Future-Proofing Vulnerability Management
How to prepare for the future of vulnerability management is crucial in today’s rapidly evolving threat landscape. Cybersecurity threats are becoming increasingly sophisticated, from zero-day exploits to automated attacks. This means that traditional vulnerability management approaches are no longer sufficient. We’ll explore the evolving threat landscape, the need for proactive strategies, and the essential skills required to build a future-proof security team.
This comprehensive guide dives deep into the critical steps for modernizing your vulnerability management program. From embracing DevSecOps to leveraging AI and machine learning, we’ll cover strategies for securing cloud and IoT environments, and building a culture of security awareness throughout your organization. The future of vulnerability management is about anticipating threats, automating responses, and integrating security into every stage of the software development lifecycle.
Understanding the Evolving Threat Landscape
The cybersecurity landscape is in constant flux, with new threats emerging at an alarming rate. Staying ahead of these evolving threats requires a proactive and adaptable approach to vulnerability management. Traditional vulnerabilities are no longer sufficient to define the scope of risk. Modern attackers are increasingly sophisticated, employing innovative techniques and leveraging automation to exploit vulnerabilities across diverse attack surfaces.The rapid adoption of cloud computing, the Internet of Things (IoT), and software supply chains has created new attack vectors and widened the attack surface.
Understanding these evolving threats is crucial to developing effective defense strategies for the future. This includes recognizing the impact of artificial intelligence (AI) on both offensive and defensive strategies, and studying real-world examples of attacks to identify patterns and potential future threats.
Emerging Cybersecurity Threats
Sophisticated attacks are becoming increasingly common, with attackers employing advanced techniques to bypass traditional security measures. Zero-day exploits, vulnerabilities unknown to vendors, pose a significant threat, allowing attackers to exploit weaknesses before patches are available. Furthermore, the automation of malicious activities is amplifying the scale and speed of attacks, enabling attackers to launch coordinated campaigns more efficiently. This shift towards automated attacks requires a more dynamic and proactive approach to vulnerability management.
Shift from Traditional to Modern Vulnerabilities
The traditional focus on vulnerabilities in on-premises systems is no longer sufficient. The rise of cloud computing, IoT devices, and software supply chains has created new avenues for exploitation. Cloud-based vulnerabilities, such as misconfigurations and insecure APIs, can expose sensitive data and applications to attackers. IoT devices, often lacking robust security features, can be vulnerable to compromise, leading to widespread network disruptions.
Software supply chain attacks, where malicious code is introduced into trusted software components, can have far-reaching consequences, affecting multiple systems and organizations. The growing complexity of interconnected systems increases the attack surface, making it harder to identify and remediate vulnerabilities.
Role of AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are transforming the cybersecurity landscape. They are used in both offensive and defensive strategies. Attackers are leveraging AI to automate the discovery and exploitation of vulnerabilities, while defenders are employing AI and ML to detect anomalies and predict potential attacks. The ongoing arms race between offensive and defensive AI highlights the need for continuous adaptation and innovation in vulnerability management strategies.
AI-powered threat intelligence systems can provide valuable insights into emerging threats and vulnerabilities. Furthermore, ML algorithms can analyze large volumes of data to identify patterns and predict future attack vectors.
Preparing for the future of vulnerability management means staying ahead of the curve, and that includes understanding specific vulnerabilities like those in Azure services. For example, knowing the details about Microsoft Azure Cosmos DB vulnerabilities, like those detailed in this resource Azure Cosmos DB Vulnerability Details , is crucial for proactive security planning. This knowledge will help organizations fortify their defenses and adapt to the evolving threat landscape.
Real-World Attack Examples
Numerous real-world attacks demonstrate the growing sophistication and impact of modern threats. The SolarWinds supply chain attack, for instance, highlighted the potential for devastating consequences of targeting software supply chains. The increasing prevalence of ransomware attacks underscores the need for robust data protection and disaster recovery plans. Understanding the motivations, tactics, and techniques (MTTS) of these attacks is crucial to predicting and preventing future vulnerabilities.
