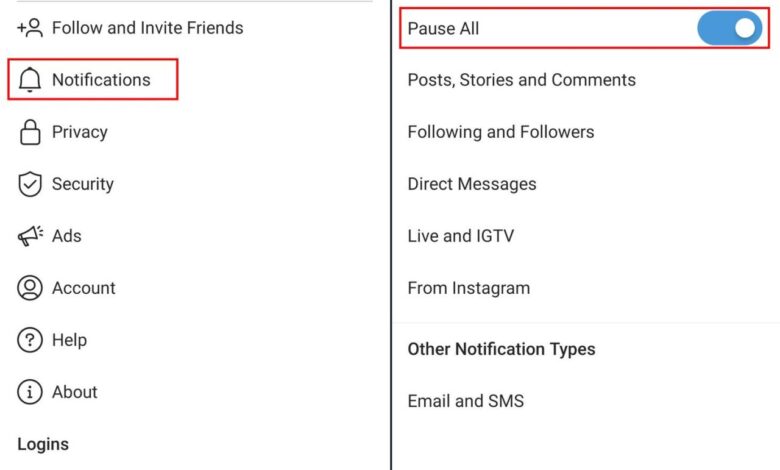
Instagram to Enhance Security of its Users
Instagram to enhance security of its users is a crucial step toward building trust and confidence among its user base. This involves a multi-faceted approach, encompassing account verification, data protection, content moderation, and safeguarding against phishing attempts. The platform must prioritize user convenience and security in equal measure to achieve a robust system.
The article explores several key areas for improving Instagram’s security posture, ranging from user account verification methods to comprehensive data protection strategies. We’ll examine how Instagram can strengthen its security measures without sacrificing the user experience.
User Account Security Enhancements
Instagram’s commitment to user safety is paramount. This focus extends beyond basic logins to encompass a multi-layered approach to verifying identities and protecting accounts from unauthorized access. This detailed look into enhanced security features will provide a comprehensive understanding of the measures being implemented to safeguard user data and accounts.Modern social media platforms must proactively address evolving cyber threats.
Implementing robust security protocols is crucial for maintaining user trust and preventing account compromise. The measures Artikeld below illustrate Instagram’s commitment to building a secure and trustworthy environment for its users.
Multi-Factor Authentication Methods
Multi-factor authentication (MFA) significantly strengthens account security by requiring more than one verification method. This adds a crucial layer of defense, making it substantially harder for attackers to gain access even if they obtain a password. By requiring additional verification steps, MFA mitigates the risk of unauthorized access.
Instagram’s recent push to bolster user security is commendable, but it’s crucial to understand the broader context of data vulnerabilities. For example, recent discoveries regarding the security of Azure Cosmos DB, as detailed in Azure Cosmos DB Vulnerability Details , highlight the need for robust security measures across all platforms. This underscores the importance of Instagram taking proactive steps to ensure their systems are as secure as possible against potential exploits, a key factor in maintaining user trust.
- Time-Based One-Time Passwords (TOTP): Users receive a unique, temporary code via a dedicated authenticator app (like Google Authenticator) or SMS. This code is valid for a short period, enhancing security by preventing attackers from using a stolen password effectively.
- Email Verification: Sending a verification code to a registered email address provides an additional layer of security, especially if the password is compromised. This step requires a user to have a valid and secure email address.
- Security Keys: These physical devices act as a second form of authentication. Users plug the key into their computer or phone to verify their identity. This method offers a high level of security as the physical key is a tangible security factor.
Account Recovery Procedures
Robust account recovery procedures are essential in case of unauthorized access. User-friendly and secure recovery options allow users to regain control of their accounts quickly and easily.
- Security Questions and Answers: A set of pre-defined questions and answers acts as a checkpoint to verify user identity. These questions should be unique and challenging to guess, making it harder for attackers to bypass this step.
- Backup Email Addresses: Having a backup email address is crucial for account recovery. Users can receive recovery codes or instructions to regain access to their account.
- Phone Verification: A registered phone number facilitates account recovery via SMS verification codes, offering a flexible and secure method.
Password Complexity and Change Requirements
Password complexity and change requirements are fundamental security elements. These procedures minimize the risk of weak passwords being used and facilitate proactive security measures.
