How to Protect Against Costly Ransomware
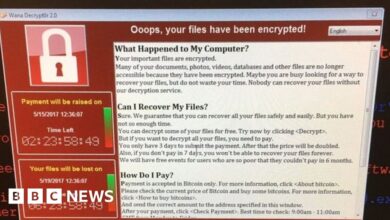
How to protect against the costly impacts of ransomware is crucial in today’s digital landscape. Cyberattacks are increasingly sophisticated, and businesses of all sizes are vulnerable. This guide delves into comprehensive strategies to prevent, mitigate, and respond to ransomware attacks, minimizing financial and operational disruption.
We’ll explore robust endpoint security, essential data backup and recovery procedures, critical employee training, and crucial incident response planning. Understanding the financial and legal implications of ransomware is also vital. By implementing these practical steps, organizations can significantly reduce their risk and build resilience against these costly threats.
Prevention Strategies

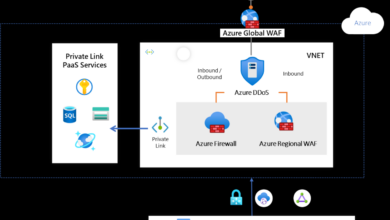
Protecting your business from ransomware requires a proactive, multi-layered approach. A robust security posture, encompassing endpoint protection, access controls, and regular updates, significantly reduces the risk of successful attacks. This section delves into practical strategies for building a strong defense against ransomware.Effective ransomware prevention hinges on understanding and implementing comprehensive security measures. Failing to address these vulnerabilities leaves your organization exposed to costly data breaches and operational disruptions.
These strategies, when integrated, create a formidable barrier against malicious actors.
Robust Endpoint Security Measures
Endpoint security is paramount in mitigating ransomware risks. Implementing strong security measures at the endpoint level acts as the first line of defense against malware. This involves deploying advanced threat detection and prevention technologies to identify and block malicious activities before they can cause harm.
- Advanced Threat Protection (ATP): ATP solutions employ sophisticated techniques to detect and respond to sophisticated attacks, including ransomware. These tools use machine learning and behavioral analysis to identify malicious patterns that traditional antivirus software might miss. Examples include identifying malicious macros, suspicious file modifications, and unusual network communication patterns.
- Intrusion Prevention Systems (IPS): IPS solutions actively monitor network traffic and block malicious activity, including ransomware attempts. They analyze network packets and identify known attack signatures. They can also block known malicious IP addresses and domains.
- Antimalware and Antivirus Software: Maintaining up-to-date antivirus and antimalware software is crucial. These tools scan files and processes in real-time, detecting and neutralizing known malware threats, including ransomware. Regular updates are essential to keep these tools effective against emerging threats.
Multi-Layered Security Architectures
Implementing a multi-layered security architecture is essential for organizations of all sizes. This approach involves combining multiple security technologies and controls to create a more comprehensive defense against various threats.
Protecting against ransomware’s hefty price tag involves more than just backups. Modern threats require proactive measures, like implementing robust security protocols and, crucially, deploying AI-powered tools. For instance, checking your code for vulnerabilities before deployment is crucial, and Deploying AI Code Safety Goggles Needed highlights the importance of this approach. Ultimately, staying ahead of the curve through advanced security measures is key to preventing costly ransomware attacks.
- Small Businesses: Small businesses can leverage cloud-based security solutions, which often include features like file encryption and access controls, along with robust antivirus software. A well-configured firewall can also act as a vital first line of defense.
- Medium-Sized Businesses: Medium-sized businesses should incorporate network segmentation to isolate critical systems from less secure parts of the network. They should also utilize intrusion detection and prevention systems (IDS/IPS) to monitor and block suspicious activity. Endpoint detection and response (EDR) tools can help detect and respond to threats on individual devices.
- Large Enterprises: Large enterprises require a more complex architecture involving advanced security information and event management (SIEM) systems. These systems correlate security events across various systems to identify patterns and potential threats. They should also implement security awareness training for employees to educate them about phishing and other social engineering tactics used in ransomware attacks.
