Human Risk Management The Next Step in Mature Security Awareness
Human risk management the next step in mature security awareness programs – it sounds serious, right? But think of it this way: your best security tech is useless if your employees click on every phishing link. This isn’t about blaming individuals; it’s about acknowledging that humans are the weakest link and building a security strategy around that reality.
We’ll explore how to shift from a purely technical approach to one that truly values and protects your people – your most valuable asset. This means understanding human error, quantifying its impact, and building a culture of security awareness that’s engaging and effective, not just another mandatory training.
We’ll delve into practical strategies for assessing human vulnerability, designing effective training programs, and integrating human risk management into your existing cybersecurity framework. We’ll cover everything from identifying common human errors and their impact to measuring the effectiveness of your initiatives and adapting to emerging threats. Get ready to transform your security approach from reactive to proactive, and significantly reduce your organization’s risk profile.
Defining Human Risk in Cybersecurity
The evolution of cybersecurity has taken a fascinating turn. Initially, the focus was almost entirely on technical solutions: firewalls, antivirus software, intrusion detection systems – the technological fortress mentality. While these remain crucial, a growing understanding has revealed a critical vulnerability: the human element. Sophisticated malware and advanced persistent threats (APTs) can be thwarted by robust technology, but a single click on a malicious link can undo years of meticulous security planning.
This shift marks the rise of human risk management as the next crucial step in mature security awareness programs.The difference between traditional security measures and human risk management strategies is profound. Traditional approaches are largely reactive, focusing on containment and remediation after a breach. Human risk management, conversely, is proactive. It aims to understand and mitigate the risks posed by human behaviorbefore* a breach occurs.
It’s about changing the culture of security within an organization, moving from a tick-box compliance mentality to a genuine commitment to security awareness at every level. This involves a comprehensive understanding of employee behavior, identifying vulnerabilities in their processes, and implementing targeted training and reinforcement to address those vulnerabilities.
Human Error Leading to Security Breaches
Human error remains a primary cause of cybersecurity incidents. Understanding the types of errors, their impact, and effective mitigation strategies is paramount. The following table illustrates some common scenarios:
| Error Type | Impact | Mitigation Strategy | Example |
|---|---|---|---|
| Phishing | Data breaches, malware infections, financial loss | Security awareness training focusing on phishing techniques, simulated phishing campaigns, multi-factor authentication (MFA) | An employee clicks on a malicious link in an email disguised as a legitimate communication from their bank, leading to malware installation and account compromise. |
| Weak or Reusable Passwords | Account takeover, unauthorized access to sensitive data | Password management training, enforcement of strong password policies, use of password managers | An employee uses the same password for multiple online accounts, resulting in a compromise when one account is breached. |
| Social Engineering | Data breaches, malware infections, financial loss, reputational damage | Security awareness training covering social engineering tactics, simulated social engineering scenarios, clear communication protocols | An employee reveals sensitive information to someone posing as a technical support representative over the phone. |
| Neglecting Security Updates | Vulnerabilities exploited by attackers, malware infections | Automated patching systems, regular security updates, employee training on the importance of updates | An employee fails to update their operating system, leaving their computer vulnerable to a known exploit. |
Assessing and Measuring Human Risk

Understanding and quantifying human risk is crucial for building a robust cybersecurity posture. It moves beyond simple awareness training to a proactive, data-driven approach that identifies vulnerabilities and mitigates potential threats before they materialize. This involves analyzing various factors influencing human behavior within the organization and developing a framework for assessing the likelihood and impact of human-caused security breaches.This section delves into the practical aspects of assessing and measuring human risk, providing a framework for evaluating employee vulnerability and methods for quantifying the financial repercussions of human error in cybersecurity.
Key Factors Influencing Human Risk
Several factors contribute to the overall human risk profile within an organization. These factors interact and influence each other, creating a complex landscape that requires careful consideration. Ignoring any single element can weaken the overall effectiveness of a risk management strategy. A holistic approach is essential for accurate assessment.
