Is Patch Tuesday Dead?
Is Patch Tuesday dead? That’s the question many are asking as the software update landscape evolves at breakneck speed. For years, the second Tuesday of the month was synonymous with system updates, a ritualistic patching process ingrained in the tech world. But with the rise of cloud computing, continuous integration, and the ever-increasing sophistication of cyber threats, the traditional Patch Tuesday model is facing its biggest challenge yet.
This post dives deep into the past, present, and future of software patching, exploring whether this once-sacred day is truly obsolete.
We’ll trace the evolution of Patch Tuesday from its humble beginnings to its current state, analyzing the factors that have contributed to its decline (or perhaps, its transformation). We’ll examine the advantages and disadvantages of both the traditional Patch Tuesday approach and the newer continuous update models, considering their impact on users, vendors, and overall security. We’ll also discuss the role of automation, the ever-present threat of zero-day exploits, and the critical importance of user behavior in maintaining a secure digital environment.
Get ready to explore a world where the rhythm of updates is changing!
The Evolution of Patch Tuesday

Patch Tuesday, a term synonymous with Microsoft’s monthly security update release, has a long and fascinating history. Its evolution reflects the changing landscape of software development, deployment, and the ever-present threat of cyberattacks. Initially conceived as a centralized method for delivering critical security fixes, it has adapted – and in some ways, been challenged – by shifts in technology and software release methodologies.The initial purpose of Patch Tuesday was to provide a predictable schedule for distributing security updates to address vulnerabilities discovered in Microsoft’s operating systems and software.
This centralized approach aimed to improve the security posture of millions of users by delivering patches simultaneously, mitigating the window of vulnerability that existed before updates were widely deployed. The regularity of the release aimed to instill a sense of routine and predictability for both Microsoft and its users.
The Shift in Software Release Cycles and Update Frequencies
The early days of Patch Tuesday were characterized by large, infrequent updates. However, the demand for faster software iteration and more responsive security patching led to significant changes. The rise of service packs, initially designed to bundle multiple updates, eventually gave way to a more continuous approach. Microsoft began releasing smaller, more frequent updates, sometimes multiple times a month, outside of the traditional Patch Tuesday schedule.
This shift was driven by the need to address vulnerabilities more quickly and reduce the risk exposure time. The increasing complexity of software and the interconnected nature of systems made the old model of monthly updates increasingly inadequate.
The Impact of Cloud Computing and Continuous Delivery
The rise of cloud computing and continuous delivery significantly altered the landscape of software updates. Cloud-based services operate on a continuous update model, with updates often being deployed automatically and seamlessly in the background. This contrasts sharply with the traditional Patch Tuesday model, which relies on scheduled releases and requires user intervention for installation. The agility and scalability of cloud-based deployments allowed for a more proactive and responsive approach to security patching, reducing the reliance on large, infrequent releases.
Companies like Microsoft itself, with its Azure cloud platform, exemplify this shift, demonstrating the increasing adoption of continuous updates in their own services.
A Timeline of Microsoft’s Patching Strategy
A clear timeline highlights the evolution of Microsoft’s patching approach:
| Year | Key Event | Description |
|---|---|---|
| Early 2000s | Inception of Patch Tuesday | Monthly release of security updates, often bundled in large service packs. |
| Mid-2000s | Increased Update Frequency | More frequent, smaller updates introduced to address vulnerabilities more rapidly. |
| Late 2000s – 2010s | Rise of Automatic Updates | Emphasis on automatic update deployment, reducing reliance on user intervention. |
| 2010s – Present | Continuous Delivery and Cloud Integration | Increased adoption of continuous delivery models, especially within cloud services, blurring the lines of traditional Patch Tuesday. |
Modern Patching Strategies
The traditional Patch Tuesday model, while familiar, is increasingly showing its limitations in today’s fast-paced threat landscape. The shift towards continuous integration and continuous delivery (CI/CD) in software development mirrors a similar evolution in patching strategies. Organizations are moving away from the once-a-month, bulk patching approach towards more frequent, smaller updates, often delivered automatically. This evolution is driven by the need to address vulnerabilities more rapidly and minimize the window of opportunity for attackers.Modern patching strategies prioritize speed and agility, aiming for near real-time response to emerging threats.