Strong Access Controls and User Authentication
Implementing robust access controls and user authentication is vital for preventing unauthorized access to sensitive data. A well-defined access policy limits the ability of malicious actors to gain control of critical systems.
- Principle of Least Privilege: Grant users only the necessary access rights to perform their job duties. Restricting unnecessary access significantly reduces the impact of a compromised account.
- Multi-Factor Authentication (MFA): Enforce MFA for all user accounts, adding an extra layer of security. This requires users to provide multiple forms of verification before gaining access to systems.
- Regular Account Reviews: Regularly review and update user accounts to ensure that access rights align with current roles and responsibilities. Remove accounts for former employees or contractors immediately to reduce risk.
Regular Software and Operating System Updates
Regularly updating software and operating systems is essential to patch known vulnerabilities. Cybercriminals often exploit known vulnerabilities to deploy ransomware.
Protecting against ransomware’s hefty price tag is crucial. Regular backups are a must, and robust cybersecurity measures are essential. Recent news about the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions highlights a potential avenue for recovery in certain situations. But ultimately, a proactive approach to data security remains the best defense against the devastating impact of ransomware attacks.
- Automated Updates: Configure systems to automatically download and install security updates. This minimizes the window of opportunity for attackers to exploit vulnerabilities.
- Patch Management System: Implement a dedicated patch management system to streamline the update process and ensure all systems are patched promptly. This system should track the status of patches for all systems and applications.
- Vulnerability Scanning: Conduct regular vulnerability scans to identify potential weaknesses in your systems and applications. This helps prioritize patching efforts based on the risk level.
Security Solution Comparison
Comparing different security solutions helps organizations select the best fit for their needs.
| Feature | Benefit |
|---|---|
| Real-time threat detection | Quickly identifies and blocks malicious activity, reducing the risk of successful ransomware attacks. |
| Vulnerability scanning | Proactively identifies vulnerabilities in systems and applications, enabling timely patching. |
| Intrusion prevention | Stops known and unknown threats, including ransomware attacks, from reaching the network. |
| Anti-malware scanning | Detects and removes existing malware infections, reducing the likelihood of data breaches. |
| Endpoint detection and response (EDR) | Provides comprehensive visibility into endpoint activity, enabling faster incident response. |
Data Backup and Recovery
Ransomware attacks can cripple businesses, leading to significant financial losses and operational disruption. A crucial component in mitigating these risks is a robust data backup and recovery strategy. Failing to regularly back up data leaves organizations vulnerable to complete data loss, making it impossible to resume operations.A comprehensive data backup and recovery plan is not just a precaution; it’s a necessity in today’s digital landscape.
This plan must go beyond simply creating backups. It should include clear procedures for testing recovery processes, verifying data integrity, and ensuring quick restoration in case of a ransomware incident. The strategy should also incorporate off-site storage for added security.
Importance of Regular Data Backups
Regular data backups are paramount for ransomware recovery. They provide a crucial safety net, allowing organizations to restore their systems and data quickly after an attack. Without backups, the recovery process can be extremely time-consuming, expensive, and often impossible. Regular backups prevent significant financial losses and ensure minimal disruption to operations.
Comprehensive Data Backup Strategy
A comprehensive data backup strategy should include several key elements. First, identify all critical data. Next, develop a schedule for regular backups, ensuring frequency aligns with data modification rates. A crucial component is off-site storage. Storing backups off-site ensures data safety even if the primary location experiences a disaster, including a ransomware attack.
Data should be encrypted and stored securely to prevent unauthorized access.
Creating and Testing Backup and Recovery Plans
Creating a backup and recovery plan requires careful planning and execution. A step-by-step guide should include:
- Identifying critical data and systems.
- Determining the frequency and type of backups needed.
- Choosing a backup solution and configuring it correctly.
- Establishing off-site storage locations for backups.
- Regularly testing the backup and recovery process.
- Documenting all procedures and contact information.
