tailor it to each specific grant opportunity, paying close attention to the funder’s guidelines and priorities.
- Executive Summary: A concise overview (typically one page) summarizing the nonprofit, the problem, the proposed solution, the budget, and the expected impact. This is often the first – and sometimes only – part read thoroughly, so it must grab the reader’s attention immediately.
- Project Description: A detailed explanation of the cybersecurity project, including its goals, objectives, activities, timeline, and methodology. Clearly articulate the problem, justifying the need for the grant. Use visuals like charts or diagrams if appropriate to illustrate your points.
- Budget: A comprehensive breakdown of all project costs, including personnel, equipment, software, training, and other expenses. Justify each expense, showing how it directly contributes to project goals. Include a clear narrative explaining the budget.
- Evaluation Plan: A plan for measuring the project’s success. Define specific, measurable, achievable, relevant, and time-bound (SMART) goals and the methods you will use to track progress and evaluate outcomes. This demonstrates accountability and responsible use of funds.
- Letters of Support: Include letters from stakeholders who endorse your project and can attest to its importance and feasibility. This could include beneficiaries, partners, or community leaders.
Narrative Elements for a Strong Proposal
The narrative is the heart of your proposal. It should be clear, concise, and persuasive, effectively conveying the urgency and impact of your project. Avoid jargon and technical details unless absolutely necessary; focus on the human impact of cybersecurity threats and the benefits of your project.
- Problem Statement: Clearly articulate the cybersecurity challenges faced by your nonprofit. Use specific examples to illustrate the vulnerabilities and the potential consequences of inaction. Quantify the impact whenever possible (e.g., “We experienced three data breaches last year, resulting in X dollars in losses and Y hours of staff time”).
- Proposed Solution: Describe how your project will address the identified challenges. Explain the specific cybersecurity measures you will implement and how they will mitigate the risks. Highlight the innovative aspects of your approach if applicable.
- Expected Outcomes: Clearly state the anticipated results of your project. Quantify the impact whenever possible (e.g., “This project will reduce our risk of data breaches by X%, improve our response time to incidents by Y%, and increase staff awareness of cybersecurity best practices by Z%”).
- Sustainability Plan: Explain how your organization will maintain the improvements made after the grant funding ends. This demonstrates long-term commitment and responsible stewardship of resources.
Examples of Strong and Weak Proposals
A strong proposal, like one that secured funding from a major foundation for a national children’s hospital, clearly Artikeld the risks of a ransomware attack, the proposed security upgrades (including staff training and new software), and the quantifiable benefits in terms of reduced downtime and protected patient data. It included compelling visuals illustrating the vulnerabilities and the solutions.In contrast, a weak proposal might vaguely mention cybersecurity needs without providing specific examples or quantifiable data.
It might lack a clear plan for implementation and evaluation, making it difficult for the grantor to assess the project’s feasibility and impact. For instance, a proposal lacking concrete budget justification or a clear timeline would likely be deemed insufficient.
Building Relationships with Grant-Making Organizations

Securing cybersecurity grants for your nonprofit isn’t just about submitting a perfect application; it’s about cultivating meaningful relationships with the organizations that fund such initiatives. Building these connections significantly increases your chances of success and opens doors to future funding opportunities. Think of it as investing in long-term partnerships, not just one-off grant applications.Effective strategies for researching and identifying suitable grant opportunities go beyond simple online searches.
A proactive approach yields far better results. It’s about understanding the grant-makers’ priorities and aligning your project goals accordingly.
Grant Research Strategies
A systematic approach to researching grants is crucial. Begin by creating a list of potential grant-making organizations known to fund cybersecurity initiatives or projects related to your nonprofit’s mission. This could involve searching online databases like GuideStar, Foundation Center (now Candid), and GrantWatch. Look for organizations with a history of supporting similar projects or those specifically focused on technology, digital security, or nonprofits in your sector.
Don’t limit yourself to national organizations; explore regional and local foundations as well. Review past grant awards to identify successful applicants and understand the types of projects they fund. This provides valuable insight into their funding priorities and application requirements. For example, if you see a pattern of funding projects focused on data breach prevention, tailoring your application to address that specific need would significantly increase your chances.
Networking and Relationship Building
Networking is paramount. Attend relevant conferences and workshops, join online forums and communities focused on cybersecurity and nonprofit funding, and actively engage with grant-makers on social media. Consider attending information sessions or webinars hosted by grant-making organizations. These events offer invaluable opportunities to learn more about their funding priorities, meet program officers, and build rapport. A simple email expressing your interest in their work and outlining your organization’s mission can go a long way in establishing a connection.
