Intelligent Finding Analytics Your Cognitive Computing App Security Expert
Intelligent finding analytics your cognitive computing application security expert – Intelligent Finding Analytics: Your Cognitive Computing Application Security Expert – that’s a mouthful, right? But it’s the future of application security. Forget sifting through endless log files; imagine a system that learns, adapts, and proactively identifies threats before they even hit. This is the power of cognitive computing applied to application security, a game-changer that’s transforming how we protect our digital assets.
We’ll delve into the core components, explore how machine learning and natural language processing work their magic, and see how this approach revolutionizes threat detection and mitigation.
We’ll unpack the benefits and limitations, compare different approaches, and even peek into the future of this exciting field. Get ready to explore how intelligent finding analytics is not just improving security, but completely redefining it.
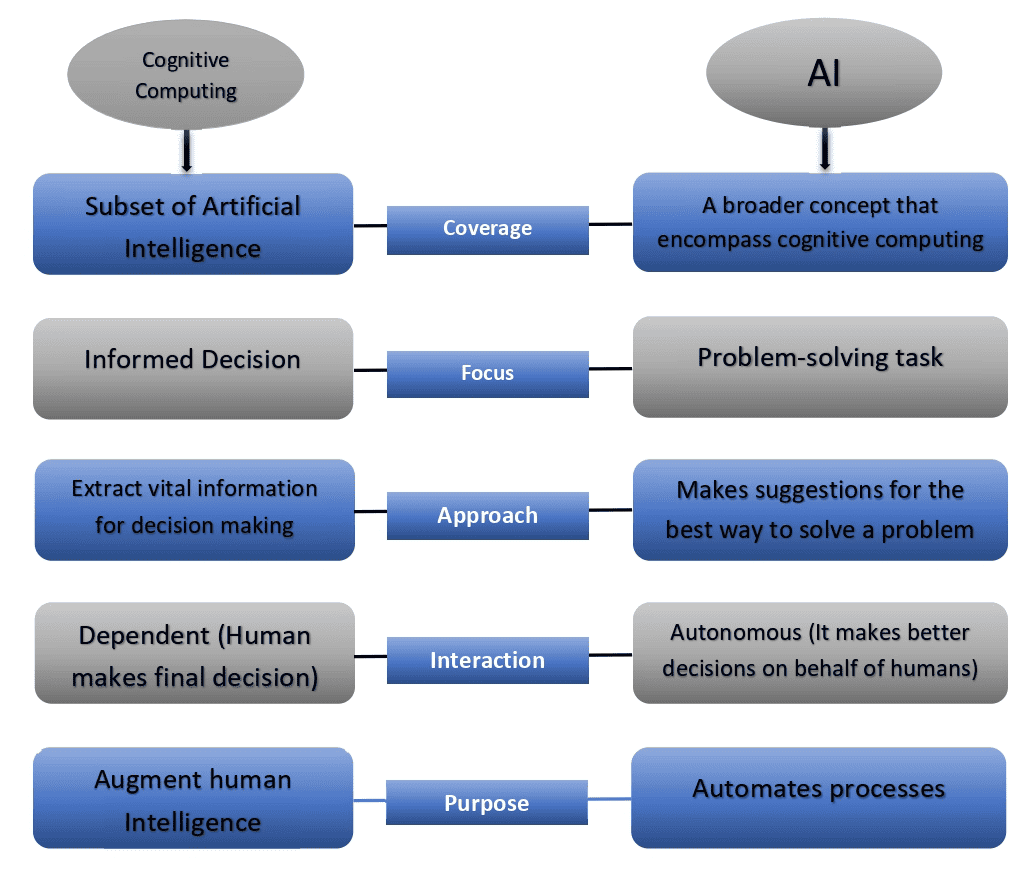
Intelligent Finding Analytics
Intelligent finding analytics represents a significant leap forward in application security, leveraging the power of cognitive computing to automate and enhance the process of identifying and prioritizing vulnerabilities. It moves beyond traditional, rule-based systems to incorporate machine learning and artificial intelligence, allowing for a more nuanced and effective approach to securing applications.This shift is crucial in today’s complex software landscape, where the sheer volume of security findings generated by static and dynamic analysis tools often overwhelms security teams.
Intelligent finding analytics aims to streamline this process, providing security professionals with the actionable insights needed to focus on the most critical risks.
