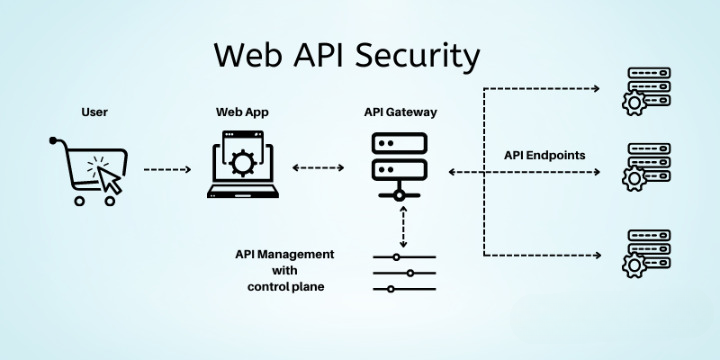
API Security Risks Graylogs Solution
If your business is not vulnerable to api security risks then you are not paying attention graylog – If your business is not vulnerable to API security risks then you are not paying attention. Graylog provides a crucial defense against these threats. APIs are the lifeblood of modern businesses, enabling seamless communication and data exchange. However, these interconnected systems are often vulnerable to sophisticated attacks. This comprehensive guide explores the critical importance of API security, highlighting the risks, and demonstrating how Graylog can help you protect your valuable data and maintain customer trust.
We’ll delve into common attack types, their impact, and effective mitigation strategies. Understanding the potential damage from breaches, and how Graylog can detect anomalies and respond to incidents will be crucial for any business that depends on APIs.
Introduction to API Security Risks
APIs, or Application Programming Interfaces, are the gateways to your digital kingdom. They allow different applications to communicate and share data, but this connectivity also exposes your business to a new set of vulnerabilities. If your API isn’t secure, your entire system could be at risk. Ignoring API security is like leaving your front door unlocked – an invitation for trouble.
Common API Security Vulnerabilities
API security vulnerabilities can manifest in various forms, often exploiting weaknesses in authentication, authorization, or data handling. These vulnerabilities are often subtle, hidden within the intricate workings of your application. Identifying and addressing them requires a deep understanding of how your API functions and the potential entry points for malicious actors.
Types of API Attacks
A variety of attacks target APIs, exploiting weaknesses in their design and implementation. These attacks can compromise sensitive data, disrupt service, or even gain unauthorized access to your entire system. Understanding these attack vectors is crucial for implementing effective mitigation strategies.
- Injection Attacks: Attackers exploit vulnerabilities in API endpoints to inject malicious code or data. This can lead to unauthorized data modification, access to sensitive information, or even complete system takeover. Examples include SQL injection, where malicious SQL queries are inserted into API requests, or command injection, where attackers insert commands to execute arbitrary code on the server.
- Authentication Bypass Attacks: These attacks focus on circumventing the API’s authentication mechanisms. By exploiting weak passwords, broken token handling, or insufficient verification procedures, attackers can gain unauthorized access to protected resources. Successful authentication bypasses often lead to data breaches or unauthorized access to internal systems.
- Authorization Attacks: Even if authentication is sound, attackers can exploit flaws in authorization logic to access resources they aren’t permitted to see or modify. Malicious actors might exploit loopholes in the authorization rules to gain access to sensitive data or perform unauthorized actions.
- Data Exposure Attacks: This involves exposing sensitive data through insecure API endpoints or inadequate data handling procedures. This can lead to the leakage of personal information, financial data, or other confidential information. For instance, improperly configured API endpoints might expose user data without adequate encryption or access controls.
Real-World API Breaches and Their Consequences
Numerous real-world API breaches have demonstrated the devastating consequences of inadequate security measures. These incidents highlight the critical need for robust API security practices to safeguard sensitive data and maintain business operations. The financial and reputational damage caused by API breaches can be substantial.
