Insider Risk Unconventional Thoughts & Lessons Learned
Insider risk unconventional thoughts and lessons learned – Insider risk: unconventional thoughts and lessons learned. This exploration delves into the surprising and often overlooked aspects of insider threats, moving beyond the typical employee theft scenarios. We’ll examine emerging trends, the role of social engineering, and the evolving technological landscape impacting these risks. Learning from past incidents and implementing proactive mitigation strategies are crucial to securing organizations in this ever-changing threat environment.
This blog post unpacks the complexities of insider risk, going beyond the surface-level concerns. We’ll examine the difference between conventional and unconventional insider threats, highlighting the unique challenges posed by emerging trends and the psychological factors driving these behaviors. Practical strategies for prevention, detection, and response will be discussed, along with the importance of a proactive security culture. The future of insider risk will also be considered, discussing the role of AI and machine learning in mitigating these threats.
Defining Insider Risk
Insider risk, a significant threat to organizations, encompasses various forms of malicious or negligent actions by individuals with authorized access. It’s not solely about theft; it encompasses a spectrum of behaviors, from deliberate sabotage to accidental data breaches. Understanding the nuances of insider risk, both conventional and unconventional, is crucial for robust security measures.
Defining Insider Risk: A Comprehensive Overview
Insider risk is the potential for harm to an organization caused by an individual with legitimate access to sensitive information or resources. This encompasses a broad range of actions, from unauthorized data access and disclosure to sabotage and theft of physical assets. The risk isn’t limited to malicious intent; it also includes unintentional errors, negligence, and compliance failures.
Insider threats can be categorized as deliberate or unintentional, based on the actor’s motivation.
Conventional vs. Unconventional Insider Risks
Conventional insider risks typically involve theft of assets, unauthorized data access, or sabotage. These are often driven by financial gain, personal vendettas, or dissatisfaction. Unconventional insider risks, however, represent a wider range of behaviors. They may not be motivated by financial gain but by factors like ideological disagreements, or even a desire to expose vulnerabilities. The motivations behind unconventional insider risks are often less tangible and more complex to predict.
Identifying Potential Vulnerabilities
Identifying vulnerabilities related to insider risk requires a multi-faceted approach. Organizations must assess access controls, employee training programs, and reporting mechanisms. Regular security audits, coupled with employee awareness campaigns, are essential for proactive risk mitigation. Scrutinizing access privileges and implementing robust authentication protocols are key elements in this process. A critical component is developing clear policies regarding acceptable use of company resources.
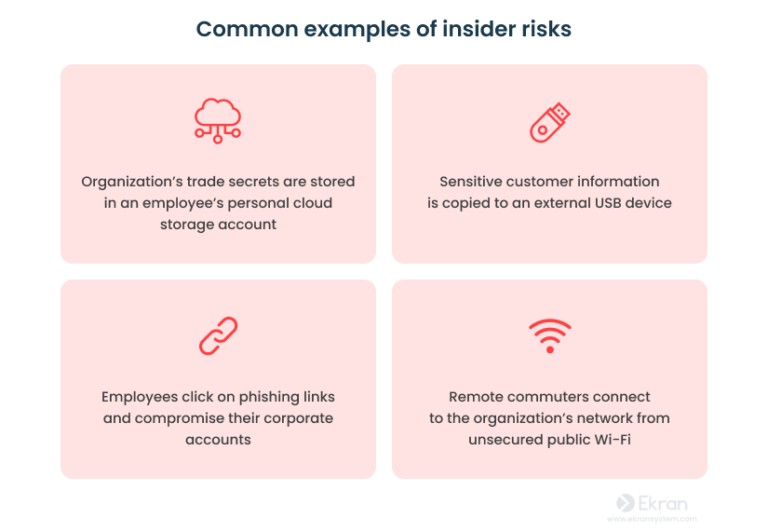
Examples of Unconventional Insider Threats
Unconventional insider threats extend beyond the typical employee theft scenarios. These include disgruntled employees seeking to expose sensitive data or disrupt operations as a form of protest. Another example is a disgruntled employee who seeks to expose the organization’s vulnerabilities to a competitor or other external parties. Also, employees who may have been subject to manipulation by outside actors or groups with ideological agendas could also pose a risk.