Increasing Sophistication of Attack Vectors
| Threat Type | Attack Vector | Sophistication Level |
|---|---|---|
| Ransomware | Exploiting vulnerabilities in software or using phishing | High |
| Supply Chain Attacks | Introducing malicious code into trusted software components | Very High |
| Cloud-Based Attacks | Exploiting misconfigurations or insecure APIs | Medium to High |
| IoT Attacks | Compromising vulnerable IoT devices to disrupt networks | Medium |
| Advanced Persistent Threats (APTs) | Employing sophisticated techniques to gain and maintain access to networks | Extremely High |
This table illustrates the growing sophistication of attack vectors, demonstrating the need for comprehensive vulnerability management strategies. Each threat type requires a tailored approach to mitigation and remediation.
Modernizing Vulnerability Management Processes: How To Prepare For The Future Of Vulnerability Management
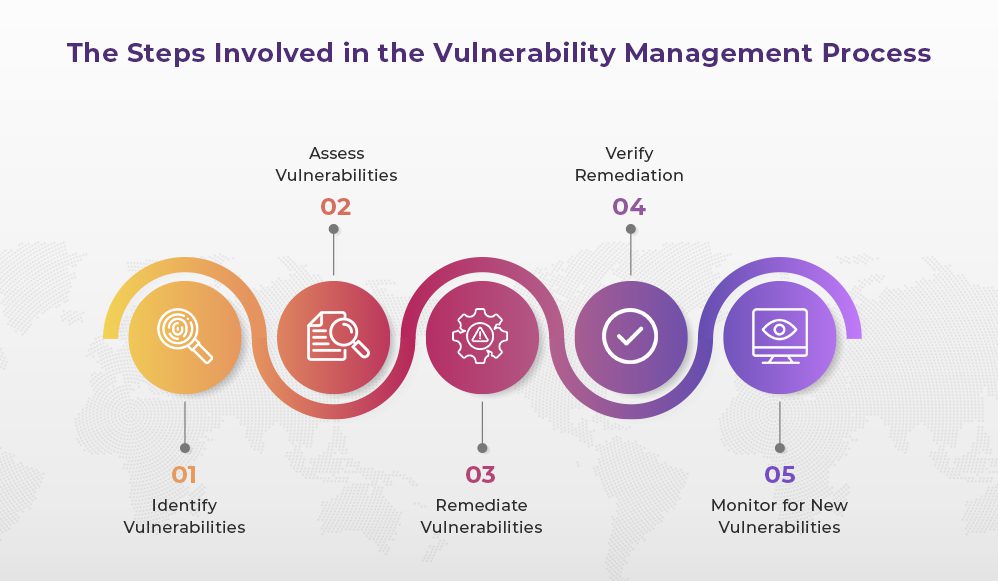
Staying ahead of evolving cyber threats demands a shift from reactive to proactive vulnerability management. Simply patching vulnerabilities after they’ve been exploited is no longer sufficient. Organizations need a robust, automated system that identifies and mitigates risks before they can be exploited. This approach requires a modernization of existing processes and a focus on automation.A proactive vulnerability management strategy anticipates and addresses potential security weaknesses before they are actively targeted.
This is a critical element in building a resilient security posture. This approach enables organizations to significantly reduce the likelihood of successful attacks and the associated financial and reputational damage.
Shifting from Reactive to Proactive Strategies
Vulnerability management has traditionally been reactive, responding to identified vulnerabilities after they’ve been discovered. This approach often results in delayed remediation, leaving organizations exposed to potential attacks. A proactive strategy, however, anticipates and addresses potential security weaknesses before they are actively targeted. This approach prioritizes continuous monitoring and automated responses to emerging threats. Proactive strategies also involve incorporating threat intelligence into vulnerability scanning and remediation processes.
Automating Vulnerability Scanning, Assessment, and Remediation, How to prepare for the future of vulnerability management
Automating vulnerability scanning, assessment, and remediation processes is crucial for efficiency and scalability. Manual processes are time-consuming and prone to errors, leading to vulnerabilities remaining unpatched for extended periods. Automated systems, on the other hand, can scan networks and applications continuously, identifying and prioritizing vulnerabilities in real-time. Automated remediation tools further enhance the efficiency by automatically applying patches or configuring systems to mitigate the risk.
Automated processes also enable organizations to manage a large attack surface and ensure a more rapid response to vulnerabilities.
