Cisco Announces Plan to Buy Observable Networks for Cloud Security
Cisco announces plan to buy Observable Networks for cloud security – a move that’s sent ripples through the tech world! This acquisition isn’t just another deal; it’s a strategic play in the ever-evolving landscape of cloud security. We’re diving deep into what this means for Cisco, Observable Networks, and the future of protecting our digital assets. Get ready to explore the potential impact on the market, the technology behind the acquisition, and the long-term implications for businesses of all sizes.
Cisco’s history of strategic acquisitions in cybersecurity is well-documented, and this latest move with Observable Networks promises to be another significant chapter. Observable’s unique approach to cloud security, focusing on [insert key feature of Observable’s tech here], makes them a valuable asset. The integration of this technology into Cisco’s existing portfolio could revolutionize how we approach cloud security, potentially leading to more robust, proactive, and efficient defenses against cyber threats.
But will the acquisition be a seamless process? What challenges might Cisco face in integrating such a specialized technology? Let’s find out.
Cisco’s Acquisition Strategy
Cisco’s acquisition of Observable Networks represents a significant move in its ongoing strategy to bolster its cloud security offerings. This isn’t a standalone event, but rather a continuation of a long-standing pattern of strategic acquisitions designed to expand its market reach and technological capabilities within the cybersecurity landscape. Understanding Cisco’s historical acquisition patterns is key to grasping the full significance of this latest deal.
Cisco’s Historical Acquisition Patterns in Cybersecurity
Cisco has a long and rich history of acquiring companies to enhance its cybersecurity portfolio. The company’s strategy often involves acquiring smaller, innovative companies with specialized technologies that complement its existing product lines. This allows Cisco to rapidly integrate cutting-edge solutions, avoiding lengthy in-house development cycles. Past acquisitions have targeted areas like network security, endpoint security, cloud security, and threat intelligence.
Notable examples include the acquisitions of Sourcefire (network intrusion prevention), OpenDNS (DNS security), and Duo Security (multi-factor authentication). These acquisitions showcase a clear pattern of strategically targeting specific gaps in their offerings to build a comprehensive cybersecurity ecosystem.
Strategic Rationale Behind Acquiring Observable Networks
Observable Networks specializes in providing cloud-native security solutions focusing on network detection and response. Their technology offers real-time visibility and threat detection capabilities across cloud environments, a crucial area where Cisco aimed to strengthen its position. The acquisition allows Cisco to directly address the increasing demand for robust cloud security solutions by integrating Observable Networks’ technology into its existing portfolio.
This move enhances Cisco’s ability to compete effectively with other major players in the cloud security market and provides its customers with a more comprehensive and integrated security solution across on-premises and cloud environments. The integration of Observable Networks’ advanced threat detection capabilities is expected to significantly improve Cisco’s threat response times and overall security posture for its cloud customers.
Cisco’s big move to acquire Observable Networks for bolstering its cloud security is huge news! It makes me think about how quickly the tech landscape is changing, and how that impacts development. For instance, the shift towards low-code/no-code solutions, as discussed in this insightful article on domino app dev the low code and pro code future , is equally transformative.
This kind of agility is crucial, especially as companies like Cisco invest heavily in enhancing cloud security infrastructure.
Comparison to Other Significant Cisco Acquisitions
The Observable Networks acquisition shares similarities with previous Cisco acquisitions, particularly those focused on expanding its security capabilities. Like the acquisitions of Sourcefire and Duo Security, this deal targets a specific niche within the broader cybersecurity market – in this case, cloud-native network security. However, the focus on cloud-native technologies differentiates this acquisition from earlier ones that primarily addressed on-premises security challenges.
The scale of the acquisition may be smaller compared to some of Cisco’s larger acquisitions, but its strategic importance in the context of the rapidly growing cloud security market is substantial. The integration of Observable Networks’ technology is likely to be a key differentiator for Cisco’s cloud security offerings in the near future.
SWOT Analysis of Observable Networks Before Acquisition
Prior to the acquisition, Observable Networks possessed several strengths, including its innovative cloud-native security platform and a strong team of engineers. Its weaknesses might have included a relatively smaller market share compared to established players and limited brand recognition. Opportunities lay in the rapidly expanding cloud security market and the increasing demand for advanced threat detection capabilities. Threats included intense competition from larger, well-established cybersecurity firms and the challenges associated with scaling its operations to meet growing market demands.