This contrasts sharply with the predictable, yet potentially slow, rhythm of Patch Tuesday. The advantages and disadvantages of each approach impact both the users and the vendors involved in the process.
Patch Tuesday vs. Continuous Updates: A Comparison
Patch Tuesday, with its predictable monthly release cycle, offers a structured approach to patching. Users benefit from a clear schedule and the ability to plan maintenance windows. However, this predictability also allows attackers to focus their efforts on exploiting vulnerabilities before patches are widely deployed. Vendors, while having a set release schedule, face the challenge of coordinating the testing and deployment of a large number of patches simultaneously.
This can lead to unforeseen compatibility issues and increased support requests.In contrast, continuous update models deliver patches as soon as they are available, often without requiring user intervention. This significantly reduces the exposure window for vulnerabilities. Users benefit from enhanced security, but may experience more frequent, albeit smaller, disruptions to their workflows. Vendors need robust automated testing and deployment systems, as well as strong communication channels to keep users informed of updates.
The constant stream of updates, however, can be challenging to manage, particularly for organizations with complex IT infrastructures.
The Role of Automated Patching Tools
Automated patching tools and systems management solutions are critical components of modern patching strategies. These tools streamline the update process, reducing manual effort and minimizing the risk of human error. They allow for centralized management of patches across multiple devices and operating systems, enabling consistent and timely updates. Features like automated vulnerability scanning, patch prioritization, and deployment scheduling enhance efficiency and improve security posture.
Examples include Microsoft’s Endpoint Manager, VMware Workspace ONE, and other enterprise-grade solutions. These systems often integrate with vulnerability databases, allowing for rapid response to newly discovered threats.
Impact of Zero-Day Exploits and Rapid Response Patching
The emergence of zero-day exploits—vulnerabilities unknown to vendors—highlights the limitations of scheduled patching cycles. The rapid response required to address these threats necessitates a departure from the Patch Tuesday model. Continuous update models, combined with robust threat intelligence and proactive security measures, are crucial for mitigating the risks associated with zero-day vulnerabilities. Organizations must be able to deploy patches quickly and efficiently, often within hours or even minutes of a vulnerability being discovered.
