How to Secure Your Apps with SaaS Security Posture Management (SSPM)
How to secure your apps with saas security posture management sspm – How to secure your apps with SaaS security posture management (SSPM) is crucial in today’s cloud-driven world. This guide dives deep into the strategies and tools necessary to fortify your applications against evolving threats. We’ll explore the fundamental principles of SSPM, highlighting the importance of proactive risk identification and implementation steps.
From understanding different types of SaaS applications and their vulnerabilities, to implementing effective security posture management, this comprehensive guide equips you with the knowledge and actionable insights needed to secure your applications. We’ll also discuss crucial tools, best practices, integration with existing security infrastructure, ongoing monitoring, and case studies of successful implementations.
Introduction to SaaS Security Posture Management (SSPM)
SaaS security posture management (SSPM) is a critical component of modern application security. It’s a proactive approach to identifying and mitigating security vulnerabilities within Software-as-a-Service (SaaS) applications. SSPM goes beyond simply patching vulnerabilities; it focuses on maintaining a consistent, secure state across all deployed SaaS applications. This proactive strategy is crucial in today’s rapidly evolving threat landscape.SSPM works by continuously monitoring and assessing the security configuration of SaaS applications, ensuring compliance with security best practices and industry standards.
By automating these processes, organizations can significantly reduce the risk of breaches and ensure that their applications remain resilient against cyberattacks. This continuous monitoring enables organizations to identify and address security issues before they can be exploited by malicious actors.
Core Principles of SSPM
SSPM leverages several key principles to effectively secure SaaS applications. These include continuous monitoring, automated remediation, and centralized management. Continuous monitoring of application configurations and configurations of underlying infrastructure is essential to detect and respond to security threats. Automated remediation helps to quickly address identified vulnerabilities, minimizing the window of exposure. Centralized management ensures that security policies and controls are consistently applied across all SaaS applications.
This centralized approach simplifies security administration and reduces the risk of misconfigurations.
Benefits of Implementing SSPM
Implementing SSPM offers significant advantages for application security. Reduced risk of security breaches is a primary benefit. Early detection of vulnerabilities minimizes the time attackers have to exploit them. Improved compliance with security standards is another key advantage. SSPM helps organizations maintain a secure posture, ensuring compliance with industry regulations and internal policies.
Increased efficiency in security operations is a critical benefit. By automating tasks, SSPM frees up security personnel to focus on more strategic initiatives.
Types of SaaS Applications and Their Vulnerabilities
Different SaaS applications have unique security characteristics and vulnerabilities. This table Artikels common types of SaaS applications and potential vulnerabilities.
| SaaS Application Type | Typical Security Vulnerabilities |
|---|---|
| Collaboration Tools (e.g., Slack, Microsoft Teams) | Improper access controls, insecure API endpoints, data leakage through compromised accounts, lack of data encryption. |
| Customer Relationship Management (CRM) Systems (e.g., Salesforce, HubSpot) | Data breaches due to weak passwords or compromised accounts, insufficient data encryption, insecure API access, lack of multi-factor authentication. |
| Cloud Storage (e.g., Dropbox, Google Drive) | Inadequate access controls, insecure sharing settings, lack of encryption, phishing attacks targeting credentials. |
| Project Management Tools (e.g., Asana, Trello) | Lack of role-based access controls, insecure API endpoints, potential for data breaches if user accounts are compromised. |
Identifying Security Risks in Applications
SaaS applications, while offering convenience and scalability, introduce unique security challenges. Understanding and proactively addressing these risks is crucial for maintaining data integrity and preventing costly breaches. This section delves into common vulnerabilities within SaaS applications, the potential consequences of overlooking these risks, and the importance of proactive identification strategies.Identifying security vulnerabilities in SaaS applications requires a multifaceted approach, encompassing both a deep understanding of the application’s architecture and a systematic evaluation of its operational environment.
A thorough assessment of potential attack vectors, coupled with a detailed analysis of the application’s codebase, are critical steps in this process.
Common Security Vulnerabilities in SaaS Applications
Numerous vulnerabilities can compromise SaaS applications. These include but are not limited to:
- Insecure APIs: Improperly configured or documented APIs can expose sensitive data to unauthorized access. For example, a poorly designed API might allow an attacker to bypass authentication mechanisms and directly access internal data stores.