Timeline of Key Events Leading to the Acquisition Announcement
A precise timeline requires access to internal Cisco and Observable Networks documents. However, a generalized timeline could include:
- Early Stages: Initial exploration and due diligence by Cisco.
- Negotiations: Formal negotiations between Cisco and Observable Networks regarding terms and conditions.
- Agreement: Reaching a definitive agreement on the acquisition price and terms.
- Regulatory Approvals: Securing necessary regulatory approvals for the acquisition.
- Announcement: Public announcement of the acquisition by Cisco.
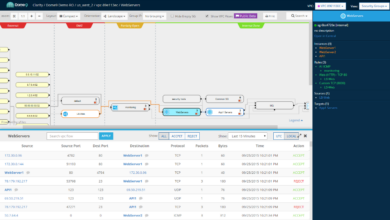
Observable Networks’ Technology and Capabilities
Observable Networks’ acquisition by Cisco signals a significant move in bolstering Cisco’s cloud security offerings. Their technology offers a unique approach to securing cloud environments, going beyond traditional security methods to provide comprehensive visibility and threat detection. This deeper dive explores the core technology, its advantages, and how it differentiates itself in the competitive landscape.Observable Networks’ core technology centers around its patented “Network Traffic Analysis” (NTA) engine.
Cisco’s big move to acquire Observable Networks for bolstering its cloud security game is a fascinating development. This highlights the growing importance of robust cloud security solutions, a trend perfectly illustrated by the advancements in Cloud Security Posture Management (CSPM), as discussed in this insightful article on bitglass and the rise of cloud security posture management. Ultimately, Cisco’s acquisition underscores the intense competition and rapid innovation within the cloud security landscape.
Unlike traditional security solutions that rely on isolated point tools, Observable Networks leverages a holistic approach, analyzing all network traffic within a cloud environment to build a comprehensive view of application behavior and identify anomalies. This allows for the detection of threats that might otherwise go unnoticed by relying solely on signature-based or anomaly detection systems operating in isolation.
The unique selling proposition lies in its ability to provide context-rich insights, allowing security teams to understand the “why” behind potential threats, not just the “what.” This speeds up investigation and response times significantly.
Observable Networks’ Technology Enhancement of Cloud Security
Observable Networks’ technology enhances cloud security by providing comprehensive visibility across complex cloud environments. Its NTA engine analyzes network traffic flows, identifies unusual patterns, and correlates data from various sources to detect sophisticated threats like lateral movement, data exfiltration, and insider threats. This holistic approach goes beyond simple intrusion detection and prevention systems (IDS/IPS), providing a more proactive and effective security posture.
By analyzing traffic patterns and application behavior, the platform identifies deviations from established baselines, flagging potentially malicious activities early in the attack chain. This proactive approach minimizes the impact of security breaches and reduces the time to resolution.
Real-World Use Cases
Consider a scenario where a compromised server within a cloud environment begins communicating with a known malicious IP address. Traditional security tools might detect this communication, but may lack the context to understand the full scope of the compromise. Observable Networks, however, would not only detect the communication but also identify the compromised server, the path the attacker took to gain access, and potentially other compromised systems within the network.
This granular level of visibility allows for swift containment and remediation. Another example would be the detection of an insider threat attempting to exfiltrate sensitive data. By analyzing unusual data transfer patterns, Observable Networks could identify the user, the data being exfiltrated, and the method used, providing crucial information for investigation and legal proceedings.
Key Differentiators from Competing Cloud Security Solutions
Observable Networks distinguishes itself from competitors by its unparalleled visibility and context-rich analysis. While many solutions focus on individual security aspects, such as firewalling or intrusion detection, Observable Networks provides a unified platform that correlates data from multiple sources, delivering a complete picture of the network’s security posture. This holistic approach, combined with its advanced analytics capabilities, enables faster threat detection and response, minimizing the impact of security incidents.