Such actions are often motivated by factors beyond immediate financial gain, making them harder to detect.
Characteristics and Impact of Insider Risk Categories
| Insider Risk Category | Common Characteristics | Potential Impact |
|---|---|---|
| Financial Gain | Theft of assets, fraudulent activities, data breaches for resale | Financial losses, reputational damage, legal consequences |
| Malicious Intent | Sabotage, data destruction, unauthorized disclosure | Operational disruption, severe financial losses, legal ramifications |
| Ideological Motivations | Data leak to expose organizational shortcomings, internal espionage | Reputational damage, loss of trust, potential legal liabilities |
| Unintentional Errors | Accidental data breaches, security lapses, system errors | Data breaches, operational disruptions, minor financial losses |
| Negligence | Failure to follow security protocols, inadequate oversight | Compromised security posture, operational vulnerabilities, data breaches |
Unconventional Thoughts on Insider Risk

Insider risk, traditionally focused on disgruntled employees, is evolving rapidly. Modern threats leverage sophisticated techniques and emerging technologies, demanding a nuanced understanding beyond the conventional models. This shift necessitates a proactive approach that anticipates and addresses the unconventional methods employed by malicious actors. The lines between internal and external threats are blurring, creating a complex and ever-changing landscape for security professionals.The conventional understanding of insider threats often centers on disgruntled employees or those motivated by financial gain.
However, unconventional insider risk involves a broader range of actors and motivations. These threats can be leveraged by external actors seeking to exploit vulnerabilities within an organization, often with minimal direct contact.
Emerging Trends and Patterns in Insider Risk Behavior
Insider risk behavior is becoming increasingly sophisticated. Gone are the days of simple theft; modern threats involve data exfiltration, sabotage, and even the manipulation of internal processes. Patterns are emerging, showing a shift from impulsive actions to more calculated and strategic activities, often leveraging social engineering and technological tools. These patterns are difficult to detect without proactive monitoring and advanced threat intelligence.
Social Engineering and Manipulation in Insider Threats
Social engineering techniques are playing a crucial role in unconventional insider threats. Attackers exploit human psychology to manipulate insiders into performing actions that compromise security. This includes phishing, pretexting, and quid pro quo exchanges. Sophisticated social engineering campaigns can target multiple individuals within an organization, creating a cascade of vulnerabilities. For instance, an attacker might use social engineering to gain access to a network administrator’s credentials, enabling them to deploy malware or exfiltrate sensitive data.
External Actors Exploiting Insider Vulnerabilities
External actors are increasingly leveraging insider vulnerabilities to achieve their objectives. This can involve infiltrating organizations by manipulating individuals through social engineering or exploiting weaknesses in security protocols. For example, an external actor might gain access to an employee’s credentials through a phishing attack and use that access to steal sensitive data. These tactics highlight the interconnectedness of internal and external threats.
External actors can use the insider as a tool for their own malicious goals.
Technological Advancements Changing the Landscape of Insider Risk
Technological advancements are transforming the insider risk landscape. Cloud computing, remote work, and the proliferation of mobile devices create new avenues for data breaches and attacks. The increasing reliance on automation and AI presents new attack vectors. Cybercriminals can leverage these technologies to gain access to sensitive data or manipulate internal processes. Remote access vulnerabilities and unsecured mobile devices are prime targets for attackers seeking to exploit insiders.
Psychology Behind Conventional and Unconventional Insider Threats
Conventional insider threats are often driven by personal motivations, such as financial gain or revenge. Unconventional threats, however, are often driven by broader organizational or political objectives, such as espionage or sabotage. The psychology behind these threats varies significantly, requiring different detection and mitigation strategies. The motivations behind unconventional threats are often more complex and strategic, making them harder to predict and counter.