- Password Strength Guidelines: Strong passwords should meet specific criteria, such as length (at least 12 characters), including a mix of uppercase and lowercase letters, numbers, and symbols. This approach makes passwords harder to crack.
- Password Change Frequency: Regular password changes are crucial. Implementing a schedule or prompts to update passwords periodically helps mitigate the impact of compromised credentials.
- Password Reset Mechanisms: A secure and reliable method for resetting passwords is vital for account recovery. This method should employ robust security protocols to prevent unauthorized password resets.
Password Management Tool Comparison
Integrating password management tools can significantly enhance user security. Different tools offer various features and benefits.
| Password Manager | Features | Pros | Cons |
|---|---|---|---|
| LastPass | Strong password generation, secure vault, browser extensions | Widely used, strong encryption | Subscription-based, potential for single point of failure |
| 1Password | Robust security features, strong encryption, cross-platform | Highly secure, strong user interface | Subscription-based, steep learning curve for some users |
| Bitwarden | Open-source, strong encryption, free and paid versions | Open-source, highly secure | Less user-friendly than others, less brand recognition |
Data Protection and Privacy
Instagram’s commitment to user security extends beyond account access. A crucial aspect of a strong platform is the safeguarding of user data and the respect for individual privacy. This necessitates robust encryption, transparent policies, and user-centric control over personal information. Data breaches have significant consequences, impacting not only individuals but also the platform’s reputation. A proactive approach to data protection builds trust and fosters a safer environment for all users.Effective data protection strategies are paramount to maintaining user confidence and avoiding reputational damage.
Robust security measures, coupled with transparent communication, are key elements in building a reliable and trustworthy platform. By prioritizing data privacy, Instagram can strengthen its position as a leader in social media and demonstrate its commitment to user well-being.
Data Encryption Strategies
Data encryption is a fundamental security measure for protecting user information. Various encryption methods are employed, such as symmetric-key and asymmetric-key cryptography. Symmetric-key encryption uses the same key for encryption and decryption, while asymmetric-key encryption employs separate keys for these processes. Choosing the appropriate encryption method depends on the sensitivity of the data and the desired level of security.
Modern encryption standards like AES (Advanced Encryption Standard) are widely used for their robust security.
Privacy Settings for Enhanced User Control
Providing users with granular control over their data is essential for enhancing privacy. Instagram can offer a range of privacy settings, allowing users to customize their profiles and data visibility. For example, users could control which information is visible to other users, such as their location, posts, and friend lists. Additionally, features allowing users to limit the sharing of data with third-party apps or services would empower users and enhance privacy.
This level of control fosters a sense of security and empowers users to manage their online presence effectively.
Limiting Data Collection and Usage
Minimizing data collection is crucial for protecting user privacy. Instagram should identify and eliminate unnecessary data points. Only collect data that is directly relevant to the platform’s services and user experience. This approach not only reduces the risk of breaches but also ensures users are aware of how their data is being utilized. A clear data policy outlining data collection and usage practices, along with transparent communication with users, is vital.
Users should have the ability to opt out of certain data collection practices.
Potential Vulnerabilities in Data Handling Processes
Potential vulnerabilities in data handling processes could stem from inadequate security protocols, weak encryption, or insufficient data access controls. A thorough risk assessment, identifying and addressing potential security loopholes, is essential to protect user data. Regular security audits and penetration testing can help uncover weaknesses and proactively address vulnerabilities before they are exploited. User data should be regularly reviewed and purged to maintain compliance with privacy regulations and minimize potential risks.
Transparent Data Policies and User Consent Mechanisms
Clear and concise data policies are vital for building user trust. These policies should explicitly Artikel how user data is collected, used, and protected. Obtaining explicit user consent for data collection practices is essential to uphold user autonomy. Users should have a clear understanding of the data they are sharing and the purposes for which it is being used.
Transparent data policies and consent mechanisms create a transparent and secure environment for users.
Content Moderation and Safety: Instagram To Enhance Security Of Its Users
Protecting users from harmful content is paramount for a safe and positive online experience. A robust content moderation system is essential to maintain a healthy community and prevent the spread of hate speech, harassment, and other forms of online abuse. This involves proactive detection, swift responses, and clear guidelines to empower users and create a space where everyone feels safe.A comprehensive content moderation strategy necessitates a multi-faceted approach that goes beyond simply removing harmful content.