This demands a highly automated and flexible patching infrastructure. The recent SolarWinds attack serves as a stark reminder of the devastating consequences of unpatched vulnerabilities and the urgent need for rapid response mechanisms.
The Security Landscape
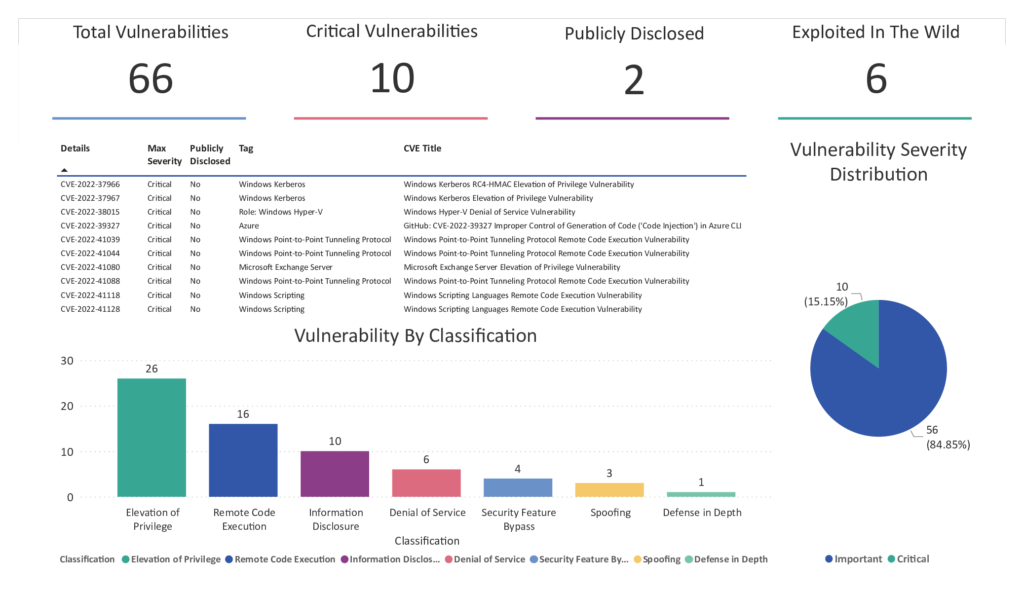
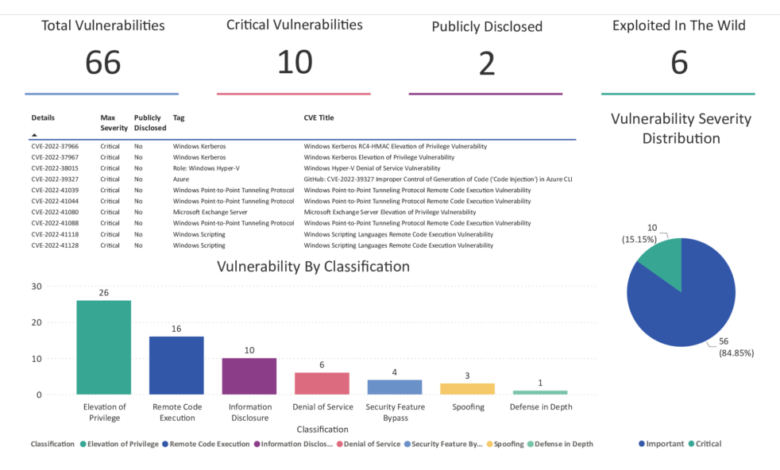
The modern digital world is a complex tapestry woven with threads of interconnected systems and data. This interconnectedness, while offering immense benefits, creates a vast attack surface for cybercriminals. Understanding the threats and vulnerabilities within this landscape is crucial for effective security strategies, and timely patching plays a pivotal role in mitigating risk. Neglecting this critical aspect can lead to devastating consequences, as evidenced by numerous high-profile breaches.The ever-evolving nature of cyber threats necessitates a proactive and adaptable approach to security.
Attackers constantly refine their techniques, exploiting newly discovered vulnerabilities and leveraging sophisticated tools to penetrate defenses. This requires a multi-layered security strategy that encompasses not only patching but also robust vulnerability scanning, penetration testing, and a strong security awareness culture.
Recent High-Profile Security Breaches and Patching
Several recent high-profile breaches highlight the critical importance of timely patching. For example, the SolarWinds attack in 2020 exploited a vulnerability in the Orion platform, allowing attackers to compromise thousands of organizations. This breach underscored the devastating impact of supply chain attacks and the need for rigorous patching practices across the entire software ecosystem. Similarly, the Log4j vulnerability in 2021, a widely used Java logging library, presented a significant threat due to its ubiquity and ease of exploitation.
Organizations that failed to patch their systems promptly faced severe consequences, including data breaches and system compromises. These examples demonstrate that even seemingly small vulnerabilities can have far-reaching and catastrophic effects if left unpatched.
Commonly Targeted Vulnerabilities
Attackers frequently target vulnerabilities in various software components. Common categories include remote code execution (RCE) flaws, which allow attackers to execute arbitrary code on a compromised system; cross-site scripting (XSS) vulnerabilities, enabling attackers to inject malicious scripts into websites; and SQL injection flaws, allowing attackers to manipulate database queries to access sensitive data. Zero-day exploits, vulnerabilities unknown to vendors, pose a particularly significant threat as they lack readily available patches.
