Immutable Data Storage Ransomwares Last Stand
Immutable data storage is last line of defense against ransomware – Immutable data storage is the last line of defense against ransomware, providing a robust barrier against encryption and deletion attempts. This method leverages the principles of immutability, ensuring data integrity and safeguarding against malicious actors. By understanding the core concepts of immutable storage and its unique approach to data security, organizations can fortify their defenses and protect critical assets from ransomware attacks.
Traditional data storage methods are vulnerable to ransomware attacks because they allow for data modification. Immutable storage, however, prevents this, creating a significant advantage in safeguarding valuable information. This article will delve into the intricacies of immutable storage, exploring its capabilities and limitations, and discussing how to implement it effectively to thwart ransomware attacks.
Introduction to Immutable Data Storage

Immutable data storage is a revolutionary approach to data management that fundamentally alters how we handle and protect information. Instead of allowing modifications to existing data, immutable storage creates entirely new versions whenever changes are needed. This inherent characteristic dramatically enhances data integrity and security, making it a powerful tool against ransomware and other malicious attacks.The core principle of immutability is to prevent any alterations to data once it’s stored.
Immutable data storage is truly the last line of defense against ransomware attacks, but robust coding practices are crucial too. Think of it like this: You can have the best security system (immutable storage), but if your code has vulnerabilities, it’s like leaving a window open. Deploying AI Code Safety Goggles Needed here is key to preventing those coding errors that could expose your data.
Ultimately, having both rock-solid code and immutable data storage is the strongest defense against any attack.
This means that a data object, once created, cannot be changed, deleted, or overwritten. This inherent characteristic ensures that any prior version of the data is preserved and readily available for recovery, while simultaneously making tampering nearly impossible. The implications for data integrity are profound, as any modifications are recorded as completely new entries. This contrasts sharply with traditional storage methods, where data modification is a common practice.
Core Principles of Immutability
Immutability ensures data integrity by creating a persistent audit trail. Every change results in a new data object, preserving all prior versions. This creates an undeniable record of all modifications, facilitating a comprehensive historical overview. This record is crucial for recovery and forensic analysis, offering a detailed timeline of data evolution.
Traditional vs. Immutable Data Storage
| Feature | Traditional Storage | Immutable Storage |
|---|---|---|
| Data Modification | Data can be modified in place. | Data is immutable; changes create new versions. |
| Recovery | Recovery often involves restoring from backups, which might not be up-to-date. | All versions are preserved, enabling precise recovery to any point in time. |
| Security | Vulnerable to data manipulation and ransomware attacks. | Highly resistant to modification, tampering, and ransomware attacks. |
| Data Integrity | Potentially susceptible to corruption or data loss due to errors during modification. | Data integrity is inherently preserved through versioning and immutability. |
Traditional data storage, prevalent in most systems today, allows for easy modification. This feature, while convenient, creates vulnerabilities. Data can be accidentally or intentionally altered, leading to data corruption or loss. Immutable data storage, on the other hand, ensures that any changes are recorded as new data, preserving the previous version. This approach makes data manipulation and tampering almost impossible, offering unparalleled protection against ransomware and data breaches.
Ransomware Attacks and Their Impact
Ransomware attacks are a growing threat to organizations of all sizes, causing significant financial and operational damage. These attacks exploit vulnerabilities in systems and networks to encrypt sensitive data, demanding payment for its release. The impact extends beyond the immediate financial cost, encompassing reputational damage and long-term operational disruption.Ransomware attacks have evolved significantly in recent years, becoming more sophisticated and targeted.
Criminals now employ advanced techniques, including exploiting zero-day vulnerabilities and using multiple attack vectors to gain unauthorized access. This evolution necessitates a proactive and multi-layered approach to cybersecurity for effective defense.
Types of Ransomware Attacks and Tactics
Ransomware attacks manifest in various forms, each employing distinct tactics to infiltrate systems and extort payment. These methods often target vulnerabilities in outdated software, weak passwords, or phishing scams. Criminals also exploit social engineering tactics to trick users into providing access or downloading malicious files.
Immutable data storage is truly the last line of defense against ransomware attacks. Recent vulnerabilities, like those detailed in the Azure Cosmos DB Vulnerability Details , highlight the importance of proactive security measures. Understanding these potential weaknesses in cloud services emphasizes the critical role immutable storage plays in ensuring data integrity and preventing data breaches. It’s a crucial step in building robust security protocols.