Defining Intelligent Finding Analytics in Application Security, Intelligent finding analytics your cognitive computing application security expert
Intelligent finding analytics, in the context of cognitive computing application security, refers to the application of AI and machine learning techniques to analyze security findings generated by various sources, such as static and dynamic application security testing (SAST and DAST) tools, software composition analysis (SCA) tools, and penetration testing reports. These techniques go beyond simple pattern matching to identify complex relationships between vulnerabilities, prioritize findings based on their potential impact, and even suggest remediation strategies.
Key Characteristics Differentiating Intelligent Finding Analytics from Traditional Methods
Traditional security analysis often relies on predefined rules and signatures to identify vulnerabilities. This approach can be brittle and struggle to detect novel or zero-day exploits. Intelligent finding analytics, in contrast, uses machine learning models trained on vast datasets of vulnerability data to identify patterns and anomalies that might indicate a security risk, even in the absence of explicit rules.
Furthermore, it can adapt and improve its accuracy over time as it learns from new data. Another key difference lies in the ability of intelligent finding analytics to correlate findings from multiple sources, providing a more holistic view of an application’s security posture. This contextual awareness allows for a more accurate assessment of risk.
Approaches to Intelligent Finding Analytics in Application Security
Several approaches exist for implementing intelligent finding analytics in application security. One common approach involves using supervised machine learning to classify vulnerabilities based on their severity and potential impact. This requires a labeled dataset of vulnerabilities, where each vulnerability is tagged with its severity level. Another approach uses unsupervised learning techniques like clustering to group similar vulnerabilities together, which can help identify patterns and trends.
Finally, reinforcement learning can be employed to optimize the process of vulnerability triage and remediation, learning from past experiences to improve its efficiency. Each approach has its strengths and weaknesses, and the best choice depends on the specific needs and resources of the organization.
Benefits and Limitations of Intelligent Finding Analytics
The benefits of intelligent finding analytics are significant. It allows for faster and more accurate vulnerability identification, prioritization, and remediation. This leads to reduced risk, improved security posture, and cost savings. However, limitations exist. The accuracy of intelligent finding analytics depends heavily on the quality and quantity of the training data.
Furthermore, the complexity of these systems can make them difficult to implement and maintain. Finally, the “black box” nature of some machine learning models can make it challenging to understand their decision-making process, potentially leading to a lack of trust among security professionals. Careful consideration of these limitations is crucial for successful implementation.
Cognitive Computing Application Security
Cognitive computing is revolutionizing application security, moving beyond traditional rule-based systems to offer more proactive and adaptive threat detection and response. This shift leverages the power of machine learning, natural language processing, and other AI techniques to analyze vast amounts of data, identify subtle anomalies, and automate security operations. This allows security teams to focus on more strategic initiatives while enhancing overall security posture.
Essential Components of a Cognitive Computing System for Application Security
A robust cognitive computing system for application security requires a synergistic interplay of several core components. These components work together to ingest, process, analyze, and respond to security-relevant information, enabling a more intelligent and efficient security approach. These aren’t independent modules, but rather interconnected parts of a sophisticated system.
Machine Learning Algorithms in Intelligent Finding Analytics
Machine learning algorithms are the engine driving intelligent finding analytics. They enable the system to learn from historical security data, identify patterns, and predict future threats. For example, anomaly detection algorithms can identify unusual network traffic or user behavior that might indicate a compromise. Supervised learning models can be trained on known attack signatures to quickly identify and classify malicious activity.
Reinforcement learning can optimize security policies and responses based on the system’s ongoing experience. The effectiveness of these algorithms hinges on the quality and quantity of training data. A well-trained model can significantly improve the accuracy and speed of threat detection.
Natural Language Processing (NLP) in Interpreting Security Alerts and Findings
Natural language processing plays a crucial role in making sense of the vast amount of unstructured security data, such as logs, alerts, and vulnerability reports. NLP techniques enable the system to extract key information from these sources, categorize alerts based on severity and type, and generate concise summaries for security analysts. This significantly reduces the time and effort required to analyze security information and allows for faster response to critical threats.
For example, NLP can automatically triage security alerts, prioritizing those that require immediate attention.
Cognitive Computing’s Enhancement of Threat Detection and Response
Cognitive computing enhances threat detection and response in several ways. First, it enables proactive threat hunting by identifying subtle anomalies and patterns that might go unnoticed by traditional systems. Second, it automates many routine security tasks, such as vulnerability scanning and incident response, freeing up security professionals to focus on more complex issues. Third, it provides more accurate and timely threat intelligence by analyzing data from multiple sources and identifying emerging threats.