This differs from solutions that may only provide alerts without sufficient context to understand and respond effectively. The platform’s ease of deployment and integration with existing security infrastructure also contributes to its competitive advantage.
Comparison Table of Observable Networks’ Features Versus Major Competitors
| Feature | Observable Networks | Competitor A (e.g., CrowdStrike) | Competitor B (e.g., Palo Alto Networks) |
|---|---|---|---|
| Network Visibility | Comprehensive, holistic view of network traffic | Endpoint-focused, network visibility limited | Network-focused, but less context-rich analysis |
| Threat Detection | Proactive detection of advanced threats | Reactive detection, relies heavily on signatures | Detects known threats effectively, but less effective against novel attacks |
| Contextual Analysis | Provides rich context for faster investigation | Limited contextual information | Moderate contextual information |
| Ease of Deployment | Easy integration with existing infrastructure | Requires significant configuration and integration | Moderate complexity in deployment |
Impact on the Cloud Security Market: Cisco Announces Plan To Buy Observable Networks For Cloud Security
Cisco’s acquisition of Observable Networks sends significant ripples through the already competitive cloud security market. This move isn’t just about adding another product to Cisco’s portfolio; it’s a strategic play to bolster its cloud security capabilities and potentially reshape the competitive landscape. The integration of Observable Networks’ advanced threat detection and response technology will undoubtedly influence pricing, availability, and innovation within the sector.The acquisition’s impact will be multifaceted, affecting various players and segments of the market.
The combined strengths of Cisco’s extensive customer base and Observable Networks’ cutting-edge technology create a powerful force, capable of influencing market dynamics in several ways.
Competitive Landscape Shifts
The acquisition significantly alters the competitive landscape. Previously, companies like CrowdStrike, Palo Alto Networks, and SentinelOne held strong positions in the cloud security market, offering comparable solutions. Cisco’s acquisition of Observable Networks’ telemetry-based detection and response capabilities enhances its competitive standing, potentially challenging the dominance of these established players. This is especially true in the areas of advanced threat detection and incident response, where Observable Networks excels.
The combined entity now offers a more comprehensive and potentially more effective solution, attracting customers seeking a unified approach to cloud security. Smaller players might face increased pressure to innovate or consolidate to remain competitive.
Pricing and Availability of Cloud Security Solutions
The impact on pricing and availability is complex and depends on several factors, including Cisco’s strategic goals. While Cisco might initially maintain or even slightly increase prices to reflect the enhanced capabilities of the combined offering, long-term pricing strategies are difficult to predict. Increased competition could lead to adjustments, potentially even downward pressure on prices in certain segments.
Availability could also be affected; Cisco’s extensive distribution network could broaden the reach of Observable Networks’ technology, making it more accessible to a wider range of organizations. However, Cisco might prioritize its existing customer base, potentially leading to some initial limitations in availability for new clients.
Innovation in Cloud Security
The acquisition has the potential to spur innovation in several ways. The combination of Cisco’s existing security infrastructure and Observable Networks’ advanced analytics could lead to more effective threat detection and response capabilities. For example, integrating Observable Networks’ technology into Cisco’s existing SecureX platform could create a more unified and intelligent security system, providing enhanced visibility and automation. This could result in the development of new features and functionalities, such as proactive threat hunting capabilities or improved automation for incident response.
Furthermore, Cisco’s resources could accelerate the development and deployment of Observable Networks’ technology, leading to faster innovation cycles and quicker adaptation to evolving threats.
Challenges in Integrating Observable Networks’ Technology
Integrating Observable Networks’ technology into Cisco’s existing ecosystem presents significant challenges. Technical compatibility, data integration, and cultural differences between the two organizations could create hurdles. Ensuring seamless integration between different platforms and technologies will require careful planning and execution. Managing the transition and maintaining existing customer relationships during the integration process is also crucial. The success of the integration will depend on effective communication, collaboration, and a well-defined integration strategy.
Failure to address these challenges could result in delays, technical glitches, and customer dissatisfaction.
Hypothetical Scenario: Impact on the Financial Services Industry
Consider a large financial institution heavily reliant on cloud-based infrastructure. Before the acquisition, this institution might have used a patchwork of security solutions from different vendors, resulting in fragmented visibility and inefficient response times. Post-acquisition, this institution could leverage Cisco’s integrated security platform enhanced by Observable Networks’ technology. This would provide a unified view of its cloud security posture, enabling proactive threat hunting and automated incident response.