| Attack Type | Description | Impact | Mitigation Strategy |
|---|---|---|---|
| SQL Injection | Malicious SQL queries inserted into API requests. | Unauthorized data access, modification, or deletion. Potential system compromise. | Input validation, parameterized queries, and stored procedures. |
| Cross-Site Scripting (XSS) | Malicious scripts injected into API responses. | Data theft, session hijacking, and redirection to malicious websites. | Output encoding, secure coding practices, and robust input validation. |
| Denial-of-Service (DoS) | Overwhelming the API with requests, disrupting service. | Inability to serve legitimate users, loss of revenue, and damage to reputation. | Rate limiting, traffic filtering, and load balancing. |
| Authentication Bypass | Circumventing API authentication mechanisms. | Unauthorized access to sensitive data and resources, potentially leading to data breaches. | Strong password policies, multi-factor authentication, and robust token management. |
Importance of API Security for Businesses
APIs, or Application Programming Interfaces, are the lifeblood of modern businesses. They facilitate communication between different software systems, enabling crucial functionalities like online shopping, mobile banking, and social media interactions. However, this interconnectedness also exposes businesses to significant security risks if not properly managed. Neglecting API security can have far-reaching consequences, impacting not only operational efficiency but also the very trust customers place in the organization.Robust API security isn’t just about avoiding technical glitches; it’s about safeguarding the foundation of your business.
A secure API ecosystem fosters customer trust, protects sensitive data, and ultimately strengthens the financial health and reputation of the organization. Failing to prioritize API security can result in a cascade of negative outcomes, ranging from financial losses to reputational damage and legal liabilities.
Damage to Business Reputation and Finances
Ignoring API security can lead to severe reputational damage. A security breach exposes sensitive customer data, leading to public distrust and potentially causing a loss of customers. The cost of repairing the damage to a company’s reputation can be immense, often exceeding the direct financial losses from the breach. Financial penalties, lawsuits, and decreased market share can be the direct result of a compromised API.
Furthermore, the cost of developing and implementing security measures to mitigate future threats is considerable.
Legal and Regulatory Implications of Security Breaches
Data breaches related to API vulnerabilities can trigger significant legal and regulatory consequences. Regulations like GDPR, CCPA, and others mandate strict data protection measures. Failure to comply with these regulations can lead to substantial fines and legal actions. The legal implications extend beyond compliance issues; they also encompass potential lawsuits from affected customers. Businesses must be prepared for the financial and reputational repercussions of a breach.
Understanding and adhering to relevant data protection regulations is crucial.
Correlation Between Robust API Security and Customer Trust
Customer trust is paramount in today’s digital landscape. A secure API environment contributes directly to building and maintaining this trust. Customers are more likely to engage with businesses that demonstrate a commitment to protecting their data. Robust API security measures reassure customers that their information is safe and that the company values their privacy. This enhanced trust fosters customer loyalty, encouraging repeat business and positive word-of-mouth referrals.
Comparison of Security Measures
| Security Measure | Description | Effectiveness | Examples |
|---|---|---|---|
| Input Validation | Validating user inputs to prevent malicious code injection. | High. Prevents SQL injection, cross-site scripting (XSS), and other attacks. | Checking input length, type, and format. |
| Authentication and Authorization | Verifying user identity and granting access only to authorized users. | Medium to High. Essential for controlling access to sensitive resources. | Using API keys, OAuth, and multi-factor authentication. |
| Rate Limiting | Restricting the frequency of API requests to prevent abuse and denial-of-service attacks. | High. Protects the API from overload and malicious requests. | Limiting the number of requests per user or IP address within a specific timeframe. |
| Encryption | Protecting data in transit and at rest using encryption protocols. | High. Crucial for safeguarding sensitive data from interception. | HTTPS, TLS, and data encryption at storage. |
| Regular Security Audits | Identifying vulnerabilities through periodic security assessments. | Medium to High. Proactive approach to security maintenance. | Penetration testing, vulnerability scanning. |
The effectiveness of each security measure varies depending on the specific context and the threat landscape. A comprehensive approach combining various techniques is generally recommended to ensure a robust and secure API environment.
Regular audits and penetration testing are essential components of a strong security posture.
Graylog’s Role in API Security Monitoring
API security is paramount in today’s interconnected world. Businesses rely heavily on APIs for communication and data exchange, making them prime targets for malicious actors. Effective monitoring and detection of suspicious activities are crucial for mitigating risks and safeguarding sensitive information. Graylog, a powerful log management and analysis platform, plays a vital role in this crucial task.Graylog excels at aggregating and analyzing diverse data sources, including API traffic logs.
This allows security teams to gain a comprehensive view of API activity, enabling proactive identification and response to potential threats. By correlating various data points, Graylog can pinpoint unusual patterns and anomalies, potentially indicating malicious activity. This proactive approach is essential for preventing significant breaches and data loss.