For example, a cognitive system might detect a sophisticated phishing campaign by analyzing email content, user behavior, and network traffic patterns, something a rule-based system might miss. It could then automatically quarantine affected accounts and alert the security team.
Hypothetical Architecture of a Cognitive Computing Application Security System
The following table illustrates a simplified architecture:
| Component | Functionality | Data Sources | Interactions |
|---|---|---|---|
| Data Ingestion Module | Collects data from various sources (logs, alerts, network traffic, etc.) | Security Information and Event Management (SIEM) systems, network devices, application logs, cloud security platforms | Connects to all data sources, preprocesses data for analysis |
| Data Preprocessing Module | Cleans, transforms, and normalizes data for machine learning algorithms | Data Ingestion Module | Provides clean data to the Machine Learning Module |
| Machine Learning Module | Applies machine learning algorithms for threat detection and anomaly detection | Data Preprocessing Module | Generates threat scores and alerts |
| Natural Language Processing (NLP) Module | Analyzes unstructured data (logs, reports) to extract key information and generate summaries | Data Ingestion Module, Machine Learning Module | Provides human-readable summaries of findings and alerts |
| Threat Response Module | Automates security responses based on threat level (e.g., quarantine, alert, block) | Machine Learning Module, NLP Module | Initiates automated responses and escalates critical issues to security teams |
| Security Information Dashboard | Provides a centralized view of security status, alerts, and insights | All modules | Allows security analysts to monitor system activity and respond to threats |
Expert Systems and Intelligent Finding Analytics: Intelligent Finding Analytics Your Cognitive Computing Application Security Expert
Expert systems have found a valuable niche in application security, offering a powerful way to automate vulnerability detection and response. By leveraging codified human expertise, these systems can analyze code, network traffic, and other security-relevant data to identify potential threats with a level of sophistication that surpasses simple signature-based detection. This post will explore how expert systems contribute to intelligent finding analytics, contrasting different approaches and highlighting the challenges in their implementation.
Examples of Expert Systems in Application Security
Several examples showcase the practical application of expert systems in bolstering application security. One common use is static analysis of source code. An expert system could be designed with rules that identify common vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows. The system analyzes the code, applying these rules to flag potential vulnerabilities based on patterns and code constructs.
Another application involves analyzing network traffic logs. An expert system could be trained to recognize suspicious patterns indicative of intrusion attempts or denial-of-service attacks, raising alerts based on pre-defined rules and thresholds. Finally, expert systems can aid in vulnerability prioritization. By integrating information on the severity of vulnerabilities, the likelihood of exploitation, and the impact of a successful attack, these systems can help security teams focus their efforts on the most critical issues.
The decision-making process typically involves a chain of rule evaluations, where the system traverses a knowledge base to determine a conclusion based on the input data.
Rule-Based Expert Systems versus Machine Learning-Based Systems
Rule-based expert systems rely on explicitly defined rules created by security experts. Their strengths lie in their explainability and transparency – the reasoning behind a decision is easily traceable through the rules. However, they struggle with handling unforeseen situations or nuanced patterns not explicitly included in the rules. Machine learning-based systems, conversely, learn patterns from data, adapting and improving their accuracy over time.
Their strengths include the ability to handle complex, noisy data and identify subtle anomalies that might escape rule-based systems. However, their decision-making processes can be opaque (“black box”), making it difficult to understand why a specific decision was made. A hybrid approach, combining the strengths of both, often proves most effective.
Challenges in Integrating Expert Knowledge into a Cognitive Computing System
Integrating expert knowledge into a cognitive computing system presents several significant challenges. Firstly, eliciting and formalizing expert knowledge can be time-consuming and difficult. Security experts often possess tacit knowledge that is hard to articulate explicitly. Secondly, maintaining and updating the knowledge base is an ongoing process. As threats evolve and new vulnerabilities emerge, the system’s rules or models must be updated to remain effective.
Thirdly, ensuring the accuracy and completeness of the knowledge base is crucial. Inaccurate or incomplete rules can lead to false positives or false negatives, undermining the system’s reliability. Finally, dealing with conflicting expert opinions or incomplete information requires sophisticated reasoning mechanisms within the system.