Getting ready for tomorrow’s vulnerability management requires a proactive approach. We need to start thinking about how to best integrate cutting-edge tools like those highlighted in Deploying AI Code Safety Goggles Needed. This means staying ahead of the curve and embracing innovative solutions to identify and mitigate potential threats, ultimately strengthening our defenses against future attacks.
The Role of SOAR Tools
Security Orchestration, Automation, and Response (SOAR) tools play a vital role in streamlining vulnerability management. These tools integrate with various security systems, enabling automated workflows for vulnerability scanning, assessment, and remediation. SOAR tools automate the entire process, from identifying vulnerabilities to applying fixes, drastically reducing the time and resources required for each step. They also help in coordinating security teams and facilitating a more coordinated response to threats.
Getting ready for the future of vulnerability management requires a proactive approach. Understanding recent legal developments, like the Department of Justice’s new Safe Harbor policy for Massachusetts transactions, Department of Justice Offers Safe Harbor for MA Transactions , is crucial. This knowledge, combined with robust security protocols and regular vulnerability assessments, will help you stay ahead of the curve in this ever-evolving landscape.
Comparing Vulnerability Management Platforms
Different vulnerability management platforms offer varying capabilities and features. Some platforms specialize in network scanning, while others focus on application security. The choice of platform depends on the specific needs and resources of the organization. Factors to consider include the size and complexity of the network, the types of applications in use, and the budget for security tools.
Features such as reporting, dashboards, and integration with other security tools should also be evaluated. The platform chosen should be scalable and adaptable to the evolving threat landscape.
Automated Vulnerability Scanning Tools
Automated vulnerability scanning tools are essential for proactively identifying security weaknesses. Different tools cater to various needs and environments.
| Tool | Strengths | Weaknesses |
|---|---|---|
| Nessus | Wide range of scans, comprehensive vulnerability database, good reporting capabilities. | Can be resource-intensive, may require dedicated expertise to configure and use effectively. |
| OpenVAS | Open-source and free, highly customizable. | Requires more technical expertise to manage compared to proprietary tools. |
| Qualys | Comprehensive platform with cloud-based solutions, scalability for large environments. | Can be expensive for smaller organizations. |
| Rapid7 | Strong in application scanning and integration with other security tools. | Potential limitations for specific vulnerability types or older technologies. |
This table provides a basic comparison, and specific strengths and weaknesses may vary depending on the organization’s environment and requirements.
Building a Future-Proof Security Team
Preparing for the future of vulnerability management requires more than just technical expertise. It demands a robust, adaptable security team capable of navigating the ever-evolving threat landscape. This team needs to be proactive, adaptable, and deeply integrated with the organization’s overall strategy. A future-proof security team fosters a culture of security, continuously learns, and collaborates seamlessly with development teams.Modern vulnerability management is not a siloed operation; it’s a crucial component of the broader cybersecurity strategy.
To succeed, security teams must possess a diverse skillset, constantly update their knowledge, and work closely with developers to proactively address vulnerabilities before they are exploited. Building a security-conscious culture is equally important. This means embedding security principles into every aspect of the organization’s operations.
Essential Skills and Knowledge for a Modern Vulnerability Management Team
A modern vulnerability management team needs individuals with a strong understanding of both technical and soft skills. Essential technical skills include proficiency in vulnerability scanning tools, scripting languages (e.g., Python), and knowledge of various operating systems and network architectures. A deep understanding of the OWASP Top 10 and common attack vectors is also crucial. Beyond technical expertise, soft skills like communication, problem-solving, and collaboration are paramount for effective vulnerability management.
The ability to clearly articulate technical findings to non-technical stakeholders and collaborate effectively with development teams is vital for successful vulnerability remediation.
Importance of Continuous Learning and Development
The cybersecurity landscape changes rapidly. Staying current with the latest threats, vulnerabilities, and security best practices is essential for effective vulnerability management. Continuous learning is critical to maintaining a competitive edge. This includes attending conferences, workshops, and webinars, engaging in online courses, and actively participating in cybersecurity communities. For example, the MITRE ATT&CK framework provides a detailed understanding of adversary tactics, techniques, and procedures (TTPs), which is vital for anticipating and responding to emerging threats.
Collaboration Between Security and Development Teams
Effective vulnerability management hinges on strong collaboration between security and development teams. A proactive approach where security is embedded into the development lifecycle, from design to deployment, is critical. Security should be a shared responsibility, not a burden for security teams alone. Implementing security best practices during the development process can significantly reduce the number of vulnerabilities that reach production.