Monitoring API Activity
Graylog provides robust tools for monitoring API activity, allowing security analysts to track every request and response. This comprehensive tracking enables a detailed understanding of API usage patterns. Identifying normal traffic volume and frequency is crucial for establishing a baseline against which suspicious activity can be measured. The platform’s ability to filter and sort data enables analysts to isolate specific API endpoints or requests, focusing their investigation on areas of potential concern.
Identifying Suspicious Patterns
Graylog excels at detecting anomalies in API activity. By correlating various data points, such as request headers, payload content, and response codes, the platform can pinpoint suspicious patterns. For instance, a sudden surge in requests from an unusual IP address, or requests with malformed data, can be flagged for immediate review. This proactive identification is essential for preventing significant breaches and data loss.
Graylog keeps reminding us that if your business isn’t vulnerable to API security risks, you’re probably not paying enough attention. Take a look at the recent Azure Cosmos DB Vulnerability Details, for example. Understanding potential weaknesses in your systems, like those detailed in Azure Cosmos DB Vulnerability Details , is crucial. Ultimately, ignoring API security risks is a risky move for any business, and that’s something Graylog consistently highlights.
Graylog’s powerful search capabilities allow for complex queries that can filter and isolate specific patterns, making threat detection more efficient.
Graylog Features Supporting API Security
Graylog offers several features that directly support API security monitoring. These features include:
- Real-time data ingestion: Graylog’s ability to ingest data from various sources in real-time allows for immediate detection of suspicious activity.
- Customizable dashboards: Dashboards can be tailored to display critical metrics, such as API request volume, error rates, and geographic distribution of requests. This allows analysts to quickly assess the overall health of API security.
- Advanced search and filtering: Complex queries enable targeted investigation of specific API endpoints, user behavior, and error patterns.
- Correlation rules: Graylog allows defining rules to correlate different events, such as unusual login attempts followed by unauthorized API access. This facilitates the identification of potential attacks.
- Alerting and notification: Graylog’s configurable alerts ensure that security teams are notified of significant events or anomalies in real-time, enabling rapid response.
Detecting Anomalies
Graylog’s anomaly detection capabilities go beyond simple threshold-based alerts. It can analyze complex patterns and identify deviations from established norms, indicating potentially malicious activity. This sophisticated approach allows security teams to identify threats that might otherwise go undetected by simpler monitoring tools. For example, a consistent increase in requests for sensitive data from an unusual IP address, even if within the expected volume, could trigger an alert.
Such alerts allow security teams to proactively investigate and mitigate potential threats.
API Security Use Cases and Graylog Implementation
| API Security Use Case | Graylog Implementation |
|---|---|
| Identifying unauthorized access attempts | Monitoring API authentication logs, searching for unusual login patterns, and correlating with network logs. |
| Detecting malicious payloads | Analyzing API request payloads, searching for known attack patterns, and correlating with security intelligence feeds. |
| Monitoring API usage patterns | Tracking API request volume, frequency, and geographical distribution, identifying anomalies and potential abuse. |
| Auditing API usage for compliance | Recording API activity for auditing purposes, filtering data based on compliance requirements, and generating reports. |
| Preventing denial-of-service attacks | Monitoring API traffic volume and identifying sudden spikes or unusual traffic patterns. |
Vulnerability Detection and Response
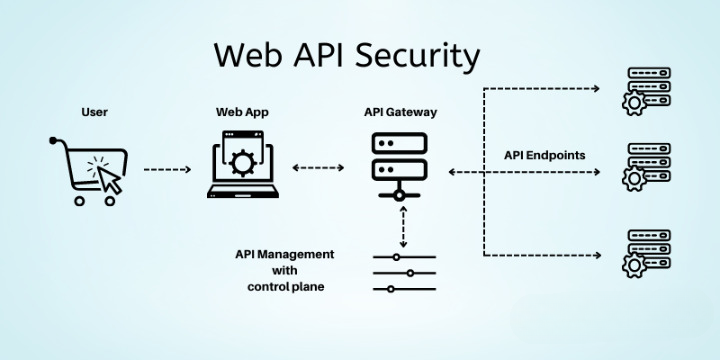
Staying ahead of API security threats requires a proactive and vigilant approach. Ignoring vulnerabilities is akin to leaving your front door unlocked – it only invites trouble. Effective vulnerability detection and a robust incident response plan are crucial for safeguarding your API infrastructure and maintaining business continuity.A critical aspect of API security is recognizing potential weaknesses and developing a strategy to address them.