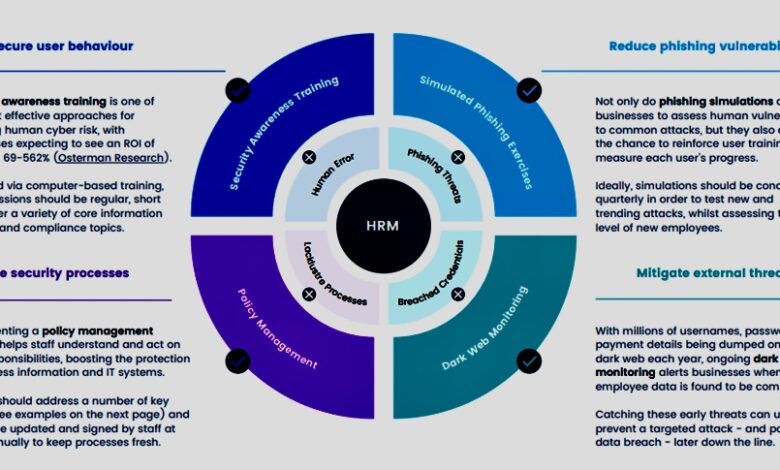
- Employee Training and Awareness: Lack of adequate security awareness training significantly increases susceptibility to phishing attacks and social engineering. Employees unfamiliar with common threats are more likely to fall victim to malicious actors.
- Organizational Culture and Policies: A strong security culture, reinforced by clear and consistently enforced policies, can significantly reduce human risk. Conversely, a lax or ambiguous security culture can embolden risky behaviors.
- Workload and Stress Levels: High workloads and stress can lead to decreased attention to detail, making employees more prone to making security mistakes, such as clicking on malicious links or overlooking suspicious emails.
- Technology and System Complexity: Complex systems and outdated technologies can increase the likelihood of human error. Intuitive and user-friendly systems can reduce the chance of mistakes.
- Employee Turnover and Onboarding: Insufficient onboarding processes for new employees can leave security gaps. Similarly, departing employees may pose a risk if their access isn’t properly revoked.
Framework for Assessing Vulnerability to Phishing and Social Engineering
A structured approach is needed to assess employee vulnerability to phishing and social engineering. This framework combines qualitative and quantitative methods for a comprehensive evaluation.
- Vulnerability Assessment Questionnaire: A detailed questionnaire targeting employees’ knowledge of phishing techniques, social engineering tactics, and safe online practices. This questionnaire should include scenarios and test their understanding of security protocols.
- Simulated Phishing Campaigns: Controlled phishing simulations provide valuable data on the effectiveness of existing security awareness training and the overall susceptibility of employees to these attacks. Analyzing the click-through rates and successful compromises helps identify areas needing improvement.
- Behavioral Analysis: Observing employee behavior in relation to security protocols and procedures. This could involve monitoring login attempts, access patterns, and overall adherence to security policies. This provides insights into potential risky behaviors.
- Data Analysis and Reporting: Analyzing data from questionnaires, simulations, and behavioral observations provides a quantifiable measure of vulnerability. This data forms the basis for targeted interventions and improvement strategies.
Quantifying the Financial Impact of Human Error
Accurately quantifying the financial impact of human error-related security incidents is crucial for demonstrating the return on investment (ROI) of security awareness programs. This involves considering both direct and indirect costs.Direct costs include:
- Incident Response Costs: The cost of investigating, containing, and remediating a security breach. This includes personnel time, external consultants, and legal fees.
- Data Breach Costs: Expenses related to notifying affected individuals, credit monitoring services, and potential legal settlements.
- System Downtime Costs: Loss of revenue due to system outages or disruptions caused by a security incident.
Indirect costs include:
- Reputational Damage: Loss of customer trust and potential impact on future business.
- Loss of Intellectual Property: The value of stolen or compromised intellectual property.
- Regulatory Fines: Penalties imposed by regulatory bodies for non-compliance with data protection regulations.
For example, a single successful phishing attack leading to ransomware deployment could cost an organization hundreds of thousands of dollars in direct costs (ransom payment, recovery efforts) and millions in indirect costs (lost business, reputational damage). This underscores the critical need for accurate assessment and mitigation of human risk.