Tools like static analysis and dynamic application security testing (DAST) can help identify vulnerabilities early in the development cycle, preventing them from reaching production. This collaborative approach helps improve security posture and fosters a culture of security awareness.
Creating a Culture of Security Awareness
Security awareness training is not just about teaching users how to identify phishing emails. It’s about fostering a culture where security is a shared value and responsibility. This involves educating all employees about common threats, best practices for password management, and the importance of reporting suspicious activities. Security awareness training programs should be regular, engaging, and relevant to the specific roles and responsibilities of employees.
This approach empowers employees to act as the first line of defense against cyber threats.
Necessary Certifications and Training Programs
| Certification/Training Program | Description ||—|—|| CompTIA Security+ | Foundational security certification covering various security domains. || Certified Ethical Hacker (CEH) | Certification focusing on penetration testing and ethical hacking techniques. || Certified Information Systems Security Professional (CISSP) | Comprehensive security certification covering a wide range of security domains. || SANS Institute Courses | Wide range of security courses covering specific technologies and topics.
|| OWASP Training | Courses on web application security and the OWASP Top 10. || Various vendor-specific training | Courses on specific security tools and technologies. |These certifications and training programs provide valuable knowledge and skills for vulnerability management professionals, helping them stay up-to-date with the latest security trends and best practices. Regular updates and ongoing learning are key to remaining effective in this dynamic field.
Implementing a DevSecOps Approach
Embracing a DevSecOps philosophy is no longer a futuristic aspiration but a crucial necessity for organizations striving to deliver secure software rapidly. Integrating security into the software development lifecycle (SDLC) from the outset, rather than as an afterthought, significantly reduces vulnerabilities and fosters a culture of proactive security. This approach aligns perfectly with the dynamic nature of today’s threat landscape, enabling businesses to adapt and respond effectively to evolving security challenges.
DevSecOps Methodology and Vulnerability Management Integration
DevSecOps is a cultural and methodological shift that integrates security practices into the software development lifecycle. It’s not merely a set of tools but a paradigm shift emphasizing collaboration and shared responsibility between development, security, and operations teams. This collaborative model fosters a proactive security mindset throughout the entire software development process. Vulnerability management becomes an integral part of the development workflow, rather than a separate, often-overlooked, process.
Embedding Security into the SDLC
Embedding security into the SDLC is paramount. Security should be considered a fundamental aspect of every stage, from initial design to final deployment. This proactive approach reduces the likelihood of vulnerabilities entering the codebase and minimizes the time and cost associated with patching vulnerabilities later in the process. Security is no longer an afterthought; it’s an integral part of the development process.
Security Tools within the CI/CD Pipeline
Integrating security tools directly into the CI/CD pipeline is critical for automating vulnerability detection and remediation. Tools like static application security testing (SAST) tools, dynamic application security testing (DAST) tools, and interactive application security testing (IAST) tools can be integrated into automated build and deployment pipelines. This ensures that security checks are performed at each stage, preventing vulnerabilities from entering production environments.
By automating security checks, teams can ensure consistent and reliable security practices throughout the software development lifecycle.
Integrating Vulnerability Scanning and Remediation into the Development Workflow
Vulnerability scanning and remediation should be seamlessly integrated into the development workflow. This means incorporating vulnerability scanning into the build process, and automatically triggering remediation steps when vulnerabilities are identified. Automated tools can provide developers with immediate feedback on vulnerabilities and guide them through remediation processes, reducing the time to resolution and promoting a culture of secure coding.
This automated feedback loop shortens the feedback cycle, allowing developers to address security concerns quickly and effectively.
