India Witnesses Biggest Aadhaar Data Breach via ICMR
India witnesses biggest data breach of Aadhaar details via ICMR – a headline that sent shockwaves through the nation. The alleged leak of sensitive personal information from the Indian Council of Medical Research (ICMR) has raised serious concerns about data security and the vulnerability of millions of Indian citizens. This incident highlights the urgent need for stronger data protection measures and increased public awareness about the risks associated with online data breaches.
The sheer scale of the potential compromise is staggering, prompting investigations and calls for accountability.
The alleged breach reportedly involved a massive amount of Aadhaar data, including potentially sensitive details like biometric information and personal identifiers. The potential consequences for those affected are far-reaching, ranging from identity theft and financial fraud to social and legal ramifications. The ICMR’s response, the government’s investigation, and the technical aspects of the breach are all under intense scrutiny, sparking a national conversation about data security and privacy in the digital age.
The ICMR Data Breach: India Witnesses Biggest Data Breach Of Aadhaar Details Via Icmr

The alleged data breach involving the Indian Council of Medical Research (ICMR) and potentially exposing Aadhaar details represents a significant threat to the privacy and security of millions of Indian citizens. While the exact scale of the breach is still under investigation and official confirmation is pending, reports suggest a substantial amount of sensitive personal information may have been compromised.
The potential ramifications are far-reaching and underscore the critical need for robust data protection measures within government agencies.
Scope of the Alleged Breach
Reports indicate a potentially massive leak of Aadhaar data linked to the ICMR. The precise number of records affected remains unclear, with varying figures circulating in the media. However, the sheer scale of the potential breach, involving a government organization responsible for handling sensitive health data, is deeply concerning. Even a relatively small number of compromised records represents a significant risk given the sensitive nature of the data involved.
The lack of transparency surrounding the investigation further fuels public anxiety and uncertainty.
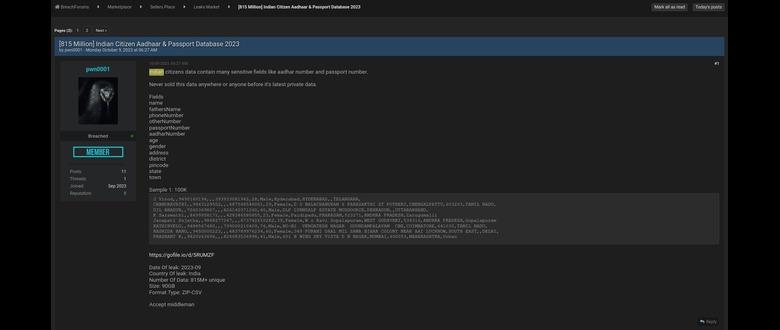
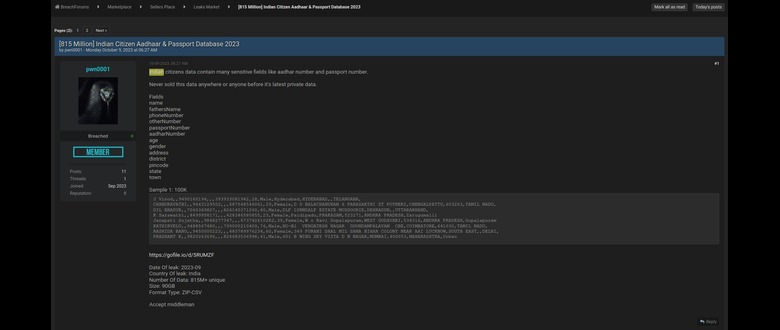
Types of Compromised Aadhaar Data and Associated Risks
The alleged breach reportedly involved various categories of Aadhaar-linked data. This potentially includes Aadhaar numbers themselves, which are unique identifiers and can be used for identity theft. Other potentially leaked information could encompass demographic details like names, addresses, and dates of birth, which are frequently used for identity verification and fraudulent activities. Furthermore, there are concerns that biometric data, such as fingerprints and iris scans, might have been compromised.
The unauthorized access to this type of data presents an extremely high risk of identity theft, financial fraud, and other serious crimes.