- Broken Authentication and Session Management: Weak or easily guessable passwords, ineffective session management, and lack of multi-factor authentication can lead to unauthorized account access. This can permit attackers to impersonate legitimate users and gain control of critical functions within the application.
- Cross-Site Scripting (XSS): Malicious scripts injected into a SaaS application can be executed on a user’s browser, potentially stealing cookies, session tokens, or redirecting users to malicious websites. This vulnerability is prevalent if input validation is inadequate.
- Injection Flaws: Code injection vulnerabilities allow attackers to execute arbitrary commands on the server, potentially gaining unauthorized access to data or causing significant damage. SQL injection, a common type of injection flaw, can be exploited to manipulate database queries.
- Insufficient Logging and Monitoring: Lack of robust logging and monitoring mechanisms hinders the ability to detect and respond to security incidents effectively. Without proper logs, identifying the source and impact of an attack can be significantly delayed.
Potential Consequences of Unaddressed Security Risks
Unaddressed security risks in SaaS applications can have severe consequences, impacting both the application’s users and the organization’s reputation. The financial implications can be substantial, including:
- Data breaches: Compromised data can lead to financial losses, reputational damage, and regulatory penalties. The cost of recovering from a data breach can be substantial, involving legal fees, notification costs, and potential fines.
- Financial losses: Unauthorized access to sensitive financial information can result in direct financial losses, as attackers can make fraudulent transactions or steal funds. This can range from simple account hijacking to more sophisticated schemes targeting financial institutions.
- Reputational damage: Security breaches can severely damage an organization’s reputation, impacting customer trust and potentially leading to loss of business. The public’s perception of an organization can be significantly tarnished following a security incident.
- Regulatory penalties: Non-compliance with data protection regulations, such as GDPR or CCPA, can result in substantial fines and legal ramifications. Failure to comply with industry standards and regulatory requirements can result in severe consequences.
Importance of Proactive Security Risk Identification
Proactive security risk identification is crucial for mitigating potential threats and ensuring the security of SaaS applications. By anticipating potential vulnerabilities, organizations can implement preventive measures and safeguard their systems and data.
Approaches to Identify Application Security Risks
Different approaches exist for identifying security risks within SaaS applications. A comparative analysis of these approaches highlights their strengths and weaknesses:
| Approach | Description | Strengths | Weaknesses |
|---|---|---|---|
| Penetration Testing | Simulates real-world attacks to identify vulnerabilities. | Reveals exploitable weaknesses. | Can be expensive and time-consuming. |
| Security Audits | Formal review of security controls and procedures. | Provides a comprehensive overview of security posture. | Might not identify zero-day exploits. |
| Static Application Security Testing (SAST) | Analyzes the codebase to detect vulnerabilities. | Early detection of vulnerabilities. | Limited in detecting runtime issues. |
| Dynamic Application Security Testing (DAST) | Tests the application during runtime to find vulnerabilities. | Identifies runtime issues and configuration errors. | Can be complex to set up. |
Implementing SSPM for Application Security
Securing applications in today’s cloud-native world requires a proactive approach, not just reactive patching. SaaS Security Posture Management (SSPM) provides a crucial framework for this, enabling organizations to continuously monitor and enforce security best practices across their applications. This proactive approach allows for early detection of vulnerabilities and misconfigurations, reducing the risk of breaches and ensuring compliance.Implementing SSPM involves a structured process, ensuring your applications are consistently evaluated and strengthened against evolving threats.
This process isn’t a one-time fix; it’s a continuous cycle of assessment, remediation, and refinement.
Key Steps in SSPM Implementation
A robust SSPM implementation requires careful planning and execution. Following a structured approach ensures that security posture is continuously improved and maintained. This section Artikels the essential steps.
- Establish Baseline Security Posture: Initial assessment of existing application security posture is critical. This includes identifying current security controls, configuration settings, and vulnerabilities. This baseline provides a benchmark against which future improvements can be measured.
- Define Security Policies and Standards: SSPM implementation needs a clear framework. Policies and standards dictate the acceptable security configurations and controls for your applications. These policies should be aligned with industry best practices and regulatory requirements.