Unconventional insider risk thinking often reveals surprising vulnerabilities. One key lesson? Protecting code from malicious insiders requires more than just traditional security measures. For example, consider the need for “AI code safety goggles,” as highlighted in Deploying AI Code Safety Goggles Needed. This proactive approach to identifying potential risks, even those hidden within seemingly benign code changes, is crucial for a robust security strategy.
Ultimately, understanding these unconventional insights is critical to mitigating insider risk.
Comparison of Strategies for Addressing Conventional and Unconventional Insider Threats
| Characteristic | Conventional Insider Threats | Unconventional Insider Threats |
|---|---|---|
| Motivation | Personal gain, revenge, dissatisfaction | Organizational objectives, espionage, sabotage |
| Detection | Behavioral anomalies, financial irregularities | Advanced threat intelligence, suspicious network activity |
| Mitigation | Strong access controls, background checks | Multi-factor authentication, security awareness training, incident response plans |
| Prevention | Employee screening, clear policies | Continuous monitoring, proactive threat hunting |
Lessons Learned from Insider Risk Incidents
Insider threats, particularly those stemming from unconventional motivations, pose a significant challenge to organizations. These threats often go undetected until significant damage is done, highlighting the critical need for proactive measures and a deep understanding of the nuances of human behavior. This section delves into key takeaways from past incidents, examining common mistakes, successful mitigations, and the crucial role of a robust security culture in preventing such risks.Understanding the motivations behind unconventional insider threats is essential to effective prevention.
These motivations can range from personal vendettas to financial gain, or even a desire for recognition or attention. Identifying these triggers and creating a security culture that addresses the underlying issues is vital to mitigating the risk.
Key Takeaways from Past Insider Risk Incidents, Insider risk unconventional thoughts and lessons learned
Past incidents involving unconventional insider threats reveal several critical takeaways. A common thread is the failure to recognize subtle indicators of potential insider threats. Organizations often focus on overt malicious intent, overlooking the more nuanced and less obvious signs of discontent or frustration that could lead to malicious actions.
Common Mistakes in Preventing and Responding to Unconventional Insider Risks
Several common mistakes hinder effective prevention and response to unconventional insider risks. One significant mistake is neglecting the importance of employee well-being and engagement. A lack of communication, recognition, or opportunities for professional growth can create resentment and frustration, which can be exploited by malicious actors. Another common pitfall is inadequate background checks and due diligence processes.
Organizations may not fully investigate an individual’s past or personal connections, potentially missing crucial information about their potential for malicious behavior.
Examples of Successful Mitigation of Unconventional Insider Risks
Organizations have successfully mitigated unconventional insider risks through various strategies. One example is fostering a culture of open communication and feedback. Encouraging employees to report concerns without fear of retribution can provide early warning signals of potential threats. Implementing regular security awareness training and simulations can help employees identify and report suspicious activities.
Importance of a Robust Security Culture in Preventing Unconventional Insider Threats
A robust security culture plays a pivotal role in preventing unconventional insider threats. It establishes a clear framework for acceptable behavior, promotes ethical conduct, and instills a sense of shared responsibility for security. This culture needs to be consistently reinforced through training, communication, and visible leadership commitment.
Case Studies Demonstrating the Consequences of Ignoring Unconventional Insider Risk Factors
Several case studies illustrate the devastating consequences of ignoring unconventional insider risk factors. One example involves an employee who felt undervalued and retaliated by stealing sensitive data. Another involves an employee seeking recognition, who sabotaged company projects to gain attention. These instances highlight the need to address the underlying issues driving insider threats.
Thinking outside the box about insider risk is crucial, and recent events like the Azure Cosmos DB Vulnerability Details highlight just how important it is to consider the unexpected. Learning from this vulnerability, and others, reveals that insiders can exploit seemingly minor weaknesses, making security robust and proactive is vital. This underscores the importance of ongoing vigilance and a focus on unconventional threat vectors in mitigating insider risk.
Azure Cosmos DB Vulnerability Details showcases the potential for seemingly innocuous flaws to have significant repercussions. This reinforces the need to develop a culture of security awareness and to consider insider risk from novel perspectives.