Remember, building relationships takes time and effort; consistent engagement is key. For instance, regularly sharing relevant news and updates about your organization’s work with the grant-makers demonstrates ongoing commitment and strengthens your relationship.
Grant Application Submission and Follow-Up
Submitting a grant application is only half the battle. Thorough preparation and careful attention to detail are essential. Ensure your application is meticulously crafted, adhering to all guidelines and deadlines. Many organizations offer online application portals. Familiarize yourself with the system and utilize all available resources.
Once you submit your application, track its progress diligently. Maintain a record of all communication, including emails and phone calls. Don’t hesitate to follow up politely after a reasonable timeframe, perhaps a week or two after the deadline, to inquire about the status of your application. A brief, professional email expressing your continued interest and reiterating the significance of your project is appropriate.
For example, you could mention any recent developments related to your project or new information relevant to the grant’s objectives. Avoid excessive follow-up; one or two polite inquiries are generally sufficient. Remember, professionalism and respect are vital throughout the entire process.
Post-Grant Management
Securing a cybersecurity grant is a significant achievement for a nonprofit, but the work doesn’t end with the award. Successful post-grant management is crucial to ensure the funds are used effectively, the project goals are met, and a strong relationship with the grantor is maintained. This involves careful planning, meticulous record-keeping, and proactive communication.Post-grant management encompasses all activities undertaken after receiving the grant funds to ensure the successful completion of the project and responsible use of the awarded funds.
This includes regular monitoring of project progress, diligent financial tracking, and consistent communication with the grant-making organization. Failing to properly manage the grant can lead to delays, budget overruns, and even the loss of future funding opportunities.
Project Implementation and Monitoring
Implementing the project as Artikeld in the grant proposal is paramount. This involves assigning responsibilities, setting timelines, and establishing clear performance indicators. Regular monitoring of progress against these indicators helps identify potential issues early on, allowing for timely adjustments and mitigation of risks. For example, if the project involves implementing a new security system, the timeline might include phases for assessment, procurement, installation, testing, and training.
Regular progress meetings with the project team should be scheduled to review progress, address challenges, and ensure the project stays on track. Documentation of these meetings, including action items and decisions made, is essential for accountability and transparency.
Financial Management and Reporting
Accurate and timely financial reporting is a cornerstone of effective post-grant management. This involves maintaining detailed records of all grant-related expenses, ensuring compliance with the grant agreement’s stipulations, and submitting regular financial reports to the grantor. A dedicated budget tracking system, whether a spreadsheet or dedicated software, is crucial. This system should allow for easy tracking of income, expenses, and remaining funds.
Regular reconciliation of the grant budget against actual expenditures ensures early detection of any discrepancies. For instance, if the budget allocated $5,000 for software licenses, and only $4,000 has been spent, the reason for the variance should be investigated and documented. The financial reports submitted to the grantor should clearly reflect the project’s financial status, providing a clear and concise overview of income, expenses, and remaining funds.
Communication with the Grant-Making Organization
Open and consistent communication with the grant-making organization is vital throughout the project lifecycle. This includes regular updates on project progress, addressing any questions or concerns promptly, and providing timely financial reports. A communication plan should be developed outlining the frequency and methods of communication, ensuring transparency and proactive engagement with the grantor. For example, quarterly progress reports could be submitted, supplemented by ad-hoc communications as needed.
These reports should highlight key achievements, challenges encountered, and any necessary adjustments to the project plan. Maintaining a positive and collaborative relationship with the grantor enhances the chances of securing future funding.
Accountability and Documentation
Maintaining comprehensive documentation is essential for demonstrating accountability and transparency. This includes all project-related documents, such as meeting minutes, financial records, progress reports, and communication logs. This documentation serves as a valuable record of the project’s activities, demonstrating how the grant funds were used and the outcomes achieved. A well-organized filing system, either physical or digital, is essential for easy access to these documents.
This detailed documentation can also be beneficial in case of audits or inquiries from the grantor. For example, if questioned about a specific expense, having the supporting documentation readily available demonstrates responsible financial management and strengthens accountability.
Illustrative Examples of Successful Grant Applications: How To Find And Apply For Cybersecurity Grants For Nonprofits
Securing cybersecurity grants for nonprofits can be challenging, but success is achievable with a well-crafted application that highlights the organization’s needs and the project’s potential impact. Here are two examples illustrating successful grant applications, focusing on the strategies employed and the results achieved. These examples showcase the importance of clear articulation of need, a well-defined project plan, and a strong demonstration of the organization’s capacity to execute the project.