- Select and Configure SSPM Tools: Choose an SSPM solution that aligns with your needs. Proper configuration is crucial. This involves integrating the tool with your applications and defining the scope of monitoring and enforcement.
- Automated Security Assessments: Implement automated security assessments to continuously scan for vulnerabilities and misconfigurations in your applications. Regular automated scans will uncover potential issues promptly.
- Prioritize Remediation Efforts: Categorize identified vulnerabilities and prioritize remediation efforts based on risk and impact. This focused approach ensures that the most critical issues are addressed first.
- Continuous Monitoring and Improvement: Establish a continuous monitoring process to track security posture over time. Regular assessments and updates to security policies ensure that your application security posture remains strong and compliant.
Regular Security Audits and Assessments
Regular security audits and assessments are vital components of SSPM. They provide a comprehensive evaluation of your application security posture, identifying weaknesses and gaps that might otherwise go unnoticed.
- Frequency and Scope: Establish a schedule for security audits and assessments. The frequency should be determined based on the risk profile of your applications and the rate of changes within the application landscape. The scope should encompass all relevant applications.
- Integration with SSPM: Integrate audit findings directly into your SSPM solution. This allows for a holistic view of security posture and enables automated remediation processes.
- Reporting and Analysis: Generate detailed reports on audit findings and use data-driven analysis to identify trends and patterns in vulnerabilities.
Automation in SSPM
Automation plays a critical role in SSPM, allowing for continuous security monitoring and enforcement. Automation streamlines the process, enabling quicker response to vulnerabilities and reducing manual effort.
- Automated Vulnerability Scanning: Implement automated vulnerability scanners to identify potential security flaws. This automated process identifies security weaknesses in your application infrastructure.
- Automated Remediation Processes: Develop automated scripts or tools for implementing security fixes. This allows for quick and efficient response to identified vulnerabilities, preventing potential breaches.
- Automated Policy Enforcement: Configure SSPM to automatically enforce security policies across your applications. This proactive approach helps ensure continuous adherence to security best practices.
Key SSPM Tools and Technologies
SaaS Security Posture Management (SSPM) tools are crucial for maintaining a strong security posture in the cloud-native world. These tools automate the identification and remediation of security risks within applications hosted in various SaaS environments. Effective SSPM tools provide a comprehensive view of security configurations, allowing organizations to proactively address vulnerabilities and ensure compliance with industry standards. Choosing the right SSPM tool is vital for efficient risk management and a secure application landscape.
Prominent SSPM Tools
Various vendors offer SSPM tools, each with its unique features and capabilities. Understanding the strengths and weaknesses of these tools is essential for selecting the right solution for your specific needs.
- Checkmarx: Checkmarx offers a comprehensive platform for application security testing and management. Their SSPM solution helps in identifying and remediating security vulnerabilities in SaaS applications. It’s known for its strong vulnerability scanning capabilities and integration with various development pipelines. This tool provides detailed reports and remediation guidance to facilitate quicker resolution of issues.
- Contrast Security: Contrast Security specializes in runtime application security. Their SSPM solution focuses on identifying and mitigating runtime vulnerabilities in SaaS applications. A key strength is the ability to identify vulnerabilities in real-time as applications run, which allows for faster remediation compared to static analysis. It provides extensive visibility into application behavior and security posture, enabling quicker responses to emerging threats.
- Aqua Security: Aqua Security offers a robust solution for securing containerized applications in the cloud. Their SSPM tool is designed to identify vulnerabilities and misconfigurations in containerized applications deployed within SaaS environments. It’s known for its ability to automate security checks and integrate with CI/CD pipelines. The tool supports a broad range of containerization technologies.
- Snyk: Snyk provides a comprehensive platform for open-source and third-party library security. Their SSPM tool helps in scanning and analyzing SaaS applications for vulnerabilities in external dependencies. A key strength is its deep integration with various development tools and platforms. The tool provides comprehensive vulnerability reports and recommendations for remediation.