Thorough testing is essential. Regularly test the backup and recovery process to verify its effectiveness and identify any potential issues. This includes simulating a ransomware attack to ensure the recovery process works as intended.
Version Control in Data Backups
Version control in data backups is vital for ransomware recovery. It allows you to revert to previous versions of files if needed, even if the most recent version is encrypted by ransomware. This feature is particularly helpful for restoring files or systems to a point in time before the attack. Version control enhances data integrity and provides a fallback option.
Backup Technologies and Their Pros and Cons
Various backup technologies are available, each with its own strengths and weaknesses.
- Cloud-based backups offer scalability, accessibility, and often automatic backups, but reliance on internet connectivity can be a drawback. Security measures and data encryption should be carefully considered.
- On-premises backups provide better control over data and infrastructure, but require significant investment in hardware and maintenance. They are susceptible to local disasters and may not offer the same scalability as cloud-based options.
- Hybrid solutions combine on-premises and cloud-based backups to offer the benefits of both approaches. This approach offers greater flexibility and can improve data redundancy.
Disaster Recovery Plans Including Ransomware Recovery
Disaster recovery plans should explicitly include ransomware recovery procedures. These plans should Artikel steps for identifying an attack, containing the spread of malware, restoring systems from backups, and recovering data. A thorough plan will guide decision-making and minimize disruption. Consider including communication protocols, contact lists, and roles and responsibilities in the event of a ransomware attack.
Comparison of Backup Solutions
| Solution | Cost | Features | Reliability |
|---|---|---|---|
| Cloud-based Backup (e.g., Dropbox, Google Drive) | Variable (often tiered pricing) | Ease of use, scalability, accessibility | High (depending on vendor reliability and security measures) |
| On-premises Backup (e.g., NAS devices) | Variable (depending on hardware and software) | High level of control | Medium to High (dependent on proper maintenance) |
| Hybrid Backup (e.g., Combining Cloud and NAS) | Variable (combination of cloud and on-premises costs) | Enhanced flexibility and data redundancy | High (combines the strengths of both approaches) |
Employee Training and Awareness
Protecting against ransomware requires a multifaceted approach, and employee training is a crucial component. Educating your workforce about the risks and how to recognize potential threats is paramount in preventing successful attacks. A well-structured training program empowers employees to act as the first line of defense against ransomware.Effective employee training goes beyond simply presenting information. It should incorporate practical exercises and real-world scenarios to solidify understanding and promote retention.
This proactive approach fosters a security-conscious culture within the organization, reducing the likelihood of human error, a significant vector for ransomware infiltration.
Phishing Scam Identification
Employee training should prioritize recognizing and avoiding phishing scams, which are a common tactic used by ransomware attackers. Employees need to understand the subtle signs of a fraudulent email or message, such as poor grammar, unusual requests, or suspicious links. A clear understanding of phishing tactics will enable employees to avoid clicking on malicious links or downloading infected attachments.
Protecting against ransomware’s hefty price tag requires a layered approach. Regular backups, strong passwords, and up-to-date software are crucial. However, understanding vulnerabilities like the ones recently discovered in Azure Cosmos DB is also key. For instance, knowing the specifics of these vulnerabilities, like those detailed in Azure Cosmos DB Vulnerability Details , allows for proactive measures to be implemented, thus fortifying your defenses against future attacks.
Ultimately, comprehensive security planning and continuous vigilance are vital to ward off ransomware threats.
Recognizing Suspicious Emails and Attachments
A robust training program should Artikel a clear procedure for recognizing suspicious emails and attachments. Employees should be taught to scrutinize the sender’s email address, look for misspellings or grammatical errors, and question the legitimacy of the email’s content. Checking for unusual requests, such as urgent financial transactions or password resets, is crucial. Attachments should be treated with extreme caution, and only opened if the sender and content are unequivocally trusted.