Best Practices for Fostering a Strong Security Culture
Establishing a strong security culture that discourages unconventional insider threats requires a multi-faceted approach. Key best practices include:
- Implementing robust background checks and due diligence processes to identify potential vulnerabilities.
- Encouraging open communication and feedback channels for employees to report concerns without fear of reprisal.
- Providing opportunities for professional development and career advancement to reduce employee dissatisfaction.
- Conducting regular security awareness training and simulations to educate employees about potential threats and how to respond.
- Promoting a culture of ethical conduct and transparency throughout the organization.
Learning from Past Incidents to Improve Future Risk Management
Learning from past insider risk incidents is crucial for improving future risk management. This involves a thorough post-incident analysis to identify the root causes of the incident. Organizations should document lessons learned, implement corrective actions, and share the findings with relevant stakeholders. A key element of this process is fostering a culture of continuous improvement in security practices.
Mitigating Unconventional Insider Risk
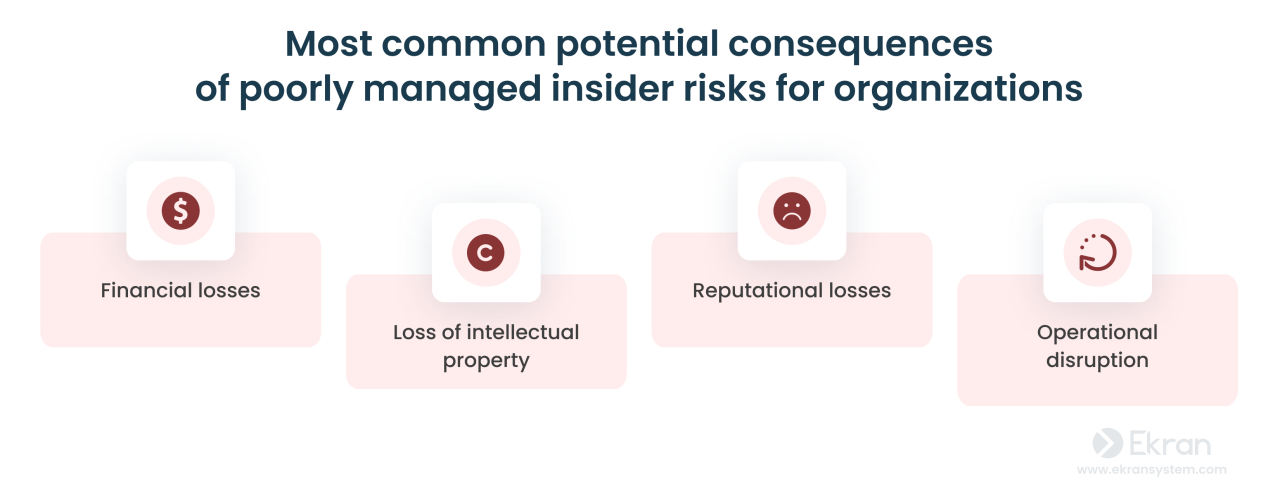
Insider threats, especially the unconventional ones, are a significant concern for organizations. While traditional insider threats often involve malicious intent, unconventional threats arise from negligence, errors in judgment, or even unwitting actions. These threats can be just as damaging, and often more difficult to detect, requiring a multifaceted approach to prevention and mitigation.Unconventional insider risks demand a shift in perspective, moving beyond the typical focus on malicious actors.
We need to consider the human element, the potential for errors, and the need for robust systems and processes that can identify and prevent both deliberate and accidental breaches. This requires a proactive, preventative, and highly adaptable approach to security.
Practical Strategies for Prevention and Detection
A comprehensive approach to mitigating unconventional insider risks involves several practical strategies. These strategies focus on building a culture of security awareness, implementing strong access controls, and establishing robust monitoring systems. The goal is to not only prevent unauthorized access but also to identify suspicious activities in a timely manner.
- Implementing robust access controls is crucial. This includes using multi-factor authentication, role-based access control, and regular access reviews. These measures limit the potential damage from unintentional or negligent actions by restricting access to sensitive information and systems to only those who need it.