Developing a Mature Human Risk Management Program
So, we’ve identified and measured human risk in our cybersecurity posture. Now comes the crucial next step: building a robust and mature human risk management program. This isn’t just about another security awareness training; it’s about embedding security into the very fabric of your organization’s culture. It requires a holistic approach that considers people, processes, and technology working in harmony.A comprehensive human risk management program goes beyond simple annual training.
It’s a continuous cycle of assessment, education, reinforcement, and improvement. It needs to be integrated into all aspects of your security strategy, from incident response to new employee onboarding. A successful program is adaptive, evolving with the changing threat landscape and the specific needs of your organization.
Essential Components of a Mature Human Risk Management Program, Human risk management the next step in mature security awareness programs
A mature program incorporates several key elements. First, it begins with a clearly defined risk appetite and tolerance. This sets the boundaries for acceptable risk levels and guides decision-making. Second, it utilizes a robust risk assessment methodology, regularly identifying and prioritizing vulnerabilities related to human behavior. Third, a well-defined communication strategy is vital, ensuring consistent and effective messaging to all employees.
Fourth, the program must include ongoing training and education, tailored to different roles and responsibilities. Finally, a comprehensive measurement and reporting system allows for continuous monitoring and improvement of the program’s effectiveness. Regularly evaluating key performance indicators (KPIs) like phishing click rates and reported security incidents provides invaluable feedback for refining the program. This continuous feedback loop is essential for adapting to evolving threats and employee behaviors.
Training Methodologies for Security Awareness
Various training methodologies exist, each with its strengths and weaknesses. Traditional classroom-based training offers in-person interaction and immediate feedback but can be costly and time-consuming. Online modules provide flexibility and scalability but may lack the engagement of in-person training. Gamification, incorporating game mechanics into training, can significantly increase engagement and knowledge retention. Simulation-based training, such as phishing simulations, provides practical experience and helps employees identify and respond to real-world threats.
A blended learning approach, combining multiple methodologies, often proves the most effective, catering to different learning styles and ensuring comprehensive coverage. For example, a program might use online modules for foundational knowledge, gamified exercises for reinforcement, and phishing simulations for practical application.
Implementing a Robust Security Awareness Program: A Step-by-Step Guide
Building a successful security awareness program requires a structured approach. Here’s a step-by-step guide:
- Assess Current State: Conduct a thorough assessment of your organization’s current security awareness level. This involves evaluating existing training programs, identifying knowledge gaps, and analyzing past security incidents.
- Define Objectives and Metrics: Clearly define the program’s goals and objectives, such as reducing phishing click rates or improving incident reporting. Establish measurable KPIs to track progress and demonstrate the program’s effectiveness.
- Develop a Training Curriculum: Create a comprehensive training curriculum tailored to different roles and responsibilities within the organization. The curriculum should cover topics such as phishing, malware, social engineering, data security, and password management.
- Choose Training Methodologies: Select the most appropriate training methodologies based on your organization’s needs, budget, and resources. Consider a blended learning approach for optimal results.
- Implement and Deliver Training: Deliver the training using the chosen methodologies, ensuring consistent and engaging content. Regularly update the training to reflect the latest threats and vulnerabilities.
- Measure and Report Results: Continuously monitor the program’s effectiveness by tracking KPIs and analyzing data. Regularly report on the program’s progress and make necessary adjustments based on the findings.
- Reinforce Learning: Use regular reminders, newsletters, and other communication channels to reinforce key security concepts and best practices. This keeps security top-of-mind and helps prevent complacency.
- Continuously Improve: Regularly review and update the program based on feedback, new threats, and evolving best practices. A dynamic and adaptive program is crucial for long-term success.
Integrating Human Risk Management into Existing Security Frameworks
Successfully integrating human risk management into your existing cybersecurity framework requires a strategic approach that aligns with your overall business goals. It’s not about adding another layer of security; it’s about weaving human factors seamlessly into your existing structure to create a more holistic and effective security posture. This involves understanding how human behavior impacts your organization’s vulnerabilities and proactively mitigating those risks.Integrating human risk management isn’t about replacing your existing framework; it’s about enhancing it.