Common Ransomware Attack Techniques and Avoidance
Training should cover various ransomware attack techniques and how to avoid them. Employees need to understand the methods employed by attackers, such as spear phishing (targeting specific individuals), social engineering (manipulating individuals into divulging sensitive information), and exploiting vulnerabilities in software. For example, employees should know to never click on suspicious links in emails or messages, and to report any suspicious activity immediately.
Furthermore, training should emphasize the importance of strong and unique passwords for all accounts.
Importance of a Security Awareness Program
Establishing a comprehensive security awareness program is essential for fostering a culture of cybersecurity vigilance. Regular training sessions, newsletters, and reminders reinforce the importance of security practices. This ongoing reinforcement ensures that employees consistently apply their knowledge to prevent ransomware incidents. A program should also incorporate rewards for employees who demonstrate proactive security behaviors.
Safe Browsing Habits
Best practices for safe browsing habits should be explicitly detailed in the training program. Employees should be educated about the risks associated with visiting untrusted websites, downloading files from unverified sources, and using insecure Wi-Fi networks. They should understand the importance of using secure browsing tools and keeping their software updated. Encourage employees to avoid accessing potentially risky websites or clicking on unfamiliar links.
Simulated Phishing Attacks for Awareness Testing, How to protect against the costly impacts of ransomware
Simulated phishing attacks are an effective way to test employee awareness and identify areas needing improvement. These exercises provide a safe environment to practice identifying phishing attempts without causing real harm. Analysis of the results of these tests allows for adjustments to the training program to better address specific vulnerabilities and areas of weakness.
Security Awareness Training Resources
Numerous security awareness training resources are available to support your program. These resources provide valuable information, exercises, and templates to enhance your training efforts. Examples include reputable cybersecurity organizations, industry publications, and online courses specifically designed for security awareness training. The use of interactive modules and gamified training can enhance employee engagement and comprehension.
Incident Response Plan
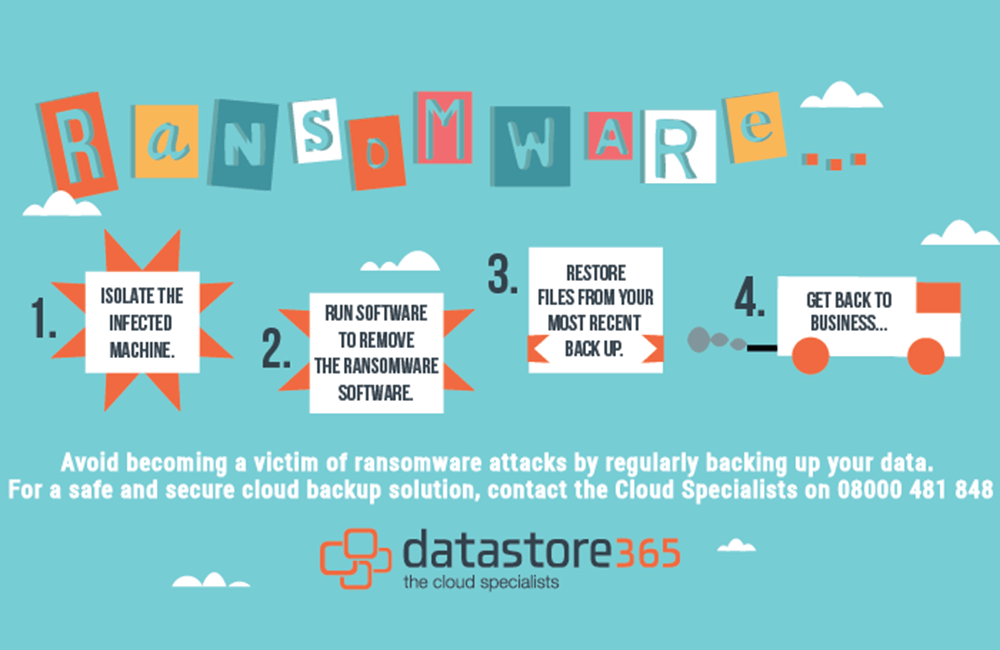
A robust incident response plan is crucial for minimizing the damage and disruption caused by a ransomware attack. This plan acts as a roadmap for your organization’s actions, guiding everyone through the critical steps needed to mitigate the impact and recover from such an event. Effective incident response not only protects your data and systems but also safeguards your reputation and maintains business continuity.A well-defined incident response plan ensures a coordinated and swift reaction to a ransomware attack, minimizing downtime and data loss.