Workflow of an Intelligent Finding Analytics System Incorporating Expert System Rules
The following flowchart illustrates a typical workflow:(Imagine a flowchart here. The flowchart would begin with “Security Data Input” (e.g., code, network logs, vulnerability scans). This would feed into a “Data Preprocessing” step, cleaning and preparing the data for analysis. Next, “Expert System Rule Engine” would apply pre-defined rules to the processed data. This would lead to “Vulnerability Identification and Prioritization,” where potential vulnerabilities are identified and ranked based on severity and likelihood of exploitation.
Finally, “Security Alert Generation and Reporting” would produce alerts and reports for security teams to act upon. Feedback loops could exist between the reporting stage and the rule engine, allowing for continuous improvement and refinement of the system’s rules based on real-world experience.)
Security Threat Detection and Mitigation using Intelligent Finding Analytics
Intelligent Finding Analytics (IFA) represents a significant leap forward in application security, leveraging the power of cognitive computing to proactively identify and mitigate threats that traditional methods often miss. By analyzing vast amounts of data from diverse sources, IFA goes beyond simple pattern matching to uncover sophisticated attacks and vulnerabilities, providing a more comprehensive and effective security posture. This approach is particularly crucial in today’s complex threat landscape, where zero-day exploits and advanced persistent threats are becoming increasingly prevalent.IFA’s ability to analyze diverse data sources, such as network logs, application logs, security information and event management (SIEM) data, and even code repositories, allows for a holistic view of the security landscape.
This comprehensive approach enables the detection of subtle anomalies that might indicate a compromise, even before a full-blown attack occurs. The combination of machine learning algorithms and expert systems allows IFA to adapt to evolving threat patterns and improve its accuracy over time.
Zero-Day Exploit and Advanced Persistent Threat (APT) Detection
Intelligent Finding Analytics excels at detecting zero-day exploits and APTs by identifying unusual patterns and behaviors within application and network traffic. Unlike signature-based systems that rely on known attack patterns, IFA uses anomaly detection techniques to identify deviations from established baselines. This allows it to flag potentially malicious activities even before security signatures are available. For example, IFA might detect unusual data exfiltration attempts or unauthorized access to sensitive data, even if the attack method is completely novel.
The system’s ability to correlate events across different systems and data sources is critical in identifying the subtle indicators often associated with APTs, which typically involve long-term, stealthy infiltration and data exfiltration.
Security Alert Prioritization and Triage
IFA streamlines the security alert management process by prioritizing and triaging alerts based on severity and potential impact. Instead of inundating security teams with a massive volume of alerts, IFA uses a risk-scoring system to focus attention on the most critical threats. This system considers various factors, such as the vulnerability’s severity, the sensitivity of the affected data, and the likelihood of successful exploitation.
By prioritizing alerts, security teams can efficiently address the most critical threats first, minimizing the potential damage from successful attacks. For example, an alert indicating unauthorized access to a database containing customer financial information would be prioritized over an alert related to a low-severity vulnerability in a non-critical application.
Vulnerability Identification and Remediation
Intelligent Finding Analytics identifies and remediates vulnerabilities in applications by analyzing application code, configuration files, and runtime behavior. Static and dynamic analysis techniques are employed to detect known vulnerabilities, such as SQL injection, cross-site scripting (XSS), and buffer overflows. IFA can also identify vulnerabilities that are not easily detectable by traditional methods, such as subtle logic flaws or unexpected interactions between different components of an application.
Beyond identification, IFA can often suggest specific remediation steps, accelerating the patching process and reducing the time applications are vulnerable.
Improved Efficiency of Security Audits and Penetration Testing
IFA significantly enhances the efficiency of security audits and penetration testing by automating many of the repetitive tasks involved in these processes. IFA can automatically scan applications and infrastructure for vulnerabilities, generating detailed reports that highlight potential weaknesses. This automation frees up security professionals to focus on more complex tasks, such as analyzing the findings and developing remediation strategies.
Furthermore, IFA can correlate the findings from multiple security assessments, providing a more comprehensive understanding of the overall security posture of an organization. This reduces the time and resources required for comprehensive security evaluations, enabling more frequent and thorough assessments.
Common Application Security Threats and IFA’s Address
Intelligent Finding Analytics addresses a wide range of application security threats. The following list illustrates how IFA’s capabilities help mitigate these risks:
- SQL Injection: IFA analyzes application code and database interactions to identify vulnerable SQL queries and prevent malicious SQL code from being executed.
- Cross-Site Scripting (XSS): IFA detects and prevents XSS attacks by analyzing application input and output, ensuring that malicious scripts are not injected into web pages.