- Establishing comprehensive monitoring systems is essential. These systems should track user activity, including file access, data transfers, and system logs. The system should be configured to alert security personnel to unusual or suspicious activity patterns.
- Regular security awareness training is paramount. Training programs should cover a range of topics, including phishing awareness, password security, data handling procedures, and reporting suspicious activities. Training should be tailored to different job roles and responsibilities, ensuring that employees understand the specific risks they face.
Employee Training and Awareness Programs
Effective employee training programs are vital in mitigating unconventional insider risks. They create a culture of security consciousness, empowering employees to identify and report potential threats.
- Establish a clear training program structure. The program should be comprehensive, covering a range of topics from general security principles to specific risks relevant to individual roles.
- Implement regular training sessions. Training should be conducted regularly to reinforce knowledge and address evolving threats. This could involve online modules, workshops, or interactive sessions.
- Tailor training to specific roles. Different job roles face different security risks. Tailoring training to those roles ensures employees understand the risks specific to their responsibilities.
- Include practical exercises. Simulating phishing attacks, data breaches, or other security scenarios allows employees to practice their response skills and identify vulnerabilities in their own behavior.
- Make training engaging and memorable. Using interactive elements, real-world examples, and gamification can enhance employee engagement and improve retention of security information.
Security Tools and Technologies
Various tools and technologies can assist in detecting and responding to unconventional insider threats. Choosing the right tools depends on the specific needs and resources of an organization.
| Security Tool | Role in Detecting Insider Risks |
|---|---|
| Intrusion Detection Systems (IDS) | Monitor network traffic for malicious activity and potential insider threats. |
| Security Information and Event Management (SIEM) systems | Collect and analyze security logs from various sources, identifying suspicious patterns and anomalies. |
| Data Loss Prevention (DLP) tools | Monitor data movement and prevent sensitive data from leaving the organization’s control. |
| User and Entity Behavior Analytics (UEBA) | Identify unusual user behaviors that might indicate malicious or negligent insider activity. |
| Endpoint Detection and Response (EDR) tools | Monitor and protect endpoints such as computers and mobile devices, detecting malicious activities and potential insider threats. |
The Future of Insider Risk
The landscape of insider threats is constantly evolving, driven by technological advancements, changing work dynamics, and the increasing sophistication of malicious actors. Predicting the future of insider risk requires a nuanced understanding of these factors and how they intertwine. This necessitates a proactive and adaptive approach to security, moving beyond reactive measures to address the evolving nature of these threats.The future of insider risk management will be defined not just by the threats themselves, but by our ability to anticipate them, understand their motivations, and deploy effective countermeasures.
This proactive approach demands a deep understanding of emerging technologies, changing work environments, and the human element of insider risk.
Potential Future Trends in Unconventional Insider Threats
The evolution of work environments, with increased remote work and the adoption of cloud technologies, creates new avenues for malicious insider activity. The blurring lines between personal and professional use of devices, combined with the rise of social engineering tactics, presents significant vulnerabilities. Additionally, the growing use of artificial intelligence (AI) and machine learning (ML) in businesses opens up the possibility of insider threats leveraging these tools for malicious purposes.
Thinking outside the box about insider risk has been a fascinating journey. Recent developments, like the Department of Justice’s new safe harbor policy for Massachusetts transactions, highlighted here , offer valuable lessons for navigating complex legal landscapes. Understanding how these policies can influence insider risk management is crucial for any organization dealing with sensitive information.
For example, an insider with access to an AI-powered system could potentially manipulate data or deploy sophisticated attacks to compromise the system.
The Evolving Role of AI and Machine Learning in Detecting Insider Risk
AI and machine learning technologies are becoming increasingly sophisticated in detecting anomalies and patterns indicative of insider threats. These tools can analyze vast datasets of user activity, network traffic, and system logs to identify suspicious behavior. Sophisticated algorithms can analyze data for patterns that may indicate malicious intent, such as unusual data access requests, unauthorized data exfiltration attempts, or unusual login patterns.
For instance, an ML model could identify a user consistently accessing sensitive files at unusual hours or in ways that deviate from their established patterns, raising a red flag for further investigation.