- Crypto-ransomware encrypts data, demanding a ransom for decryption. This is the most common type, targeting critical files and databases.
- Locker ransomware locks the user out of their system, demanding payment to regain access.
- Ransomware-as-a-service (RaaS) models allow individuals without technical expertise to launch attacks, making them more prevalent.
- Double extortion tactics involve not only encrypting data but also threatening to publish it publicly if the ransom is not paid.
Damage Caused by Ransomware Attacks
The consequences of ransomware attacks are multifaceted, impacting organizations in various ways. Financial losses from ransom payments, recovery efforts, and downtime are significant. Operational disruptions caused by system outages, data loss, and the need for system restoration further compound the damage.
- Financial losses include the ransom paid, costs of incident response, legal fees, and potential fines or penalties.
- Operational disruptions can lead to lost productivity, delays in project completion, and damage to customer relationships.
- Reputational damage is another critical consequence, affecting customer trust and investor confidence.
High-Profile Ransomware Attacks and Consequences
Several high-profile ransomware attacks have highlighted the devastating impact of these attacks on organizations. These attacks often disrupt critical infrastructure, causing widespread business disruption.
- The WannaCry ransomware attack in 2017 affected hundreds of thousands of computers globally, causing significant disruption to healthcare facilities, businesses, and government agencies.
- The NotPetya attack in 2017 was particularly damaging due to its ability to spread laterally across networks, causing significant data loss and operational issues for organizations.
Financial and Reputational Costs of Ransomware Incidents
The financial and reputational costs of ransomware attacks vary significantly across industries, reflecting differing vulnerabilities and risk profiles.
| Industry | Financial Costs (Estimated) | Reputational Costs |
|---|---|---|
| Healthcare | Millions of dollars in ransom payments, system restoration, and lost revenue | Loss of patient trust, potential regulatory fines, and damage to public image |
| Finance | Significant losses due to downtime, data recovery, and potential regulatory penalties | Loss of investor confidence, damage to brand reputation, and regulatory scrutiny |
| Manufacturing | Downtime, lost production, and ransom payments | Damage to supply chain, loss of customer confidence, and potential delays |
Immutable Data Storage as a Ransomware Defense
Immutable data storage stands as a powerful countermeasure against ransomware attacks. By design, this approach prevents unauthorized modification or deletion of data, rendering ransomware attempts ineffective. This inherent immutability makes it a crucial last line of defense in a robust security strategy.Immutable storage systems are engineered to resist ransomware attacks by leveraging the concept of immutability. This means once data is written to the system, it cannot be altered or deleted.
This crucial feature effectively blocks ransomware from encrypting or deleting critical files, safeguarding the integrity of the data.
Mechanisms of Ransomware Resistance, Immutable data storage is last line of defense against ransomware
Immutable storage systems employ various mechanisms to thwart ransomware attacks. These mechanisms typically involve dedicated storage systems or cloud-based solutions. A key principle is data versioning, ensuring historical integrity. Data is stored in a series of immutable versions, preventing modification of past versions.
Role of Versioning and Snapshots
Versioning and snapshots are critical components in maintaining data integrity within immutable storage. Snapshots capture the state of the data at specific points in time, providing a historical record. These snapshots are immutable, ensuring that past versions of data remain unaffected by ransomware attacks. This capability is essential for recovering to a previous, uncompromised state.
Effectiveness of Immutability Mechanisms
The effectiveness of immutability mechanisms against various ransomware techniques can be assessed through several criteria. Different mechanisms offer varying levels of protection against different ransomware tactics. The following table illustrates this:
| Immutability Mechanism | Effectiveness against Ransomware Techniques | Description |
|---|---|---|
| Data Versioning | High | Creating immutable copies of data at different points in time. Ransomware cannot modify or delete older versions. |
| Snapshotting | High | Capturing a consistent view of the data at a particular time. Ransomware cannot modify or delete the snapshot. |
| Data Replication | Medium | Creating multiple copies of data across different storage locations. Ransomware must compromise multiple locations. |
| Write-Once, Read-Many (WORM) Systems | High | Data written once cannot be altered or deleted. Ransomware has no impact on the data. |
Implementing Immutable Data Storage Solutions
Immutable data storage, a cornerstone of ransomware defense, involves permanently preventing data modification or deletion after initial creation. This crucial aspect ensures that even if attackers gain access, they cannot alter or erase vital information. Implementing such solutions requires a shift in mindset from traditional data management practices, emphasizing the immutability principle across the entire data lifecycle. Understanding the various technologies and their suitability for specific use cases is paramount.Implementing immutable storage involves several key steps, including data ingestion, storage, and retrieval, all designed to maintain data integrity.