It should encompass proactive measures to prevent such content from appearing in the first place, as well as robust reporting mechanisms and clear community guidelines. A balanced system is required that allows for the free exchange of ideas while maintaining a safe and respectful environment.
Framework for Detecting and Removing Harmful Content
Effective content moderation requires a sophisticated framework capable of identifying and removing harmful content quickly and accurately. This framework must be adaptable to emerging threats and evolving language, employing a combination of automated tools and human review. It should be designed to identify not just explicit hate speech, but also the subtle nuances and coded language often used to mask harmful intent.
System for Reporting Suspicious Activities
A user-friendly reporting system is crucial for fostering a sense of safety and empowerment. Users must feel confident that their reports will be taken seriously and acted upon swiftly. This system should allow users to report a wide range of suspicious activities, including hate speech, harassment, cyberbullying, and the promotion of illegal activities. Clear guidelines on the types of content that can be reported, as well as the process for submitting a report, are vital.
Strategies for Combating Cyberbullying and Online Abuse
Combating cyberbullying and online abuse requires a proactive approach that combines technological solutions with community engagement. Implementing robust content moderation tools to detect and remove abusive content is critical. Additionally, fostering a culture of empathy and respect through educational campaigns and clear community guidelines is vital. This includes promoting positive interactions and encouraging users to report any instances of abuse.
Comparison of Different Approaches to Moderating User-Generated Content
Different approaches to content moderation each have their own strengths and weaknesses. Automated systems can process a large volume of content quickly, but they may struggle with nuanced or evolving forms of harassment. Human moderators can interpret context and intent more effectively, but they can be susceptible to bias and may not be able to scale to handle the sheer volume of content generated online.
A hybrid approach, combining automated tools with human review, often proves most effective, allowing for the rapid detection of obvious violations while ensuring nuanced judgments are made by trained moderators.
User Guidelines and Community Standards
Clear user guidelines and community standards are essential for establishing a shared understanding of acceptable online behavior. These guidelines should clearly define prohibited content, including hate speech, harassment, and cyberbullying. They should also promote respectful interactions and encourage users to report any violations they encounter. The guidelines should be easily accessible and consistently enforced.
- Prohibited Content: This category should explicitly detail examples of hate speech, harassment, and cyberbullying. It’s crucial to define these terms comprehensively to avoid ambiguity.
- Respectful Interactions: Guidelines should emphasize the importance of courteous communication, empathy, and understanding. This should encourage users to approach discussions with consideration for others’ perspectives.
- Reporting Procedures: Clear instructions on how to report violations should be provided, including a simple and intuitive process. Users should understand the actions that will be taken upon reporting.
Protecting Against Phishing and Scams
Instagram’s commitment to user safety extends to proactively combating phishing and scams. These fraudulent activities can lead to significant harm, from the theft of personal information to the spread of malicious content. By implementing robust measures to identify and prevent such threats, Instagram aims to foster a secure and trustworthy platform for all users.
Identifying Suspicious Accounts and Messages
A crucial aspect of combating phishing and scams is the ability to recognize suspicious accounts and messages. This involves developing algorithms and human review processes to flag profiles and interactions that exhibit characteristics indicative of fraudulent activity. Indicators might include unusual profile pictures, inconsistent usernames, or a sudden influx of requests for sensitive information. These characteristics are often present in phishing attempts, designed to trick users into divulging personal details.
Educating Users About Phishing Tactics
User education plays a pivotal role in mitigating the impact of phishing attempts. Instagram can create comprehensive resources to educate users about common phishing tactics and scams. These resources should cover various types of phishing attacks, including those targeting personal information, financial data, and account access. This knowledge empowers users to recognize and avoid traps.
Visual Cues for Recognizing Fraudulent Activities
Recognizing fraudulent activities often relies on visual cues. Instagram can highlight visual indicators, such as suspicious links with shortened URLs or misspellings in messages. These visual cues can be subtle but, when combined with other indicators, can provide a clearer picture of potential fraudulent activity. By making these subtle indicators prominent, users can be more easily alerted to potential risks.