These vulnerabilities often reside in web applications, operating systems, and network devices, making a comprehensive patching strategy crucial.
Vulnerability Scanning and Penetration Testing, Is patch tuesday dead
Proactive security measures are essential to identify and mitigate vulnerabilities before attackers can exploit them. Vulnerability scanning involves automated tools that analyze systems for known weaknesses, providing a comprehensive inventory of potential vulnerabilities. Penetration testing, on the other hand, simulates real-world attacks to identify security weaknesses that vulnerability scans might miss. These assessments provide crucial insights into the effectiveness of existing security controls and guide remediation efforts, including prioritizing patching efforts based on risk.
Regular vulnerability scanning and penetration testing are critical components of a robust security posture.
Hypothetical Scenario: Consequences of Patch Neglect
Imagine a mid-sized financial institution neglecting to implement timely patching. A critical vulnerability in their core banking application, allowing remote code execution, remains unpatched for several weeks. An attacker discovers this vulnerability and exploits it, gaining unauthorized access to the bank’s systems. The attacker exfiltrates sensitive customer data, including account numbers, social security numbers, and financial transactions.
This breach results in significant financial losses, reputational damage, regulatory fines, and legal repercussions. Furthermore, the compromised systems might be used to launch further attacks, impacting other organizations and individuals. This hypothetical scenario illustrates the potentially devastating consequences of neglecting timely patching, emphasizing its crucial role in maintaining a strong security posture.
User Behavior and Patch Adoption
Understanding why users install (or don’t install) software updates is crucial for effective security. Patch adoption rates directly impact an organization’s vulnerability to cyber threats. Factors influencing this behavior are complex and multifaceted, ranging from individual technical skills to organizational policies.
User decisions regarding software updates are driven by a combination of factors, including perceived risk, convenience, trust in the software vendor, and even the user’s overall digital literacy. A lack of understanding about the consequences of neglecting updates, coupled with the potential disruption caused by installation processes, often leads to procrastination or outright avoidance. Furthermore, the complexity of patch management systems, particularly in enterprise settings, adds another layer of difficulty.
This complexity can lead to frustration and a lack of user engagement.
Factors Influencing Patch Adoption
The following table summarizes how various demographic groups tend to approach software patching. It’s important to note that these are generalizations and individual behavior can vary significantly.
| Demographic | Patching Behavior | Motivations | Challenges |
|---|---|---|---|
| Tech-Savvy Users (e.g., developers, IT professionals) | Prompt and consistent patching | Understanding of security risks, proactive approach, familiarity with processes | May encounter more complex patches and potential conflicts with custom software |
| Average Users (e.g., office workers, casual internet users) | Delayed or inconsistent patching | Limited understanding of security risks, convenience, fear of system disruption | Lack of technical expertise, reliance on IT support, potential for work interruption |
| Less Tech-Literate Users (e.g., elderly individuals, those with limited digital skills) | Infrequent or no patching | Lack of understanding, difficulty navigating update processes, fear of irreversible damage | Need for simplified instructions, increased support, potentially requiring in-person assistance |
| Mobile Device Users | Generally more prompt patching due to automated updates | Convenience of automatic updates, reliance on mobile OS providers for security | Potential for unexpected data usage during updates, reliance on reliable internet connectivity |
Strategies for Improving Patch Adoption
Encouraging timely patching requires a multi-pronged approach that combines technical solutions with improved communication and user education. Simply mandating updates isn’t enough; users need to understand
-why* updates are important and how they benefit them personally.
Strategies should include clear and concise communication about the importance of security updates, simplifying the update process to minimize disruption, providing regular feedback to users on their patching status, and offering accessible technical support for those who need assistance. Gamification techniques, such as reward systems for timely updates, could also be considered.
