Island Hopping A Rising Cyber Attack Threat
Island hopping becomes an increasingly popular cyber attack, and it’s seriously worrying. This sneaky tactic, where hackers hop from one compromised system to another, is becoming a major headache for businesses and organizations of all sizes. Think of it like a digital game of hopscotch, but instead of chalk, it’s stolen data and compromised systems. We’re diving deep into this escalating threat, exploring how it works, why it’s so effective, and what you can do to protect yourself.
From healthcare providers to financial institutions, no one is immune. We’ll look at real-world examples, examine the vulnerabilities hackers exploit, and uncover the strategies used to both detect and prevent these attacks. Get ready to learn how to safeguard your digital world from this increasingly prevalent threat.
Defining Island Hopping Attacks
Island hopping, in the context of cybersecurity, isn’t about sun-drenched vacations; it’s a sophisticated attack method where malicious actors leverage a series of compromised systems to reach their ultimate target. This technique allows attackers to bypass traditional security measures and move laterally within a network, often remaining undetected for extended periods. Understanding the mechanics and impact of these attacks is crucial for bolstering organizational defenses.Island hopping attacks exploit vulnerabilities in multiple systems, using each compromised system as a stepping stone to infiltrate another, eventually reaching the desired target.
The attacker might initially compromise a less secure system, such as a poorly protected IoT device or a vulnerable employee workstation. This initial foothold then serves as a base to launch further attacks against more critical systems within the network, utilizing techniques like exploiting known vulnerabilities, phishing, or social engineering. The attacker’s movement is often masked by the seemingly legitimate traffic between these intermediate systems, making detection difficult.
Types of Island Hopping Attacks and Targeted Infrastructures
Island hopping attacks can target various critical infrastructures. For example, in the financial sector, attackers might compromise a small bank’s system to gain access to their network and then use that access to move laterally towards larger financial institutions. In healthcare, an attacker could begin by compromising a medical device or a less secure hospital system before moving towards patient databases or electronic health records.
The versatility of this attack method allows attackers to tailor their approach to the specific vulnerabilities present within a target’s network infrastructure. They might use different methods of lateral movement depending on the target’s security posture.
Real-World Case Studies of Island Hopping Attacks
The NotPetya ransomware attack of 2017 serves as a chilling example of a large-scale island hopping attack. While initially disguised as a tax software update, NotPetya spread rapidly through compromised systems, causing widespread disruption and billions of dollars in damages across numerous industries globally. The attack’s success stemmed from its ability to exploit vulnerabilities in widely used software, allowing it to hop from system to system with ease.
The attackers utilized a software update mechanism to spread laterally, making it incredibly difficult to contain. Another notable example is the 2014 Target data breach, where attackers gained initial access through a third-party vendor’s HVAC system and then moved laterally through the network to access sensitive customer data. This highlights the vulnerability of supply chains and the importance of securing even seemingly insignificant systems.
These examples demonstrate the devastating consequences of successful island hopping attacks, emphasizing the need for robust security measures and proactive threat detection.
Vulnerabilities Exploited in Island Hopping

Island hopping attacks rely on exploiting weaknesses in multiple systems to achieve their objectives. Attackers don’t just target a single vulnerability; instead, they strategically chain together several compromises, moving laterally across a network like stepping stones across an archipelago. Understanding the common vulnerabilities exploited is crucial for effective defense.Attackers leverage a range of vulnerabilities to gain initial access and then traverse the network.
This often involves a combination of technical weaknesses and human error. Once a foothold is established, attackers use this access to hunt for further weaknesses, expanding their control until they reach their target. This process can be slow and methodical, making detection difficult.
Common Vulnerabilities and Exploitation Techniques, Island hopping becomes an increasingly popular cyber attack
The success of an island hopping attack hinges on the attacker’s ability to exploit a series of vulnerabilities. These vulnerabilities often stem from outdated software, weak or reused passwords, and unpatched systems, creating pathways for lateral movement.