Steps of Incorporating Security into the SDLC
| Step | Description | Tools | Procedures |
|---|---|---|---|
| Design | Security considerations are embedded in the initial design phase, such as secure coding practices and threat modeling. | Threat modeling tools, secure design patterns | Requirement reviews, security risk assessments, secure design documentation |
| Development | Developers utilize secure coding guidelines and write secure code from the start. | Static Application Security Testing (SAST) tools (e.g., SonarQube), Interactive Application Security Testing (IAST) tools | Code reviews, adherence to coding standards, secure coding training |
| Build | Security testing is integrated into the build pipeline, such as automated vulnerability scanning. | SAST, DAST, Software Composition Analysis (SCA) tools (e.g., Snyk) | Automated build scripts, integration into CI/CD pipeline |
| Test | Vulnerabilities are identified and addressed during various testing phases (unit, integration, system, and acceptance testing). | Dynamic Application Security Testing (DAST) tools (e.g., OWASP ZAP), Penetration testing tools | Automated testing scripts, integration into CI/CD pipeline |
| Deployment | Security measures are implemented during deployment, including secure configuration management and access controls. | Configuration management tools (e.g., Ansible), Infrastructure as Code (IaC) tools | Automated deployment scripts, secure configuration management, access control |
Leveraging AI and Machine Learning for Prediction
The future of vulnerability management is intrinsically linked to the ability to anticipate and prevent emerging threats. Traditional methods often struggle to keep pace with the rapid evolution of cyberattacks. AI and machine learning offer a powerful approach to predict and prevent vulnerabilities, moving beyond reactive patching to proactive threat mitigation.AI-powered systems can analyze vast datasets of security events, code repositories, and known vulnerabilities to identify patterns and anomalies indicative of potential future threats.
This predictive capability empowers security teams to allocate resources effectively and prioritize remediation efforts, significantly reducing the risk of successful attacks.
Potential of AI and Machine Learning for Vulnerability Prediction
AI and machine learning algorithms can identify subtle indicators of vulnerabilities within software code and configurations. By analyzing historical data on vulnerabilities, attack patterns, and software development practices, these systems can detect anomalies that might signal a new vulnerability type or exploit method. This proactive approach to vulnerability management allows organizations to mitigate potential risks before they are exploited.
For instance, AI can analyze code changes for potential injection vulnerabilities or memory leaks, flagging them for immediate review.
Anomaly Detection Techniques for Suspicious Activities
Anomaly detection techniques are crucial in identifying suspicious activities that might indicate a vulnerability or attack. These techniques use statistical models and machine learning algorithms to establish baseline behaviors. Deviations from these baselines are flagged as potential anomalies, alerting security teams to suspicious activities that might lead to vulnerabilities. Examples include unusual network traffic patterns, unexpected user logins, or atypical file access attempts.
Automation of Vulnerability Analysis and Prioritization
AI can automate the process of vulnerability analysis and prioritization, significantly improving efficiency and reducing manual effort. Instead of manually scanning and analyzing software components, AI algorithms can quickly identify vulnerabilities, assess their severity, and prioritize them based on factors like exploitability and potential impact. This automation allows security teams to focus on critical vulnerabilities requiring immediate attention.
For example, AI can prioritize vulnerabilities based on the likelihood of exploitation, considering factors such as the prevalence of exploits targeting a specific vulnerability, and the frequency of related attack attempts.
Ethical Considerations of Using AI in Vulnerability Management
The ethical implications of using AI in vulnerability management are significant. Bias in training data can lead to inaccurate predictions and unfair targeting of specific vulnerabilities or systems. Furthermore, the potential for misuse of AI-powered tools by malicious actors should be carefully considered. Organizations must ensure that their AI systems are transparent and explainable, enabling security teams to understand the rationale behind the predictions and prioritize vulnerabilities responsibly.
AI-Powered Vulnerability Analysis Tools
| Tool | Strengths | Weaknesses |
|---|---|---|
| Vulnerability Intelligence Platform (VIP) | Provides comprehensive vulnerability intelligence, including threat intelligence and risk assessments. | Can be complex to implement and require significant data analysis expertise. |
| Automated Vulnerability Scanner (AVS) | Quickly identifies vulnerabilities across diverse software applications and systems. | May require extensive configuration and fine-tuning to achieve optimal results. |
| AI-Powered Security Information and Event Management (SIEM) | Provides real-time threat detection and response capabilities. | Requires large amounts of historical data to train the AI models effectively. |
Adapting to the Cloud and IoT Environments
The rapid adoption of cloud-based infrastructure and the proliferation of Internet of Things (IoT) devices have fundamentally altered the threat landscape. These environments introduce unique security vulnerabilities that traditional on-premises security approaches struggle to address effectively. Successfully navigating this new terrain requires a proactive and adaptable vulnerability management strategy.Cloud environments, with their distributed and dynamic nature, present a complex challenge.