It’s not just about technical fixes; it’s about a comprehensive approach that addresses the human and organizational aspects of the crisis.
Critical Steps for Responding to a Ransomware Attack
Immediate action is paramount in a ransomware attack. A swift and organized response can significantly reduce the scope of the damage. The first step is to identify the attack, contain the spread, and assess the extent of the damage. Understanding the specific tactics used in the attack can inform the recovery process.
Roles and Responsibilities During a Ransomware Incident
Clearly defined roles and responsibilities are essential for effective incident response. Designate specific individuals or teams to handle different aspects of the response. This could include IT personnel, security teams, legal counsel, public relations, and senior management. Each role should have a well-defined set of responsibilities and communication protocols.
Importance of Isolating Affected Systems
Isolating affected systems is a critical step in containing the spread of ransomware. This involves disconnecting infected devices from the network to prevent further encryption and data compromise. This action helps limit the scope of the attack and prevents the ransomware from spreading to other systems. Consider isolating the affected systems as quickly as possible.
Checklist for Handling a Ransomware Attack
A checklist provides a structured approach to managing the incident response process. It ensures that critical steps are not overlooked and that all relevant parties are aware of their responsibilities. The checklist should include actions for initial response, containment, eradication, recovery, and post-incident review.
- Initial Response: Identify the attack, contain the spread, assess the damage.
- Containment: Isolate affected systems, prevent further data compromise.
- Eradication: Remove the malware, restore affected systems.
- Recovery: Restore data and systems from backups, test the restoration process.
- Post-Incident Review: Evaluate the response, identify areas for improvement.
Containing the Spread of Ransomware
Implementing containment strategies is crucial to preventing the ransomware from spreading further. This involves isolating infected systems, disabling network access, and potentially quarantining infected files. It’s important to act quickly to minimize the impact of the ransomware.
Legal and Regulatory Considerations After a Ransomware Attack
Organizations must be aware of legal and regulatory requirements following a ransomware attack. These considerations include notification requirements, incident reporting, and compliance with data privacy regulations. This may include contacting law enforcement and legal counsel to understand the necessary legal procedures.
Key Steps in a Ransomware Incident Response Plan
| Step | Action | Responsible Party |
|---|---|---|
| 1 | Identify the attack | Security Team/IT |
| 2 | Contain the spread | Security Team/IT |
| 3 | Assess the impact | Security Team/IT |
| 4 | Isolate affected systems | Security Team/IT |
| 5 | Notify relevant parties | Management/Legal |
| 6 | Establish communication channels | Management/PR |
| 7 | Recover data from backups | IT/Data Recovery Team |
| 8 | Review and improve plan | Security Team |
Financial and Legal Considerations
Ransomware attacks are more than just a digital threat; they carry significant financial and legal burdens for organizations. Understanding the potential costs and legal ramifications is crucial for developing a robust defense strategy. Beyond the immediate ransom demands, the ripple effects can be devastating, impacting operational efficiency, reputation, and even future profitability. This section explores the multifaceted nature of these implications.The financial and legal fallout from a ransomware attack can be substantial, stretching far beyond the immediate costs of the ransom itself.
A holistic approach to risk mitigation requires a thorough understanding of these interconnected aspects.
Financial Impact of Ransomware Attacks
The financial impact of a ransomware attack extends far beyond the immediate ransom payment. Direct costs include the ransom itself, the expenses incurred during the incident response, such as forensic investigations and system recovery, and the costs of lost productivity. Indirect costs, such as reputational damage, loss of customer trust, and potential regulatory fines, can be even more significant and harder to quantify.