This involves a multi-faceted approach, encompassing automated tools, manual assessments, and continuous monitoring. This proactive posture ensures that vulnerabilities are identified and mitigated before they can be exploited.
Methods for Detecting API Security Vulnerabilities
Identifying potential vulnerabilities within your API architecture is a continuous process. A combination of automated tools and manual reviews provides the most comprehensive approach. Automated security scanners can identify common vulnerabilities like injection flaws, authentication bypasses, and authorization issues. However, these tools are not foolproof and should be complemented by manual penetration testing. Experienced security professionals can employ advanced techniques to identify more complex and subtle vulnerabilities.
Seriously, if your business isn’t vulnerable to API security risks, you’re not paying attention, and that’s where Graylog comes in. Recent news about the Department of Justice’s safe harbor policy for MA transactions ( Department of Justice Offers Safe Harbor for MA Transactions ) highlights the ever-evolving threat landscape. This underscores the critical need for robust security measures, and if you’re not actively monitoring for potential vulnerabilities, you’re simply not taking security seriously.
So, back to the basics: if your business isn’t vulnerable to API security risks, you’re not paying attention, plain and simple.
Importance of a Proactive Approach to Vulnerability Management
A proactive approach to vulnerability management is essential for mitigating risks. Waiting until a breach occurs is far too late. Instead, organizations should prioritize continuous vulnerability assessment and remediation. This approach enables businesses to patch flaws before attackers can exploit them, preventing costly data breaches and reputational damage. By consistently evaluating API security, organizations can demonstrate their commitment to data protection and build trust with customers.
Proactive measures can prevent significant financial losses associated with breaches. Consider the case of a company whose API was compromised, leading to the theft of sensitive customer data. The resulting legal fees, regulatory fines, and reputational damage could have been avoided with a proactive approach.
Structured Process for Responding to API Security Incidents
A well-defined incident response plan is critical for effectively managing security incidents. This plan should detail procedures for detecting, analyzing, containing, eradicating, recovering, and learning from each security event. The plan should be regularly reviewed and updated to reflect evolving threats and vulnerabilities.
Incident Response Phases and Actions
A structured incident response process allows for a coordinated and efficient response to security incidents. This systematic approach ensures that critical steps are not missed, and that the response is timely and effective. The following table Artikels the key phases and associated actions:
| Incident Response Phase | Corresponding Actions |
|---|---|
| Detection | Identify the incident, log the details, and alert the security team. Use monitoring tools to detect anomalies and suspicious activities. |
| Analysis | Determine the scope of the incident, the nature of the vulnerability exploited, and the impact on the system. Gather evidence and document the incident. |
| Containment | Isolate the affected systems to prevent further damage. Block access to compromised resources. |
| Eradication | Remediate the vulnerability, patch affected systems, and restore functionality. This includes removing malicious code and implementing security enhancements. |
| Recovery | Restore systems and data to their previous state. Implement preventative measures to reduce the risk of similar incidents. |
| Learning | Review the incident, identify lessons learned, and update security policies and procedures. Conduct root cause analysis to prevent future occurrences. |
Best Practices for API Security
APIs, the lifelines of modern applications, are increasingly vulnerable to attacks. Failing to implement robust security measures can expose sensitive data, disrupt services, and damage your reputation. This section Artikels key best practices to safeguard your APIs against threats.Implementing a proactive and multi-layered approach to API security is crucial. This includes secure coding practices, strong authentication and authorization, and consistent monitoring throughout the API lifecycle.
Understanding and applying these principles will dramatically reduce the risk of exploitation and ensure the integrity of your data and systems.
Secure Coding Practices for API Development
Proper coding practices are fundamental to API security. Developers should follow established principles to minimize vulnerabilities.
- Input Validation: Validate all user-supplied data rigorously. This prevents malicious input from manipulating application logic or causing database errors. Employ whitelisting or blacklisting techniques, as appropriate, to ensure data conforms to expected formats and ranges. For instance, if an API expects an integer, ensure the input is an integer and not a string, potentially containing SQL injection commands.