Frameworks like NIST Cybersecurity Framework (CSF) provide a robust foundation, offering a structured approach to identify, assess, and manage cybersecurity risks. By incorporating human risk management, you’re essentially adding a crucial dimension to this existing structure, making it more comprehensive and effective. This involves mapping human risk factors to the different functions and activities Artikeld within the framework, allowing for a more granular understanding of where human error might lead to security breaches.
So, we’ve built a robust security awareness program, but the next frontier is truly understanding human risk. It’s about empowering users, not just training them, and that often means providing them with intuitive tools. This is where streamlined application development comes in; check out this article on domino app dev the low code and pro code future to see how simpler app creation can help reduce the friction of security protocols.
Ultimately, making security easier to implement translates directly into better human risk management.
Alignment with NIST Cybersecurity Framework
The NIST CSF provides a clear structure for integrating human risk management. Its five core functions – Identify, Protect, Detect, Respond, and Recover – offer a natural framework for incorporating human risk considerations. For example, the “Identify” function can include assessments of employee awareness and training effectiveness. The “Protect” function can incorporate measures like access control policies and multi-factor authentication, acknowledging human susceptibility to phishing and social engineering.
The “Detect” function can leverage security information and event management (SIEM) systems to monitor for anomalous user behavior indicative of compromise or malicious intent. The “Respond” and “Recover” functions benefit from incident response plans that consider the role of human error in the incident and plans for retraining or remediation. By aligning human risk management initiatives with each of these functions, organizations can create a more robust and resilient cybersecurity posture.
Aligning Human Risk Management with Business Objectives
A successful human risk management program isn’t just about ticking security boxes; it needs to be directly tied to the organization’s overall business objectives. This means demonstrating a clear return on investment (ROI) and showing how reduced human risk translates into tangible benefits like decreased downtime, improved operational efficiency, and enhanced brand reputation. For example, a financial institution might prioritize human risk management to protect against fraud and maintain customer trust.
A healthcare provider might focus on preventing data breaches that could expose patient information. By clearly articulating the connection between human risk management and business goals, organizations can secure the necessary resources and support for the program.
Examples of Successful Integrations
Several organizations have successfully integrated human risk management into their existing security initiatives. One example is a large multinational corporation that integrated human risk assessments into its annual security audits. By identifying high-risk employees and departments, they could prioritize security training and awareness programs, leading to a significant reduction in phishing incidents. Another successful example involves a financial services company that incorporated human risk factors into their incident response plan.
This allowed them to quickly identify and mitigate the impact of insider threats, reducing financial losses and reputational damage. These examples demonstrate the practical benefits of integrating human risk management into existing security programs and achieving better overall security outcomes.
Measuring the Effectiveness of Human Risk Management Initiatives
So, you’ve implemented a robust human risk management program. Fantastic! But how do you know if it’s actually working? Measuring the effectiveness of your initiatives is crucial, not just for demonstrating ROI to stakeholders, but also for identifying areas needing improvement and ensuring your program remains relevant and impactful. This involves tracking key metrics and using data-driven insights to refine your strategies.The effectiveness of human risk management, particularly security awareness training, isn’t easily measured with a single metric.
Instead, a multifaceted approach is necessary, combining quantitative data with qualitative feedback to gain a holistic understanding of program success. This allows for a more nuanced assessment than simply looking at a single number.
Methods for Measuring the Effectiveness of Security Awareness Training Programs
Effective measurement requires a blend of pre- and post-training assessments, ongoing monitoring, and feedback mechanisms. Pre-training assessments establish a baseline understanding, while post-training evaluations gauge knowledge improvement. Ongoing monitoring through simulated phishing campaigns or other vulnerability tests provides real-world data on behavioral changes. Finally, gathering feedback through surveys and focus groups helps identify areas for improvement and understand employee perspectives.
For example, a pre-training phishing campaign might show a 40% click rate, while a post-training campaign could reveal a significant drop to 10%, demonstrating the program’s impact on reducing susceptibility to phishing attacks.
