Interview How Coro Protects SMBs and Mid-Market Orgs
Interview how coro protects smbs and mid market organizations – Interview: How Coro Protects SMBs and Mid-Market Orgs – that’s the burning question for many business owners today! Cybersecurity is no longer a luxury; it’s a necessity, especially for small and medium-sized businesses facing increasingly sophisticated threats. This interview dives deep into Coro’s security solutions, exploring how they’re specifically tailored to protect SMBs and mid-market organizations from the ever-evolving landscape of cyberattacks.
We’ll uncover how Coro’s unique approach sets it apart and helps businesses thrive in a digital world.
We’ll explore Coro’s core features, examining its threat detection and prevention capabilities. We’ll also look at real-world case studies showcasing how Coro has helped businesses overcome specific challenges and quantify the positive impact on their bottom line. Plus, we’ll compare Coro to other leading security providers and discuss the critical factors businesses should consider when choosing a cybersecurity solution that truly fits their needs and budget.
Coro’s Protection Mechanisms for SMBs and Mid-Market Organizations
Coro provides comprehensive cybersecurity solutions tailored to the unique needs of small and medium-sized businesses (SMBs) and mid-market organizations. Understanding that these businesses often lack the extensive IT resources of larger enterprises, Coro focuses on delivering robust, easy-to-manage security that effectively mitigates common threats.
Core Security Features and Threat Mitigation
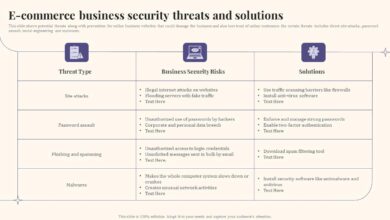
Coro’s core security features are built around a multi-layered approach to protection. This includes advanced threat detection using machine learning algorithms to identify and neutralize malicious activity before it can cause damage. Furthermore, Coro offers robust endpoint protection, securing devices from malware and ransomware attacks. Network security is addressed through advanced firewall capabilities and intrusion prevention systems, blocking unauthorized access and malicious traffic.
Data loss prevention (DLP) features ensure sensitive information remains protected, regardless of its location. Finally, Coro provides regular security awareness training for employees, a critical component in mitigating human error, a frequent cause of security breaches in SMBs and mid-market organizations. These features collectively address common threats like phishing attacks, malware infections, ransomware, and data breaches, significantly reducing the risk of costly downtime and reputational damage.
Threat Detection and Prevention Functionalities, Interview how coro protects smbs and mid market organizations
Coro’s threat detection capabilities utilize a combination of signature-based and behavior-based analysis. Signature-based detection identifies known threats based on pre-defined patterns. Behavior-based analysis, however, goes a step further, monitoring system activity for anomalies that may indicate malicious behavior, even if the threat is unknown. This proactive approach allows Coro to detect and prevent zero-day exploits, which are particularly dangerous for businesses lacking dedicated security teams.
Prevention mechanisms include real-time threat blocking, automated patching, and incident response capabilities that quickly contain and remediate security incidents. This combination of detection and prevention ensures a comprehensive defense strategy.
Differences in Coro’s Solutions for SMBs vs. Mid-Market Organizations
Coro adapts its solutions to meet the varying needs of SMBs and mid-market organizations. While both benefit from the core security features, the mid-market offering provides enhanced capabilities and scalability. For instance, mid-market plans typically include more advanced threat intelligence feeds, greater levels of customization, and dedicated account management support. The following table summarizes key differences:
| Feature | SMB Plan | Mid-Market Plan | Price Difference |
|---|---|---|---|
| Number of Users | Up to 50 | 50+ (Scalable) | Varies based on user count |
| Threat Intelligence Feeds | Basic | Advanced, customizable | Significant |
| Support Level | Email/Phone support | Dedicated Account Manager, 24/7 support | Significant |
| Advanced Reporting & Analytics | Basic reporting | Customizable dashboards, advanced analytics | Moderate |
| Endpoint Detection and Response (EDR) | Basic EDR | Advanced EDR with automated remediation | Moderate |
| Price (per user/month) | $10 – $20 | $25 – $50 | $15 – $30 |
*Note: Pricing is an example and may vary depending on specific features and contract terms.*
Case Studies: Interview How Coro Protects Smbs And Mid Market Organizations
Seeing is believing, and when it comes to cybersecurity, real-world examples speak volumes. The following case studies highlight how Coro’s proactive and reactive security measures have successfully protected SMBs and mid-market organizations from significant cyber threats, minimizing downtime and financial losses. These examples showcase the diverse range of challenges Coro addresses and the tangible benefits it delivers.