| Vulnerability Type | Exploitation Technique | Impact | Mitigation Strategy |
|---|---|---|---|
| Outdated Software | Exploiting known vulnerabilities in older software versions through malware, phishing, or social engineering. Attackers leverage publicly available exploit kits or custom-developed tools. | Compromised system, data breaches, lateral movement to other systems. | Regular software updates and patching, vulnerability scanning, and robust change management processes. |
| Weak Passwords/Password Reuse | Brute-force attacks, credential stuffing, phishing attacks to obtain credentials. Attackers leverage stolen credentials to access multiple accounts. | Account takeover, unauthorized access to sensitive data and systems. | Strong password policies, multi-factor authentication (MFA), password managers, regular password rotation, security awareness training. |
| Unpatched Systems | Exploiting known vulnerabilities in unpatched systems using publicly available exploits or custom-developed tools. | System compromise, data breaches, malware infections, lateral movement. | Regular security patching, vulnerability scanning, and automated patch management systems. |
| Misconfigured Systems | Exploiting default credentials, open ports, or improperly configured services to gain unauthorized access. | Unauthorized access to systems and data. | Regular security audits, secure configuration baselines, and principle of least privilege. |
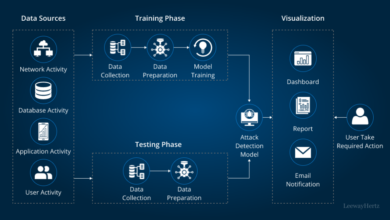
Detection and Prevention Strategies
Island hopping attacks, while sophisticated, are not insurmountable. Effective detection and prevention require a multi-layered approach that combines proactive security measures with robust monitoring and response capabilities. By understanding the attack vectors and implementing appropriate safeguards, organizations can significantly reduce their vulnerability.Proactive measures are crucial in preventing island hopping attacks before they even begin. This involves strengthening the overall security posture and making it more difficult for attackers to gain an initial foothold.
A strong defense-in-depth strategy is key.
Network Segmentation
Network segmentation divides a network into smaller, isolated segments. This limits the impact of a breach, preventing attackers from easily moving laterally across the entire network. If an attacker compromises a system in one segment, they are prevented from accessing other critical systems in different segments. Implementing strict access control policies between segments further enhances security. For example, a company might segment its network into zones for guest Wi-Fi, employee workstations, and sensitive server infrastructure.
Each zone would have its own firewalls and access controls, limiting the potential damage from a compromised device.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS systems play a vital role in detecting and preventing malicious activity. IDS monitors network traffic for suspicious patterns, alerting administrators to potential threats. IPS goes a step further, actively blocking malicious traffic based on predefined rules or signatures. A well-configured IDS/IPS can identify unusual lateral movement, such as unauthorized access attempts to sensitive servers or databases, indicating a possible island hopping attack.
For instance, an IDS might detect repeated failed login attempts from an internal IP address to a high-value server, which could signal an attacker trying to escalate privileges.
Security Information and Event Management (SIEM) Systems
SIEM systems centralize and analyze security logs from various sources across the network. This provides a comprehensive view of security events, enabling security analysts to identify suspicious patterns and correlate events to detect advanced attacks, including island hopping. By analyzing log data, SIEM systems can detect anomalous behavior, such as unusual login times, access from unexpected locations, or multiple failed login attempts from the same IP address.
This correlation of events allows for faster identification of lateral movement and quicker response times. For example, a SIEM system might detect a user logging in from an unusual location, followed by access to sensitive files, and then attempts to access other systems, all indicating a potential island hopping attack.
Endpoint Security Best Practices
Effective endpoint security is critical in preventing lateral movement. Implementing the following best practices minimizes the risk of an attacker using compromised endpoints to hop between systems:
- Regular Patching and Updates: Keeping all software, including operating systems, applications, and firmware, updated with the latest security patches is crucial to prevent exploitation of known vulnerabilities.
- Strong Password Policies: Enforcing strong, unique passwords and multi-factor authentication (MFA) significantly reduces the risk of unauthorized access.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection and response capabilities on endpoints, identifying and mitigating malicious activity in real-time.
- Antivirus and Antimalware Software: Regularly updated antivirus and antimalware software is essential for detecting and removing malware that could be used to facilitate lateral movement.
- Principle of Least Privilege: Granting users only the necessary permissions to perform their job reduces the impact of a compromised account.
- Regular Security Audits: Conducting regular security audits helps identify vulnerabilities and misconfigurations that could be exploited by attackers.
The Increasing Popularity of Island Hopping
Island hopping, a cyberattack technique that leverages multiple compromised systems as stepping stones to reach a final target, is rapidly gaining popularity. This contrasts with more direct attack methods, highlighting a shift in attacker strategies and the evolving threat landscape. Understanding this rise is crucial for developing effective defenses.Island hopping presents a compelling alternative to other attack methods like phishing and ransomware.