Key Performance Indicators (KPIs) for Tracking the Success of Human Risk Management Strategies
Several KPIs can provide insights into the success of your human risk management strategies. These KPIs should align with your overall security objectives. Examples include:
- Phishing Simulation Click Rates: Tracks the percentage of employees who click on malicious links in simulated phishing emails. A significant reduction in click rates after training indicates improved awareness.
- Security Awareness Training Completion Rates: Measures the percentage of employees who complete required security awareness training modules. Low completion rates might indicate issues with training accessibility or engagement.
- Number of Security Incidents Reported by Employees: Tracks the number of security incidents reported by employees. An increase in reporting could suggest improved awareness and a willingness to report suspicious activity, even if it means increased workload for the security team.
- Time to Resolve Security Incidents: Measures the time taken to resolve security incidents. A faster resolution time can indicate improved employee awareness and reporting practices leading to faster containment of threats.
- Employee Satisfaction with Security Awareness Training: Gathered through surveys, this KPI helps gauge employee engagement and satisfaction with the training program. Negative feedback can point to areas needing improvement in training content or delivery.
Strategies for Continuous Improvement and Adaptation of Human Risk Management Programs Based on Performance Data
Regular review and adaptation are critical to maintaining a successful human risk management program. Analysis of KPIs should inform program adjustments. For instance, consistently high phishing click rates despite training might necessitate a review of training content, delivery methods, or the inclusion of more engaging and interactive elements. Low employee satisfaction scores might indicate a need for more personalized training or improved communication strategies.
Continuous improvement involves iterative refinement based on data-driven insights, ensuring the program remains effective and relevant. This might involve adjusting training frequency, incorporating new training modules on emerging threats, or adjusting communication strategies based on employee feedback. Regularly updating training materials to reflect the latest threats and vulnerabilities is also essential. A company might find that after implementing a new training module on social engineering tactics, the number of reported incidents related to this type of attack decreases, demonstrating the positive impact of the update.
Addressing the Human Element in Incident Response
Effective incident response hinges critically on the actions of employees. They are the first line of defense, often the first to detect suspicious activity, and their swift, informed response can significantly mitigate the impact of a security breach. Ignoring the human element in incident response plans is a major oversight, leaving organizations vulnerable to prolonged downtime, data loss, and reputational damage.Employees play a multifaceted role in both the reporting and recovery phases of incident response.
Their vigilance in identifying potential threats, their adherence to established protocols, and their cooperation during investigations are all vital components of a successful response. A well-trained workforce can significantly reduce the time it takes to contain and resolve security incidents, minimizing the overall impact on the organization.
Employee Roles in Incident Reporting and Response
A clear and concise procedure for incident reporting is crucial. Employees need to understand what constitutes a security incident, how to report it, and who to contact. This clarity minimizes confusion and delays in response. The following flowchart illustrates a simplified employee-centric incident reporting and response process:[Imagine a flowchart here. The flowchart would begin with a box labeled “Suspicious Activity Detected.” Arrows would lead to decision points: “Is it a known issue?” (Yes leads to “Follow existing procedures,” No leads to “Report to Security Team”).
From “Report to Security Team,” an arrow leads to “Security Team investigates,” followed by “Incident Confirmed?” (Yes leads to “Follow Incident Response Plan,” No leads to “Inform employee, close ticket”). The “Follow Incident Response Plan” box would branch out to various actions, such as isolating affected systems, collecting evidence, and restoring services. The flowchart would emphasize the employee’s role in providing information and cooperating with the investigation.]
Training Programs for Security Incidents
Effective training programs are paramount to equip employees with the knowledge and skills to handle security incidents appropriately. These programs should not be one-off sessions but integrated into ongoing security awareness initiatives. Training should cover several key areas:* Incident Identification: Employees need to be able to distinguish between routine technical glitches and actual security incidents. Training should include examples of phishing attempts, malware infections, and unauthorized access attempts.