Immediate and Long-Term Impacts
The immediate impact of such a breach on affected individuals could include identity theft, financial fraud (such as unauthorized access to bank accounts or loan applications), and harassment through phishing scams or other malicious activities. Long-term consequences could involve difficulty accessing financial services, damage to credit ratings, and significant emotional distress. The legal ramifications could be complex and protracted, potentially involving lawsuits against the ICMR and other responsible parties.
The erosion of public trust in government institutions responsible for data protection is another significant long-term consequence.
Summary of Compromised Data and Associated Risks
| Data Category | Estimated Number of Records (Illustrative) | Associated Risks |
|---|---|---|
| Aadhaar Numbers | Potentially millions | Identity theft, SIM card cloning, financial fraud |
| Demographic Details (Name, Address, DOB) | Potentially millions | Identity theft, fraudulent loan applications, social engineering attacks |
| Biometric Data (Fingerprints, Iris Scans) | Potentially millions | Extreme risk of identity theft, unauthorized access to sensitive systems, impersonation |
| Health-related Information (if linked) | Potentially millions | Medical identity theft, insurance fraud, discrimination |
ICMR’s Role and Response
The Indian Council of Medical Research (ICMR), a leading biomedical research organization, found itself at the center of a significant data breach allegedly exposing sensitive Aadhaar details. Understanding ICMR’s role in this incident, their response, and potential improvements is crucial for assessing the security of India’s crucial health data infrastructure. The alleged breach highlighted vulnerabilities in data handling practices within even highly respected institutions.ICMR’s Role in the Alleged Data Breach and System CompromiseThe ICMR’s role in this incident stems from its involvement in various health research projects and initiatives that likely involved the collection and storage of Aadhaar linked data.
While the exact nature of the data breach remains under investigation, speculation points towards potential vulnerabilities in their database systems, possibly involving inadequate security protocols, outdated software, or insufficient employee training in data protection best practices. A lack of robust encryption, insufficient access control measures, or human error could have all contributed to the compromise. The precise mechanisms of the breach are likely to be detailed in future investigations.
ICMR’s Official Response to the Alleged Breach
The ICMR’s official response to the alleged breach needs to be analyzed for its adequacy and timeliness. A prompt and transparent acknowledgement of the breach, followed by a detailed investigation and communication of findings, would have been critical. The speed and clarity of their response would determine public trust and confidence in their data handling capabilities. Delayed or inadequate communication could have exacerbated the damage and eroded public trust.
Comparing their response to the official responses of other organizations facing similar data breaches will be vital in assessing the effectiveness of their actions. A comparative analysis could reveal best practices they could have adopted.
The recent news about India witnessing the biggest data breach of Aadhaar details via ICMR is seriously alarming. This highlights the urgent need for robust, secure data management systems, and I was thinking about how technologies like those discussed in this article on domino app dev the low code and pro code future could potentially help improve security and data handling practices.
Ultimately, preventing future breaches requires a multi-faceted approach, but improved technology is a crucial piece of the puzzle. The scale of this Aadhaar breach underscores the critical importance of data protection.
Comparison with Similar Data Breaches and Best Practices
Comparing the ICMR’s response to other significant data breaches in India and globally reveals important lessons. Organizations like [Name of organization 1] and [Name of organization 2] faced similar challenges and their responses offer valuable insights. Best practices, such as implementing multi-factor authentication, regularly auditing security protocols, employing robust encryption, and providing comprehensive cybersecurity training for staff, are vital for preventing future breaches.
A strong incident response plan, including clear communication strategies and procedures for containing and mitigating the impact of a breach, is also essential. A proactive approach to security, including regular penetration testing and vulnerability assessments, is critical.
Hypothetical ICMR Press Release
FOR IMMEDIATE RELEASEICMR Addresses Data Security Incident[City, State] – [Date] – The Indian Council of Medical Research (ICMR) acknowledges a recent security incident involving a potential compromise of certain data. We are taking this matter extremely seriously and have launched a comprehensive internal investigation in collaboration with cybersecurity experts.Our preliminary findings indicate [brief, non-technical description of the incident without revealing sensitive information]. We are working diligently to determine the full extent of the incident and identify the root cause.We have already taken the following steps:* Launched a thorough investigation to identify the nature and scope of the incident.