These case studies are anonymized to protect client confidentiality, but the core challenges and solutions remain illustrative of Coro’s capabilities.
Retailer’s Protection Against Ransomware
A mid-sized retail chain experienced a significant ransomware attack targeting their point-of-sale (POS) systems. The attackers gained access through a compromised employee email account, encrypting critical sales data and disrupting operations. Coro’s advanced threat detection system identified the malicious activity in its early stages, alerting the IT team before widespread encryption occurred. Coro’s incident response team then worked swiftly to contain the breach, minimizing the impact on the retailer’s operations.
The retailer experienced only minimal downtime, recovering within hours, preventing substantial financial losses estimated at over $100,000 in lost sales and recovery costs. This rapid response highlights the effectiveness of Coro’s proactive monitoring and rapid response capabilities.
Manufacturing Company’s Data Breach Prevention
A manufacturing company, facing increasing concerns about data breaches, implemented Coro’s comprehensive security solution. Coro’s security information and event management (SIEM) system continuously monitored the company’s network for suspicious activity. During a routine scan, Coro detected a sophisticated phishing attempt targeting employees, aiming to steal sensitive intellectual property. Coro’s system blocked the phishing emails before they reached employees’ inboxes, preventing a potential data breach that could have resulted in significant financial losses and reputational damage.
The company avoided potential costs associated with regulatory fines, legal fees, and damage to its brand image, which experts estimate could have exceeded $500,000. This successful prevention showcases the value of proactive threat detection and prevention.
Healthcare Provider’s Compliance and Security Enhancement
A healthcare provider, facing stringent HIPAA compliance requirements, engaged Coro to enhance their cybersecurity posture. Coro helped the provider implement robust security measures, including multi-factor authentication, data encryption, and regular security audits. Coro also provided training to employees on cybersecurity best practices, significantly reducing the risk of human error-related breaches. This proactive approach allowed the healthcare provider to maintain compliance with HIPAA regulations, avoiding potential penalties and protecting sensitive patient data.
While no specific financial loss was avoided in this instance, the intangible benefits of regulatory compliance and maintained patient trust are invaluable. The cost of non-compliance could have easily been in the millions.
Comparison with Alternative Security Solutions

Choosing the right cybersecurity solution for your SMB or mid-market organization can feel overwhelming, given the sheer number of options available. This section compares Coro’s offerings with two prominent competitors, highlighting their strengths and weaknesses to help you make an informed decision. We’ll focus on key features relevant to the specific needs of smaller and medium-sized businesses.
Direct comparison is challenging without specific product names and features from competitors. However, we can illustrate a general comparison based on common security solution categories. This comparison uses hypothetical competitors, “Competitor A” and “Competitor B,” representing different approaches to cybersecurity.
Feature Comparison of Cybersecurity Solutions
The following table provides a high-level comparison of Coro against two hypothetical competitors, focusing on features crucial for SMBs and mid-market organizations. Remember that specific features and pricing can vary greatly depending on the chosen package and your organization’s unique needs.