Critical to this process is the selection of appropriate storage solutions that match the organization’s specific needs and budget. Different immutable storage technologies offer varying levels of performance, scalability, and security, which need careful consideration.
Immutable Storage Technologies
Various technologies facilitate the creation and maintenance of immutable data stores. Cloud-based solutions, such as Amazon S3 with immutability policies, and dedicated immutable storage services, provide readily available options. On-premises solutions often rely on specialized file systems or storage appliances designed for immutability. Choosing the right technology hinges on factors like performance requirements, cost, and the level of control desired.
Cloud-Based Immutable Storage
Cloud providers offer various options for implementing immutable storage. For instance, Amazon S3’s immutability policies allow setting a specific retention period for objects. Once objects reach this period, they become immutable, preventing any modification or deletion. Similarly, Azure Blob Storage and Google Cloud Storage provide comparable services. The advantage lies in the scalability and management offered by cloud platforms.
However, the reliance on third-party providers raises concerns about vendor lock-in and data governance.
On-Premise Immutable Storage
On-premise solutions provide greater control over data storage. These solutions often employ specialized file systems or storage appliances designed for immutability. The deployment and maintenance might be more complex and costly compared to cloud-based options. However, the ability to maintain complete control over data is a major advantage for organizations with stringent security or regulatory requirements.
Choosing the Right Solution
Selecting the appropriate immutable storage solution necessitates a careful evaluation of several factors. These include the volume of data to be stored, performance requirements, budget constraints, and the level of control needed over data management. The need for data compliance and regulatory requirements, like HIPAA or GDPR, should also influence the choice. Organizations must also consider future growth projections and potential scalability needs.
Comparison of Immutable Storage Technologies
| Technology | Pros | Cons |
|---|---|---|
| Amazon S3 with Immutability Policies | Scalability, ease of use, cost-effectiveness (often), wide availability | Vendor lock-in, potential for data breaches if cloud provider is compromised |
| Azure Blob Storage with Immutability Policies | Robust security features, high availability, diverse integration options | Potential cost variations based on usage, reliance on cloud provider |
| Google Cloud Storage with Immutability Policies | Advanced data analytics tools, flexible storage options | Pricing structure can be complex, vendor lock-in |
| On-Premise Immutable Storage Appliance | Complete control over data, high security, no vendor lock-in | High initial investment, complex implementation and maintenance |
Challenges and Considerations
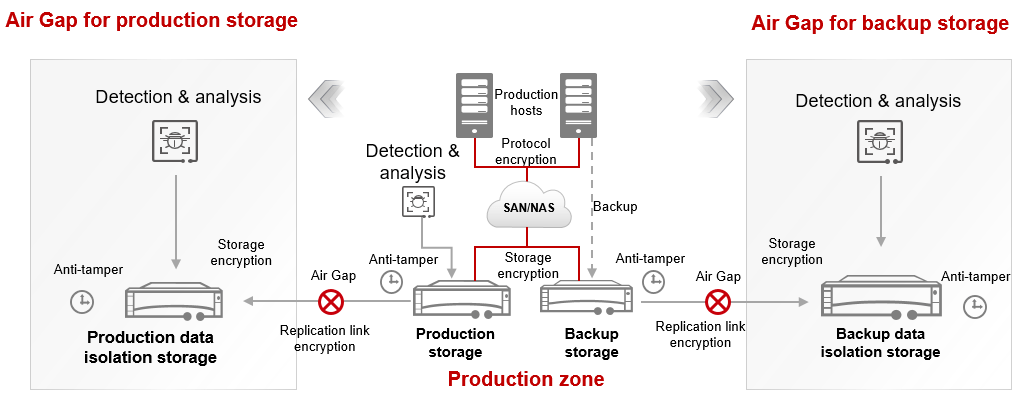
Immutable data storage, while offering strong ransomware protection, presents its own set of hurdles. The fundamental nature of immutability—once written, data cannot be altered—requires careful planning and consideration to avoid unforeseen problems. These challenges range from the initial implementation complexities to the ongoing management of data retention and recovery. Understanding these issues is crucial for organizations seeking to leverage the benefits of immutable storage without compromising operational efficiency.Implementing immutable storage solutions often necessitates a shift in existing data management practices.