Comparing SSPM Tools
Comparing different SSPM tools is essential for selecting the right solution for your organization’s specific requirements. Factors like pricing, features, and ease of use play a significant role in this decision.
| Tool | Pricing | Features | Ease of Use |
|---|---|---|---|
| Checkmarx | Typically tiered, based on usage and features | Comprehensive vulnerability scanning, remediation guidance, integration with various development tools | Moderate to high, depending on the specific configuration and user expertise |
| Contrast Security | Often based on usage and features | Real-time vulnerability detection, deep insights into application behavior, integration with development tools | High, thanks to user-friendly interface and automation capabilities |
| Aqua Security | Variable pricing models | Container security focused, vulnerability scanning, integration with CI/CD pipelines | Moderate, requiring some understanding of containerization concepts |
| Snyk | Typically based on project or subscription usage | Open-source and third-party library vulnerability scanning, integration with development tools | High, thanks to its intuitive interface and ease of integration |
Functionality and Capabilities
Each SSPM tool provides specific functionalities to assess the security posture of SaaS applications. Their capabilities vary based on their design and the specific features they offer.
Security Best Practices with SSPM
SaaS Security Posture Management (SSPM) empowers organizations to proactively identify and mitigate security risks within their cloud-based applications. This proactive approach is crucial for maintaining data integrity, ensuring compliance, and preventing breaches. By implementing strong security best practices, organizations can significantly reduce the attack surface and enhance the overall resilience of their applications.Effective SSPM implementation is not a one-time effort; it’s an ongoing process of monitoring, adapting, and improving security posture.
The integration of security best practices with SSPM tools and technologies forms the cornerstone of a robust security strategy, allowing organizations to dynamically respond to emerging threats and maintain a strong security posture.
Multi-Factor Authentication (MFA) and Strong Passwords
Multi-factor authentication (MFA) is a critical security measure that enhances the protection of application access. Implementing MFA adds an extra layer of security beyond simple passwords, requiring users to provide multiple verification methods before gaining access. This significantly reduces the risk of unauthorized access, even if a password is compromised. Strong passwords are equally important, as they resist brute-force attacks and sophisticated cracking techniques.
Using complex, unique passwords for each application, and regularly changing them, further strengthens the security posture.
Data Encryption and Access Control Mechanisms
Data encryption plays a pivotal role in securing sensitive data stored within applications. By encrypting data both in transit and at rest, organizations significantly reduce the risk of data breaches. Robust access control mechanisms are equally essential. Restricting access to sensitive data based on the principle of least privilege ensures that only authorized users can access specific information.
This granular control minimizes the potential damage from unauthorized access.
Vulnerability Management
Regular vulnerability assessments are crucial in the context of SSPM. SSPM tools automate the identification of vulnerabilities within applications, providing a comprehensive inventory of potential weaknesses. This information allows organizations to prioritize remediation efforts and effectively address vulnerabilities before they can be exploited. The continuous monitoring and management of vulnerabilities through SSPM are vital for maintaining a strong security posture.
Regular Security Audits and Updates
Regular security audits, conducted by internal teams or external security consultants, are essential to assess the effectiveness of security controls and identify areas for improvement. These audits provide a comprehensive overview of the current security posture and highlight any discrepancies or vulnerabilities. Regular updates to application software and libraries are critical to address known vulnerabilities and enhance the security posture of the application.
These updates ensure the application remains protected against the latest threats and exploits.
Integrating SSPM with Existing Security Infrastructure
Seamless integration of SaaS Security Posture Management (SSPM) with your existing security infrastructure is crucial for a robust and effective security posture. This integration allows for a holistic view of your application security, enabling proactive threat detection and response. It also streamlines security operations and minimizes the need for redundant tools and processes.Effective integration avoids creating silos of security data, facilitating a unified approach to managing security risks across your entire application landscape.
Securing your apps with SaaS Security Posture Management (SSPM) is crucial these days. It’s all about proactively identifying and mitigating security risks, and while the Department of Justice Offers Safe Harbor for MA Transactions ( Department of Justice Offers Safe Harbor for MA Transactions ) is a significant development for a different area of compliance, it underscores the importance of a robust security posture.
Ultimately, SSPM is a critical part of the process to protect your data and maintain compliance.
This unified approach enables faster identification and remediation of security vulnerabilities, ultimately leading to a more secure and resilient environment.