Real-world examples of phishing emails, screenshots of malicious software, and descriptions of successful attacks would be used to illustrate these concepts.* Reporting Procedures: Employees should understand the proper channels for reporting incidents, including who to contact, what information to provide, and how to document their observations. The training should include practice scenarios and simulations to reinforce these procedures.
For example, a role-playing exercise where an employee reports a suspected phishing email to a designated security contact would be beneficial.* Post-Incident Actions: Employees should know what to expect during and after an investigation, including potential data loss, system downtime, and changes to their work processes. They should also understand their responsibilities in cooperating with investigators and following any instructions provided.
A realistic scenario involving a data breach, explaining the recovery process and the employee’s role in data restoration, could be part of the training.* Security Best Practices: Reinforcement of basic security hygiene practices, such as strong password creation, avoiding suspicious links, and recognizing social engineering tactics, remains crucial. Regular reminders and refresher courses help maintain a high level of security awareness.
For instance, a monthly newsletter highlighting recent phishing attempts and best practices for email security would be a valuable component.The success of any human risk management program, and incident response in particular, depends on consistent, engaging, and practical training. Investing in well-designed training programs is an investment in the overall security posture of the organization.
Building a Culture of Security Awareness: Human Risk Management The Next Step In Mature Security Awareness Programs
Building a robust security awareness program isn’t just about ticking boxes; it’s about fundamentally shifting the organizational culture to prioritize security. This requires a multifaceted approach, integrating security into everyday workflows and making it a shared responsibility, rather than the sole domain of the IT department. A successful culture of security awareness is proactive, engaging, and continuously reinforced.Security awareness training is only one piece of the puzzle.
A truly effective program fosters a sense of ownership and responsibility for security at all levels, from the CEO to the newest intern. This requires consistent communication, engaging content, and visible leadership support. The goal is to move beyond simple compliance and cultivate a mindset where employees actively identify and report potential security risks.
Techniques for Fostering a Culture of Security Awareness
Creating a culture of security awareness requires a sustained effort across multiple channels. It’s not a one-time event but a continuous process of education, reinforcement, and engagement. Effective techniques include gamification to make learning fun and memorable, regular security newsletters and communications that highlight relevant current events, and the use of real-world examples to illustrate the consequences of security breaches.
Furthermore, incorporating security into existing company meetings and communications ensures consistent reinforcement. Openly discussing security incidents (while maintaining privacy) can serve as valuable learning experiences, demonstrating the practical impact of security measures.
A Communication Plan for Security Awareness
A comprehensive communication plan is crucial for disseminating security awareness messages effectively. This plan should Artikel the target audience (segmented by role, department, or experience level), the key messages to be conveyed, the communication channels to be used (e.g., email, intranet, posters, team meetings, videos), and the frequency of communication. For instance, senior management can participate in company-wide town halls to emphasize the importance of security, while departmental managers can conduct more targeted training sessions.
The communication should be tailored to the audience’s level of understanding and should use clear, concise language. Regular feedback mechanisms should be incorporated to measure the effectiveness of the communication and make adjustments as needed. Finally, a consistent brand and tone of voice across all communications builds recognition and reinforces the message.
Examples of Successful Engagement Strategies
Successful engagement strategies often incorporate interactive elements that go beyond passive learning. For example, simulated phishing campaigns can demonstrate the effectiveness of security training in a real-world context, providing employees with hands-on experience in identifying and reporting suspicious emails. Reward programs that recognize employees for their proactive security behavior, such as reporting phishing attempts or identifying vulnerabilities, can incentivize engagement and foster a culture of security.
Furthermore, creating a security champions program, where employees are trained to act as advocates and mentors within their teams, can effectively disseminate security awareness throughout the organization. Finally, incorporating security awareness into new employee onboarding ensures that security is prioritized from day one. The use of interactive quizzes, short videos, and infographics can enhance engagement and knowledge retention.
Future Trends in Human Risk Management
The landscape of cybersecurity threats is constantly evolving, demanding a proactive and adaptable approach to human risk management. No longer can organizations rely on static training programs and infrequent phishing simulations; the future of effective security hinges on embracing emerging technologies and anticipating the next wave of attacks. This necessitates a shift from reactive measures to a predictive and preventative model, focusing on continuous improvement and the integration of cutting-edge tools.The increasing sophistication of cyberattacks, coupled with the expanding attack surface presented by remote work and the proliferation of connected devices, requires a more nuanced understanding of human vulnerabilities.