Security breaches can originate from misconfigurations in virtual machines, inadequate access controls, or vulnerabilities in third-party services integrated into the cloud infrastructure. IoT devices, often lacking robust security features, are susceptible to exploitation, potentially leading to widespread network compromise. Addressing these distinct threats necessitates a nuanced understanding of the specific vulnerabilities inherent in each environment.
Cloud Security Challenges
Cloud environments introduce a range of security challenges that differ significantly from traditional on-premises models. These include:
- Shared Responsibility Model: Cloud providers typically handle the security of the underlying infrastructure, but customers are responsible for securing their data and applications running on that infrastructure. Understanding this division of responsibility is crucial for implementing effective security measures.
- Dynamic Environments: Cloud resources are constantly changing, introducing new vulnerabilities and configurations. Maintaining a constant vigilance over these dynamic environments is vital for proactively addressing emerging threats.
- Third-Party Dependencies: Cloud environments frequently rely on third-party services and APIs. Vulnerabilities in these external components can compromise the entire cloud environment.
- Access Control Complexity: Managing access control in a distributed cloud environment is more complex than in a traditional network. Implementing robust identity and access management (IAM) solutions is critical.
IoT Security Challenges
The security of IoT devices is a growing concern. These devices often have limited processing power, memory, and security features. This makes them highly susceptible to various attacks.
- Limited Resources: Many IoT devices have constrained computing resources, which limits the effectiveness of security measures. Consequently, security implementations must be lightweight and efficient.
- Lack of Security Features: Many IoT devices lack basic security features, such as strong authentication, encryption, and vulnerability scanning. This exposes them to exploitation by attackers.
- Lack of Patching Mechanisms: Updating and patching IoT devices can be difficult, or even impossible, due to various constraints. This creates a constant vulnerability to known exploits.
- Lack of Visibility: Monitoring and managing the security of a large number of IoT devices can be challenging. Lack of visibility into device activity can hinder the ability to detect and respond to security incidents.
Securing Cloud Environments
Implementing a robust zero-trust security model is critical for cloud environments. This approach assumes no implicit trust, verifying every user and device attempting access, regardless of their location within the network.
- Zero Trust: Adopt a zero-trust security model. Verify every user and device, regardless of location or network access, before granting access. This limits the impact of a breach, as access is not automatically granted.
- Cloud-Native Application Security: Secure cloud-native applications and microservices by implementing security practices from the development stage. This includes incorporating security testing into the CI/CD pipeline.
- Regular Security Assessments: Conduct regular security assessments to identify and remediate vulnerabilities. This includes penetration testing, vulnerability scanning, and configuration reviews.
Securing IoT Devices
Developing a robust security strategy for IoT devices is crucial. This involves a multifaceted approach that includes device hardening, secure communication protocols, and regular updates.
- Device Hardening: Implement security hardening on IoT devices. This includes configuring strong passwords, restricting access, and disabling unnecessary services.
- Secure Communication: Utilize secure communication protocols such as HTTPS for data transmission. Implement encryption to protect data in transit and at rest.
- Regular Updates: Maintain up-to-date firmware and software on IoT devices to address known vulnerabilities.
- Segmentation: Segment IoT devices from the rest of the network to limit the impact of a breach.
Best Practices for Cloud and IoT Security
A comprehensive approach is essential to secure both cloud and IoT environments. The following practices provide a framework for developing a robust security posture:
| Category | Best Practice |
|---|---|
| Cloud Security | Implement a robust zero-trust security model. |
| Cloud Security | Use security-hardened images for virtual machines. |
| Cloud Security | Employ strong access controls and least privilege principles. |
| IoT Security | Utilize secure communication protocols. |
| IoT Security | Implement device hardening procedures. |
| IoT Security | Develop and enforce security policies. |
Fostering a Culture of Security
Building a strong security posture isn’t just about technology; it’s fundamentally about people. A culture of security, where everyone understands and embraces their role in protecting sensitive data and systems, is crucial for mitigating risks and ensuring business continuity. This culture permeates every level of the organization, from the CEO to the newest intern.A robust security culture starts with understanding the importance of everyone’s contribution.