- Parameterization: Parameterize all database queries and commands. This prevents SQL injection attacks by treating user inputs as data rather than code. Using parameterized queries ensures that input data is handled safely, separating it from the SQL command structure. This prevents malicious code from being executed.
- Least Privilege Principle: Grant API users only the necessary permissions to perform their tasks. Limit access to resources and functionalities to minimize the impact of potential breaches. Avoid giving users administrative privileges unless strictly required. For example, a user should only be allowed to read specific data fields, not modify the entire database.
- Output Encoding: Encode all output data before displaying it to the user. This prevents cross-site scripting (XSS) attacks. Ensure that user-supplied data is properly escaped and sanitized to prevent script injection vulnerabilities.
Strong Authentication and Authorization Mechanisms
Robust authentication and authorization are critical for controlling access to APIs. They verify the identity of users and restrict their actions.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. This requires multiple forms of verification, such as a password and a one-time code from a mobile device. This significantly increases the difficulty for attackers to gain unauthorized access.
- API Keys and Tokens: Use API keys or tokens for authentication. These provide a secure and scalable way to identify and authorize API requests. Rotate keys periodically to enhance security.
- Role-Based Access Control (RBAC): Implement RBAC to define roles and permissions for users. This controls which APIs and resources users can access based on their role. This ensures that users only have access to data relevant to their job functions.
Securing APIs Throughout the Lifecycle
A comprehensive security strategy encompasses all stages of the API lifecycle.
- Design Phase: In the design phase, incorporate security considerations from the outset. Define clear security requirements and integrate them into the API design specifications. This proactively prevents vulnerabilities from arising later.
- Development Phase: Implement secure coding practices, as described earlier. Conduct regular security assessments and code reviews during the development process. This ensures early detection of potential vulnerabilities.
- Testing Phase: Thoroughly test the API for vulnerabilities using penetration testing and security scanning tools. This helps identify and address weaknesses before deployment.
- Deployment Phase: Deploy APIs in a secure environment with appropriate access controls. Use a secure deployment pipeline and ensure continuous monitoring.
- Maintenance Phase: Continuously monitor and update APIs for security vulnerabilities. Implement security patches and updates promptly. Address new threats as they emerge.
Case Studies and Examples
API security is no longer a nice-to-have, but a critical necessity for any business operating in the digital age. Vulnerabilities in APIs can expose sensitive data, disrupt operations, and damage a company’s reputation. This section explores real-world examples of how businesses have successfully implemented API security measures, highlighting the effectiveness of Graylog in the process.Understanding the potential damage from API attacks is crucial.
A breach can lead to financial losses, legal ramifications, and a significant erosion of customer trust. Effective API security strategies, combined with robust monitoring tools like Graylog, are essential for mitigating these risks.
Successful API Security Implementations, If your business is not vulnerable to api security risks then you are not paying attention graylog
Implementing robust API security requires a multi-faceted approach. Companies that have successfully implemented API security measures often follow a well-defined strategy that includes:
- Comprehensive API Inventory: Creating a detailed inventory of all APIs, their endpoints, and the data they handle is the first step. This helps in identifying potential vulnerabilities and prioritizing security measures.
- Implementing Strong Authentication and Authorization Mechanisms: Robust authentication and authorization methods, such as OAuth 2.0, are crucial to ensure that only authorized users and applications can access APIs. This limits unauthorized access to sensitive data.
- Implementing Rate Limiting and Throttling: Rate limiting and throttling mechanisms help protect APIs from denial-of-service attacks and abuse by preventing malicious actors from overwhelming the system with excessive requests. This helps maintain API performance and availability.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing are vital to identify vulnerabilities in API design, implementation, and configuration. This proactive approach helps in identifying weaknesses before they are exploited.
Graylog’s Role in Detecting and Responding to API Attacks
Graylog’s ability to collect and analyze logs from various sources, including API gateways and application servers, provides a crucial advantage in API security monitoring. This comprehensive view allows for the identification of suspicious patterns and anomalies indicative of API attacks.
- Real-time Threat Detection: Graylog can be configured to detect unusual API activity in real time. By correlating log data from various sources, Graylog can identify anomalies that might indicate an attack.
- Anomaly Detection Capabilities: Graylog’s advanced analytics capabilities enable the identification of unusual patterns in API traffic. This helps in proactively detecting and responding to threats before they escalate.
- Integration with Security Information and Event Management (SIEM) Systems: Graylog can integrate with existing SIEM systems to provide a holistic view of security events and facilitate faster incident response.