Traditional security awareness training, while still crucial, needs augmentation with advanced techniques that better engage employees and foster a robust security culture.
Emerging Threats and Vulnerabilities Requiring Adaptation
The rise of AI-powered attacks, such as deepfakes and highly personalized phishing campaigns, presents a significant challenge. These attacks leverage advanced technologies to bypass traditional security measures and exploit human psychology more effectively. For example, a deepfake video of a CEO authorizing a wire transfer could easily deceive employees, leading to significant financial losses. Similarly, highly targeted phishing emails that mimic legitimate communications are increasingly difficult to detect, requiring more sophisticated training and detection mechanisms.
Furthermore, the increasing reliance on cloud services and the Internet of Things (IoT) expands the attack surface and creates new vulnerabilities that require a more holistic approach to human risk management. These new attack vectors demand that human risk management programs adapt to incorporate awareness of these sophisticated attacks and training on how to identify and report them.
The Role of Technology in Enhancing Human Risk Management
Technology plays a pivotal role in enhancing human risk management programs. Simulation tools, for instance, allow organizations to create realistic scenarios that mimic real-world cyberattacks, providing employees with valuable hands-on experience in identifying and responding to threats. These simulations can be tailored to specific roles and responsibilities, ensuring that training is relevant and effective. Gamification, another powerful tool, transforms security training into engaging and interactive experiences, improving knowledge retention and fostering a positive learning environment.
Points, badges, and leaderboards can motivate employees to participate actively and learn about security best practices in a fun and competitive way. Furthermore, AI-powered tools can analyze employee behavior and identify patterns indicative of potential risks, allowing organizations to proactively address vulnerabilities before they can be exploited. For example, an AI system could detect unusual login attempts or suspicious email interactions, flagging these incidents for further investigation.
Predictions for the Future of Human Risk Management
The future of human risk management will be characterized by a greater emphasis on predictive analytics, personalized training, and continuous monitoring. Organizations will leverage AI and machine learning to identify and assess individual risk profiles, tailoring training programs to address specific vulnerabilities. Continuous monitoring of employee behavior and system activity will enable organizations to detect and respond to threats in real-time, minimizing the impact of successful attacks.
We can anticipate a greater integration of human risk management into broader enterprise risk management frameworks, recognizing the critical role of the human element in overall organizational security. For instance, a company might integrate its human risk management program with its incident response plan, ensuring that employees are properly trained to handle security incidents and cooperate effectively with incident response teams.
This integrated approach will be crucial for organizations to effectively manage and mitigate human-related security risks in the face of increasingly sophisticated cyber threats.
Last Point
Ultimately, securing your organization isn’t just about firewalls and intrusion detection systems; it’s about empowering your employees to be the first line of defense. By embracing a human-centric approach to security, you can create a culture where security awareness isn’t just a program, but a way of working. This means building trust, providing the right tools and training, and fostering a collaborative environment where everyone feels responsible for protecting sensitive information.
This isn’t just about ticking boxes; it’s about building a truly resilient and secure organization, one informed employee at a time. Ready to take that next step?
FAQs
What’s the difference between security awareness training and human risk management?
Security awareness training is a component of human risk management. Training focuses on educating employees, while human risk management encompasses a broader strategy that includes risk assessment, mitigation planning, and ongoing monitoring and improvement.
How do I measure the ROI of a human risk management program?
Measure the reduction in phishing attacks, successful social engineering attempts, and overall security incidents. Also track improvements in employee security knowledge and behavior through assessments and simulations. Quantify the financial impact avoided by preventing breaches.
What if my employees resist security awareness training?
Make training engaging and relevant to their daily work. Use gamification, interactive modules, and real-world examples. Focus on the “why” – explain how their actions directly impact the company and their colleagues. Consider incentives and recognition for participation and positive behavior.