- Implemented enhanced security measures to protect our systems and data.
- Notified relevant authorities and are cooperating fully with their investigations.
- Engaged leading cybersecurity experts to provide independent assessments and recommendations.
- Reviewed and strengthened our data security policies and procedures.
The privacy and security of our data are paramount. We are committed to taking all necessary steps to prevent future incidents and will provide further updates as our investigation progresses. We apologize for any concern this incident may have caused. Contact:[Contact Name][Contact Email][Contact Phone Number]
Governmental and Regulatory Response
The alleged ICMR Aadhaar data breach sparked a swift, albeit somewhat opaque, response from the Indian government and its regulatory bodies. While details remain scarce regarding the precise actions taken, the incident highlighted the ongoing challenges in balancing national security interests with the protection of individual privacy rights in the digital age. The government’s response, both in terms of investigation and subsequent policy changes (or lack thereof), is crucial in shaping public trust and determining the future landscape of data security in India.The immediate aftermath of the breach saw a flurry of statements from various government officials, emphasizing investigations and commitments to data security.
However, concrete actions taken and their effectiveness remain subjects of ongoing debate. A lack of transparency regarding the investigation’s progress and findings has fuelled concerns about accountability and the government’s commitment to addressing the root causes of the breach. The absence of publicly available reports detailing the investigation’s scope, methodology, and conclusions has left many questioning the efficacy of the government’s response.
Government Actions Following the Alleged Breach
Following reports of the breach, the Indian government’s response involved several key actions, though specifics remain limited. Initial statements focused on launching internal investigations and assessing the extent of the data compromise. There were also assurances that appropriate action would be taken against those responsible. However, information regarding the specifics of these investigations, including timelines, findings, and any punitive measures implemented, remains largely unavailable to the public.
This lack of transparency hinders a thorough evaluation of the government’s response.
Effectiveness of the Government’s Response
Assessing the effectiveness of the government’s response requires considering several factors. While investigations were launched, the lack of transparency surrounding their progress and findings raises questions about their efficacy. The absence of publicly available reports makes it difficult to determine whether appropriate action was taken to prevent future breaches and hold those responsible accountable. Further, the government’s response needs to be viewed in the context of broader data protection legislation and enforcement in India.
The existing framework’s strength and weaknesses directly impact the effectiveness of any governmental response to a data breach.
Comparison with International Responses to Data Breaches
The Indian government’s response can be compared to those of other countries facing similar incidents. For instance, in the aftermath of major data breaches in the EU, governments have often implemented stringent regulatory measures, coupled with transparent investigations and clear accountability mechanisms. In contrast, some countries with less robust data protection laws may have exhibited a less decisive or transparent response.
The varying approaches highlight the importance of strong data protection legislation and effective enforcement mechanisms in ensuring an adequate governmental response to data breaches. A comparative analysis of different governmental responses across nations could provide valuable insights into best practices and areas for improvement in India.
Timeline of Events
A detailed timeline of events surrounding the ICMR data breach and the subsequent governmental response is difficult to construct due to the lack of publicly available information. However, a general Artikel can be created based on available reports:
- [Date of initial breach report]: Initial reports of the Aadhaar data breach emerge in the media.
- [Date of government statement]: The Indian government releases a statement acknowledging the incident and initiating investigations.
- [Ongoing]: Investigations are underway. Specific details remain largely undisclosed.
Technical Aspects of the Breach
The alleged ICMR Aadhaar data breach raises critical questions about the technical vulnerabilities within their systems and the adequacy of their security measures. Understanding the potential methods employed by the attackers and the preventative measures that could have been implemented is crucial for preventing future incidents. This section delves into the technical aspects of the breach, analyzing potential attack vectors and highlighting necessary security improvements.
The scale of the reported breach suggests a sophisticated attack, likely involving multiple stages. While the exact methods remain unclear without official investigation reports, we can speculate on plausible scenarios based on common attack vectors and vulnerabilities frequently exploited in similar incidents.