- Cross-Site Request Forgery (CSRF): IFA employs techniques to prevent CSRF attacks by verifying the authenticity of user requests and preventing unauthorized actions.
- Buffer Overflow: IFA analyzes application code to identify potential buffer overflow vulnerabilities and recommends appropriate remediation strategies.
- Denial-of-Service (DoS) Attacks: IFA monitors network traffic and application behavior to detect and mitigate DoS attacks, ensuring application availability.
- Data Breaches: IFA monitors access to sensitive data and detects unusual patterns that might indicate a data breach attempt, enabling timely response and mitigation.
- Malware Infections: IFA analyzes system logs and application behavior to detect malware infections and take appropriate actions to contain and remove the malware.
- Insider Threats: IFA monitors user activity and access patterns to identify potentially malicious actions by insiders.
Visualization and Reporting of Security Findings
Effective visualization and reporting are crucial for translating the complex data generated by intelligent finding analytics into actionable insights. Without clear and concise communication, even the most sophisticated security system’s findings remain useless. This section details dashboard design, visualization techniques, and report creation for communicating security findings effectively to both technical and non-technical audiences.
Dashboard Design for Key Security Metrics
A well-designed dashboard provides a high-level overview of the system’s security posture. The following table illustrates a sample dashboard displaying key metrics. This dashboard is designed to be responsive, adapting to different screen sizes.
| Metric | Description |
|---|---|
| High-Severity Vulnerabilities | Number of critical and high-severity vulnerabilities identified. This metric highlights immediate threats requiring urgent attention. |
| Average Time to Remediation | Average time taken to resolve identified vulnerabilities. This metric tracks the efficiency of the security response team. |
| Number of Security Incidents | Total number of security incidents detected, including attempted intrusions, malware infections, and data breaches. |
| Successful Phishing Attempts | Number of successful phishing attempts detected. This metric helps assess the effectiveness of security awareness training. |
| System Uptime | Percentage of time the system was operational without security-related downtime. This metric reflects overall system stability. |
Visualization Techniques for Complex Security Data
Various visualization techniques can effectively present complex security data. The choice of technique depends on the specific data and the audience.Several techniques are particularly useful:* Heatmaps: Illustrate the density of vulnerabilities across different systems or network segments. A darker color indicates a higher concentration of vulnerabilities. For example, a heatmap could show the vulnerability density across different departments in a company, highlighting areas needing immediate attention.
Bar Charts
Compare the number of vulnerabilities across different categories (e.g., web applications, databases, operating systems). A bar chart provides a clear and concise comparison of vulnerability counts across various system components.
Line Charts
Show trends in security metrics over time (e.g., number of vulnerabilities detected per month). This allows for the tracking of security improvements or deteriorations over time. For instance, a line chart could track the number of successful phishing attempts over a year, demonstrating the effectiveness of security awareness training programs.
Pie Charts
Illustrate the proportion of vulnerabilities by severity level. This allows for a quick understanding of the overall risk profile. A pie chart can visually represent the proportion of high, medium, and low-severity vulnerabilities, providing a quick overview of the risk landscape.
Network Graphs
Visualize the relationships between different systems and the flow of data. This is particularly useful for identifying potential attack paths. A network graph can map the connections between various systems within a company network, highlighting potential vulnerabilities and attack vectors.
Effective Reporting for Technical and Non-Technical Stakeholders
Effective reporting requires tailoring the presentation to the audience. Technical reports should include detailed technical information, while non-technical reports should focus on high-level summaries and recommendations. The use of clear language and visuals is crucial for both audiences. For example, a technical report might detail the specific vulnerabilities found in a system’s code, while a non-technical report might simply state that the system needs patching to address identified weaknesses.
Sample Security Report
This sample report highlights key findings and recommendations: Subject: Security Assessment Report – [System Name] Date: October 26, 2023 Executive Summary: This report summarizes the findings of a security assessment conducted on [System Name] using intelligent finding analytics. Several high-severity vulnerabilities were identified, requiring immediate remediation. Recommendations for mitigation are provided. Key Findings:* Three critical vulnerabilities were detected in the web application, allowing for potential remote code execution.
- Weak password policies were identified across multiple systems.
- Insufficient logging and monitoring were observed, hindering incident detection and response.
Recommendations:* Immediately patch the critical vulnerabilities identified in the web application.
- Implement a strong password policy, enforcing complexity and regular password changes.
- Enhance logging and monitoring capabilities to improve incident detection and response.