Successful Grant Application: The Community Tech Center, How to find and apply for cybersecurity grants for nonprofits
The Community Tech Center (CTC), a nonprofit providing digital literacy training and computer access to underserved communities, successfully secured a $50,000 grant from the National Cybersecurity Alliance (NCA) to implement a comprehensive cybersecurity awareness training program. The grant funded the development and delivery of workshops, online resources, and one-on-one consultations focused on phishing scams, password security, and safe online practices.
The success of the CTC’s application stemmed from several key elements:
- Clearly Defined Need: The application meticulously documented the high incidence of cybercrime affecting the CTC’s target population, highlighting the lack of readily available cybersecurity resources within their community.
- Measurable Objectives: Specific, measurable, achievable, relevant, and time-bound (SMART) objectives were established, including the number of individuals trained, the increase in cybersecurity awareness scores, and the reduction in reported phishing incidents.
- Detailed Project Plan: A comprehensive project plan Artikeld the training curriculum, the marketing strategy to reach the target audience, and the evaluation methods to assess the program’s effectiveness.
- Strong Budget Justification: The budget was meticulously detailed, justifying each expense and demonstrating responsible financial management.
- Experienced Team: The application showcased the CTC’s experienced staff and their capacity to deliver the proposed training program.
Challenges faced included securing buy-in from the community and overcoming initial skepticism about the importance of cybersecurity training. These challenges were overcome through community outreach, building partnerships with local organizations, and emphasizing the practical and immediate benefits of the training. The impact of the project was significant, resulting in a 30% reduction in reported phishing incidents and a 40% increase in users demonstrating secure online practices within the community.
Successful Grant Application: The Children’s Advocacy Center
The Children’s Advocacy Center (CAC), a nonprofit supporting child victims of abuse, received a $25,000 grant from a local foundation to enhance its data security infrastructure. The grant funded the implementation of advanced encryption, multi-factor authentication, and employee cybersecurity training.
Key elements contributing to the success of the CAC’s application included:
- Emphasis on Protecting Sensitive Data: The application strongly emphasized the sensitive nature of the data handled by the CAC (including children’s personal information and case files) and the critical need to protect it from unauthorized access and breaches.
- Specific Technological Solutions: The application detailed the specific technological solutions proposed, justifying their selection based on their effectiveness, cost-efficiency, and compatibility with the CAC’s existing infrastructure.
- Compliance with Regulations: The application highlighted the CAC’s commitment to complying with relevant data privacy regulations, such as HIPAA and FERPA.
- Long-Term Sustainability Plan: The application included a plan for maintaining the upgraded security infrastructure beyond the grant period, demonstrating long-term commitment to data protection.
- Collaboration with Cybersecurity Experts: The application demonstrated collaboration with cybersecurity experts who provided technical guidance and support for the project.
A significant challenge was demonstrating the CAC’s technical capacity to implement and manage the proposed security upgrades. This challenge was addressed by partnering with a local university’s cybersecurity program, which provided technical assistance and training to the CAC staff. The resulting enhanced data security infrastructure significantly reduced the risk of data breaches and ensured the confidentiality of sensitive information.
Conclusive Thoughts

Securing cybersecurity grants for nonprofits is achievable with the right approach. By carefully researching potential funding sources, crafting a strong proposal that highlights your needs and impact, and nurturing relationships with grant-makers, you can significantly improve your organization’s cybersecurity defenses. Remember, protecting your data and the sensitive information of those you serve is an investment, not an expense, and securing funding for this is a crucial step.
So, dive in, explore the resources, and start building a more secure future for your nonprofit!
Quick FAQs
What if my nonprofit doesn’t have a dedicated IT department?
Many grants understand that smaller nonprofits may lack dedicated IT staff. Highlight the need for cybersecurity improvements and how the grant will help you either hire a consultant, outsource services, or provide training for existing staff.
How long does the grant application process typically take?
It varies greatly depending on the grant-maker and the complexity of the application. Allow ample time – research suggests at least a few months to complete a thorough application.
What happens if my grant application is rejected?
Don’t be discouraged! Many applications are rejected. Request feedback from the grant-maker if possible to improve future applications. Often, small tweaks can make a big difference.
Are there any specific cybersecurity certifications that increase my chances of getting a grant?
While not always required, demonstrating a commitment to cybersecurity best practices through staff certifications (like CompTIA Security+, CISSP, etc.) can strengthen your application.