Potential Breach Methods and Exploited Vulnerabilities
Several methods could have been used to breach the ICMR’s systems. These range from simple phishing attacks targeting employees to more complex exploits leveraging known vulnerabilities in software or hardware. The lack of transparency surrounding the incident makes pinpointing the exact method difficult, but analyzing common attack vectors provides valuable insight.
A likely scenario involves exploiting vulnerabilities in web applications or databases. Outdated software, weak passwords, or insufficient input validation can all create entry points for attackers. For example, a SQL injection attack could allow an attacker to directly query the database and extract sensitive data. Similarly, a cross-site scripting (XSS) vulnerability could allow an attacker to inject malicious code into a web application, potentially stealing session cookies or other sensitive information.
Furthermore, a compromised employee’s credentials could provide direct access to the system.
Preventive Security Measures
Robust security measures are essential to prevent such breaches. A multi-layered approach is necessary, combining technical controls with strong security policies and employee training.
Several key technical security measures could have significantly mitigated the risk. These include:
- Regular Security Audits and Penetration Testing: Independent security assessments can identify vulnerabilities before attackers exploit them. This includes both automated vulnerability scans and manual penetration testing by security experts.
- Strong Access Control and Authentication: Implementing multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access. Strong password policies and regular password changes are also crucial.
- Data Encryption: Encrypting data both at rest and in transit protects it even if the database is compromised. This ensures that even if attackers gain access, they cannot read the sensitive information.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic and system activity for malicious behavior, alerting administrators to potential threats in real-time. They can block attacks and provide valuable logs for incident response.
- Regular Software Updates and Patching: Keeping software up-to-date is crucial to address known vulnerabilities. Regular patching prevents attackers from exploiting known weaknesses in the system.
- Database Security Measures: Implementing database security best practices, including proper access control, auditing, and encryption, is vital. This includes restricting access to sensitive data based on the principle of least privilege.
Comparison with Industry Best Practices
Comparing the ICMR’s security protocols (assuming the information released by the investigation) with industry best practices reveals potential discrepancies. Many organizations, particularly those handling sensitive personal data, adhere to stringent security standards like ISO 27001 or NIST Cybersecurity Framework. A thorough investigation would be needed to determine whether the ICMR met these standards. The scale of the alleged breach suggests a significant gap between their security posture and industry best practices.
This could include inadequate investment in security infrastructure, insufficient staff training, or a lack of a comprehensive security policy.
Hypothetical Attack Scenario
Let’s consider a hypothetical scenario illustrating how an attacker might have gained access:
This example highlights a possible attack path. The actual attack might have involved different techniques or exploited different vulnerabilities.
- Phishing Attack: The attacker sends a phishing email to an ICMR employee, masquerading as a legitimate request. The email contains a malicious link or attachment.
- Malware Infection: The employee clicks the link or opens the attachment, infecting their computer with malware.
- Credential Theft: The malware steals the employee’s login credentials, providing the attacker with access to the ICMR’s network.
- Database Access: The attacker uses the stolen credentials to access the database containing Aadhaar data.
- Data Exfiltration: The attacker downloads the Aadhaar data and exfiltrates it from the network.
Public Awareness and Prevention
The ICMR data breach highlighted a critical gap: insufficient public awareness regarding the risks associated with Aadhaar data breaches and online security in general. While the Indian government promotes digital literacy, the understanding of the real-world consequences of data breaches, especially concerning sensitive personal information like Aadhaar details, remains limited among a significant portion of the population. Greater public education is urgently needed to empower individuals to protect themselves and mitigate the potential damage from such incidents.The lack of awareness translates into vulnerable individuals who may unknowingly fall prey to identity theft, financial fraud, and other serious crimes.
Improving public understanding requires a multi-pronged approach, encompassing proactive education campaigns, accessible resources, and clear, concise information. This will not only help prevent future breaches but also equip citizens with the tools to respond effectively should a breach occur.
Public Awareness Levels and the Need for Education
Surveys and reports consistently indicate a low level of awareness among the general public regarding the risks associated with Aadhaar data breaches and online security. Many individuals are unaware of the potential consequences of having their personal information compromised, such as identity theft, financial fraud, and social engineering attacks. This lack of awareness is further compounded by a lack of understanding of the technical aspects of data security and the various methods used by cybercriminals.