Importance of Proactive Risk Assessment Strategies
Proactive risk assessment strategies are critical for mitigating future insider threats. These strategies involve identifying vulnerabilities, assessing potential threats, and developing mitigation plans. This includes identifying critical assets and assessing the likelihood and impact of various threats to those assets. By employing a comprehensive approach, organizations can proactively address potential risks before they materialize into incidents. For instance, a company might assess the risk of a disgruntled employee accessing and exfiltrating sensitive customer data, and develop protocols to monitor such activities and mitigate the risk.
Leveraging Emerging Technologies to Bolster Insider Threat Defenses
Emerging technologies, such as blockchain, biometrics, and zero-trust architectures, can bolster insider threat defenses. Blockchain technology can enhance data integrity and transparency, making it more difficult for insiders to tamper with sensitive information. Biometric authentication methods can enhance access controls, reducing the risk of unauthorized access. Implementing a zero-trust architecture can limit access to sensitive resources based on the principle of “never trust, always verify,” which is particularly useful in preventing insider threats.
For instance, a company might use blockchain to secure financial transactions, ensuring the integrity of financial records and making it harder for an insider to manipulate the data.
Fostering a Proactive Security Posture
A proactive security posture involves a commitment to continuous improvement and adaptation. Organizations must embrace a culture of security awareness, training employees on identifying and reporting suspicious activities, and promoting a strong security ethos. This requires continuous monitoring, analysis, and improvement of security controls to address evolving threats. For example, regular security awareness training sessions can equip employees with the knowledge and skills to recognize and report potential insider threats.
Need for a Dynamic Security Approach
A dynamic security approach is essential for addressing the ever-changing landscape of unconventional insider threats. Organizations must be prepared to adapt their security strategies in response to new threats and vulnerabilities. This includes staying informed about emerging trends in insider threats and adapting security controls accordingly. For instance, a company that experiences a significant shift in its work model (e.g., moving to a fully remote environment) should re-evaluate its security posture and adapt controls to the new paradigm.
Integrating External Threat Intelligence into Insider Risk Management
Integrating external threat intelligence into insider risk management is crucial for staying ahead of emerging threats. This involves monitoring external sources for information on emerging threats, vulnerabilities, and malicious actors. By analyzing this intelligence, organizations can identify potential insider threats and tailor their security measures accordingly. For example, if a news report reveals a new phishing campaign targeting specific industries, an organization can incorporate this information into its security training and awareness programs, and adapt security controls to mitigate the risk of insider compromise.
Ultimate Conclusion: Insider Risk Unconventional Thoughts And Lessons Learned
In conclusion, understanding and addressing unconventional insider risk requires a multifaceted approach. This blog post has highlighted the importance of moving beyond conventional thinking to proactively anticipate and mitigate emerging threats. By combining robust security measures with a strong security culture, organizations can significantly reduce the impact of insider risks. Ultimately, the future of insider risk management hinges on a dynamic and adaptable approach that learns from the past, adapts to the present, and proactively anticipates future challenges.
Popular Questions
What are some examples of unconventional insider threats?
Unconventional insider threats can include disgruntled employees using their access to sabotage systems, or external actors exploiting vulnerabilities through social engineering tactics. These threats go beyond the typical theft of physical assets and target information or intellectual property. They might involve leaking confidential data, manipulating systems for financial gain, or even disrupting operations.
How can organizations differentiate between conventional and unconventional insider threats?
Conventional insider threats often involve direct financial gain, whereas unconventional threats may stem from motives like revenge, sabotage, or ideological opposition. Recognizing the nuanced motivations behind insider actions is crucial for developing effective mitigation strategies.
What is the role of social engineering in unconventional insider threats?
Social engineering plays a significant role in manipulating individuals to reveal sensitive information or perform actions that compromise security. This can involve exploiting human psychology and trust to gain access to systems or data.
What are some best practices for fostering a strong security culture?
Fostering a strong security culture involves creating a climate where employees feel comfortable reporting suspicious activities without fear of retaliation. Open communication channels, clear policies, and consistent training are essential.