This transition can be complex, involving changes to workflows, infrastructure, and potentially the retraining of personnel. Furthermore, the inherent immutability of the data can create challenges when dealing with accidental data loss or the need for data updates.
Implementation Challenges
Careful planning and thorough testing are critical for successful implementation. This includes the selection of appropriate storage solutions that align with organizational needs and regulatory requirements. Selecting the right vendor and technology is critical, requiring a thorough understanding of the strengths and weaknesses of each option. Testing should include simulations of ransomware attacks and data recovery procedures to ensure preparedness.
This includes evaluating how the system handles high volumes of data and potential performance bottlenecks.
Immutable data storage is truly the last line of defense against ransomware attacks. While initiatives like the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions are helpful, they don’t completely solve the problem. Ultimately, having data that can’t be altered is the strongest safeguard against malicious actors looking to encrypt or delete critical information.
Data Retention and Recovery
Immutable storage by its nature prevents modification. Therefore, traditional data recovery methods based on rollback or modification are not applicable. Implementing a robust data retention and recovery strategy is essential for minimizing the impact of data loss. Data backups are necessary to maintain historical versions of the data and to facilitate data recovery. However, the nature of immutable storage requires the backups themselves to be stored immutably as well.
Limitations and Drawbacks
Immutable data storage, while a powerful defense against ransomware, isn’t a silver bullet. One significant limitation is the inability to directly modify existing data. This can pose problems for situations requiring data updates or corrections. Another potential drawback is the increased storage costs associated with maintaining multiple versions of the data, including backups. Careful evaluation of storage capacity is essential to prevent unexpected costs.
Additionally, existing data management systems may need significant adjustments to integrate with immutable storage.
Mitigating Challenges
Data retention and recovery in immutable systems require a multi-layered approach. Regular data backups to immutable storage are crucial, with versioning to maintain historical data. A comprehensive disaster recovery plan is vital, encompassing data retrieval processes and testing procedures. A clear understanding of data retention policies, along with the legal and regulatory implications of data storage and retention, should be implemented.
A key aspect of mitigation is the creation of a robust and tested recovery process that considers all potential failure scenarios.
Summary of Challenges and Solutions
| Challenge | Suggested Solution |
|---|---|
| Inability to modify existing data | Implement a system for data versioning and backups, ensuring all previous versions are also immutable. |
| Increased storage costs | Optimize storage capacity utilization, leverage cloud-based solutions for scalable storage, and employ efficient data compression techniques. |
| Compatibility with existing systems | Choose storage solutions that integrate seamlessly with existing workflows and data management systems. |
| Data retention and recovery | Implement a robust backup and recovery strategy, utilizing immutable storage for backups as well. Develop a documented disaster recovery plan. |
Case Studies and Examples
Immutable data storage is proving to be a powerful tool in the fight against ransomware. While the theoretical benefits are clear, seeing real-world examples of organizations successfully using this technology to mitigate attacks provides invaluable insight. These case studies reveal the practical application and effectiveness of these strategies, highlighting not only the technical aspects but also the organizational and operational considerations involved.
Real-World Implementations
Organizations adopting immutable data storage are finding that it significantly reduces the risk of data loss from ransomware attacks. This approach effectively prevents attackers from encrypting or deleting critical data, as the data is permanently protected from modification. A critical element in these implementations is the proactive design and implementation of robust backup and recovery strategies. By employing immutable storage for the primary data repository, organizations are able to focus on efficient backups for recovery purposes.
Specific Benefits and Outcomes
A key benefit of immutable data storage is the significant reduction in downtime associated with ransomware attacks. By ensuring the data’s immutability, organizations can quickly restore to known good versions, minimizing the disruption to operations. This resilience is further enhanced by a well-defined backup and recovery strategy. In many cases, these implementations have resulted in substantial cost savings, as the recovery process is faster and less complex compared to traditional methods.
Faster recovery time also translates to reduced business interruption and financial losses.
Role of Backup and Recovery
Backup and recovery strategies are crucial components of an effective ransomware defense strategy. When data is stored immutably, the backup process focuses on maintaining consistent copies of the data, enabling rapid recovery to a known, good state. These backups, stored in a separate immutable repository, are not subject to the same vulnerabilities as the primary data. By implementing a robust backup and recovery plan, organizations can minimize the impact of ransomware events and quickly restore their operations.