Effective public education campaigns are crucial to bridge this knowledge gap and empower individuals to take proactive measures to protect their data. These campaigns should utilize various media channels, including television, radio, print media, and social media, to reach a wider audience. Furthermore, educational materials should be available in multiple languages to ensure accessibility for all citizens.
Protecting Yourself After a Data Breach, India witnesses biggest data breach of aadhaar details via icmr
Following a data breach, individuals should take immediate steps to mitigate potential risks. This includes monitoring bank accounts and credit reports for any unauthorized activity, changing passwords for online accounts, and reporting any suspicious activity to the appropriate authorities. Individuals should also be vigilant about phishing emails and suspicious phone calls, as cybercriminals often attempt to exploit data breaches to gain access to additional personal information.
Consider placing a fraud alert or security freeze on your credit reports to prevent the opening of new accounts in your name. Regularly reviewing your bank statements and credit reports for any unusual activity is crucial. If you suspect any fraudulent activity, contact your bank and the relevant credit bureaus immediately.
Public Service Announcements
The following public service announcements can help raise awareness about data security:
- Protect Your Aadhaar: Never share your Aadhaar number unnecessarily. Only provide it to trusted sources and verify their authenticity.
- Strong Passwords Matter: Use strong, unique passwords for all your online accounts. Avoid using easily guessable information.
- Beware of Phishing: Be cautious of suspicious emails, messages, and phone calls requesting personal information.
- Update Software: Regularly update your software and applications to patch security vulnerabilities.
- Use Two-Factor Authentication: Enable two-factor authentication wherever possible to add an extra layer of security.
- Secure Your Devices: Protect your computers, smartphones, and tablets with strong passwords and antivirus software.
- Report Suspicious Activity: Report any suspicious activity to the appropriate authorities immediately.
Infographic: Understanding Online Threats
The infographic would visually represent common online threats using easily understandable icons and short descriptions. One section would depict phishing scams, illustrating an email with suspicious links or attachments. Another section would showcase malware attacks, portraying a virus infecting a computer. A third section would illustrate ransomware attacks, showing a locked computer screen demanding a ransom. A fourth section would depict identity theft, showing a person’s identity being stolen and used fraudulently.
Finally, the infographic would offer practical advice for each threat, such as avoiding suspicious links, using antivirus software, backing up data regularly, and being cautious about sharing personal information online. The color scheme would be bright and attention-grabbing, with clear headings and concise text to ensure easy comprehension. The overall design would be clean and visually appealing, making it easily shareable across social media platforms.
Final Review
The alleged ICMR data breach serves as a stark reminder of the critical need for robust data security protocols and a proactive approach to protecting sensitive personal information. The scale of this potential breach underscores the vulnerabilities within even established institutions and highlights the urgent need for improved data protection measures across all sectors. While investigations continue, the incident emphasizes the importance of individual vigilance and collective responsibility in safeguarding our digital identities.
It’s a wake-up call that demands a comprehensive overhaul of data security practices and a renewed focus on public education and awareness.
Question & Answer Hub
What specific types of Aadhaar data were allegedly leaked?
Reports suggest a range of data, including biometric information (fingerprints, iris scans), Aadhaar numbers, addresses, and potentially other personally identifiable information. The exact details are still emerging from investigations.
What is the ICMR’s role in this alleged breach?
The ICMR was allegedly the source of the leaked data, suggesting a vulnerability within their systems or databases. The exact nature of the vulnerability and how it was exploited is still under investigation.
What steps can individuals take to protect themselves after a data breach?
Monitor bank accounts and credit reports closely for any unauthorized activity. Consider placing a fraud alert or security freeze on your credit reports. Be wary of suspicious emails or phone calls requesting personal information. Change passwords regularly for all online accounts.
What are the potential long-term consequences of this breach?
Long-term consequences could include identity theft, financial fraud, reputational damage, and difficulty accessing services requiring Aadhaar verification. The full impact may not be apparent for some time.