For example, a small business might face a significant blow to its operations if it cannot access critical data needed for customer service or order fulfillment. Larger organizations can experience disruptions in supply chains, impacting millions of dollars in revenue.
Legal Frameworks Relating to Ransomware Attacks
Various legal frameworks can apply to ransomware attacks, depending on the jurisdiction and specific circumstances. These frameworks include data privacy laws (like GDPR or CCPA), anti-money laundering regulations, and cybercrime laws. Compliance with these regulations is essential to avoid penalties and legal repercussions. For instance, if a company fails to properly secure customer data and a ransomware attack occurs, they may face legal challenges under data privacy laws.
Evaluating Financial Implications of a Ransomware Attack
A structured approach to evaluating the financial implications of a ransomware attack is crucial. This framework should consider direct costs (ransom, recovery), indirect costs (lost revenue, reputational damage), and potential future costs (regulatory fines, legal fees). A thorough cost-benefit analysis, taking into account the potential long-term impact, is critical. A detailed financial impact assessment will provide a clear picture of the financial risks involved and the necessary mitigation strategies.
Potential Legal Liabilities Associated with Ransomware Attacks
Organizations face potential legal liabilities if they fail to take reasonable precautions to prevent a ransomware attack. These liabilities can stem from data breaches, non-compliance with data protection regulations, and the failure to adequately secure systems. Examples include the inability to meet regulatory requirements for data security, leading to penalties and legal actions.
Handling Ransom Demands
The decision of whether or not to pay a ransom is a complex one. Organizations must carefully weigh the potential costs and risks of paying against the risks of not paying. Factors to consider include the potential for data loss, business disruption, and reputational damage. Sometimes, paying the ransom can be the lesser of two evils, but it’s not always the case.
Consulting with legal and security experts is essential before making any decision. Organizations should carefully consider the potential implications before making any decision.
Role of Insurance in Mitigating Ransomware Costs
Cyber insurance policies can help mitigate the financial impact of a ransomware attack. These policies can cover ransom payments, incident response costs, and other associated expenses. However, it’s important to understand the limitations and exclusions of the policy. Cyber insurance should be viewed as a complement to a robust security posture, not a replacement for preventative measures.
The specific coverage will depend on the policy details.
Different Legal Options for Organizations Experiencing a Ransomware Attack
Organizations experiencing a ransomware attack have several legal options. These include reporting the incident to law enforcement, pursuing legal action against the attackers, and negotiating with the attackers to minimize financial and operational disruptions. Each option has potential advantages and disadvantages. The best course of action will depend on the specific circumstances of the attack. Consulting with legal counsel is crucial for navigating the legal landscape effectively.
Final Review: How To Protect Against The Costly Impacts Of Ransomware
In conclusion, safeguarding against ransomware requires a multifaceted approach. Proactive measures like robust endpoint security, comprehensive backups, and vigilant employee training are fundamental. Developing a well-defined incident response plan and understanding the financial and legal ramifications are equally critical. By taking these steps, organizations can significantly reduce their vulnerability and better withstand the increasing threat of ransomware attacks.
Helpful Answers
What are some common types of ransomware attacks?
Common ransomware attack types include phishing emails with malicious attachments, exploit kits targeting software vulnerabilities, and supply chain attacks. These attacks can exploit various entry points into a system, emphasizing the importance of multi-layered security defenses.
How often should I back up my data?
Regular, frequent backups are essential. Daily or even more frequent backups, depending on the sensitivity and volume of data, are recommended to ensure recent data is protected. This is crucial for minimizing data loss in case of a ransomware attack.
What are the legal implications of a ransomware attack?
Legal implications vary by jurisdiction. These can include regulatory compliance issues, potential fines, and reputational damage. Understanding the specific legal frameworks and liabilities in your region is crucial.
How can I test my employee’s awareness of ransomware?
Simulated phishing attacks are an effective way to gauge employee awareness. These exercises expose vulnerabilities and allow for targeted training to enhance employee understanding of phishing tactics and malicious emails.