Integration with Security Information and Event Management (SIEM) Systems
SSPM tools often offer APIs or connectors for seamless integration with SIEM systems. This integration allows for the automatic correlation of application security events with other security events, providing a broader context for threat detection and analysis. This holistic view is critical for understanding the complete security posture. By correlating SSPM data with SIEM data, security teams can identify patterns, anomalies, and potential threats more effectively.
For example, if an SSPM tool detects a suspicious configuration change in a SaaS application, the correlated SIEM data might reveal a related intrusion attempt from a known malicious IP address.
Integration with Vulnerability Management Tools
Integrating SSPM with vulnerability management tools provides a comprehensive view of security risks. This integration allows for the automatic identification and prioritization of vulnerabilities discovered within SaaS applications. This integration can enhance the vulnerability management process by providing insights into the impact of vulnerabilities on specific applications. For instance, if a vulnerability management tool identifies a known vulnerability in a widely used library, SSPM can help pinpoint which SaaS applications utilize that library and assess the potential impact on each application.
Integration with Identity and Access Management (IAM) Systems, How to secure your apps with saas security posture management sspm
SSPM tools often integrate with IAM systems to identify and manage user access to applications. This integration allows for a comprehensive view of user permissions and access privileges within SaaS applications. By connecting SSPM with IAM, security teams can identify potential misconfigurations or excessive access rights that might expose applications to unauthorized access. For instance, if an SSPM tool detects an unusual spike in login attempts from a particular user, the linked IAM system can provide details on the user’s access rights, helping security teams determine if the access has been compromised.
Designing a Secure Architecture with SSPM
A secure architecture incorporating SSPM should be designed with a phased approach. Initial steps involve identifying critical applications and defining clear security policies for each. Next, evaluate existing security tools and platforms, and map out the integration points with the SSPM solution. Thorough documentation of the integration process and ongoing maintenance is essential. This approach ensures a gradual but comprehensive integration of SSPM, minimizing disruption to existing workflows.
Importance of Consistent Security Policies
Consistent security policies are vital for effective SSPM implementation. These policies should clearly define acceptable configurations, access controls, and vulnerability remediation procedures for all SaaS applications. By establishing consistent policies, organizations can ensure that all applications adhere to a common security baseline, mitigating the risk of misconfigurations and vulnerabilities. Furthermore, clear policies promote accountability and ensure that security measures are applied consistently across the organization, minimizing the risk of blind spots in the security posture.
Using standardized policies enables easier enforcement and compliance with regulatory requirements.
Monitoring and Maintaining Security Posture: How To Secure Your Apps With Saas Security Posture Management Sspm

Staying ahead of evolving threats requires a proactive approach to security posture management. Simply implementing SSPM isn’t enough; ongoing monitoring and maintenance are crucial for maximizing its effectiveness. This involves continuously evaluating the security posture of your applications, identifying weaknesses, and adapting your defenses accordingly.Continuous vigilance is vital in the ever-changing landscape of cybersecurity. The security posture of an application can shift rapidly due to new vulnerabilities, updates, or changes in user behavior.
A static approach to security is inadequate; dynamic monitoring and adaptation are essential for maintaining a robust defense.
Importance of Ongoing Monitoring
Regular monitoring ensures that security controls remain effective and that any deviations from the desired security posture are identified promptly. This proactive approach allows organizations to address vulnerabilities before they can be exploited. Monitoring allows for a timely response to threats, minimizing potential damage and downtime. It also provides valuable data for continuous improvement efforts.
Continuous Security Improvement
Continuous security improvement is an iterative process that involves analyzing security posture data, identifying areas for enhancement, and implementing necessary changes. This cycle of assessment, analysis, and improvement is essential for maintaining a strong security posture and adapting to new threats. Regularly assessing and refining security measures based on identified weaknesses ensures the long-term effectiveness of your security posture.
Tracking and Analyzing Security Posture Changes
A well-defined process for tracking and analyzing security posture changes is essential for understanding trends, identifying potential risks, and implementing appropriate countermeasures. This process should involve regularly collecting data on security controls, identifying anomalies, and using this information to adjust security configurations and policies as needed.This involves establishing a clear baseline of your current security posture, defining specific metrics to track changes, and establishing a system to automatically report on these changes.