While phishing relies on social engineering and ransomware focuses on data encryption for extortion, island hopping offers a more stealthy and persistent approach. It allows attackers to bypass traditional perimeter security measures by moving laterally through a network of compromised systems, often remaining undetected for extended periods.
Advantages and Disadvantages of Island Hopping Compared to Other Attack Methods
Island hopping’s advantages lie in its stealth and persistence. Attackers can exploit vulnerabilities in less-protected systems to gain a foothold, then use these compromised systems to move towards their ultimate target, often a high-value asset. This makes detection significantly harder than, say, a direct ransomware attack, which typically involves immediate encryption and a ransom demand. However, island hopping requires more technical expertise and planning, making it a less accessible tactic for less-skilled attackers.
The complexity also increases the risk of detection if any single compromised system is investigated thoroughly. Phishing, on the other hand, is simpler to execute but far less subtle and relies heavily on user error. Ransomware is similarly straightforward, but carries a higher risk of immediate detection and legal repercussions.
Factors Contributing to the Rise of Island Hopping Attacks
Several factors are driving the increase in island hopping attacks. The growing interconnectedness of systems, fueled by cloud adoption and the Internet of Things (IoT), provides a vast network of potential stepping stones. Remote work, while offering flexibility, also expands the attack surface by introducing numerous home networks and devices into the corporate ecosystem, each potentially vulnerable. The increase in the number of IoT devices, many with weak security, further expands the pool of potential entry points for attackers.
Island hopping attacks, where hackers move laterally through a network, are becoming a serious threat. Building robust security requires strong, adaptable systems, and that’s where learning more about domino app dev, the low-code and pro-code future , comes in. Understanding these development approaches can help organizations create more secure and resilient applications, ultimately making them less vulnerable to these sophisticated island hopping techniques.
Moreover, the sophistication of attack tools readily available on the dark web makes it easier for even relatively unsophisticated actors to execute complex attacks like island hopping. Finally, the increasing reliance on cloud services introduces new complexities and vulnerabilities, especially when cloud security practices are inadequate.
Attacker Perspective: Why Island Hopping is a Favored Tactic
From the attacker’s perspective, island hopping offers several key advantages. The distributed nature of the attack makes it harder to trace back to the origin. By using multiple compromised systems, attackers can mask their true IP address and evade detection by security systems focused on identifying single points of intrusion. The ability to move laterally through a network also allows attackers to explore for valuable data or systems undetected for longer periods.
This provides more time to achieve their objectives, whether it’s data exfiltration, intellectual property theft, or disruption of services. The relatively lower risk of immediate detection compared to other methods makes it a more attractive option for long-term campaigns aimed at gaining persistent access and control over target systems. The long-term access allows attackers to plan further operations and exploit their foothold at the most opportune moment.
This contrasts with the more immediate nature of ransomware attacks, which frequently trigger alarms and prompt rapid responses.
Responding to Island Hopping Attacks
Island hopping attacks, while sophisticated, are not insurmountable. A robust incident response plan, coupled with proactive security measures, significantly reduces the impact and allows for swift recovery. Effective response hinges on speed, accuracy, and a well-defined process. The following Artikels a structured approach.
Incident Response Procedure
A successful response requires a methodical approach. The first step involves immediate isolation of the compromised systems to prevent further lateral movement. This is followed by containment, eradication of the malware, and finally, a thorough post-incident analysis to identify vulnerabilities and implement preventative measures. Failure to follow a structured approach can prolong the attack’s impact and increase recovery costs.
Containment and Eradication Techniques
Containment focuses on limiting the attacker’s access and preventing further damage. This often involves disconnecting infected systems from the network, disabling affected accounts, and implementing firewall rules to block malicious traffic. Eradication involves removing the malware completely. This might include reinstalling operating systems, wiping hard drives, and employing specialized malware removal tools. For example, isolating a compromised server from the network using a network tap to observe traffic patterns before disconnecting it entirely would be a key containment step.
Then, using a combination of antivirus software and manual file system analysis to locate and remove malicious files is a common eradication method.