Reporting Phishing Attempts and Scams
Establishing a clear and accessible reporting mechanism is vital for addressing phishing attempts and scams. Users should have straightforward procedures to report suspicious accounts or messages to Instagram. This process should allow for detailed reporting, including screenshots of suspicious activity and any relevant information.
Instagram’s recent push to enhance user security is a smart move, but truly robust protection needs more than just basic measures. Think about how crucial it is to employ advanced tools like those discussed in Deploying AI Code Safety Goggles Needed – AI-powered code analysis can spot vulnerabilities that human eyes might miss. This proactive approach is vital to keep Instagram users safe from increasingly sophisticated threats.
Ultimately, a layered security strategy, incorporating cutting-edge tech, is the best way for Instagram to stay ahead of the curve.
Comparing Instagram Alert Methods for Potential Scams, Instagram to enhance security of its users
| Method | Description | Pros | Cons |
|---|---|---|---|
| Email Alerts | Sends emails about suspicious activity. | Easy to understand, can be reviewed offline. | Can be overwhelming if too many alerts, may not be checked frequently. |
| In-App Notifications | Displays notifications directly in the app. | Immediate action, visible when using the app. | Can be disruptive if too frequent, might be missed if user is not actively using the app. |
| Community Forums | Allows users to share tips and discuss scams. | Community-driven, sharing of real-world experiences, collaborative learning. | Requires moderation to ensure accuracy and avoid spreading misinformation, potential for scams to be discussed within the forum. |
This table provides a concise comparison of different alert methods. The optimal approach will likely involve a combination of methods, tailored to the specific nature of the scam or phishing attempt.
Third-Party App Integration and Security
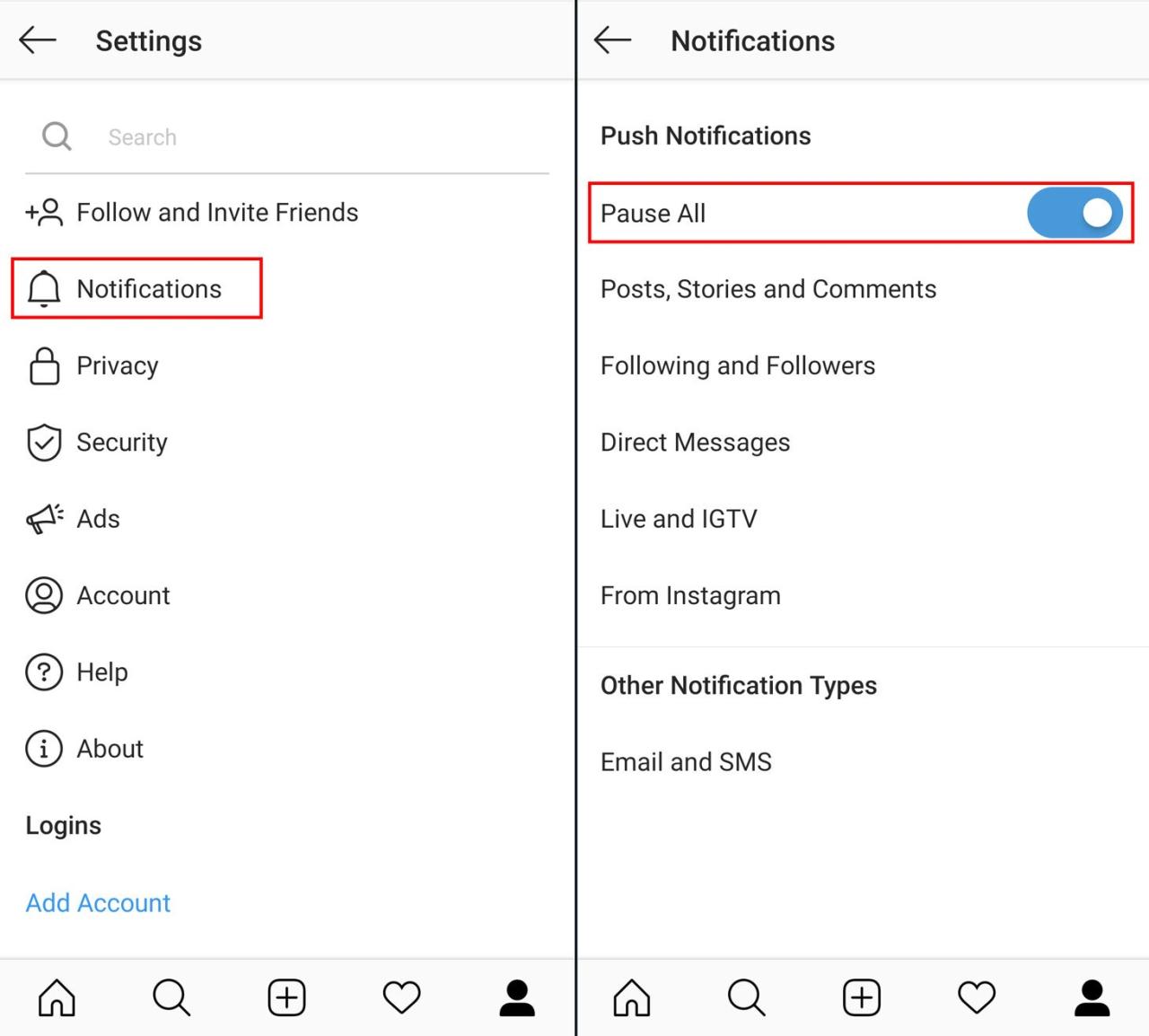
Third-party application integrations are crucial for enhancing user experience, but they introduce significant security risks if not carefully managed. The ease of access to user data through these integrations necessitates stringent security protocols and robust verification processes to protect user accounts and data. This section delves into the security implications of such integrations and proposes measures to mitigate potential vulnerabilities.Third-party applications often require access to user data to function.
This access can range from basic profile information to sensitive data like financial details. Security must be paramount in managing these integrations, ensuring user data is protected and used responsibly. A lack of robust security measures can lead to data breaches, unauthorized access, and financial loss for users.
Security Implications of Third-Party App Integrations
Integrating with third-party applications necessitates a thorough assessment of security risks. These applications may have vulnerabilities that could compromise user accounts and data. Furthermore, the third-party app’s developers may not adhere to the same security standards as the platform, exposing users to potential threats. The potential for malicious actors to exploit vulnerabilities in third-party apps to gain unauthorized access to user data must be considered.
Verification of Third-Party App Legitimacy