Securing your apps with SaaS Security Posture Management (SSPM) is crucial, especially when considering vulnerabilities like those found in Azure services. For instance, understanding the specifics of Azure Cosmos DB vulnerabilities, as detailed in Azure Cosmos DB Vulnerability Details , is vital. Knowing these vulnerabilities helps you proactively address potential weaknesses and build more robust security measures into your SSPM strategy.
This proactive approach is key to keeping your applications safe and compliant.
The analysis should identify patterns and pinpoint areas needing attention. Regular reporting to stakeholders provides transparency and facilitates informed decision-making.
Metrics for Measuring and Monitoring Security Posture
- Vulnerability Detection Rate: This metric tracks the rate at which vulnerabilities are detected and addressed. A high rate of detection suggests effective vulnerability scanning and a proactive approach to security. A low rate indicates potential gaps in your security posture management process. For example, if your application consistently shows a high rate of vulnerabilities detected, this suggests that the vulnerability scanning process and remediation procedures are not effective enough.
- Compliance Score: This metric reflects the degree to which your application complies with relevant security standards and regulations. A high compliance score indicates a strong security posture. A low score points to areas needing improvement. For instance, if your application fails to meet certain compliance requirements, it highlights a need for specific security controls to be implemented or updated.
- Security Incident Response Time: This metric measures the time taken to detect and resolve security incidents. A short response time demonstrates a well-functioning security incident response plan. A long response time exposes vulnerabilities in the incident response process and could lead to significant damage.
- Security Control Effectiveness: This metric assesses the effectiveness of security controls in preventing and mitigating attacks. High effectiveness indicates that controls are working as intended. Low effectiveness signals a need for control improvements. For instance, if intrusion detection systems are not effectively identifying and blocking malicious traffic, this shows a gap in the security control effectiveness.
- User Activity Monitoring: This metric tracks user activity patterns and behaviors, flagging anomalies that may indicate malicious activity. This includes user login attempts, file access, and application usage. Detecting anomalies allows for timely identification of potential breaches. An example could be a user logging in from an unusual location, which should trigger an investigation.
| Metric | Description | Example |
|---|---|---|
| Vulnerability Detection Rate | Percentage of vulnerabilities detected per scan. | 95% of vulnerabilities detected before exploitation. |
| Compliance Score | Percentage of compliance standards met. | 90% of security standards met. |
| Incident Response Time | Time to resolve a security incident. | Average response time of 24 hours. |
| Control Effectiveness | Effectiveness of security controls in preventing attacks. | 98% of attacks blocked by intrusion detection system. |
| User Activity Monitoring | Detection of anomalies in user activity. | Alert triggered for unusual login from unknown location. |
Case Studies of Successful SSPM Implementations
SaaS Security Posture Management (SSPM) is rapidly becoming a critical component of any organization’s security strategy. Real-world examples of successful implementations demonstrate the significant impact SSPM can have on improving application security and reducing risk. These case studies highlight not only the positive outcomes but also the hurdles encountered and how they were navigated.Implementing SSPM isn’t a one-size-fits-all solution.
The specific challenges and successes vary depending on the organization’s existing security posture, the maturity of its development processes, and the chosen SSPM solution. However, consistent themes emerge, demonstrating the value of a proactive, continuous approach to application security.
Successful Implementation of SSPM at Acme Corporation
Acme Corporation, a mid-sized e-commerce company, implemented an SSPM solution to address escalating security concerns related to their cloud-based applications. Their previous approach relied heavily on reactive security measures, leading to significant delays in vulnerability remediation.Acme’s SSPM implementation involved a phased approach. Initially, the team focused on identifying and prioritizing security vulnerabilities in their core applications. This involved integrating the SSPM tool with their existing CI/CD pipeline, allowing for automated scanning and reporting of security issues.
The tool flagged several critical vulnerabilities in their payment processing system, which were promptly addressed, mitigating potential financial risks.Subsequently, Acme implemented a standardized security configuration policy for all their applications. This significantly reduced the risk of misconfigurations and ensured consistent security across the application portfolio. The centralized dashboard provided by the SSPM tool enabled the security team to proactively monitor the security posture of all applications.The positive outcomes included a 30% reduction in security incidents and a 20% improvement in application performance due to streamlined processes.