Examples of API Security Incidents and Prevention
Unfortunately, API security breaches are not uncommon. A company might experience a denial-of-service attack targeting an API, leading to service disruptions. Another potential incident is an unauthorized access attempt to a sensitive API endpoint, exposing critical data.
- Case Study Example 1: A major e-commerce platform experienced a surge in API requests, overwhelming their servers and causing a temporary outage. By implementing rate limiting and throttling measures, the platform was able to mitigate future attacks and maintain service availability.
- Case Study Example 2: A financial institution discovered a vulnerability in their API that allowed unauthorized access to customer account information. Through proactive security audits and penetration testing, they were able to identify and fix the vulnerability, preventing a potential data breach. This proactive approach saved the company significant financial and reputational damage.
Graylog Integration with Other Security Tools
Graylog’s extensibility allows for seamless integration with other security tools. This integration provides a comprehensive security posture and facilitates efficient threat detection and response.
- Integration with Web Application Firewalls (WAFs): Integrating Graylog with WAFs allows for a comprehensive view of API traffic, enabling faster identification and response to potential threats. This unified approach to security monitoring strengthens the overall security posture.
- Integration with Intrusion Detection and Prevention Systems (IDPS): Combining Graylog with IDPS systems enhances threat detection capabilities by providing a comprehensive view of security events. This unified view allows for quicker incident response and mitigation.
Graylog Integration with Other Security Tools: If Your Business Is Not Vulnerable To Api Security Risks Then You Are Not Paying Attention Graylog
API security is a multifaceted challenge, and relying solely on Graylog for monitoring isn’t always sufficient. Effective security requires a holistic approach, combining different tools to provide a comprehensive view of threats and vulnerabilities. Integrating Graylog with other security tools enhances its capabilities and allows for a more robust and proactive security posture.Integrating Graylog with other security tools provides a richer understanding of the security landscape.
This goes beyond just collecting logs; it enables correlation of events across various systems, providing a holistic view of potential threats. By connecting Graylog to other tools, you gain a deeper insight into the context surrounding security events, helping to quickly identify and respond to issues.
Integration Capabilities
Graylog’s robust API and flexible architecture allow seamless integration with various security tools. This includes SIEM (Security Information and Event Management) platforms, vulnerability scanners, intrusion detection systems (IDS), and endpoint detection and response (EDR) solutions. This interoperability empowers analysts to gain a comprehensive view of the security posture. The integration process often involves exchanging data through APIs or standardized formats like STIX.
Benefits of Integration
Integrating Graylog with other security tools offers several advantages. These include improved threat detection, quicker incident response, enhanced visibility into the attack surface, and better security posture management. By consolidating data from various sources, Graylog facilitates more accurate threat assessments and enables a faster response to security incidents. Furthermore, integrated data enables proactive threat hunting and allows security teams to understand the context surrounding events, leading to more effective incident response.
Integration Approaches
Several integration approaches are available, each with its own strengths and weaknesses, depending on the specific security tools involved and the desired level of integration. These include:
- Direct API Integration: This approach leverages the APIs provided by both Graylog and the other security tool. It allows for real-time data exchange, providing the most dynamic and comprehensive view of the security landscape. This is often the preferred method for highly automated environments, where real-time data flow is crucial.
- Data Ingestion via Standardized Formats: Standardized formats like STIX (Structured Threat Information eXpression) allow for easier integration with a wider range of tools. This allows for interoperability across different security solutions, creating a more cohesive security ecosystem. This approach is often more suitable for environments with heterogeneous security tools or where the tools do not offer direct API access.
- Custom Scripting/Middleware: For complex integration scenarios or when neither direct API integration nor standardized formats are available, custom scripting or middleware can be developed to facilitate the exchange of data. This approach provides maximum flexibility but also requires significant development effort.
Suitability for Various Scenarios
The suitability of each integration approach depends on the specific needs and environment. For example, direct API integration is best for high-volume, real-time data exchange, while standardized formats are suitable for interoperability across various security tools. Custom scripting is suitable for highly complex integration needs where no readily available solution exists.
Setting up an Integration (Example)
Let’s imagine integrating Graylog with a vulnerability scanner like Nessus. Nessus would generate reports containing identified vulnerabilities. To integrate with Graylog, Nessus would need to output the vulnerability data in a standardized format, like JSON. Graylog would then receive and parse this data, storing it for analysis. This would allow Graylog to aggregate vulnerability information across various systems, providing a complete picture of the security risks.