Employees are often the weakest link in the security chain, but also the strongest line of defense. Proactive training and engagement empower them to recognize and report potential threats, ultimately strengthening the overall security posture.
Security Awareness Training for All Employees
Security awareness training is a cornerstone of a strong security culture. It educates employees about common threats, best practices, and their individual responsibilities in maintaining security. This training isn’t a one-time event but an ongoing process of reinforcement and updates.Effective security awareness training programs should cover a wide range of topics, including phishing scams, social engineering tactics, malware recognition, password management, and safe internet browsing.
Examples of Effective Security Awareness Programs
Several effective security awareness programs use interactive methods to keep employees engaged. Simulated phishing emails, real-world case studies of security breaches, and gamified training modules are all excellent approaches. These methods make learning more memorable and engaging, leading to better retention of critical security information. Regular quizzes and assessments reinforce the knowledge acquired. A successful program often includes a feedback loop to allow employees to provide input and suggestions for improvement.For example, a company might use a platform that tracks employee performance in identifying phishing attempts.
This gamified approach can incentivize employees to participate and improve their security awareness skills.
Promoting a Culture of Security Through Leadership and Employee Engagement
Leadership plays a critical role in establishing and maintaining a security-conscious culture. Executives must clearly communicate the importance of security, demonstrate their commitment through their actions, and actively participate in security initiatives. Security should be integrated into every aspect of the company’s operations and communication.Furthermore, promoting employee engagement is key. This involves creating opportunities for employees to share their security concerns, offer suggestions, and contribute to the security strategy.
Security committees, brainstorming sessions, and regular security updates via newsletters or internal forums can foster a sense of shared responsibility and encourage active participation. Encouraging employees to report security incidents or suspicious activities, without fear of reprisal, is vital.
Incident Response Planning and Preparation
A comprehensive incident response plan is crucial for managing and mitigating security incidents effectively. This plan should Artikel the procedures for identifying, containing, eradicating, recovering, and learning from security breaches. The plan should be regularly reviewed and updated to address evolving threats. Regular drills and simulations, involving all relevant personnel, help refine the response plan and ensure a smooth and effective execution in case of an actual incident.A clear communication plan during an incident is critical.
Employees must understand who to contact, what information to provide, and how to report incidents appropriately.
Summary of Security Awareness Training Programs
| Training Program | Benefits | Limitations |
|---|---|---|
| Simulated Phishing Emails | Engaging, memorable, reinforces practical skills in recognizing phishing attempts. | Can be perceived as intrusive if not managed properly. Requires constant updates to stay relevant. |
| Interactive Modules | Engaging, adaptable to different learning styles, and often incorporates gamification. | Might require dedicated software or platforms, which could present costs and compatibility issues. |
| Case Studies | Relatable, provides context to real-world threats and encourages understanding of consequences. | May require specialized content development, and it might not be possible to cover all types of incidents. |
| Regular Quizzes and Assessments | Reinforces knowledge retention, and tracks progress. | Might not be effective if not tied to real-world application and practice. |
Conclusion
In conclusion, successfully navigating the future of vulnerability management requires a multifaceted approach. By understanding the evolving threat landscape, modernizing processes, building a skilled security team, and implementing DevSecOps, organizations can proactively mitigate risks. Embracing AI, adapting to cloud and IoT environments, and fostering a culture of security are all essential components of a robust vulnerability management strategy.
The key takeaway is that the future of vulnerability management is about constant adaptation and innovation.
Answers to Common Questions
What are some key indicators of a sophisticated attack?
Sophisticated attacks often exhibit indicators like advanced persistent threats (APTs), zero-day exploits, and highly targeted social engineering campaigns. These attacks are typically more complex and difficult to detect than traditional attacks.
How can I prioritize vulnerabilities?
Vulnerability prioritization involves considering factors like the potential impact, exploitability, and likelihood of the vulnerability being exploited. Using tools that assess these factors can help prioritize remediation efforts effectively.
What is the role of a security awareness program?
A robust security awareness program educates employees about common threats, best practices, and how to identify phishing attempts and other malicious activities. This crucial element of security is often overlooked.
What are the most important considerations when selecting vulnerability scanning tools?
Consider factors such as the tool’s ability to scan various platforms, its coverage of different vulnerability types, its integration capabilities, and its reporting features when selecting vulnerability scanning tools.