The proactive identification and remediation of vulnerabilities also fostered a culture of security awareness among the development teams.
Securing your apps with SaaS Security Posture Management (SSPM) is crucial, but it’s not just about the tools. You also need to think about the latest in AI-powered code security solutions like those discussed in Deploying AI Code Safety Goggles Needed. Integrating these advanced tools into your existing SSPM strategy will give you a more robust and comprehensive approach to securing your applications.
Ultimately, a proactive approach to securing your apps remains vital.
Challenges and Overcoming Them
Implementing SSPM, like any new security initiative, presented challenges. One significant challenge was the integration of the SSPM tool with Acme’s existing CI/CD pipeline. This required careful planning and collaboration between the development, security, and operations teams. Furthermore, the initial training for developers on the new security standards and the SSPM tool was critical to successful adoption. By establishing clear communication channels and allocating sufficient resources to training and integration, Acme successfully navigated these challenges.Another challenge was the initial resistance from some development teams to adopting the new security processes.
Addressing this required demonstrating the value proposition of SSPM by showing how it streamlined their workflows and reduced the risk of security breaches. The security team presented clear data illustrating the benefits of the SSPM implementation to foster buy-in and commitment from the development teams.
Positive Outcomes
The successful implementation of SSPM at Acme Corporation led to numerous positive outcomes:
- Reduced Security Incidents: A 30% decrease in security incidents demonstrated the effectiveness of proactive security measures.
- Improved Application Performance: Streamlined processes and early vulnerability detection led to a 20% improvement in application performance.
- Enhanced Security Posture: The standardized security configurations and proactive monitoring improved the overall security posture of the applications significantly.
- Increased Developer Awareness: The proactive identification and remediation of vulnerabilities fostered a culture of security awareness within the development teams.
Examples of Enhanced Security Posture
The SSPM tool helped Acme identify and address critical vulnerabilities in their payment processing system. This significantly reduced the risk of financial fraud and data breaches. Further, the SSPM solution allowed the team to identify and address misconfigurations in their API gateway, improving the overall security posture of their application ecosystem.
Future Trends in SSPM
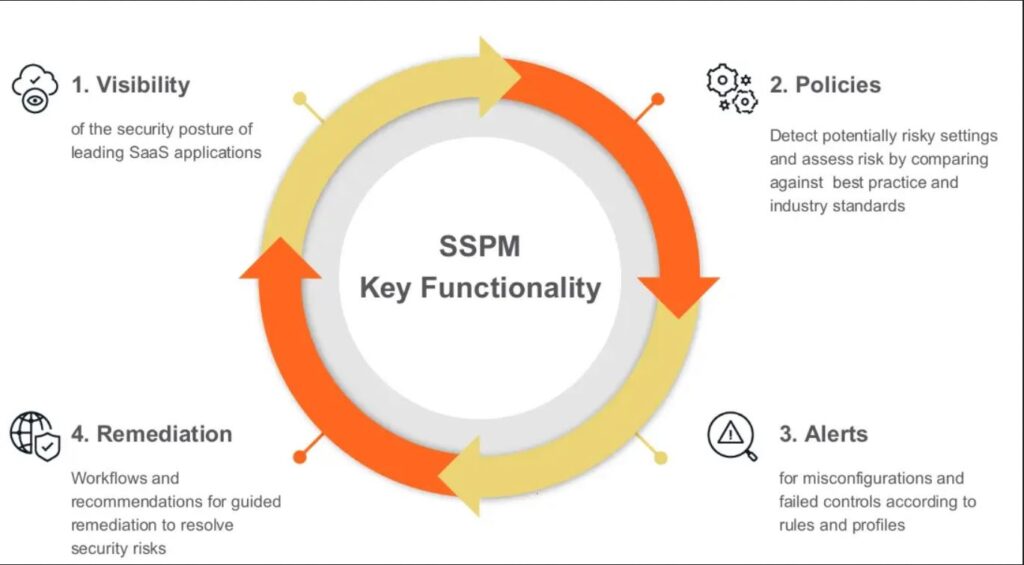
SaaS Security Posture Management (SSPM) is rapidly evolving, driven by the ever-increasing complexity of cloud-based applications and the rising sophistication of cyber threats. Understanding these emerging trends is crucial for organizations seeking to maintain a robust security posture and effectively mitigate risks associated with SaaS deployments. This exploration delves into the future trajectory of SSPM, highlighting key developments and their implications for application security.The future of SSPM is characterized by a move towards more proactive and automated security measures.