This detailed understanding would support a proactive security approach and aid in preventing potential attacks.
Future Trends in API Security
The API landscape is constantly evolving, demanding a proactive approach to security. Emerging threats and technologies necessitate continuous adaptation and innovation in API security strategies. Businesses must anticipate these future trends to maintain operational resilience and safeguard sensitive data.The increasing reliance on APIs for communication and data exchange has created a fertile ground for potential vulnerabilities. This requires businesses to stay ahead of the curve and implement robust security measures to mitigate these risks.
Organizations must prioritize the security of their APIs, recognizing that vulnerabilities can lead to significant financial and reputational damage.
Emerging Threats and Vulnerabilities
APIs are exposed to a range of evolving threats, from sophisticated attacks targeting authentication and authorization mechanisms to vulnerabilities within the underlying infrastructure. These threats often leverage new attack vectors and exploit vulnerabilities in widely used technologies.
- Automated Attacks: Sophisticated bots and automated tools are increasingly used to launch large-scale attacks against APIs, making it challenging to detect and respond to these attacks in a timely manner. For example, distributed denial-of-service (DDoS) attacks can overwhelm API endpoints, rendering them inaccessible to legitimate users. Such attacks can be incredibly damaging to online services.
- Supply Chain Attacks: Vulnerabilities in third-party libraries or services used by APIs can be exploited by attackers to compromise the entire system. These attacks can bypass traditional security measures and cause widespread damage. Consider the implications of a widely-used API library containing a hidden backdoor.
- API-Specific Attacks: New types of attacks specifically targeting APIs are constantly emerging, exploiting vulnerabilities in API design, implementation, and communication protocols. These attacks can range from exploiting insecure authentication methods to manipulating data payloads.
Emerging Technologies and Techniques
The security landscape is constantly evolving with new technologies and techniques. These advancements are crucial for strengthening API security and mitigating emerging threats.
- Zero Trust Architecture: Implementing a zero-trust architecture for APIs can help limit the impact of a breach by minimizing the attack surface and enforcing strict access controls. This approach assumes no implicit trust and verifies every request, even from internal users.
- AI-Powered Security Tools: Artificial intelligence and machine learning are being increasingly utilized to detect and respond to threats in real time. These tools can identify anomalies, predict potential attacks, and automatically adjust security responses.
- Secure Coding Practices: Adherence to secure coding practices and standards during the API development lifecycle is essential to prevent vulnerabilities from being introduced in the first place. Developers need to be well-versed in security best practices and follow secure coding guidelines to minimize the risk of vulnerabilities.
Evolving Role of Security Tools
The role of security tools in API security is evolving, with a greater emphasis on proactive threat detection, automated responses, and real-time monitoring.
- API Gateway Security: API gateways are increasingly integrated with advanced security features to monitor and control API traffic, enforce policies, and provide real-time threat detection. This includes features like rate limiting, authentication, and authorization.
- Behavioral Analytics: Security tools that leverage behavioral analytics can detect unusual patterns and activities indicative of malicious behavior. This helps to identify attacks before they escalate into significant breaches.
- Threat Intelligence Integration: Security tools can be integrated with threat intelligence feeds to provide real-time updates on emerging threats and vulnerabilities. This enables organizations to proactively adjust their security posture.
Future Impact on Businesses
The future impact of API security on businesses is significant. Organizations that fail to prioritize API security will face substantial risks.
- Financial Losses: Breaches can result in significant financial losses due to data breaches, service disruptions, and regulatory fines. Consider the potential cost of a data breach affecting sensitive customer information or financial transactions.
- Reputational Damage: A security breach can severely damage a company’s reputation, leading to loss of customer trust and decreased market share. Companies that prioritize customer data protection are better positioned to maintain trust and reputation.
- Compliance Requirements: Stringent compliance requirements for data protection are becoming increasingly common, requiring organizations to implement robust API security measures to ensure adherence to regulations.
Practical Implementation Advice
Implementing robust API security requires a proactive and layered approach. It’s not a one-time fix but an ongoing process of vigilance and adaptation to evolving threats. This involves prioritizing vulnerabilities, allocating resources strategically, and effectively utilizing tools like Graylog for comprehensive monitoring and response.Effective API security implementation hinges on understanding your specific environment and threat landscape. A tailored strategy, built upon a clear understanding of your critical APIs and potential attack vectors, is crucial for minimizing risks and maximizing protection.