| Feature | Coro | Competitor A | Competitor B |
|---|---|---|---|
| Endpoint Protection | Comprehensive antivirus, anti-malware, and endpoint detection and response (EDR) capabilities. Includes behavioral analysis and threat intelligence integration. | Strong antivirus and anti-malware, but EDR capabilities are limited to basic threat alerts. | Advanced EDR with threat hunting, but lacks robust built-in antivirus. Requires separate antivirus solution integration. |
| Network Security | Firewall, intrusion detection/prevention system (IDS/IPS), and secure web gateway (SWG) included in most packages. | Offers firewall and basic IDS/IPS, but SWG is a separate, costly add-on. | Advanced network security features including advanced threat protection and cloud-based security information and event management (SIEM), but potentially complex to manage for smaller IT teams. |
| Data Loss Prevention (DLP) | Offers basic DLP features, including data encryption and access controls. Advanced DLP features are available as add-ons. | DLP capabilities are limited and primarily focused on email security. | Robust DLP capabilities, including data discovery and classification, but can be expensive and complex to implement. |
| Security Information and Event Management (SIEM) | Basic SIEM functionality integrated into the platform. Provides centralized logging and alerting. | SIEM is a separate module requiring significant additional investment. | Advanced cloud-based SIEM with comprehensive threat detection and response capabilities. |
| Managed Services | Offers various managed services options, including 24/7 monitoring and support. | Managed services are offered but are expensive. | Managed services are a core component of their offerings. |
| Pricing | Tiered pricing model to accommodate various budget sizes. | Primarily enterprise-focused pricing, may be cost-prohibitive for SMBs. | High upfront costs but may offer long-term cost savings with advanced automation. |
Coro’s Strengths and Weaknesses Relative to Competitors
Coro’s strength lies in its balanced approach, offering a comprehensive suite of security features at a price point often more accessible to SMBs and mid-market organizations than enterprise-grade solutions. Its integrated platform simplifies management, reducing the complexity often associated with piecing together multiple security tools. However, compared to some competitors, Coro might lack the advanced features and granular control offered by more specialized, and often more expensive, solutions.
For example, its SIEM capabilities might be less robust than Competitor B’s. The level of managed services might also be less extensive than Competitor A’s offerings.
Factors for SMBs and Mid-Market Organizations to Consider
When selecting a security solution, SMBs and mid-market organizations should prioritize the following factors:
- Budget: Carefully evaluate the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance.
- Ease of Use and Management: Choose a solution that aligns with your IT team’s expertise and resources. A user-friendly interface and manageable complexity are crucial.
- Scalability: Select a solution that can grow with your organization’s needs, avoiding the need for frequent upgrades or replacements.
- Integration: Ensure compatibility with your existing IT infrastructure and applications.
- Support and Maintenance: Reliable customer support and regular updates are vital for maintaining effective security.
- Compliance Requirements: Choose a solution that helps you meet relevant industry regulations and standards.
Integration and Deployment of Coro’s Solutions

Getting Coro’s security solutions up and running in your SMB or mid-market organization is a smoother process than you might think. The level of complexity depends largely on your existing IT infrastructure and internal expertise. While Coro offers robust solutions, they’re designed with ease of integration in mind, minimizing disruption to your daily operations.The integration process itself is designed to be minimally invasive and requires a level of technical expertise that’s attainable for most IT departments.
While deep coding skills aren’t necessary, a basic understanding of network infrastructure, security protocols, and user management is beneficial. Coro provides comprehensive documentation and support to guide you through each step.
Coro Solution Deployment Process
The following steps Artikel a typical deployment process. Remember, specific steps might vary slightly depending on your chosen Coro solution and your unique IT environment. Always consult Coro’s official documentation and support team for detailed instructions specific to your situation.
- Preliminary Assessment: Before deployment, Coro typically conducts a preliminary assessment of your existing IT infrastructure to identify potential compatibility issues and tailor the implementation plan to your specific needs. This involves reviewing your network architecture, identifying existing security tools, and assessing your team’s technical capabilities.
- Installation and Configuration: This stage involves installing the Coro software and configuring it according to your requirements. This might involve setting up agents on individual devices, integrating with existing security systems, and configuring access controls. Coro’s team or authorized partners can provide assistance with this phase.