The improved security posture could reduce the risk of costly data breaches and regulatory fines, resulting in significant cost savings and increased operational efficiency. The enhanced security could also bolster customer trust and improve the institution’s competitive advantage in a highly regulated industry.
Financial Implications and Market Reaction
Cisco’s acquisition of Observable Networks, while strategically sound, carries significant financial implications and will undoubtedly impact investor sentiment. The success of this deal hinges on several factors, including the integration process, market reception of the combined offerings, and, of course, the financial terms themselves. Let’s delve into the specifics.
Acquisition Cost and Funding
While the exact financial terms weren’t publicly disclosed in the initial announcement, acquisitions of this nature often involve a combination of cash and stock. Given Cisco’s considerable financial resources, a predominantly cash offer is likely, but a portion might be paid in Cisco stock to incentivize Observable Networks’ shareholders and potentially reduce the immediate impact on Cisco’s cash reserves.
Speculation in financial news outlets placed the acquisition price somewhere in the range of $200 million to $500 million, although this remains unconfirmed. The final cost will influence Cisco’s short-term earnings and will be carefully scrutinized by analysts. For comparison, Cisco’s acquisition of Duo Security in 2018 was valued at approximately $2.35 billion, showcasing the scale of potential deals in the cybersecurity space.
Potential Return on Investment
Cisco anticipates a strong return on investment from this acquisition. Observable Networks’ technology fills a crucial gap in Cisco’s cloud security portfolio, allowing them to offer a more comprehensive and competitive solution. The potential ROI stems from several sources: increased market share in the rapidly growing cloud security sector, cross-selling opportunities with existing Cisco customers, and the potential for new revenue streams from Observable Networks’ unique capabilities.
The success of the integration and the ability to effectively market the combined offerings will be critical in realizing this predicted ROI. Successful integrations, such as Cisco’s acquisition of Meraki, which seamlessly integrated into their existing portfolio, serve as a positive precedent.
Initial Market Reaction
The initial market reaction to the acquisition announcement was largely positive, with a modest increase in Cisco’s stock price. Investors generally viewed the acquisition as a strategic move to bolster Cisco’s cloud security capabilities, a vital area for growth. News outlets highlighted the deal’s strategic fit and the potential synergies between the two companies. However, the lack of detailed financial information initially limited the extent of the positive reaction.
The market’s response was less enthusiastic than some other high-profile tech acquisitions, possibly due to the relatively smaller size of the deal in comparison to Cisco’s overall market capitalization.
Shifting Investor Sentiment
Investor sentiment in the following months will depend heavily on the successful execution of the integration process and the demonstration of tangible benefits. Positive factors, such as rapid integration, increased sales of the combined offerings, and clear evidence of cost synergies, will likely lead to a sustained increase in Cisco’s stock price. Conversely, delays in integration, lackluster sales performance, or unexpected challenges in combining the two technologies could negatively impact investor confidence and result in a decrease in the stock price.
This highlights the importance of transparent communication from Cisco regarding the progress of the integration and the performance of the acquired technology. Investor reports and financial analyst commentary will be crucial in shaping this evolving sentiment.
Hypothetical Stock Price Prediction, Cisco announces plan to buy observable networks for cloud security
A hypothetical graph illustrating potential market response might show a modest initial increase following the announcement, followed by a period of consolidation. If the integration proceeds smoothly and the combined offerings perform well, the stock price could experience a gradual, sustained upward trend over the next 12-18 months. However, if challenges arise during the integration or if the market response to the new offerings is underwhelming, the stock price might plateau or even decline slightly before potentially recovering.
The graph would depict a relatively stable price initially, rising slightly upon the announcement, followed by a gradual incline if the acquisition is successful, or a plateau/dip if integration and market acceptance are problematic. This resembles the pattern seen with other successful technology acquisitions, such as Salesforce’s acquisition of Tableau, where initial market enthusiasm was followed by a period of consolidation before sustained growth.