Prioritizing Vulnerabilities and Resource Allocation
Identifying and prioritizing API vulnerabilities is paramount. A systematic risk assessment process should identify critical APIs based on their sensitivity, usage frequency, and potential impact. This evaluation should also consider the potential financial and reputational damage associated with a successful breach. This prioritization should guide the allocation of resources for patching, security testing, and monitoring. A well-defined budget and a clear understanding of the resources required for each phase of the implementation process will contribute to the overall effectiveness of the security strategy.
Utilizing Graylog for API Security Monitoring
Graylog’s powerful log management capabilities are essential for API security monitoring. It allows for real-time analysis of API traffic and logs, enabling swift detection of suspicious activities. Graylog’s ability to correlate data across various sources, including API gateways, application logs, and security information and event management (SIEM) systems, provides a comprehensive view of potential threats. This integrated approach enhances the effectiveness of security monitoring, providing early warning of potential incidents.
Configuring Graylog for API Security Monitoring
Implementing Graylog for API security monitoring involves several key steps. First, establish clear log collection points for API traffic and related activities. Configure Graylog to ingest logs from these sources, ensuring proper formatting and indexing for efficient searching and analysis. Second, define custom dashboards and alerts tailored to specific API security concerns. For example, identify critical API endpoints and configure alerts for unauthorized access attempts or unusual request patterns.
Seriously, if your business isn’t vulnerable to API security risks, then you’re not paying attention. Graylog’s got a lot to say about that. And if you’re looking to bolster your defenses further, consider deploying AI code safety goggles – like those discussed in Deploying AI Code Safety Goggles Needed. Ultimately, recognizing and mitigating API vulnerabilities is crucial.
So, if your business isn’t vulnerable to API security risks, you’re probably not paying enough attention.
Finally, create and regularly update security playbooks based on detected vulnerabilities and Graylog’s alert triggers. This enables rapid incident response and minimizes the impact of security incidents.
- Log Collection: Ensure logs from API gateways, application servers, and security tools are properly formatted and piped into Graylog. This involves configuring input sources and ensuring proper data structure.
- Custom Dashboards: Develop dashboards to visualize critical API metrics and potential threats. These should be customized to monitor for suspicious activity patterns, unusual traffic spikes, and unauthorized access attempts.
- Alerting Mechanisms: Establish alerts for key security events. For example, set alerts for failed authentication attempts, unusual request patterns, or unauthorized access to sensitive data. The alerts should trigger immediate action and investigation.
Example of Graylog Dashboard
A well-designed Graylog dashboard for API security monitoring would display key metrics like API request volume, error rates, and geographical distribution of requests. It would also include visualizations of security events, such as failed authentication attempts and suspicious IP addresses. The dashboard should be customizable to meet the specific needs of the organization and provide real-time insights into API activity.
This allows for quick identification of anomalies and potential threats.
Ultimate Conclusion
In conclusion, API security is paramount in today’s digital landscape. Ignoring these vulnerabilities can lead to significant financial and reputational damage. Graylog’s advanced monitoring capabilities provide a robust solution for identifying and responding to API threats. By proactively addressing potential weaknesses and employing best practices, businesses can ensure the safety and integrity of their APIs. This guide equips you with the knowledge and tools to implement effective API security measures and safeguard your business from emerging threats.
Top FAQs
What are some common API attack types?
Common API attacks include injection attacks (SQL injection, command injection), authentication bypass, denial-of-service attacks, and broken authentication. These vulnerabilities exploit weaknesses in the API’s design and implementation, often leading to unauthorized access or data breaches.
How can Graylog help detect anomalies in API activity?
Graylog’s powerful log aggregation and analysis capabilities allow for real-time monitoring of API activity. By identifying unusual patterns and deviations from expected behavior, Graylog helps proactively detect suspicious activities and potential threats. Its ability to correlate data across various sources enhances threat detection accuracy.
What are some best practices for securing APIs?
Best practices include strong authentication and authorization mechanisms, input validation, secure coding practices, regular security audits, and a robust incident response plan. Implementing these measures strengthens the overall security posture of your APIs.