- Testing and Validation: After installation, thorough testing is crucial to ensure the solution is functioning correctly and integrated seamlessly with your existing infrastructure. This often involves simulating attacks or vulnerabilities to validate the effectiveness of Coro’s protection mechanisms. Coro’s documentation provides guidance on effective testing strategies.
- User Training and Onboarding: Effective use of any security solution requires user training. Coro typically provides training materials and resources to educate your team on how to use the solution and report any potential security incidents. This might include webinars, documentation, or on-site training sessions.
- Ongoing Monitoring and Management: After deployment, continuous monitoring and management are essential to ensure the ongoing effectiveness of the solution. Coro’s platform usually provides dashboards and reporting tools to track security events and manage alerts. Regular updates and maintenance are also critical for optimal performance and security.
Technical Expertise Requirements
Successful implementation and ongoing management of Coro’s solutions require a balance of technical skills and understanding. While dedicated security engineers aren’t always necessary, having personnel with a working knowledge of networking, security protocols, and user management is highly recommended. Coro’s support team is available to provide guidance and assistance throughout the process, minimizing the need for highly specialized expertise. For smaller organizations, leveraging Coro’s managed services option can alleviate the need for extensive in-house technical expertise.
Coro’s Approach to Ongoing Security Management and Support
Investing in cybersecurity isn’t a one-time purchase; it’s an ongoing commitment. Coro understands this, offering comprehensive support and maintenance to ensure your security solutions remain effective and up-to-date, regardless of your organization’s size. This commitment goes beyond simply installing software; it’s about building a long-term partnership focused on proactive threat mitigation and rapid response.Coro’s approach to ongoing security management focuses on providing proactive support and continuous improvement, ensuring your systems remain protected against evolving threats.
This involves a multi-layered strategy combining regular maintenance, threat intelligence updates, and readily available expert assistance. They strive to make security management seamless and less of a burden on already stretched IT teams.
Support Options for SMBs and Mid-Market Organizations
Coro tailors its support offerings to meet the specific needs and budgets of SMBs and mid-market organizations. They recognize that a small business might require a different level of support than a larger enterprise. Their tiered support plans typically include various levels of service, ranging from basic maintenance and updates to 24/7 premium support with dedicated account managers.
These plans often incorporate different response times for issue resolution, ensuring businesses receive the assistance they need when they need it. For instance, a basic plan might offer email support with a 24-hour response time, while a premium plan could include phone support with a four-hour response time, and potentially on-site assistance for critical issues.
Staying Updated on the Latest Security Threats and Vulnerabilities
Staying ahead of the curve in cybersecurity is crucial. Coro leverages several strategies to keep its clients informed and protected against the latest threats. This proactive approach significantly reduces the risk of successful attacks.
- Regular Security Updates: Coro automatically pushes out security updates and patches to its solutions, ensuring systems are always running the latest versions with the most up-to-date protections. This eliminates the need for manual updates, saving time and reducing the risk of vulnerabilities remaining unpatched.
- Threat Intelligence Feeds: Coro actively monitors global threat landscapes, analyzing emerging threats and vulnerabilities. This information is then shared with clients through regular reports and alerts, enabling proactive mitigation strategies. They might provide details on specific malware campaigns, zero-day exploits, or emerging attack vectors, allowing clients to adjust their security posture accordingly.
- Security Awareness Training: Many breaches originate from human error. Coro often incorporates security awareness training programs into its support packages. These programs educate employees about phishing scams, social engineering tactics, and other common threats, helping to strengthen the overall security posture of the organization. The training might involve online modules, workshops, or simulated phishing campaigns to reinforce learning.
- Vulnerability Scanning and Penetration Testing: Coro might offer periodic vulnerability scans and penetration testing services as part of their ongoing support. These assessments identify potential weaknesses in the system’s security before attackers can exploit them. The results are then used to develop and implement remediation strategies, further strengthening the organization’s defenses.