Instead of simply identifying vulnerabilities, SSPM solutions will increasingly focus on preventing breaches and enforcing security policies in real-time. This shift demands greater integration with existing security infrastructure and a focus on continuous monitoring and adaptation.
AI-Powered Threat Detection and Response
Advanced machine learning and artificial intelligence (AI) are revolutionizing threat detection and response capabilities in SSPM. AI algorithms can analyze vast amounts of security data to identify patterns and anomalies indicative of potential threats, far exceeding the capabilities of traditional rule-based systems. This proactive approach allows for quicker identification and mitigation of vulnerabilities, significantly reducing the window of opportunity for attackers.
Furthermore, AI-powered systems can automatically adjust security policies and responses based on evolving threat landscapes, enhancing the effectiveness of SSPM.
Integration with DevSecOps Pipelines
SSPM is increasingly being integrated into DevSecOps pipelines. This integration enables security checks to be performed throughout the application lifecycle, from development to deployment. Early identification and remediation of vulnerabilities within the development process are key to preventing costly and time-consuming fixes later in the deployment pipeline. This proactive approach promotes a culture of security throughout the development process, making applications more secure by design.
This collaboration enhances the effectiveness of security practices and fosters a more secure development environment.
Emphasis on Zero Trust Security Principles
Zero trust security principles are becoming paramount in SSPM. This approach assumes no implicit trust in any user, device, or application. SSPM solutions will need to be adapted to verify the identity and trustworthiness of every user and application accessing SaaS applications, implementing multi-factor authentication and granular access controls. This emphasis on zero trust security is expected to mitigate the risks associated with unauthorized access and insider threats.
Implementing a zero trust security model necessitates a paradigm shift from traditional security models, focusing on strict verification at every access point.
Enhanced Granularity and Customization
SSPM solutions are evolving towards offering greater granularity and customization options. This means tailoring security policies to the specific needs and characteristics of individual applications and users, instead of a one-size-fits-all approach. More advanced and nuanced configurations will be crucial for organizations with diverse SaaS applications, different levels of user access, and varying regulatory compliance requirements. This allows for a more fine-grained approach to security, providing more specific protection against potential threats, resulting in a higher level of security.
Focus on Cloud Native Applications
With the increasing adoption of cloud-native applications, SSPM solutions need to adapt to the unique security challenges of these architectures. This includes supporting containerized applications, serverless functions, and microservices. Solutions will need to incorporate mechanisms to secure these dynamic and distributed environments, ensuring the security of applications and data deployed in cloud-native environments. The future of SSPM will need to address the specific security challenges posed by the rapidly evolving cloud landscape.
Outcome Summary
In conclusion, securing your applications with SaaS security posture management (SSPM) is a multifaceted process that demands a proactive approach. By understanding the principles, tools, and best practices Artikeld in this guide, you can effectively mitigate risks and build a robust security posture for your applications in the cloud. Remember, continuous monitoring and improvement are essential to staying ahead of emerging threats.
Let’s secure our applications!
Clarifying Questions
What are the most common security vulnerabilities in SaaS applications?
Common SaaS application vulnerabilities include insecure APIs, insufficient access controls, insecure configurations, and lack of vulnerability management. These often lead to data breaches and unauthorized access.
How does SSPM differ from traditional security approaches?
SSPM focuses on proactively identifying and managing security risks within SaaS applications, whereas traditional methods often react to security incidents. SSPM emphasizes continuous improvement and vulnerability management.
What are some examples of SSPM tools?
Examples of SSPM tools include those that provide centralized visibility, automated security assessments, and policy enforcement. Specific tools vary in features and capabilities, so comparison is crucial.
How important is automation in SSPM?
Automation plays a critical role in SSPM by streamlining tasks like vulnerability scanning, policy enforcement, and security posture monitoring. It helps improve efficiency and accuracy.