A significant negative deviation from this pattern would indicate unforeseen issues with the acquisition.
Integration and Future Outlook

The acquisition of Observable Networks by Cisco presents both significant challenges and exciting opportunities. Successfully integrating Observable’s technology and talent into Cisco’s existing ecosystem will be crucial for realizing the full potential of this deal. The integration process will likely involve careful planning, resource allocation, and a strategic approach to minimizing disruption while maximizing synergy.Integrating Observable Networks’ technology and personnel into Cisco’s vast infrastructure will require a multi-faceted strategy.
Cisco will likely prioritize a phased approach, starting with the integration of key personnel and core technologies. This will involve careful consideration of cultural compatibility, ensuring a smooth transition for Observable employees and minimizing any potential friction. Simultaneously, Cisco will need to develop a clear roadmap for integrating Observable’s cloud-native security platform into its existing security portfolio, leveraging its established distribution channels and customer relationships.
Synergies Between Cisco and Observable Networks
The combination of Cisco’s extensive network infrastructure expertise and Observable’s advanced cloud security capabilities creates powerful synergies. Cisco’s broad customer base provides a ready market for Observable’s solutions, particularly within enterprise environments requiring robust cloud security. Observable’s technology, focused on detecting and responding to threats across complex cloud environments, complements Cisco’s existing security offerings, allowing for a more comprehensive and integrated security posture.
For example, integrating Observable’s threat detection capabilities with Cisco’s Secure Access Service Edge (SASE) platform could provide a unified, cloud-based security solution that offers enhanced visibility and protection. This synergy could lead to the development of more effective security solutions, better protecting organizations from increasingly sophisticated cyber threats.
Future of Cloud Security Post-Acquisition
This acquisition signifies a significant shift in the cloud security landscape. Cisco’s acquisition of Observable Networks underscores the growing importance of cloud-native security solutions and the increasing demand for comprehensive security architectures that span on-premises and cloud environments. We can expect to see increased innovation in cloud security, driven by the integration of Observable’s advanced threat detection and response capabilities with Cisco’s broader security portfolio.
Similar to the way Cisco’s acquisition of Meraki transformed the networking market, this acquisition has the potential to significantly impact the cloud security market by offering a more comprehensive and integrated solution. The combined entity will be better positioned to compete with other major players in the cloud security space, leading to further innovation and improvements in cloud security technology.
Potential Future Product Offerings
The integration of Observable Networks into Cisco’s portfolio is likely to result in several new and enhanced product offerings. The following bullet points illustrate potential future product directions:
- An enhanced Cisco SecureX platform with integrated threat detection and response capabilities from Observable Networks, providing a single pane of glass for managing security across hybrid environments.
- A cloud-native security information and event management (SIEM) solution leveraging Observable’s data analytics and threat intelligence capabilities.
- Integrated security solutions for specific cloud platforms (e.g., AWS, Azure, GCP) incorporating Observable’s expertise in cloud-native security.
- Advanced threat hunting and incident response capabilities powered by Observable’s technology, offering proactive threat detection and faster remediation.
- A more comprehensive SASE offering with integrated cloud security capabilities, providing enhanced security and performance for users accessing cloud resources.
Final Thoughts
Cisco’s acquisition of Observable Networks is more than just a financial transaction; it’s a statement about the future of cloud security. By bringing Observable’s innovative technology under its umbrella, Cisco is positioning itself to lead the charge in a rapidly changing market. The success of this integration will depend on careful planning and execution, but the potential rewards are enormous – a more secure digital world for all of us.
Only time will tell the full impact, but one thing is certain: this is a game-changer worth watching.
Common Queries
What is Observable Networks’ core technology?
Observable Networks specializes in [brief, concise description of their core technology, e.g., a cloud-native security platform that uses AI and machine learning to detect and respond to threats].
How much did Cisco pay for Observable Networks?
The exact financial terms of the acquisition haven’t been publicly disclosed yet.
When will the acquisition be finalized?
The completion date for the acquisition is expected to be [insert expected completion date if available, otherwise say “not yet announced”].
Will this acquisition lead to job losses?
It’s too early to say definitively. Cisco typically aims for smooth integrations, but some restructuring is possible.