Key Lessons Learned
| Lesson | Explanation |
|---|---|
| Data Immutability is Crucial | Immutable data storage is essential to prevent ransomware from corrupting or deleting critical data. |
| Comprehensive Backup Strategy is Essential | A well-defined backup strategy, coupled with immutable storage, is crucial for rapid recovery to a known, good state. |
| Security-Focused Data Architecture | Immutable data storage requires a careful consideration of the data architecture to ensure that all data and critical systems are secured and protected. |
| Regular Testing and Validation | Regular testing and validation of backup and recovery procedures are vital to ensure the effectiveness of the overall solution. |
| Training and Awareness | Employee training and awareness programs on ransomware prevention and data security best practices are important. |
Future Trends and Predictions: Immutable Data Storage Is Last Line Of Defense Against Ransomware
Immutable data storage is rapidly evolving, moving beyond a simple ransomware defense mechanism. Its potential extends far beyond cybersecurity, impacting areas like data integrity, compliance, and even decentralized applications. This evolution will be driven by advancements in technology and a growing awareness of its importance in safeguarding critical information.The future of immutable data storage will be defined by its ability to adapt to the ever-changing landscape of security threats.
Expect to see innovations that enhance immutability’s efficiency, scalability, and accessibility. These advancements will be crucial for businesses and organizations to maintain data integrity and compliance in a rapidly evolving digital environment.
Immutable Storage and Blockchain Integration
Blockchain technology’s inherent immutability aligns perfectly with the principles of immutable data storage. This integration will likely lead to more secure and transparent data management systems. Organizations can leverage blockchain’s decentralized nature to further enhance the resilience of their data against unauthorized modification or deletion. This will enable secure and verifiable data provenance, ensuring data integrity across the entire lifecycle.
Enhanced Scalability and Accessibility
Current immutable storage solutions face challenges with scaling to meet the demands of massive datasets. Future developments will focus on optimizing storage infrastructure and improving data retrieval mechanisms. This will involve exploring novel indexing and retrieval techniques, possibly integrating with cloud-based storage solutions. The goal is to maintain immutability while simultaneously enhancing scalability and accessibility for easier data management and analysis.
Advanced Data Integrity Verification
Methods for verifying data integrity will become more sophisticated. Advanced cryptographic techniques and distributed ledger technologies will play a crucial role in ensuring the authenticity and trustworthiness of immutable data. The development of more efficient and robust verification processes will be paramount to maintaining the security and reliability of immutable storage solutions.
Table of Potential Future Developments
| Emerging Technology | Use Cases |
|---|---|
| Blockchain-based immutability verification | Enhanced data provenance, tamper-proof audit trails, and secure data sharing in supply chains. |
| Decentralized immutable storage networks | Improved data redundancy and resilience, mitigating single points of failure, and enhancing data security in distributed environments. |
| AI-powered anomaly detection in immutable storage | Real-time identification of potential security threats and malicious activity, enhancing proactive security measures, and improving the accuracy of threat detection. |
| Improved data retrieval and querying | Faster access to data, efficient data analysis, and reduced latency in data retrieval for various applications. |
| Integration with cloud storage services | Enhanced scalability and accessibility, cost-effectiveness, and seamless integration with existing infrastructure. |
Closing Notes

In conclusion, immutable data storage presents a powerful countermeasure against the ever-evolving threat of ransomware. By embracing immutability, organizations can enhance their resilience against these attacks and protect their data integrity. While challenges remain, the proactive implementation of immutable storage solutions is crucial in today’s increasingly complex cybersecurity landscape.
FAQ Corner
What are the common types of ransomware attacks?
Ransomware attacks can manifest in various forms, including encrypting files, locking systems, or disrupting operations. Some common types include Locker ransomware, which locks the system; Crypto ransomware, which encrypts files; and Wiper ransomware, which permanently deletes data.
What are the potential limitations of immutable storage solutions?
While highly effective against ransomware, immutable storage solutions might present challenges in data retention and recovery. The immutability nature can make it difficult to recover from accidental deletion or corrupted data. Careful planning and data backup strategies are essential to mitigate these limitations.
How does immutability prevent ransomware attacks?
Immutable storage systems prevent ransomware by not allowing the modification or deletion of data once it’s stored. This inherent property makes it virtually impossible for ransomware to encrypt or delete data, significantly reducing the threat of data loss and financial damage.
What are some examples of successful implementations of immutable data storage?
Numerous organizations have successfully deployed immutable storage solutions to bolster their ransomware defenses. Specific examples are often confidential due to security concerns, but the general trend shows a positive impact in mitigating ransomware risks. Many organizations report substantial reductions in attack impact and faster recovery times.