Next Steps: A detailed remediation plan will be developed and implemented within [timeframe]. Regular security assessments will be conducted to maintain a robust security posture.
Future Trends in Intelligent Finding Analytics for Application Security
The field of application security is undergoing a rapid transformation, driven by the increasing sophistication of cyber threats and the ever-growing reliance on software. Intelligent Finding Analytics (IFA), powered by AI and machine learning, is at the forefront of this change, promising more efficient and effective security practices. However, the future of IFA holds both exciting opportunities and significant challenges, demanding careful consideration of emerging technologies and ethical implications.Emerging technologies like quantum computing and blockchain will profoundly impact IFA.
Quantum computing’s immense processing power could potentially break current encryption methods, requiring a complete overhaul of security protocols and IFA’s ability to detect and respond to such breaches. Blockchain technology, on the other hand, offers a transparent and immutable record of security events, potentially enhancing the accuracy and trustworthiness of IFA systems by providing a verifiable audit trail.
Impact of AI and Machine Learning on Application Security
The increased use of AI and machine learning in application security presents both opportunities and challenges. Opportunities include the automation of vulnerability detection, significantly reducing the time and resources required for security assessments. Machine learning algorithms can analyze vast amounts of data to identify patterns indicative of malicious activity, leading to earlier detection of threats. However, challenges include the potential for bias in algorithms, leading to inaccurate or unfair results.
Furthermore, the “black box” nature of some AI models can make it difficult to understand how they arrive at their conclusions, hindering trust and explainability. The potential for adversarial attacks, where malicious actors attempt to manipulate AI systems, also poses a significant risk. For example, an attacker might craft malicious code specifically designed to evade detection by a machine learning-based security system.
Ethical Considerations in Intelligent Finding Analytics
The deployment of IFA systems raises several ethical considerations. Privacy concerns are paramount, as IFA systems often process sensitive data. Ensuring data privacy and compliance with relevant regulations, such as GDPR, is crucial. Another critical ethical consideration is the potential for algorithmic bias. If the data used to train IFA systems is biased, the system may perpetuate and even amplify existing inequalities.
For example, a system trained on data predominantly from one geographic region might be less effective at detecting threats originating from other regions. Transparency and accountability are also essential. It’s important to understand how IFA systems make decisions and to be able to hold developers and users accountable for their actions.
The Future Role of Human Experts in Application Security
While automation is increasing, the role of human experts in application security will remain crucial. Human expertise is needed to interpret the output of IFA systems, validate findings, and make critical decisions in complex situations. The increasing complexity of cyber threats and the limitations of current AI technology mean that human judgment and intuition will continue to be essential components of effective security practices.
The focus will shift towards collaboration between humans and machines, with humans focusing on strategic decision-making, complex problem-solving, and ethical oversight, while machines handle repetitive and data-intensive tasks. For example, a human expert might use an IFA system to identify potential vulnerabilities, but then leverage their experience to prioritize those vulnerabilities based on their potential impact and the organization’s specific risk profile.
Closing Summary
So, there you have it – a glimpse into the world of intelligent finding analytics and its role in cognitive computing application security. It’s clear that this technology is more than just a buzzword; it’s a powerful tool that’s reshaping the security landscape. By leveraging machine learning, natural language processing, and expert systems, we can move beyond reactive security measures and embrace a proactive, intelligent approach.
The future of application security is intelligent, and it’s here to stay. Stay tuned for more insights into this rapidly evolving field!
Essential FAQs
What are the biggest challenges in implementing intelligent finding analytics?
The biggest challenges include data quality (noisy or incomplete data hinders learning), integrating with existing security infrastructure, and the need for skilled personnel to manage and interpret the system’s outputs. Also, ensuring ethical considerations and mitigating bias in algorithms are crucial.
How much does an intelligent finding analytics system cost?
The cost varies significantly depending on the scale, complexity, and features of the system. It ranges from relatively affordable solutions for smaller organizations to highly complex, enterprise-grade systems with substantial upfront and ongoing costs.
Can intelligent finding analytics replace human security experts?
No, not entirely. While these systems automate many tasks, human expertise remains crucial for interpreting complex findings, making strategic decisions, and handling nuanced situations that AI might miss.
What types of security alerts are best suited for intelligent finding analytics?
Systems excel at handling high-volume, repetitive alerts, such as log file analysis and network traffic monitoring. They’re less effective with highly context-dependent alerts that require deep human understanding.