Challenges of Patching in Large Enterprise Environments
Patching in large organizations presents unique complexities. The sheer number of devices, diverse operating systems and applications, and the need to minimize disruption to business operations make it a significant undertaking. Effective patch management requires robust infrastructure, skilled personnel, and well-defined processes. Centralized patch management systems are crucial, but even with these systems, challenges remain. Testing patches in a controlled environment before deploying them across the entire organization is essential to prevent unforeseen issues.
The need to balance security with operational efficiency is a constant challenge. For example, a large financial institution might need to carefully schedule updates to minimize downtime during peak trading hours.
The Future of Software Updates
The traditional Patch Tuesday model, while serving its purpose for many years, is increasingly showing its limitations in the face of rapid software development cycles and the ever-evolving threat landscape. The future of software updates will be characterized by a move away from the rigid, scheduled approach towards more agile, continuous, and automated processes, driven by advancements in technology and a greater understanding of user needs and security risks.The shift towards continuous delivery and integration models, already prevalent in DevOps practices, is fundamentally changing how software is updated.
This means smaller, more frequent updates instead of large, infrequent patches, reducing the disruption to users and minimizing the window of vulnerability. This approach also allows for quicker responses to newly discovered vulnerabilities.
Automated Patching and Self-Healing Systems
Automated patching, leveraging machine learning and AI, will become the norm. Systems will be able to identify vulnerabilities, download and install necessary patches autonomously, and even roll back updates if issues arise. This will minimize the reliance on manual intervention, reducing the risk of human error and improving overall security posture. Imagine a scenario where your operating system automatically detects and patches a critical vulnerability in the background, without requiring any user interaction, similar to how antivirus software operates today, but encompassing all software components.
This level of automation promises to significantly improve system resilience and reduce the attack surface.
AI and Machine Learning in Patch Management
Artificial intelligence and machine learning will play a crucial role in predicting and mitigating security risks. AI algorithms can analyze vast amounts of data—from vulnerability databases to user behavior patterns—to identify potential threats and prioritize patches accordingly. This predictive capability allows for proactive patching, addressing vulnerabilities before they can be exploited. For instance, an AI system could analyze code changes during development to identify potential security flaws before they are even released, preventing vulnerabilities from ever reaching production environments.
This proactive approach is a significant leap forward from the reactive patching strategies of the past.
A Potential Future Update Model: Microservices and Patching
One potential future update model involves the adoption of microservices architecture. Instead of updating large monolithic applications, individual microservices can be updated independently. This modular approach allows for granular control over updates, minimizing downtime and reducing the impact of potential errors. For example, an e-commerce platform might have separate microservices for user authentication, product catalog, and payment processing.
A vulnerability in the payment processing service can be patched without affecting other functionalities.Advantages of this model include reduced downtime, improved scalability, and easier rollback capabilities. However, managing numerous microservices and their respective patches can be complex, requiring robust orchestration and monitoring tools. This necessitates a sophisticated infrastructure and expertise in managing complex distributed systems. The initial investment might be higher, but the long-term benefits in terms of stability and security could outweigh the costs.
Closure
So, is Patch Tuesday dead? Not entirely. While the rigid, once-a-month schedule might be fading into the background, the fundamental need for regular software updates remains paramount. The shift is towards more agile, continuous patching strategies, tailored to the specific needs of individual systems and organizations. The future of software updates is likely to be a blend of automated patching, proactive vulnerability management, and a heightened awareness among users about the importance of keeping their software up-to-date.
The battle against cyber threats is ongoing, and staying ahead of the curve through proactive and continuous patching is more critical than ever.
Commonly Asked Questions: Is Patch Tuesday Dead
What are zero-day exploits?
Zero-day exploits are attacks that target software vulnerabilities before the vendor is aware of them, making them particularly dangerous. There’s no patch available yet.
How often should I update my software?
It depends on your software and your risk tolerance. Ideally, updates should be installed as soon as they are available. Prioritize critical security updates.
What are some common types of vulnerabilities?
Common vulnerabilities include buffer overflows, SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks.
What is automated patching?
Automated patching uses software to automatically download and install updates, reducing manual effort and improving consistency.