Ensuring the legitimacy of third-party applications is paramount. This involves verifying the application’s developers, their security practices, and their compliance with data privacy regulations. Thorough background checks, security audits, and adherence to established security standards are vital. User reviews, app store ratings, and developer reputations are valuable indicators of legitimacy. The platform should employ robust verification mechanisms to validate the legitimacy of any third-party application seeking access to user data.
Potential Risks and Vulnerabilities
Third-party app integrations present potential risks and vulnerabilities. These include unauthorized data access, data breaches, and the potential for malicious actors to exploit vulnerabilities in the app to gain access to user data. A lack of security protocols for data transmission between the platform and the third-party app can also expose users to security risks. Compromised third-party applications can potentially expose a platform’s entire user base to vulnerabilities.
Procedures for Reviewing and Approving Third-Party App Requests
A standardized procedure for reviewing and approving third-party app requests is critical. This procedure should include a comprehensive review of the application’s security practices, data handling policies, and compliance with data privacy regulations. The application’s request for user permissions must be clearly defined and transparent to the user. The platform should establish clear criteria for reviewing and approving requests, ensuring that only legitimate applications are granted access to user data.
Instagram’s recent moves to bolster user security are definitely a step in the right direction. It’s great to see platforms taking proactive measures. Meanwhile, the Department of Justice Offers Safe Harbor for MA Transactions ( Department of Justice Offers Safe Harbor for MA Transactions ) is a parallel effort that highlights the importance of secure transactions. Ultimately, these efforts all contribute to a safer digital landscape for everyone.
This involves a rigorous assessment of the application’s security posture and adherence to established security standards.
Permissions for Third-Party Apps
The following table Artikels the permissions third-party applications should request from users, categorized by function. This categorization helps ensure users are aware of the specific data access requests and can make informed decisions.
| Permission Category | Description | Example Permissions |
|---|---|---|
| Account Access | Accessing user profile information. | Read profile, post history |
| Content Access | Accessing user-generated content. | Read posts, comment on posts |
| Data Access | Accessing user data. | Read user data, write user data |
Security Auditing and Compliance
Regular security audits are crucial for maintaining a strong security posture and safeguarding user data on platforms like Instagram. A comprehensive security audit process not only identifies vulnerabilities but also helps in proactively mitigating potential risks before they can be exploited. This proactive approach minimizes the impact of security breaches and enhances the overall trustworthiness of the platform.Security audits are essential for maintaining compliance with evolving industry standards and regulations, ensuring Instagram continues to protect user data and maintain a high level of security.