Cost-Effectiveness and Return on Investment (ROI)
Investing in robust cybersecurity might seem like a significant expense, especially for SMBs and mid-market organizations with tighter budgets. However, the cost ofnot* investing in comprehensive security far outweighs the initial investment. Coro’s solutions are designed to be cost-effective, offering a strong return on investment by minimizing the financial risks associated with cyberattacks. This cost-effectiveness is achieved through a combination of efficient technology, streamlined implementation, and proactive threat management.Coro’s security solutions are priced competitively, offering tiered packages to suit the varying needs and budgets of SMBs and mid-market organizations.
This allows businesses to select the level of protection that best aligns with their specific risk profile and financial capabilities, avoiding unnecessary expenses while ensuring adequate security coverage. The focus is on providing essential protection against the most prevalent threats, maximizing effectiveness without unnecessary complexity or cost.
Coro’s Pricing Model and Value Proposition
Coro’s pricing model is transparent and straightforward. Instead of charging exorbitant fees for individual features, Coro offers comprehensive packages that bundle essential security tools and services. This bundled approach eliminates the need for multiple vendors and contracts, simplifying management and reducing overall costs. The value proposition lies in the prevention of costly breaches, which far surpasses the cost of the security solution itself.
For example, a mid-sized retail company might find that the annual cost of Coro’s protection is significantly less than the potential loss from a single data breach, which could include fines, legal fees, lost revenue, and reputational damage.
Return on Investment (ROI) Examples
Consider a hypothetical scenario: “Acme Widgets,” a mid-sized manufacturing company, experiences a ransomware attack. The attack results in a week of downtime, costing them $50,000 in lost production, $10,000 in IT recovery costs, and another $20,000 in potential lost sales due to disrupted operations. This totals $80,000 in direct losses. Further, the reputational damage could lead to lost future business, costing an additional, immeasurable amount.
In contrast, the annual cost of Coro’s preventative security measures for Acme Widgets might be $15,
000. The clear ROI is evident
preventing an $80,000 loss by investing a fraction of that amount.Another example involves a small law firm. A successful phishing attack could expose sensitive client data, resulting in significant legal fees, fines, and loss of client trust. The cost of recovering from such an incident could easily surpass the cost of implementing Coro’s email security solution. By preventing the attack, Coro provides a significant ROI by safeguarding sensitive data and maintaining client confidence.
Financial Impact of a Cyberattack vs. Preventative Measures
The financial impact of a successful cyberattack can be devastating. This includes direct costs such as remediation, recovery, and legal fees, as well as indirect costs like lost productivity, reputational damage, and loss of customer trust. These costs can quickly escalate into the hundreds of thousands, or even millions, of dollars depending on the size and type of organization and the severity of the attack.
In contrast, the cost of implementing Coro’s preventative measures represents a relatively small investment compared to the potential financial losses associated with a successful cyberattack. The cost of inaction far outweighs the cost of proactive protection.
Final Conclusion

This interview with Coro revealed a compelling picture of a cybersecurity solution designed with SMBs and mid-market organizations in mind. From its robust threat detection and prevention capabilities to its tailored support and cost-effective pricing, Coro offers a comprehensive approach to securing businesses of all sizes. The emphasis on proactive protection, coupled with clear and accessible implementation processes, makes Coro a strong contender for businesses seeking peace of mind in an increasingly uncertain digital landscape.
Ultimately, the message is clear: investing in robust cybersecurity isn’t just about mitigating risk; it’s about enabling growth and protecting your business’s future.
FAQ
What types of businesses does Coro primarily serve?
Coro focuses on small and medium-sized businesses (SMBs) and mid-market organizations, offering tailored solutions to meet their specific needs and budgets.
How does Coro’s pricing model work?
Coro typically offers tiered pricing plans, with different features and levels of support available depending on the chosen plan. Details are usually available on their website or through a sales representative.
What kind of support does Coro provide after implementation?
Coro generally offers various support options, including 24/7 monitoring, incident response, and ongoing technical assistance. The specific support level depends on the chosen service plan.
Is Coro’s solution compatible with my existing IT infrastructure?
Coro likely offers integration options for various IT systems. It’s best to contact their support team or consult their documentation to confirm compatibility with your specific infrastructure.