Post-Incident Analysis and Remediation
Post-incident analysis is crucial for preventing future attacks. This involves a detailed examination of the attack’s timeline, the methods used, and the vulnerabilities exploited. This information is then used to strengthen security measures, such as patching vulnerabilities, implementing stronger access controls, and enhancing intrusion detection systems. For instance, analyzing logs to determine the entry point of the attack, the lateral movement techniques employed, and the data accessed will allow for targeted remediation.
Failure to conduct a thorough post-incident analysis leaves the organization vulnerable to similar attacks in the future. A common remediation strategy might involve implementing multi-factor authentication and enforcing regular security awareness training for employees.
Future Trends and Predictions

Island hopping attacks, while currently a significant threat, are poised for significant evolution in the coming years. The increasing sophistication of attack methods, coupled with the expansion of interconnected systems, suggests a future where these attacks become more frequent, harder to detect, and potentially more devastating in their impact. Understanding these potential trends is crucial for developing effective countermeasures.The convergence of several technological advancements will likely shape the future landscape of island hopping attacks.
We can expect attackers to leverage advancements in artificial intelligence (AI) and machine learning (ML) to automate the process of identifying vulnerable systems, crafting more effective exploits, and even adapting to evolving security measures in real-time. Simultaneously, the growing adoption of the Internet of Things (IoT) and cloud computing will expand the attack surface, providing numerous potential stepping stones for attackers to traverse.
Emerging Technologies and Their Impact
The proliferation of AI and ML will undoubtedly empower both attackers and defenders. Attackers can utilize AI to automate the reconnaissance phase, identifying weak points in network security with greater efficiency than manual methods. For example, an AI-powered tool could scan millions of IoT devices for known vulnerabilities, significantly accelerating the identification of potential entry points. Conversely, defenders can employ AI-driven security information and event management (SIEM) systems to analyze network traffic and identify suspicious activity patterns indicative of an island hopping attack, allowing for quicker detection and response.
The increased use of blockchain technology could potentially improve security by enhancing the integrity and traceability of digital assets and transactions, making it harder for attackers to compromise systems and move laterally. However, the same technology could also be used by attackers to create more resilient and decentralized attack infrastructure.
Visual Representation of Future Impact on Critical Infrastructure
Imagine a visualization: A map of a major city, representing its critical infrastructure—power grids, water treatment plants, hospitals, and communication networks—represented by interconnected nodes. Each node is color-coded, initially green, representing secure systems. As an island hopping attack progresses, a series of nodes change color, starting with a compromised IoT device (a smart meter, for example) in a residential area.
This node turns red. Then, leveraging the compromised meter as a foothold, the attacker gains access to a nearby substation (another node turning red), moving closer to the city’s core power grid. The visualization would show the progression of the attack, with more nodes turning red as the attacker successfully compromises additional systems. Finally, the visualization could highlight the cascading effect, where the compromise of one critical system (e.g., power grid) leads to the failure of others (e.g., hospitals losing power, disrupting medical services).
This visual would powerfully demonstrate the potential widespread disruption and societal impact of a successful island hopping attack against interconnected critical infrastructure. The visualization emphasizes the need for robust security measures across all interconnected systems, highlighting the interconnectedness and vulnerability of modern infrastructure.
Closing Summary: Island Hopping Becomes An Increasingly Popular Cyber Attack

Island hopping attacks are a clear and present danger in today’s hyper-connected world. While the sophistication and frequency of these attacks are growing, so too are the defensive measures. By understanding the mechanics of island hopping, identifying vulnerabilities, and implementing robust security protocols, organizations can significantly reduce their risk. Staying informed, proactive, and adaptable is key to surviving in this ever-evolving cyber landscape.
Remember, vigilance is your best defense.
Answers to Common Questions
What are the long-term consequences of a successful island hopping attack?
Long-term consequences can include significant financial losses, reputational damage, legal repercussions, and the loss of customer trust. Recovery can be lengthy and expensive, potentially impacting business operations for an extended period.
How can I tell if my organization is under an island hopping attack?
Look for unusual network activity, unauthorized access to systems, data exfiltration, and changes to system configurations. Regular security audits and monitoring are crucial for early detection.
Are there any specific industries more vulnerable to island hopping attacks?
Industries with large, complex networks and sensitive data, such as finance, healthcare, and government, are particularly vulnerable due to the potential value of their data and the extensive interconnectedness of their systems.