A robust audit process is not just about identifying weaknesses; it’s about building a culture of security within the organization.
Importance of Regular Security Audits
Regular security audits are vital for proactively identifying and addressing potential vulnerabilities. They help uncover weaknesses in systems, processes, and procedures that could be exploited by malicious actors. This preventative approach helps protect against a wide range of threats, including data breaches, unauthorized access, and service disruptions. By staying ahead of potential threats, Instagram can safeguard its users’ sensitive information and maintain the integrity of its platform.
Procedures for Identifying and Addressing Security Vulnerabilities
A structured approach is necessary for identifying and addressing security vulnerabilities. This involves a multi-faceted process encompassing automated vulnerability scanning, penetration testing, and manual code reviews. Automated tools can identify common weaknesses in applications and infrastructure, while penetration testing simulates real-world attacks to assess the effectiveness of existing security measures. Manual code reviews provide a deep dive into the source code to detect potential flaws that automated tools might miss.
A dedicated team with expertise in security auditing is also crucial for comprehensive vulnerability assessment and subsequent remediation efforts.
Industry Best Practices for Security Compliance
Instagram can leverage industry best practices for security compliance, including the NIST Cybersecurity Framework and ISO 27001. The NIST Cybersecurity Framework provides a comprehensive structure for organizations to manage cybersecurity risk, while ISO 27001 offers a globally recognized standard for information security management systems. Implementing these frameworks allows Instagram to demonstrate its commitment to security compliance and build trust with its users and stakeholders.
Adherence to these standards demonstrates a dedication to protecting user data and preventing potential security breaches.
Evaluating the Effectiveness of Security Measures
Evaluating the effectiveness of security measures requires a rigorous and ongoing process. This involves regularly assessing the security posture of the platform through metrics like successful penetration attempts, identified vulnerabilities, and the time taken to resolve them. Metrics and reports on these factors provide valuable insights into the efficacy of security measures and allow for adjustments as needed.
This process allows for a dynamic evaluation of security measures, ensuring that they remain relevant and effective in the face of emerging threats.
Maintaining a Strong Security Posture and Adapting to Emerging Threats
Maintaining a strong security posture involves continuous monitoring and adaptation to emerging threats. This includes staying informed about new vulnerabilities and attack vectors, updating security tools and procedures, and implementing new technologies to address evolving threats. Active participation in industry forums and collaboration with security researchers helps Instagram stay ahead of the curve in the ever-evolving cybersecurity landscape.
Regular training for employees on security awareness and best practices is also critical for maintaining a strong security posture and reducing the risk of human error.
Outcome Summary
In conclusion, Instagram’s commitment to enhancing user security is vital for its continued success. By implementing robust security measures across various aspects of the platform, Instagram can build user trust and ensure a safer online environment. The measures discussed, including improved account security, data protection, and content moderation, lay the groundwork for a more secure future for Instagram users.
Question Bank
What are some examples of multi-factor authentication techniques Instagram could utilize?
Instagram could implement various multi-factor authentication methods, such as time-based one-time passwords (TOTP), biometric authentication (fingerprint or facial recognition), or security keys. These methods provide an extra layer of security beyond a simple password.
How can Instagram limit data collection and usage to enhance user privacy?
Instagram can limit data collection by clearly defining what data is necessary for specific services. They could also offer granular control over data sharing options, allowing users to choose what information is shared with third-party apps.
What are some common phishing tactics and scams on Instagram?
Common phishing tactics include fake login pages, messages requesting personal information, and links to malicious websites disguised as legitimate Instagram features. Scammers may also impersonate popular users or offer unrealistic rewards.
How can Instagram educate users about common phishing tactics and scams?
Instagram can educate users through in-app notifications, educational content in the help center, and interactive tutorials. Highlighting visual cues and providing examples of phishing attempts can also help users recognize fraudulent activities.